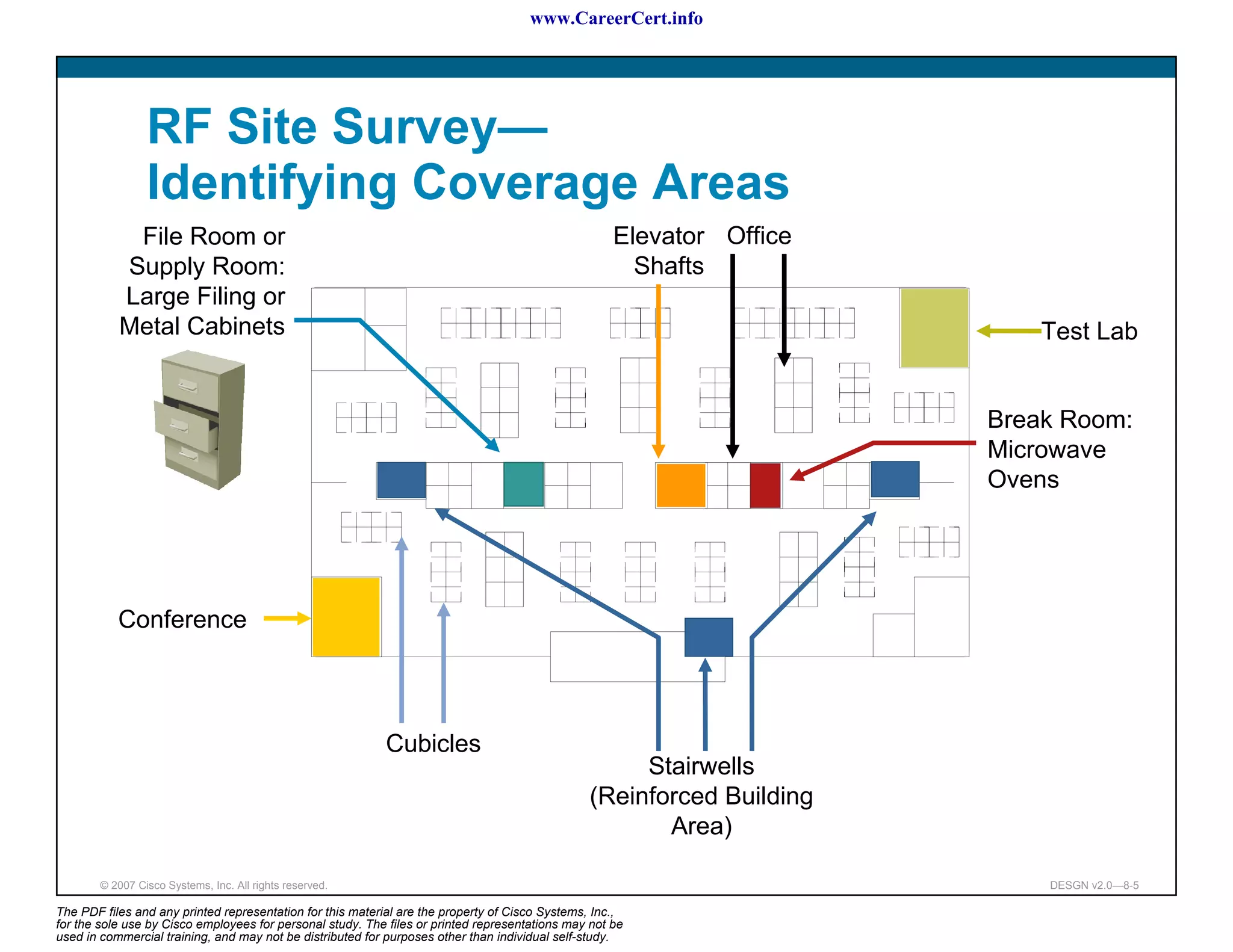
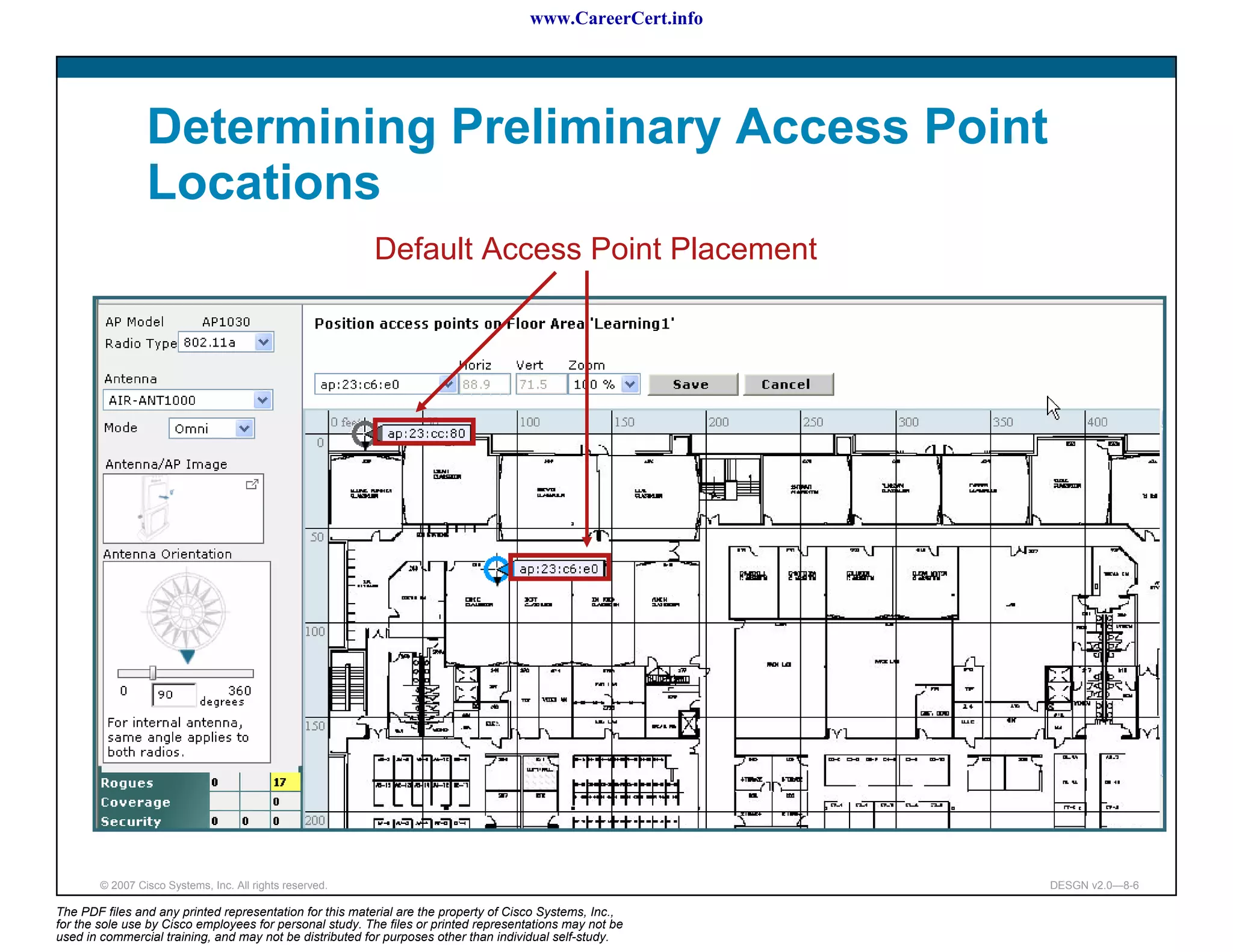
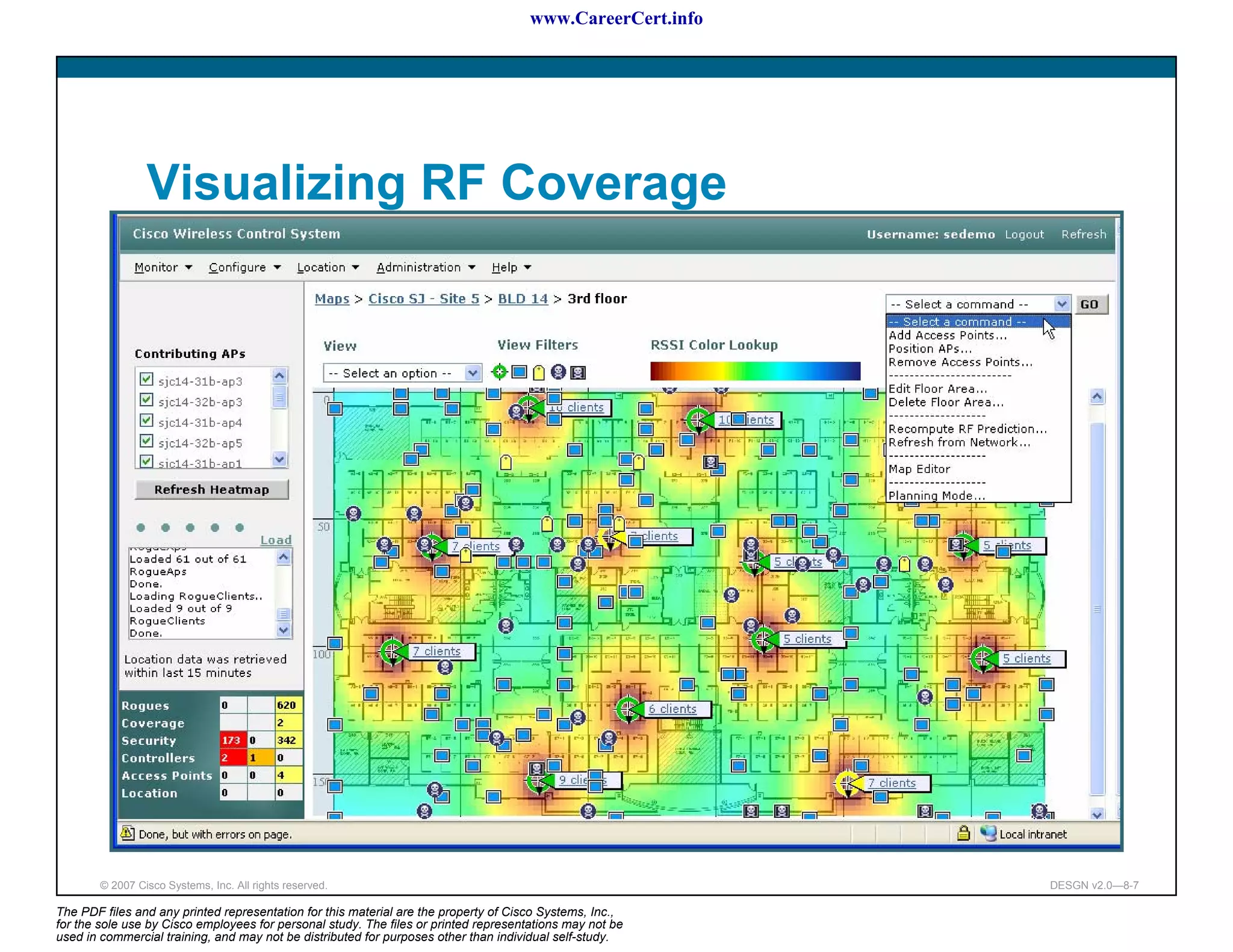
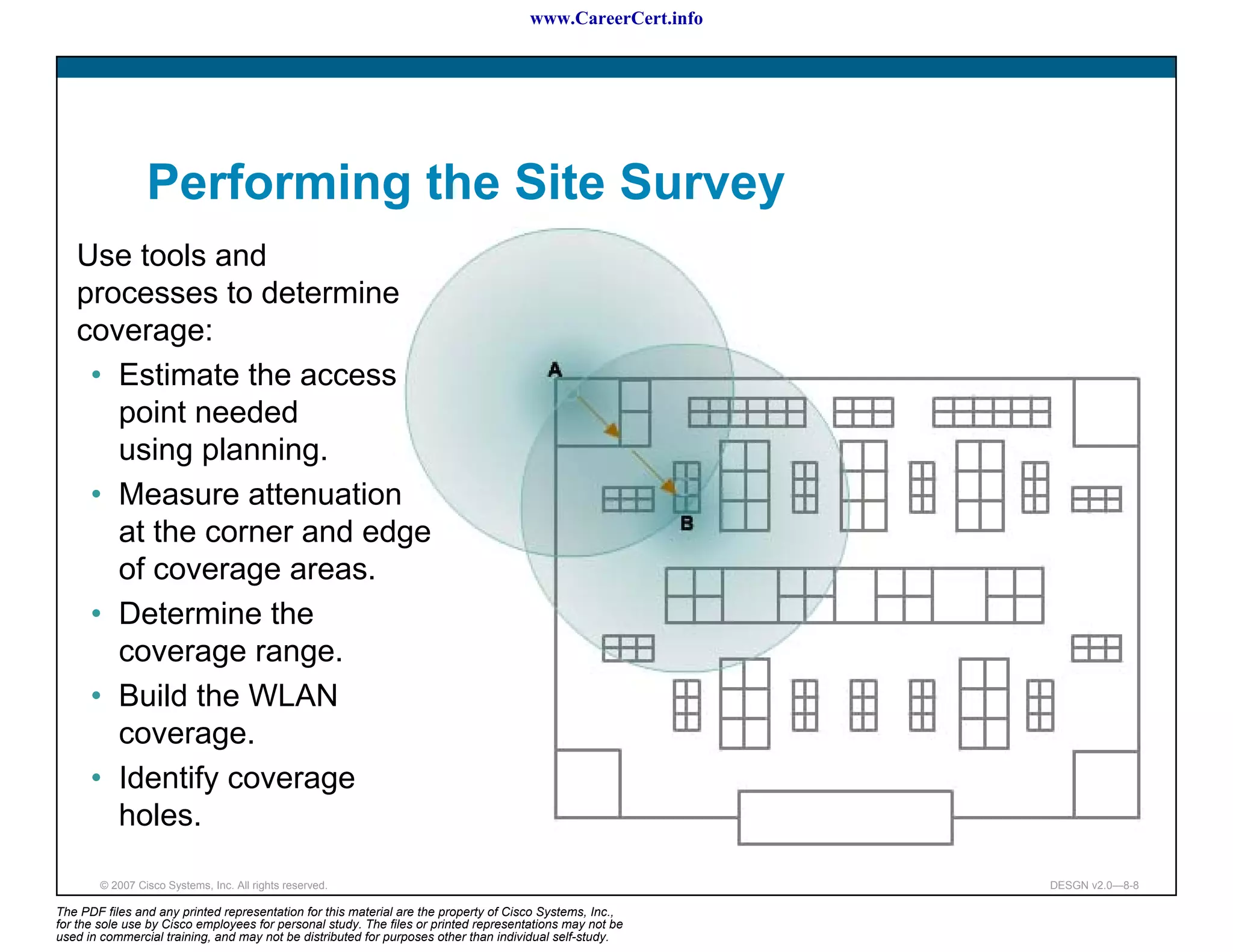
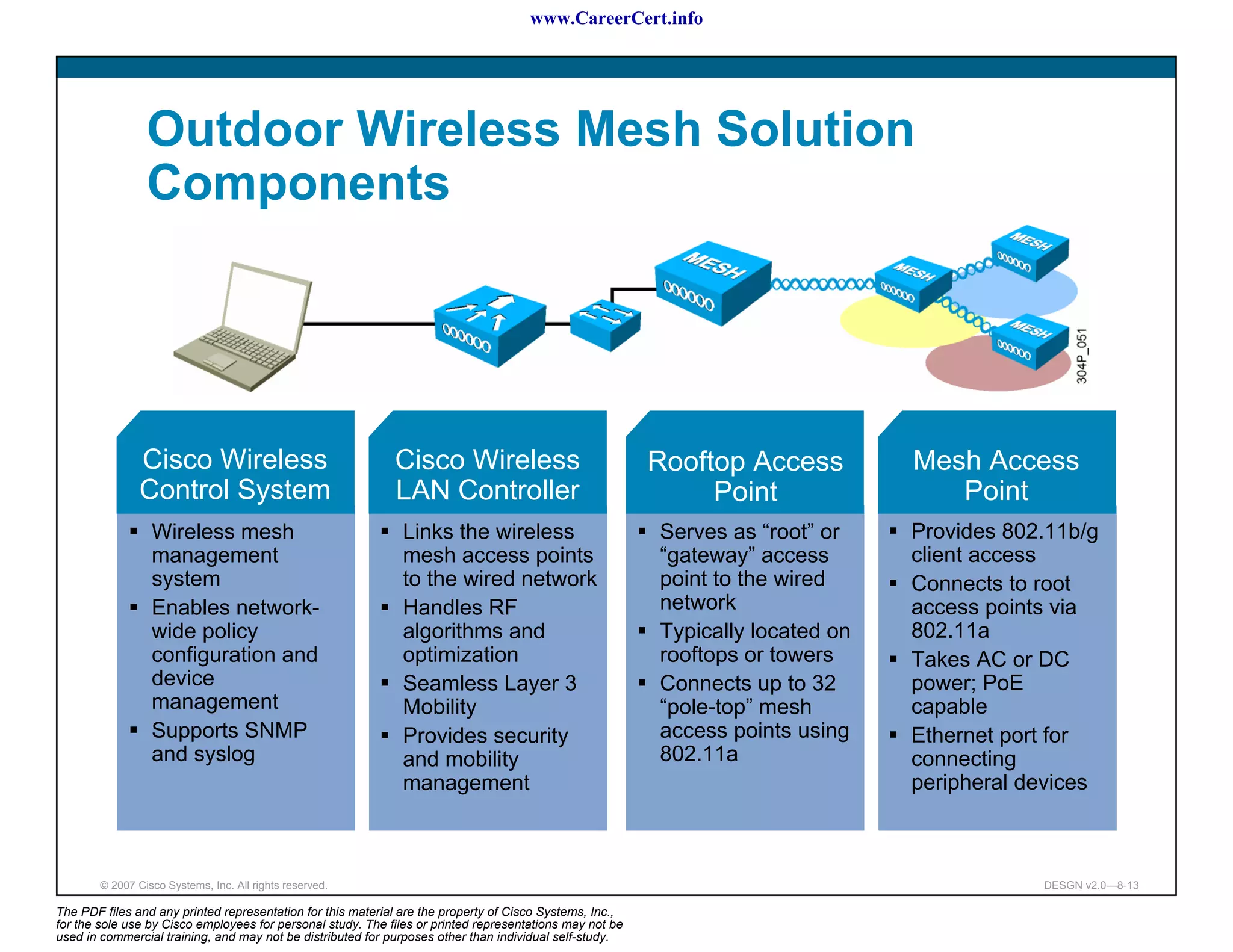
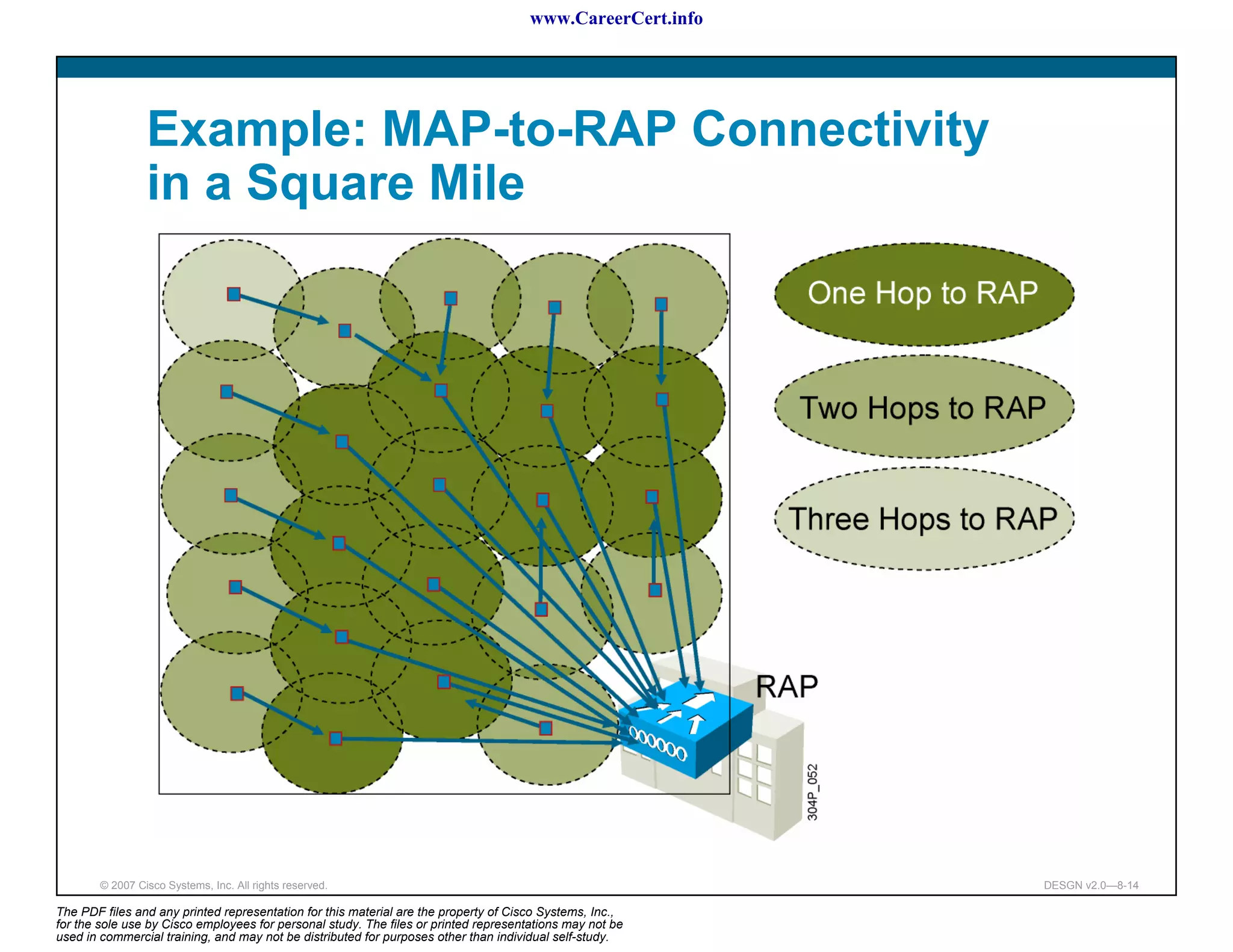
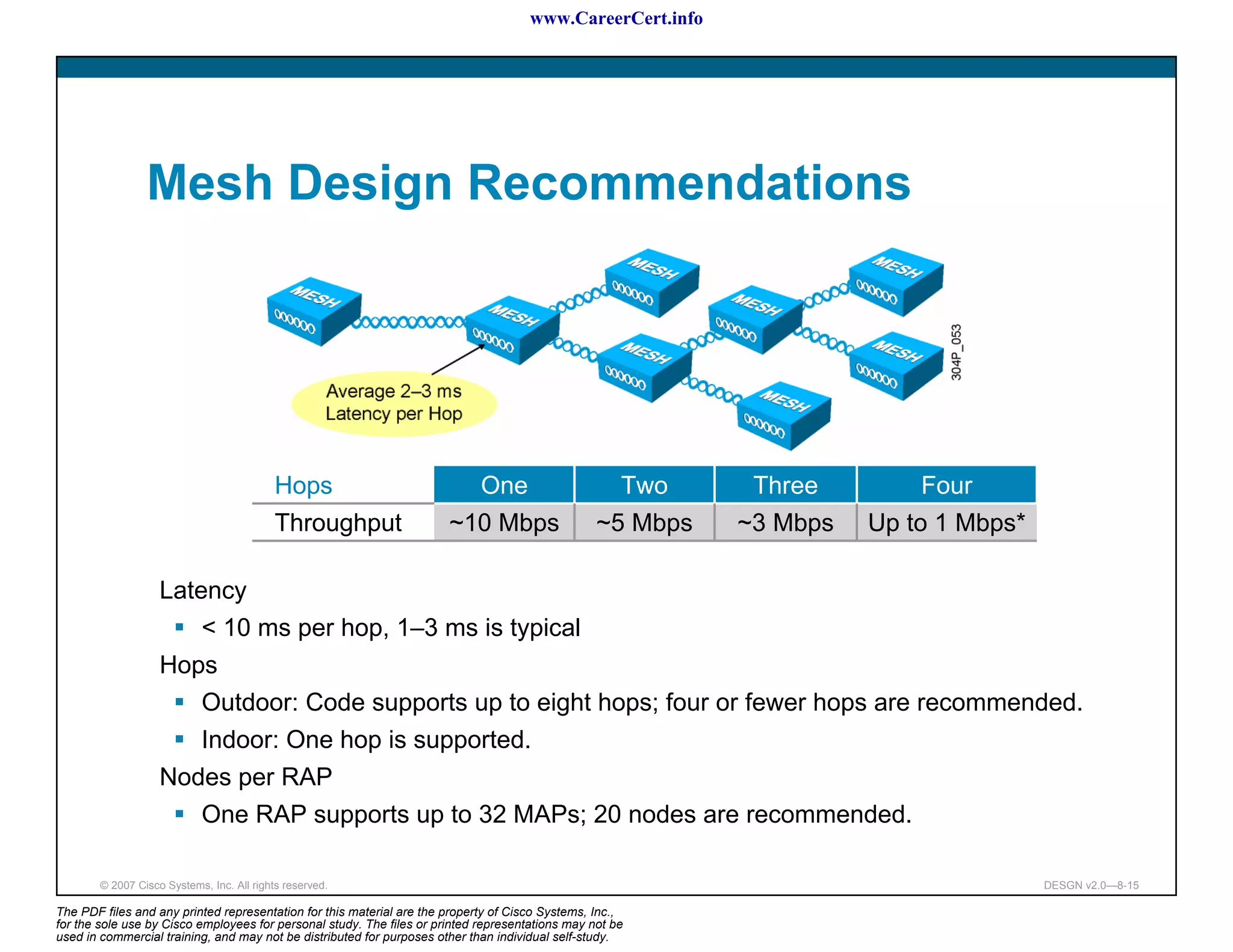
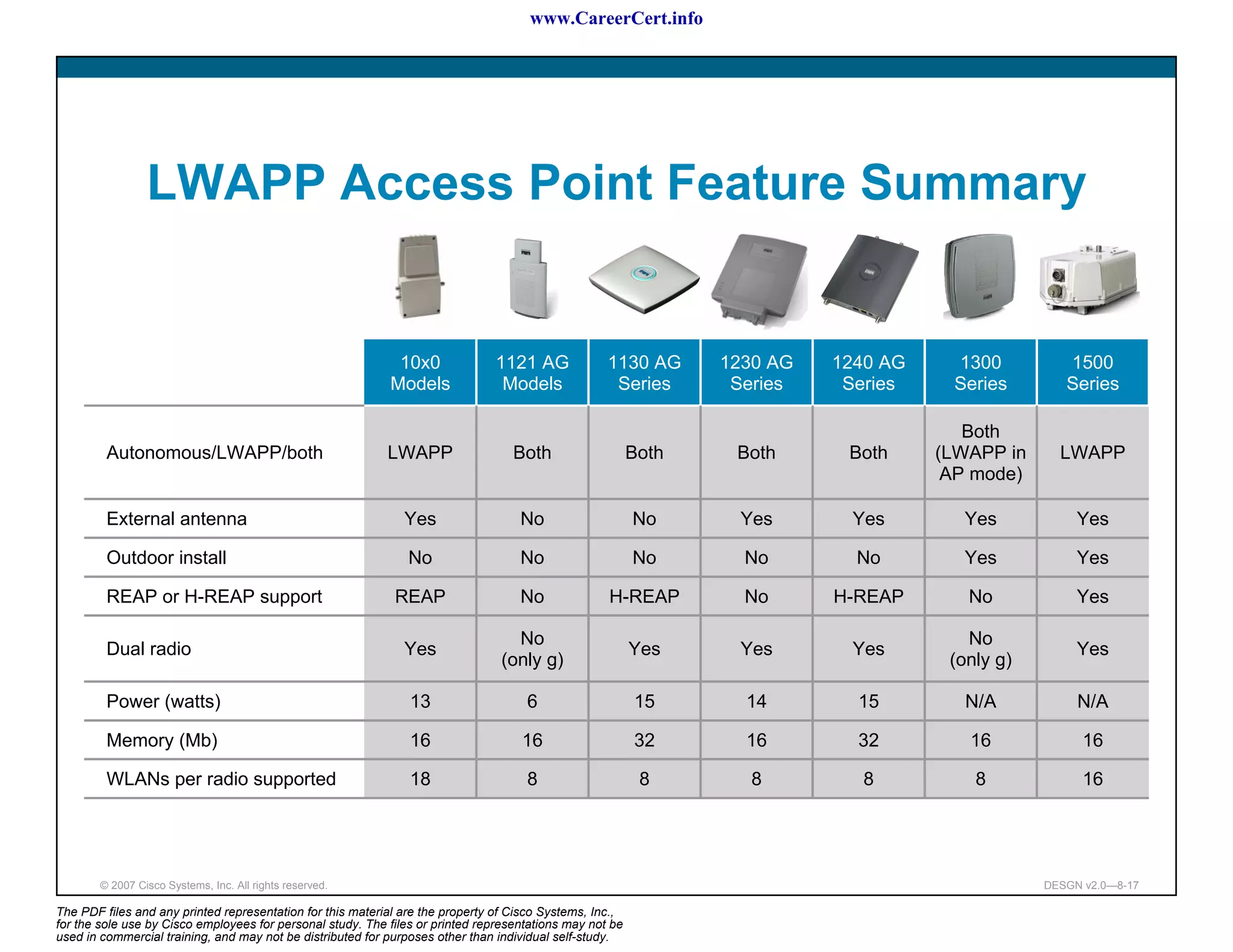
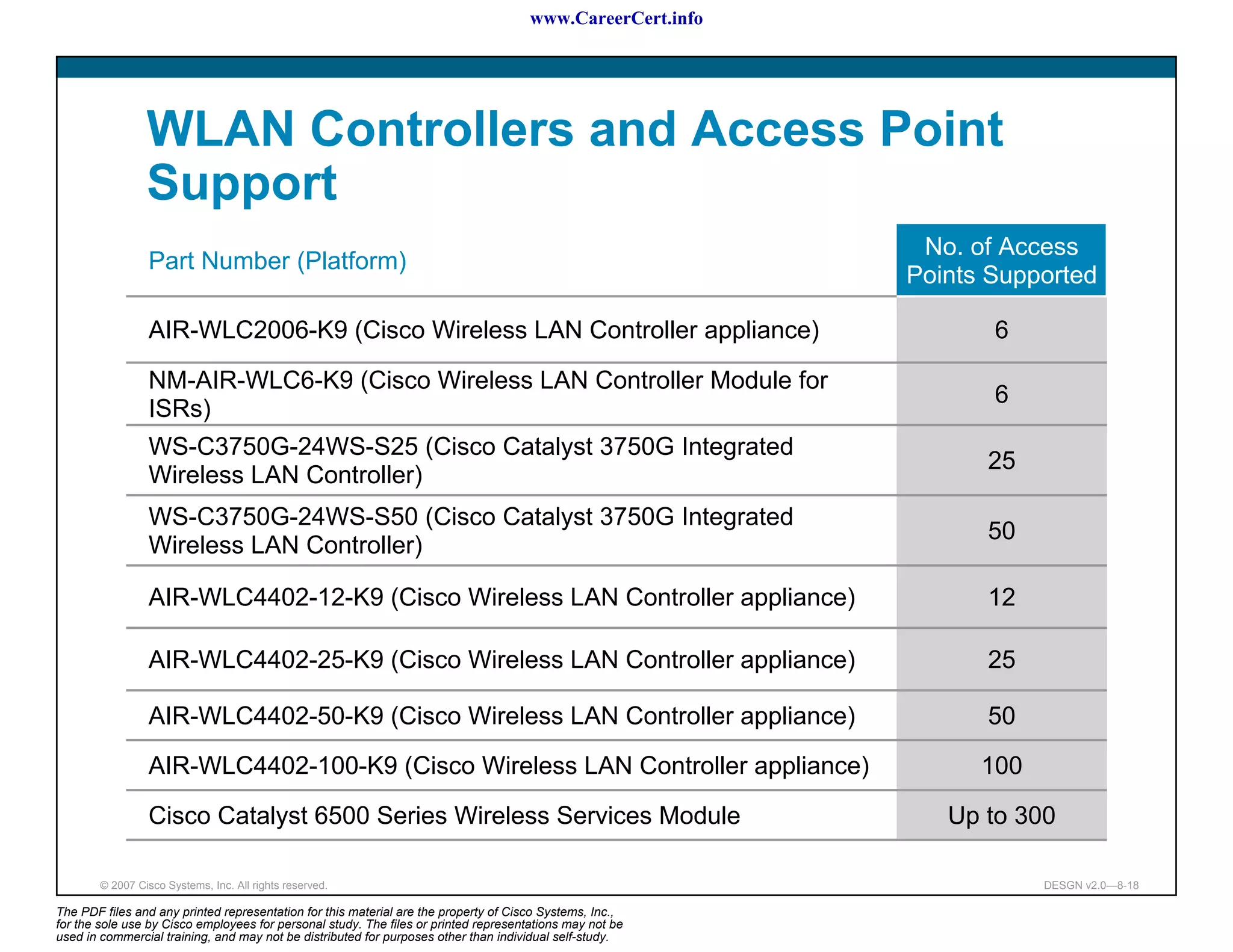
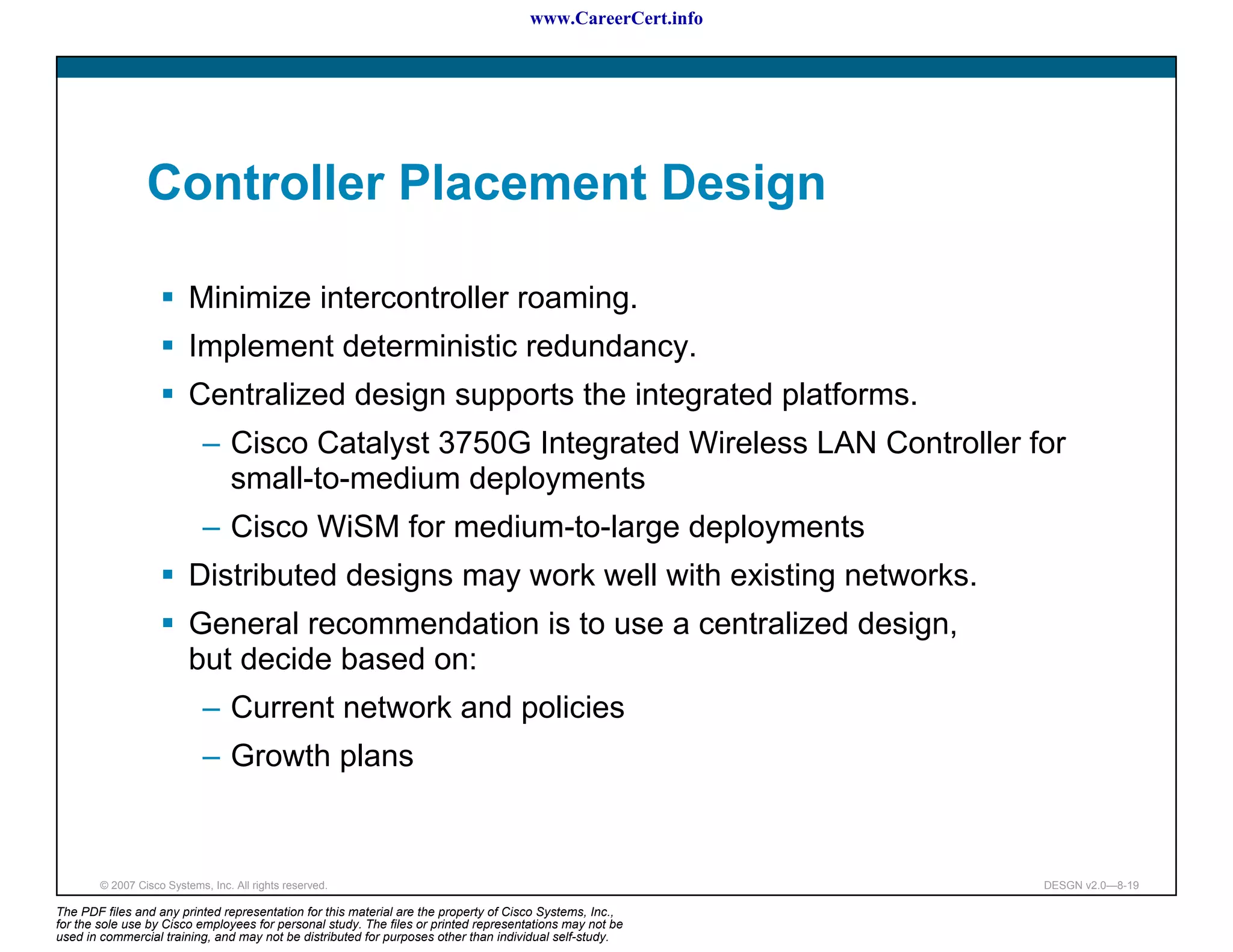
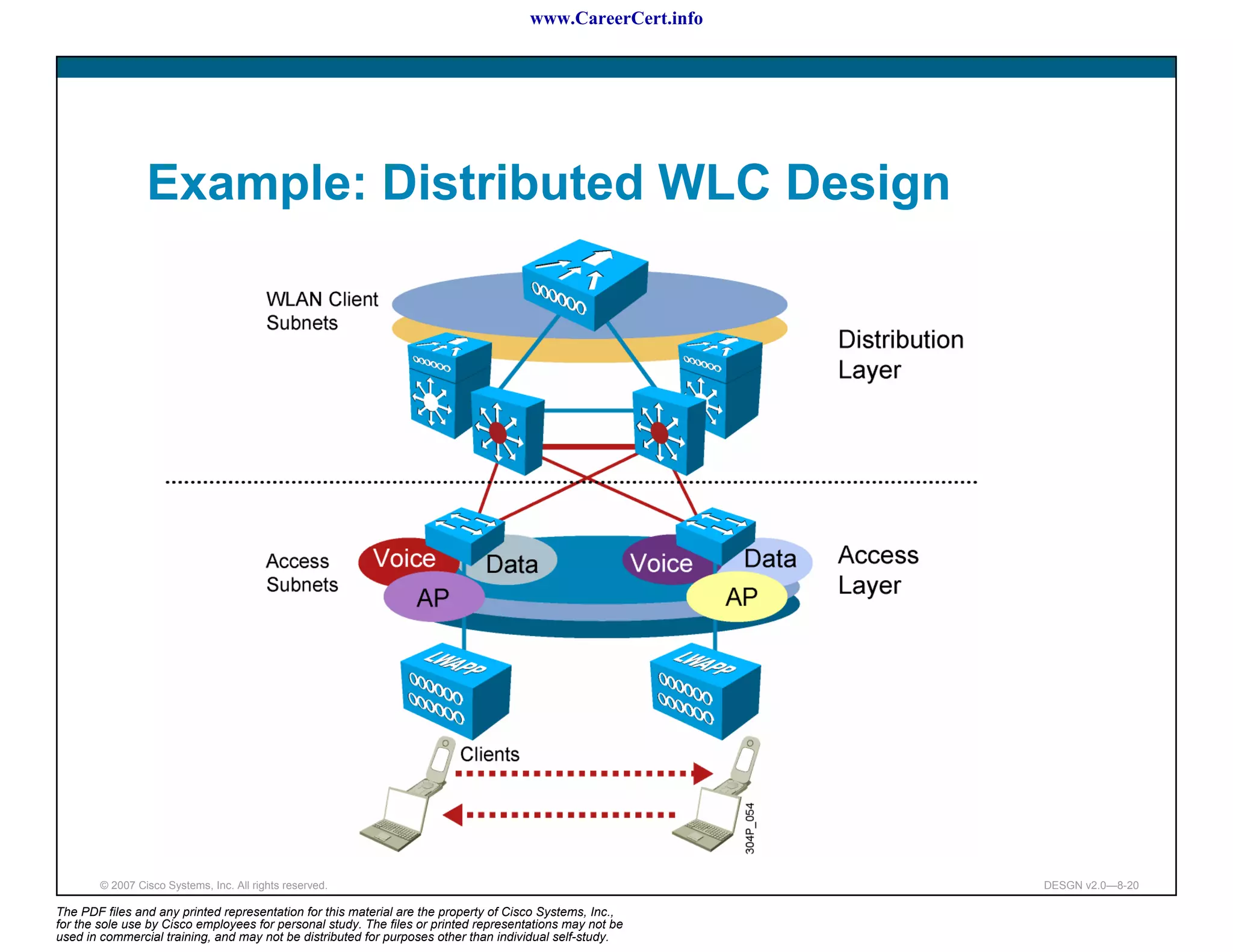
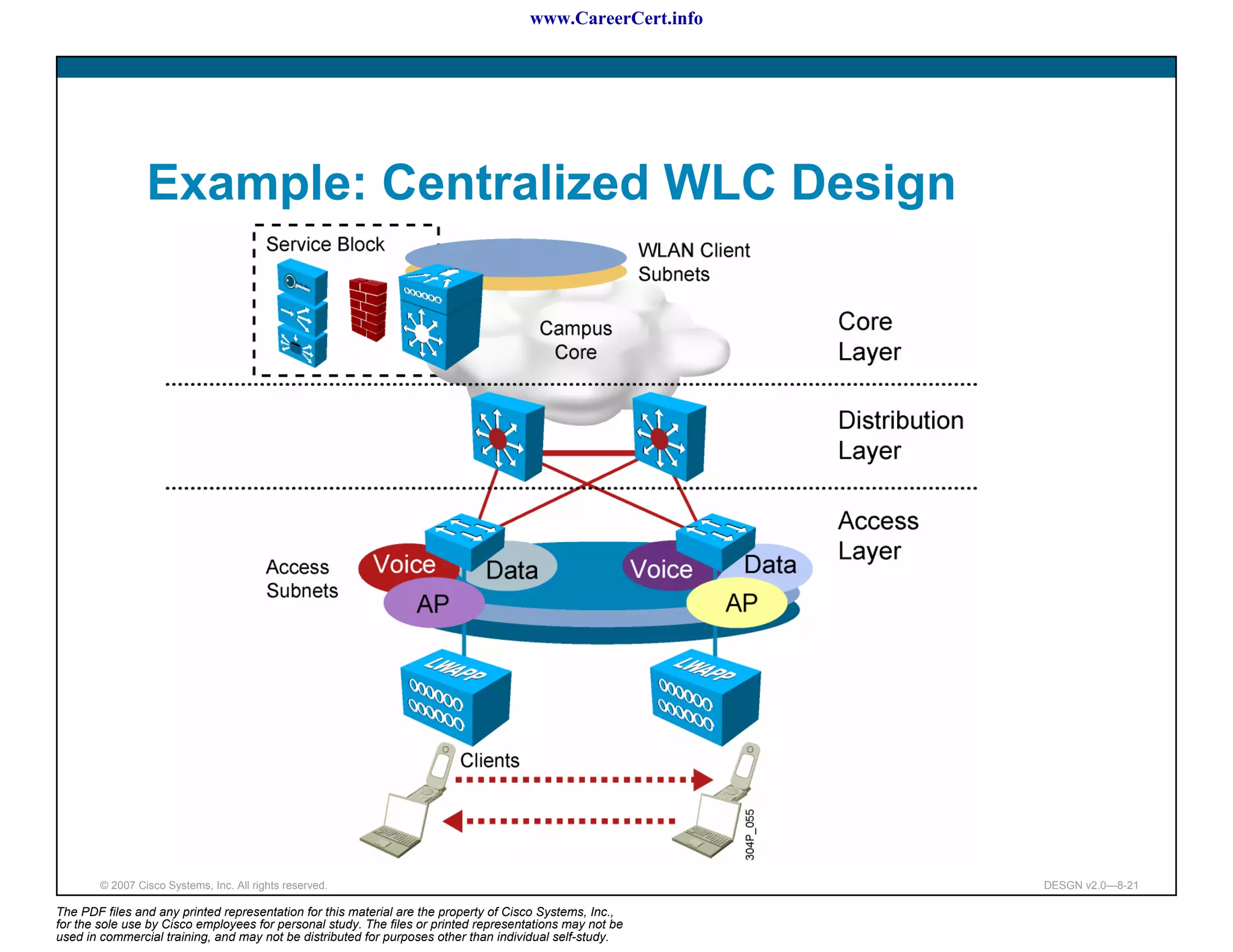
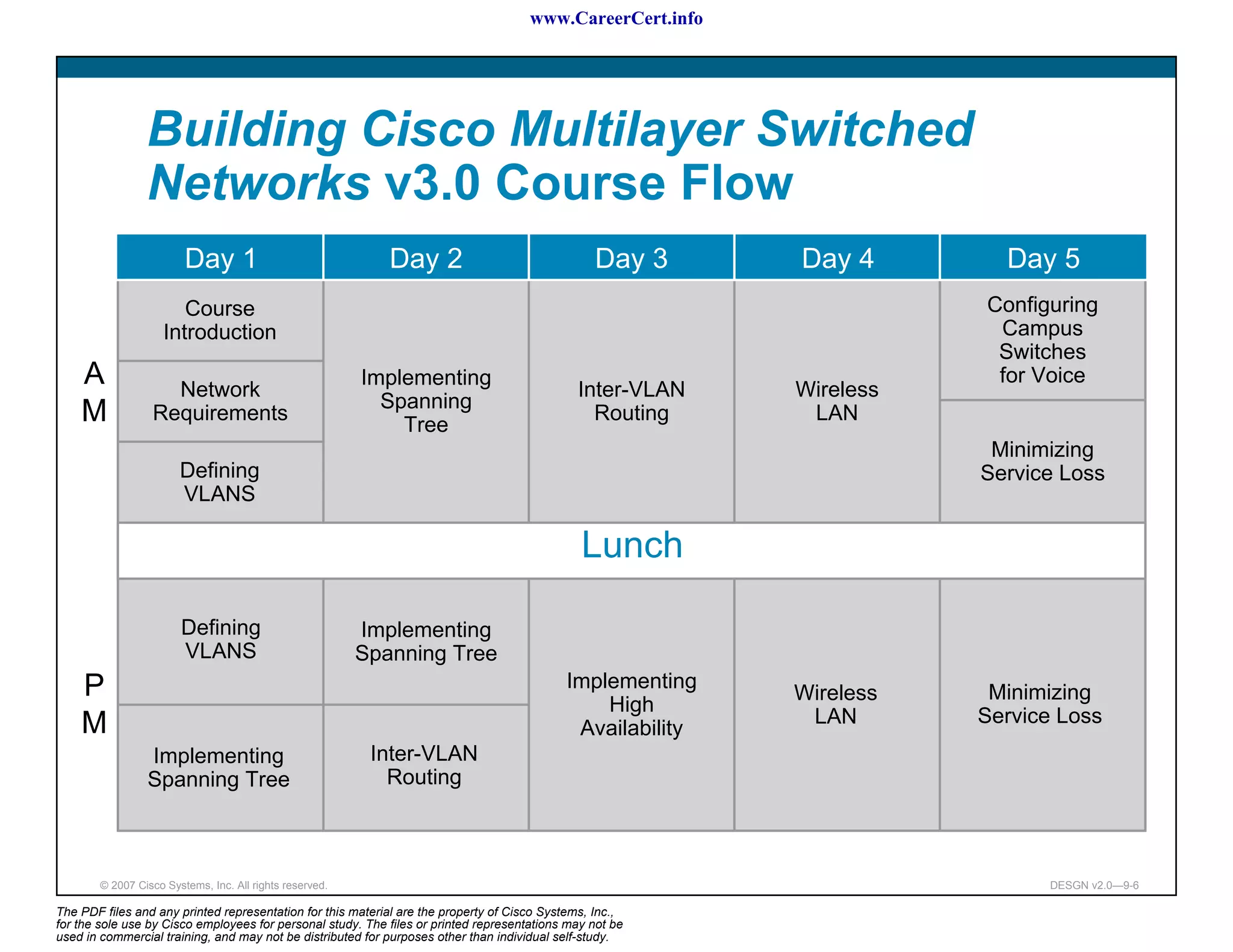
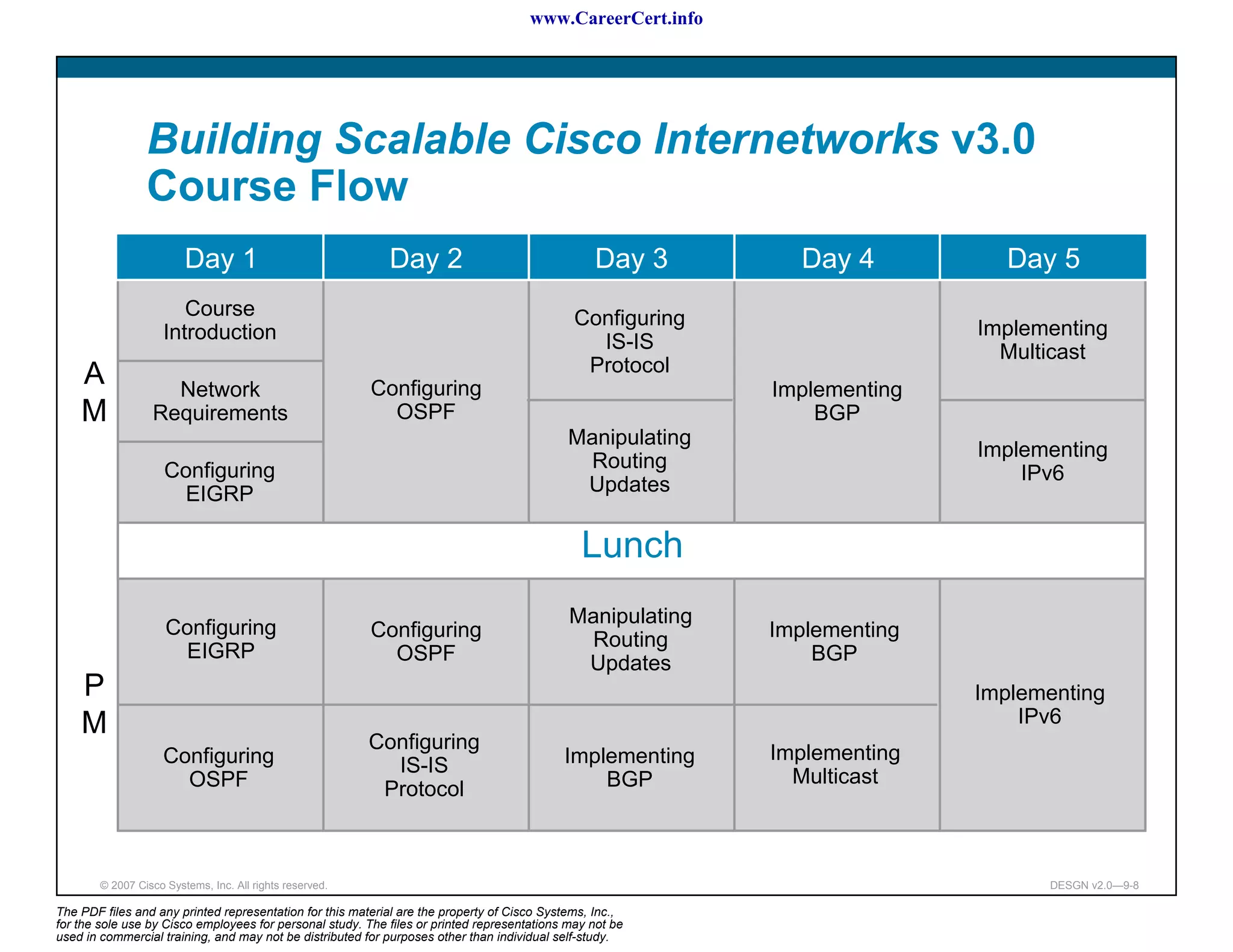
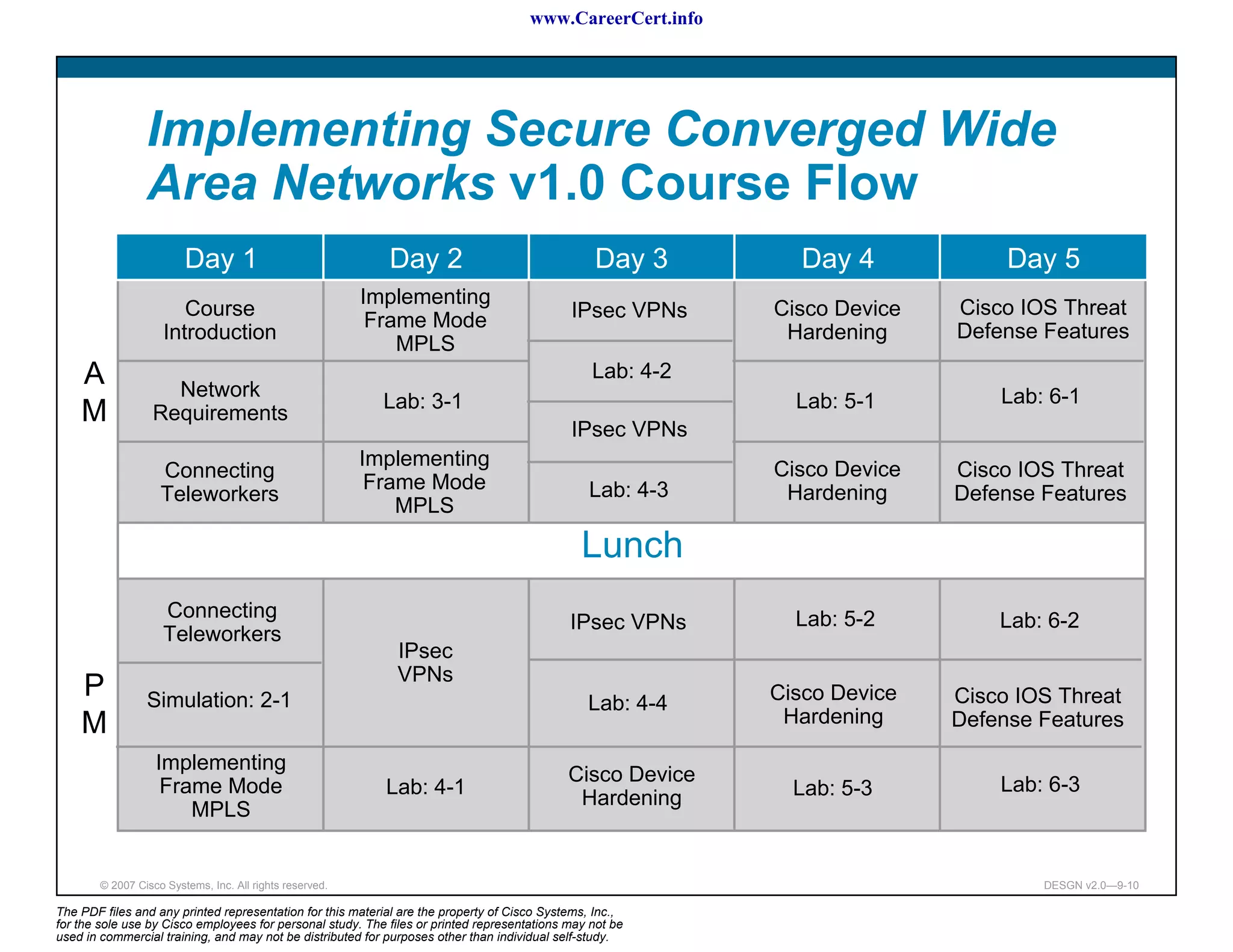
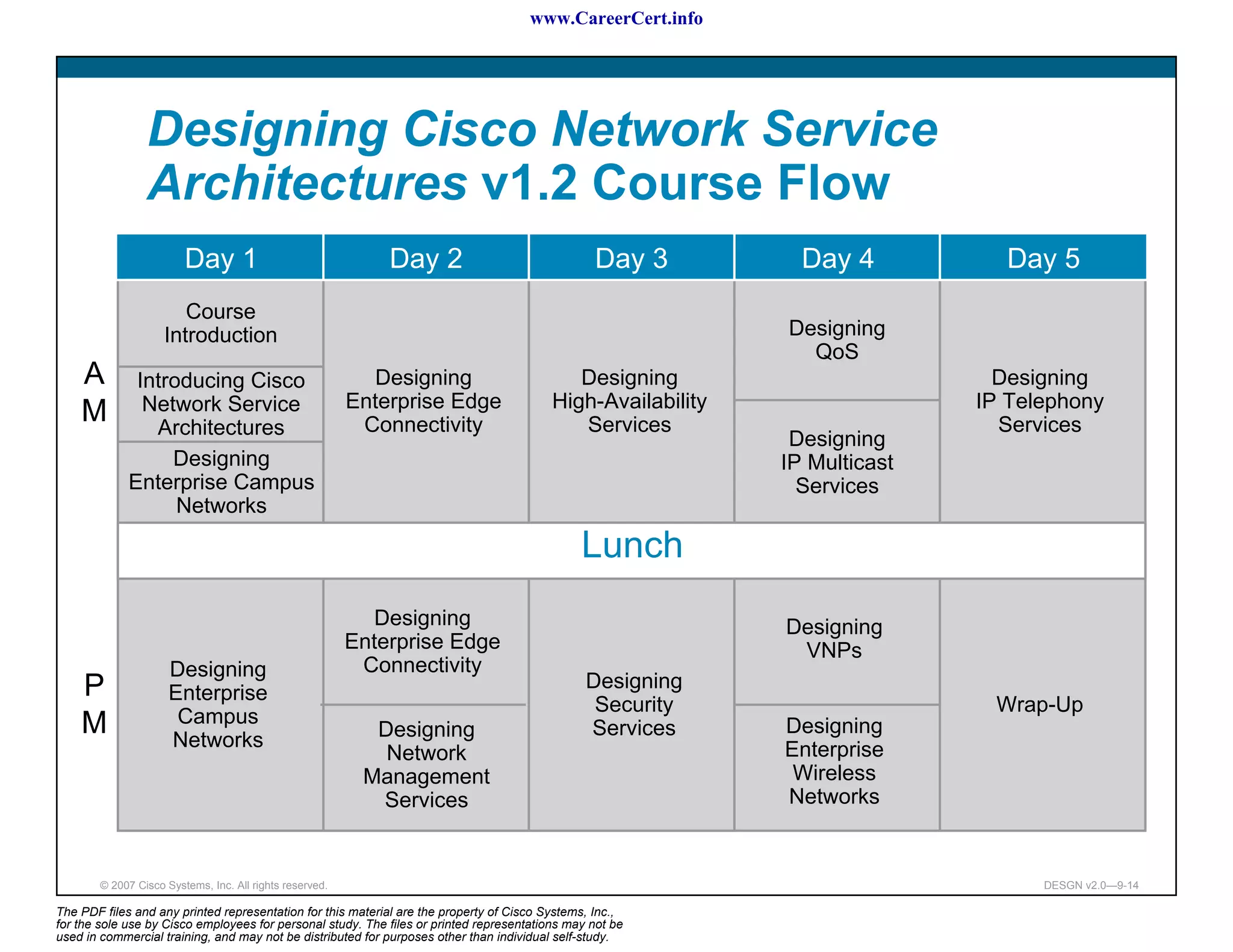
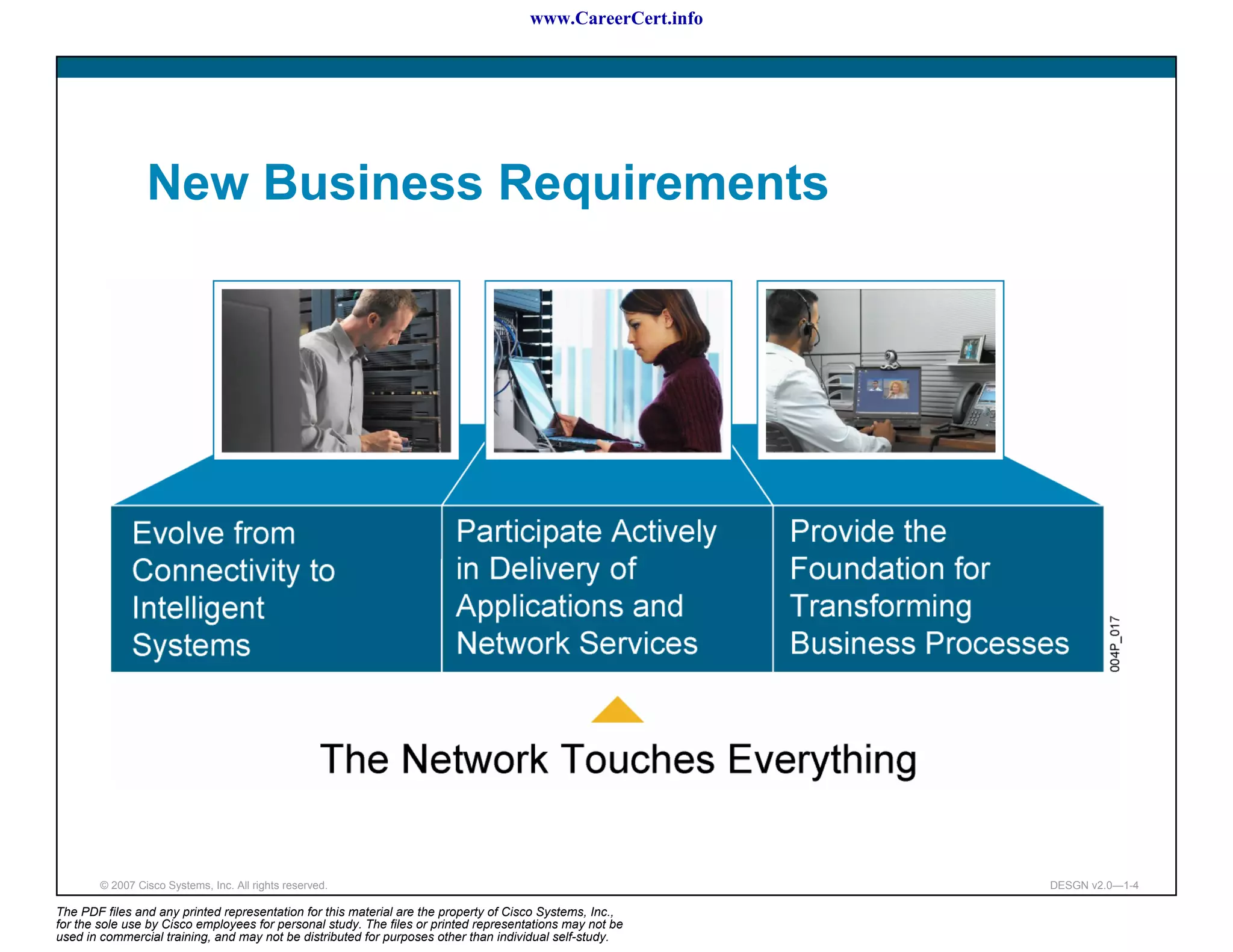
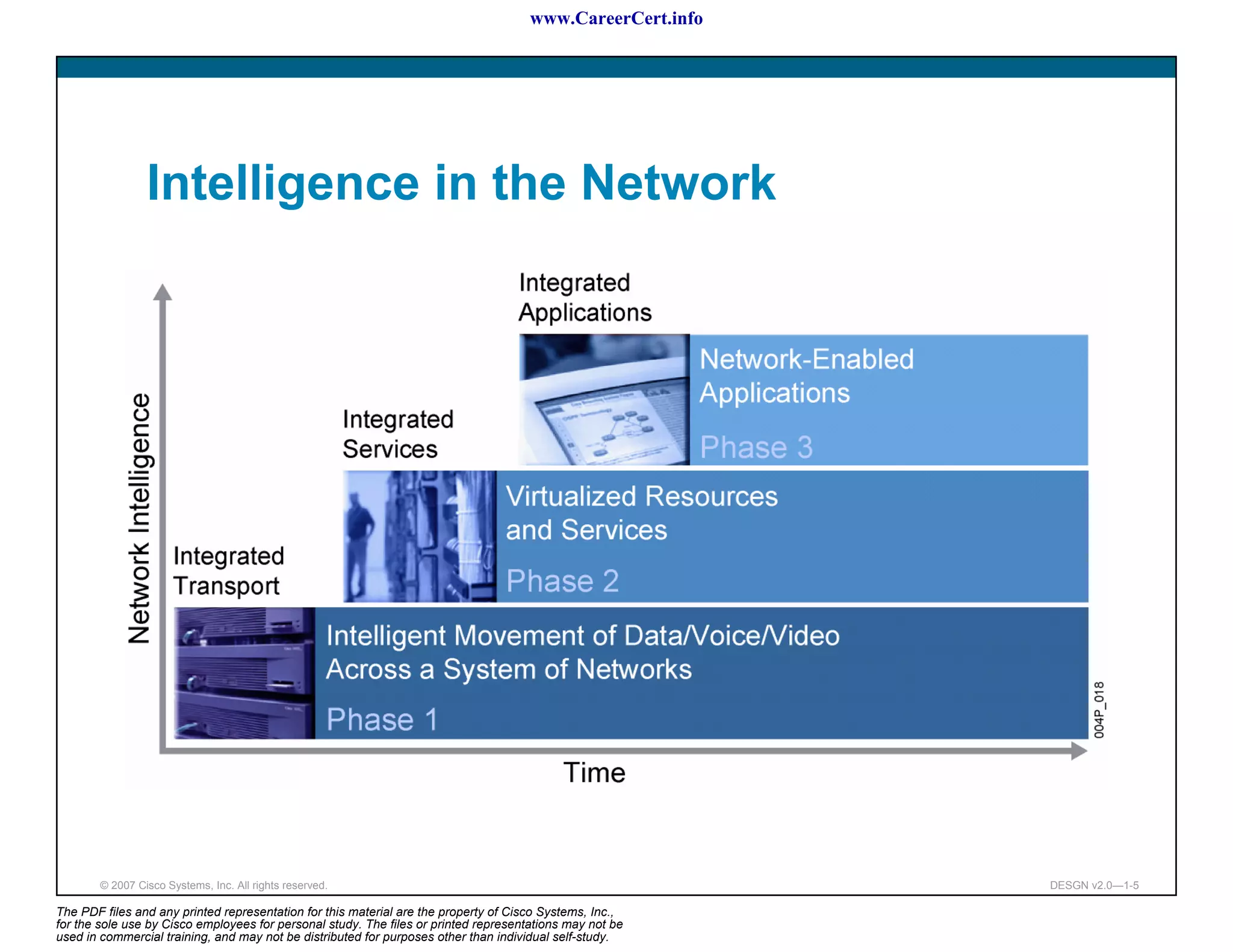
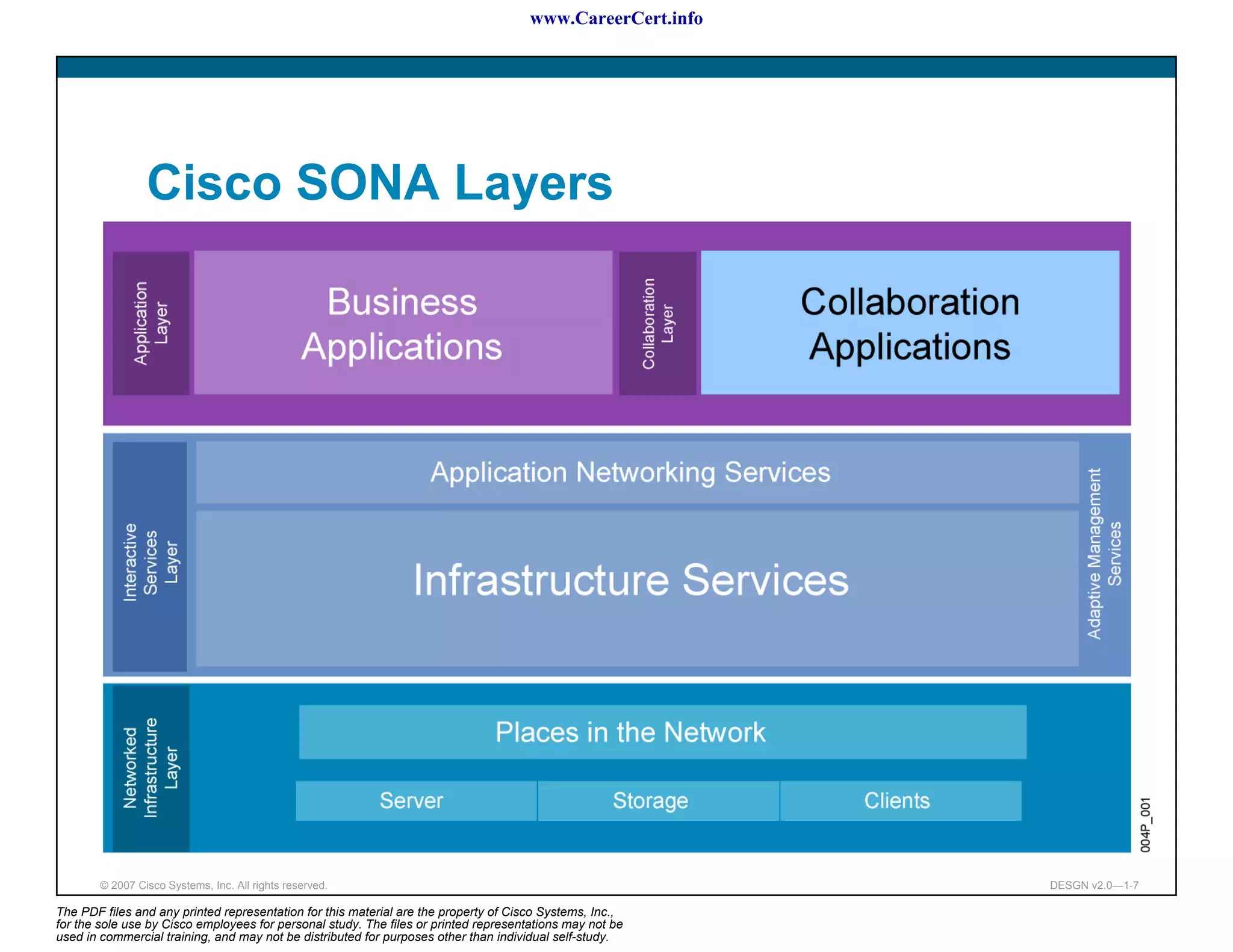
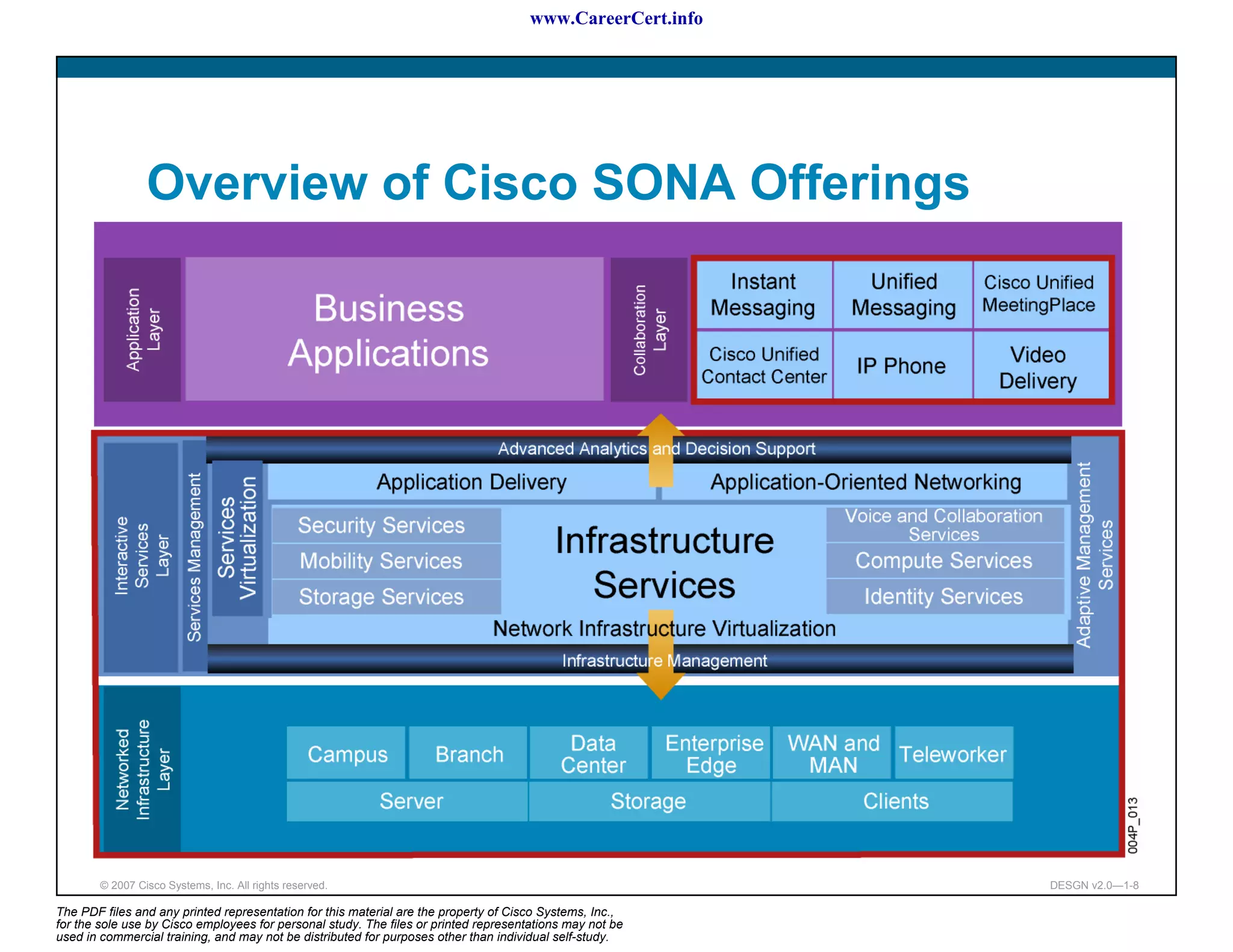
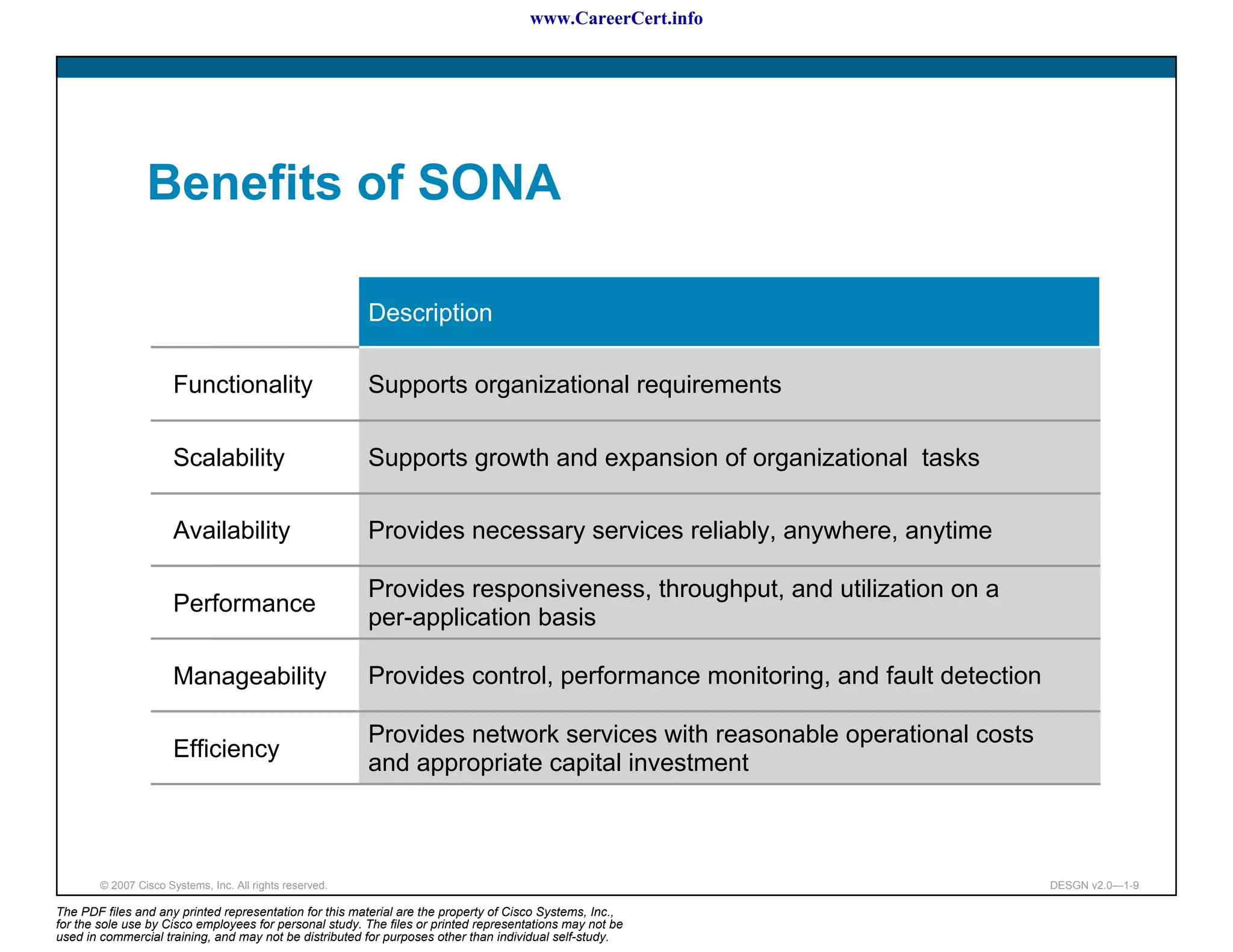
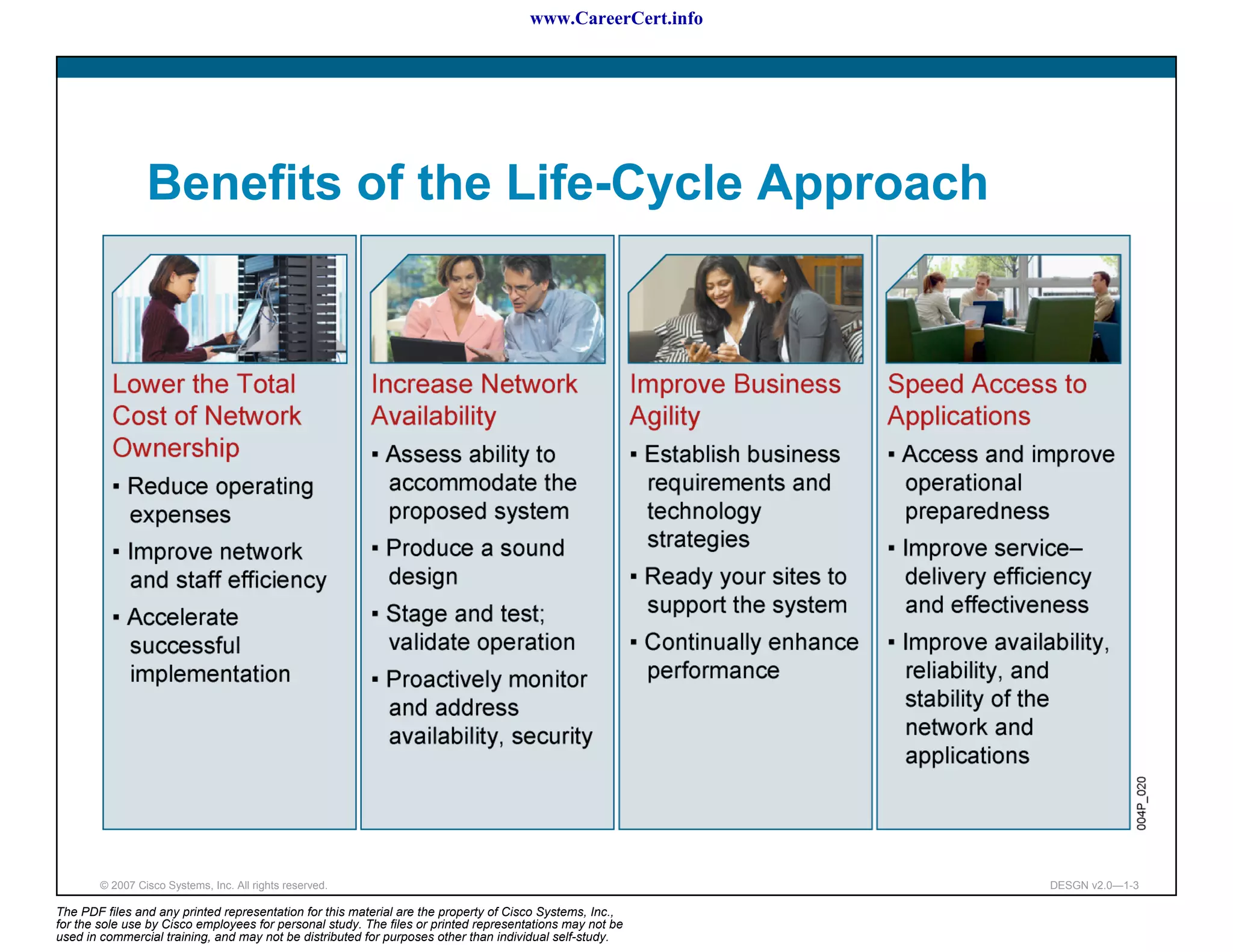
