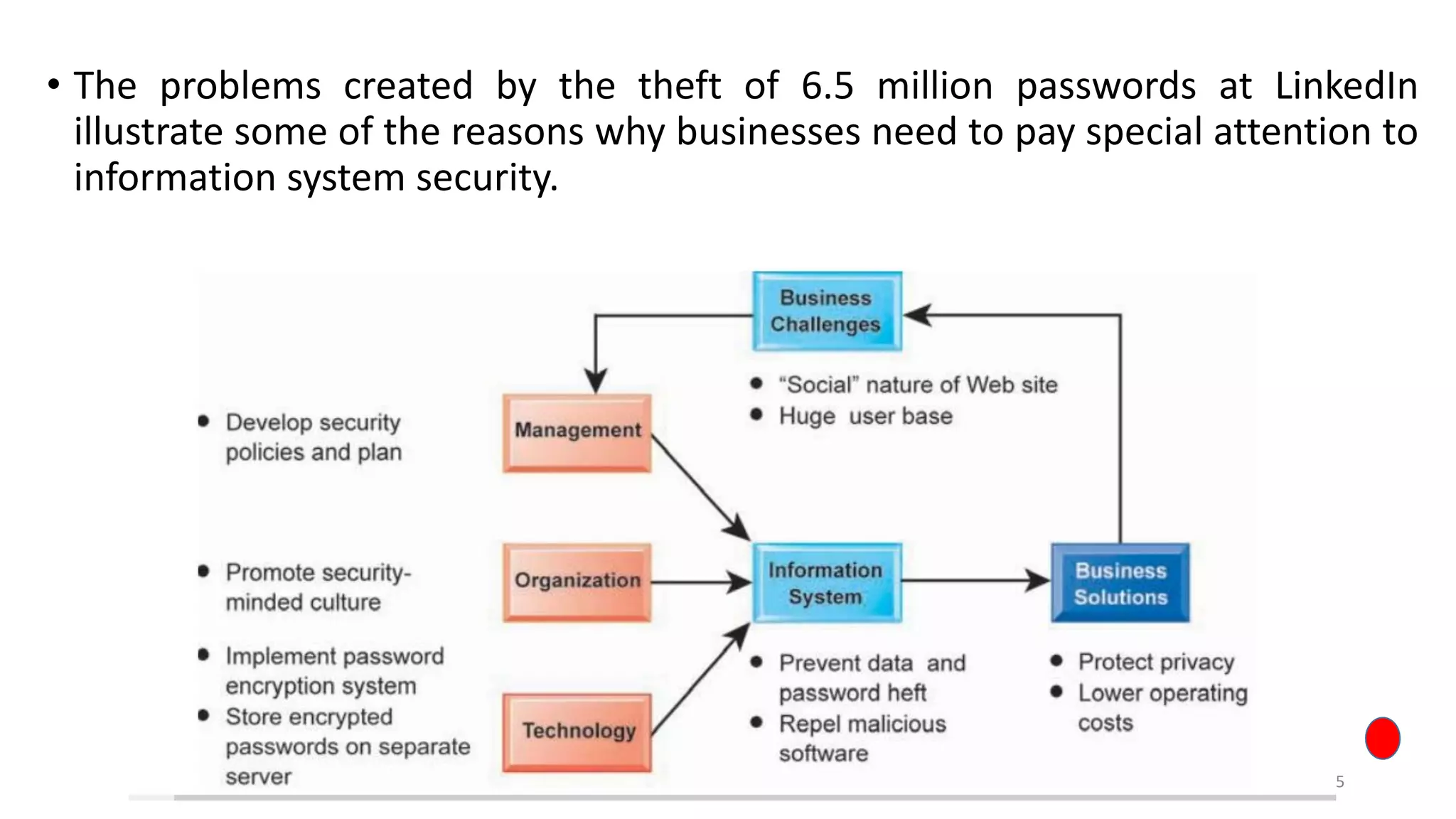
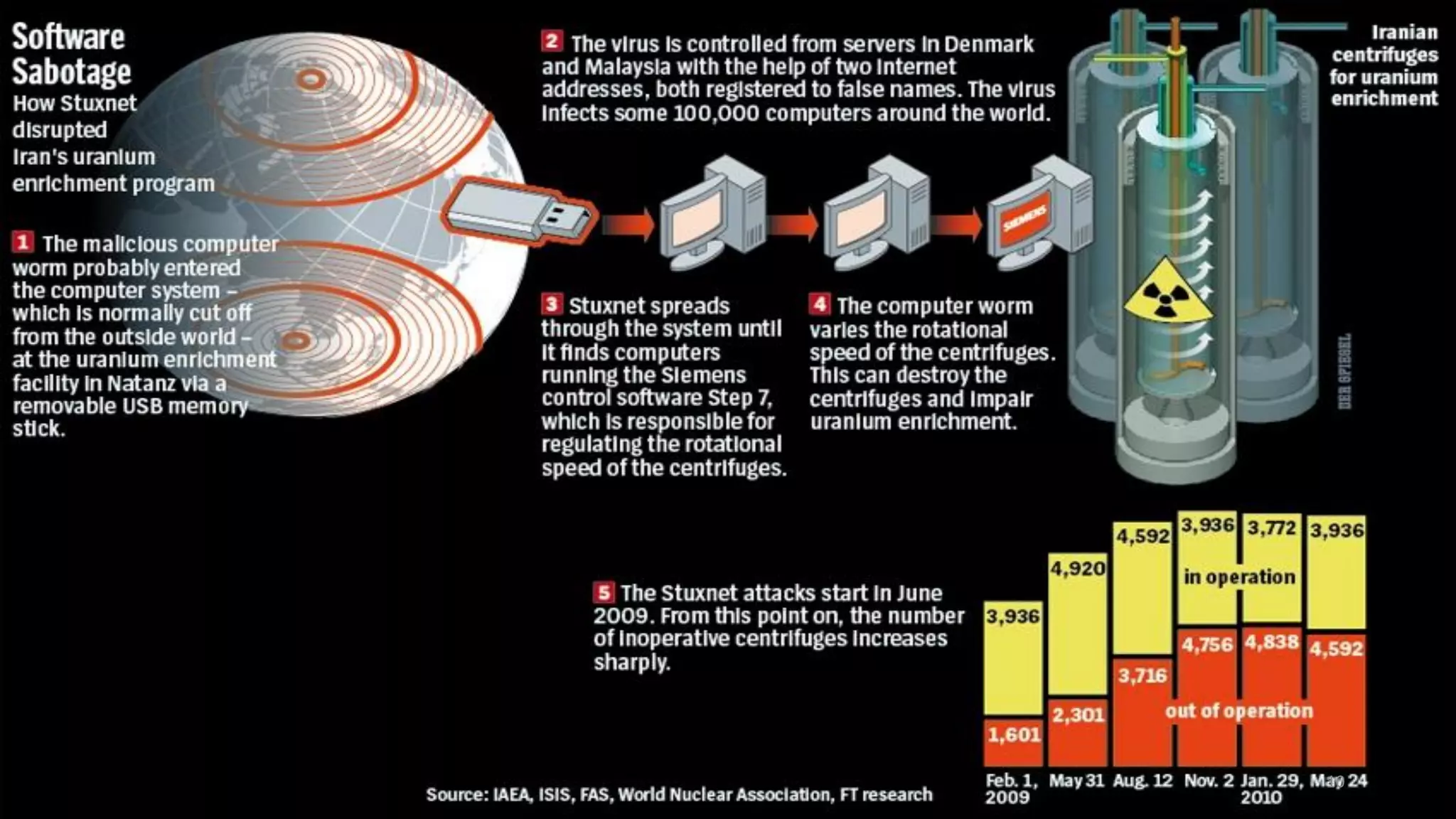
The document discusses LinkedIn's 2012 security breach where 6.5 million user passwords were stolen, resulting in a lawsuit and criticism for inadequate security measures. It also covers the Stuxnet cyber attack on Iran's nuclear facilities, which delayed Iran's nuclear capabilities by five years due to its sophisticated design and nation-state involvement. Additionally, it highlights information security challenges in Europe, including past cyber attacks and initiatives to improve cyber resilience across EU member states.