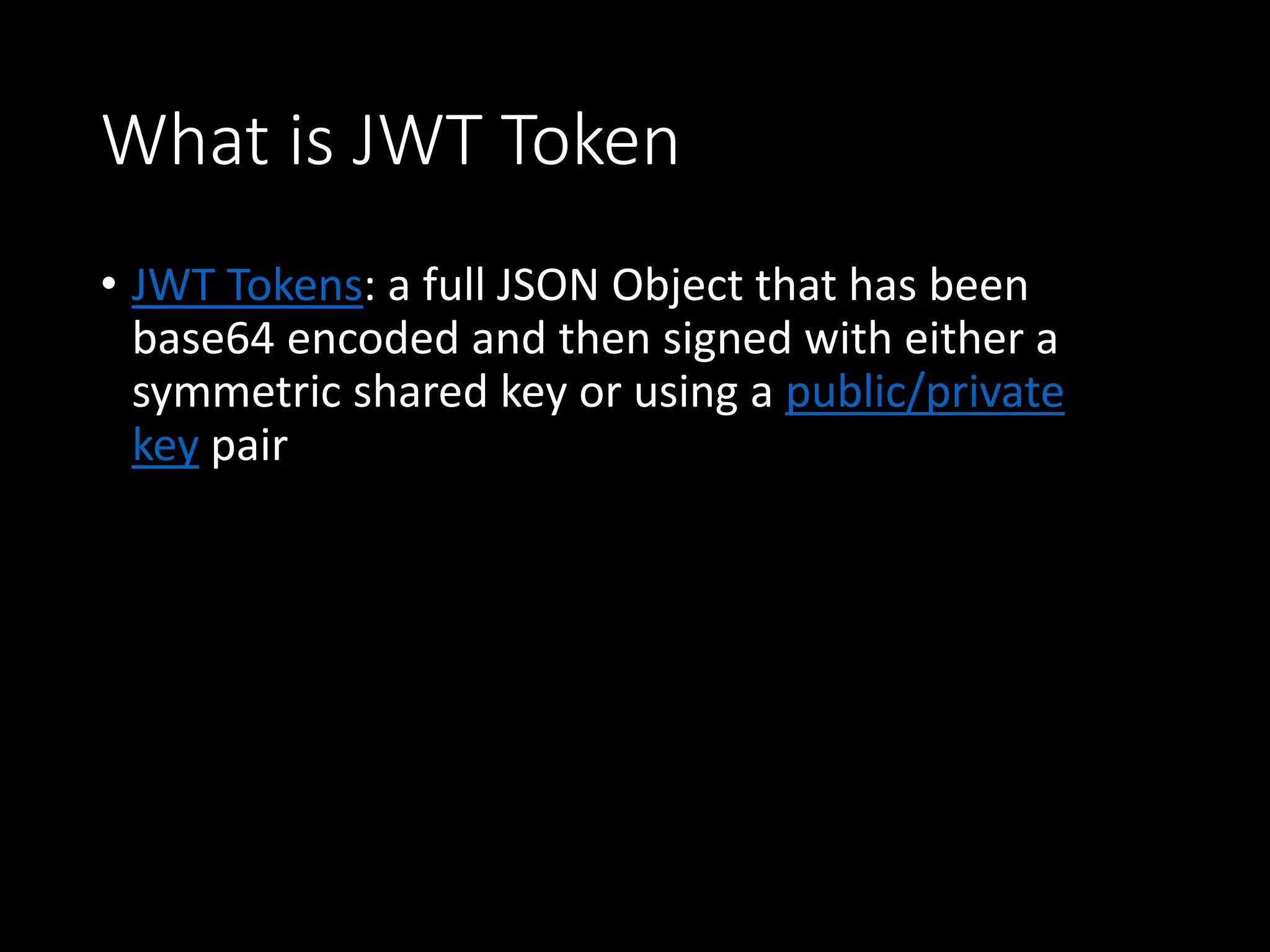
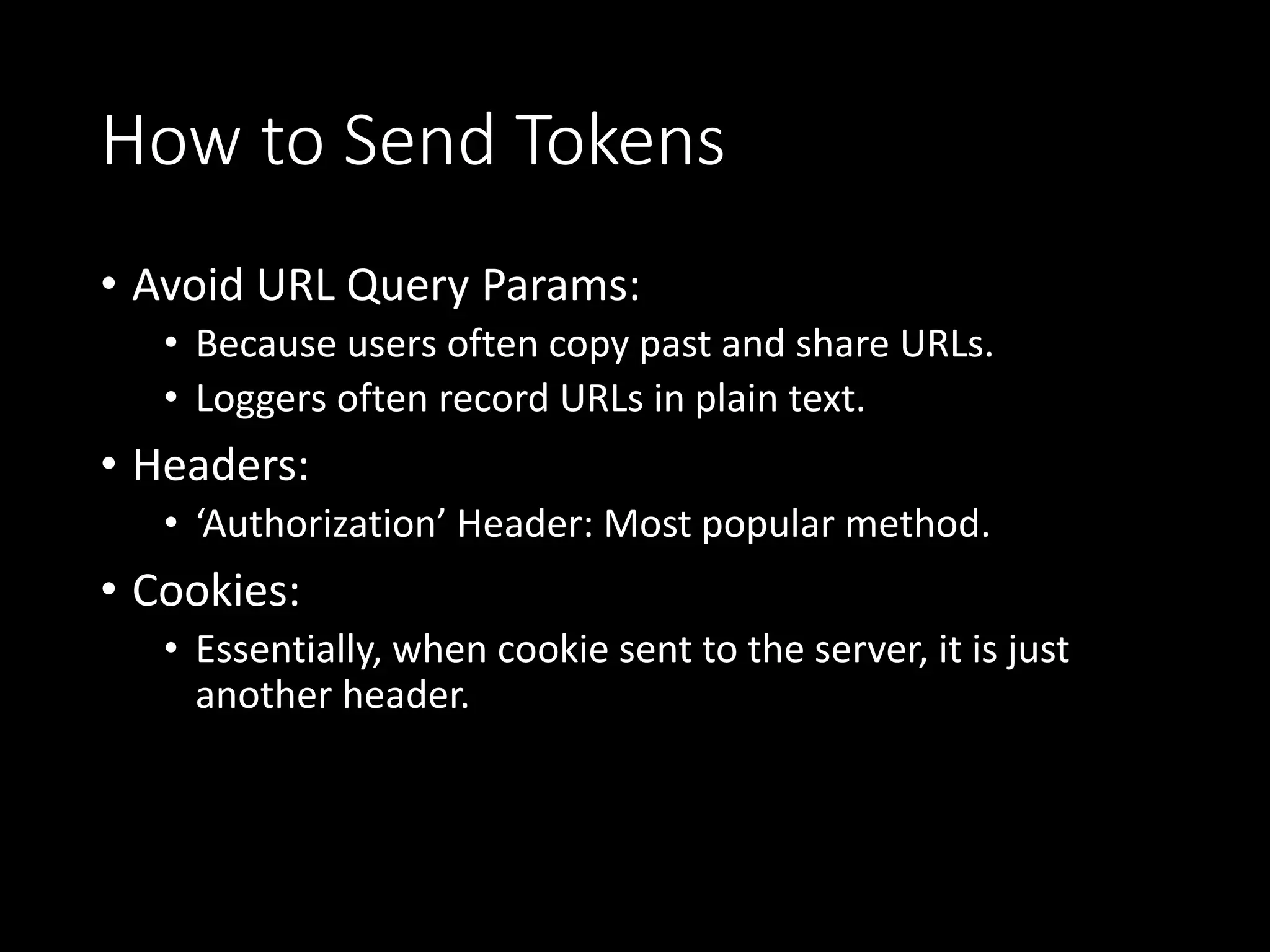
This document is a comprehensive guide for setting up a secure scheme for RESTful APIs, detailing steps for authentication and authorization, as well as options for token types such as JWT and opaque tokens. It discusses the advantages and disadvantages of each token type, how to send them, and methods for storing tokens on the client-side including cookies and local storage. The guide emphasizes the importance of maintaining security while ensuring flexibility in user roles and permissions.