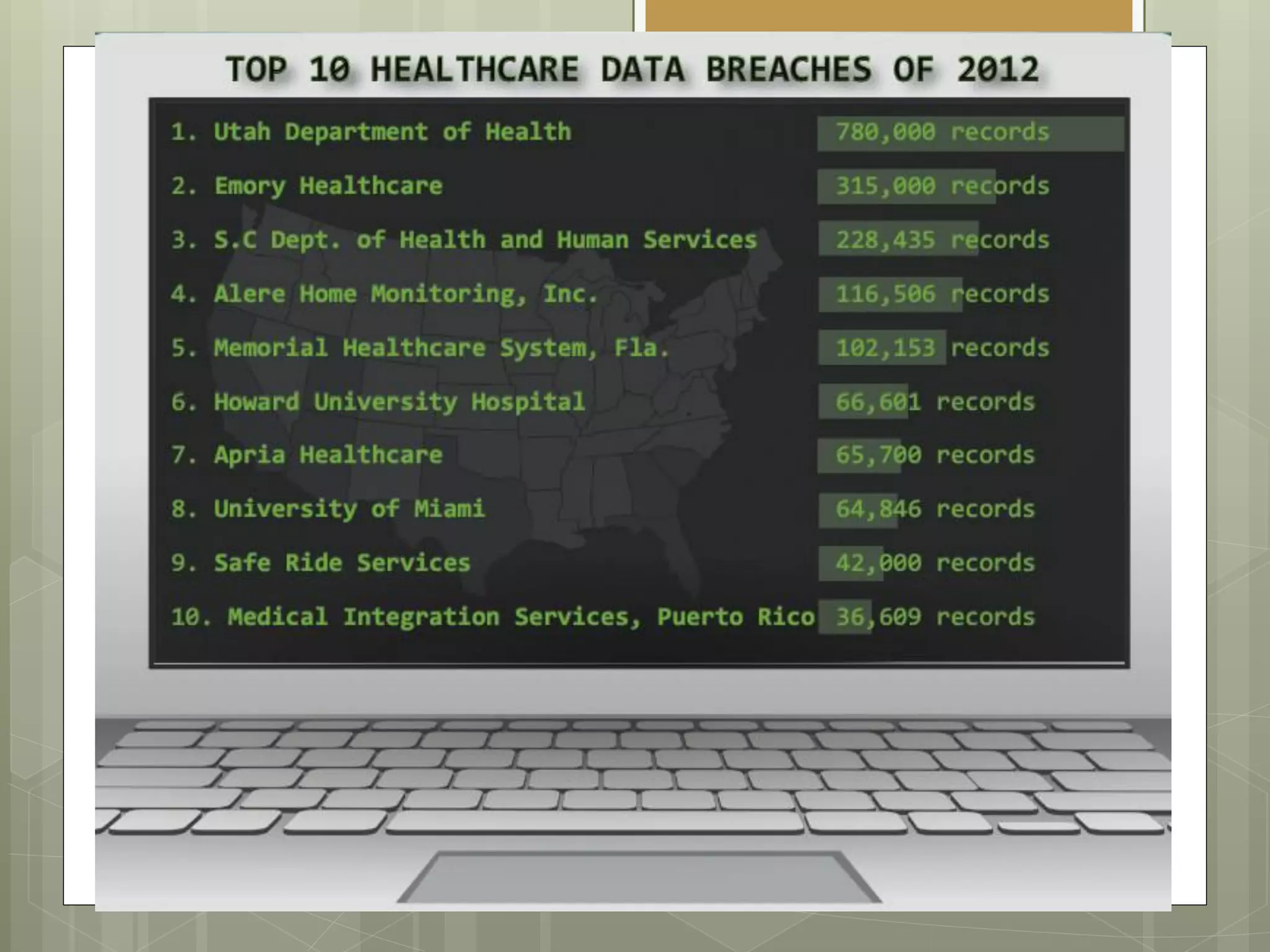
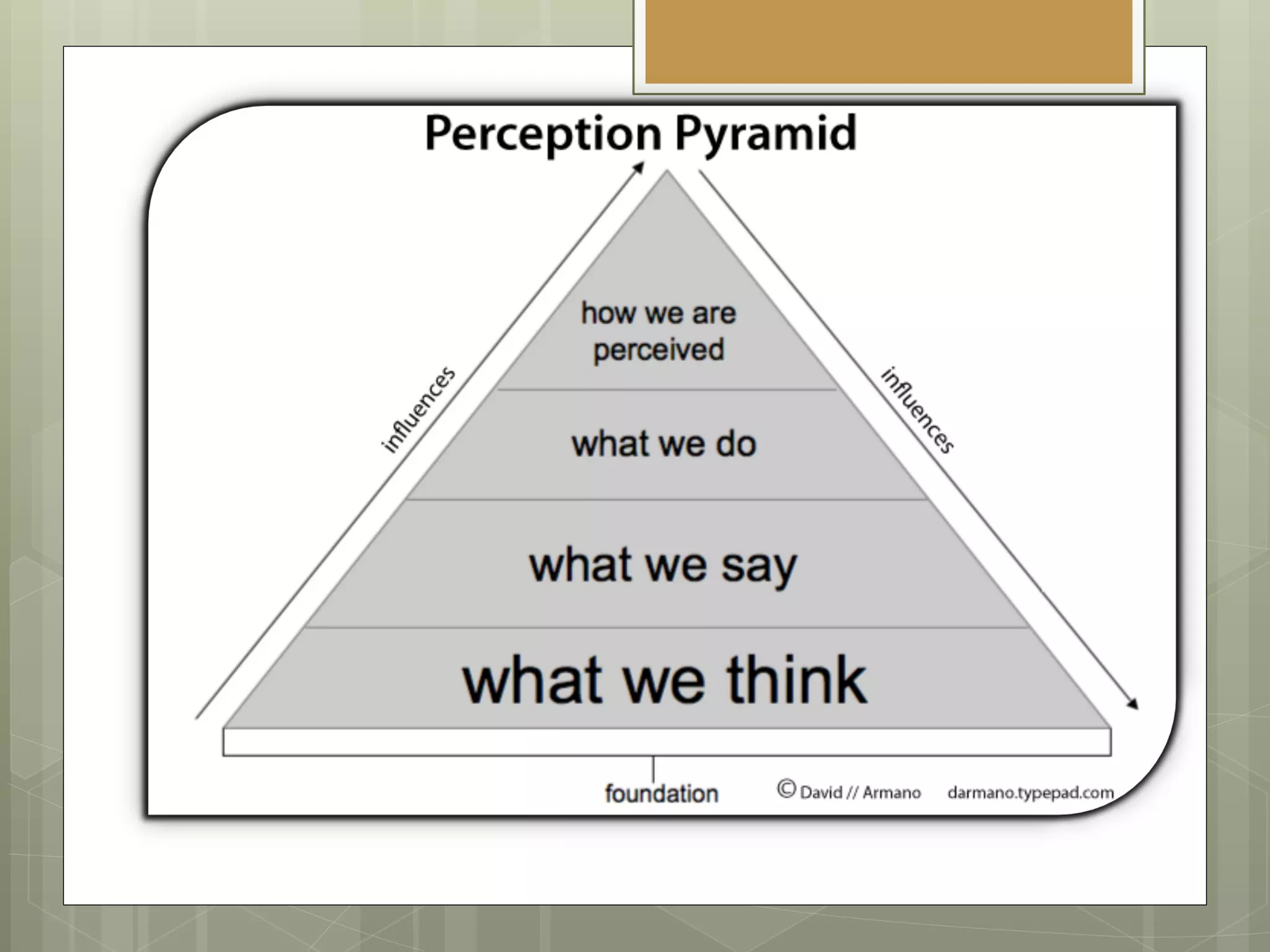
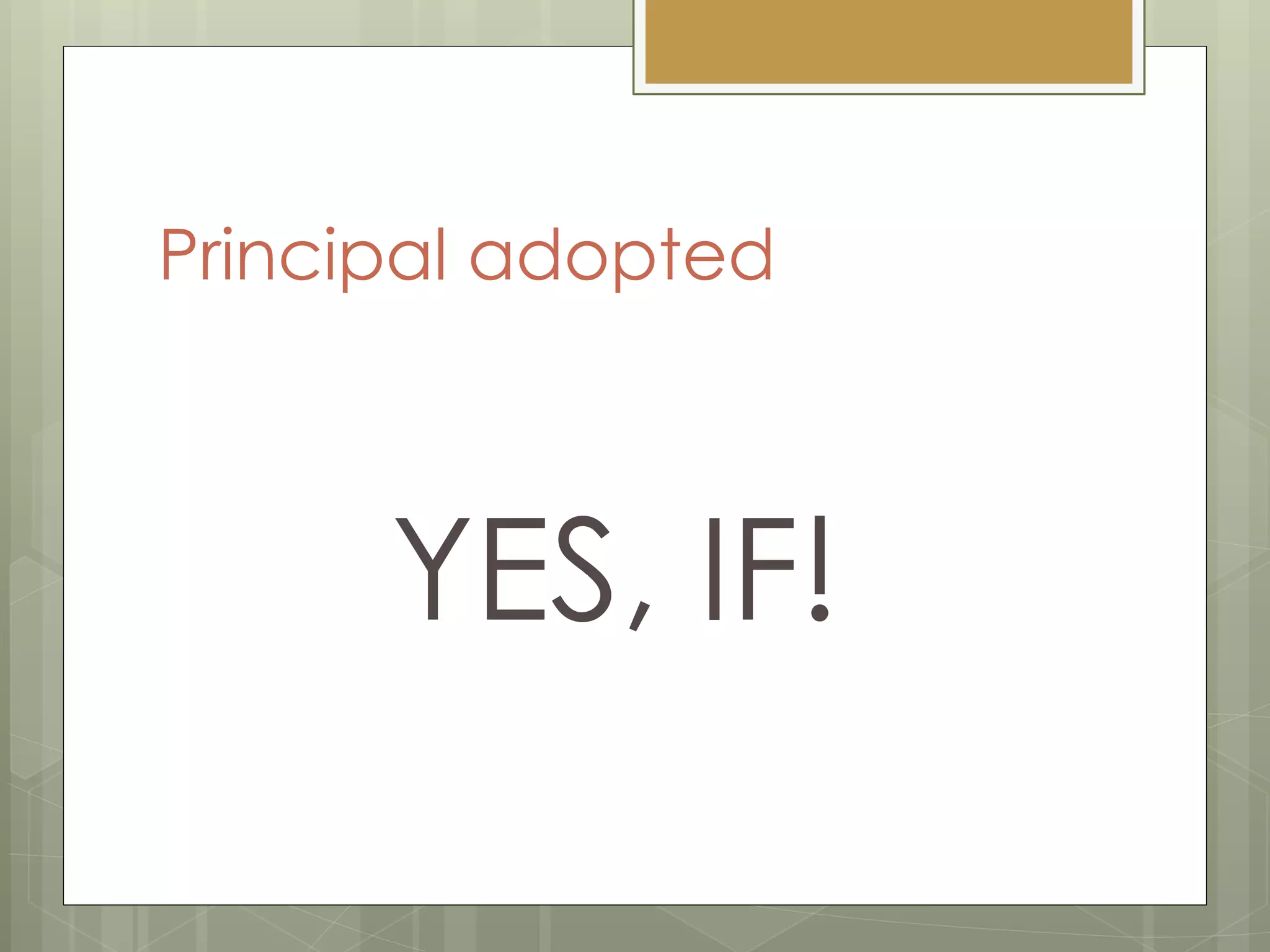
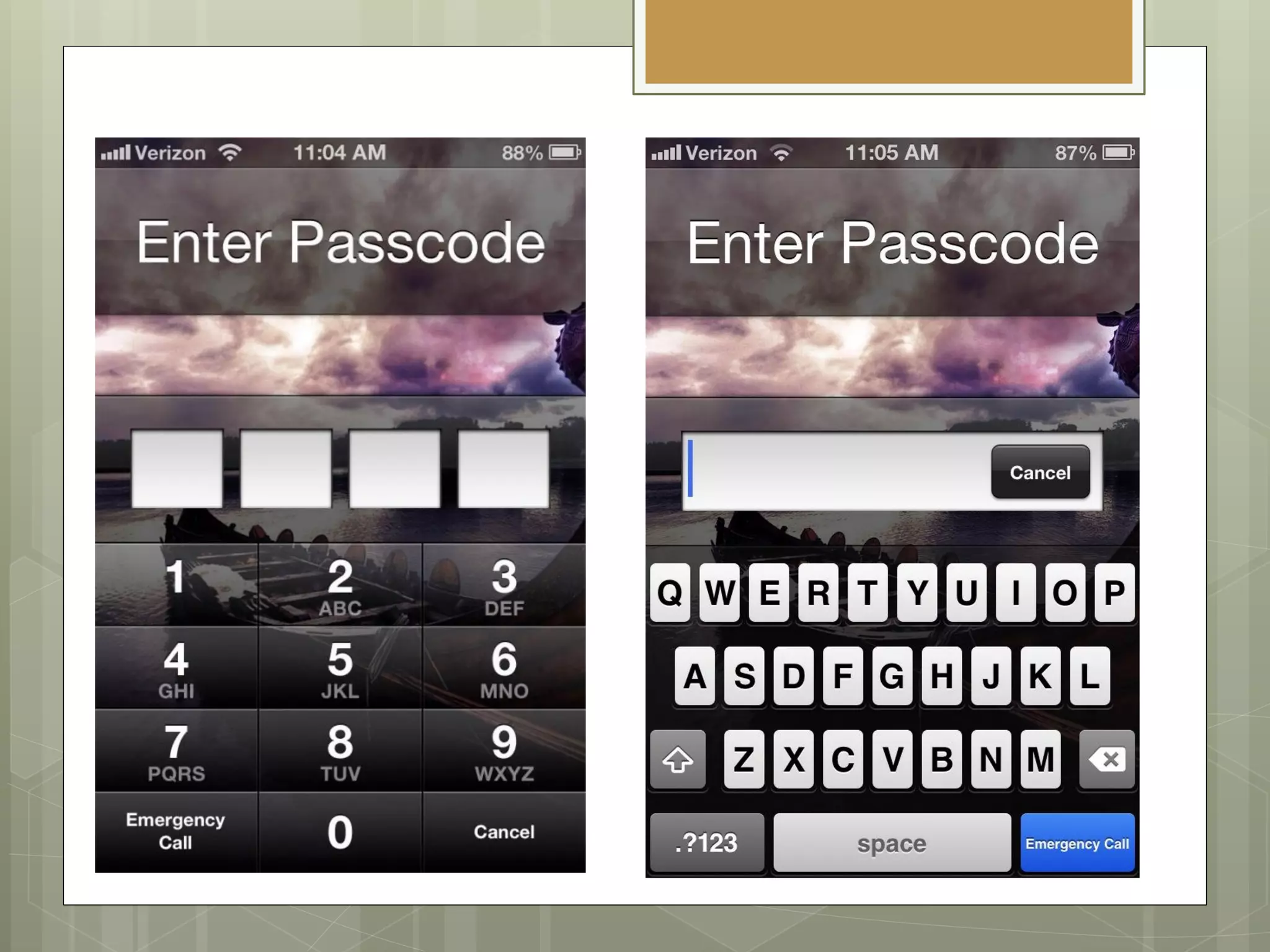
The document discusses the information security strategy of Presbyterian Healthcare Services, focusing on addressing challenges such as negative perceptions and resource constraints while promoting cloud solutions and mobile device usage. It emphasizes the importance of a positive communication strategy and governance in overcoming obstacles and fostering innovation within the organization. The key takeaway is to adopt a 'yes, if' mindset to support security and innovation in a collaborative manner.