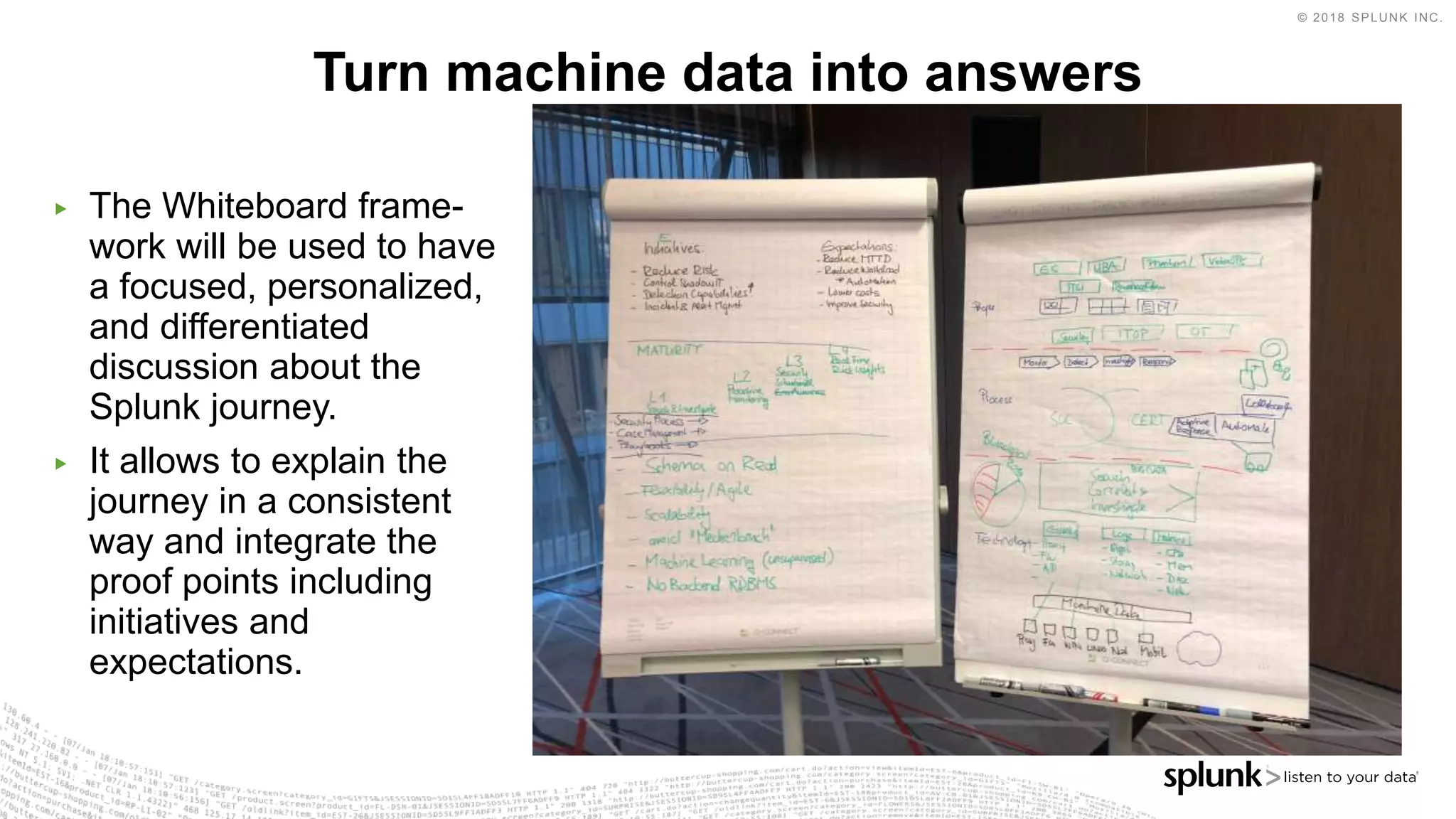
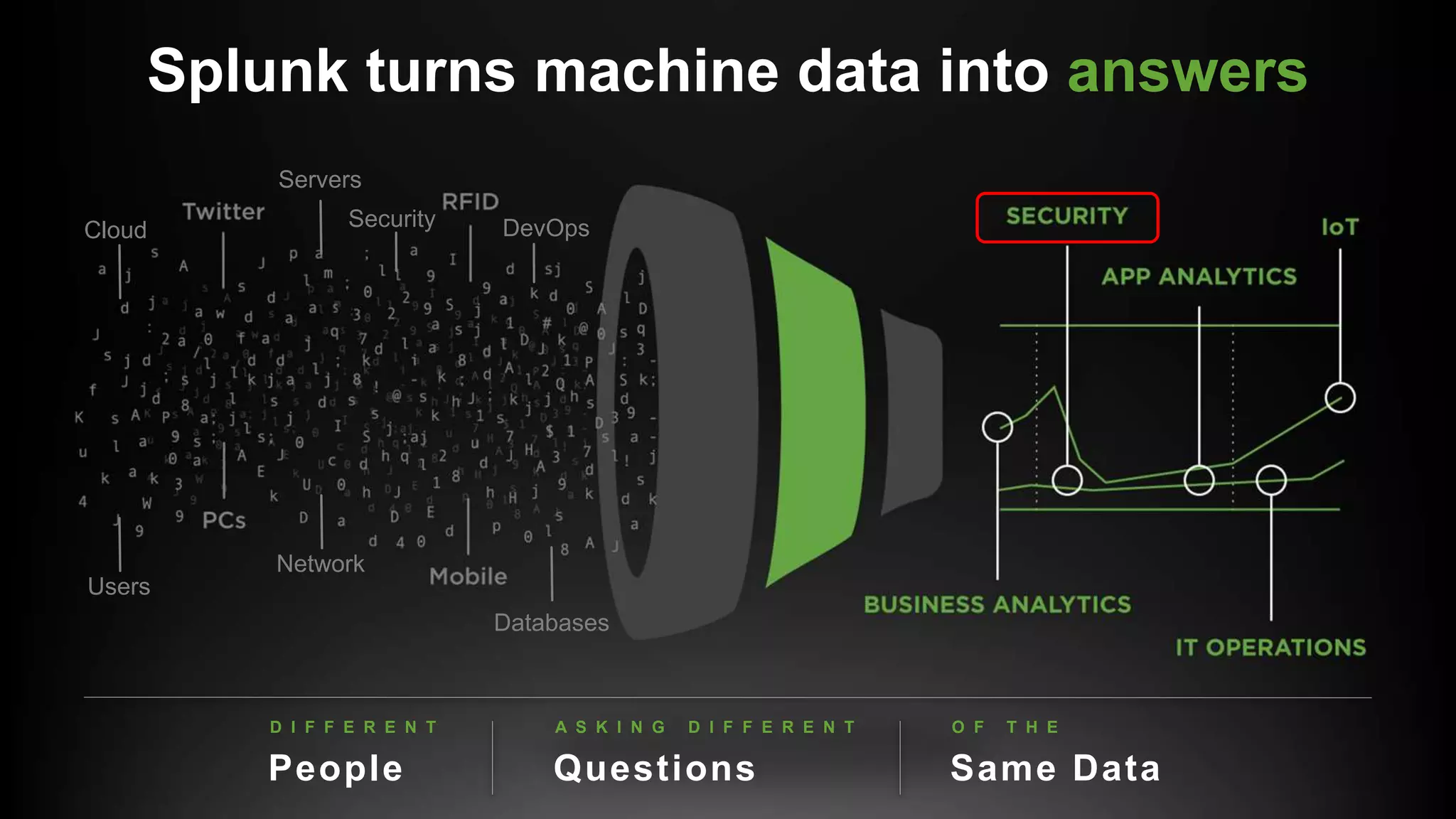
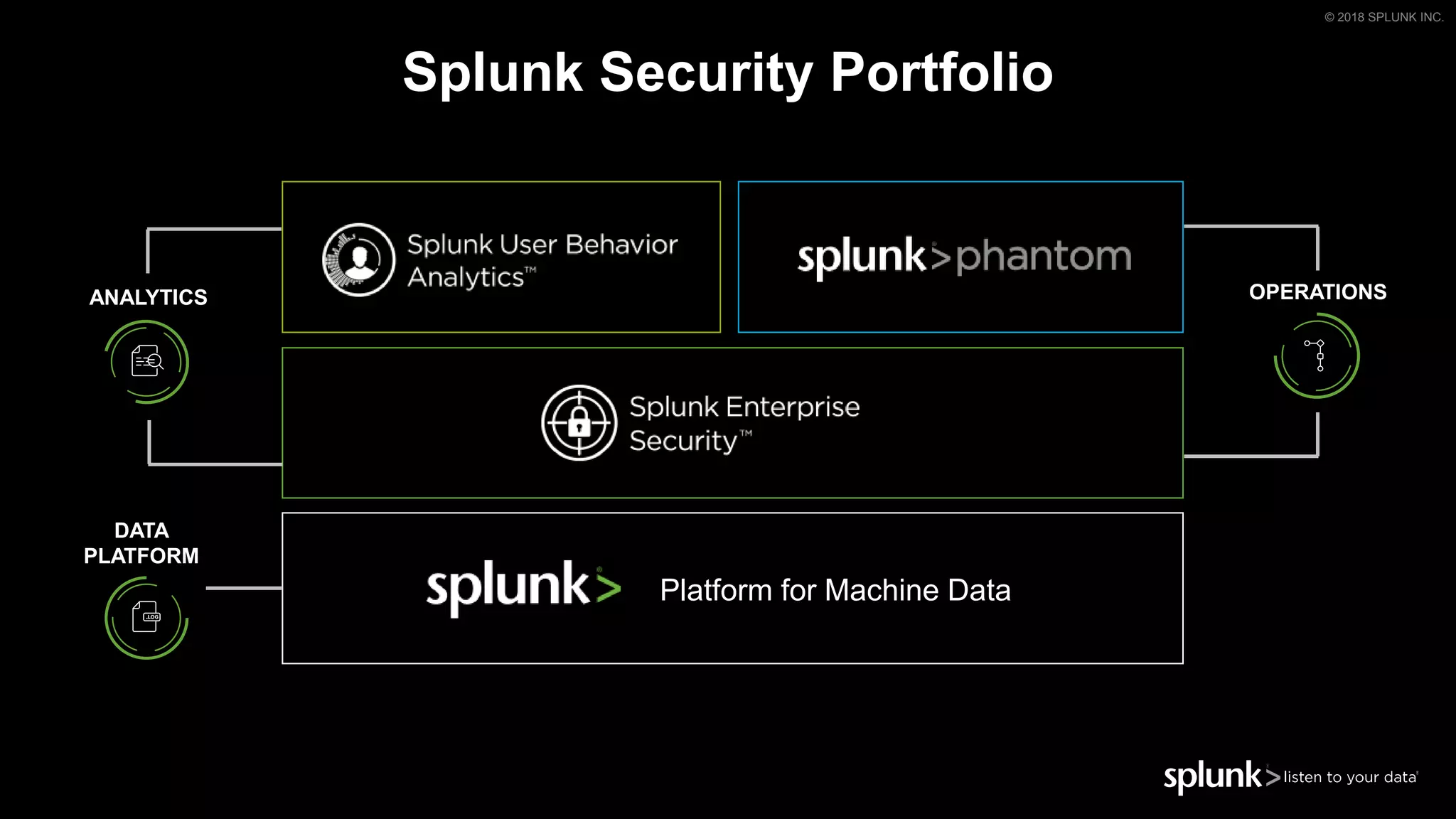
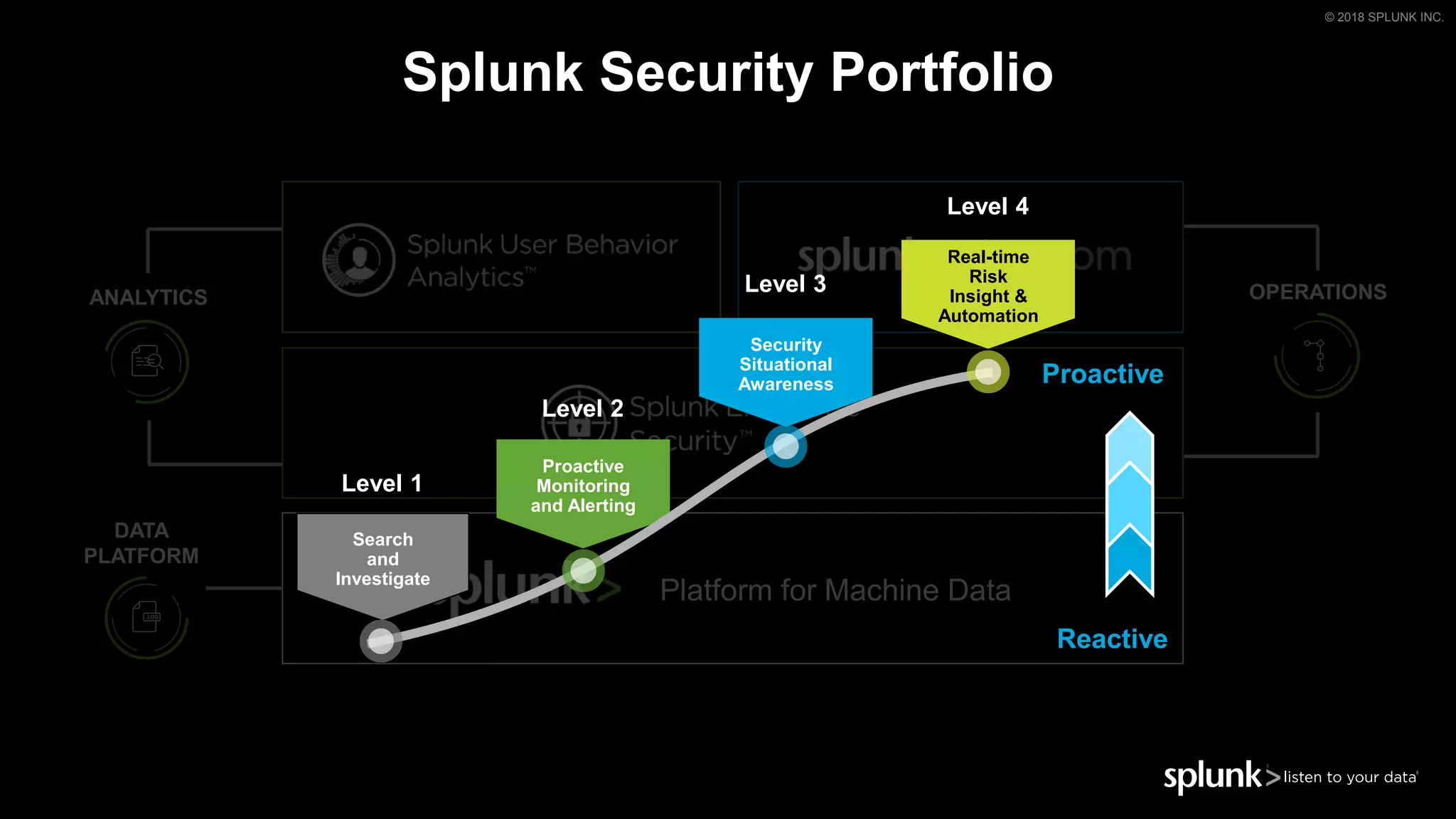