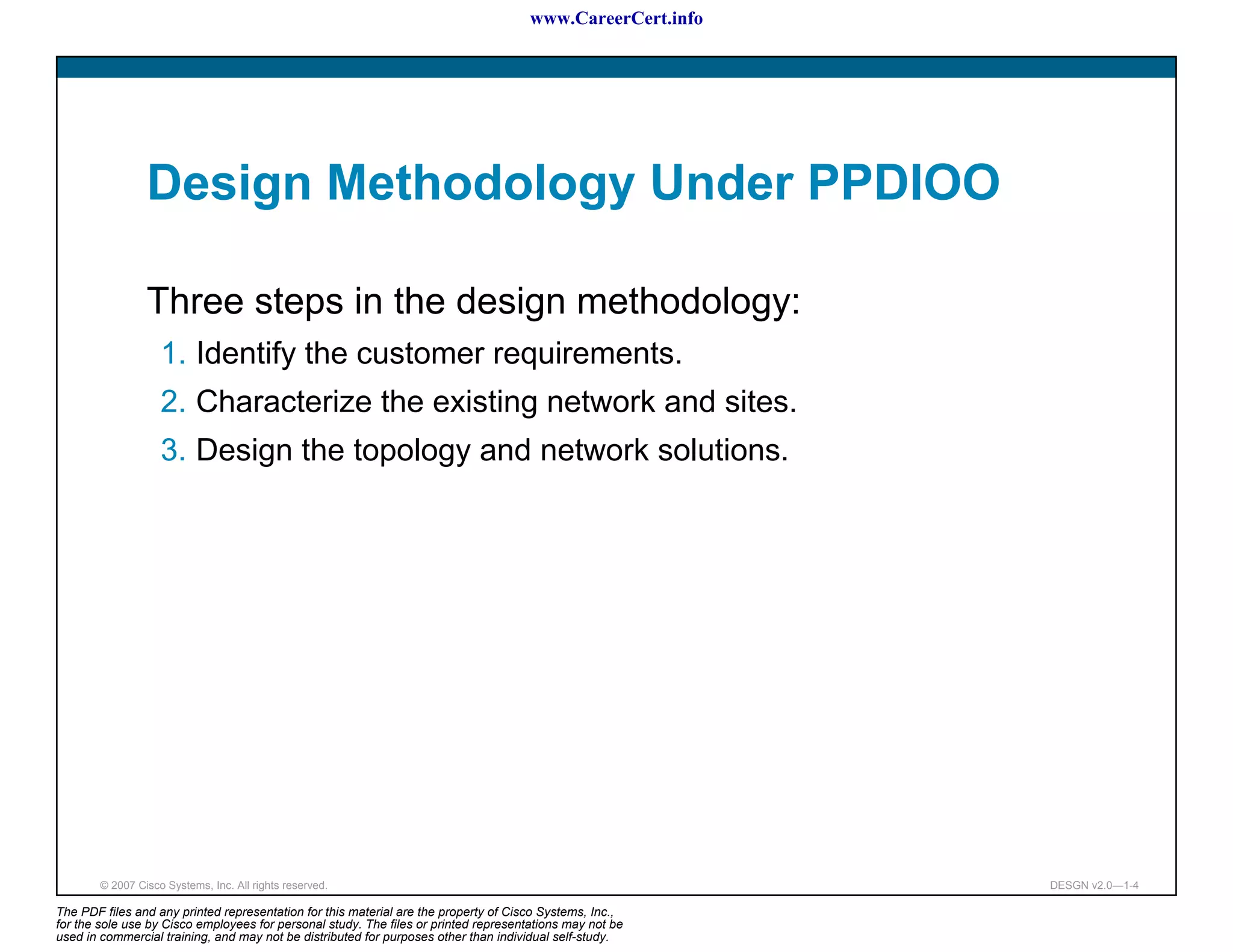
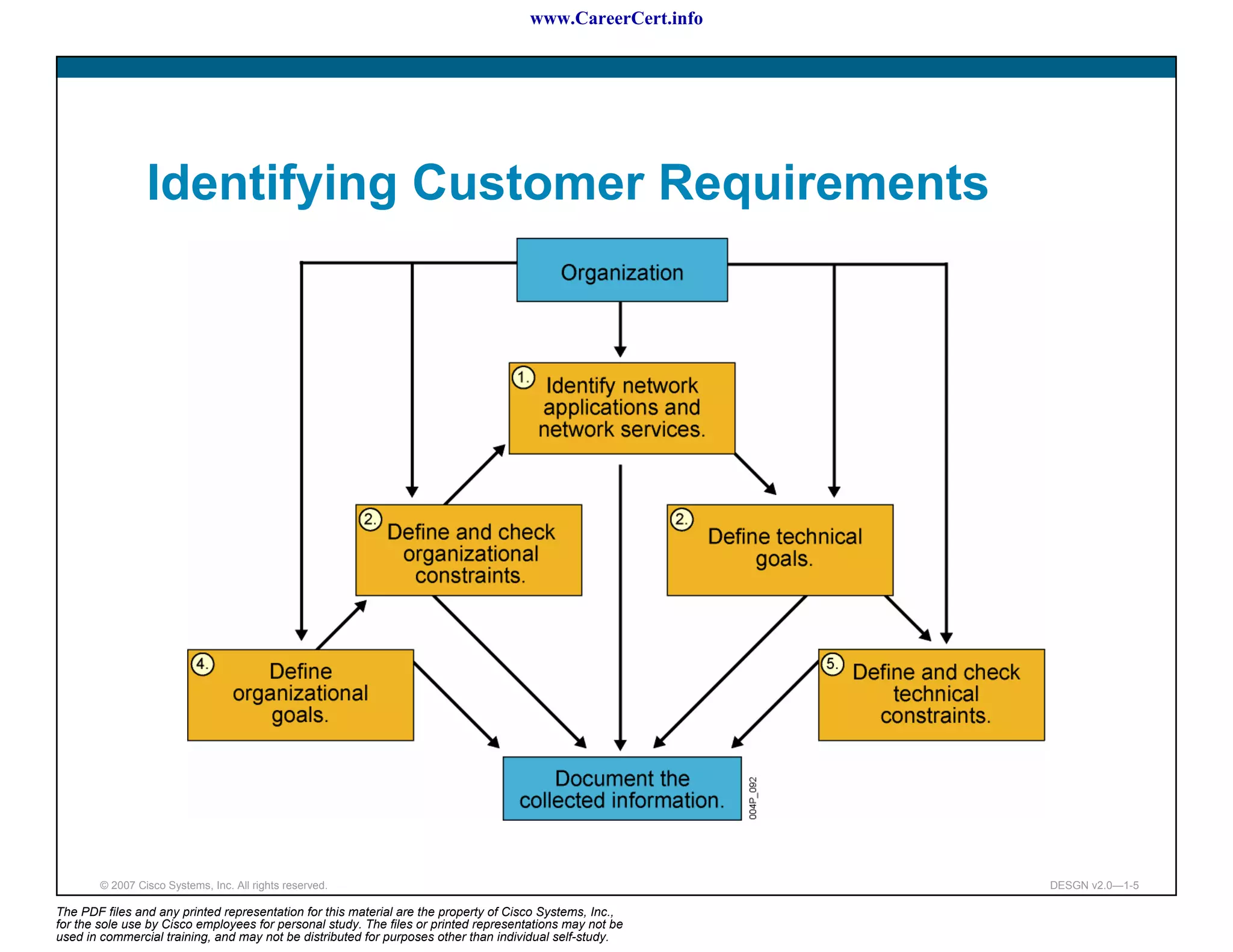
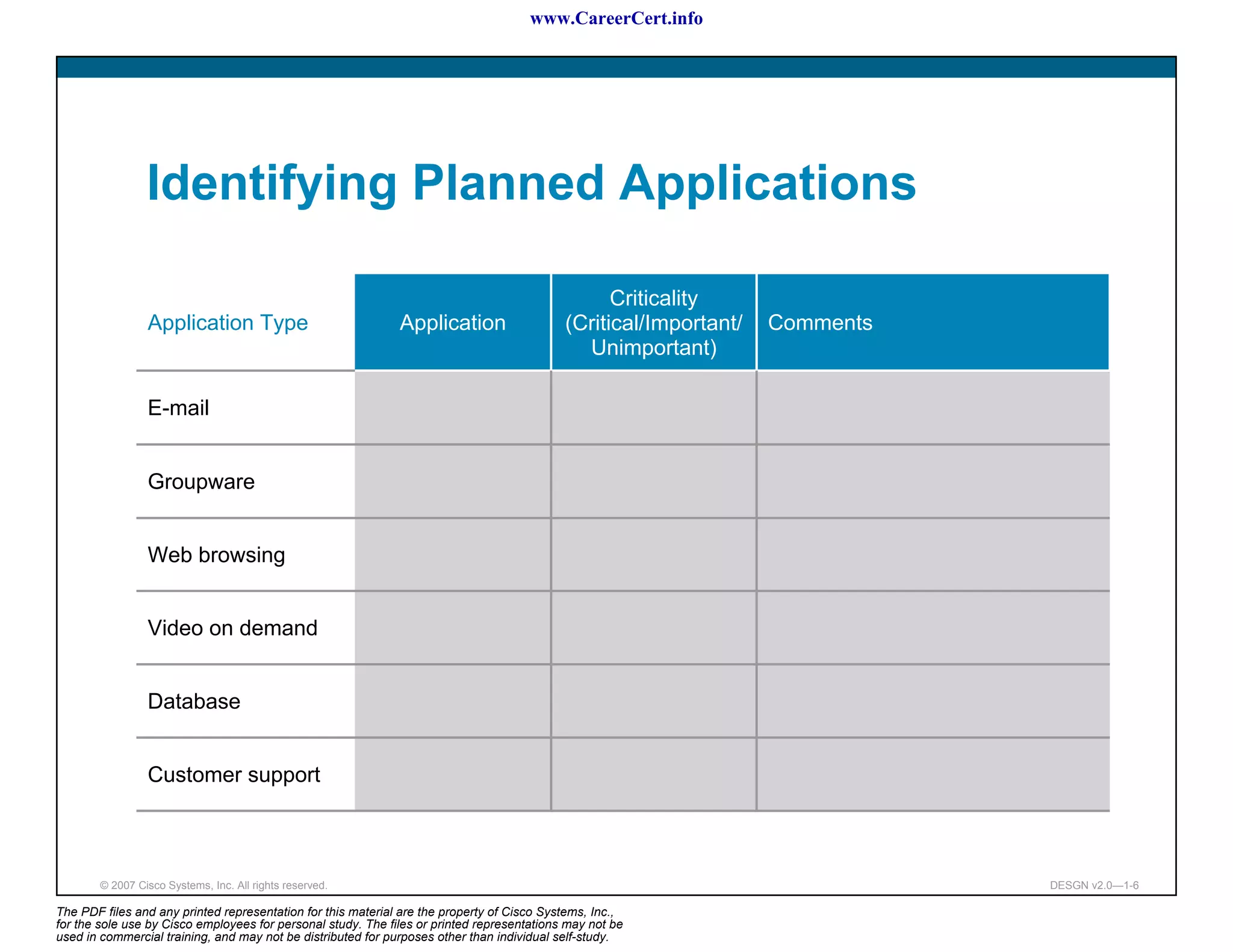
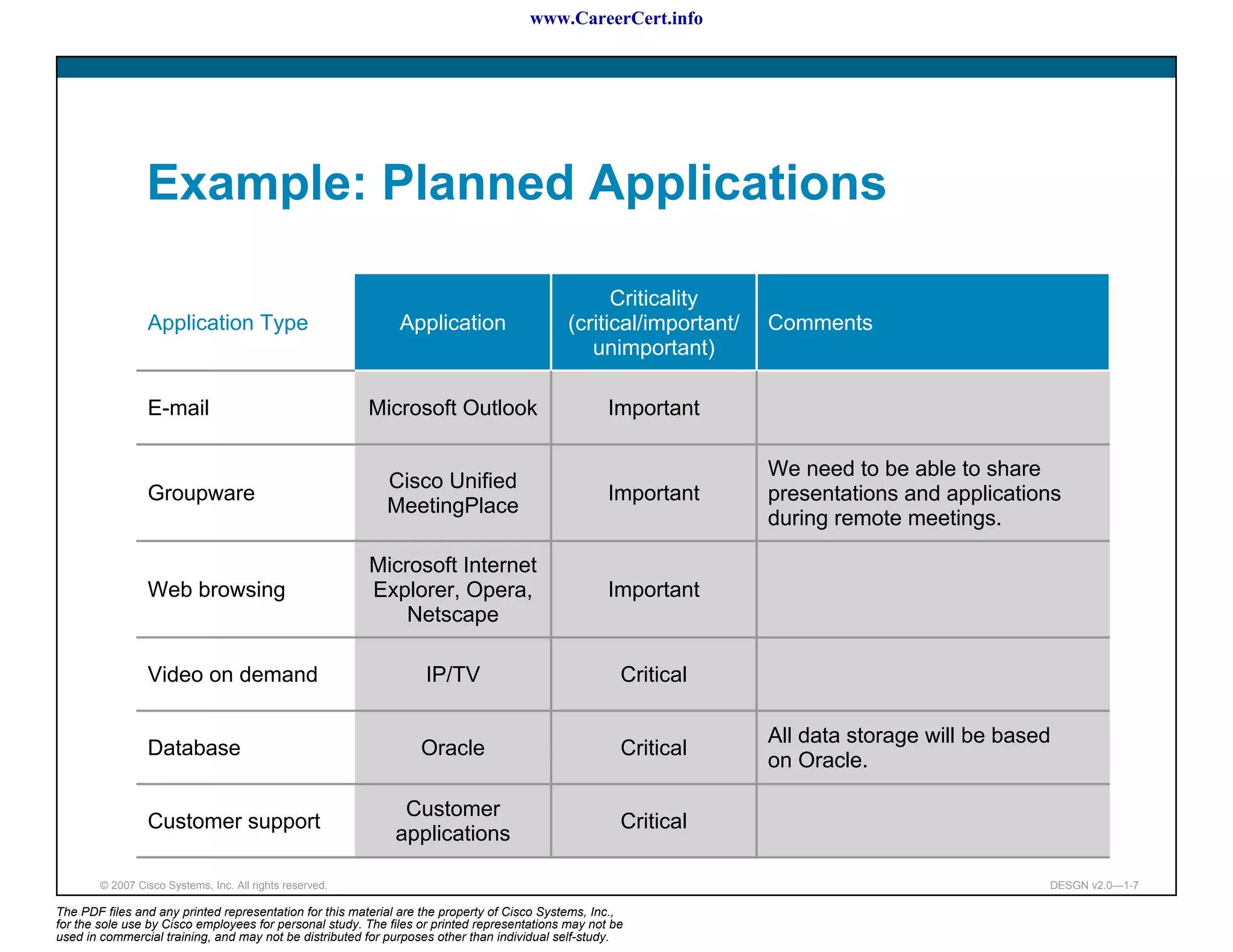
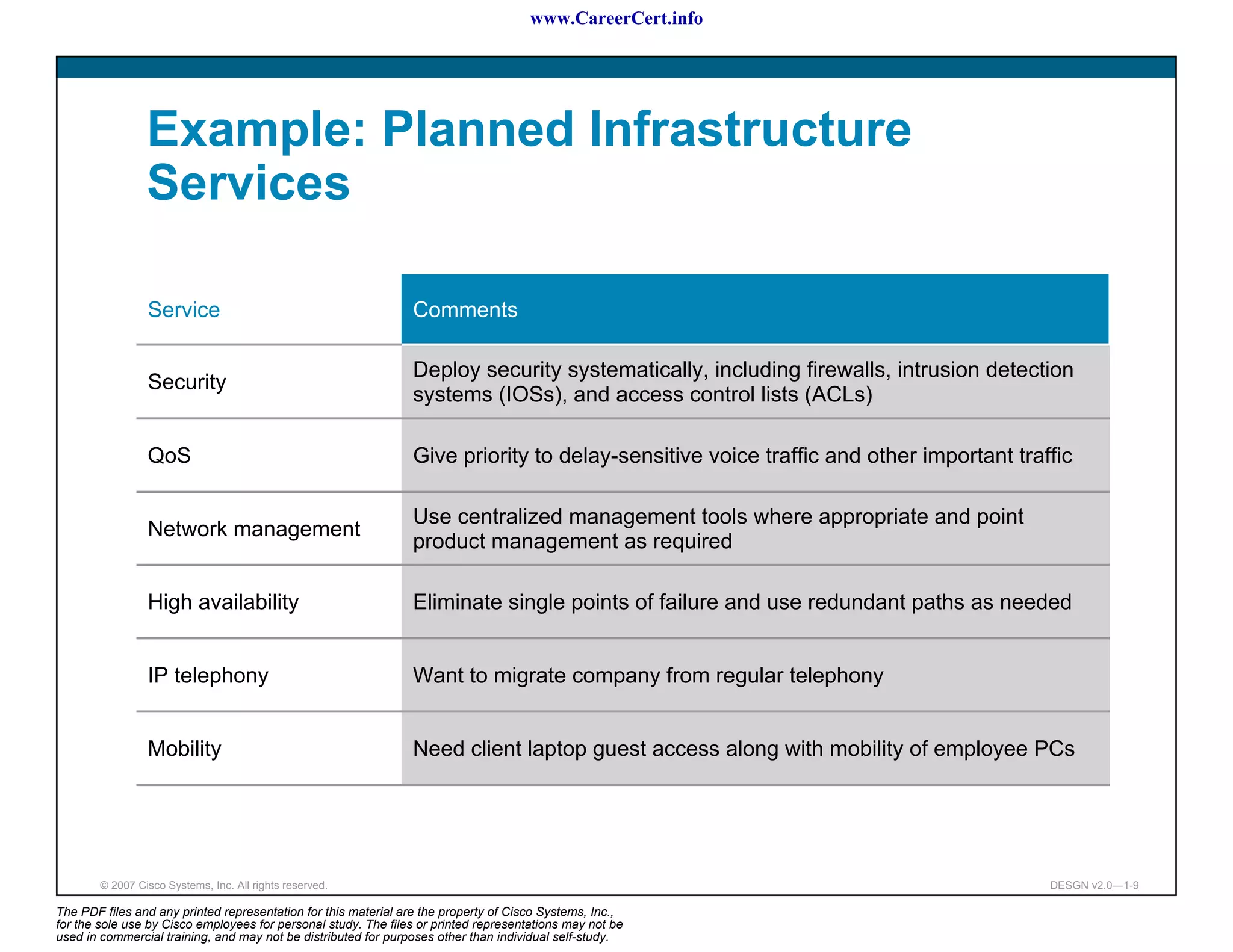
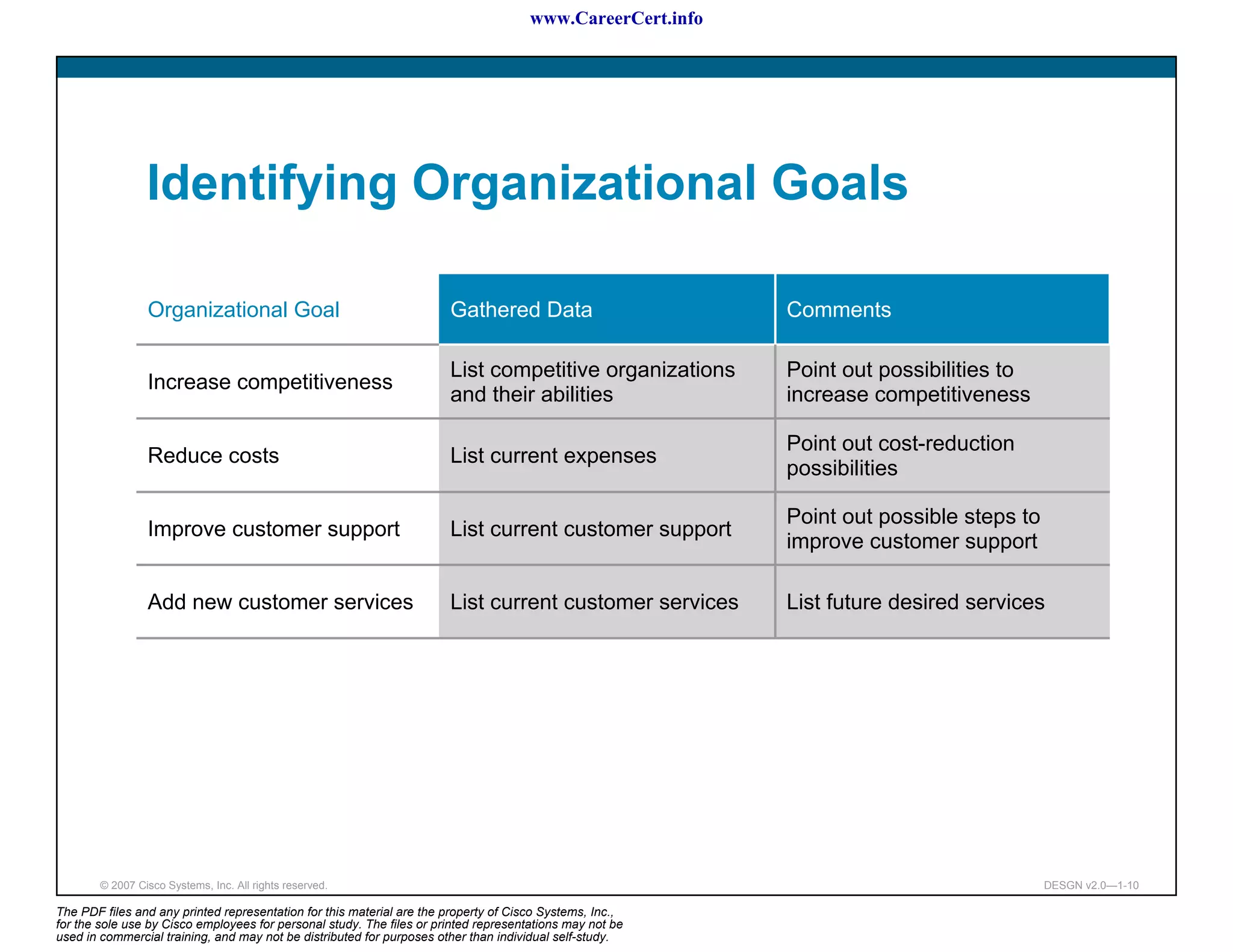
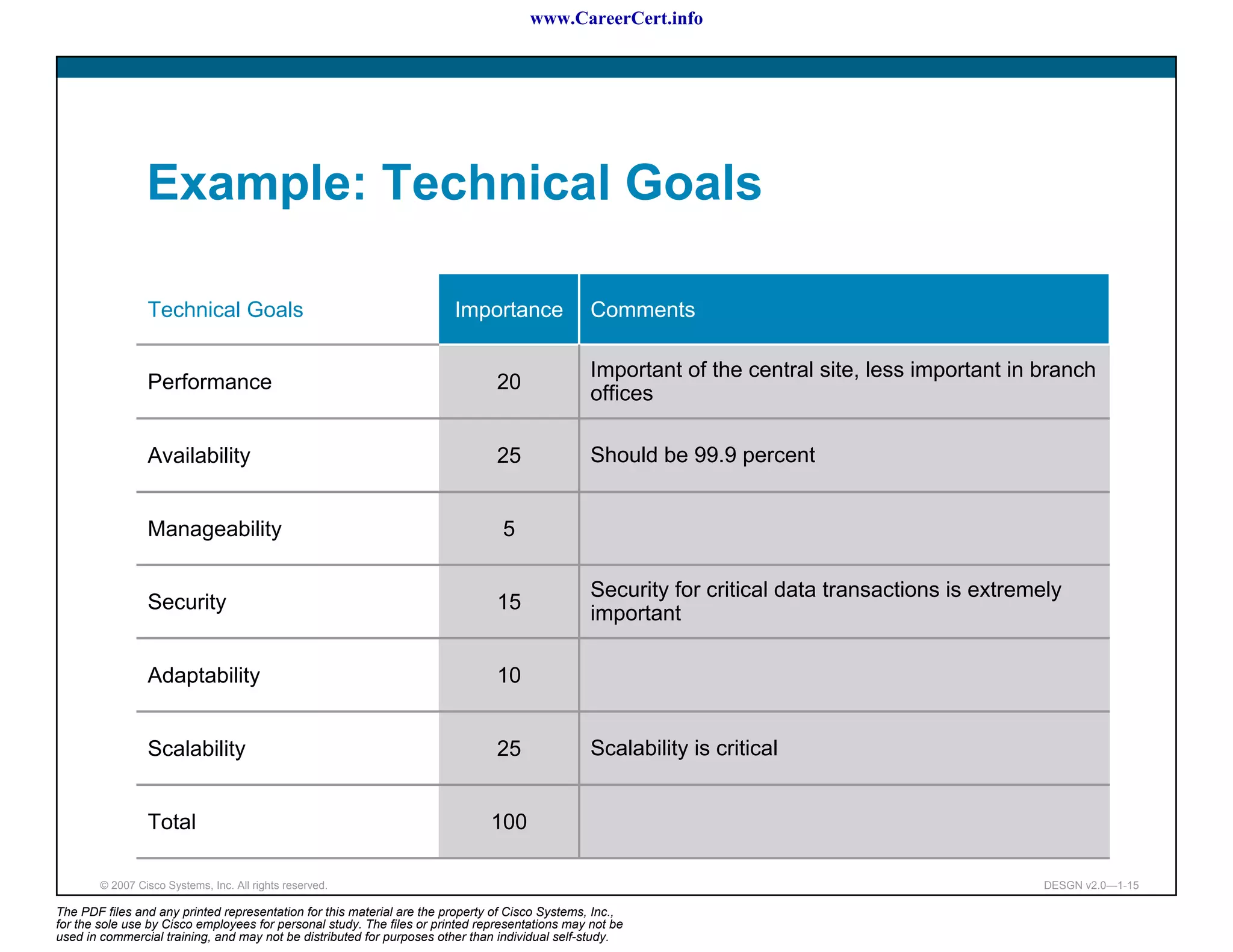
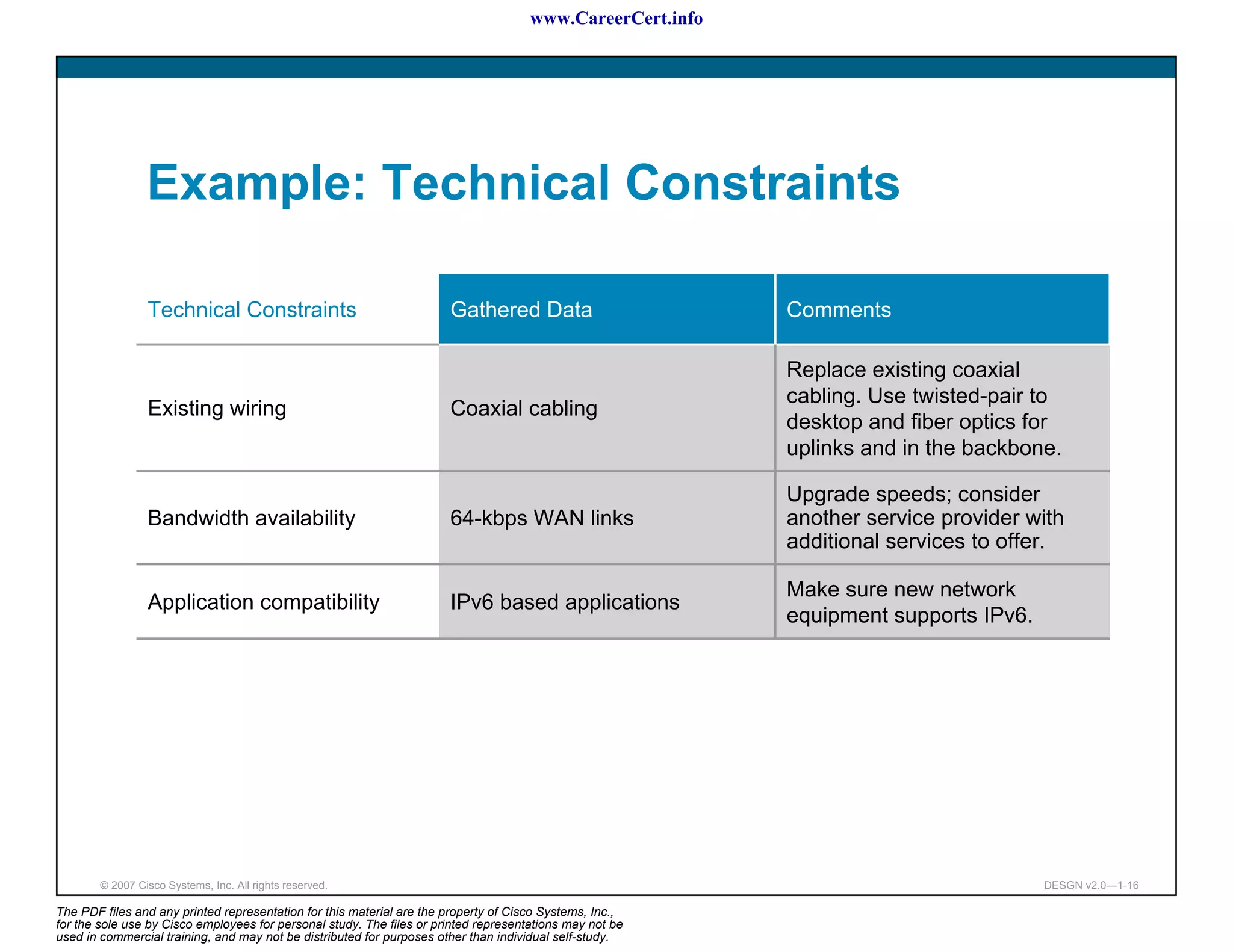
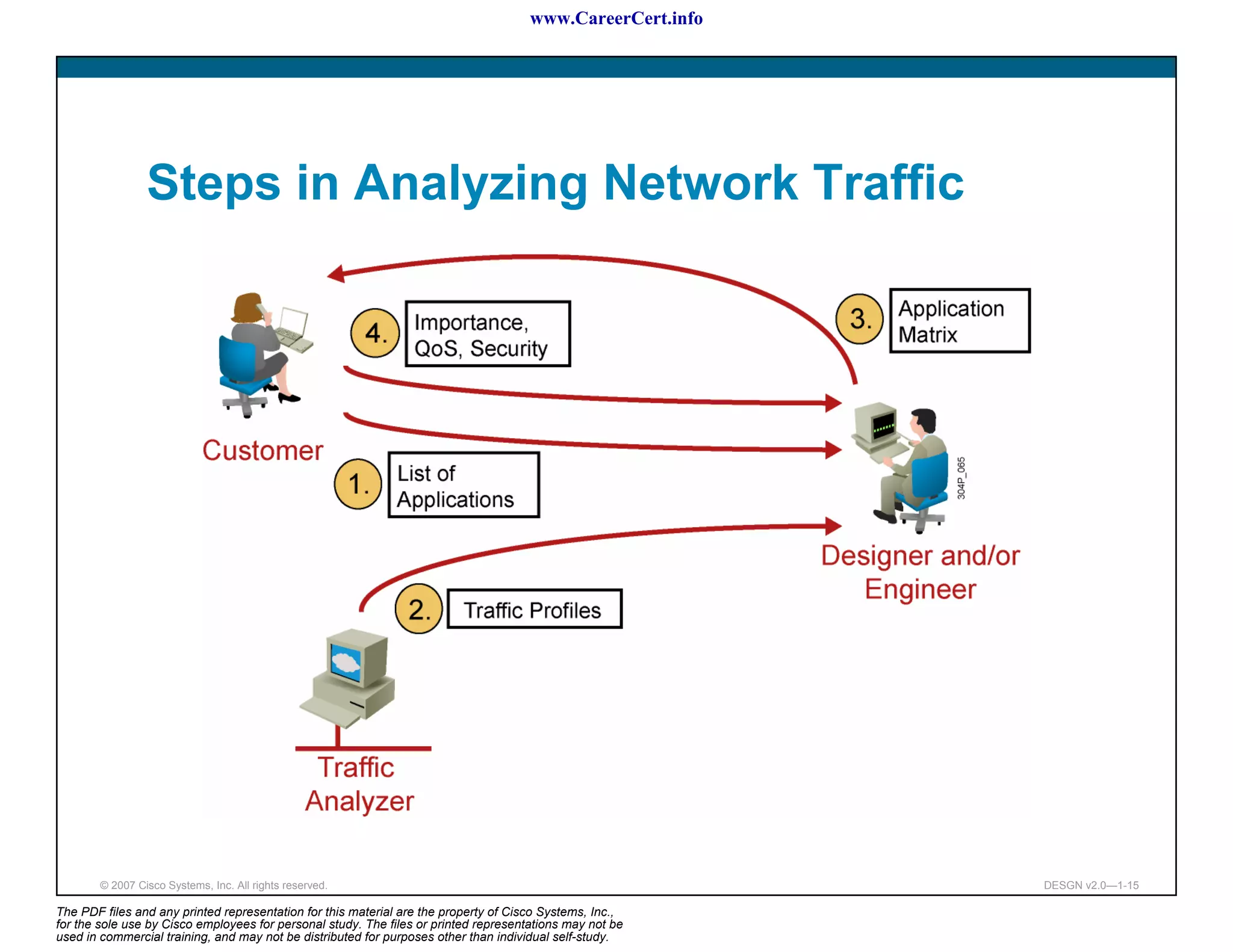
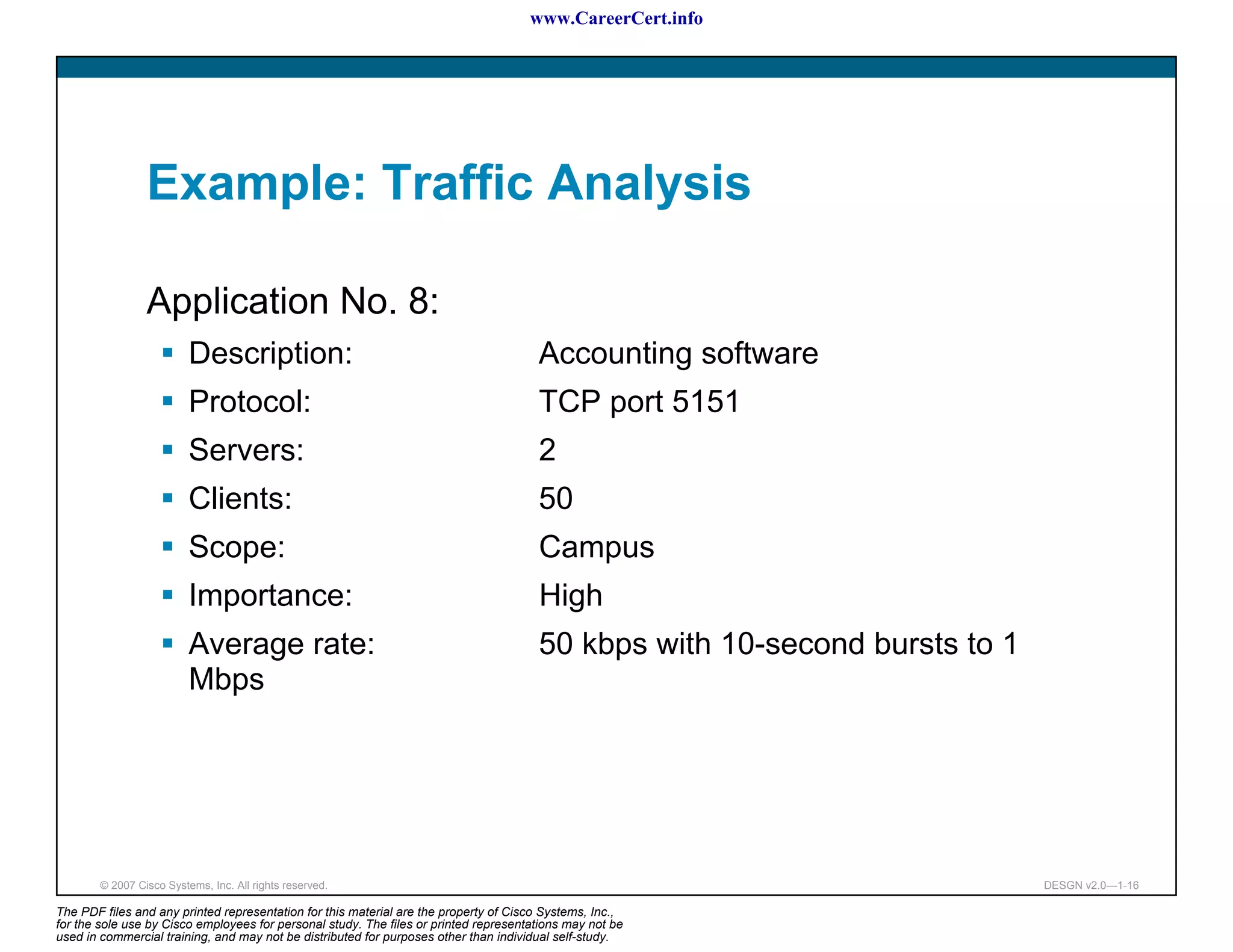
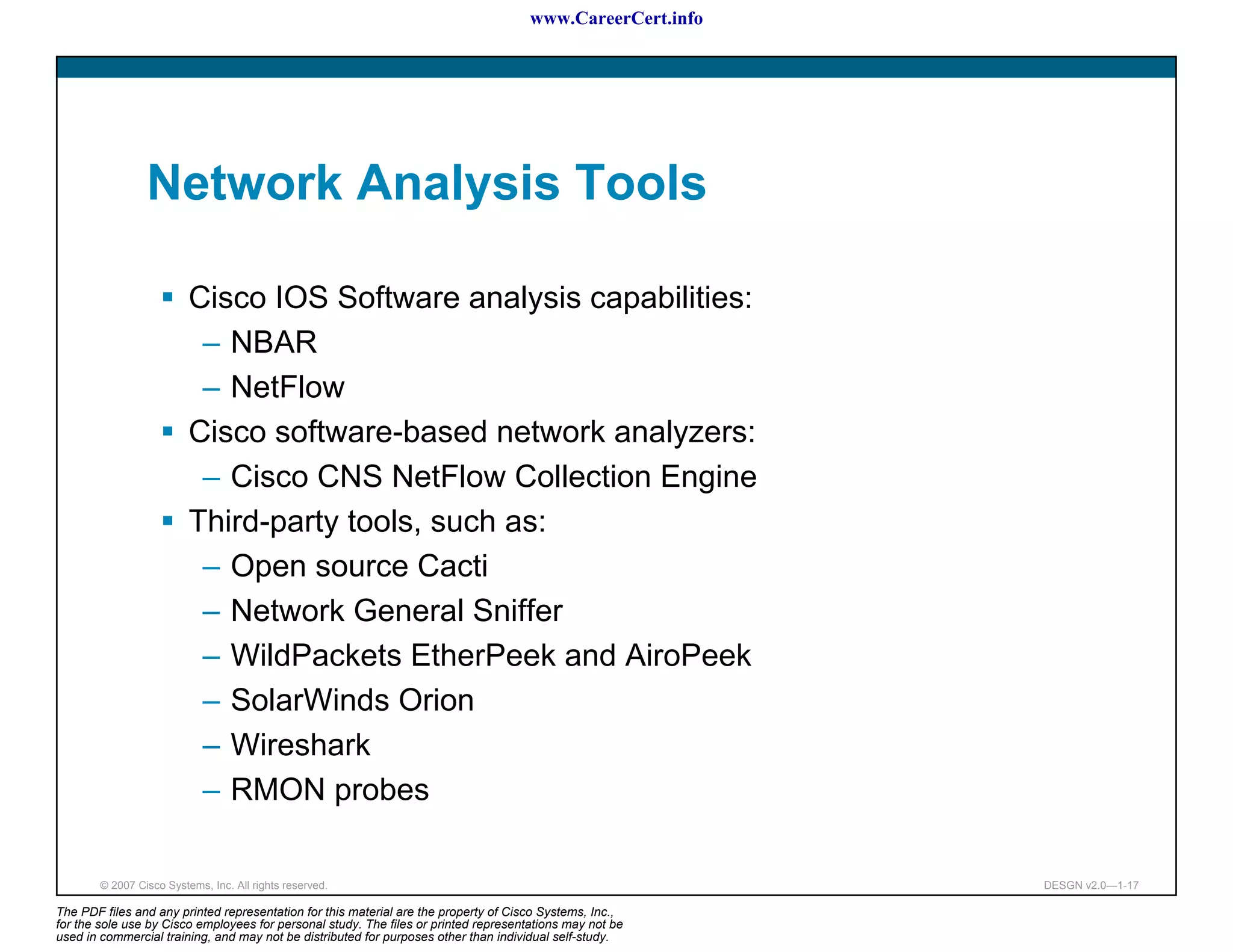
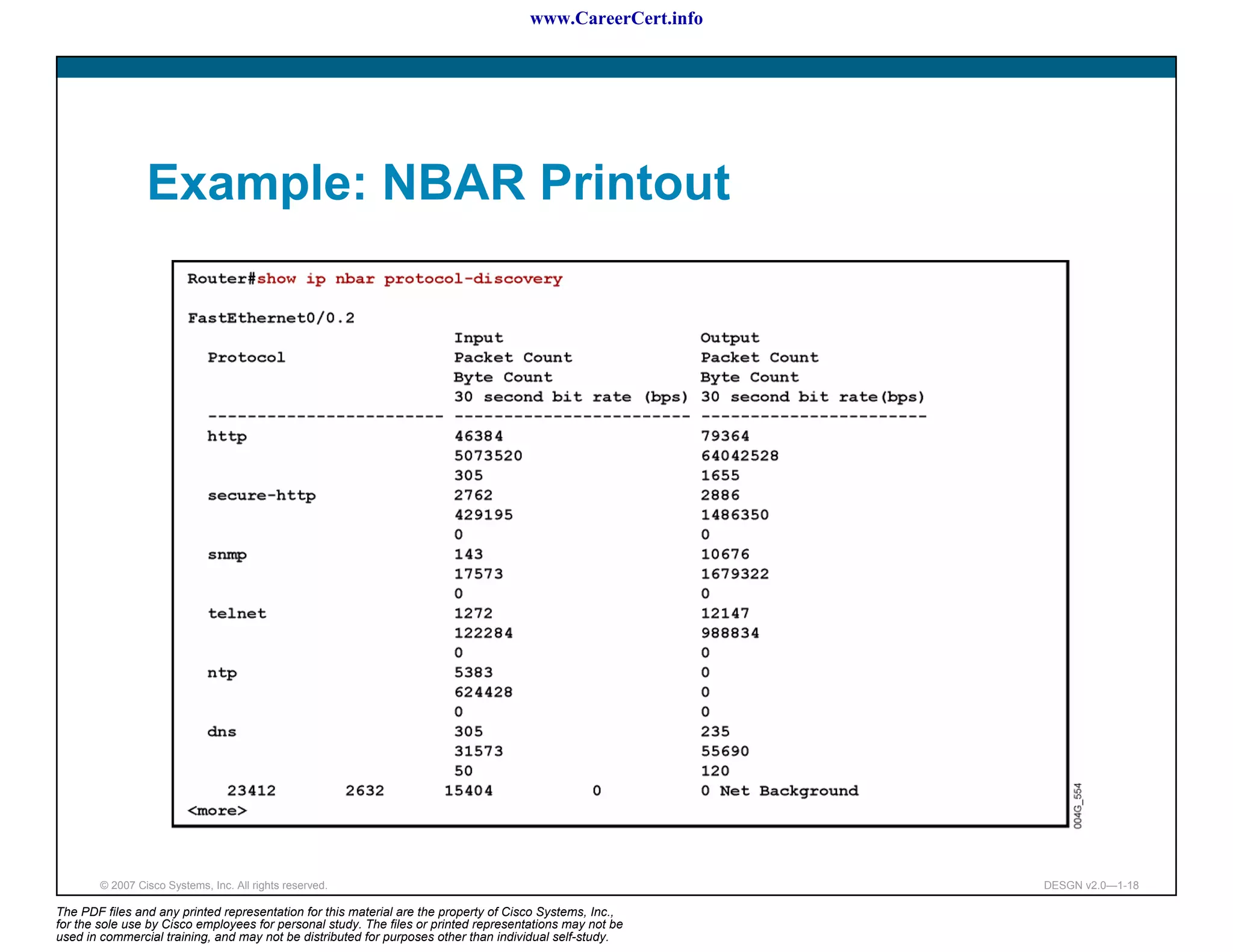
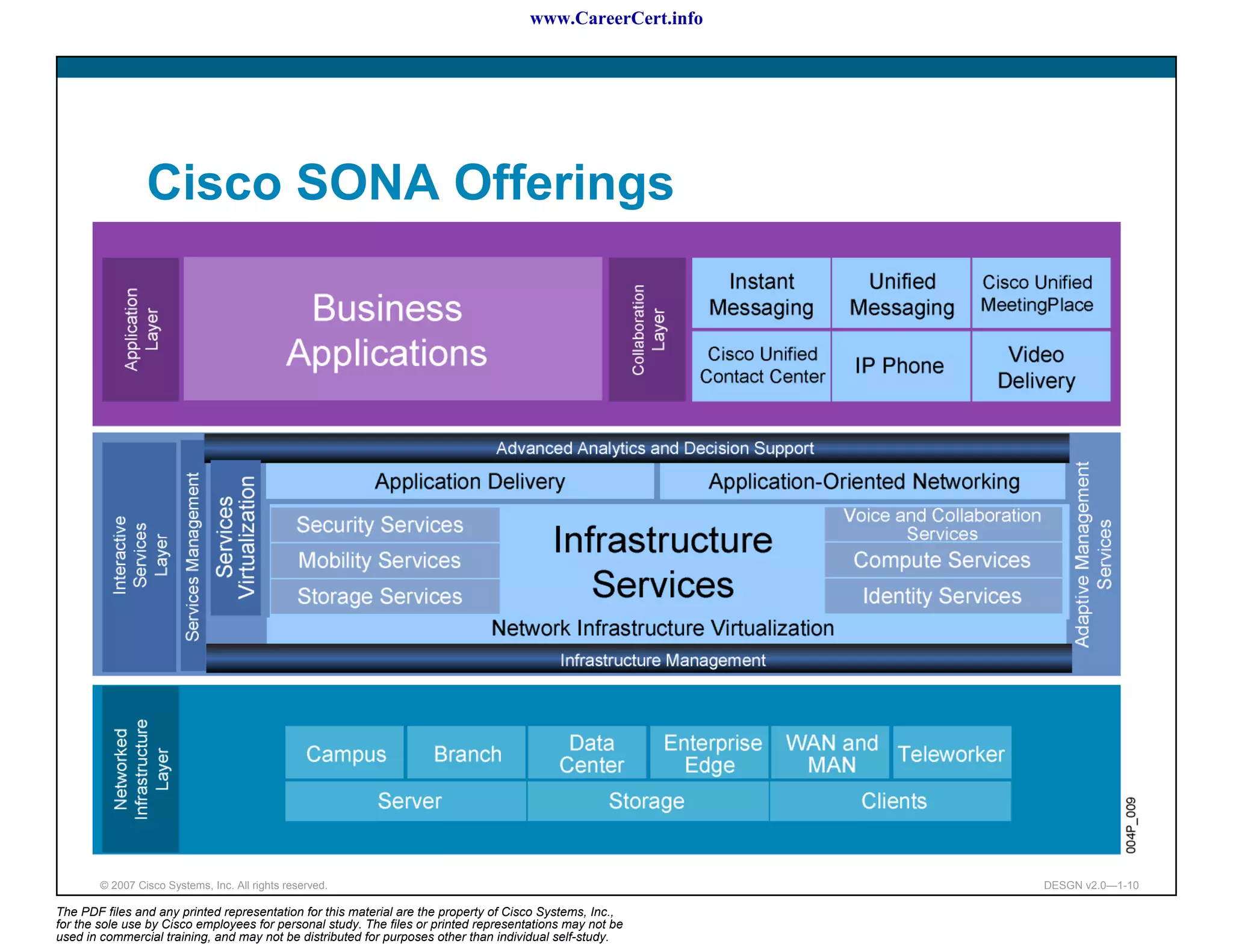
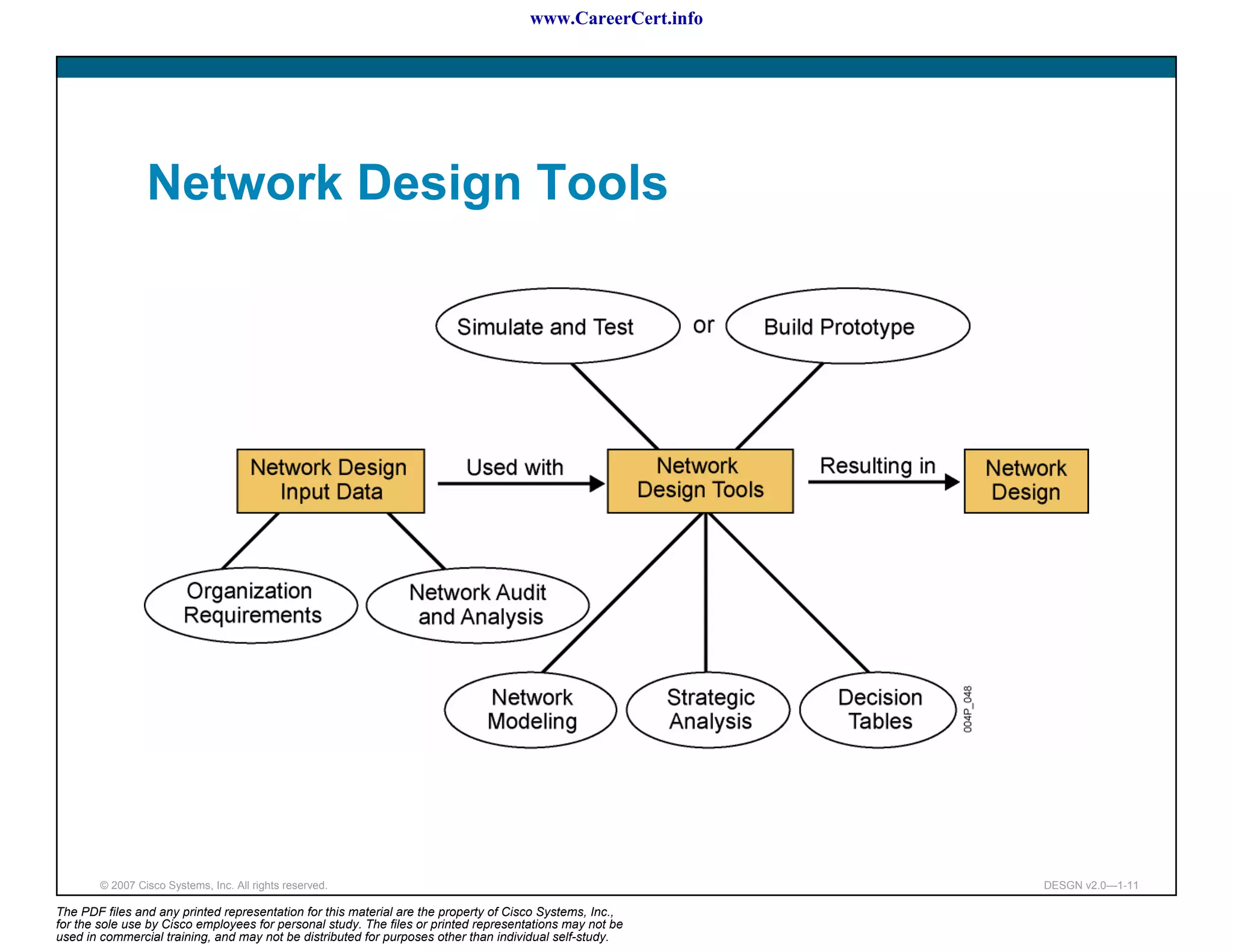
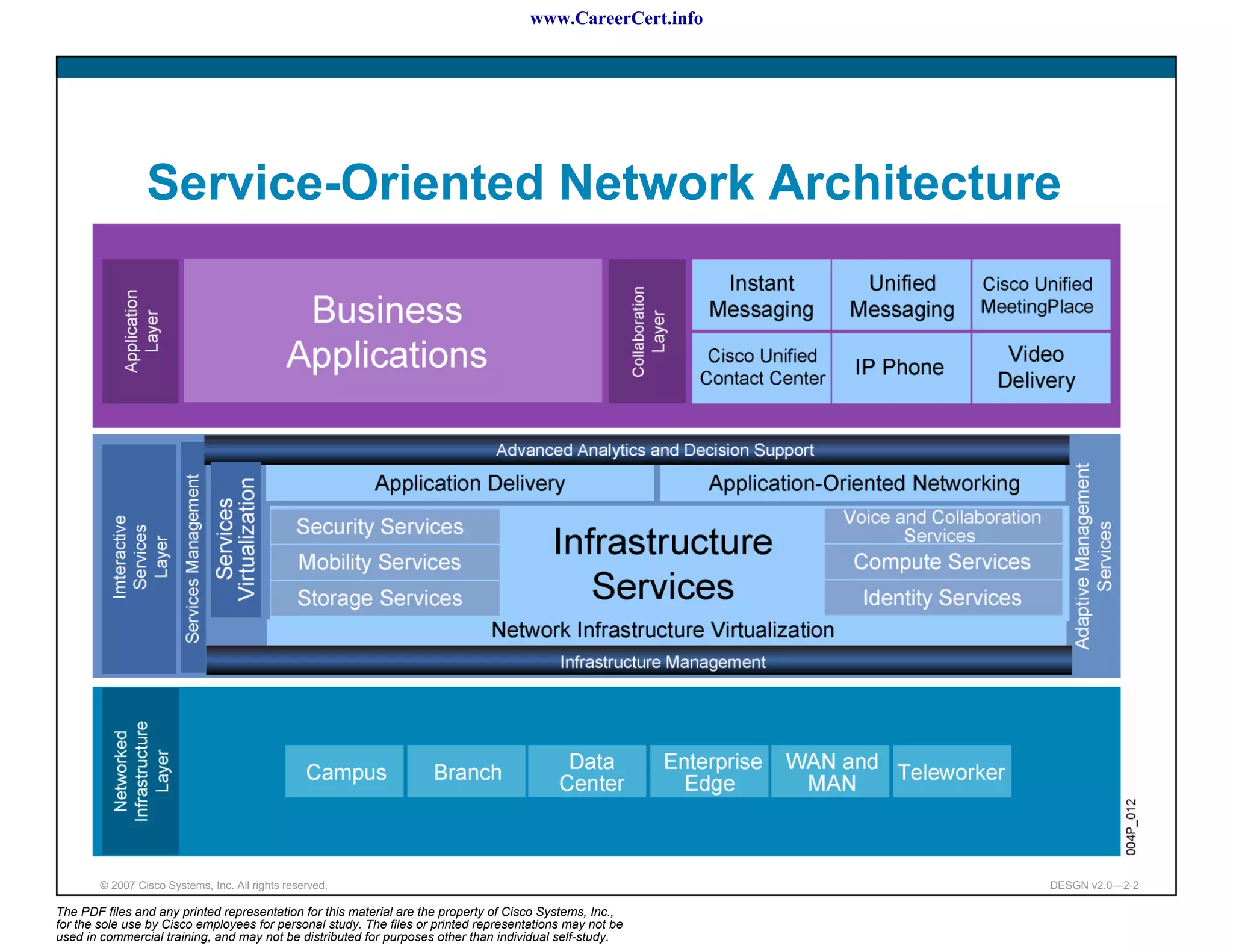
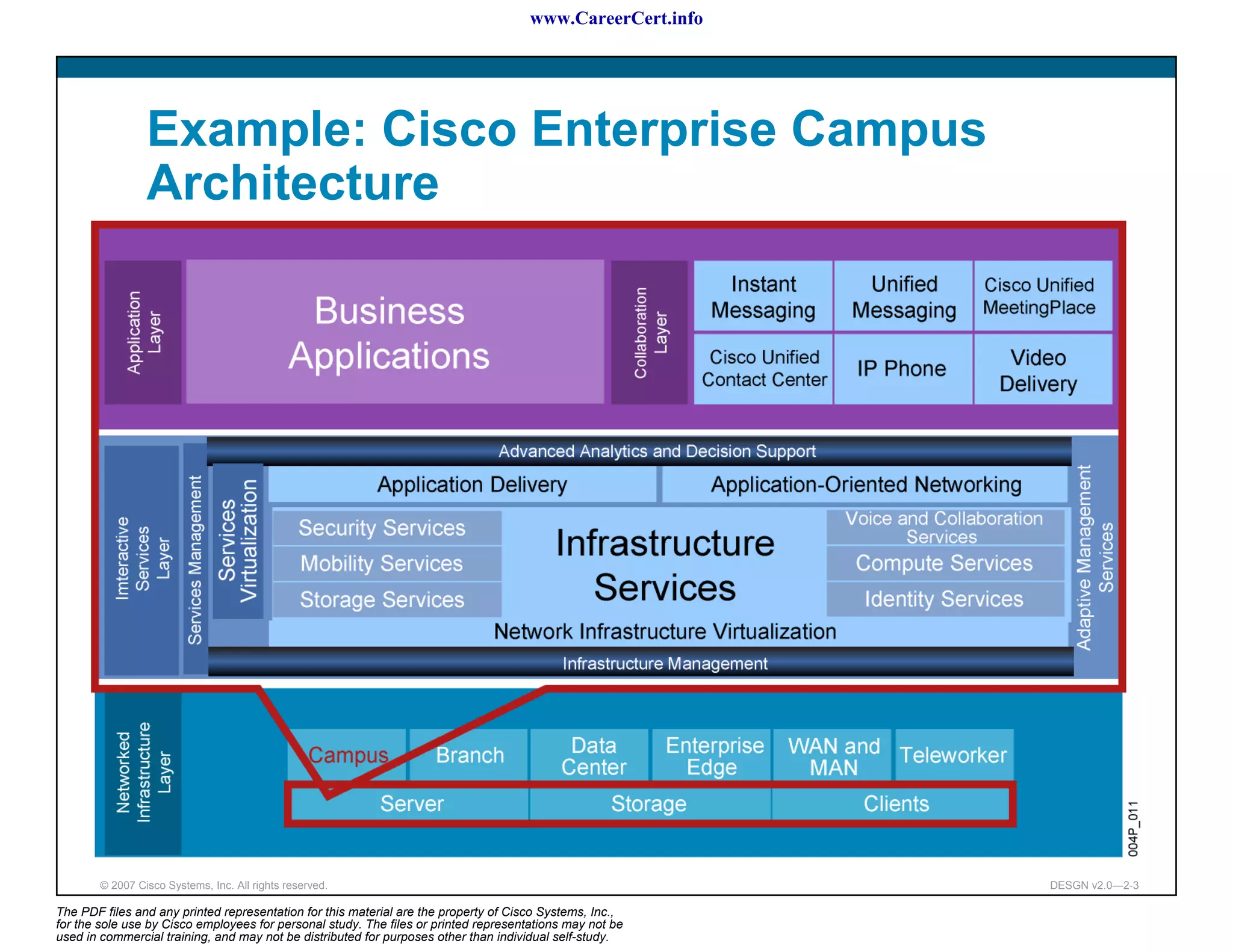
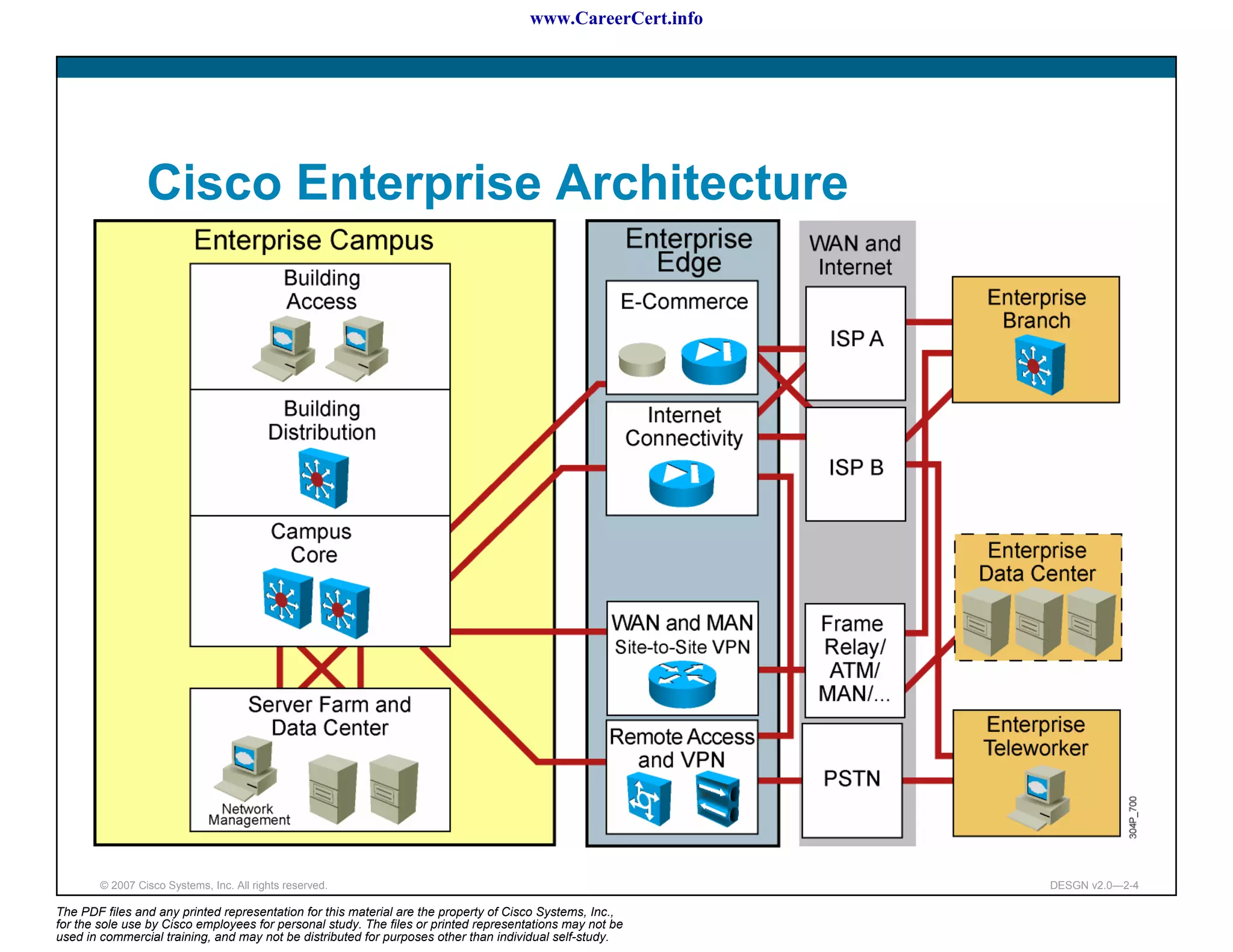
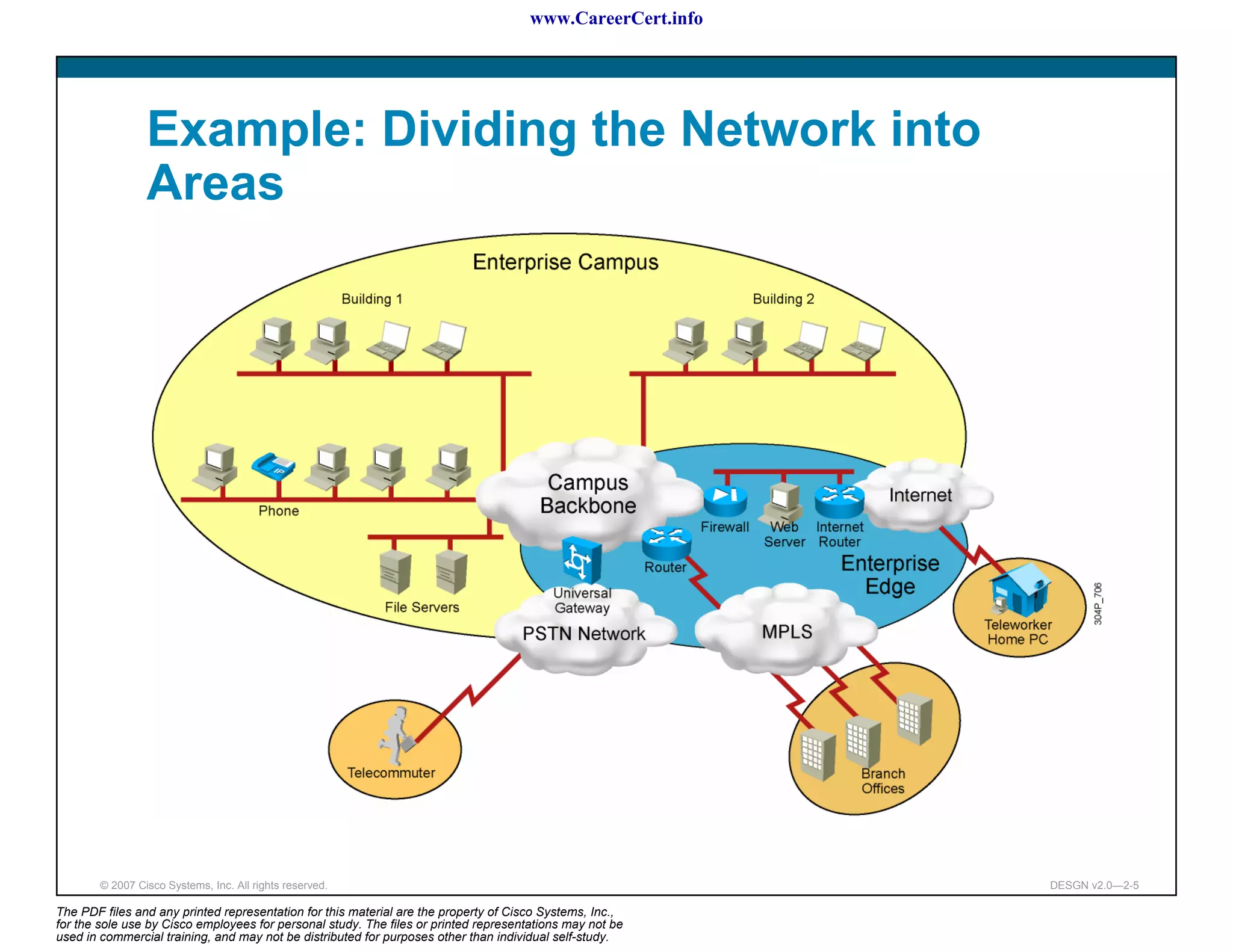
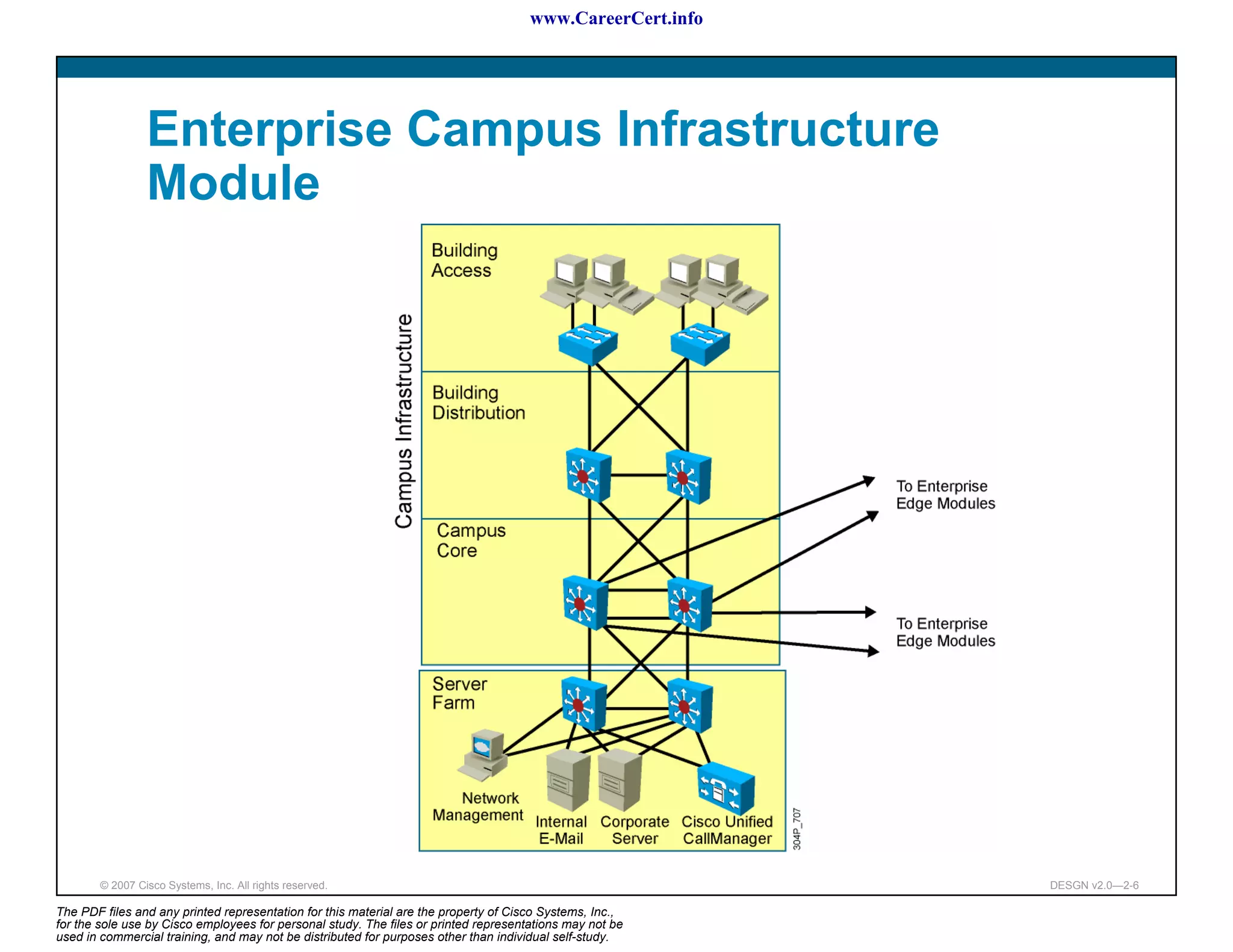
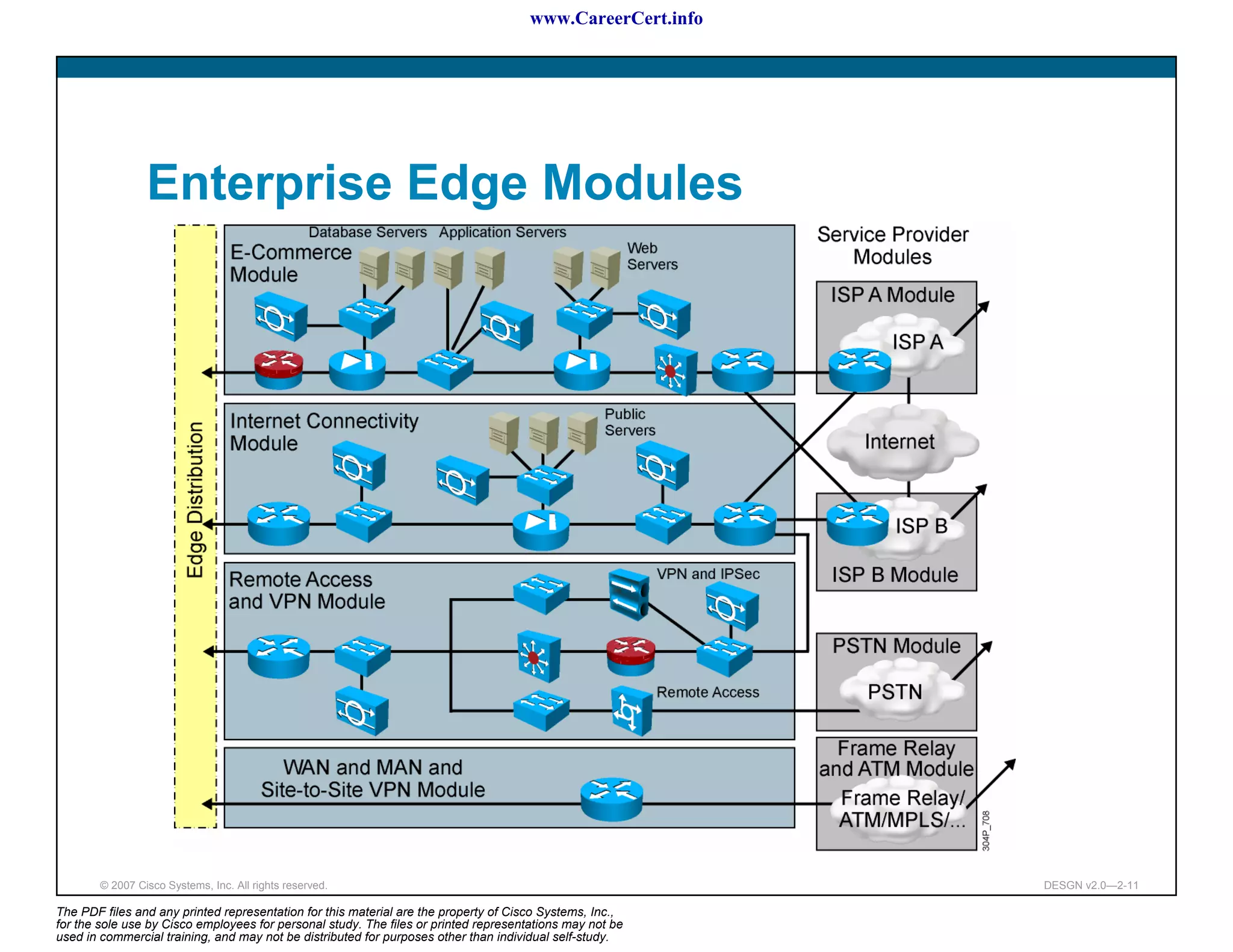
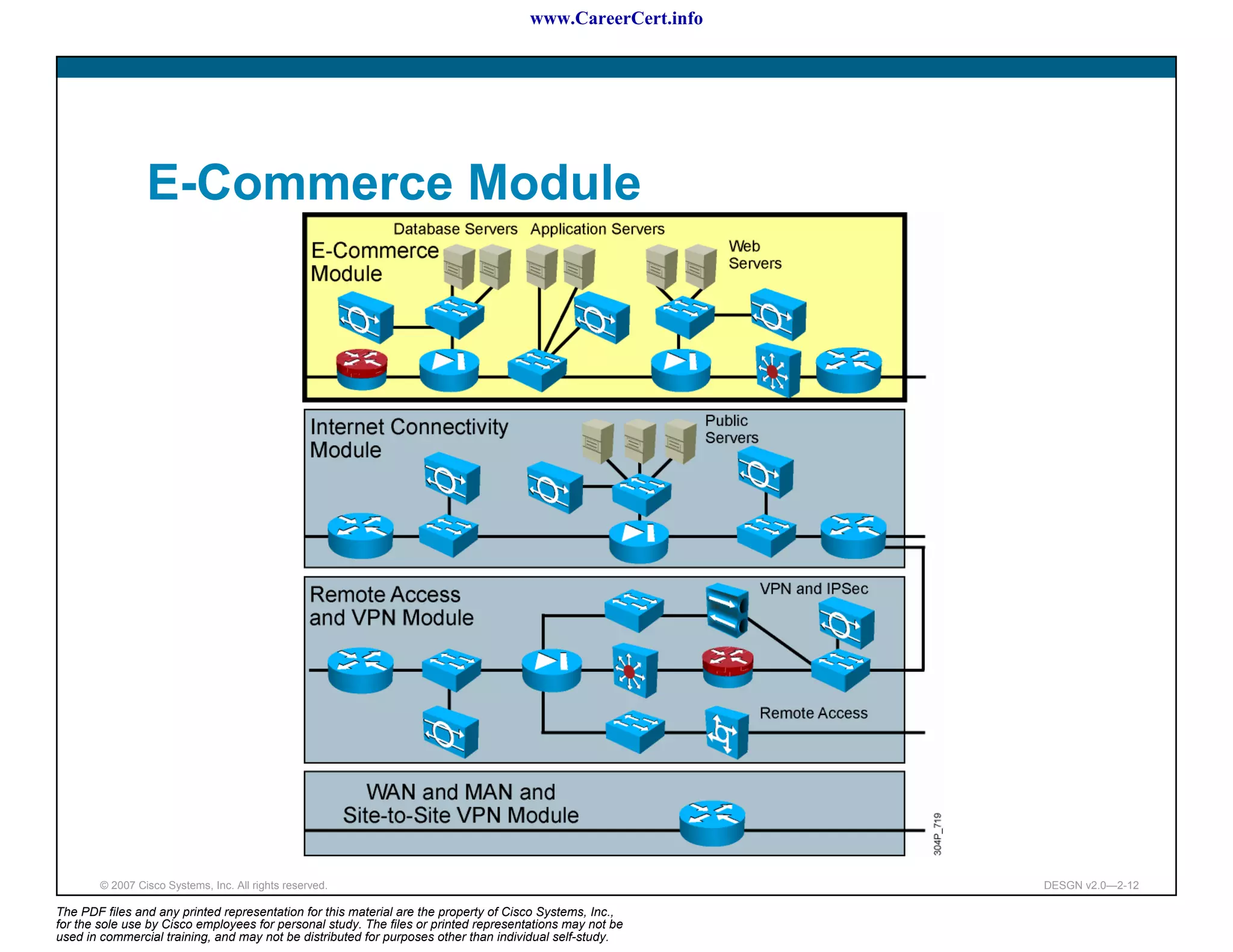
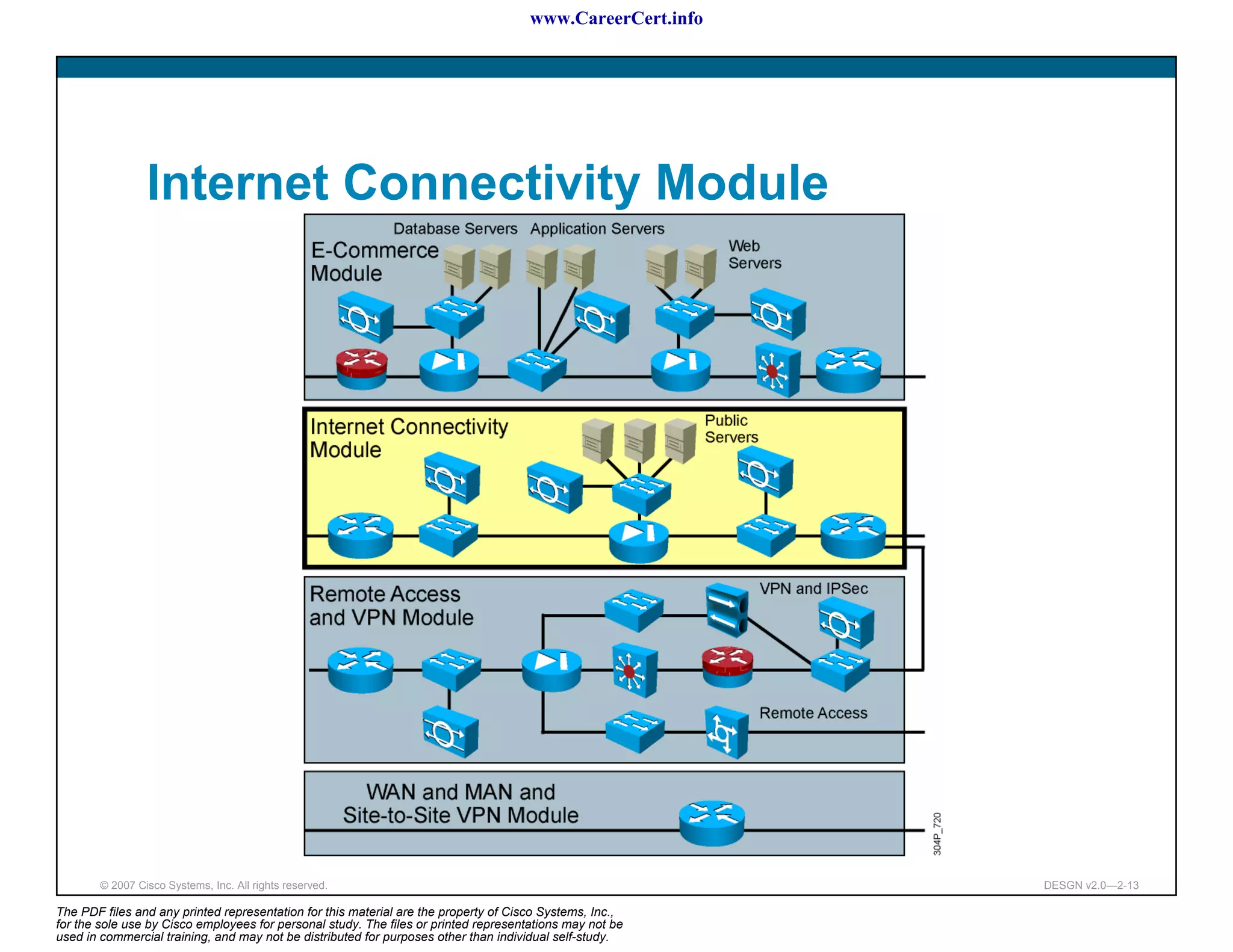
