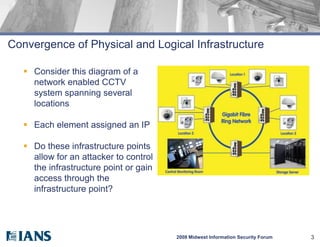
The document discusses the convergence of physical and logical security infrastructure. It notes that as physical security systems like access control become network-enabled, they can be vulnerable to hacking and compromise the entire organization. The document outlines a solution of building cross-training between physical and IT security teams to increase awareness and complete small collaborative projects. Key lessons discuss managing expectations, having central change management, balancing both security teams, and integrating process models for collaboration. The document emphasizes that knowledge sharing between teams is important for effective security.