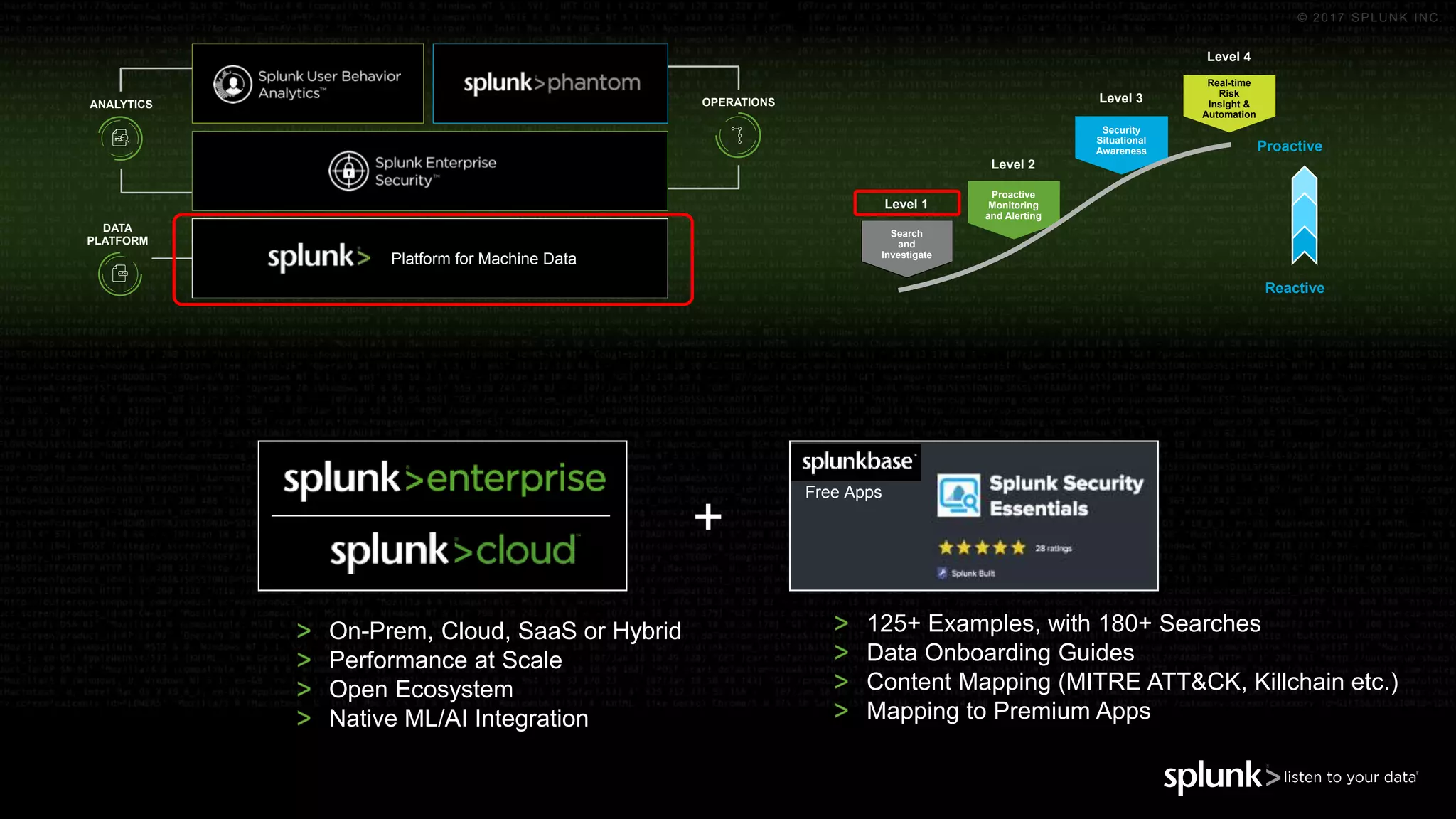
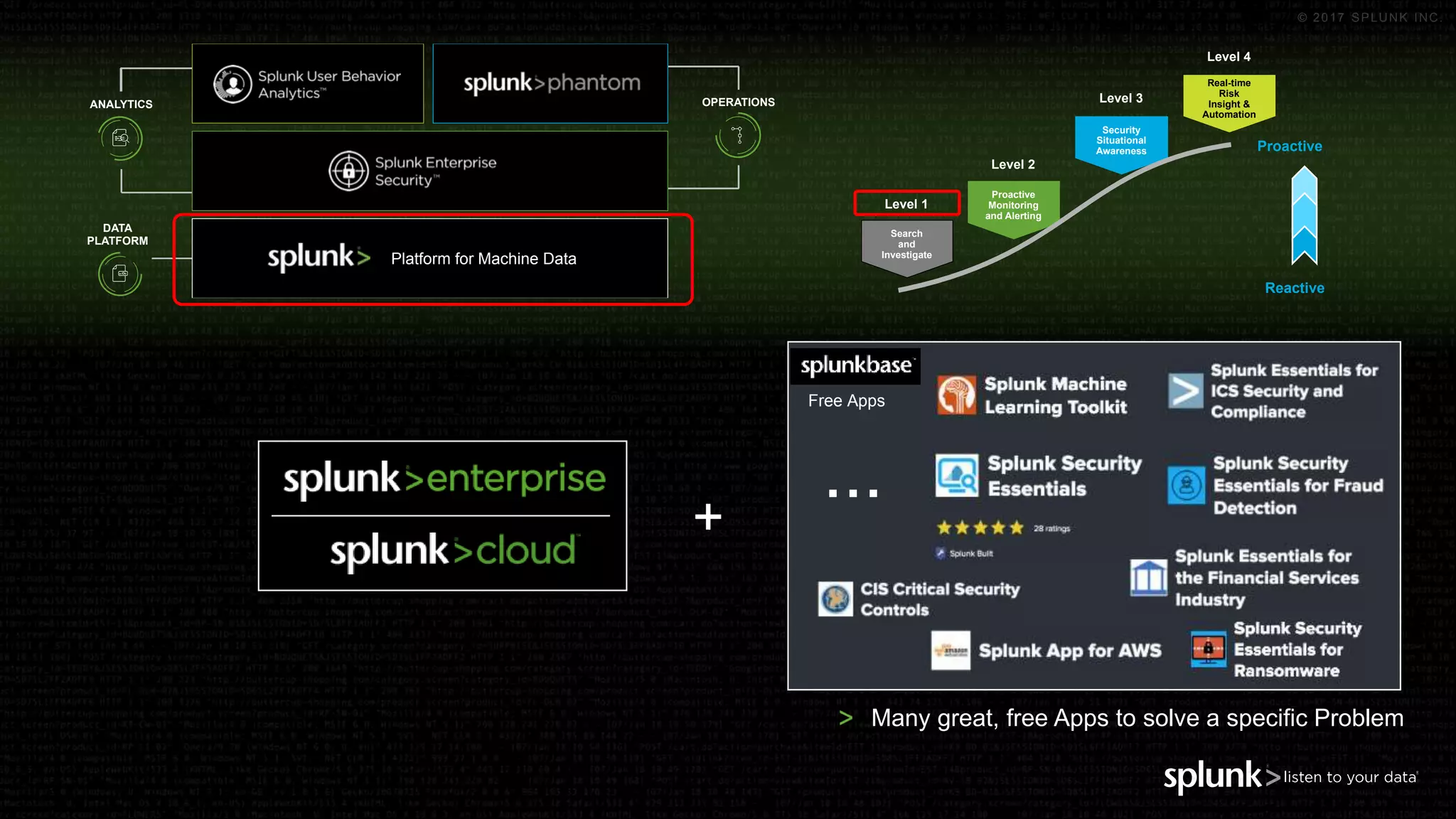
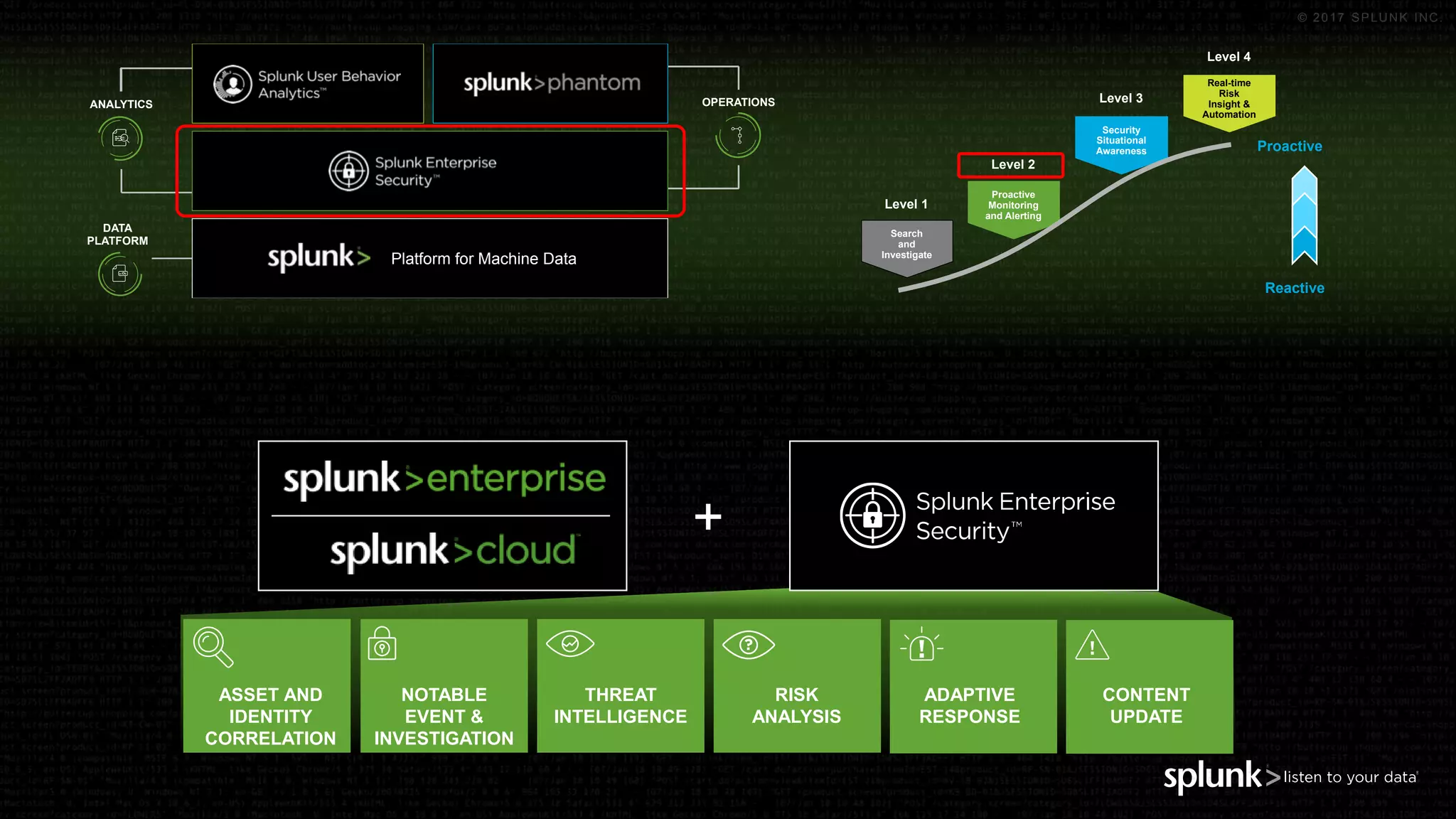