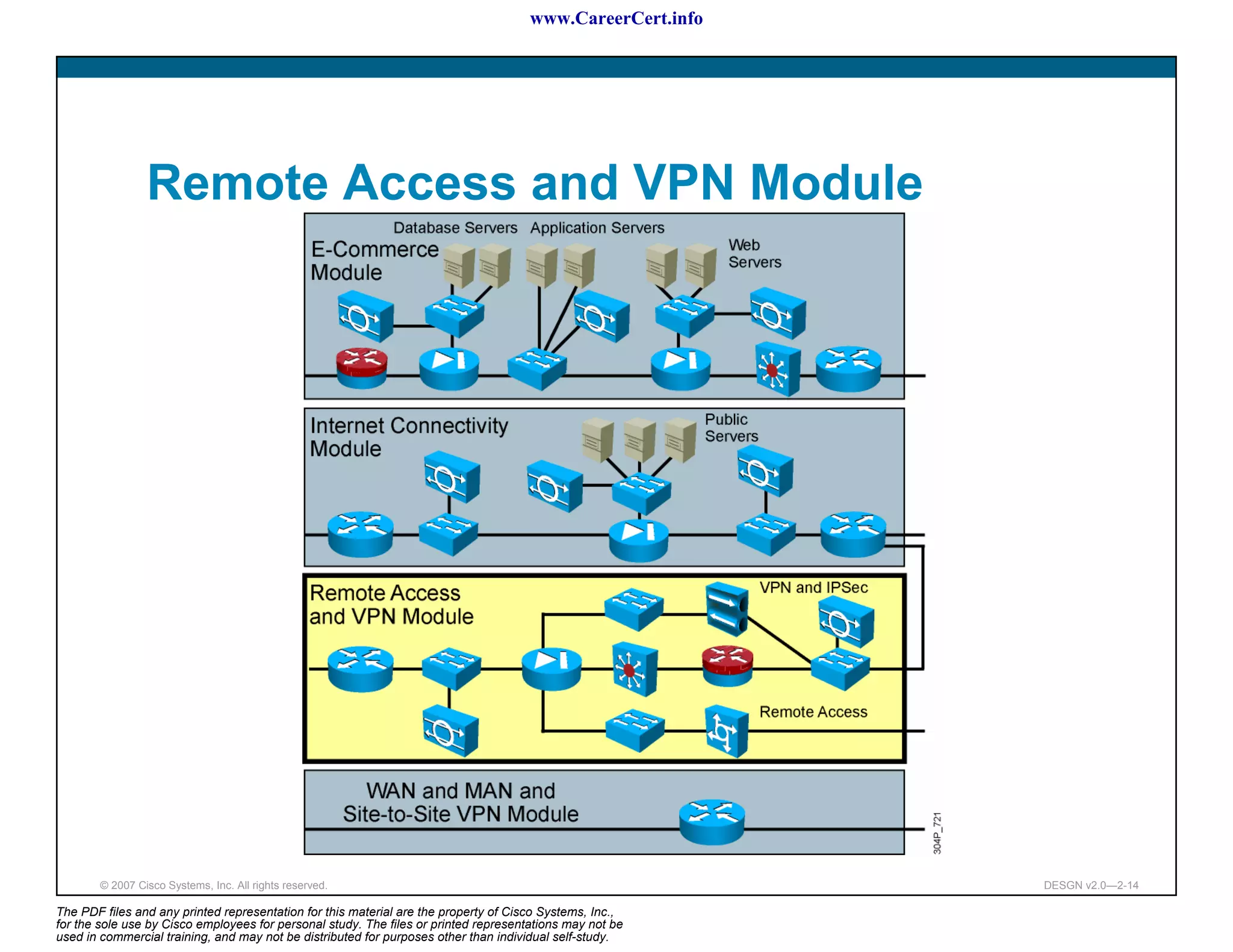
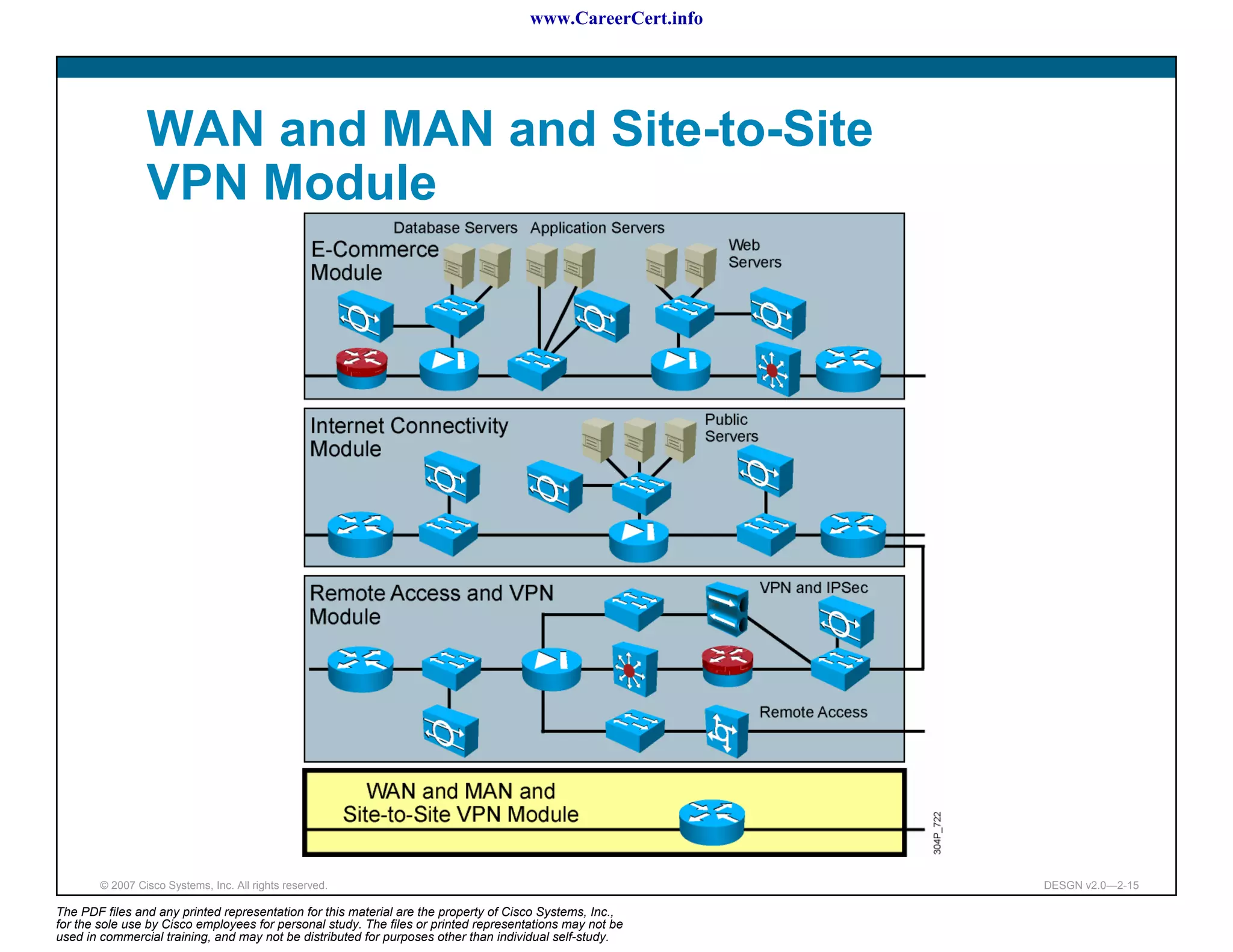
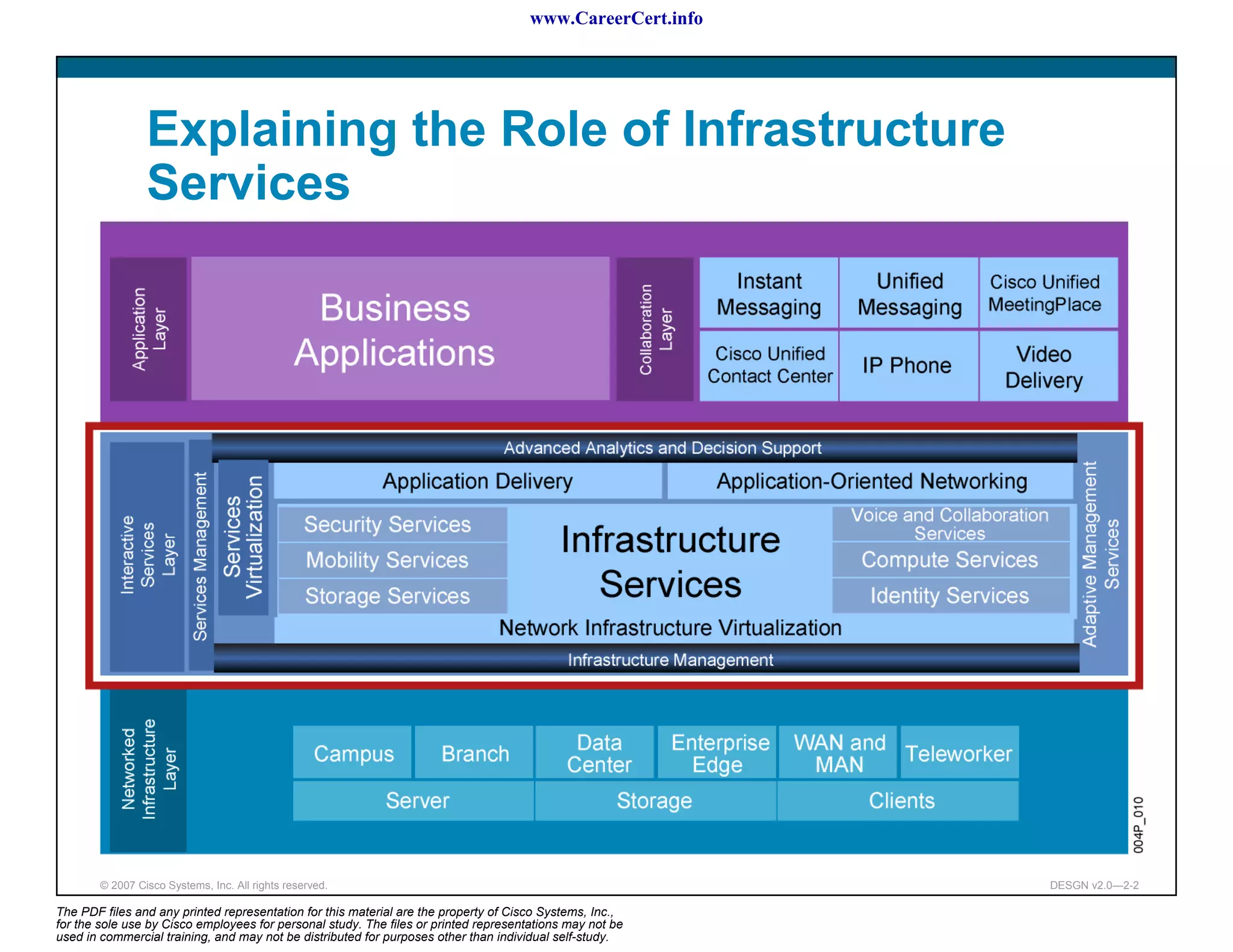
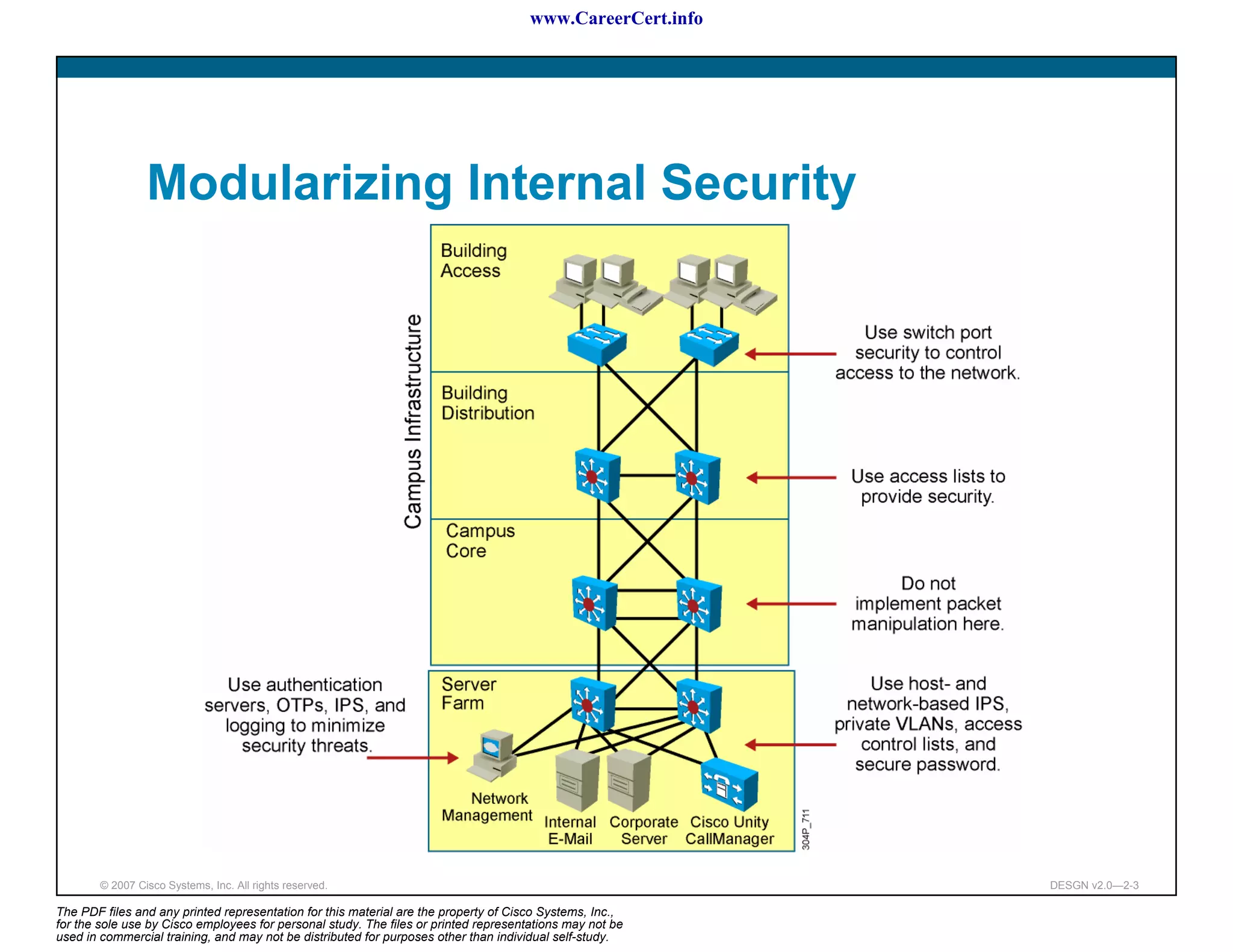
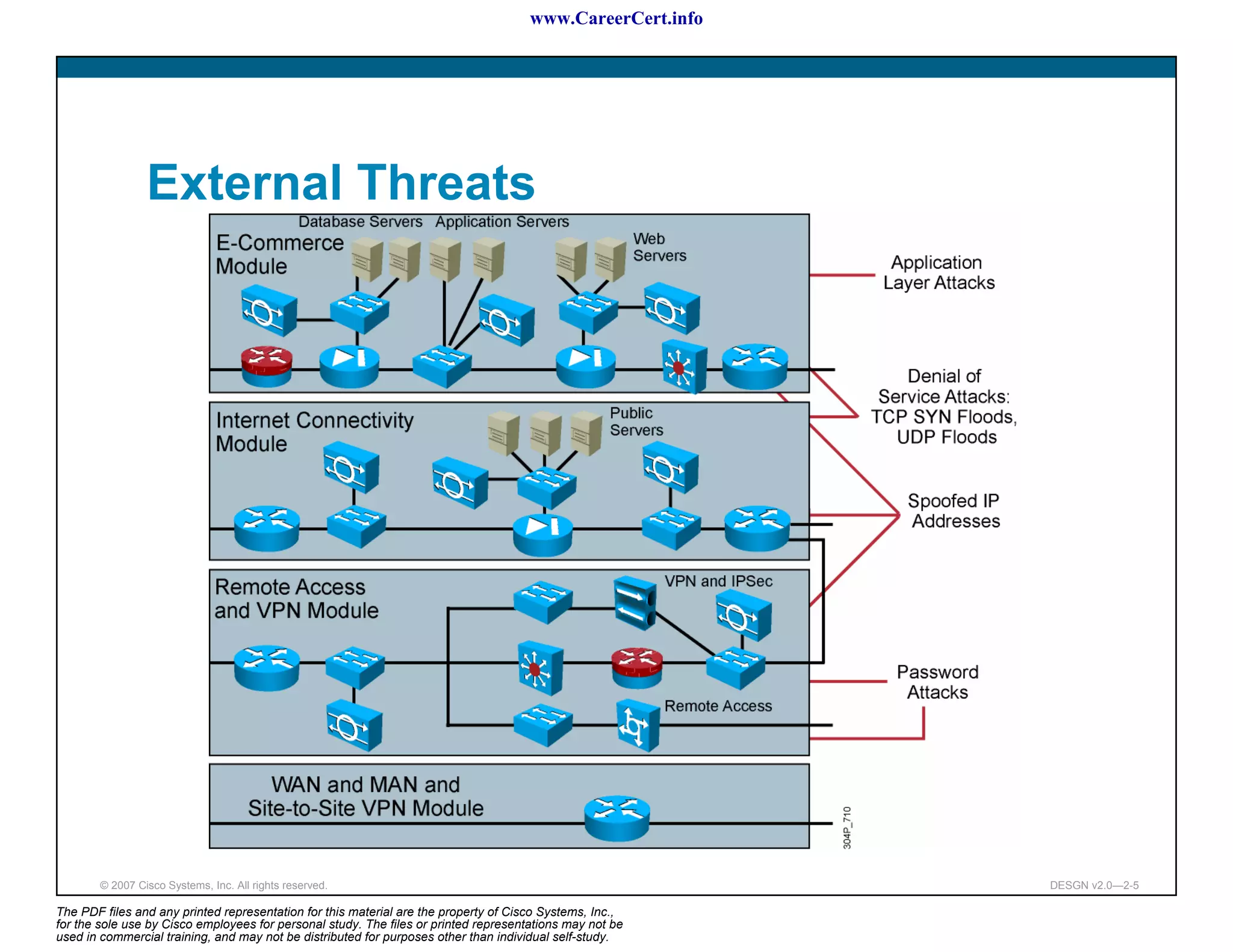
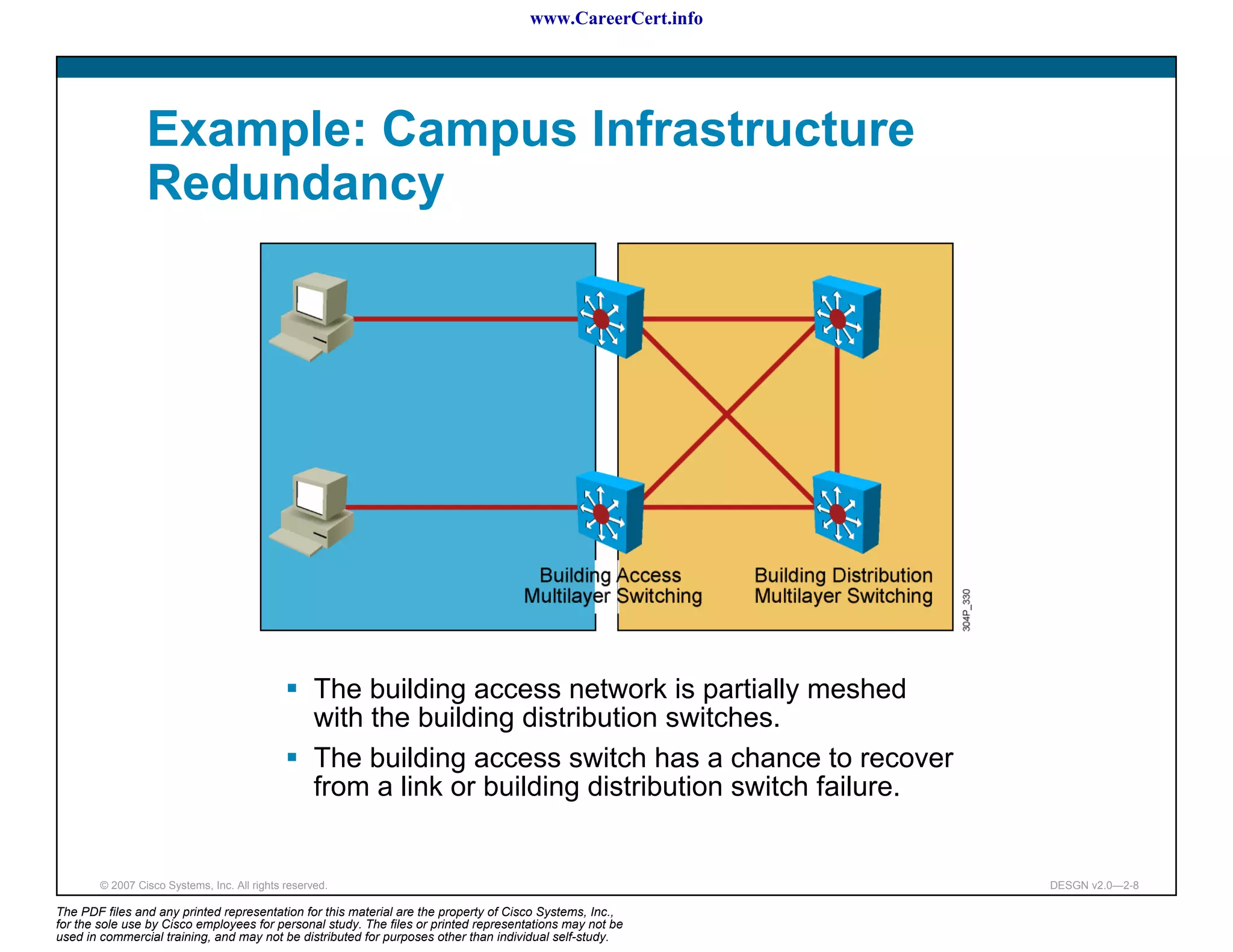
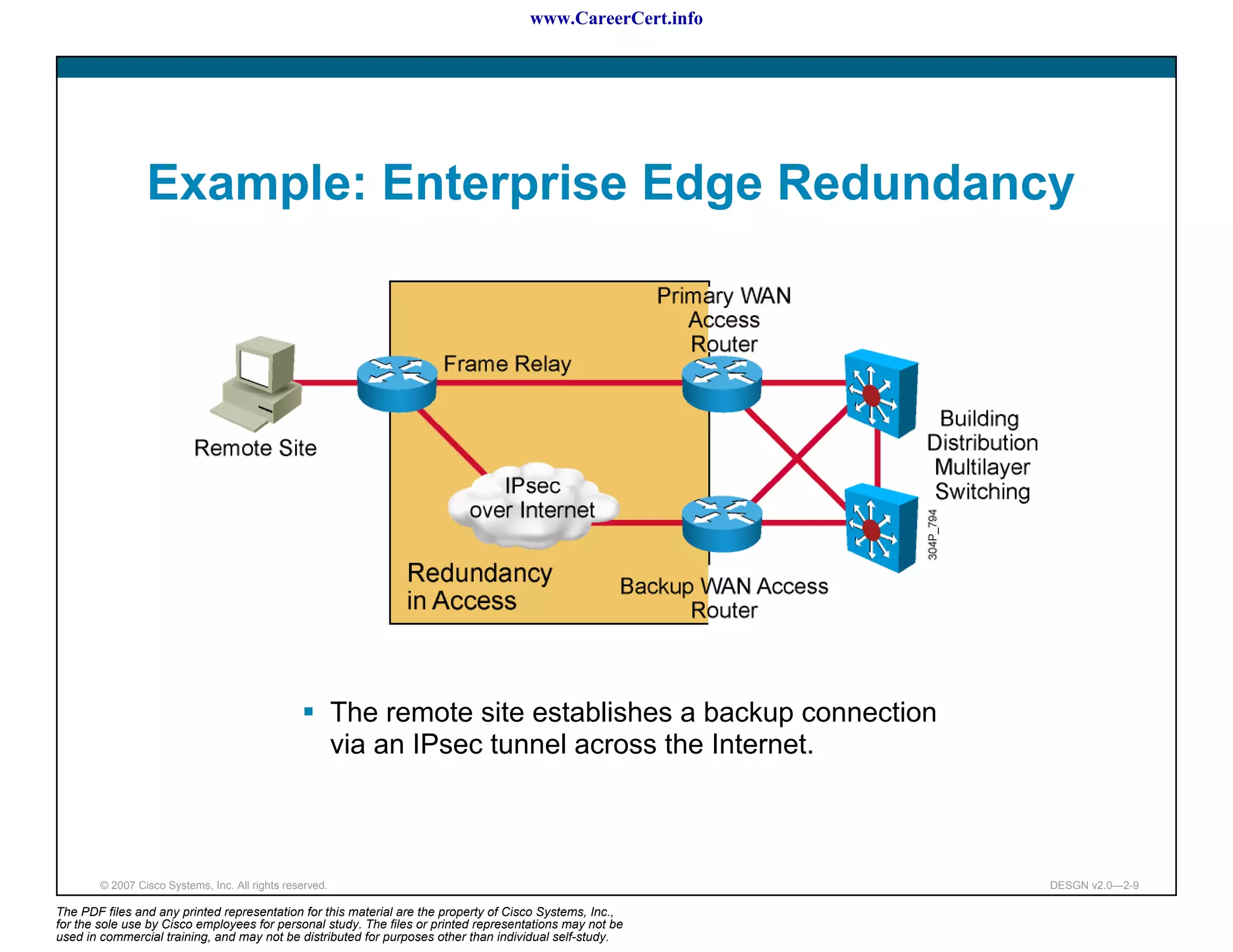
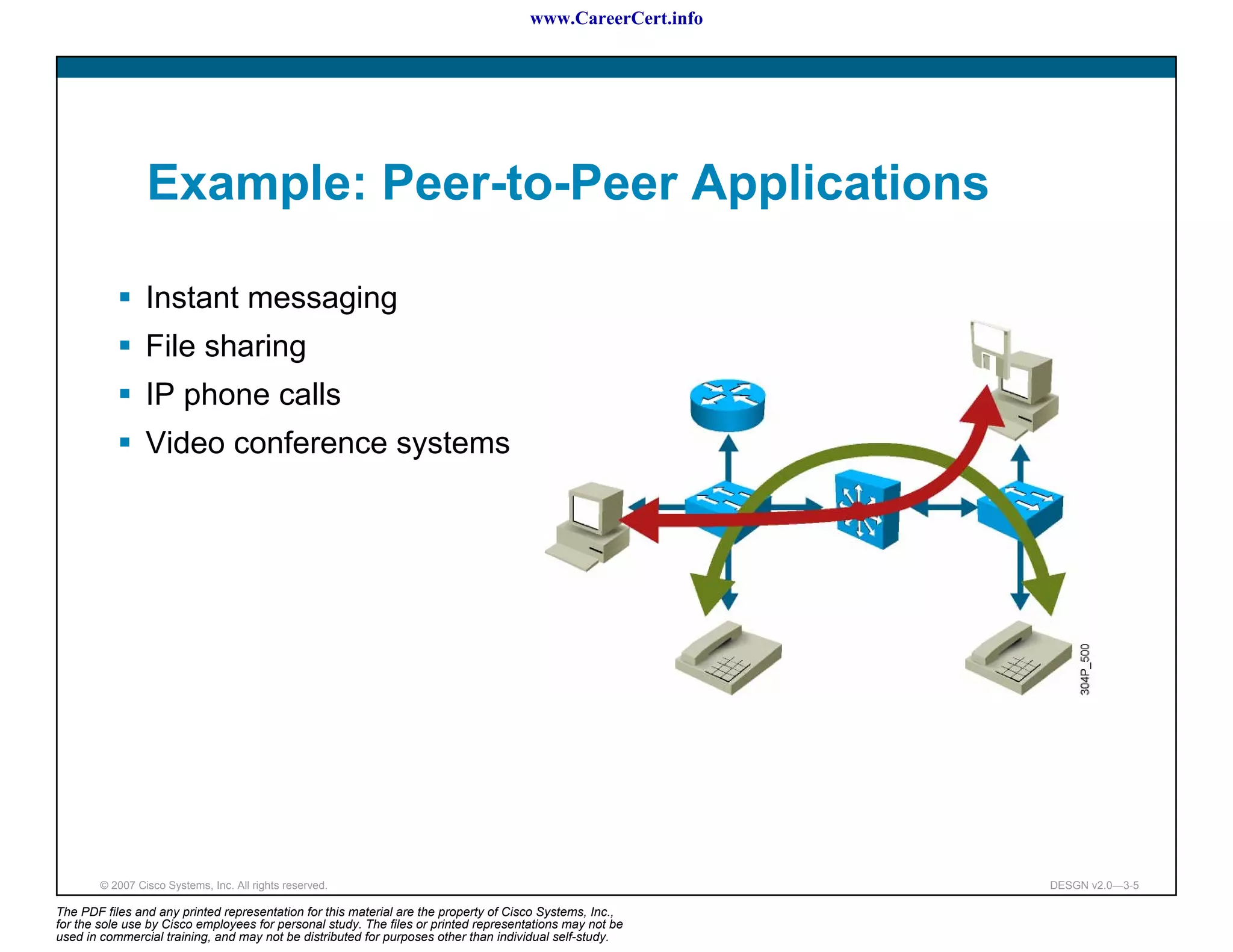
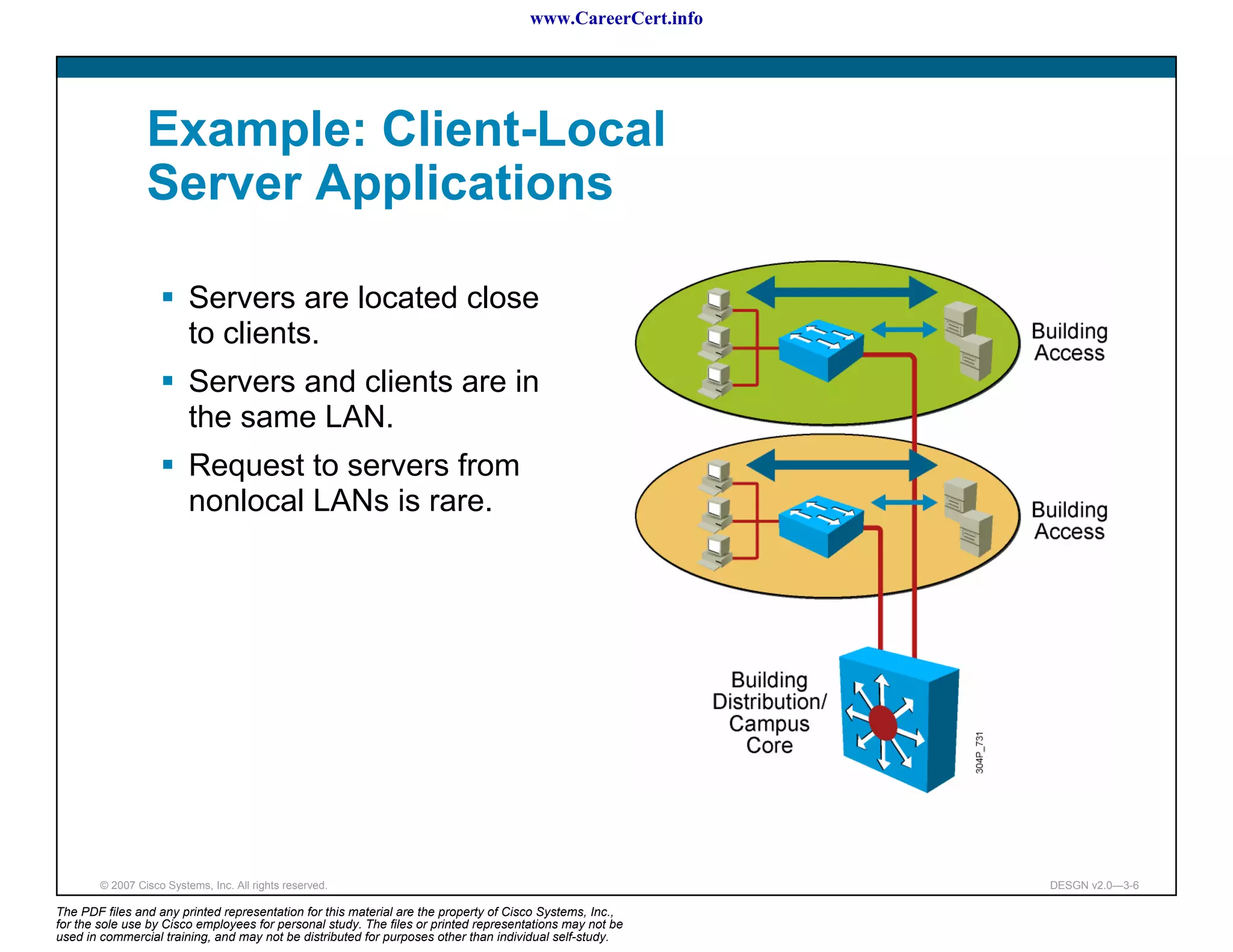
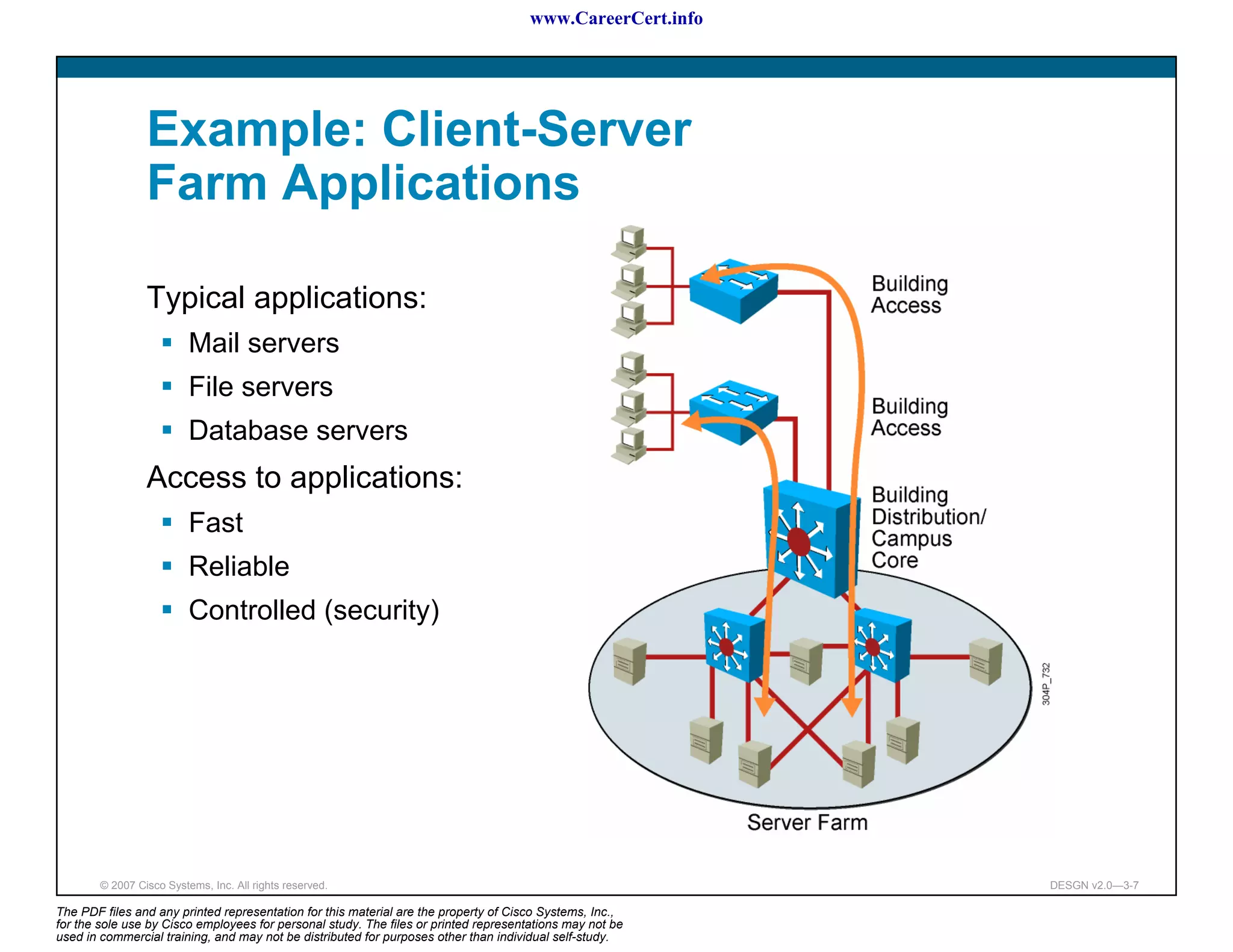
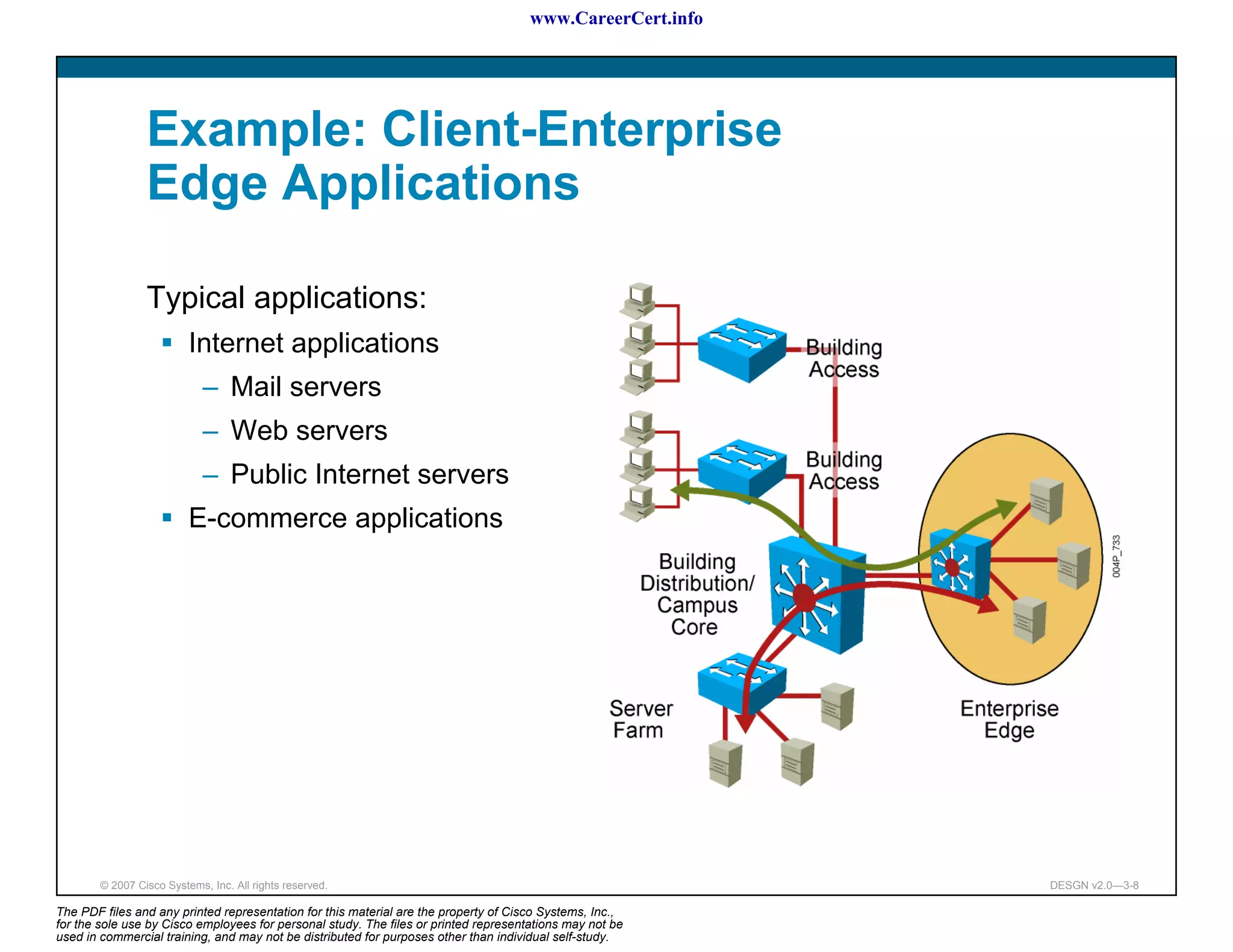
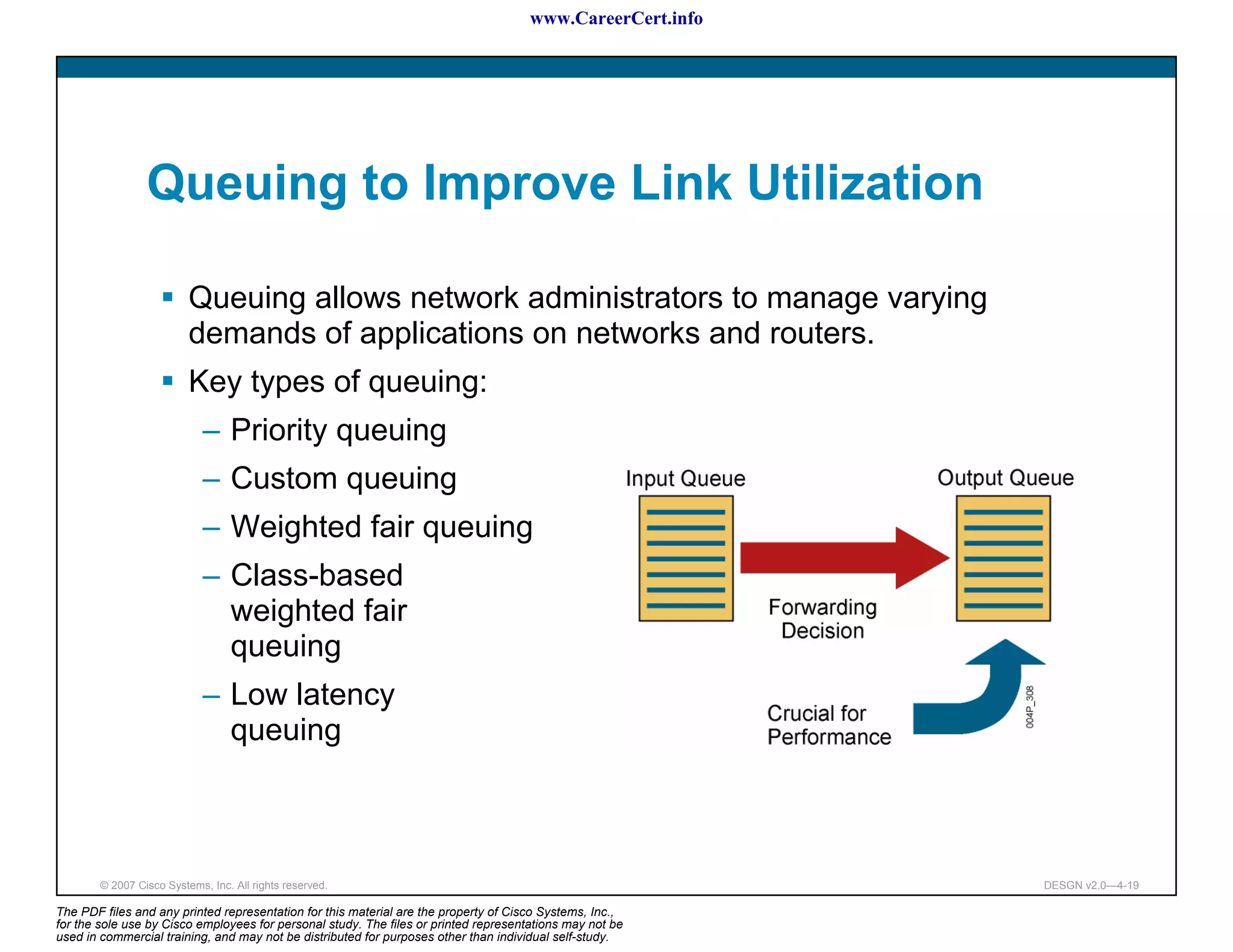
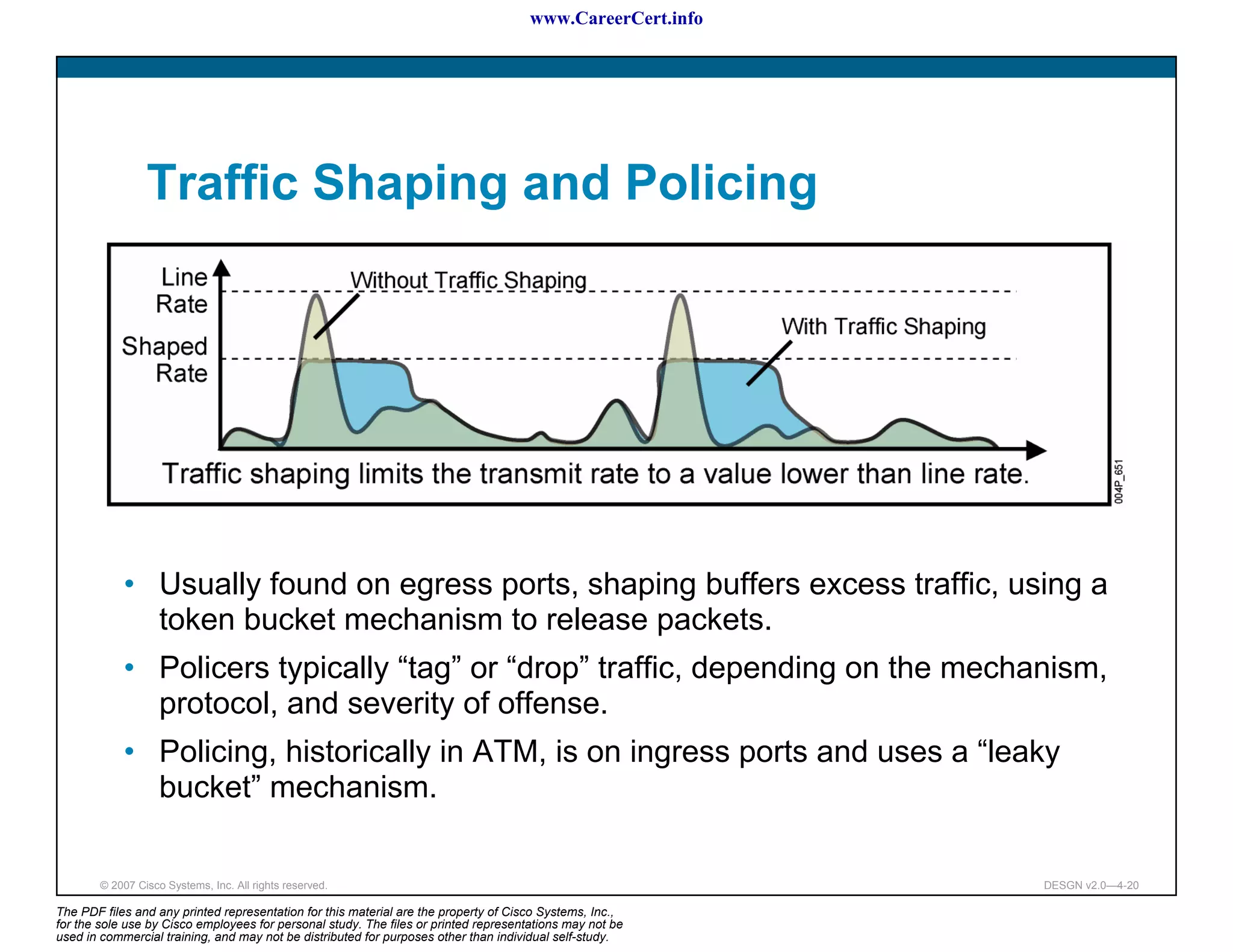
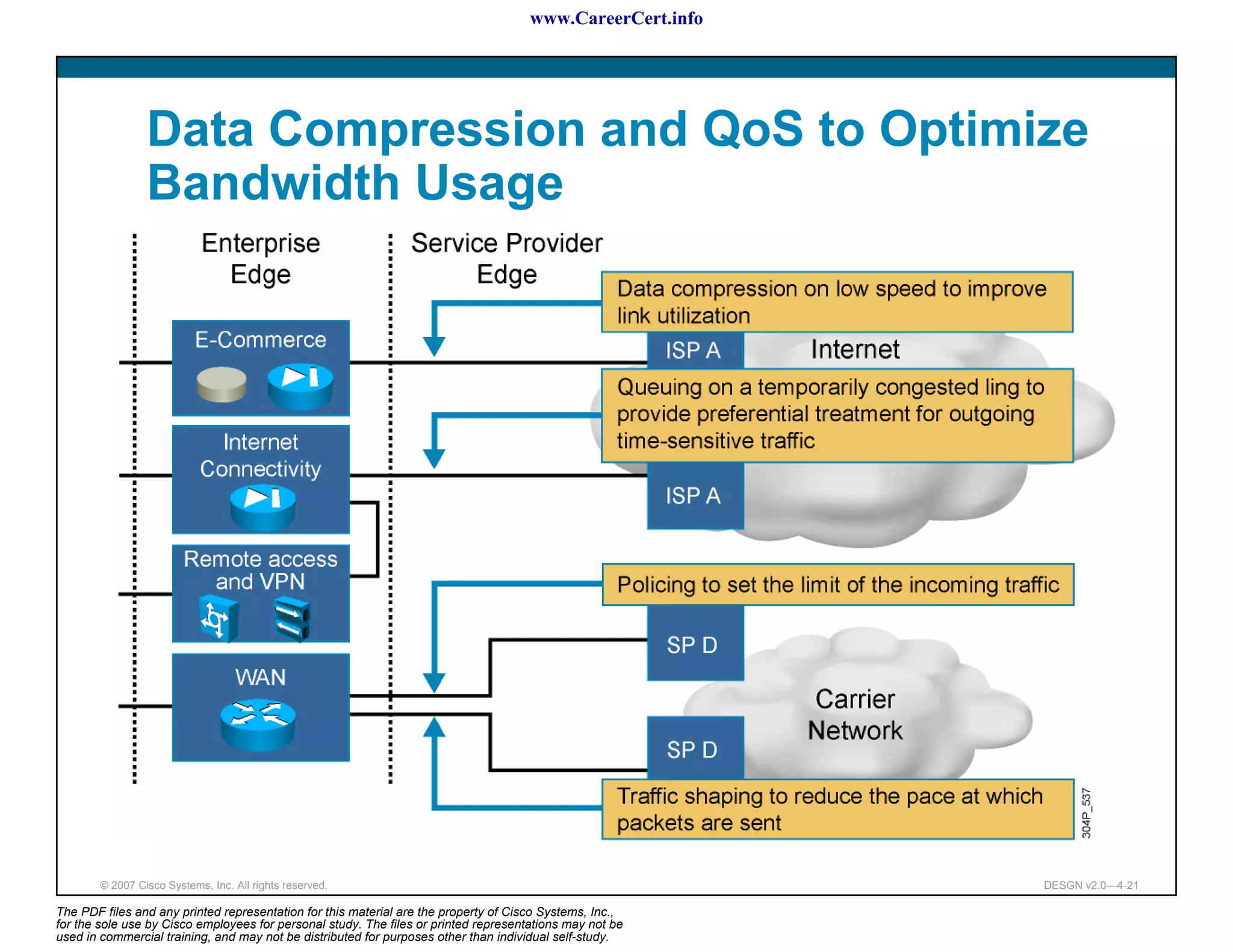
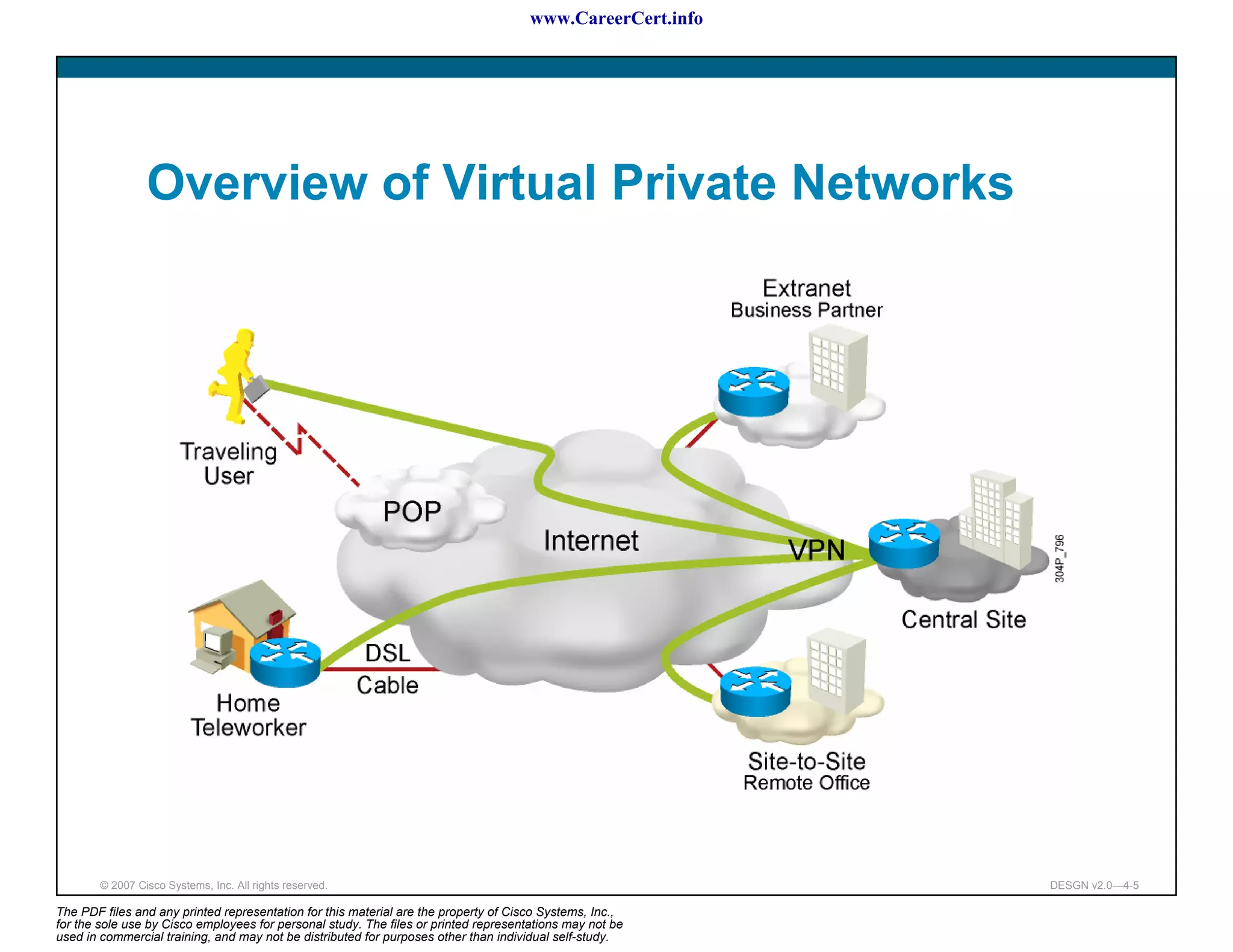
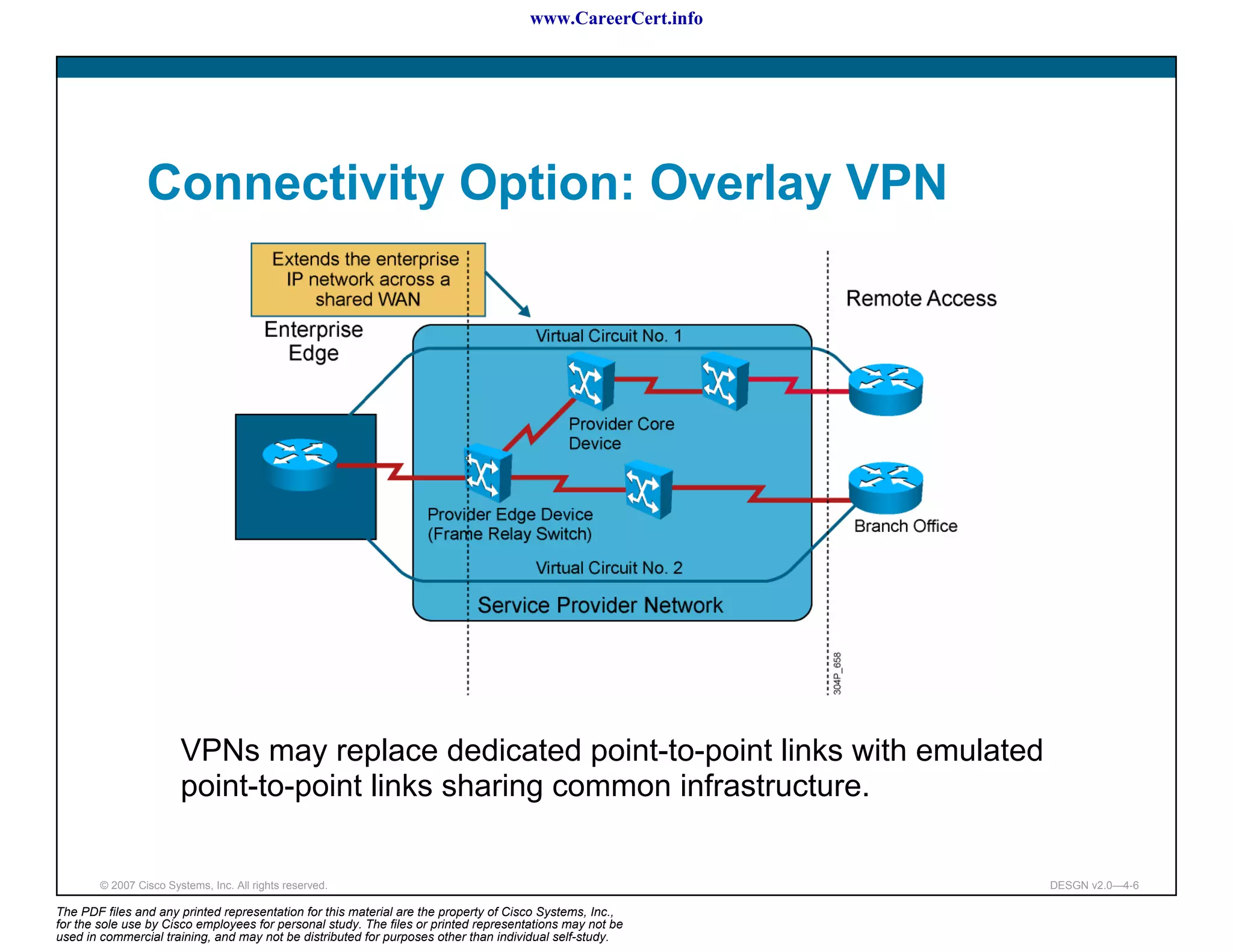
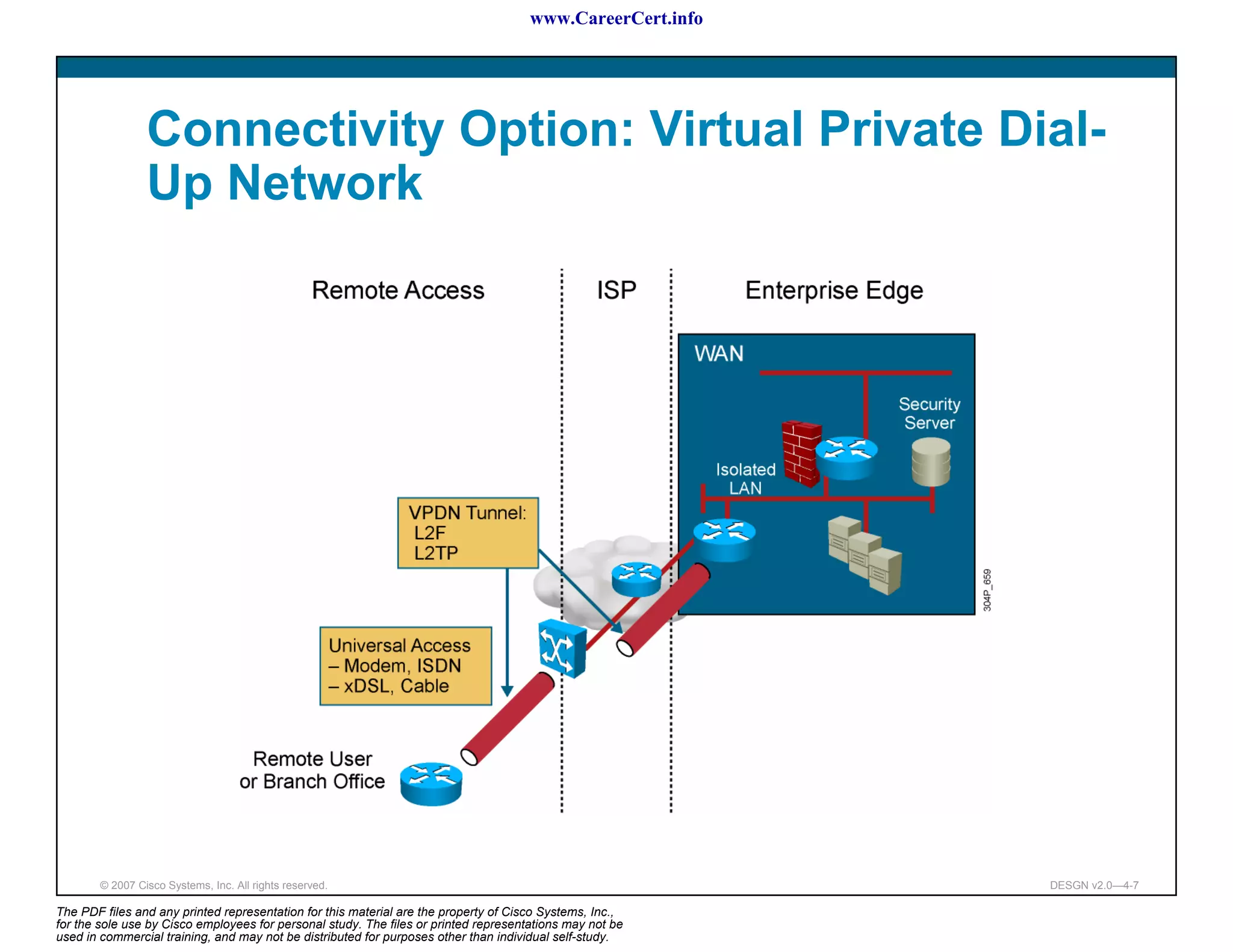
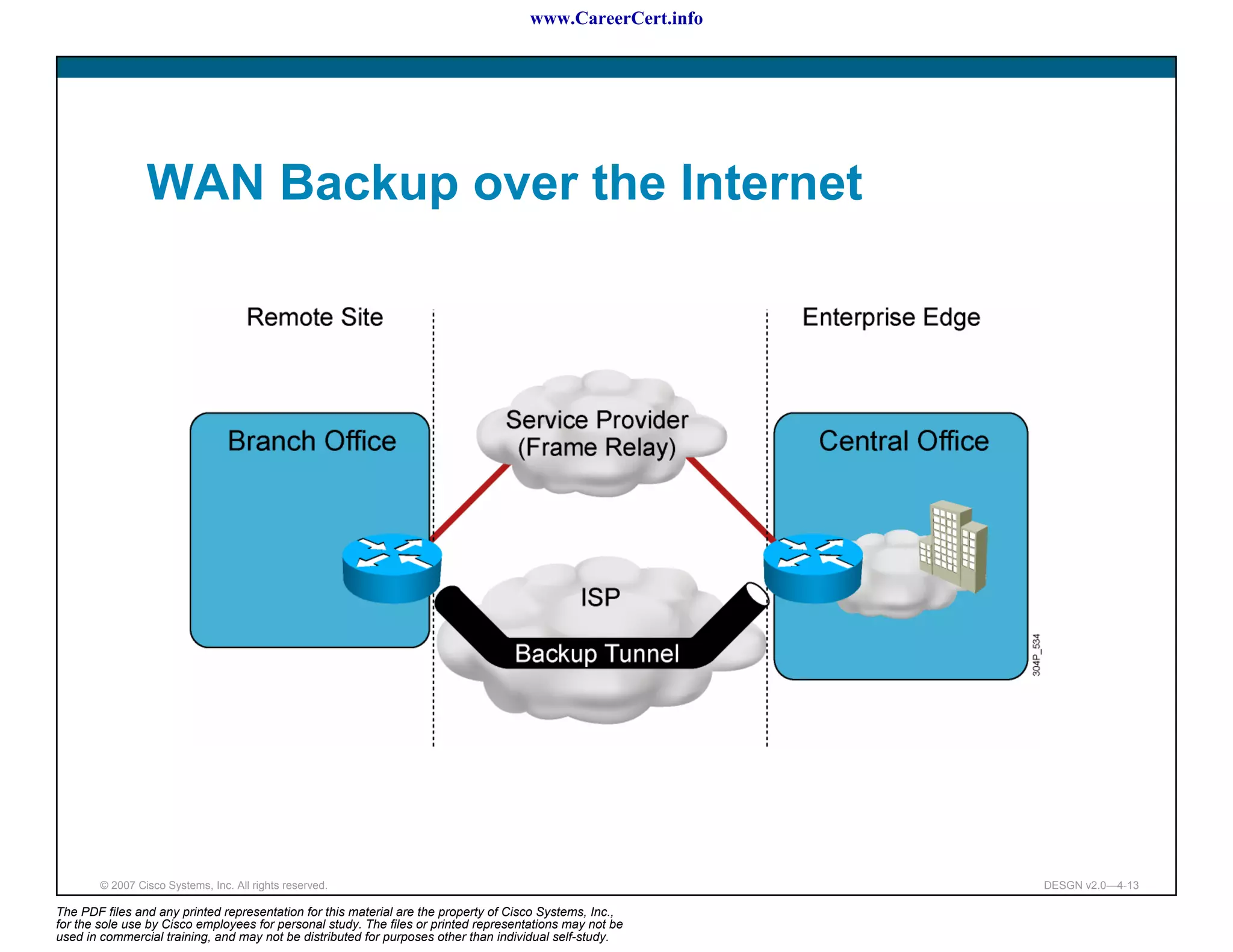
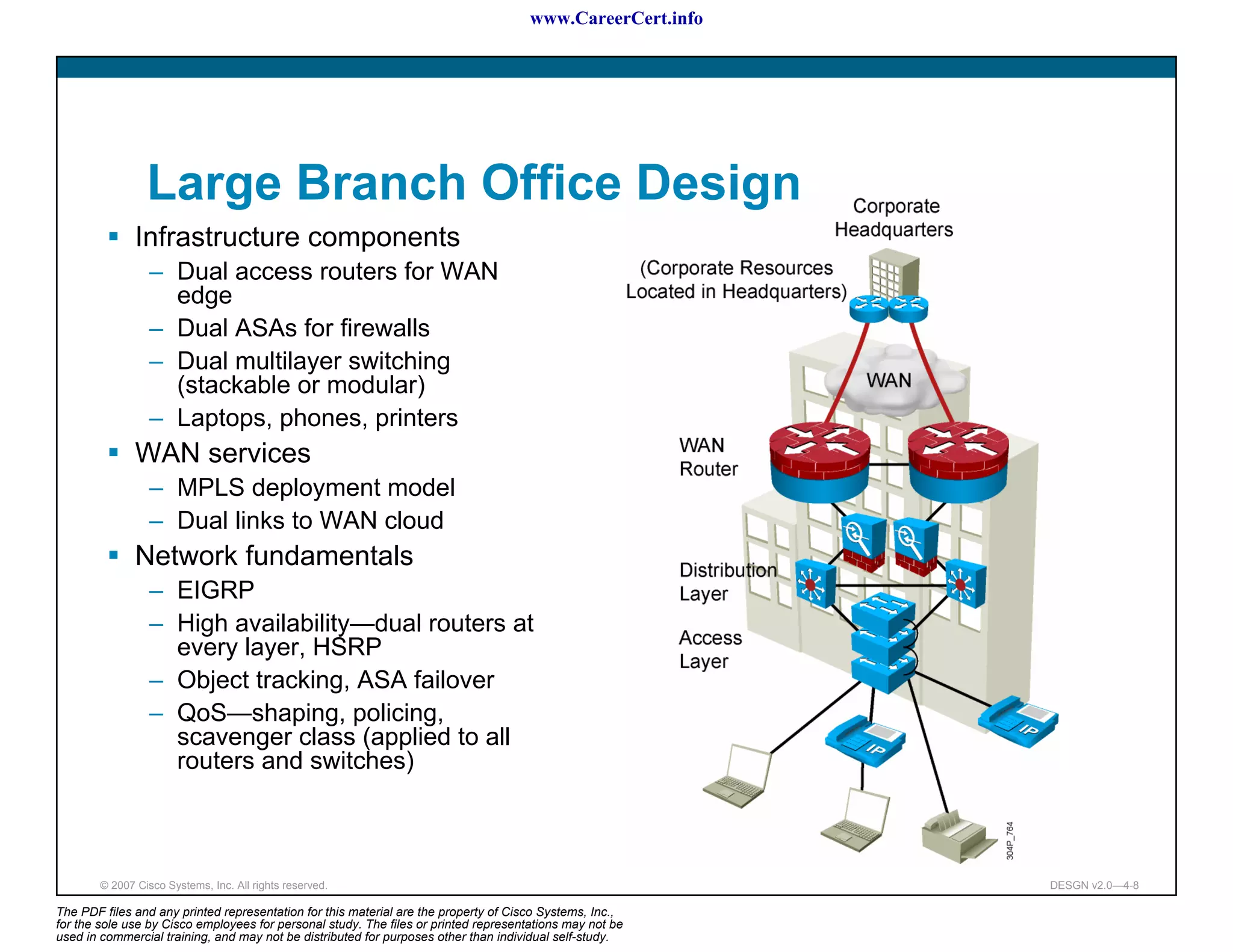
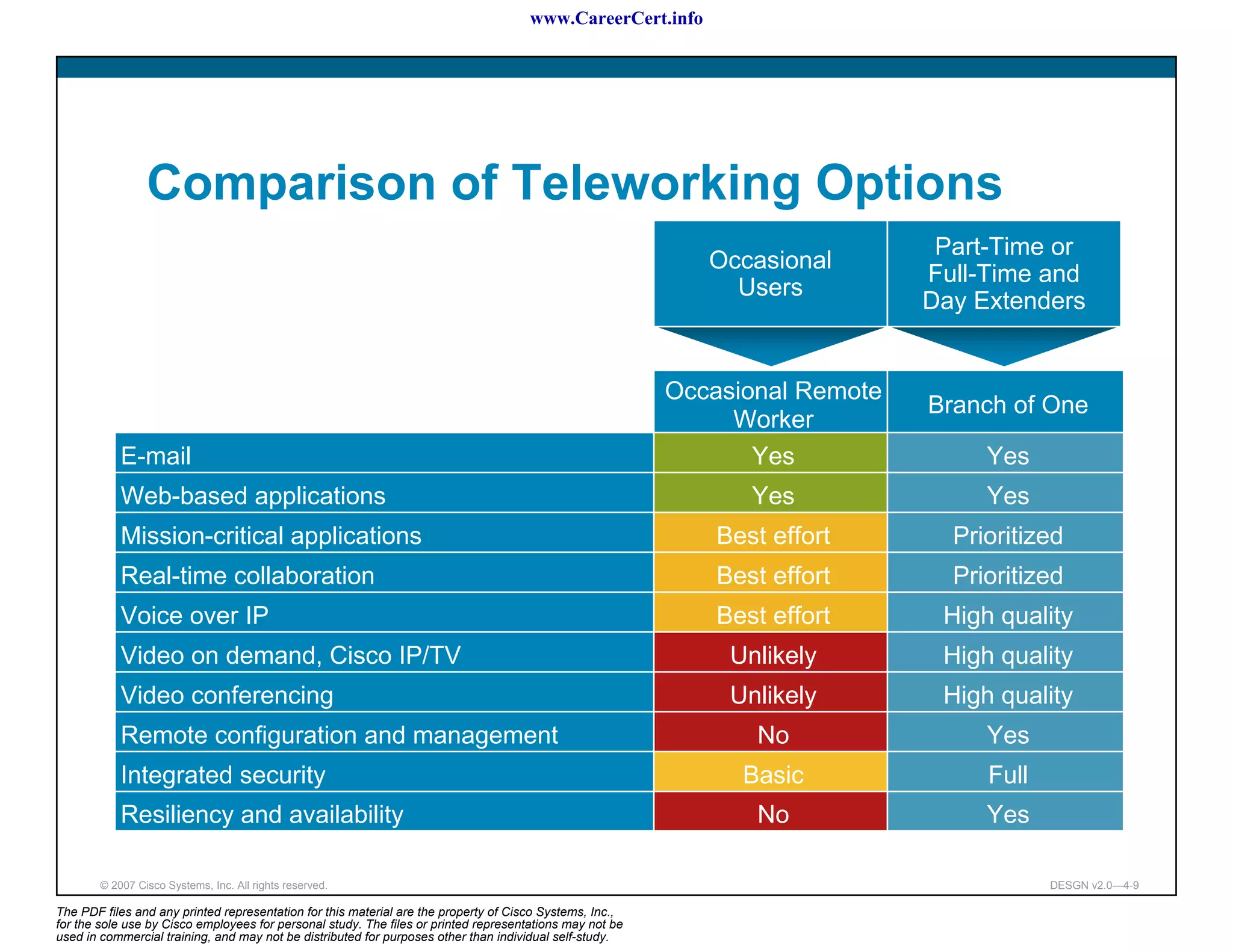
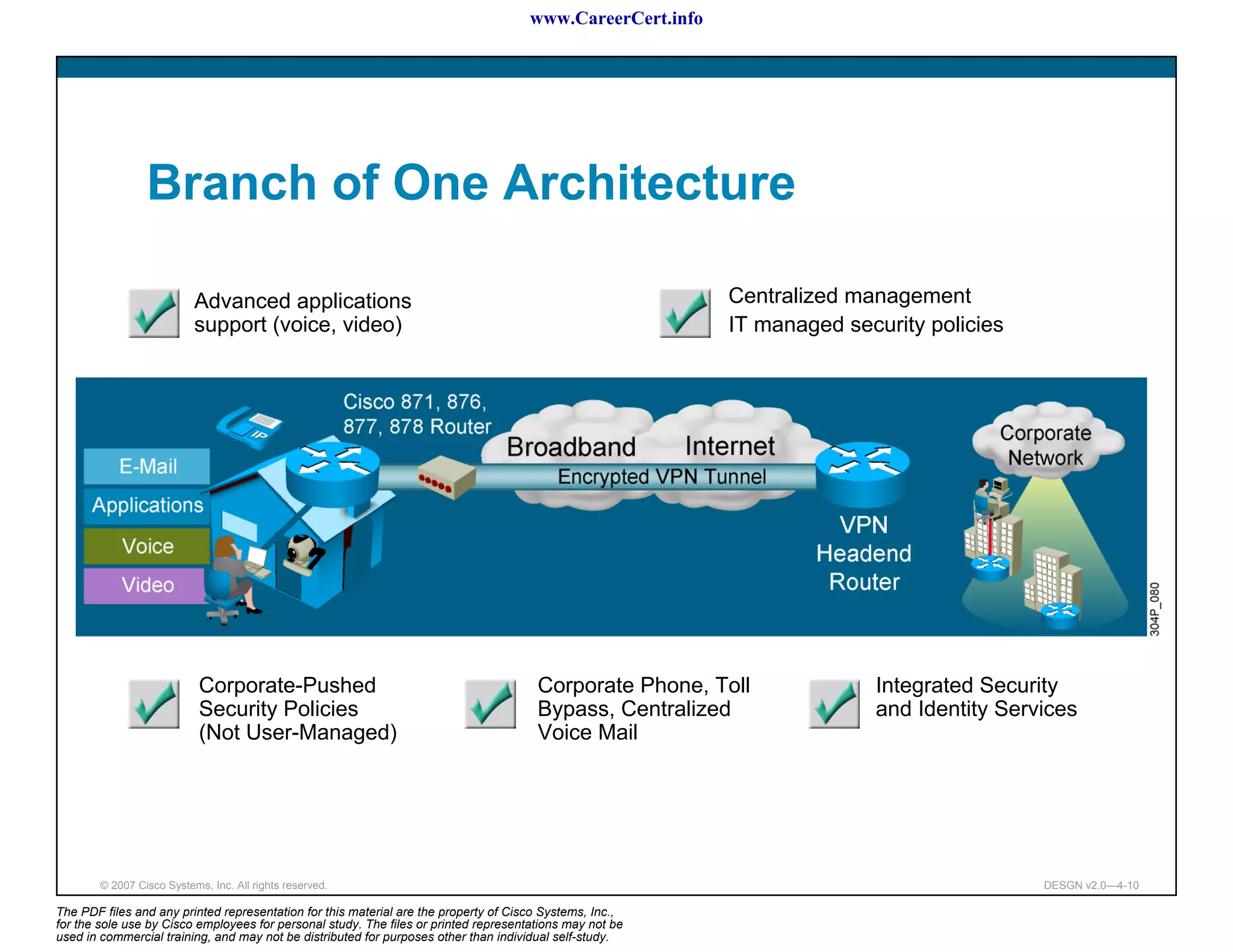
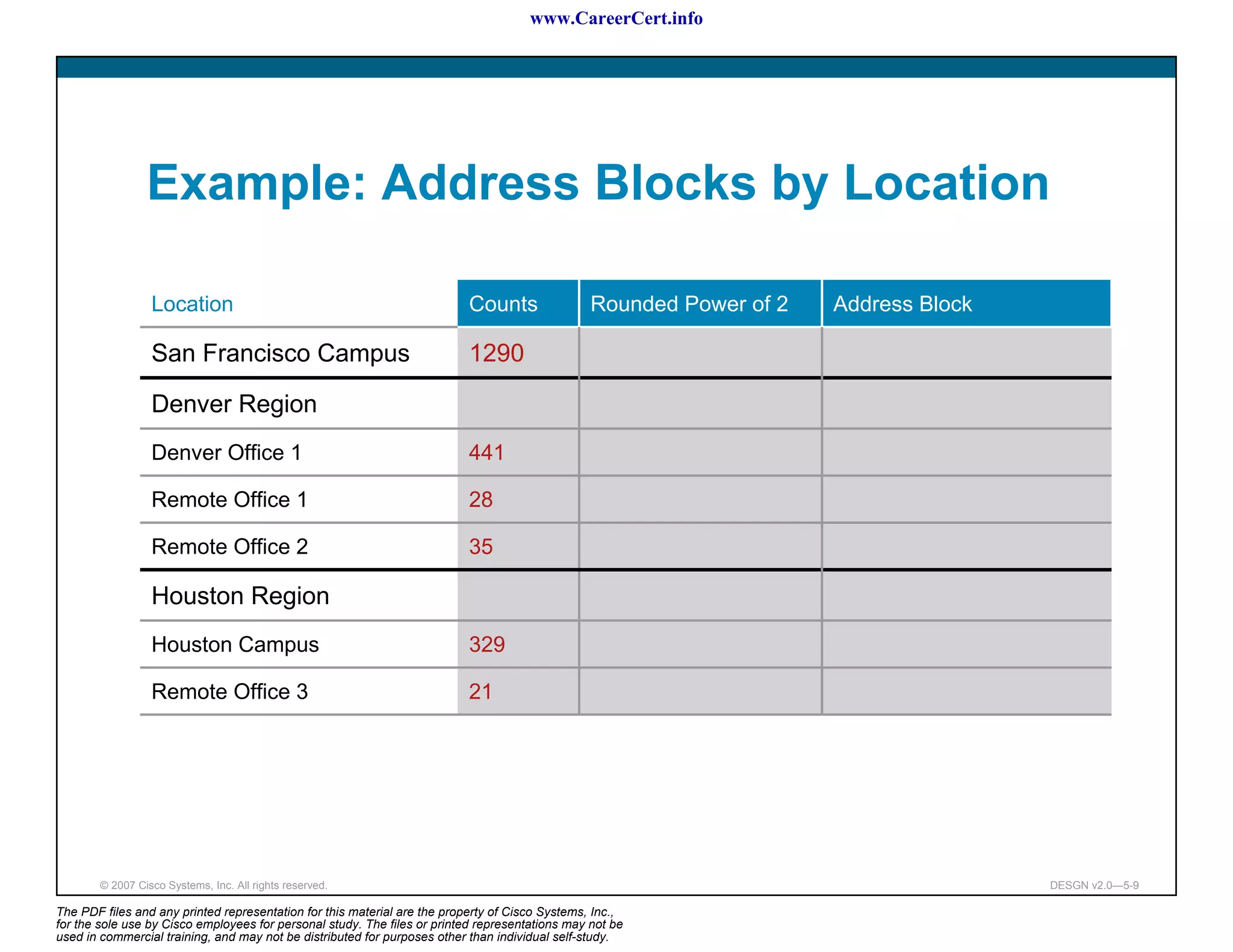
