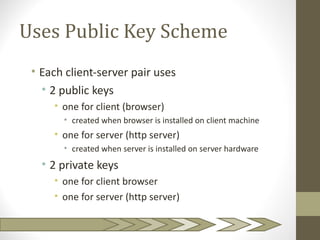
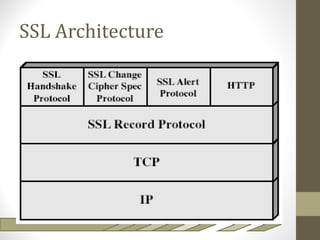
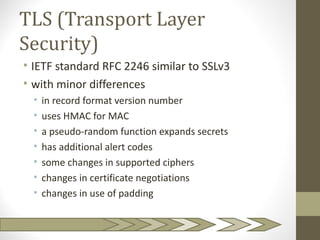
The document discusses SSL and TLS architecture, highlighting their importance for web security amidst various threats such as integrity and confidentiality issues. It covers the ITU-T recommendations and x.800 series that outline a comprehensive security framework, addressing different layers of security including infrastructure, services, and applications. Key mechanisms like the handshake protocol, key exchange, and use of X.509 certificates are explained to illustrate how these protocols ensure secure end-to-end communication over the internet.




































![TLS: Change Cipher Spec,
Finished
Client Server
[ChangeCipherSpec]
Finished
40
[ChangeCipherSpec]
Finished
Application Data Application Data](https://image.slidesharecdn.com/ssltlsarchitectureshort-120507194057-phpapp01/85/SSL-TLS-Architecture-short-40-320.jpg)

![TLS: Using a Session
Client Server
ClientHello (Session #)
ServerHello (Session #)
42
[ChangeCipherSpec]
Finished
[ChangeCipherSpec]
Finished
Application Data Application Data](https://image.slidesharecdn.com/ssltlsarchitectureshort-120507194057-phpapp01/85/SSL-TLS-Architecture-short-42-320.jpg)