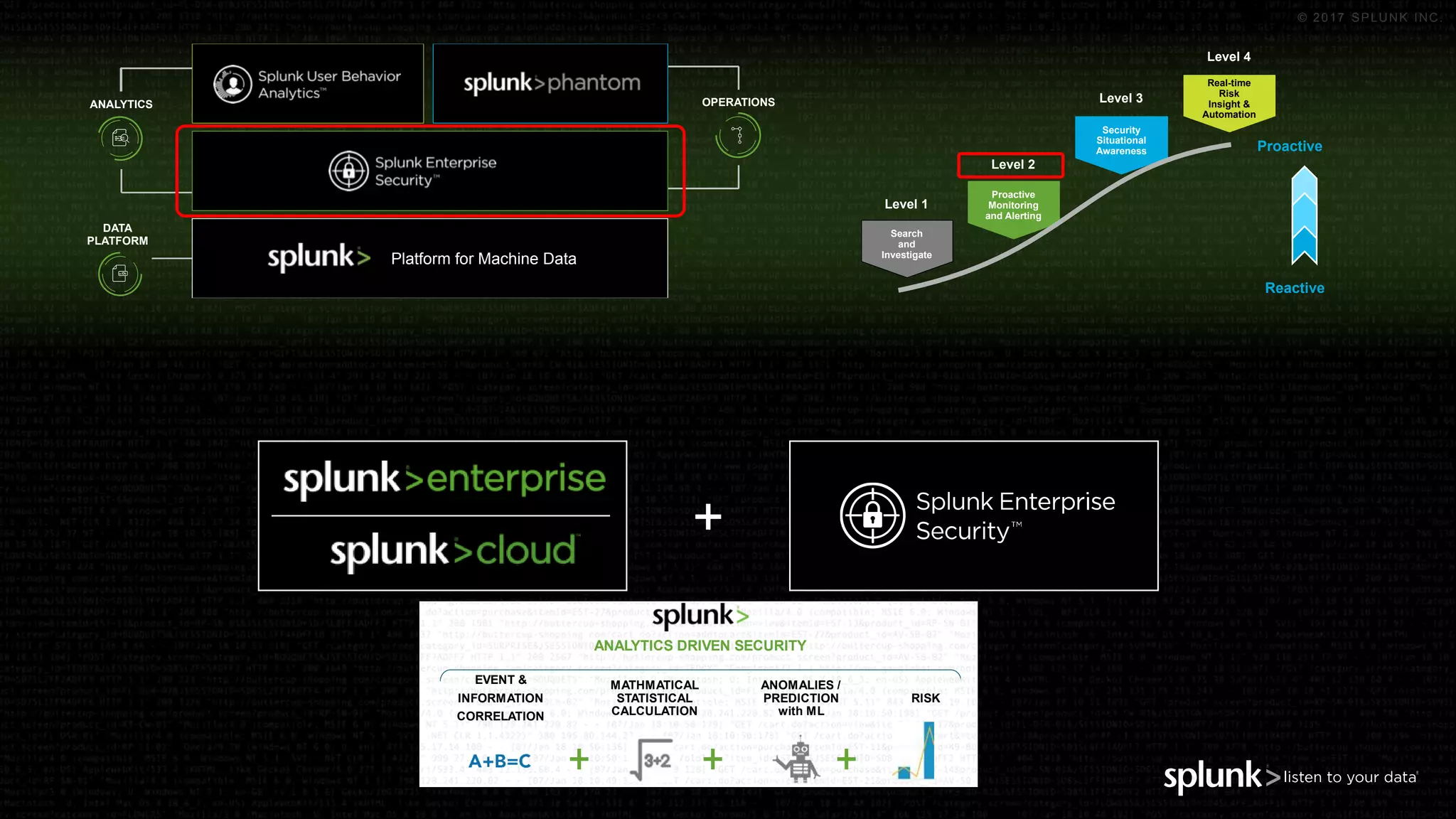
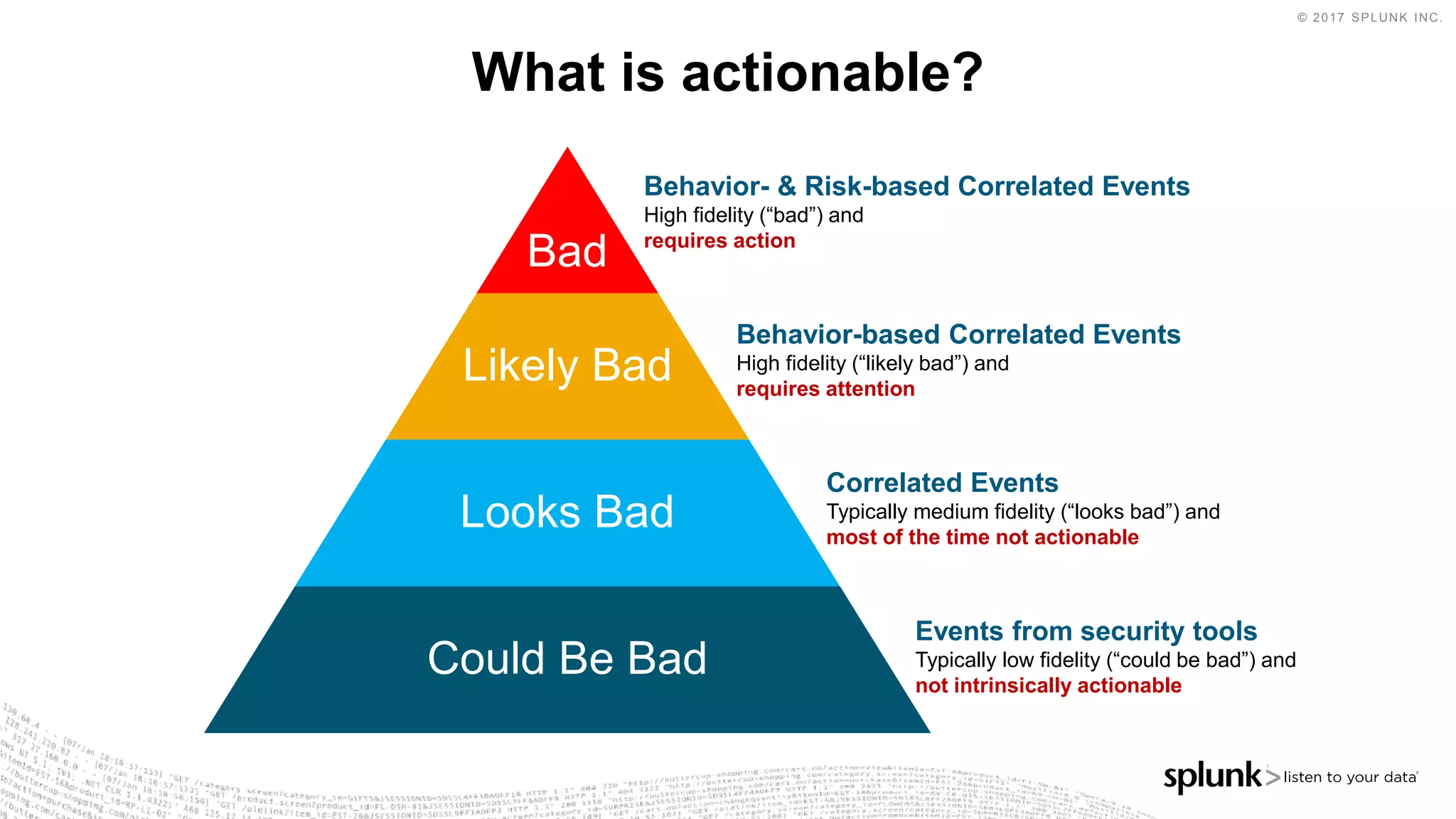
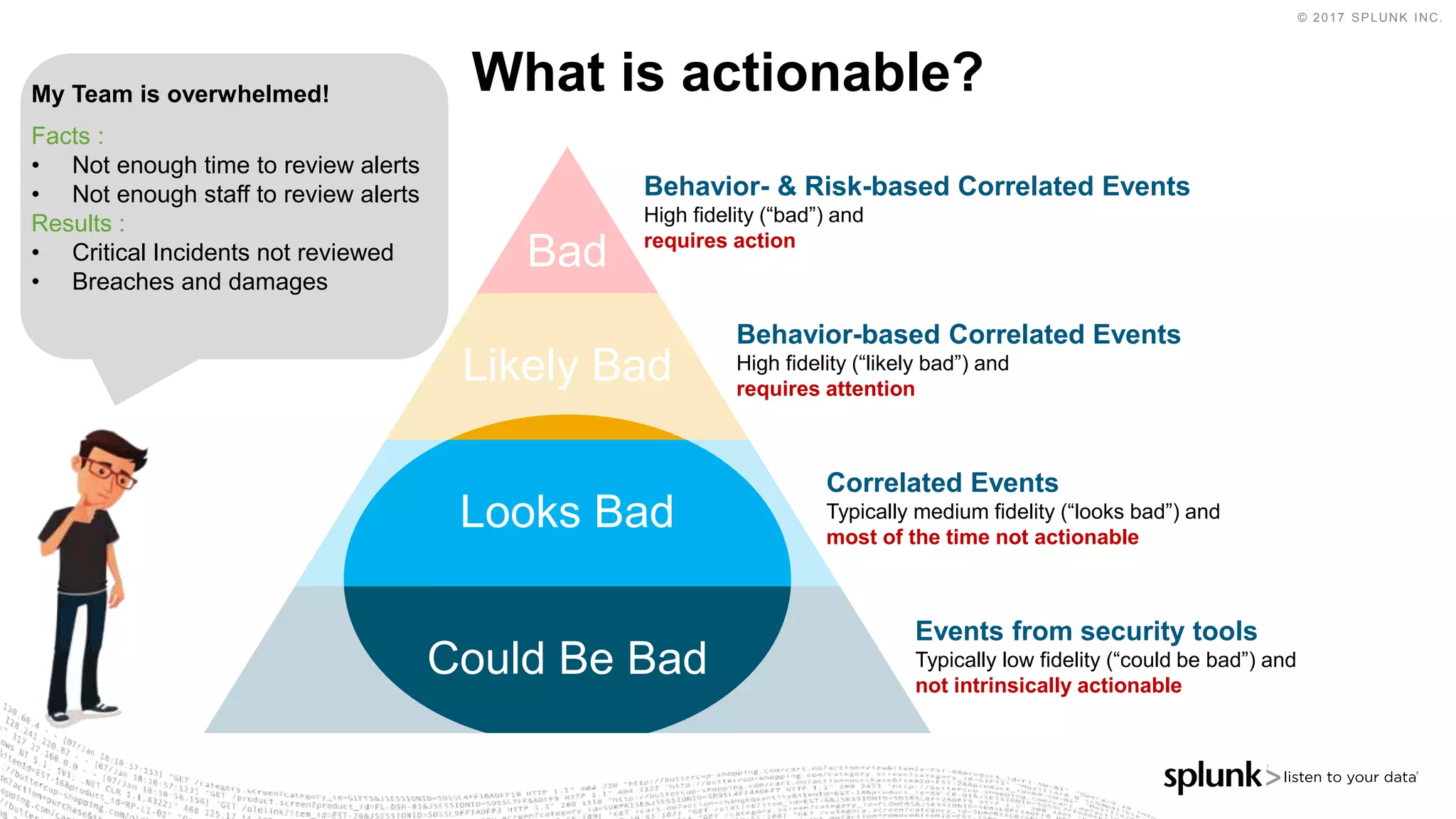
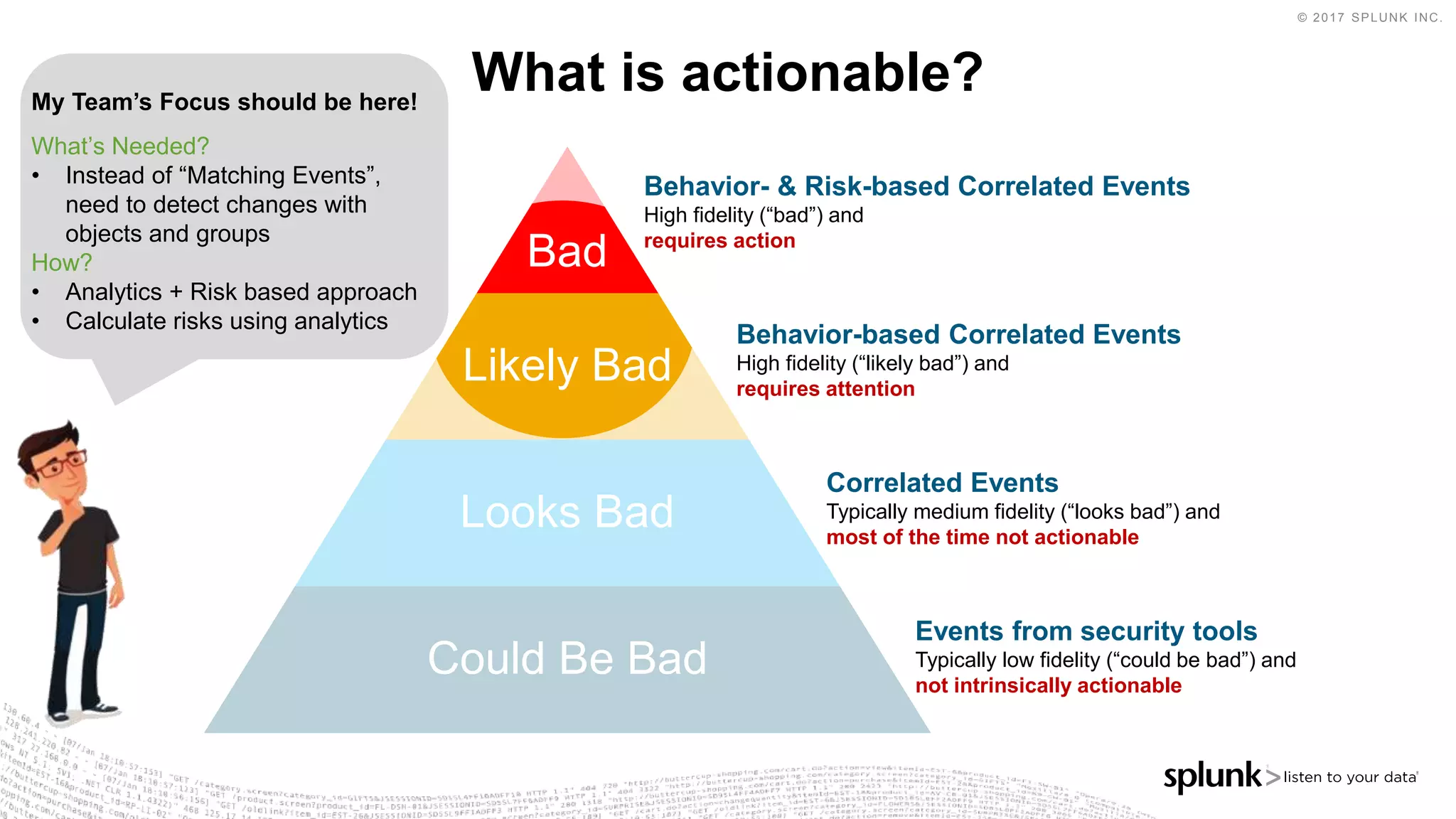