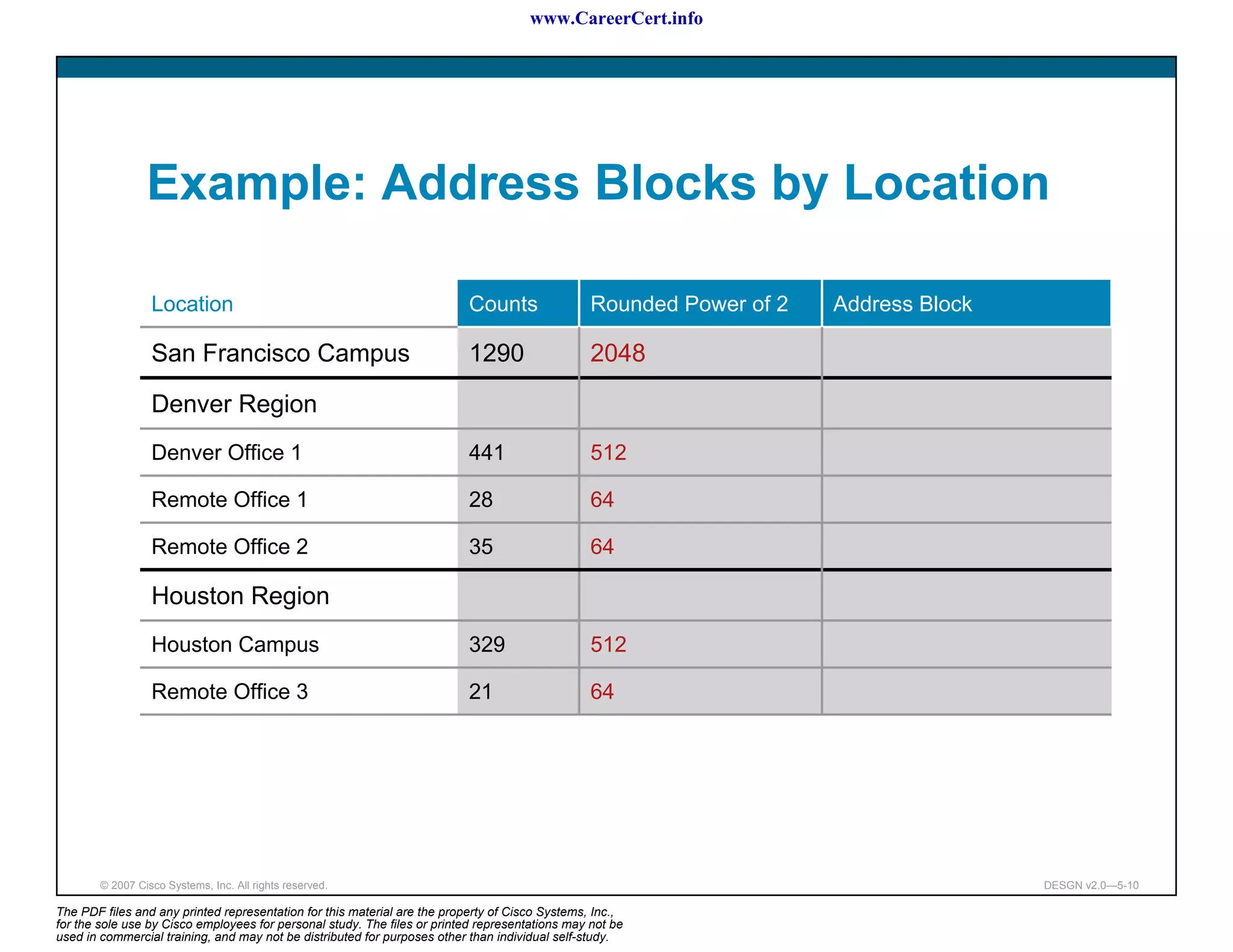
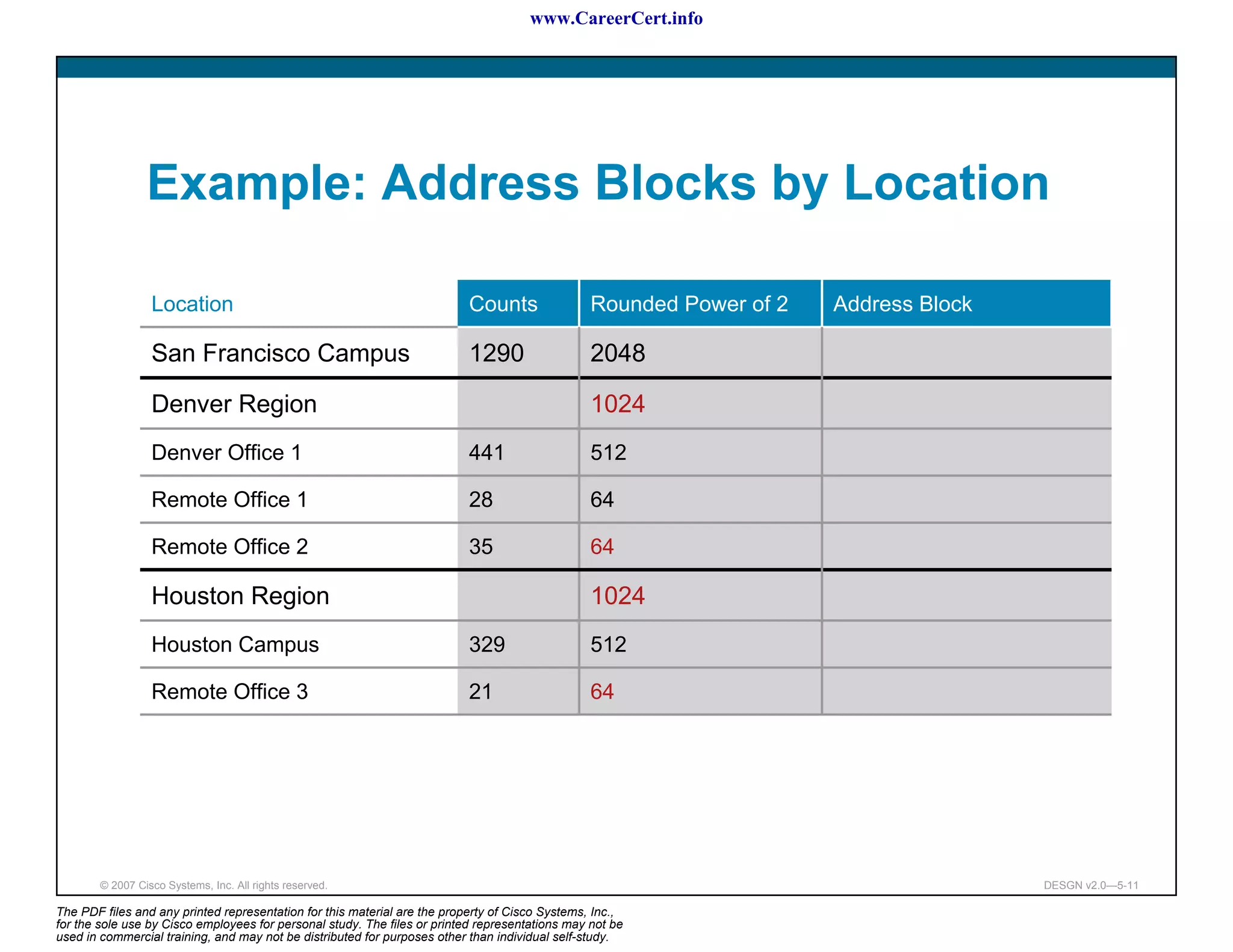
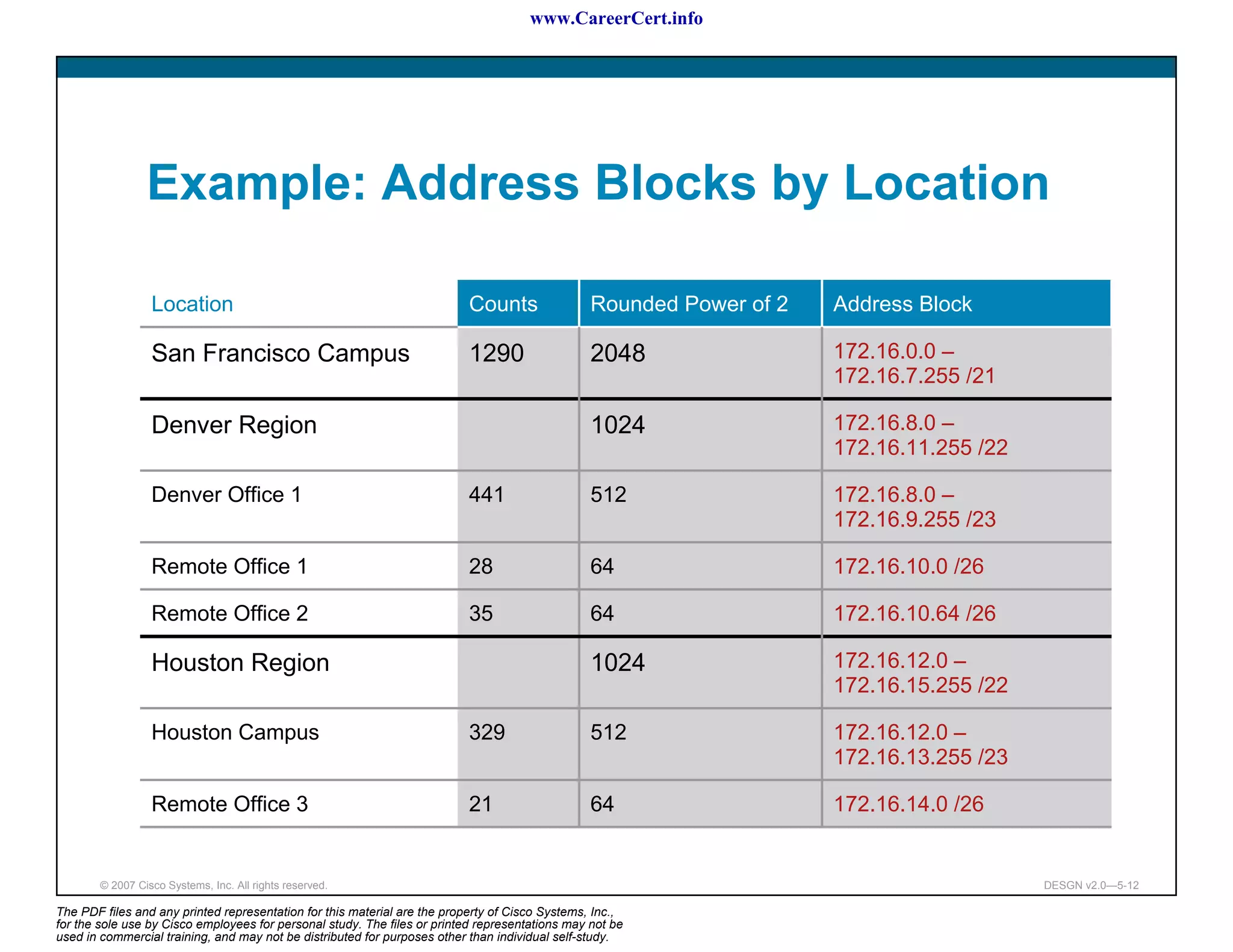
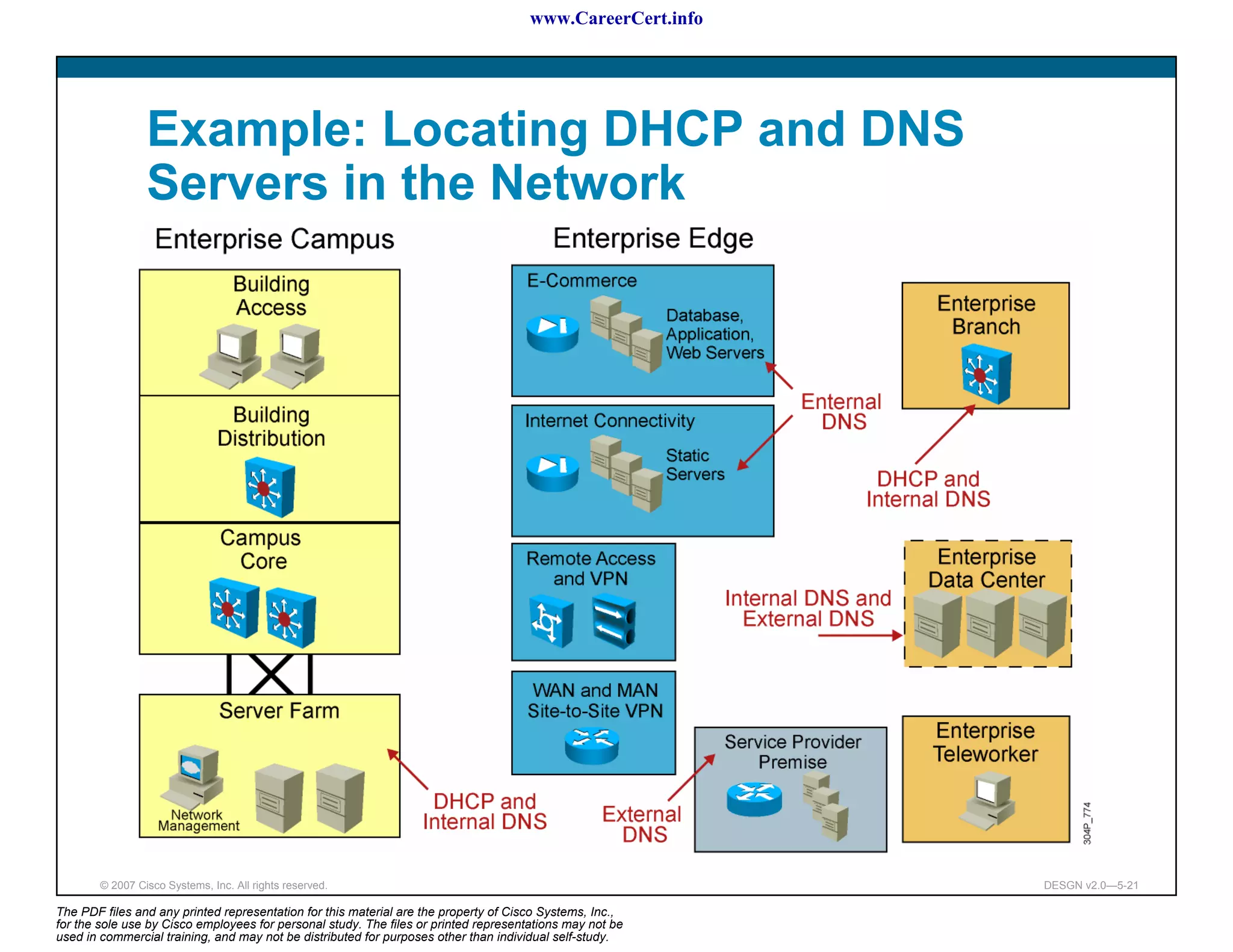
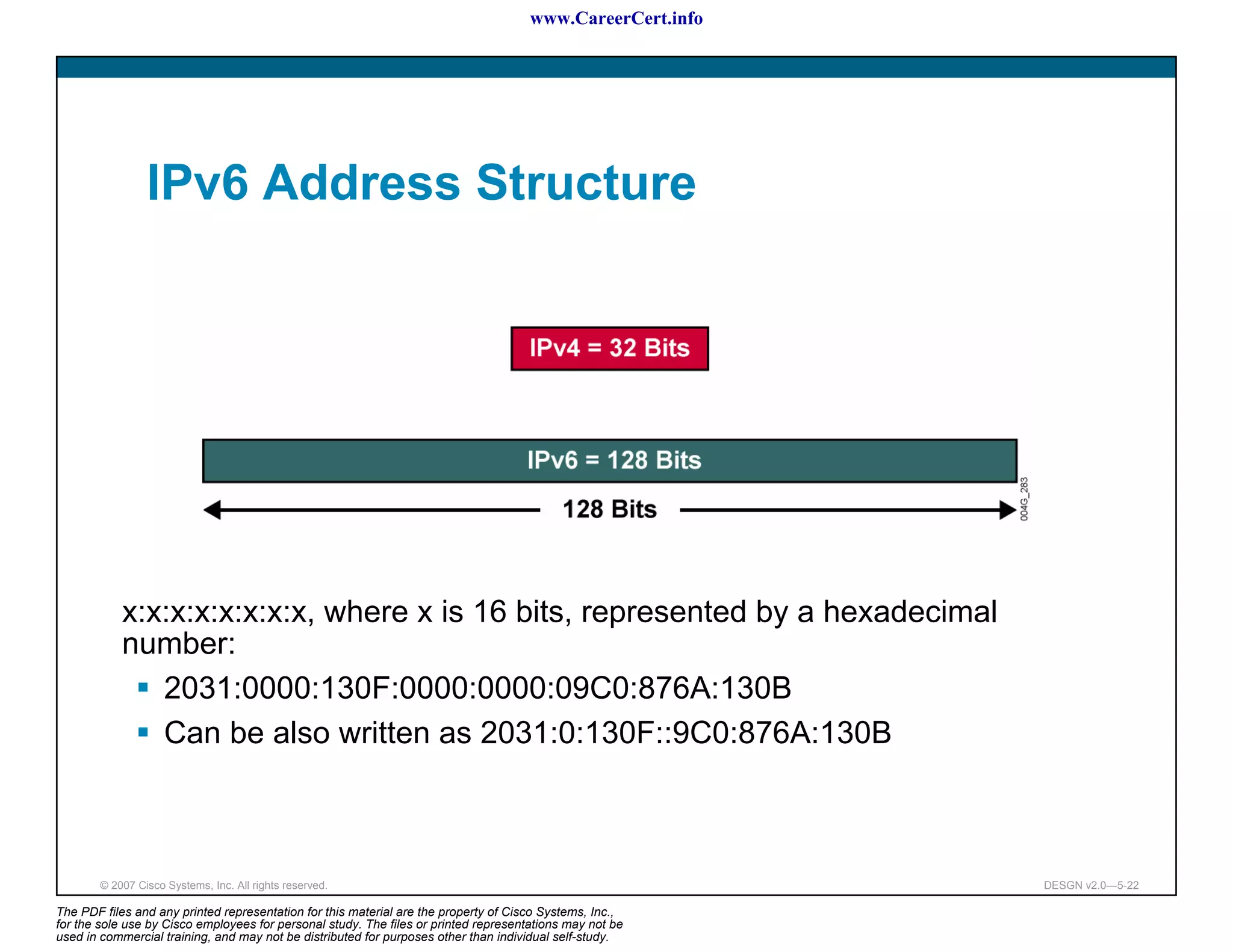
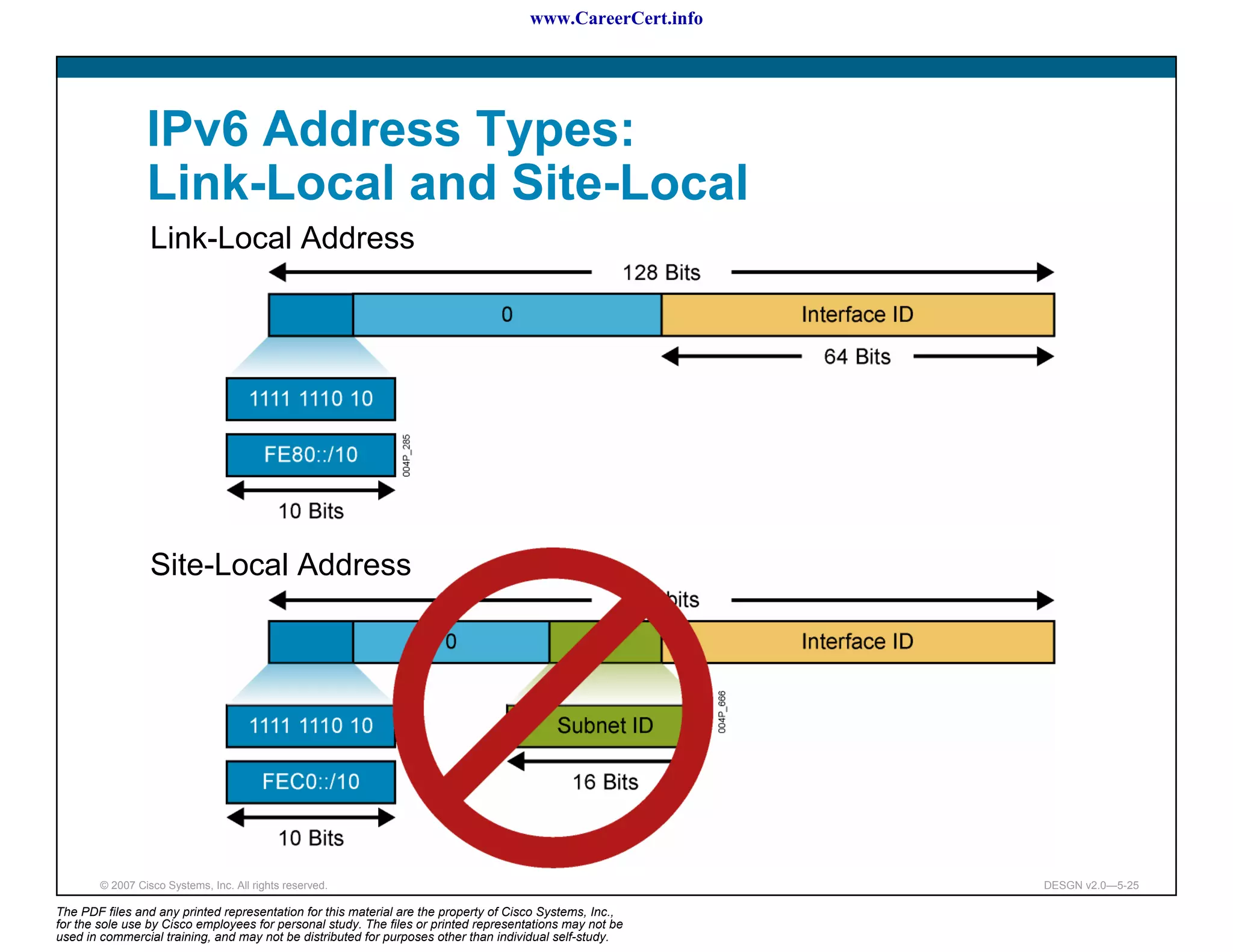
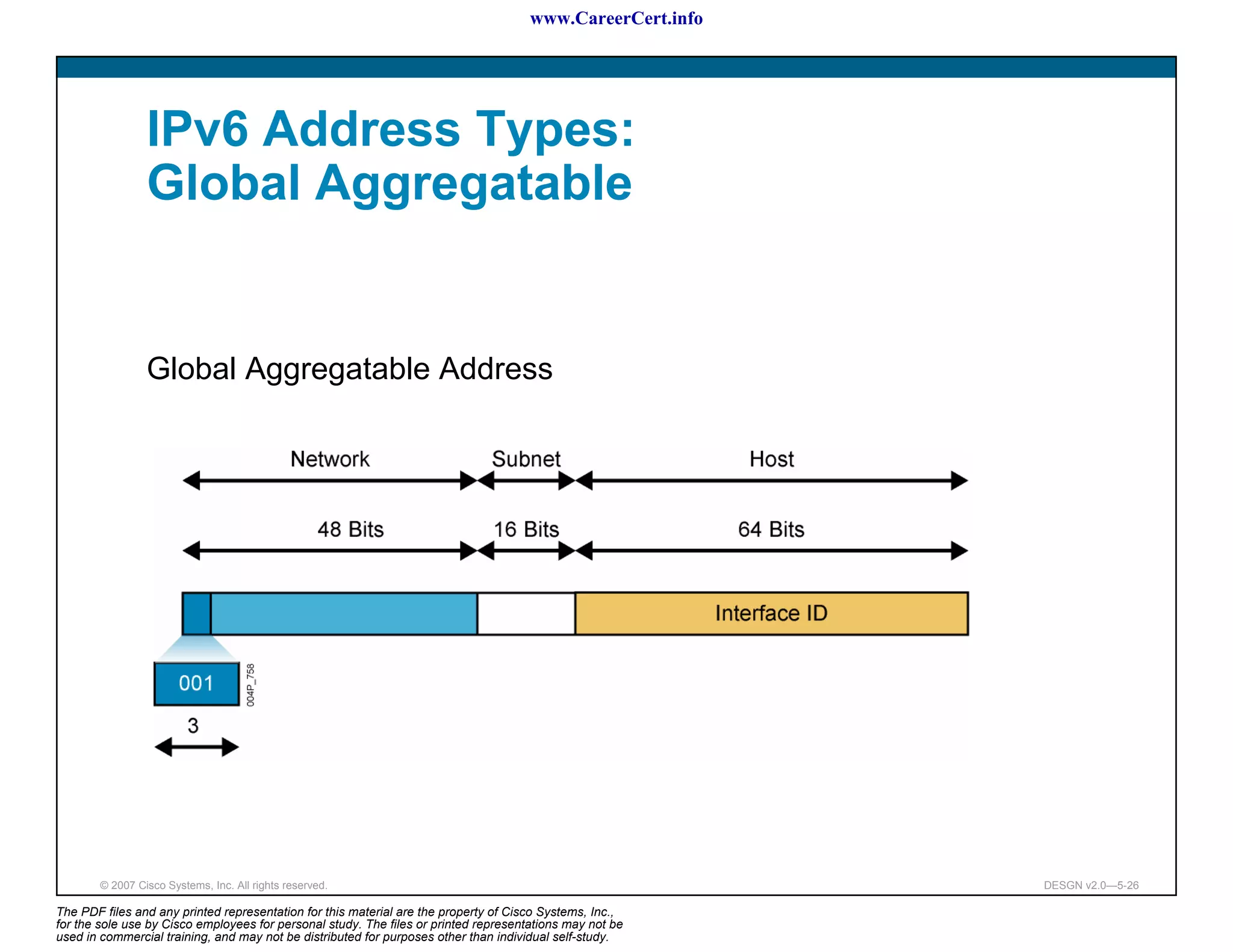
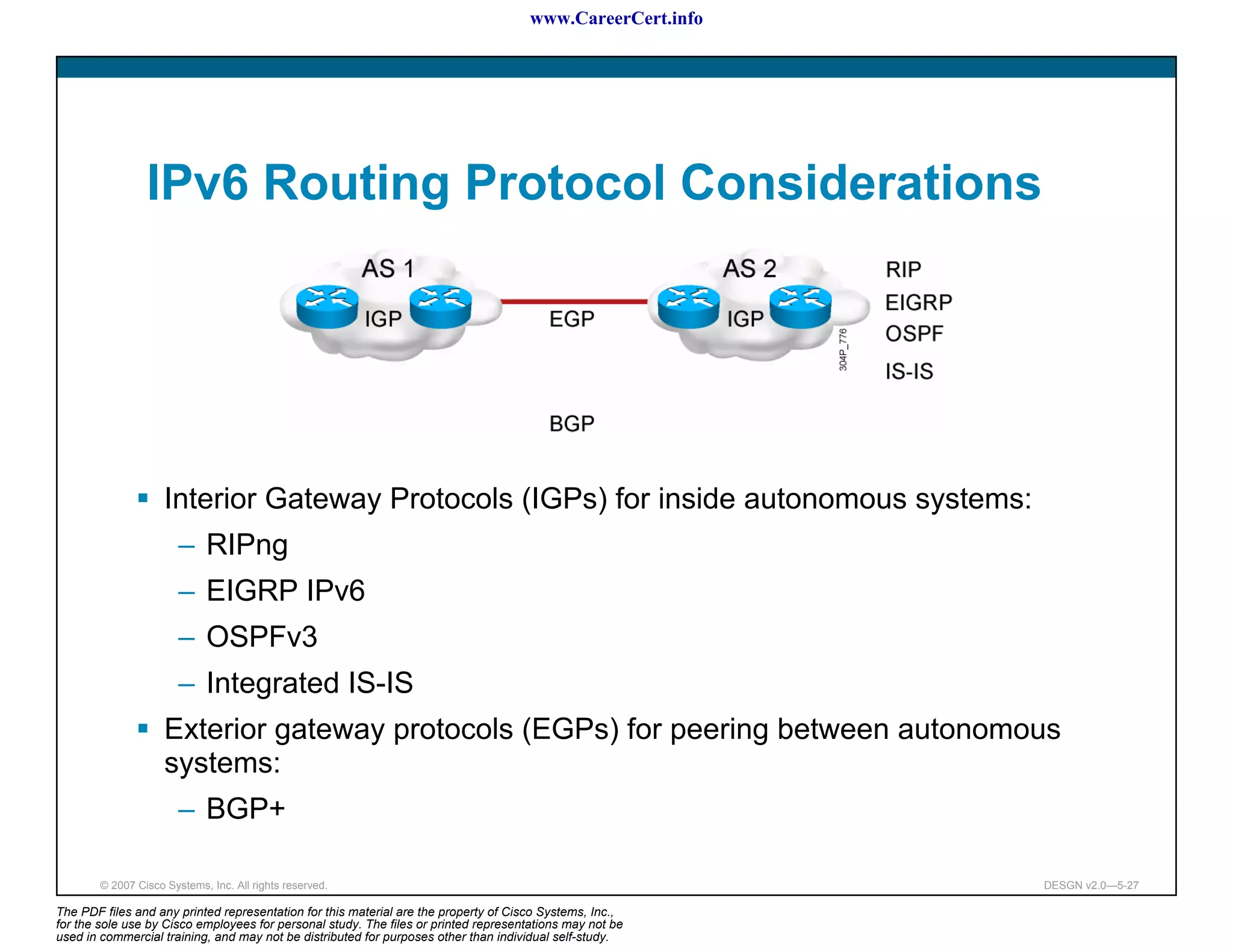
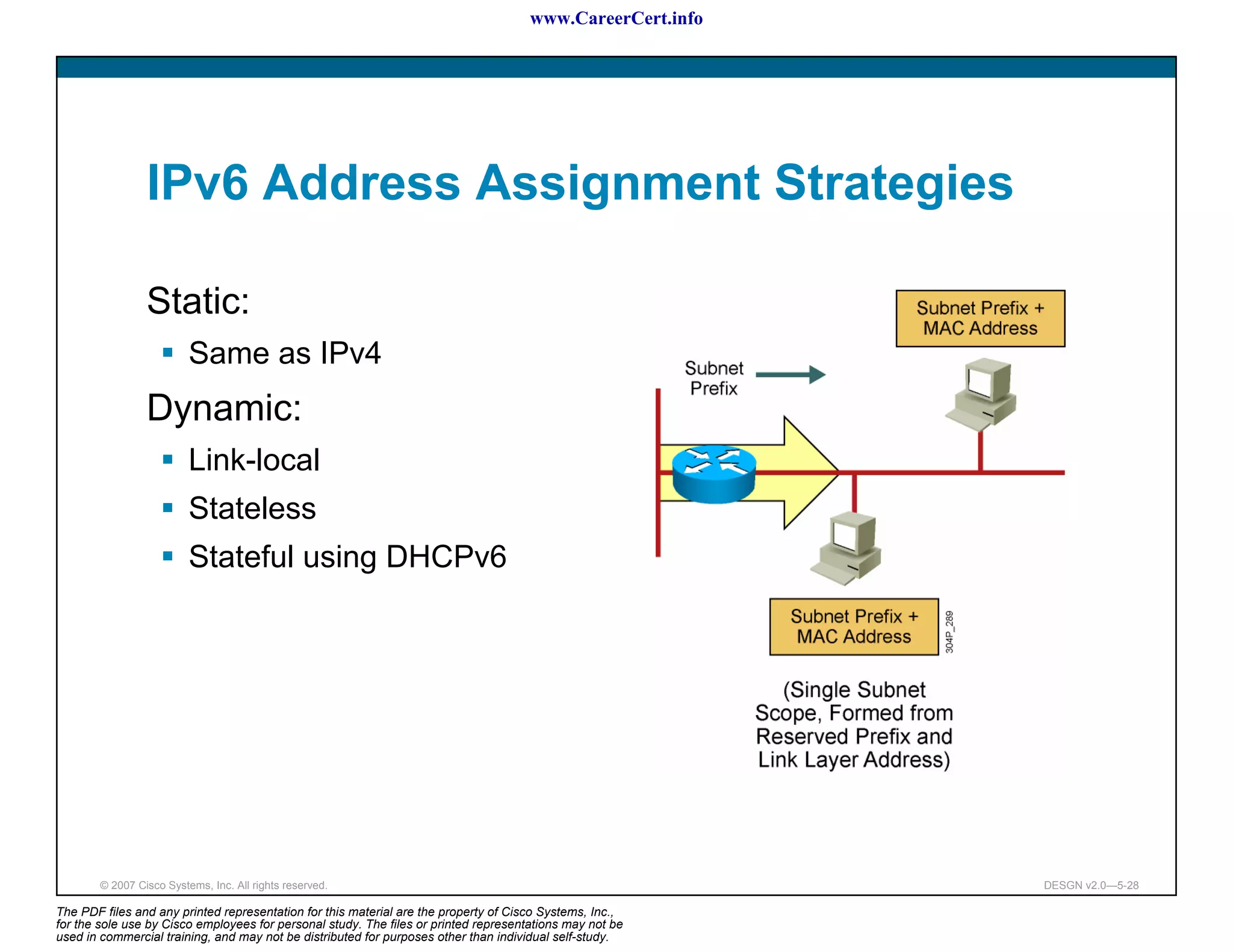
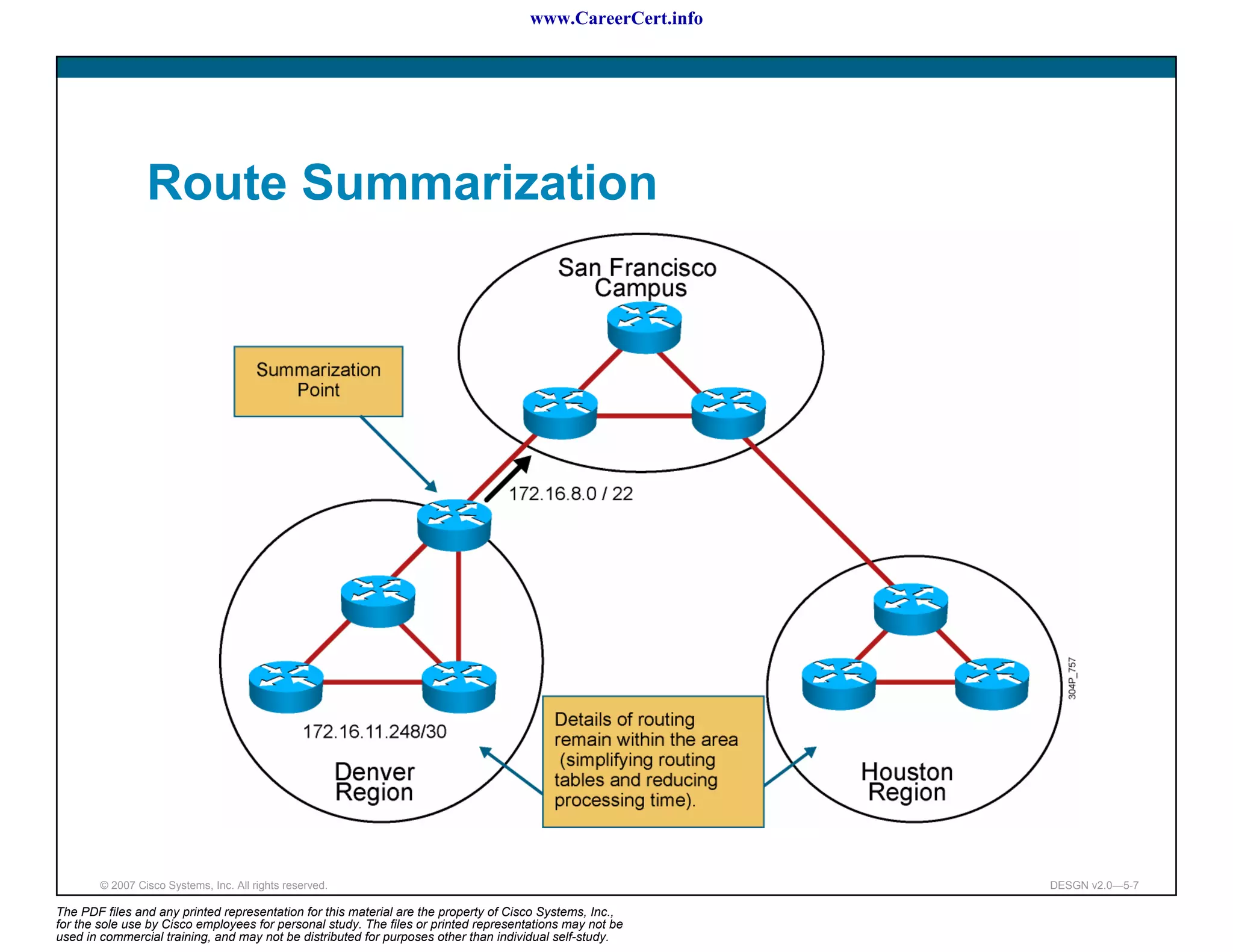
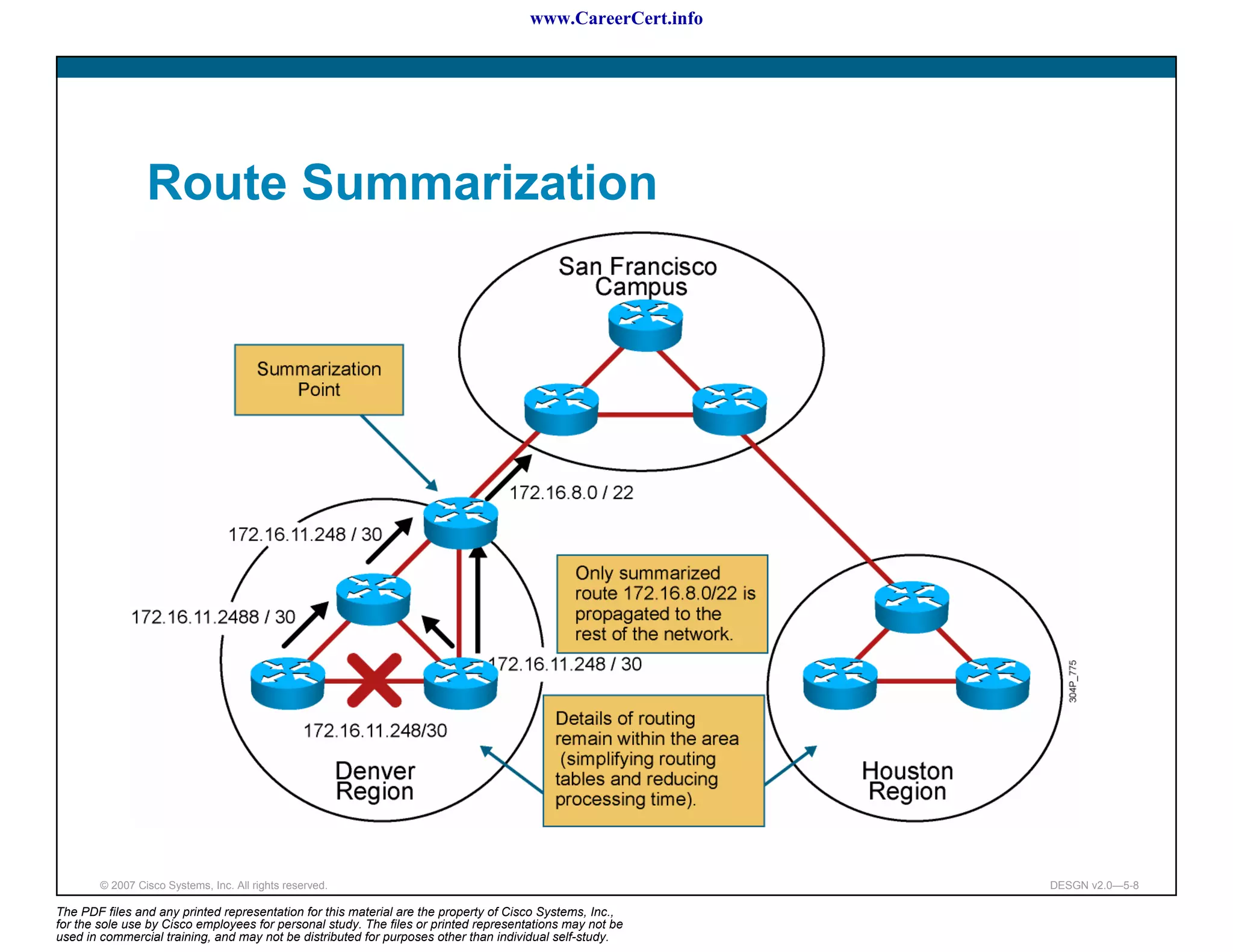
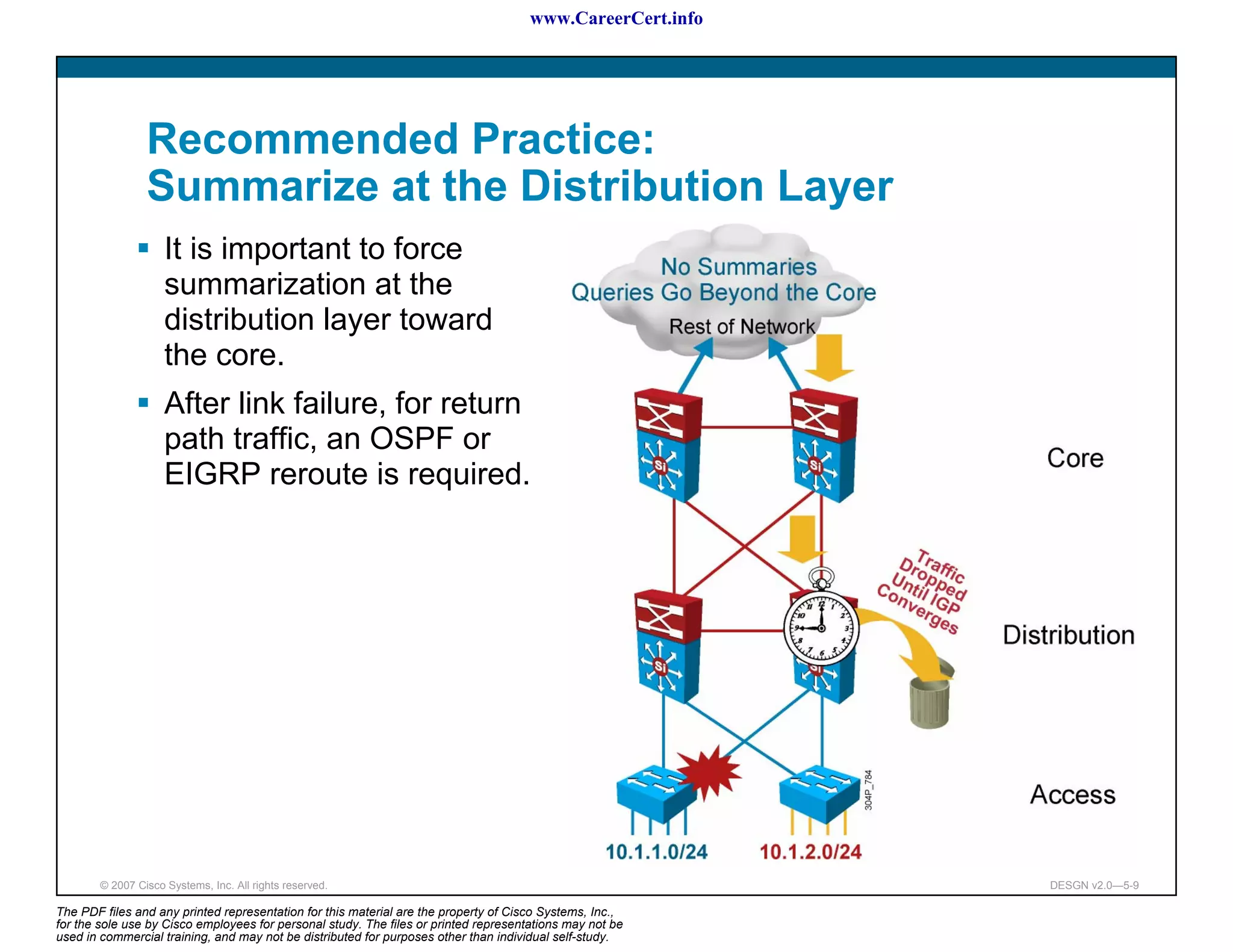
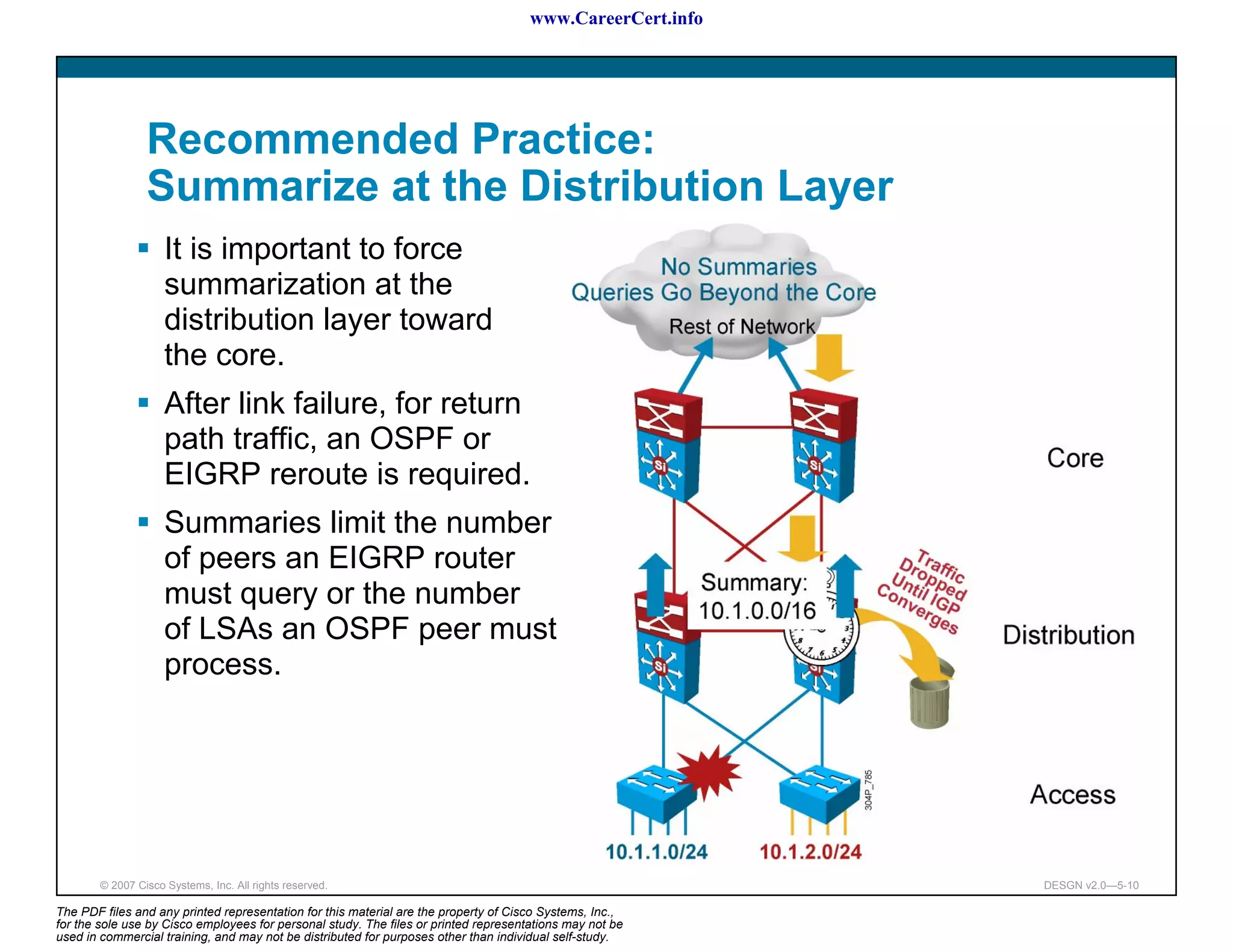
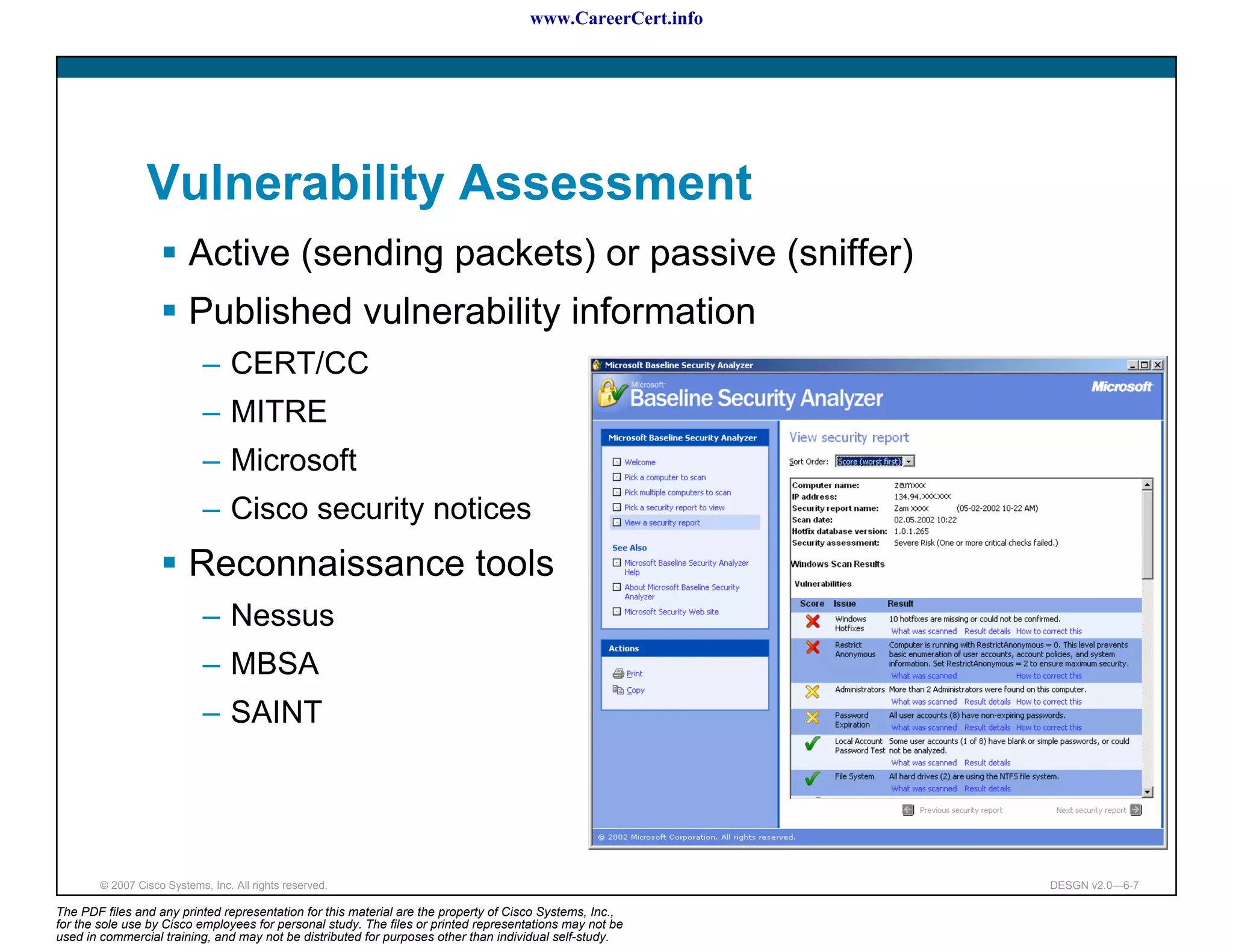
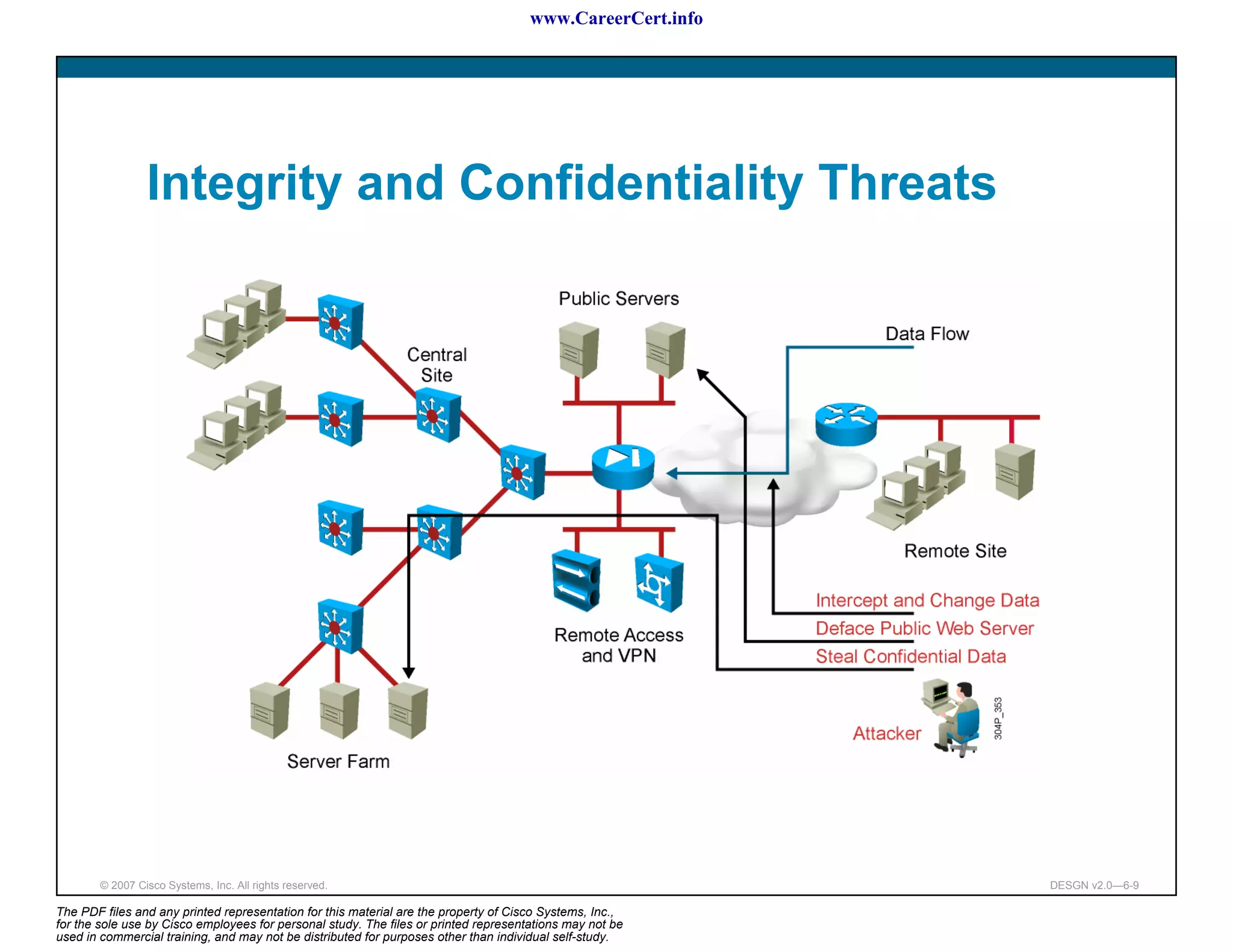
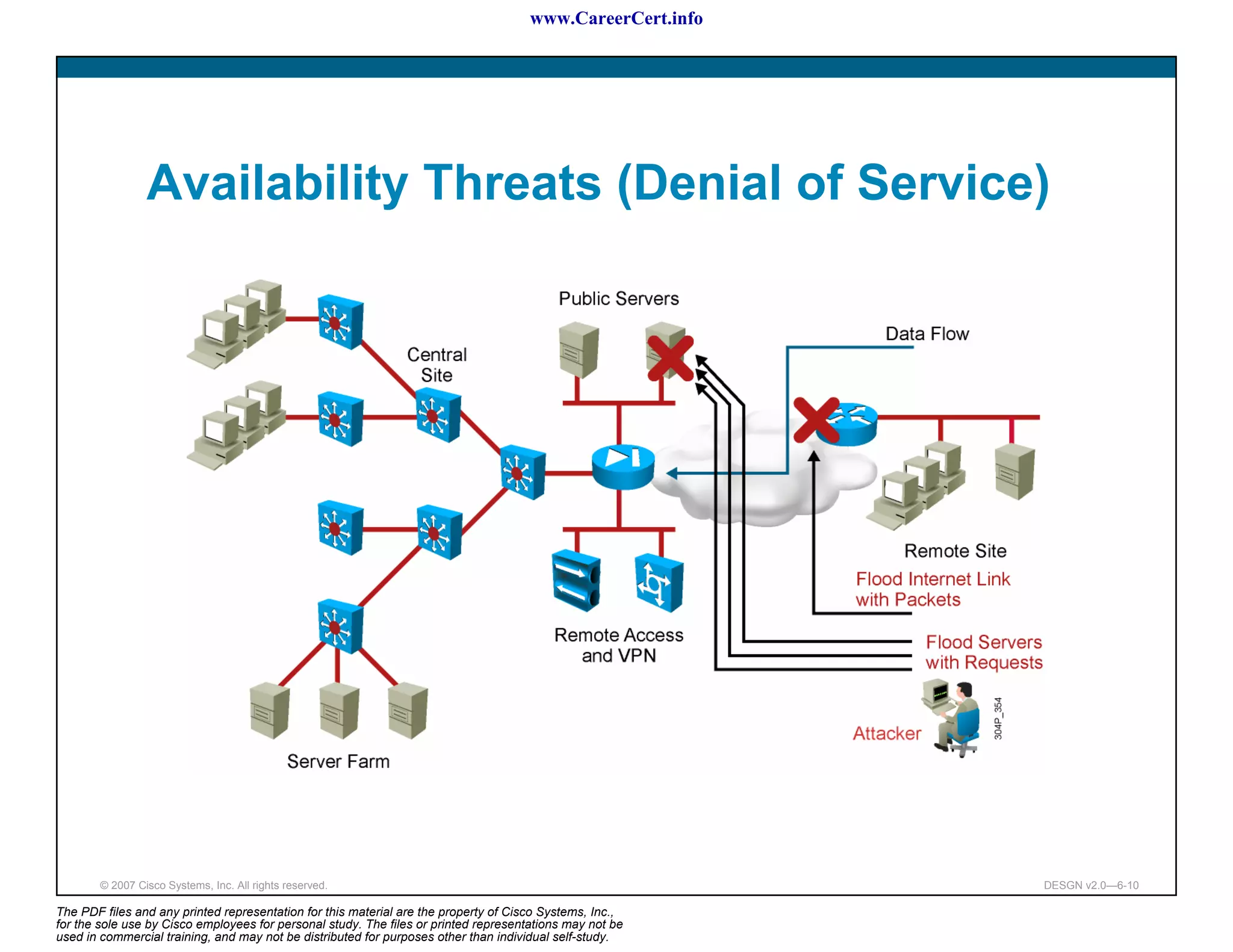
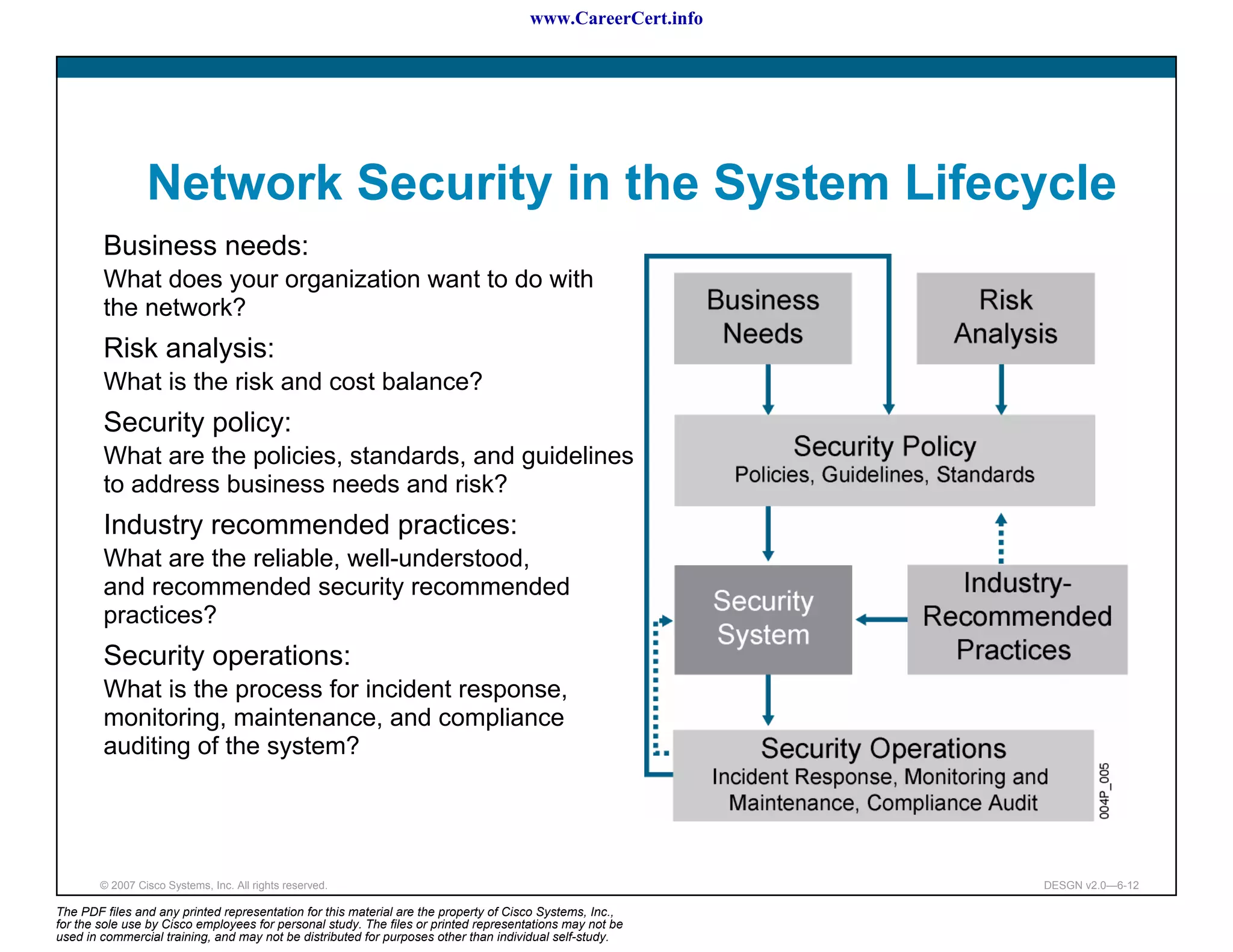
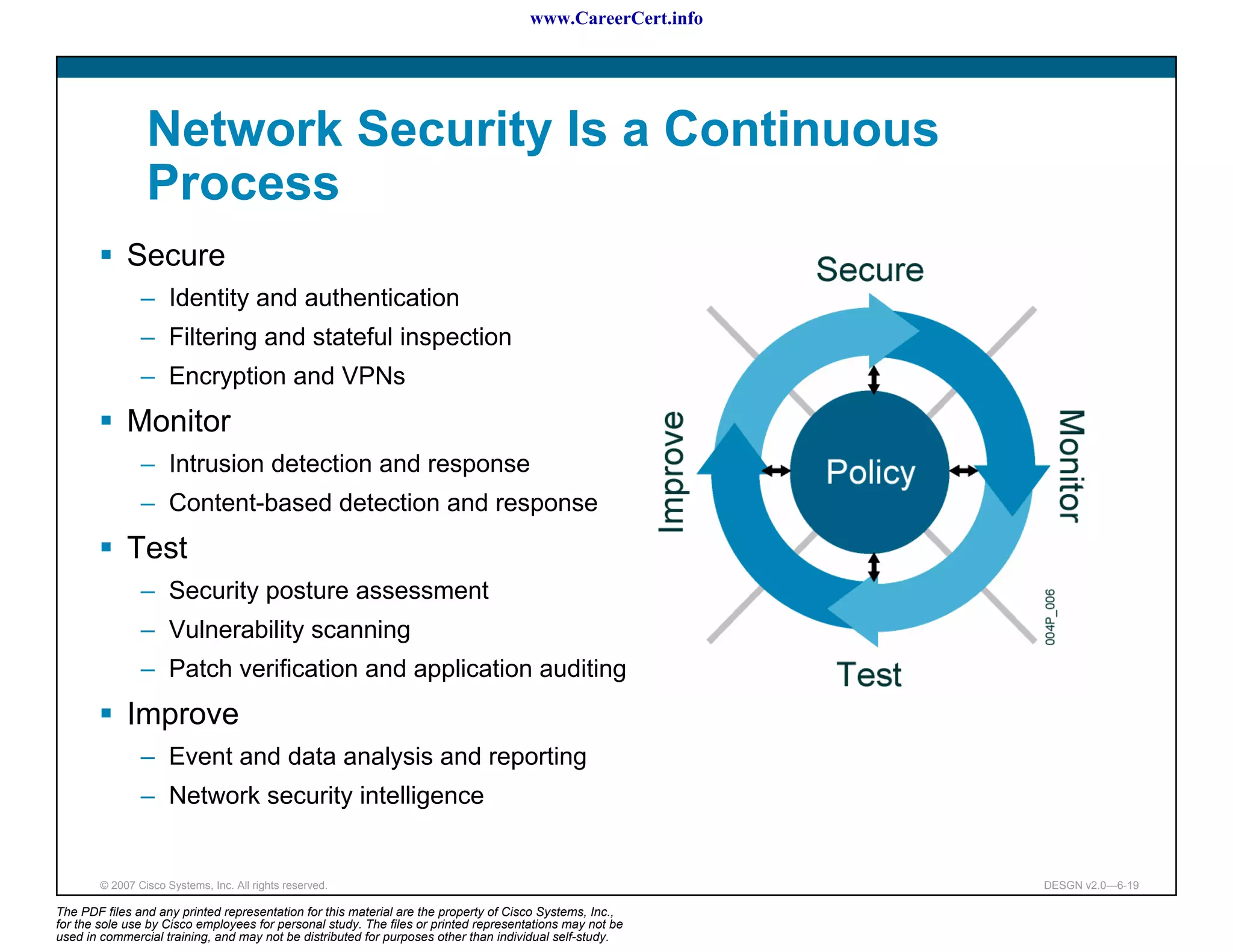
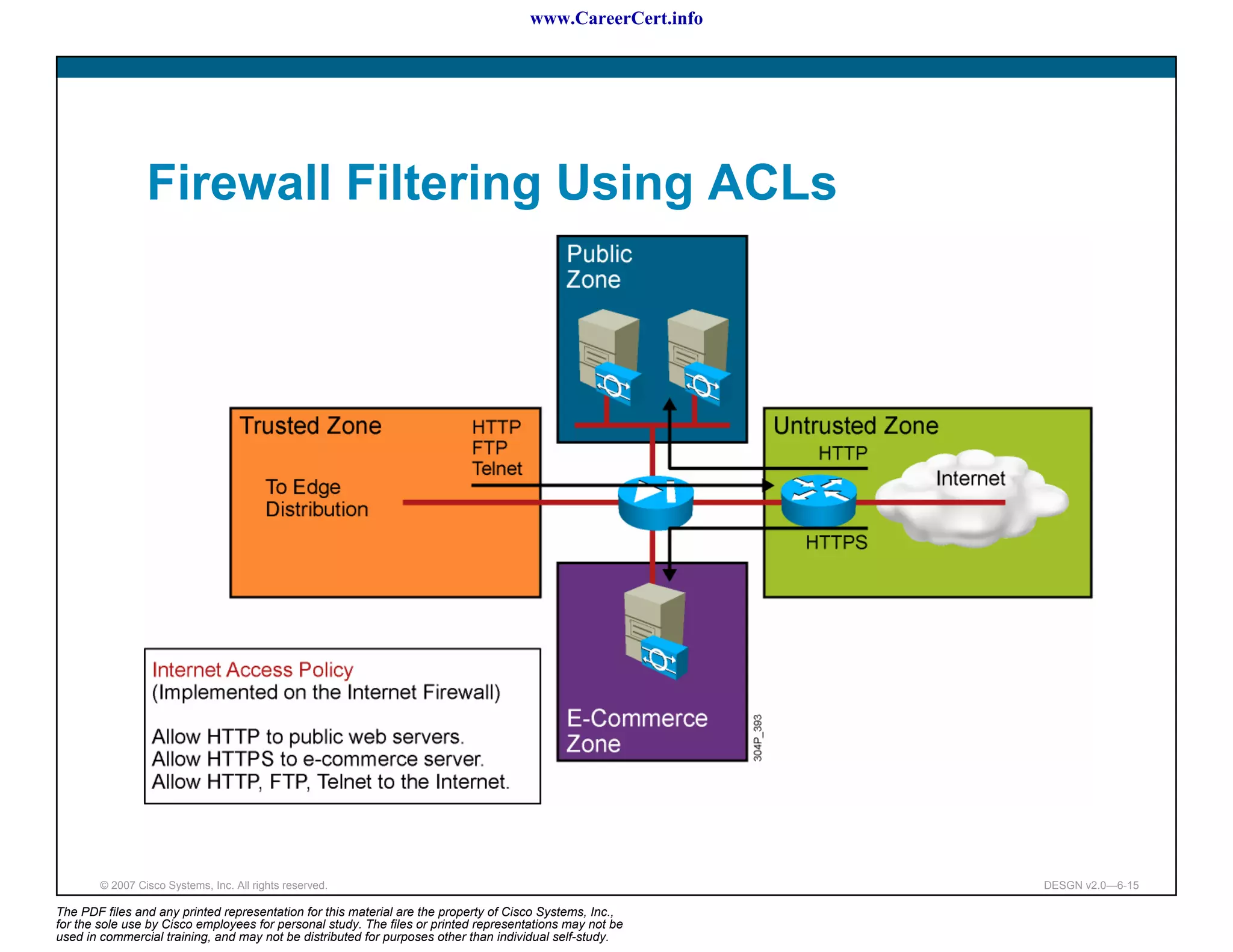
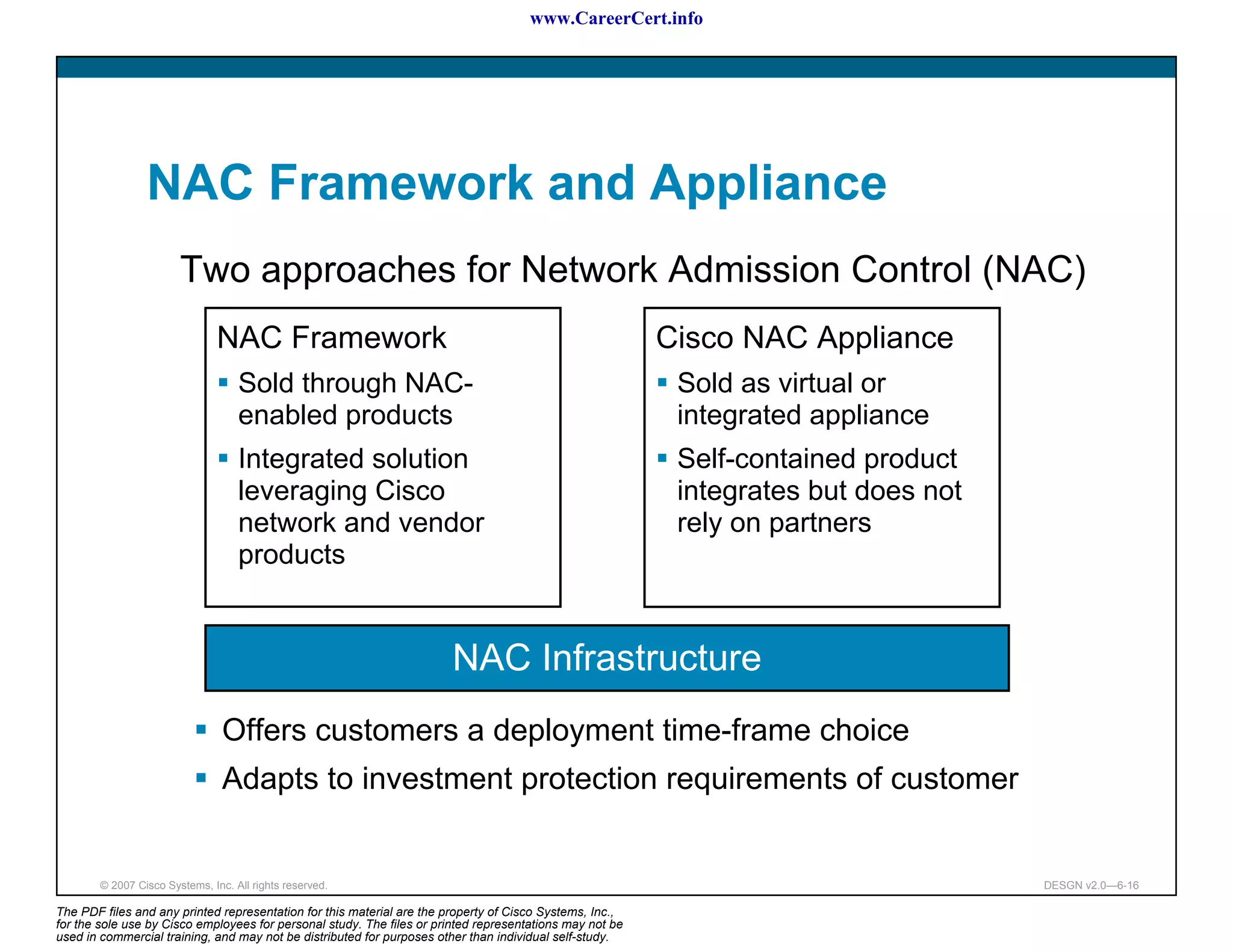
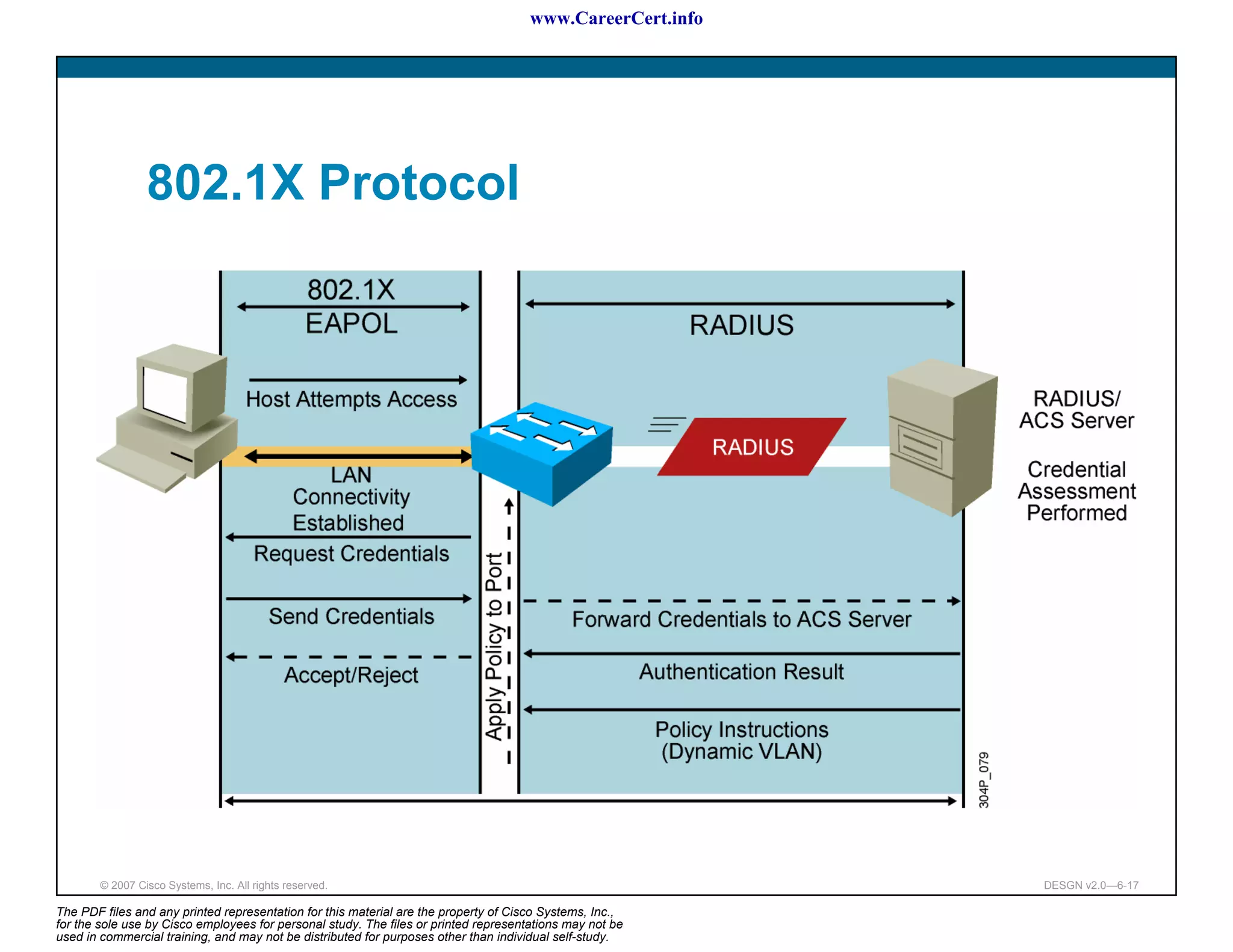
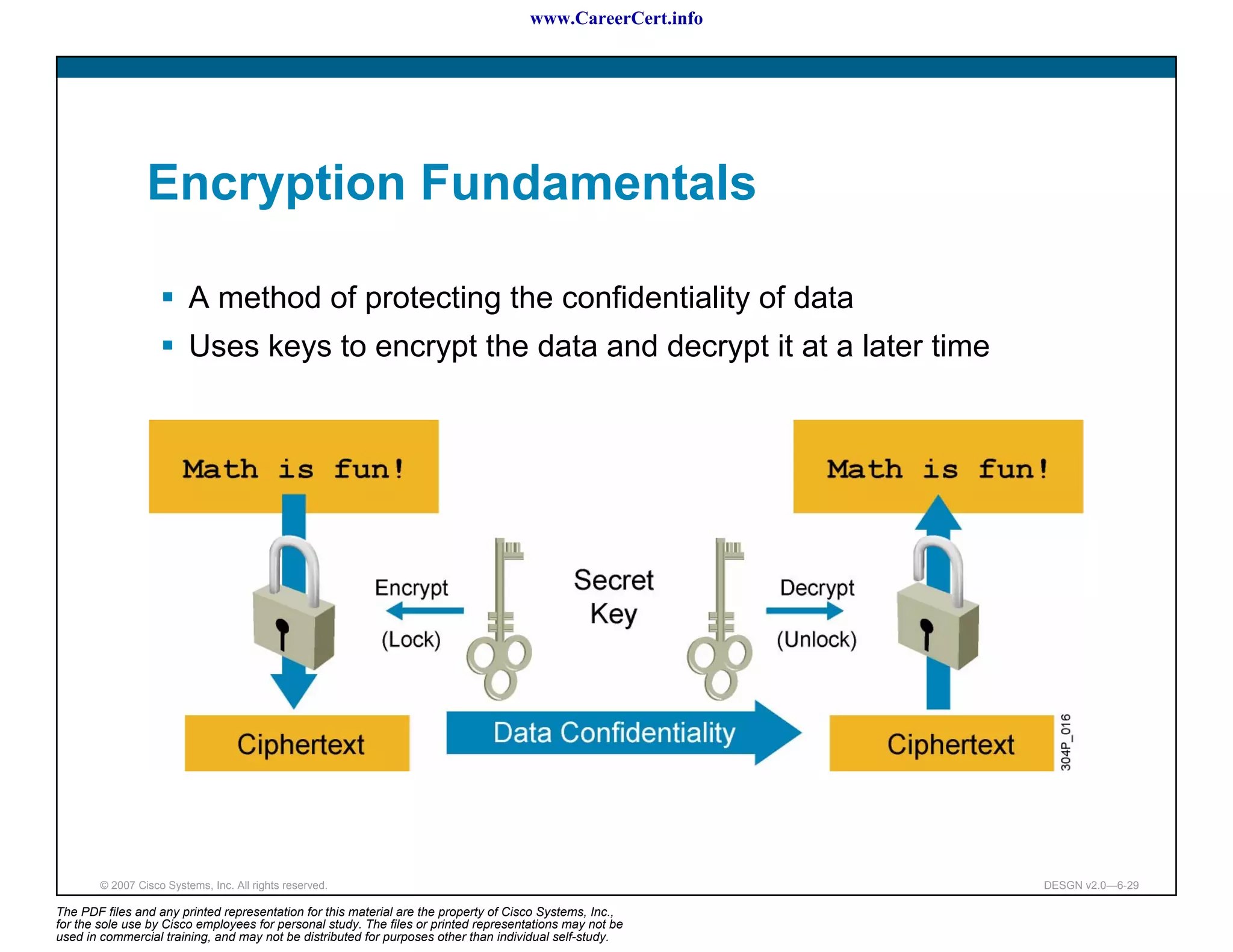
