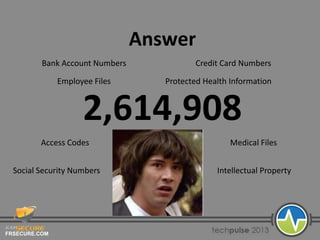
Frsecure, founded in 2008 by experts in information security, emphasizes the importance of mobile device management and encryption to prevent data breaches. They discuss the risks associated with personal mobile device usage and provide an example of a significant data breach that resulted from poor security practices. The document advocates for comprehensive policies, employee training, and a risk-based approach to enhance organizational security.