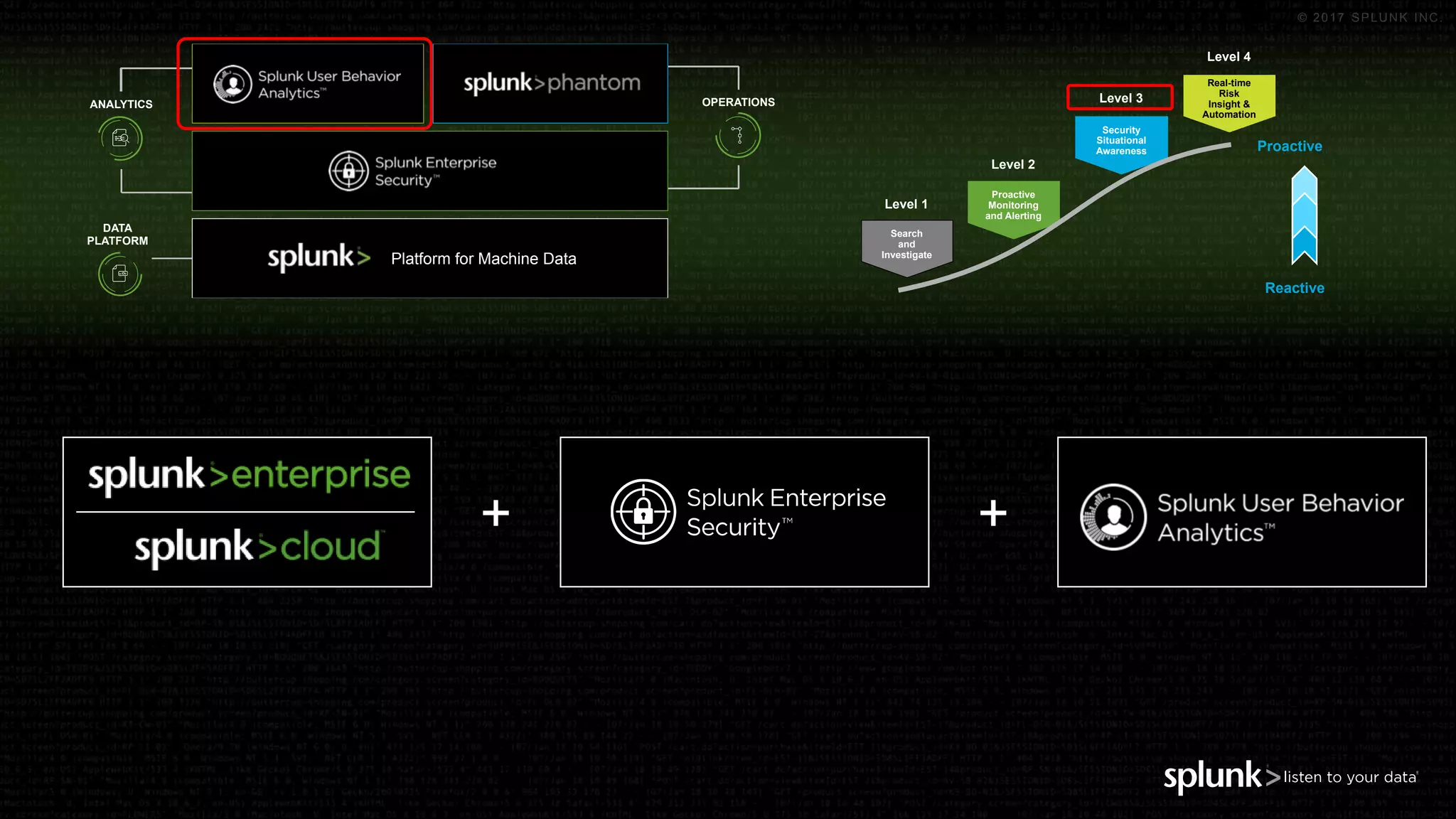
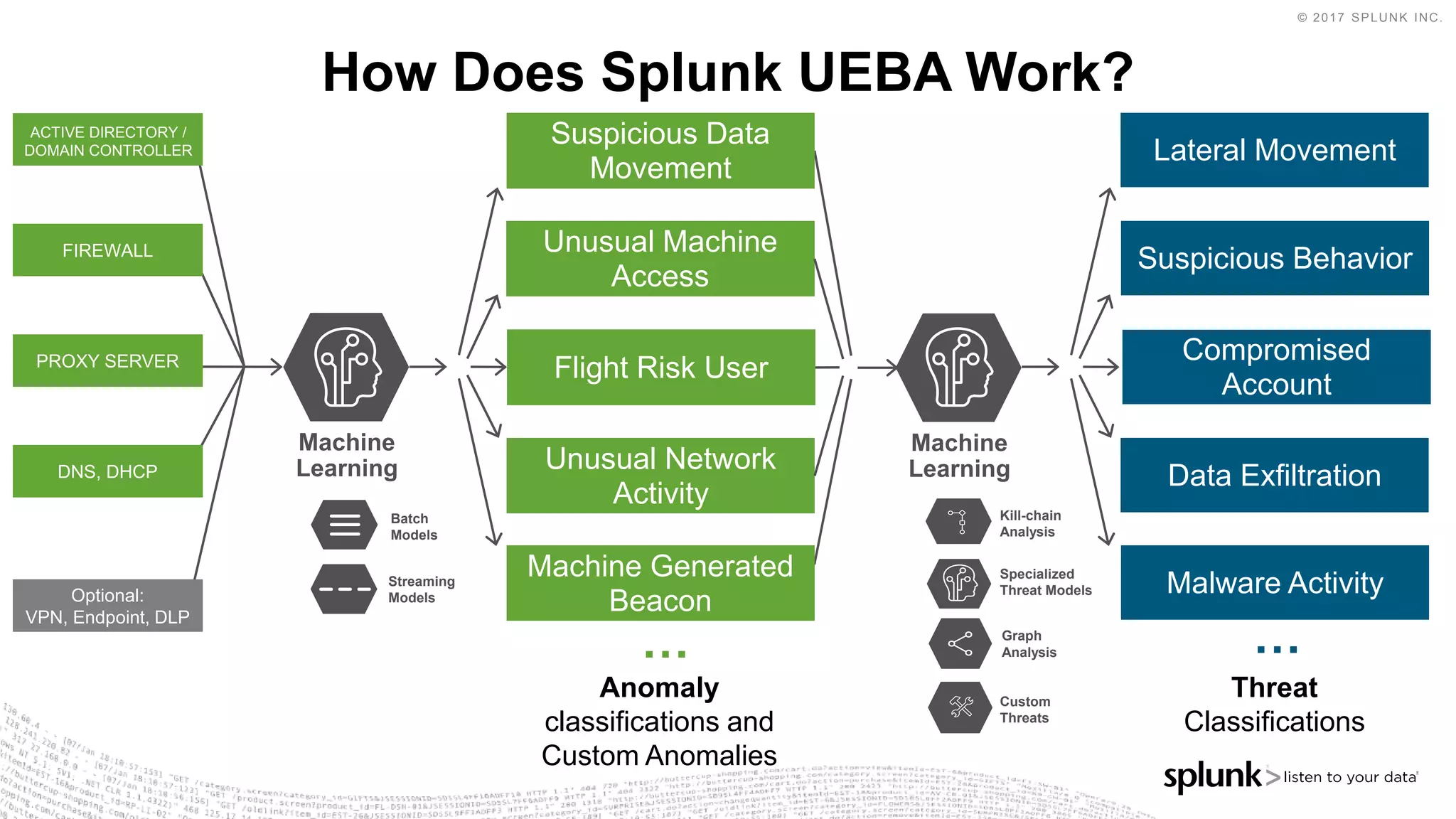
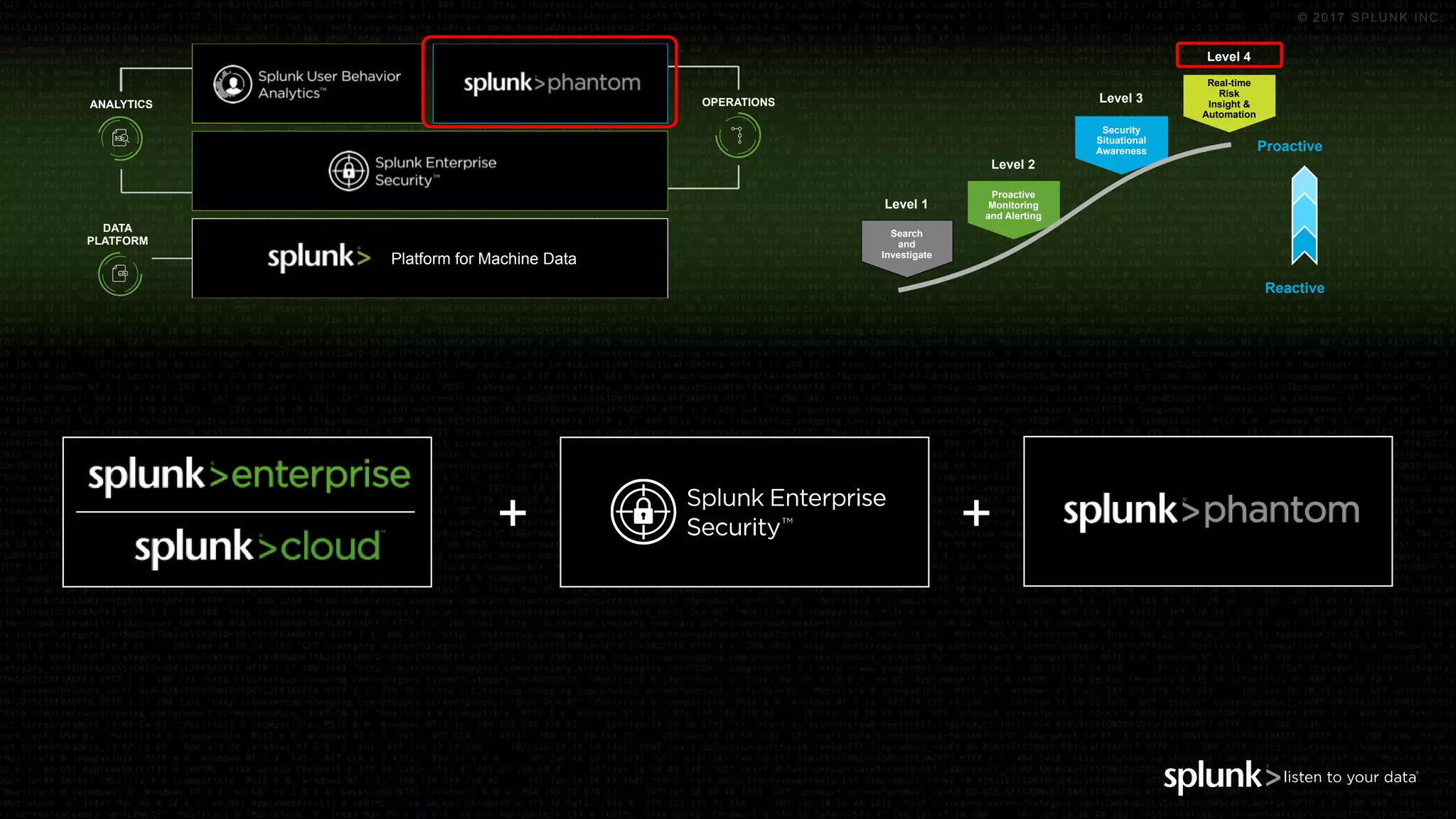