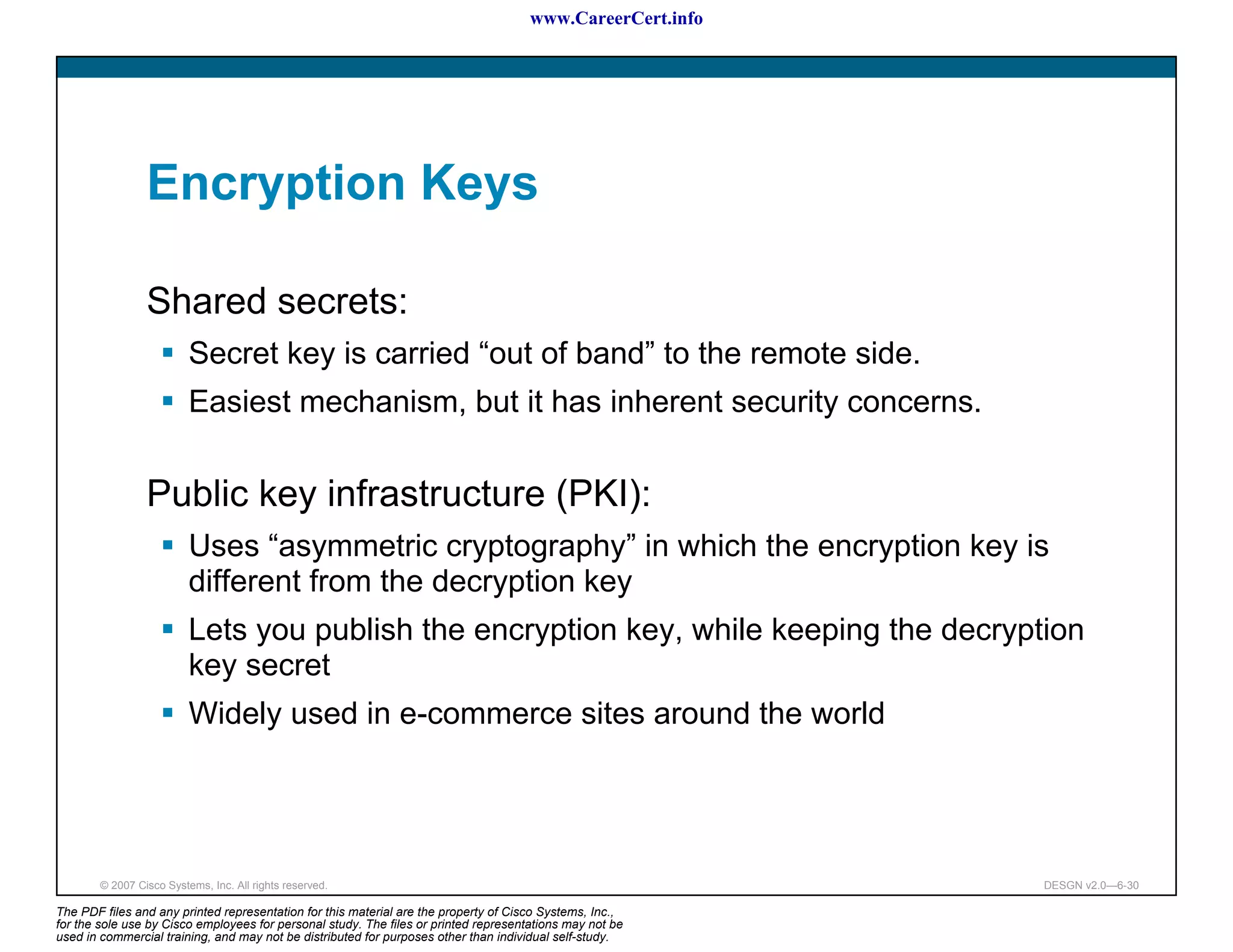
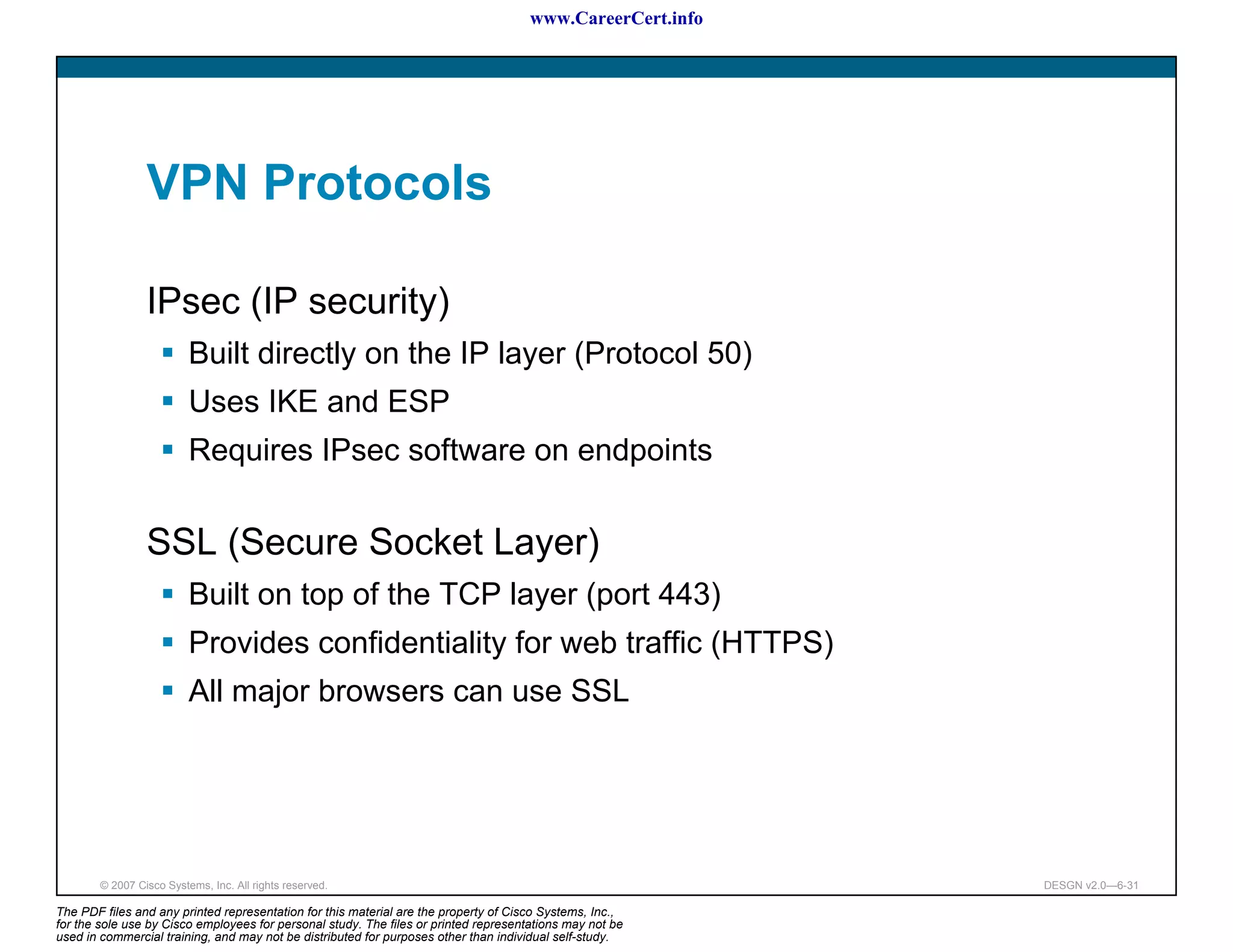
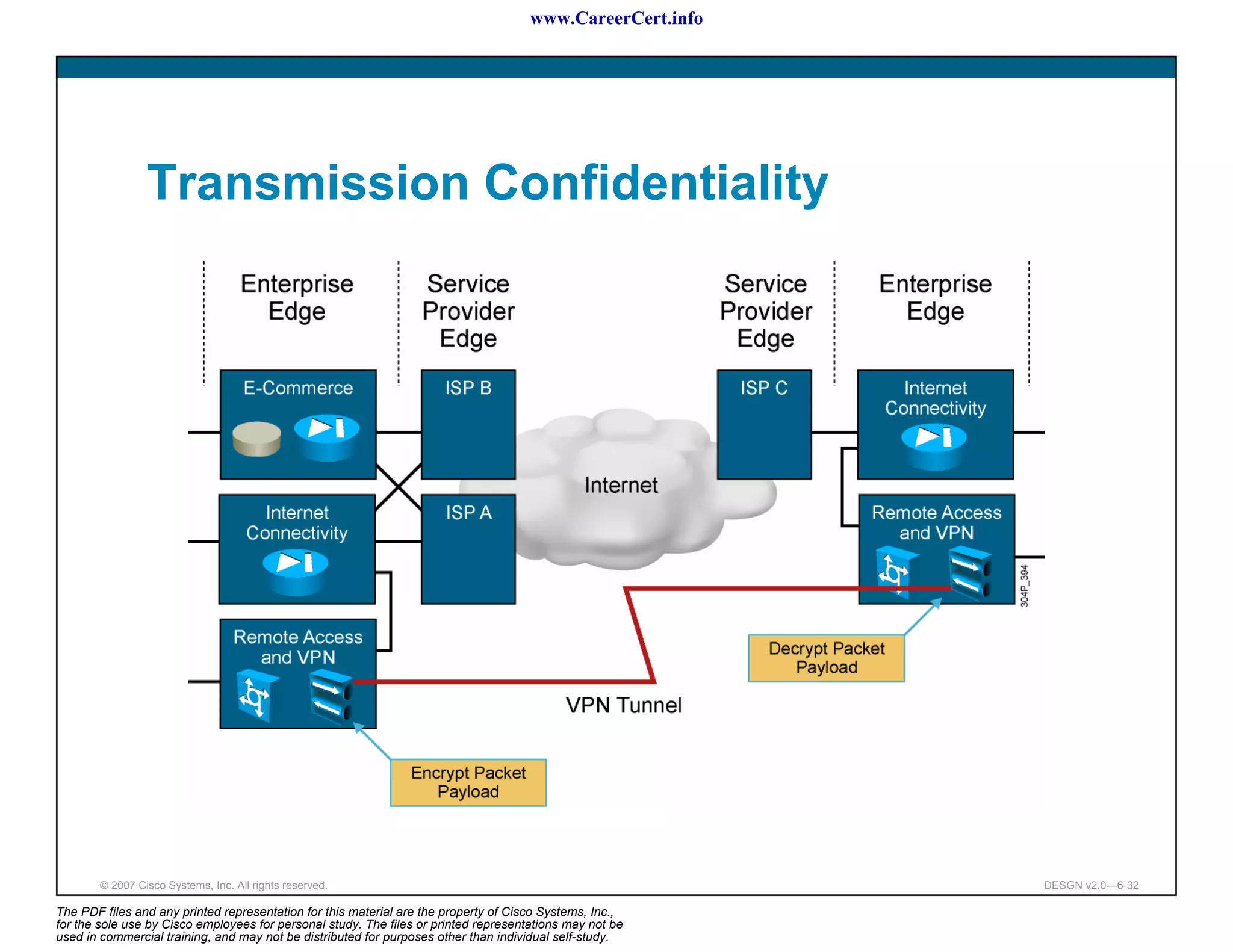
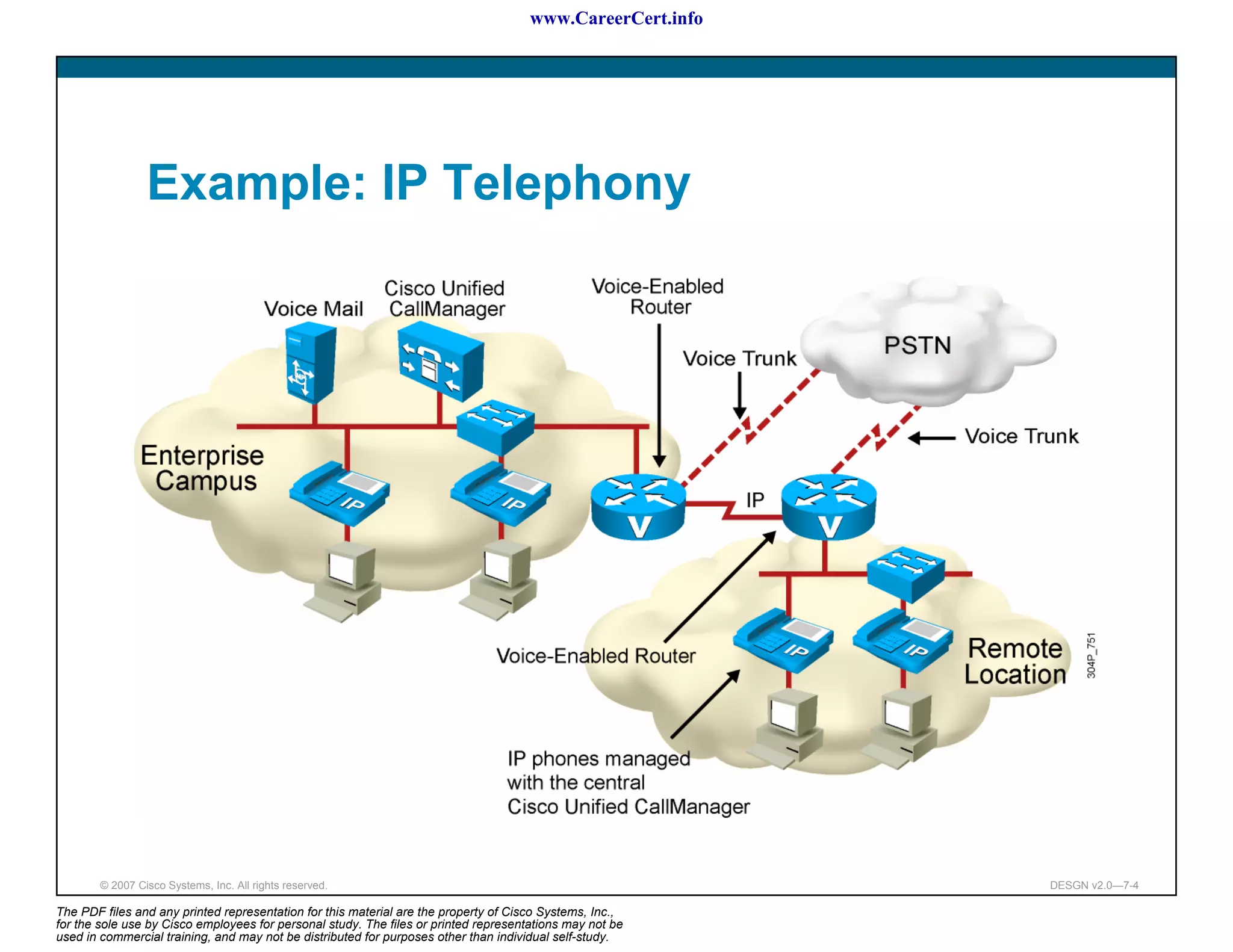
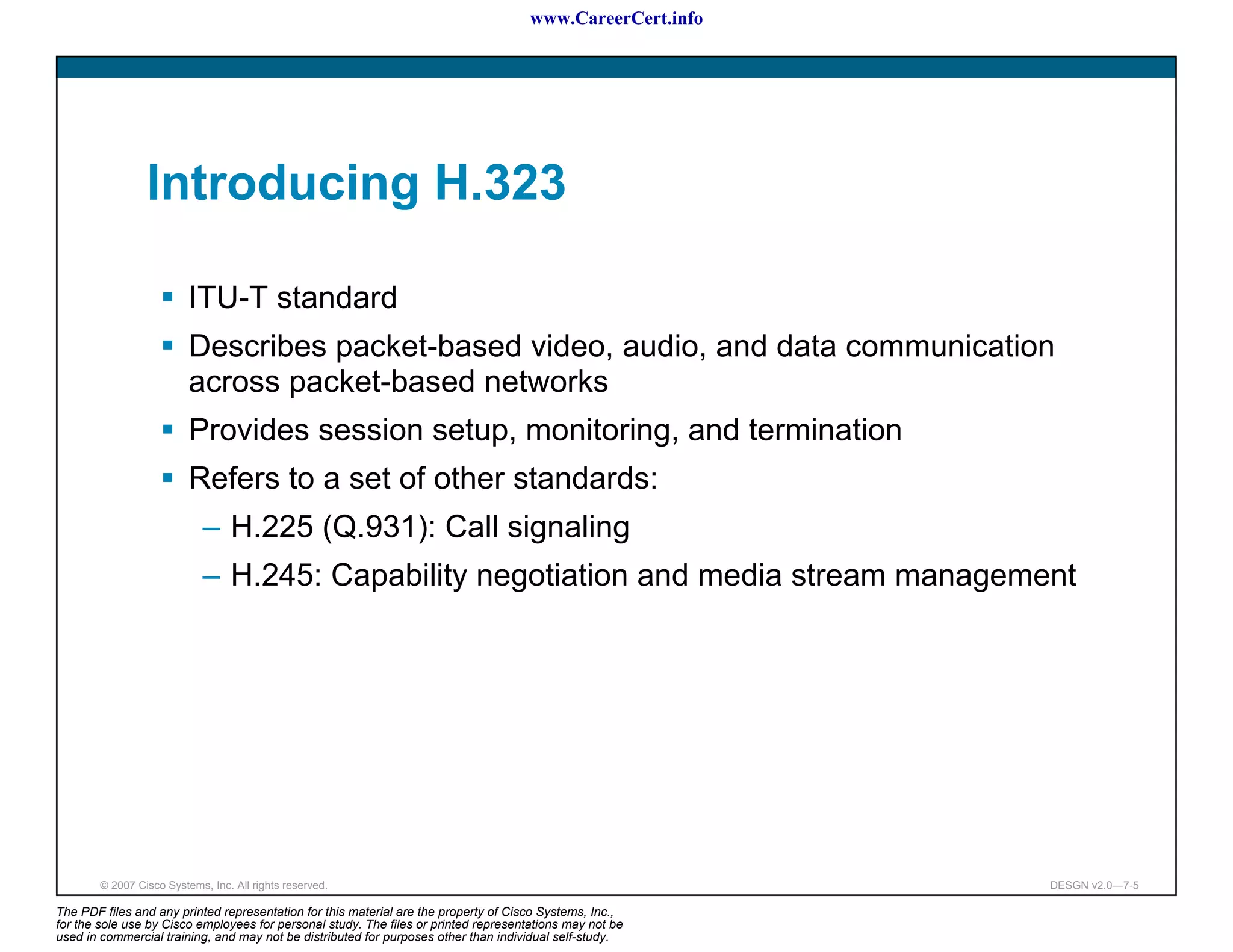
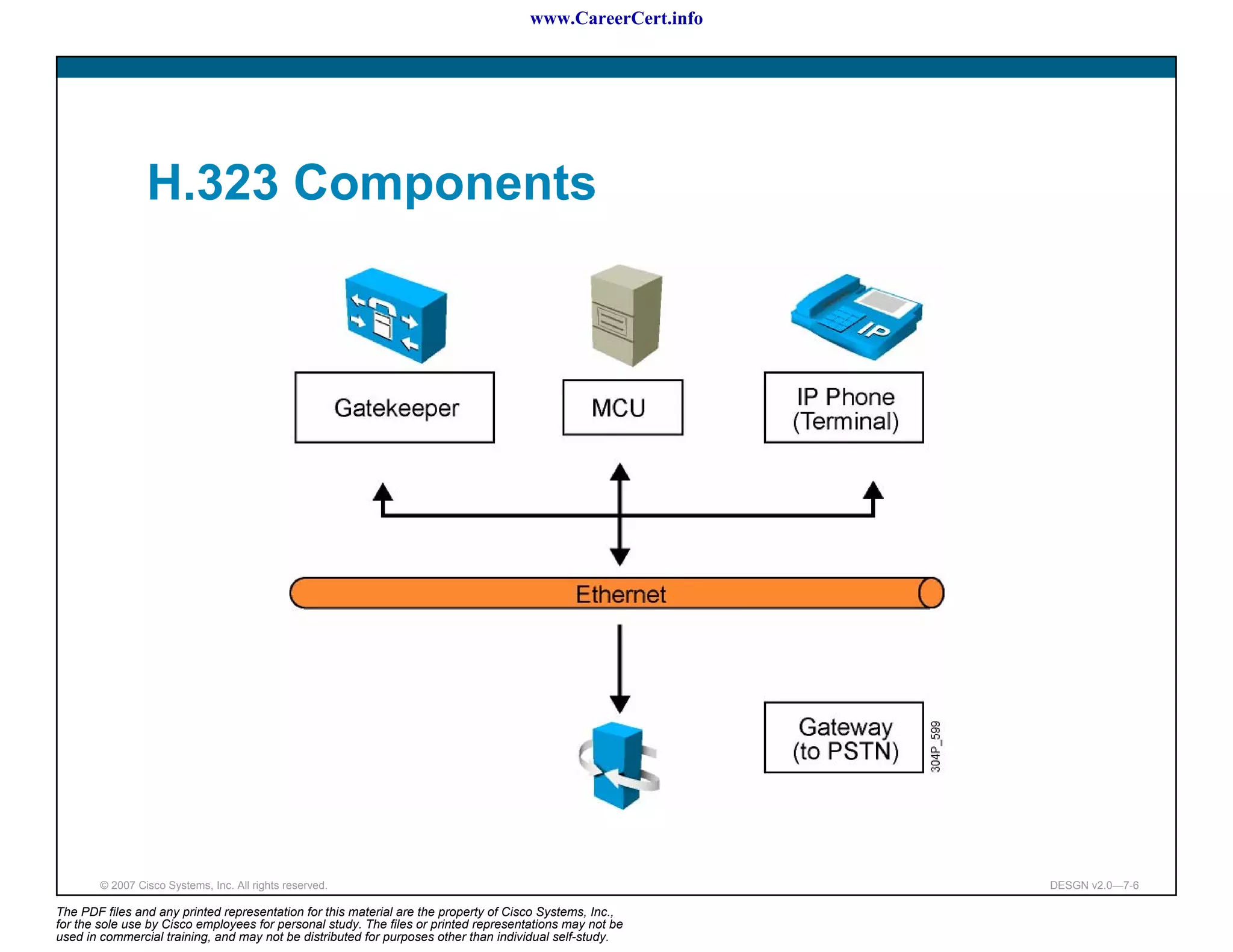
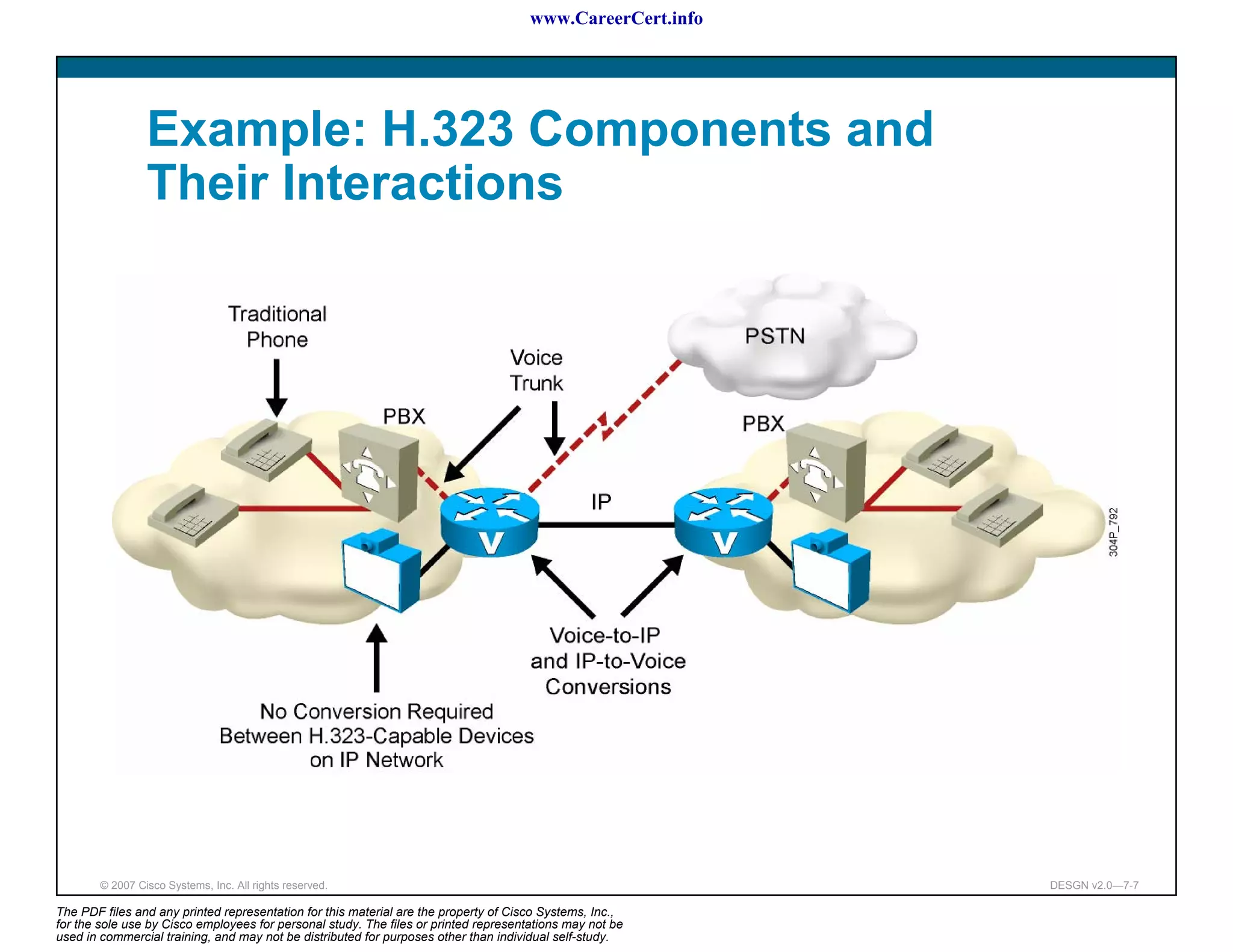
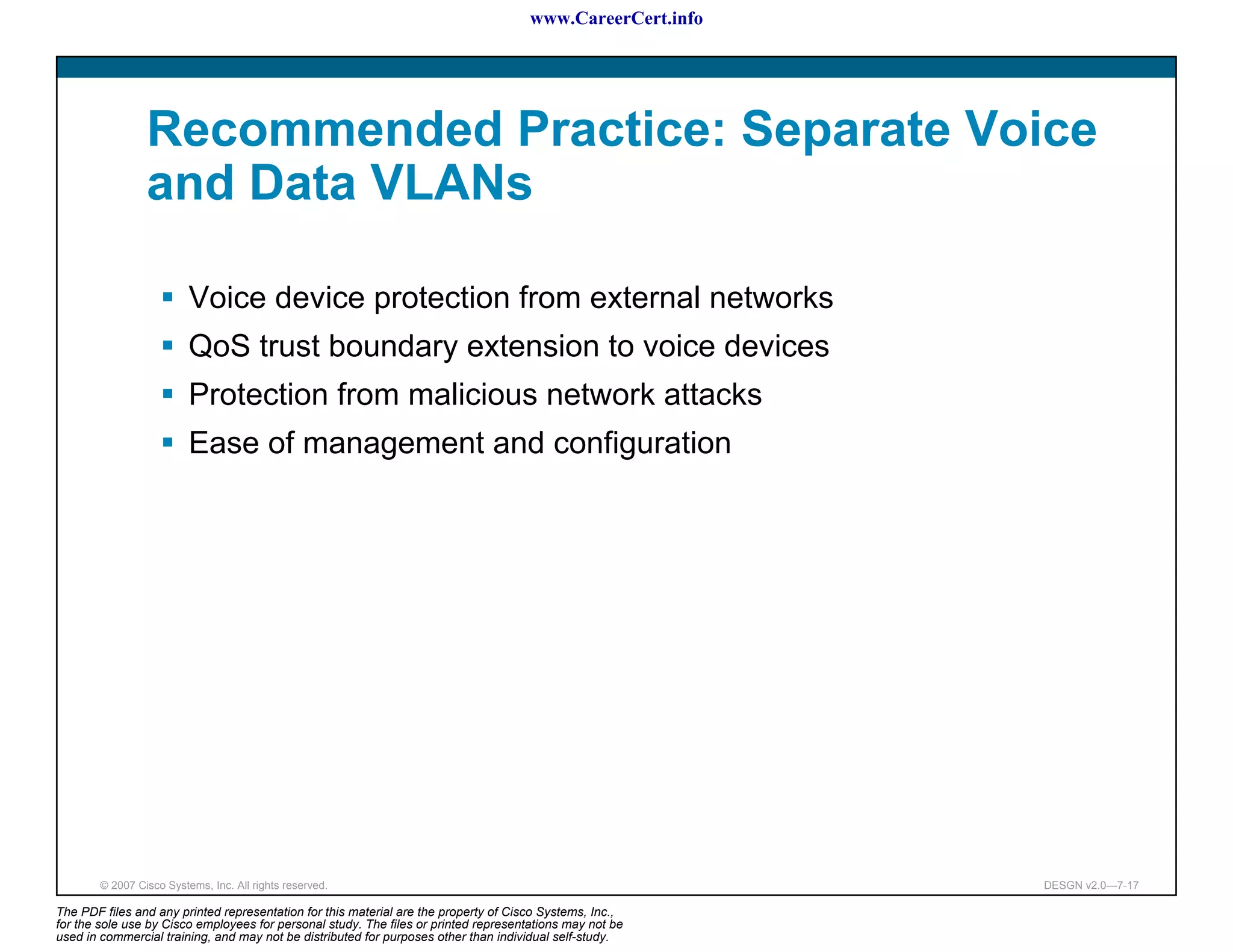
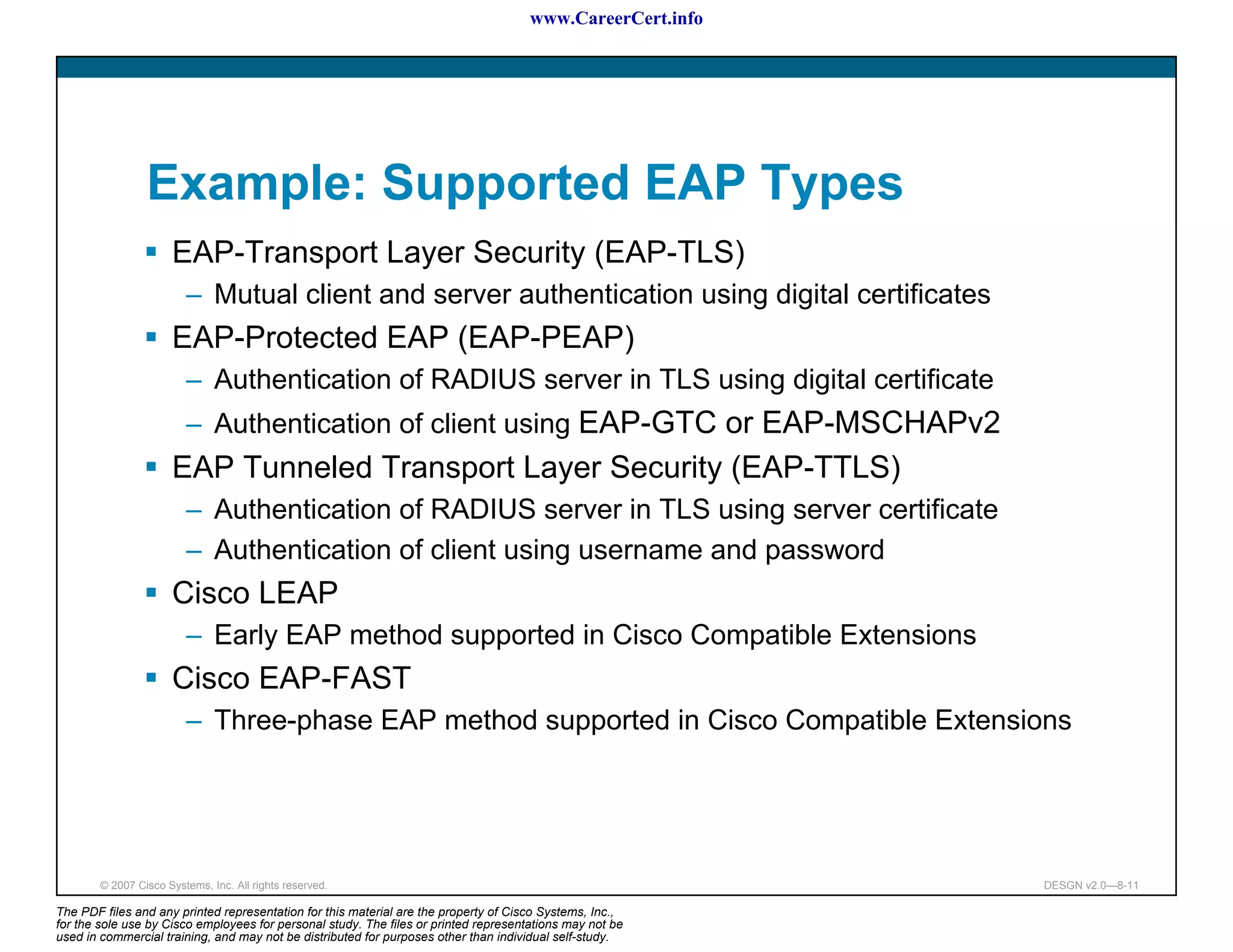
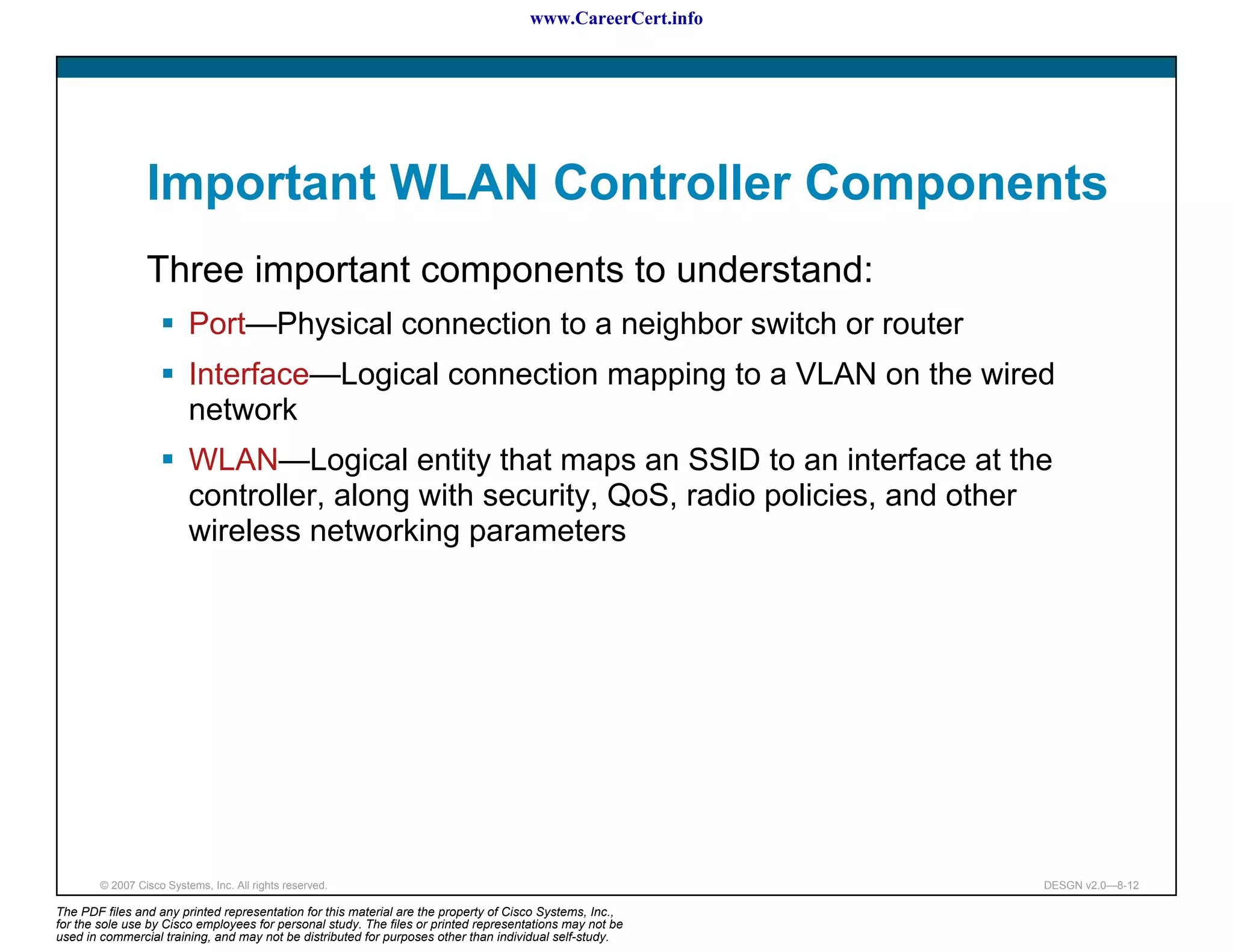
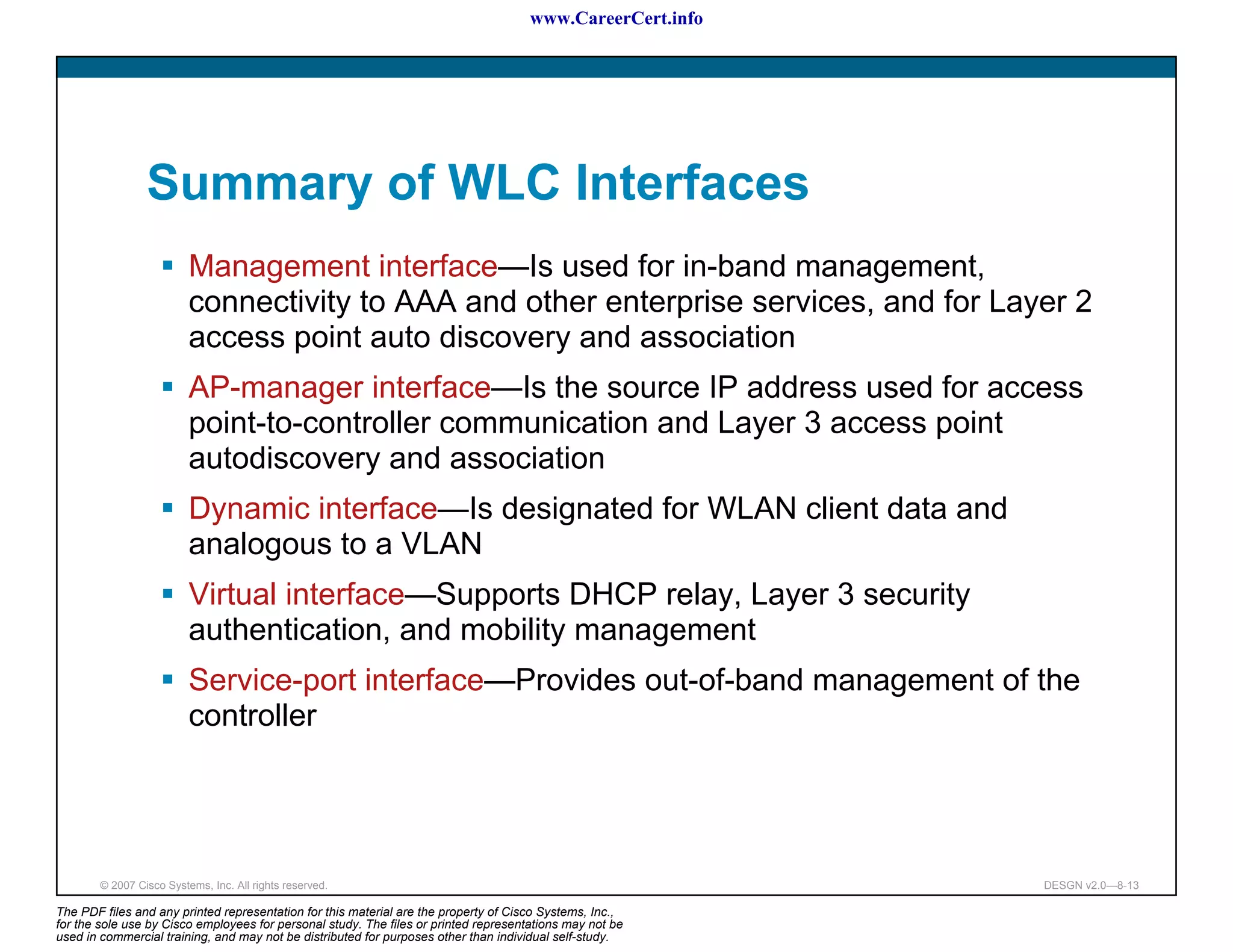
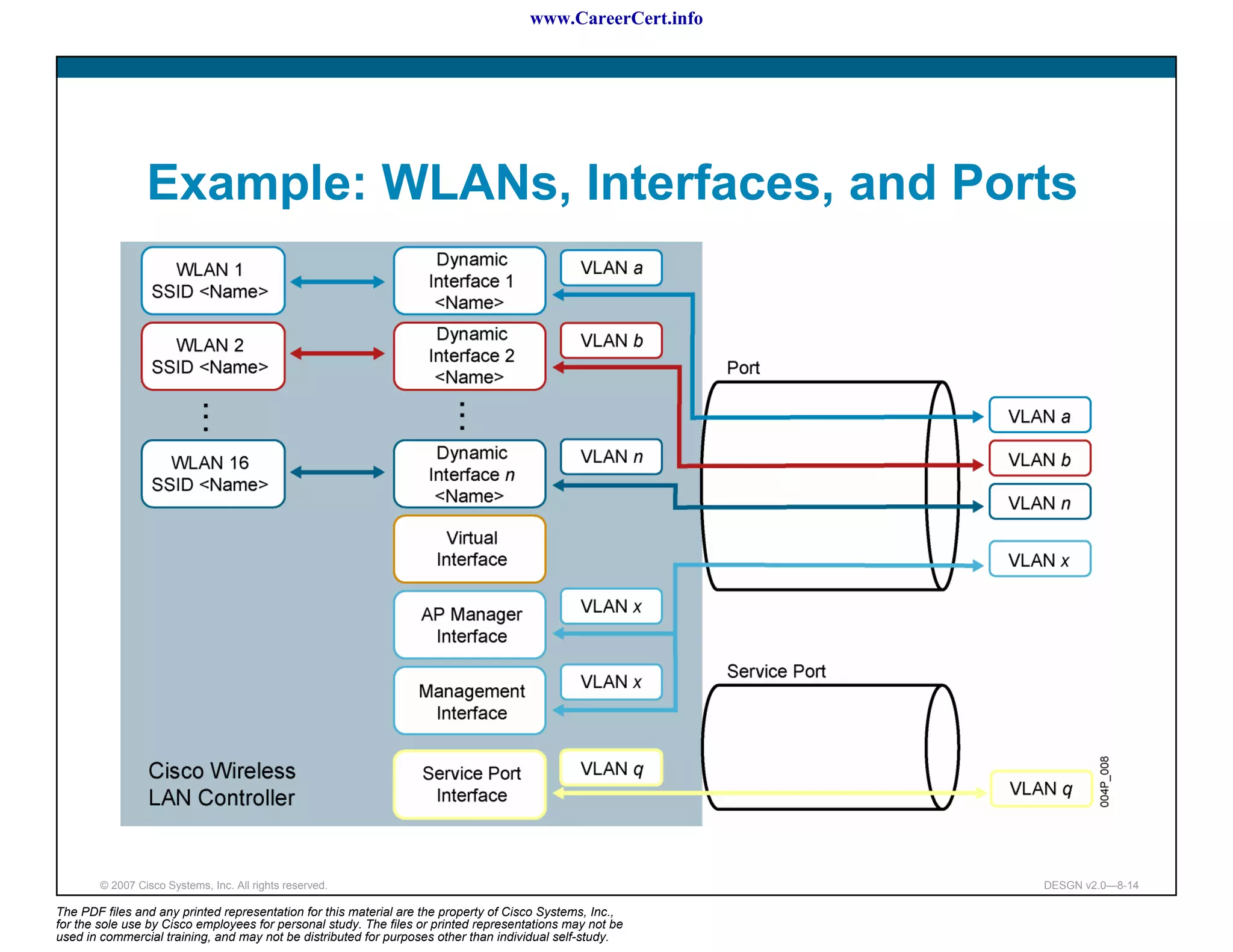
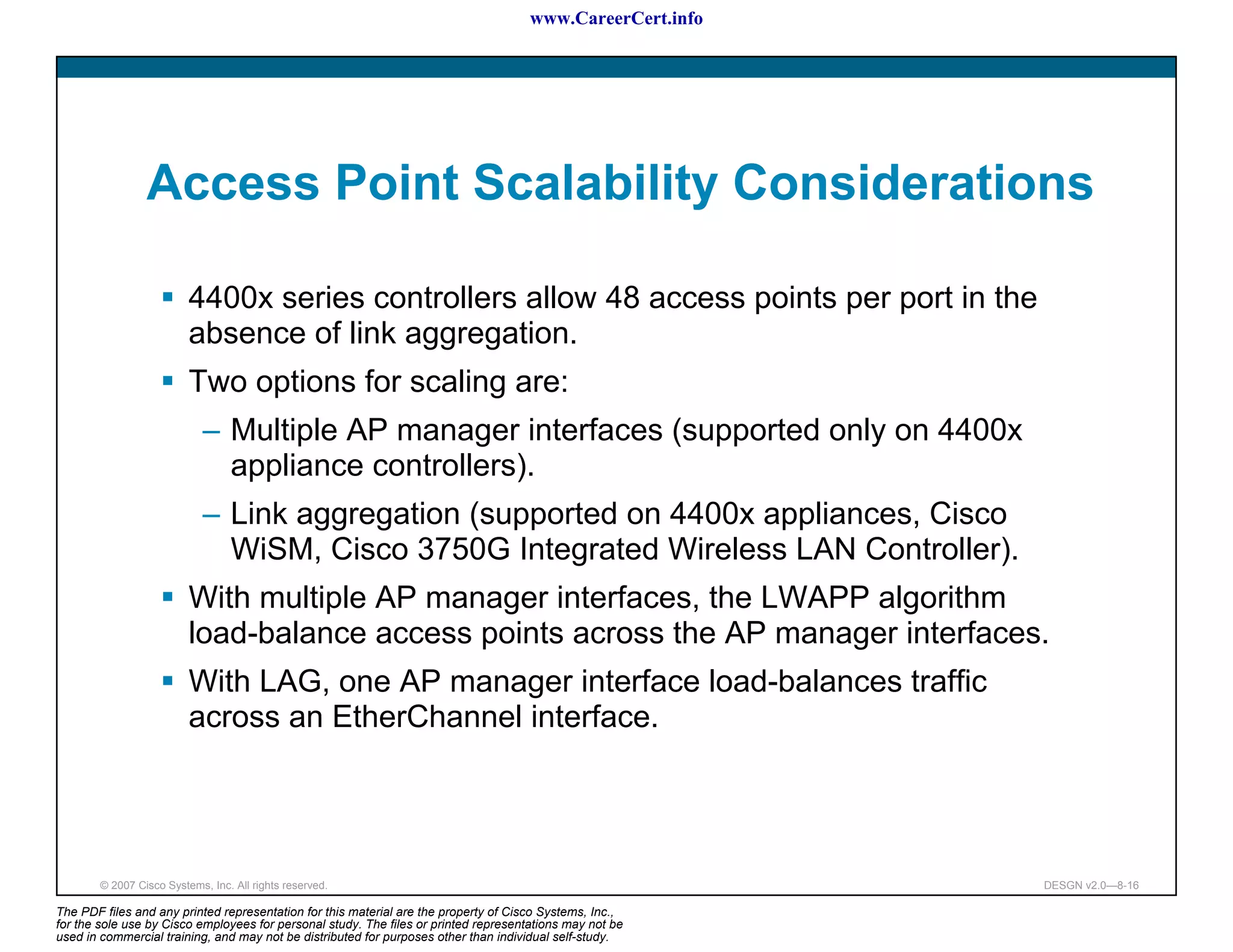
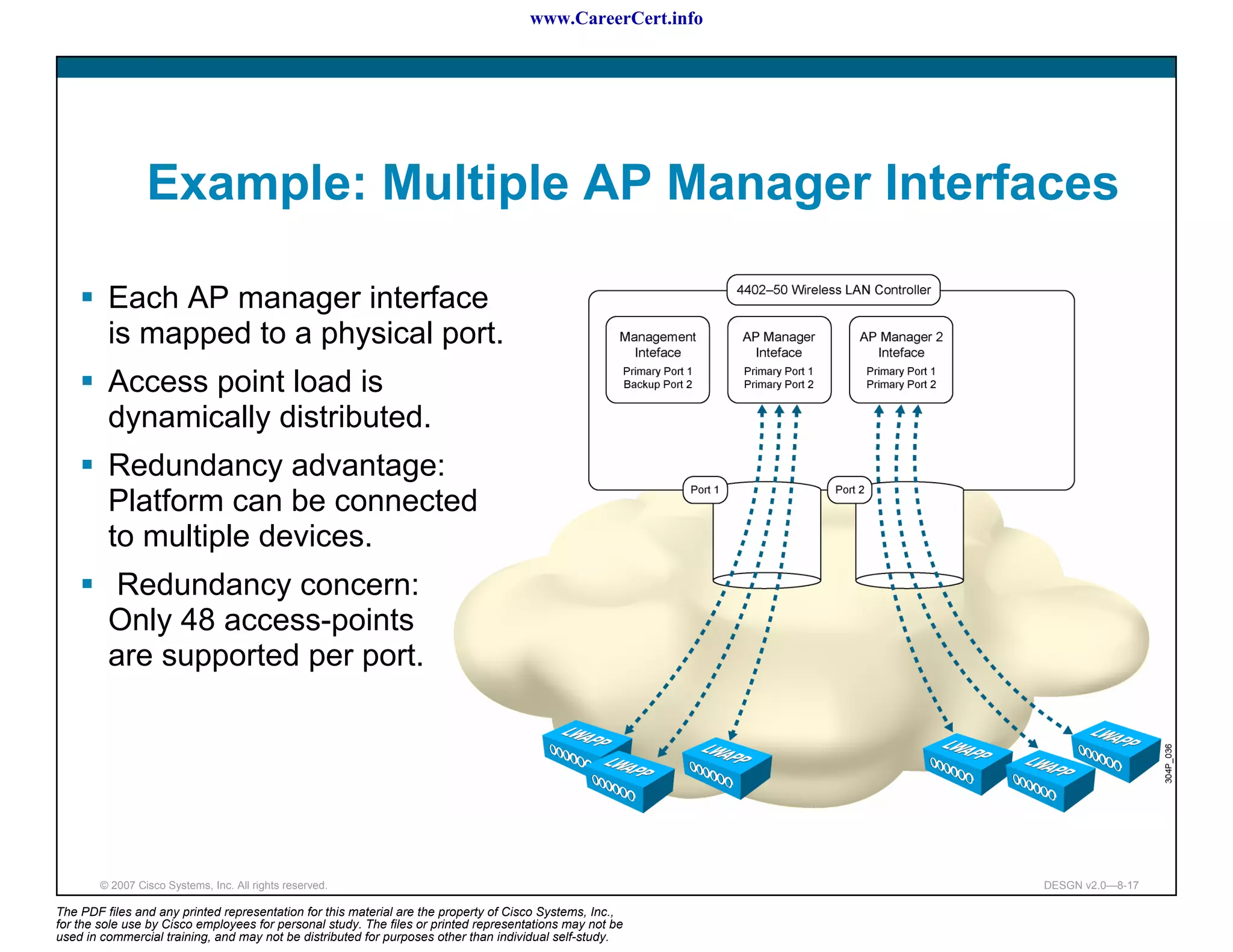
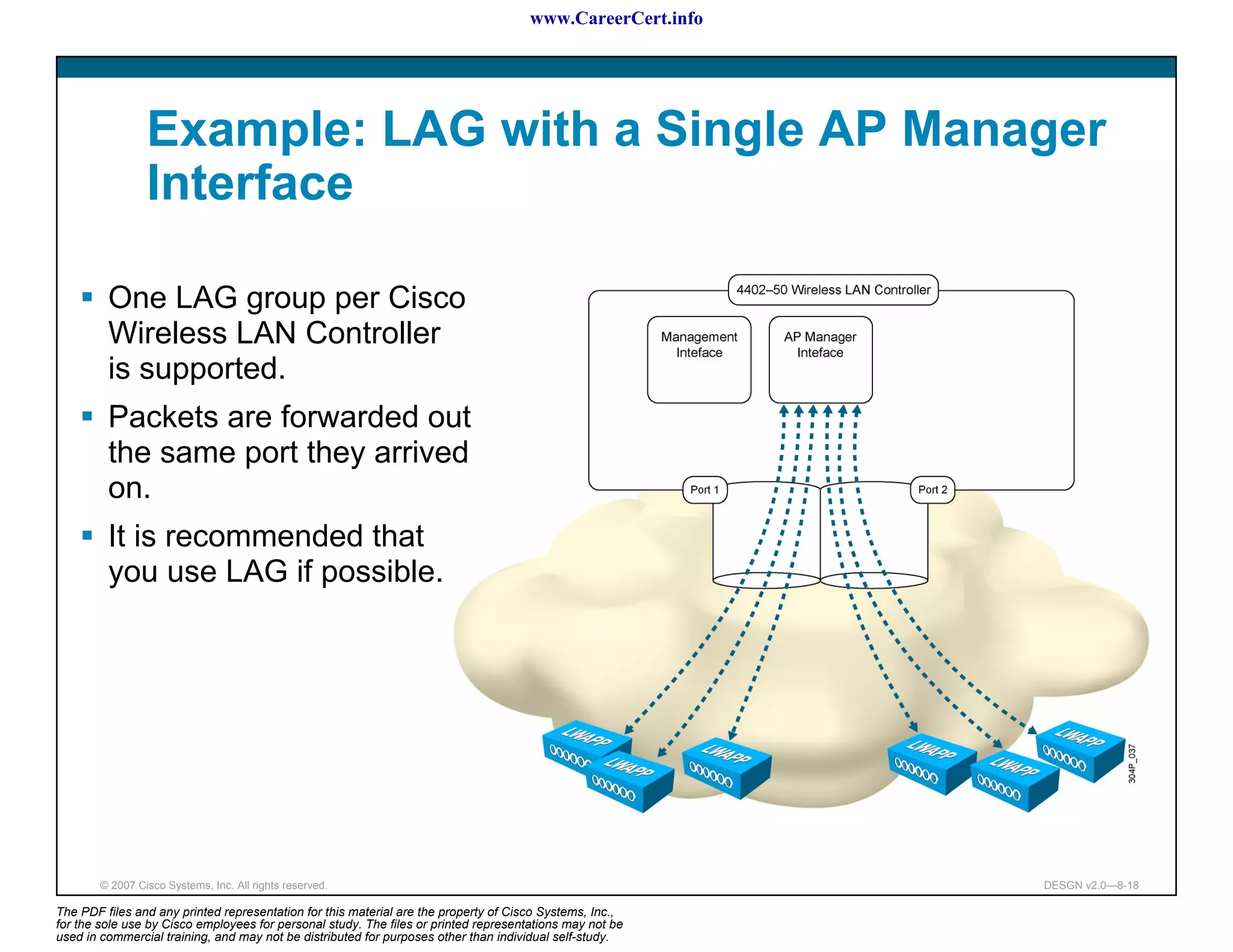
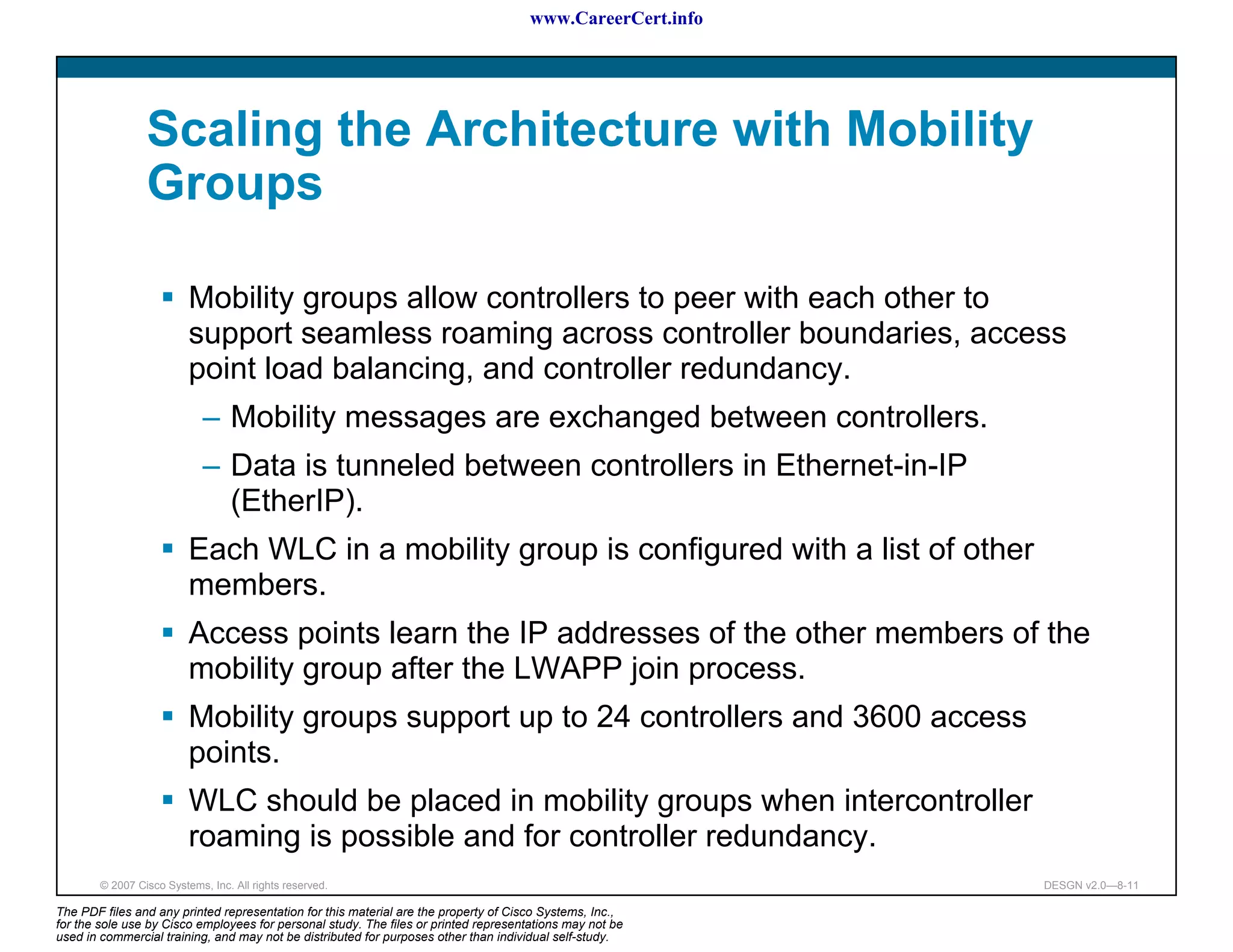
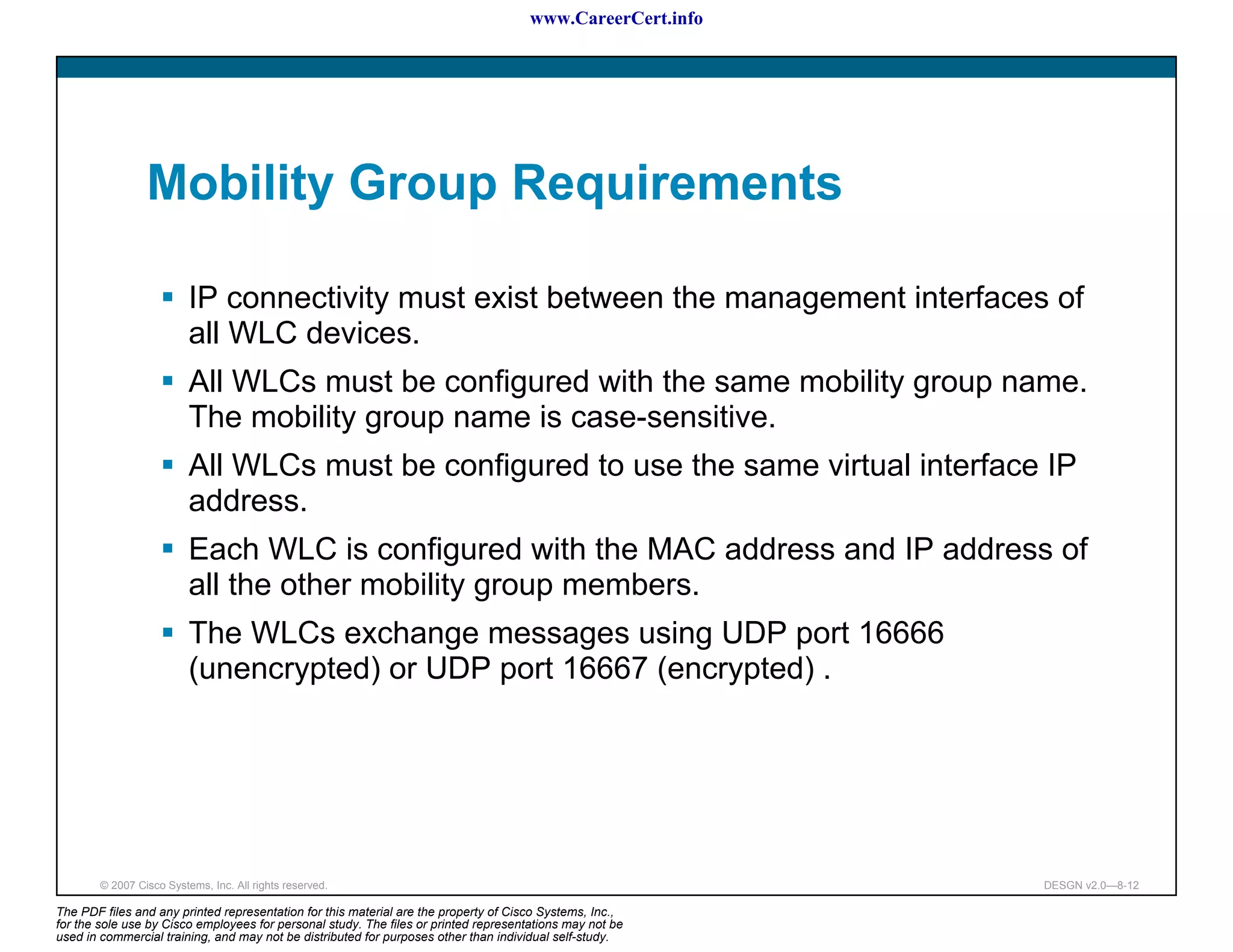
The document discusses applying a methodology to network design. It introduces Cisco's Service-Oriented Network Architecture (SONA) framework, which aims to build intelligence in the network. SONA has three layers: