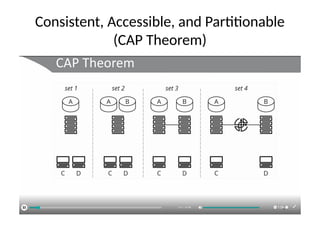
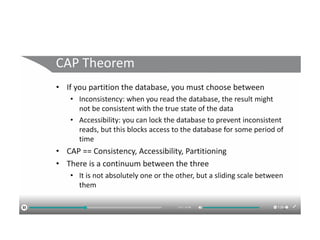
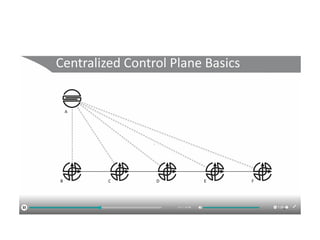
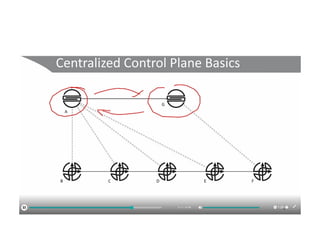
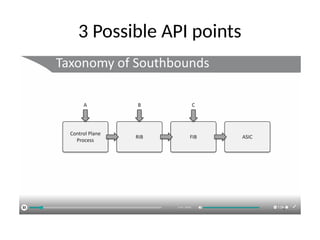
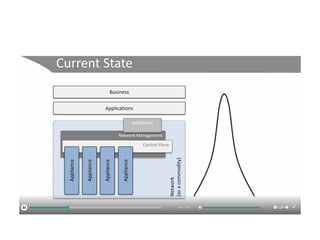
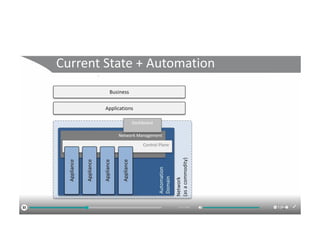
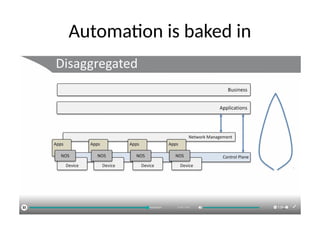
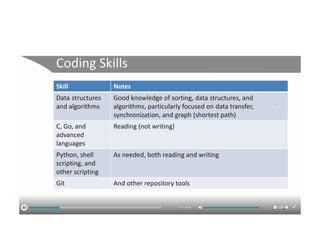
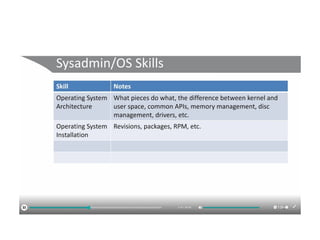
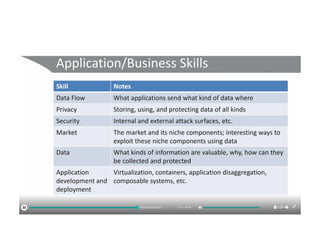
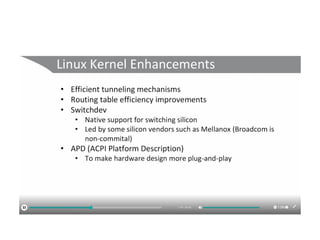
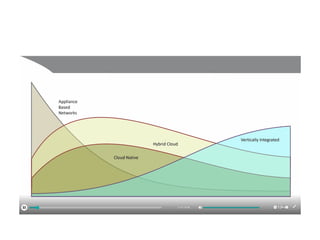
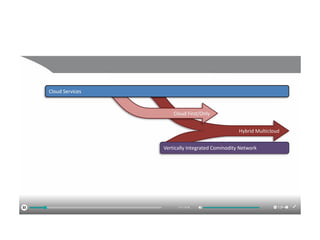
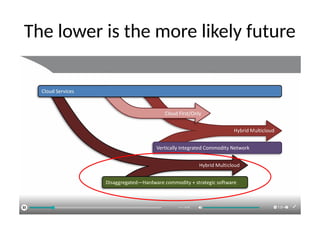
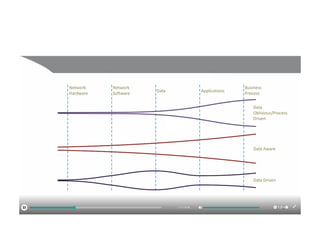
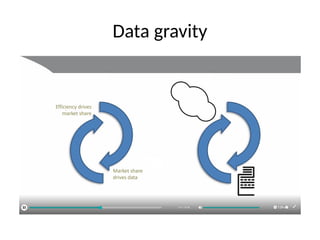
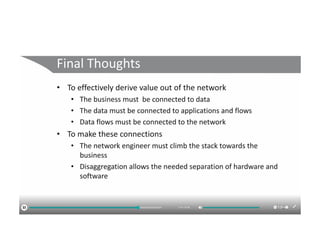
The document discusses the trade-offs between centralized and distributed control planes in networking, highlighting factors like network control and policy complexity. It outlines three potential API points for injecting information into network devices, facilitating different operational modes and interactions with routing tables. Additionally, it emphasizes the shift in focus for network professionals towards the control plane and the significance of data-driven approaches in future business models.