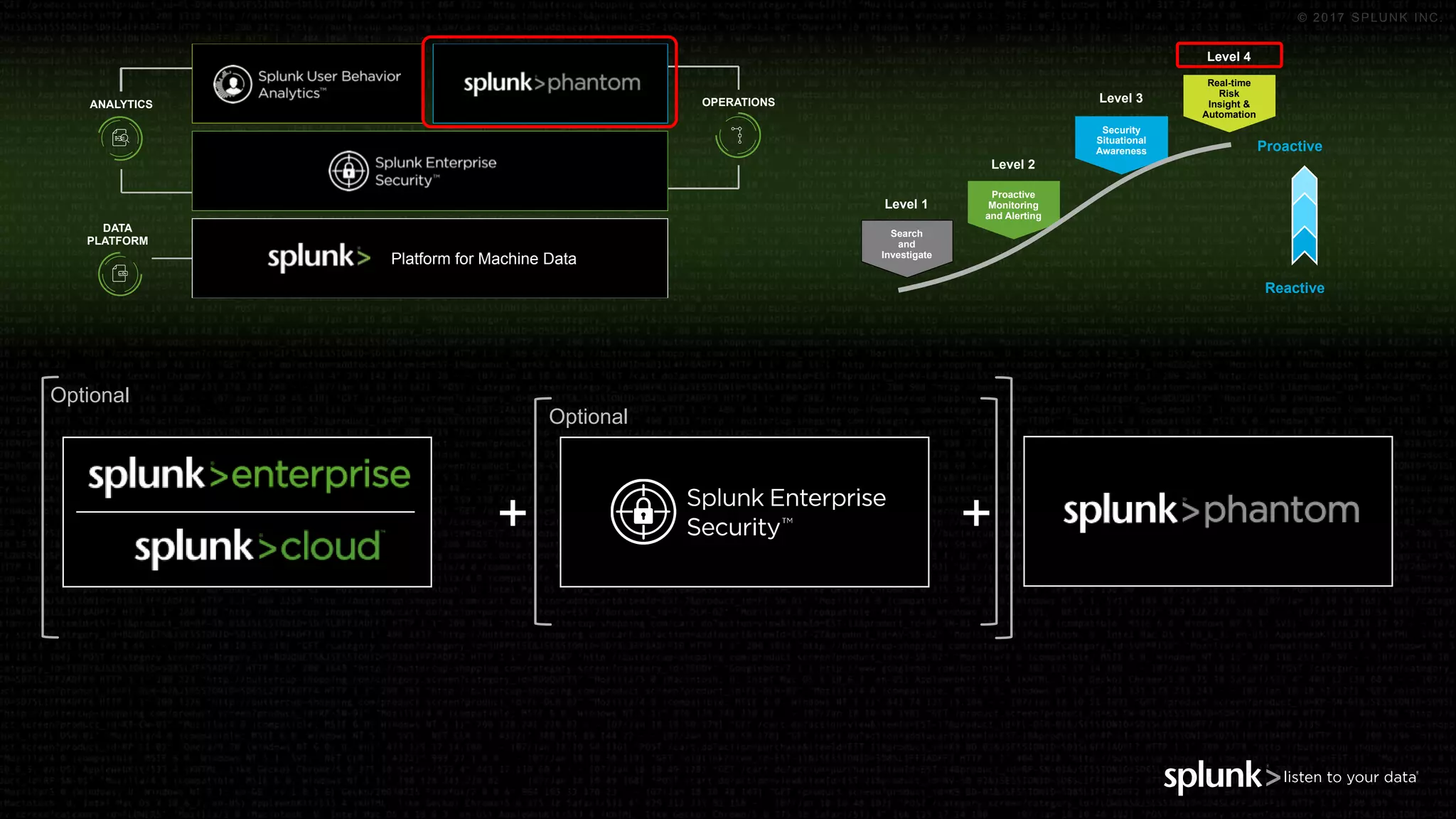
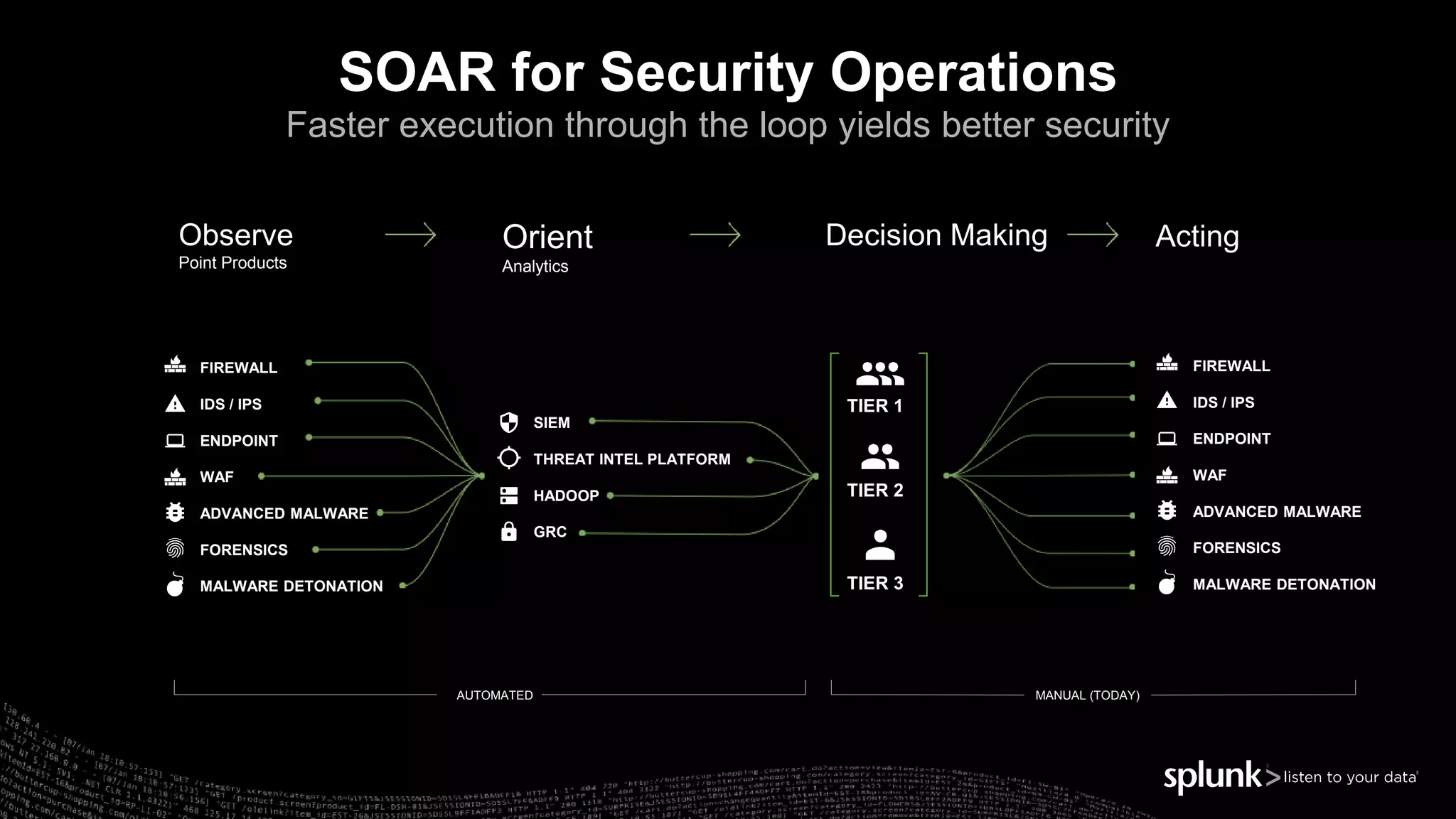
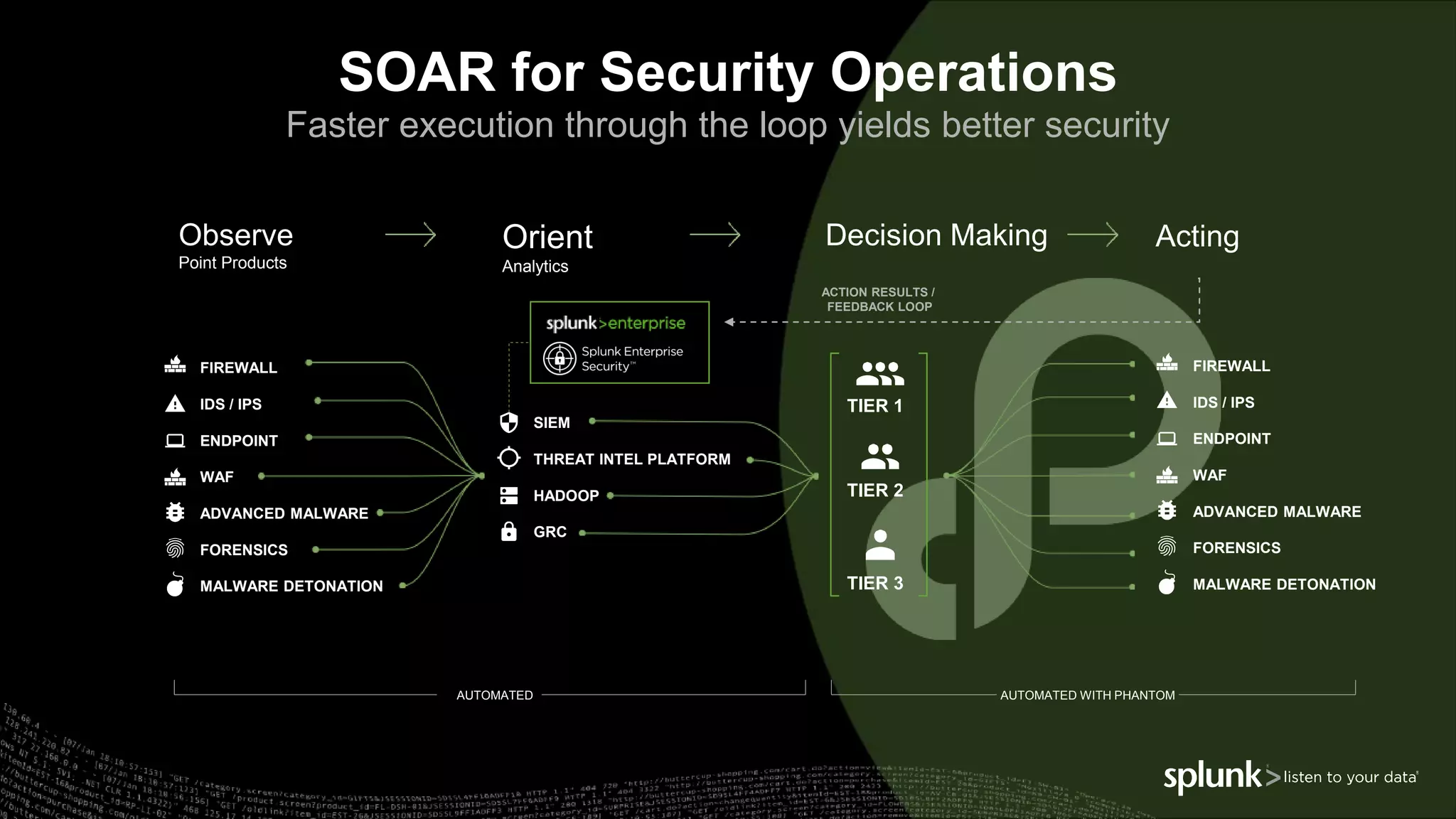
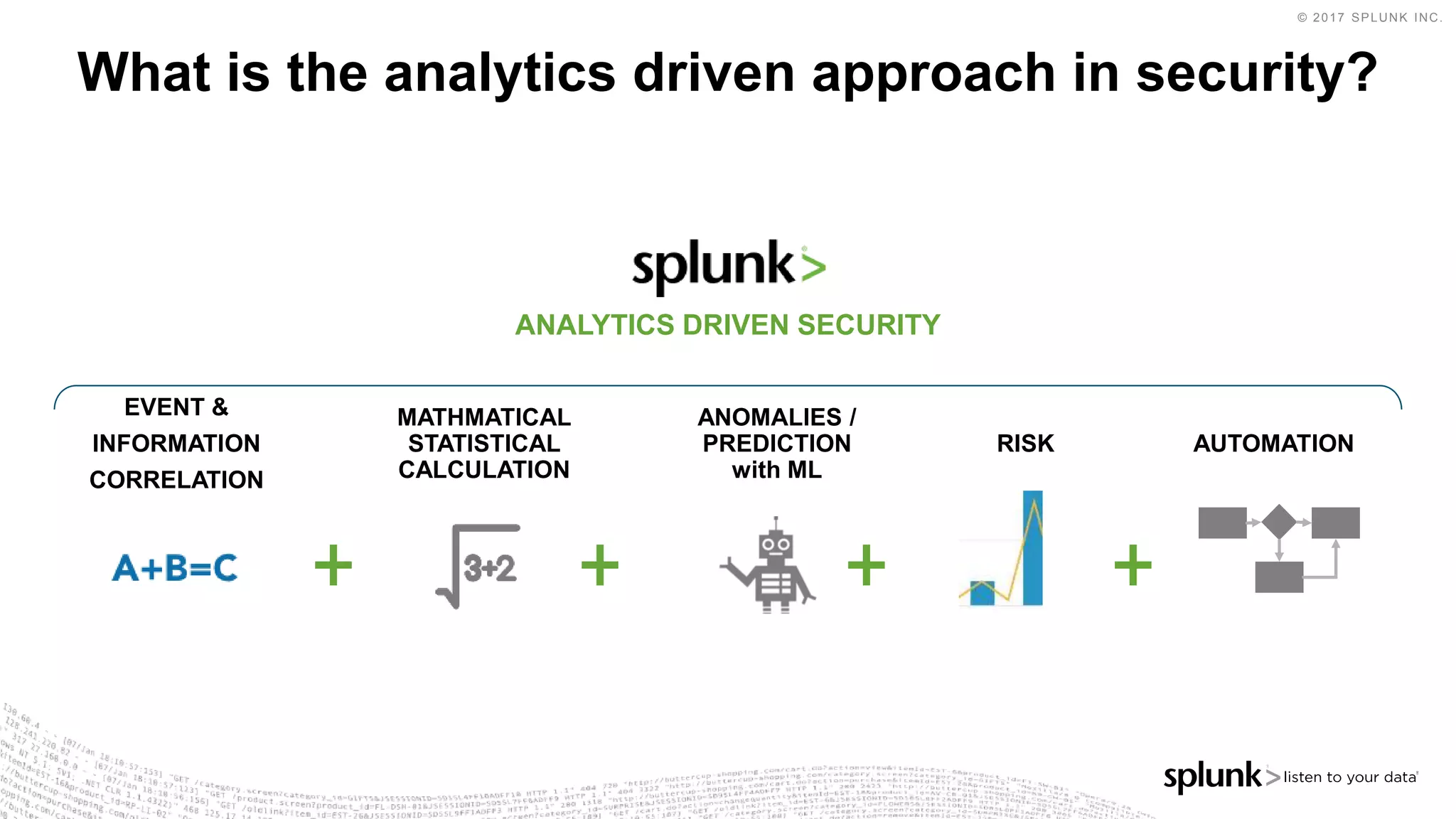