an integrated infrastructure layer, an interactive services layer, and an application layer. The document also discusses identifying customer requirements, which is the first step in Cisco's PPDIOO network life-cycle design methodology. It involves identifying planned applications and their criticality levels.




































































![www.CareerCert.info
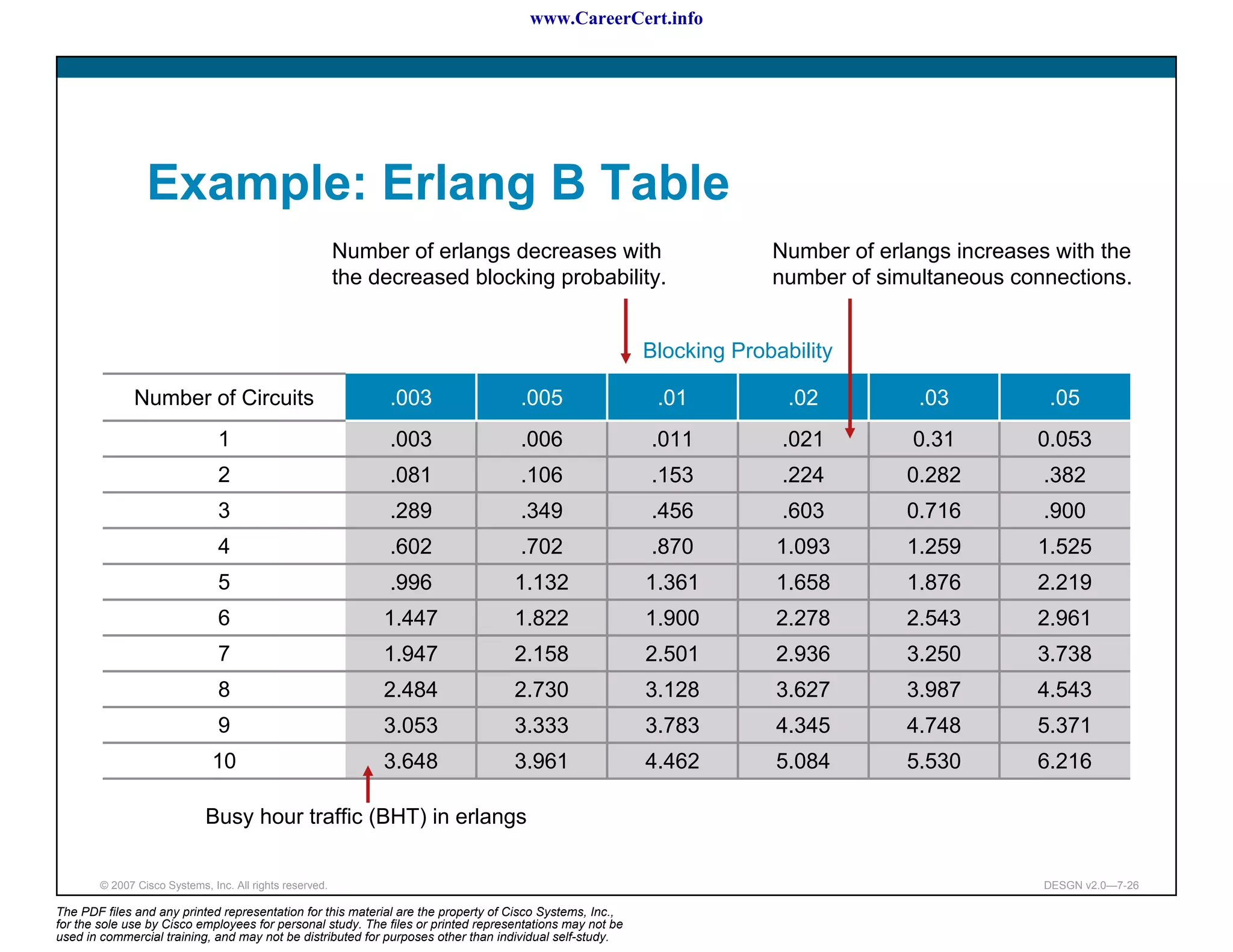
Portion of UK National Numbering Plan
Number Range Description
(01xxx) xxx xxx Trunk prefix (national long-distance calling prefix)
(01xxx) xxx xxx Geographic numbering options—area code and
(01x1) xxx xxxxx subscriber number
(011x) xxx xxxxx
(02x) xxxx xxxx
(01xxx[x]) xxxx[x]
(05x) xxxx xxxx Mobile phones, pagers, and personal numbering
(07xxx) xxxxxx Reserved for corporate numbering.
(0800) xxx xxx Freephone (except for mobile phone)
(0800) xxx xxxx
