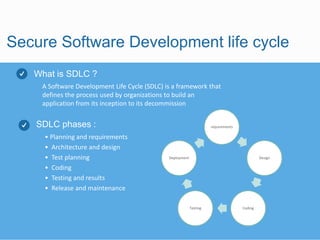
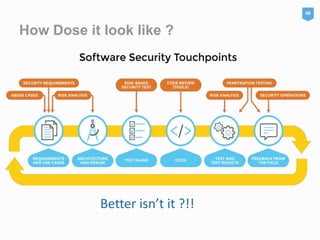
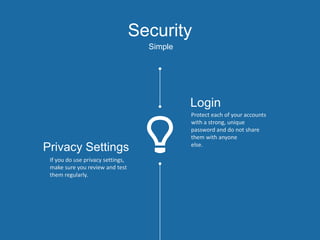
Security is everyone's responsibility. The document discusses secure software development lifecycles (SSDLC), social media security, and information security ethics. It promotes building security into every phase of the software development process from planning through deployment. It emphasizes using strong, unique passwords for all accounts, enabling privacy settings, and being wary of suspicious links and potential scams on social media. The document also outlines a code of ethics for information security professionals, including contributing to society, avoiding harm, being honest, respecting privacy and intellectual property, and knowing and following relevant laws.