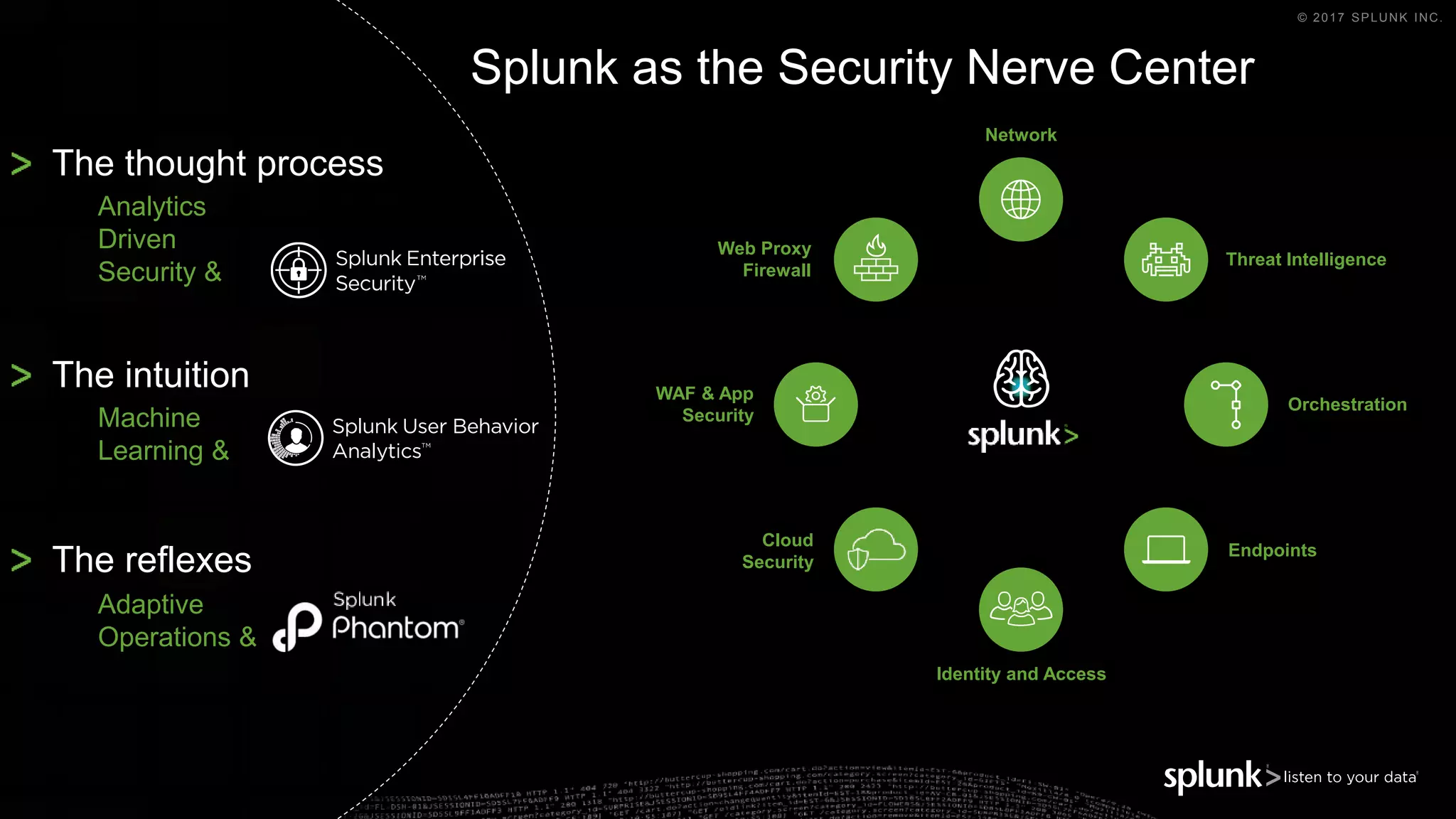
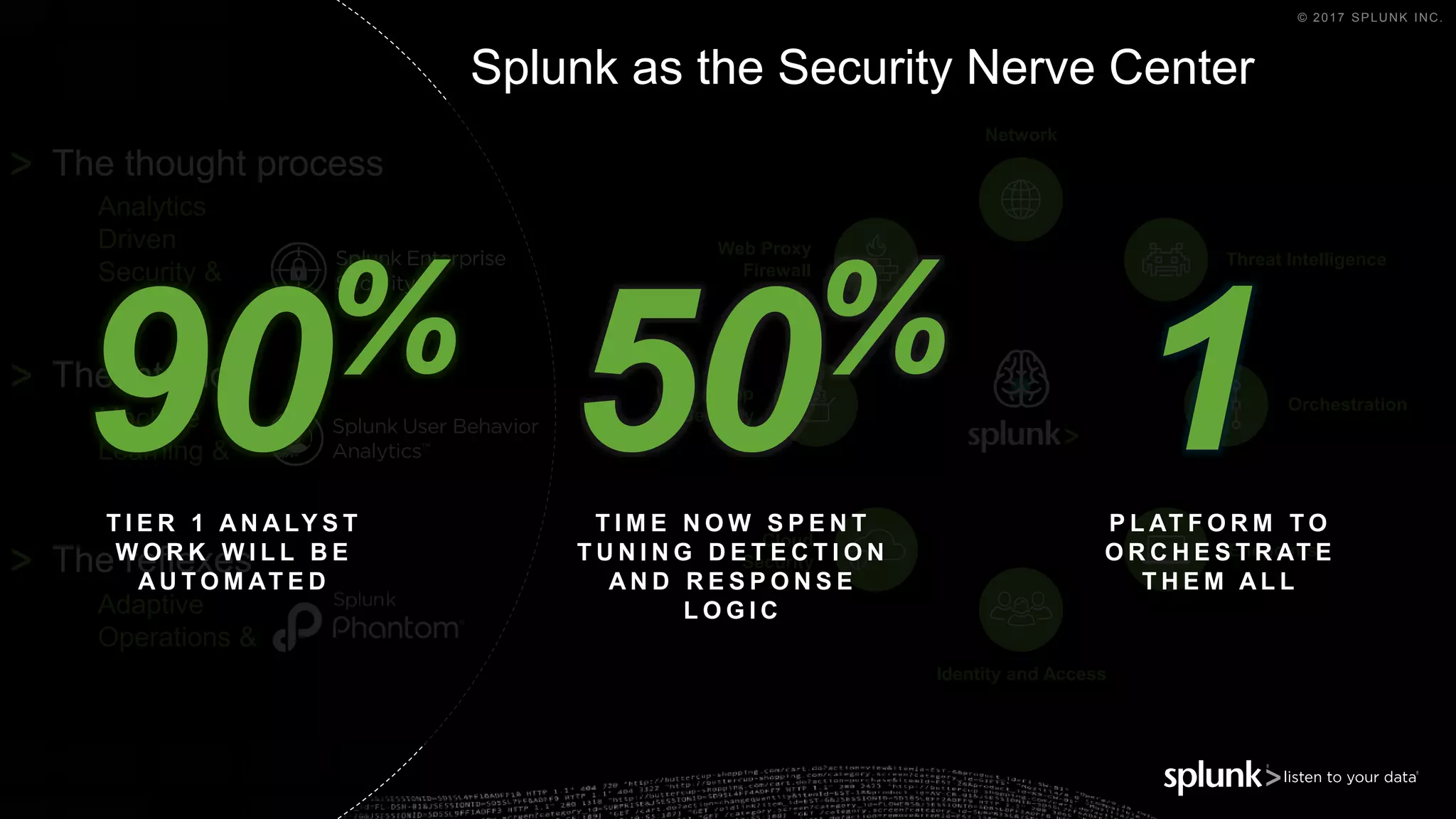
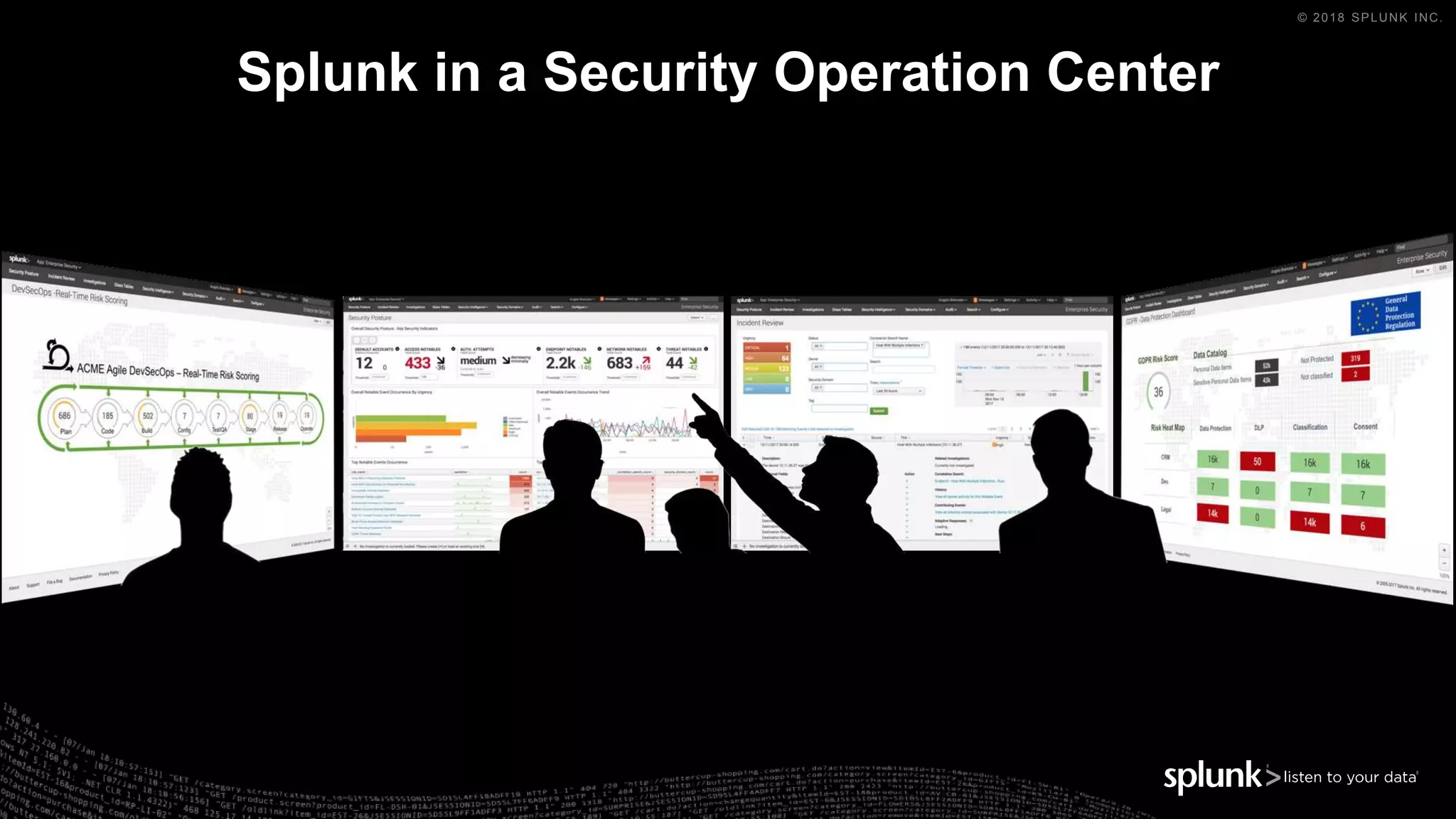
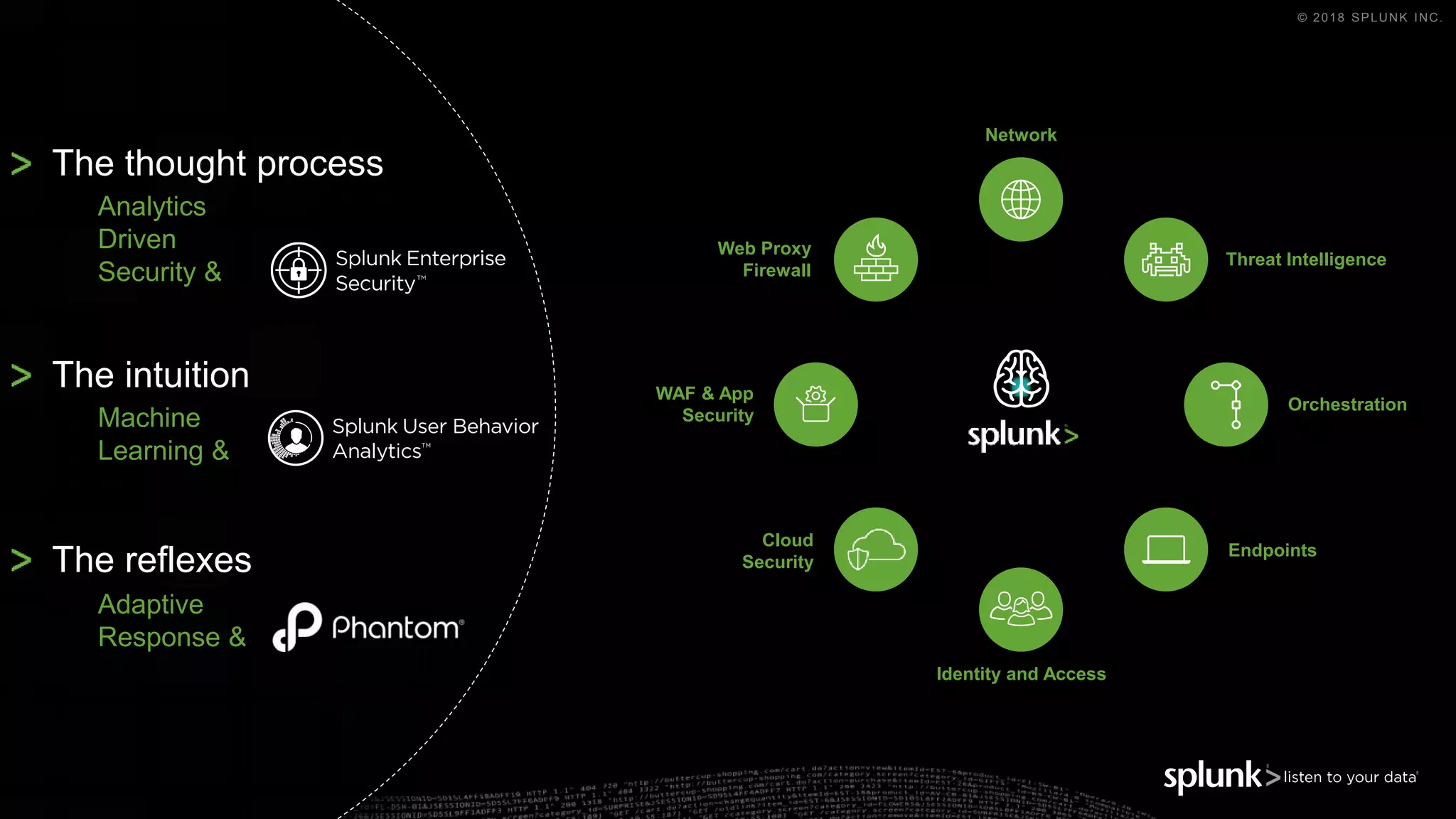