(0808) xxx xxxx
999 Free emergency number
112
© 2007 Cisco Systems, Inc. All rights reserved. DESGN v2.0—7-28
The PDF files and any printed representation for this material are the property of Cisco Systems, Inc.,
for the sole use by Cisco employees for personal study. The files or printed representations may not be
used in commercial training, and may not be distributed for purposes other than individual self-study.](https://image.slidesharecdn.com/ccdadesgnv2-0sgppttopdf-120625111643-phpapp01/75/Ccda-desgn-v2-0-sg-ppt-to-pdf-493-2048.jpg)















![www.CareerCert.info
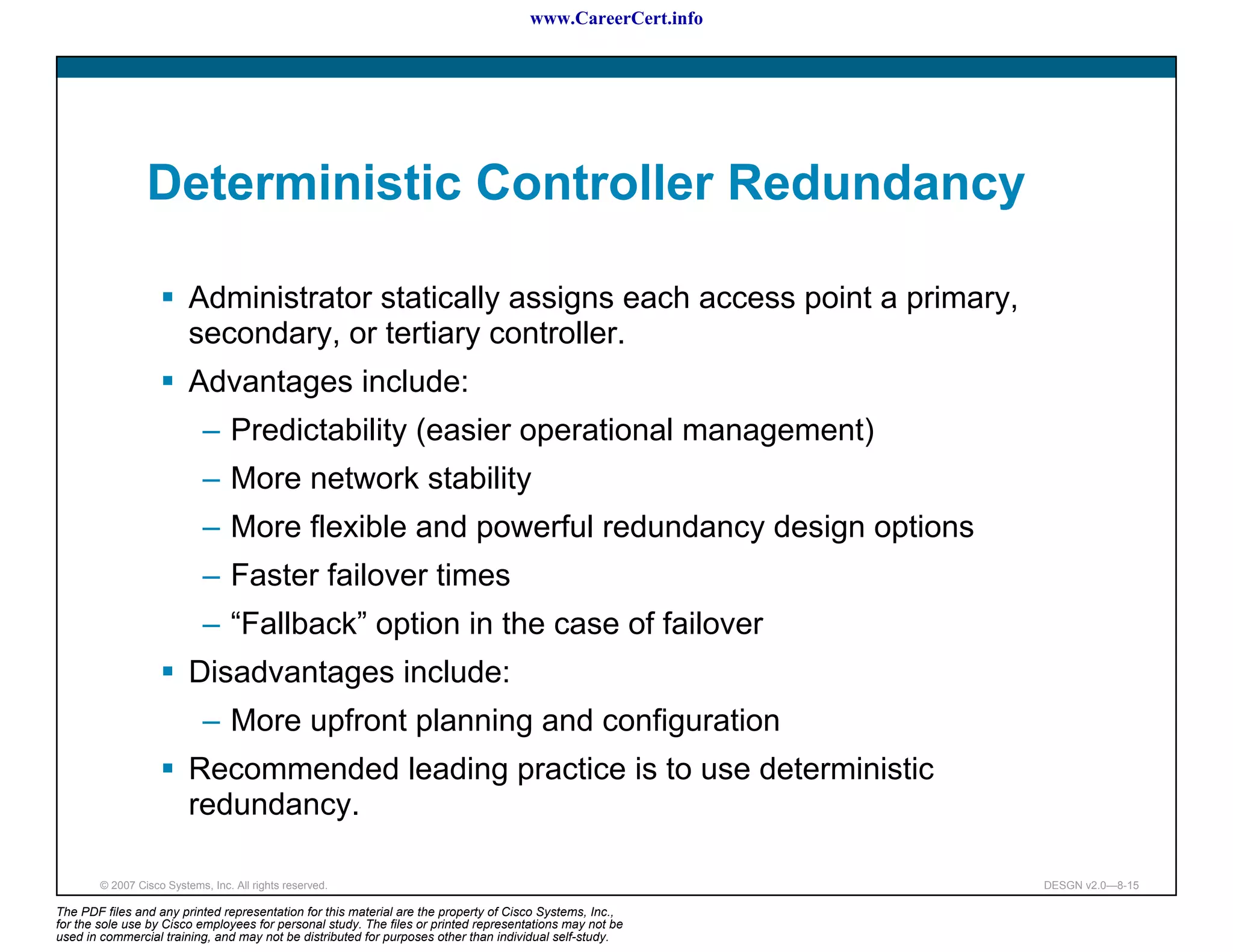
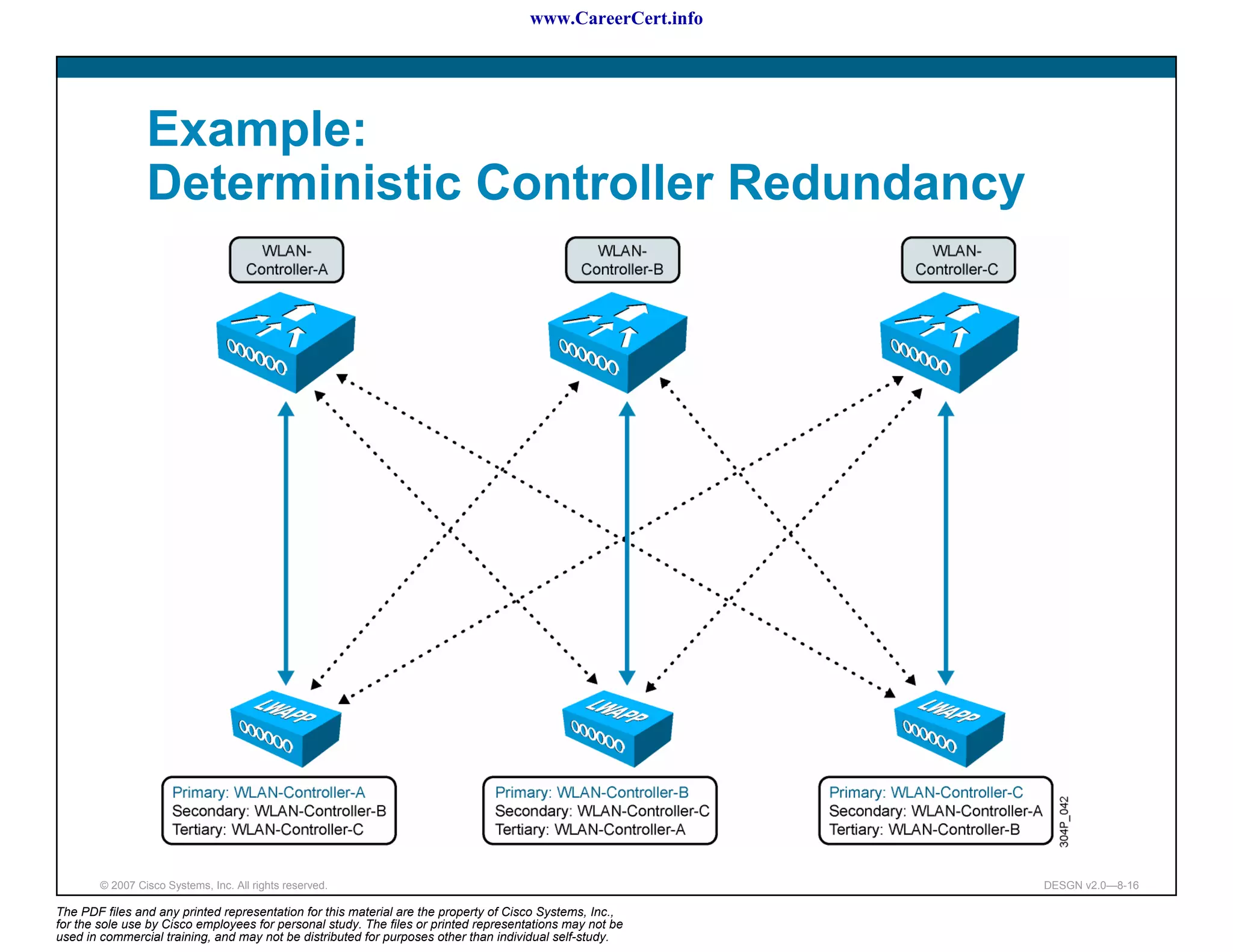
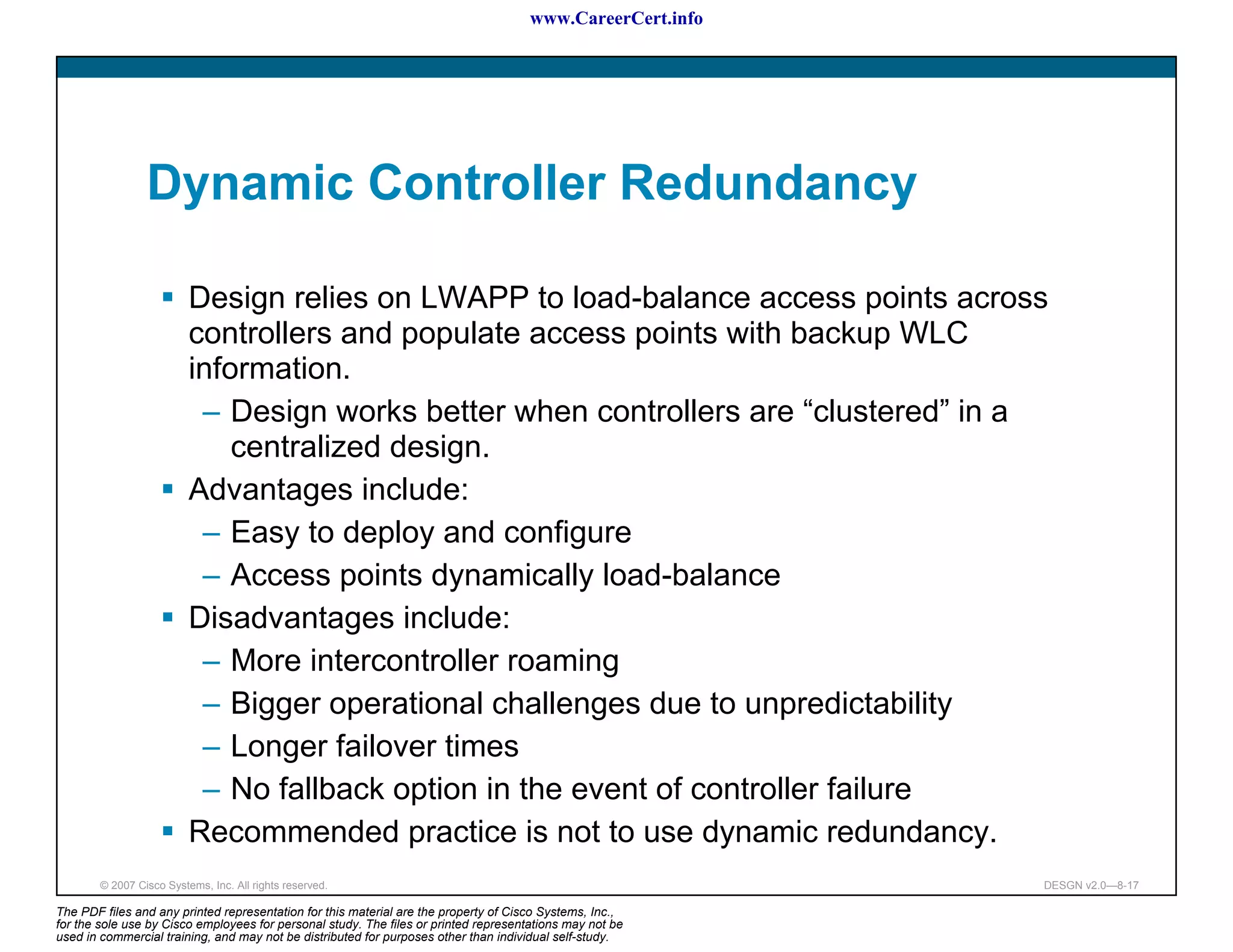
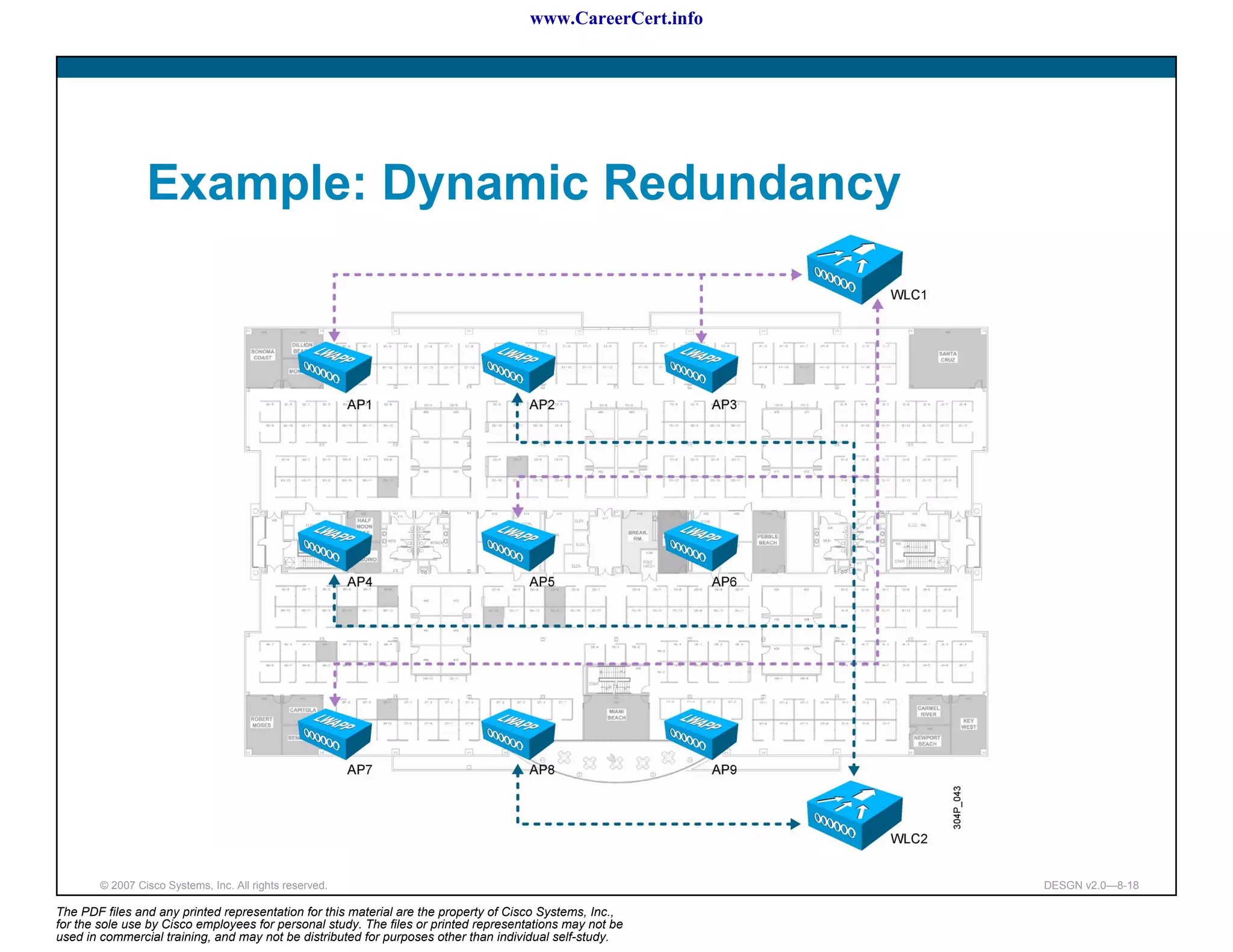
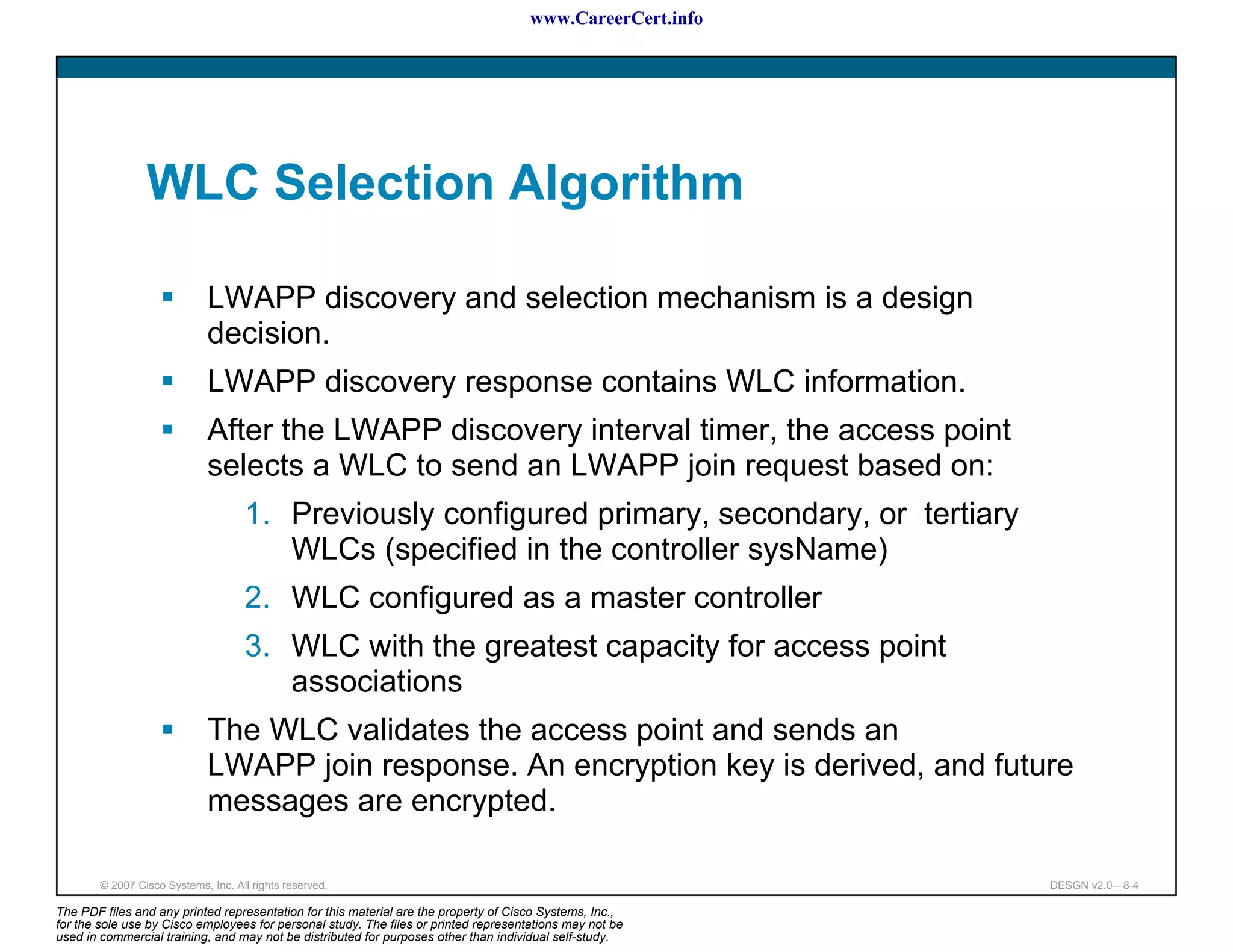
Controller Redundancy Design
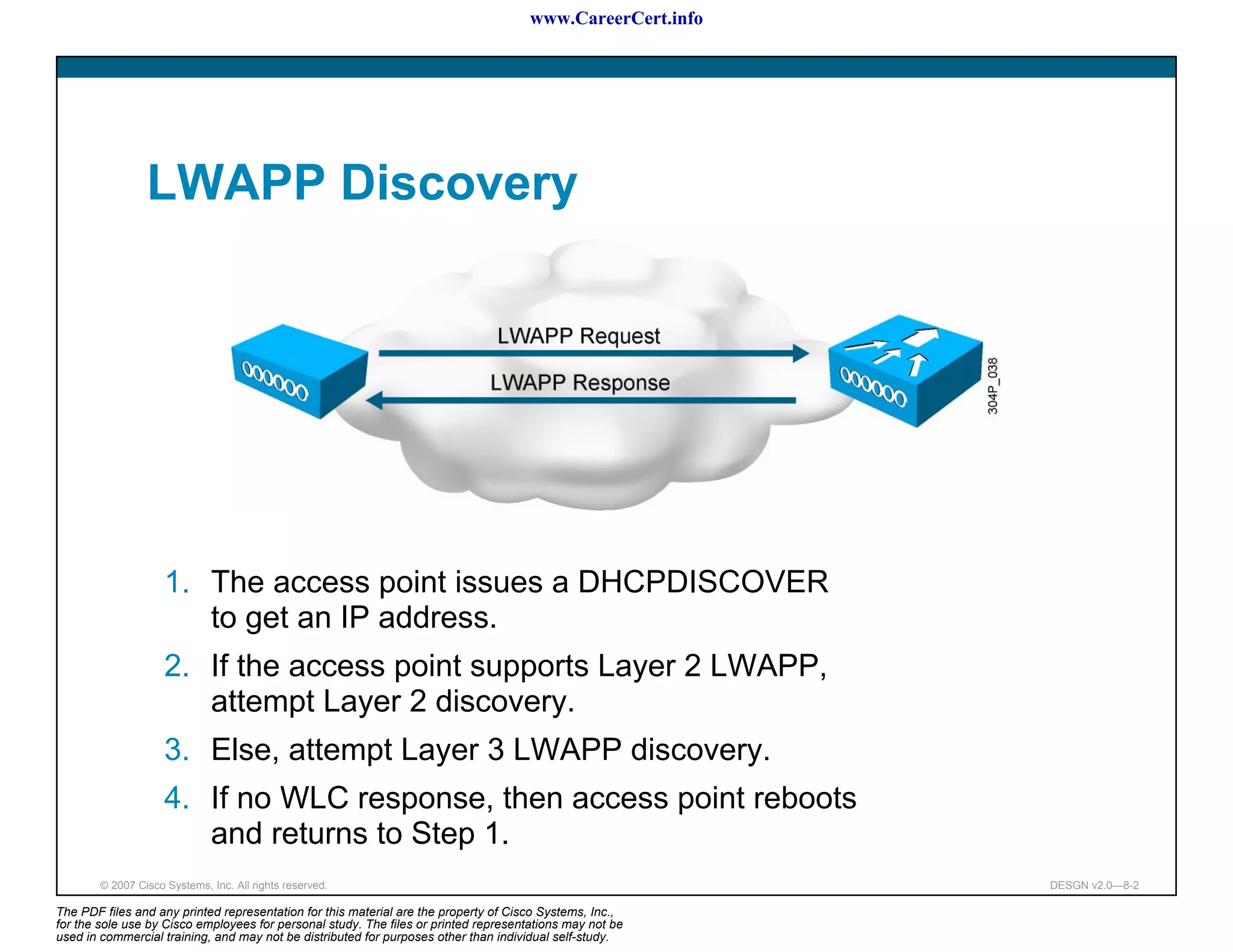
Access point selects its WLC with this sequence:
[Deterministic] If an access point has been previously configured
with a primary, secondary, or tertiary controller, the access point
attempts to join these first (specified by controller sysName).
[Initializing] The access point attempts to join a WLC configured
as a master controller.
[Dynamic] The access point attempts to join the WLC with the
greatest availability for access point associations.
© 2007 Cisco Systems, Inc. All rights reserved. DESGN v2.0—8-14
The PDF files and any printed representation for this material are the property of Cisco Systems, Inc.,
for the sole use by Cisco employees for personal study. The files or printed representations may not be
used in commercial training, and may not be distributed for purposes other than individual self-study.](https://image.slidesharecdn.com/ccdadesgnv2-0sgppttopdf-120625111643-phpapp01/75/Ccda-desgn-v2-0-sg-ppt-to-pdf-580-2048.jpg)