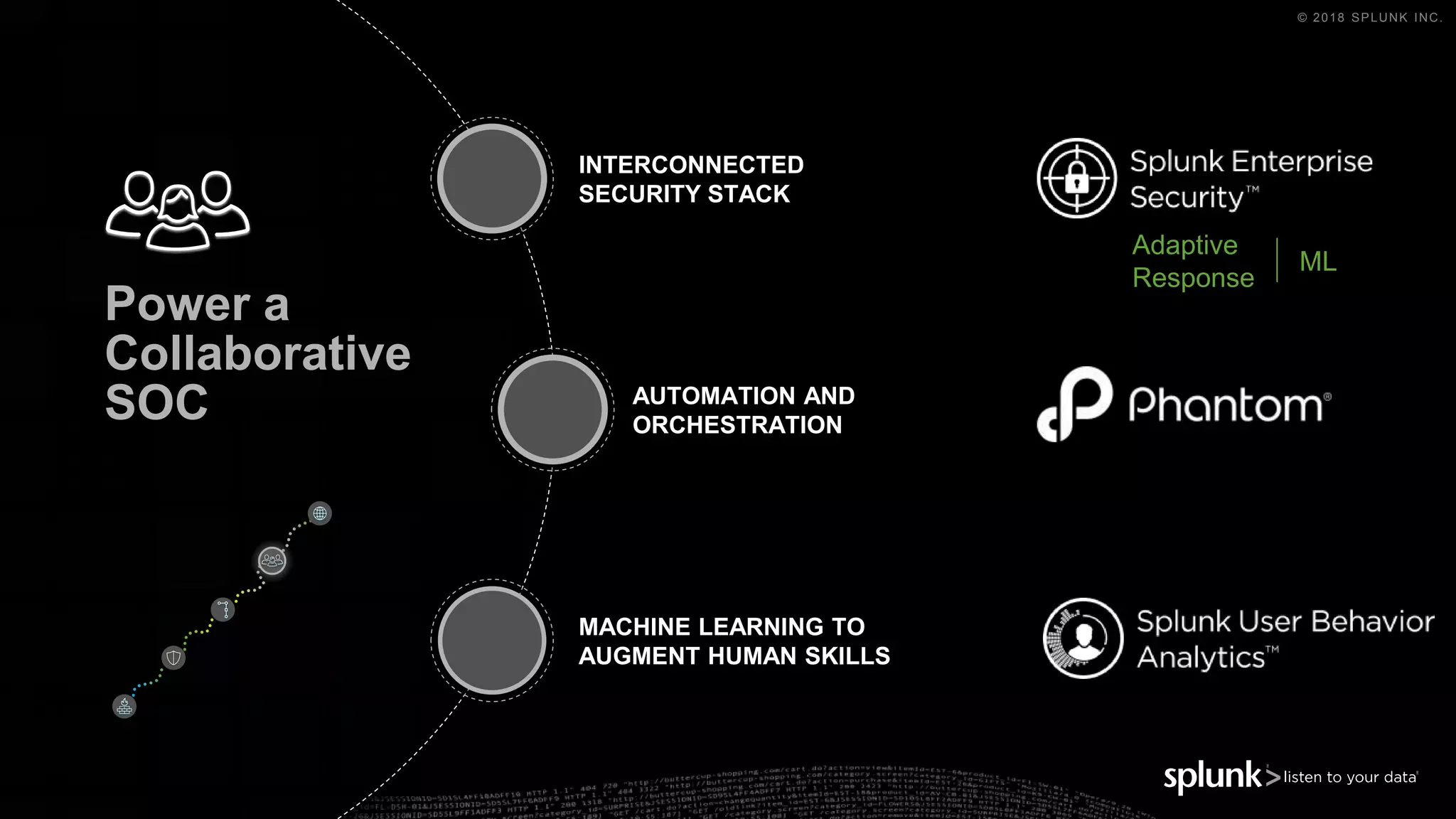
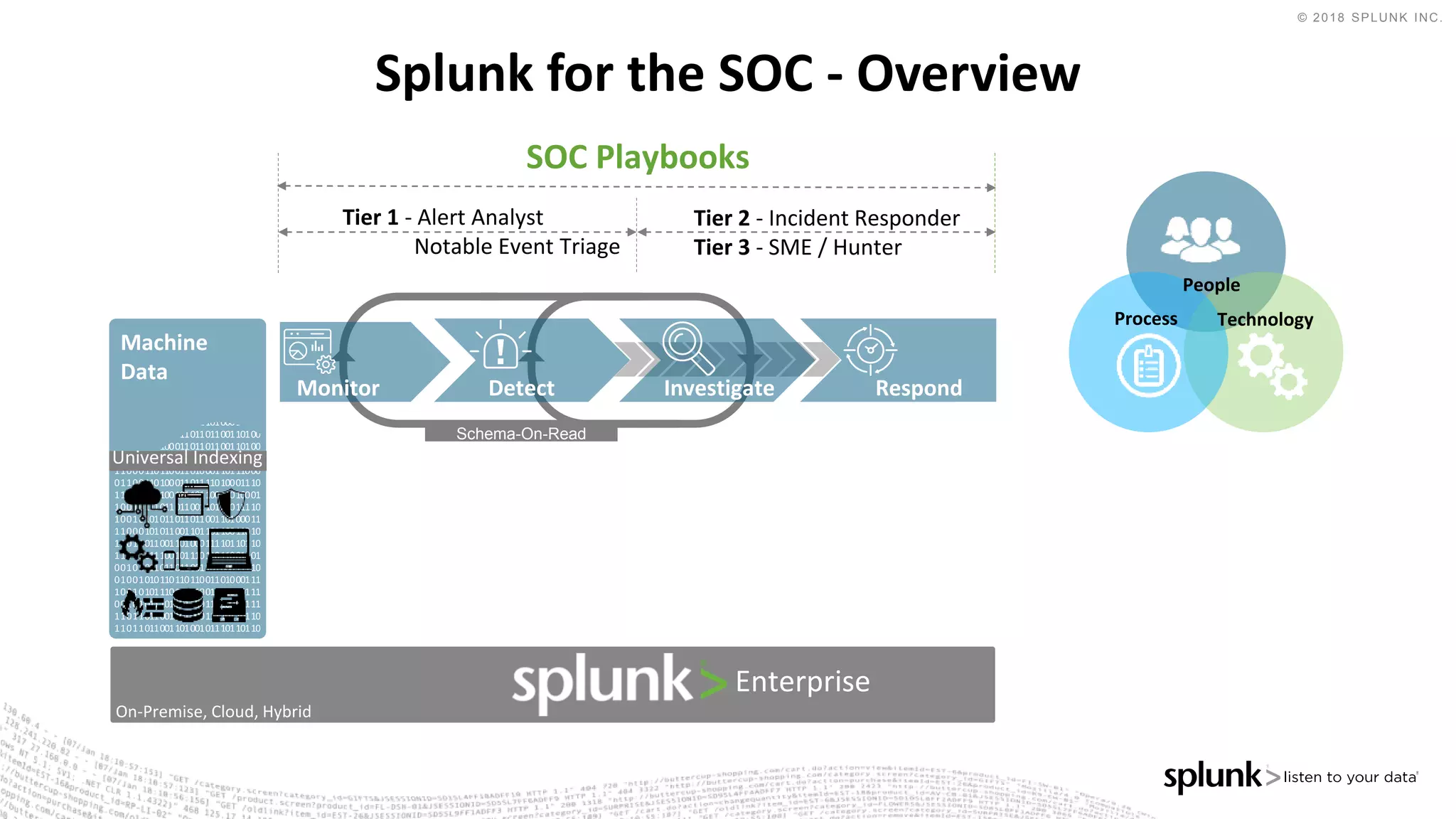
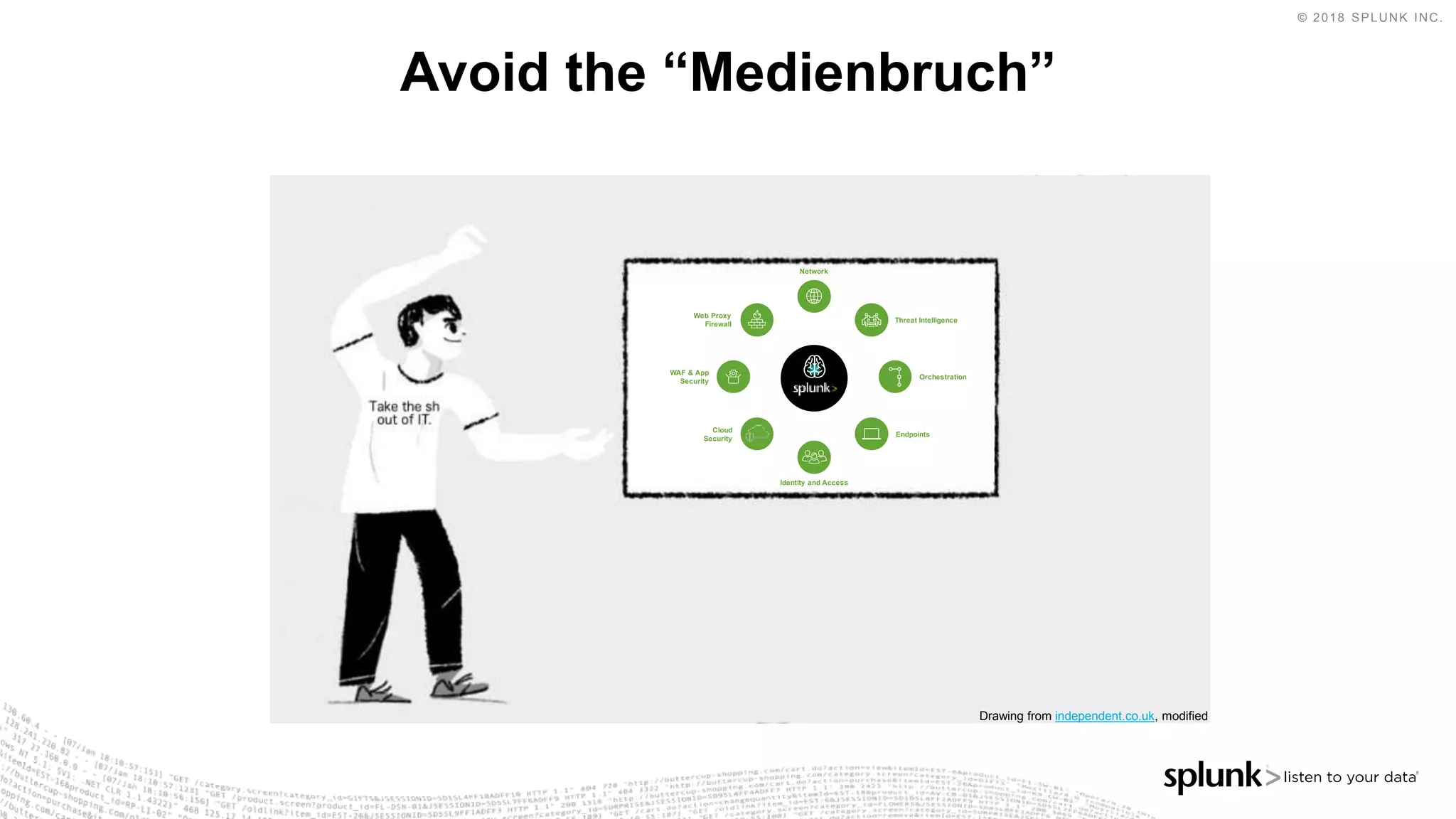
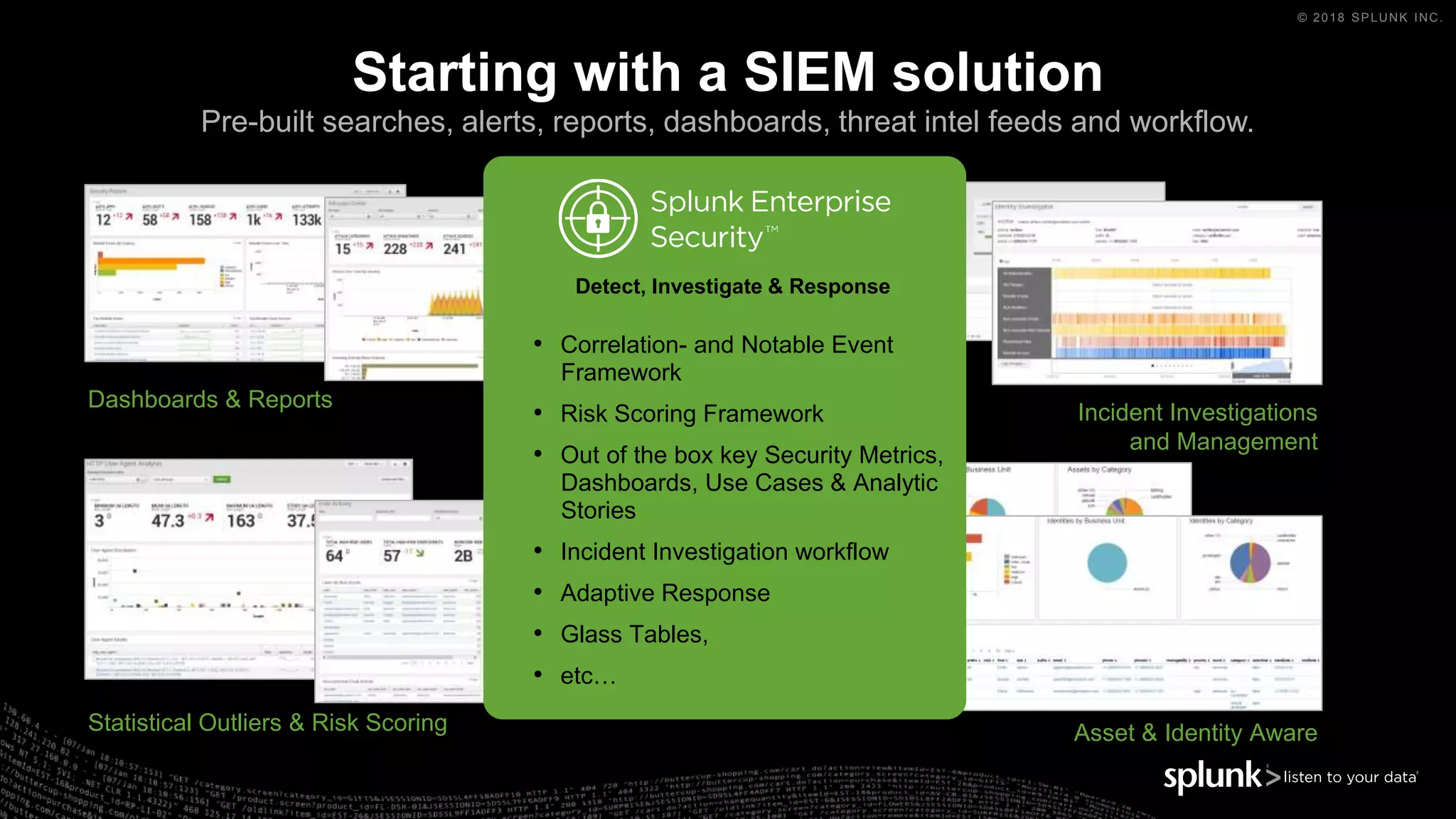
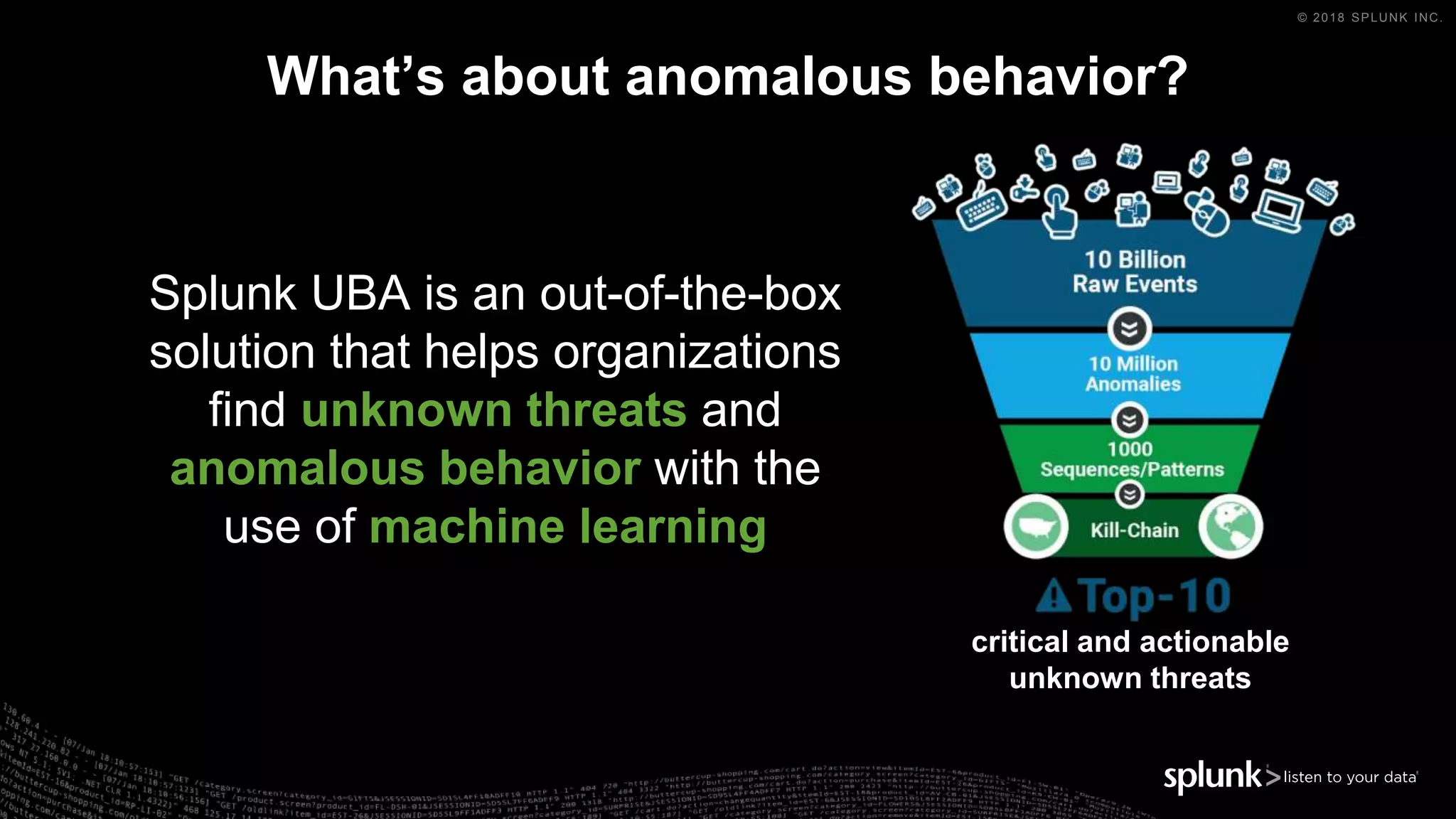
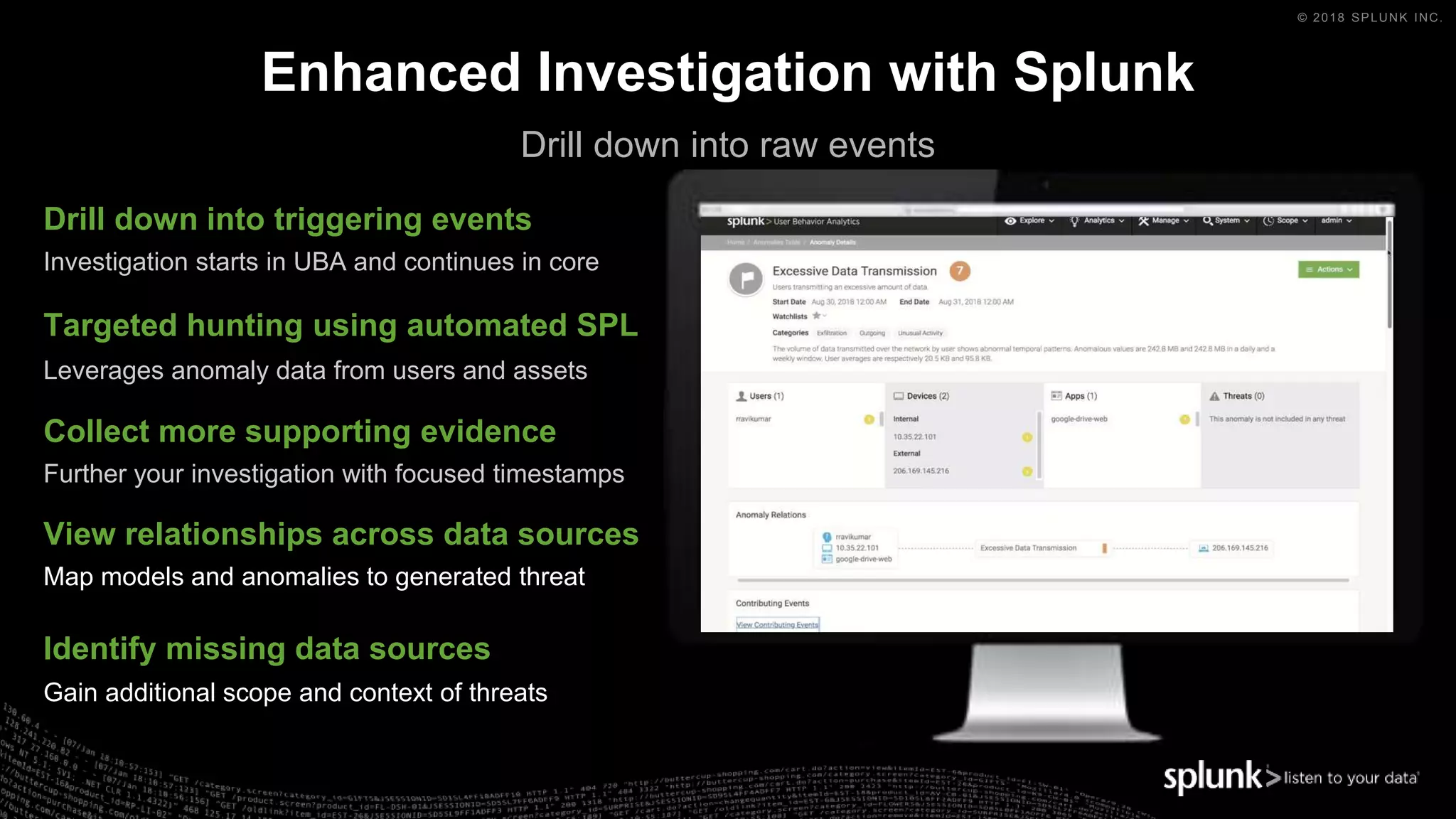
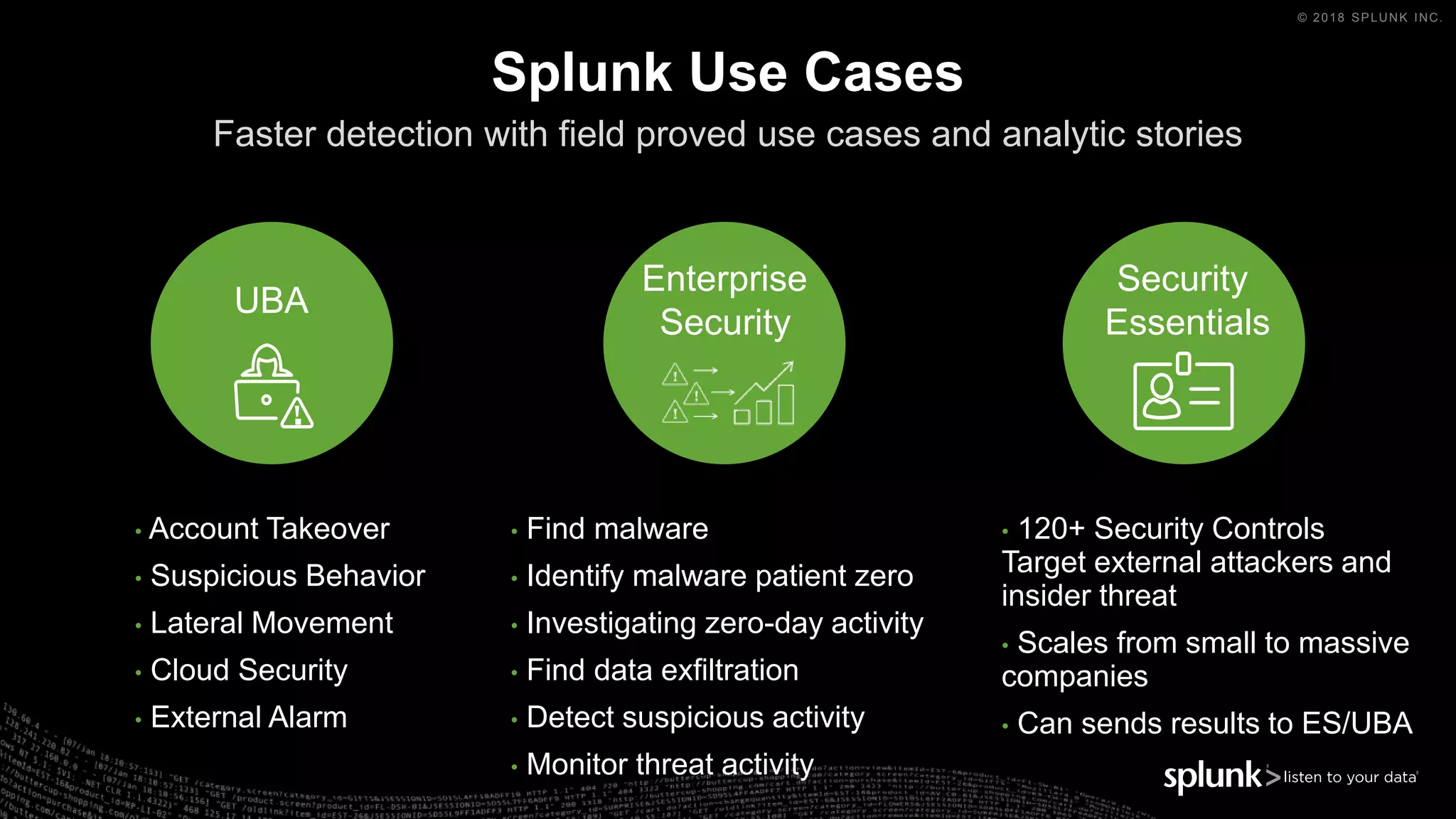
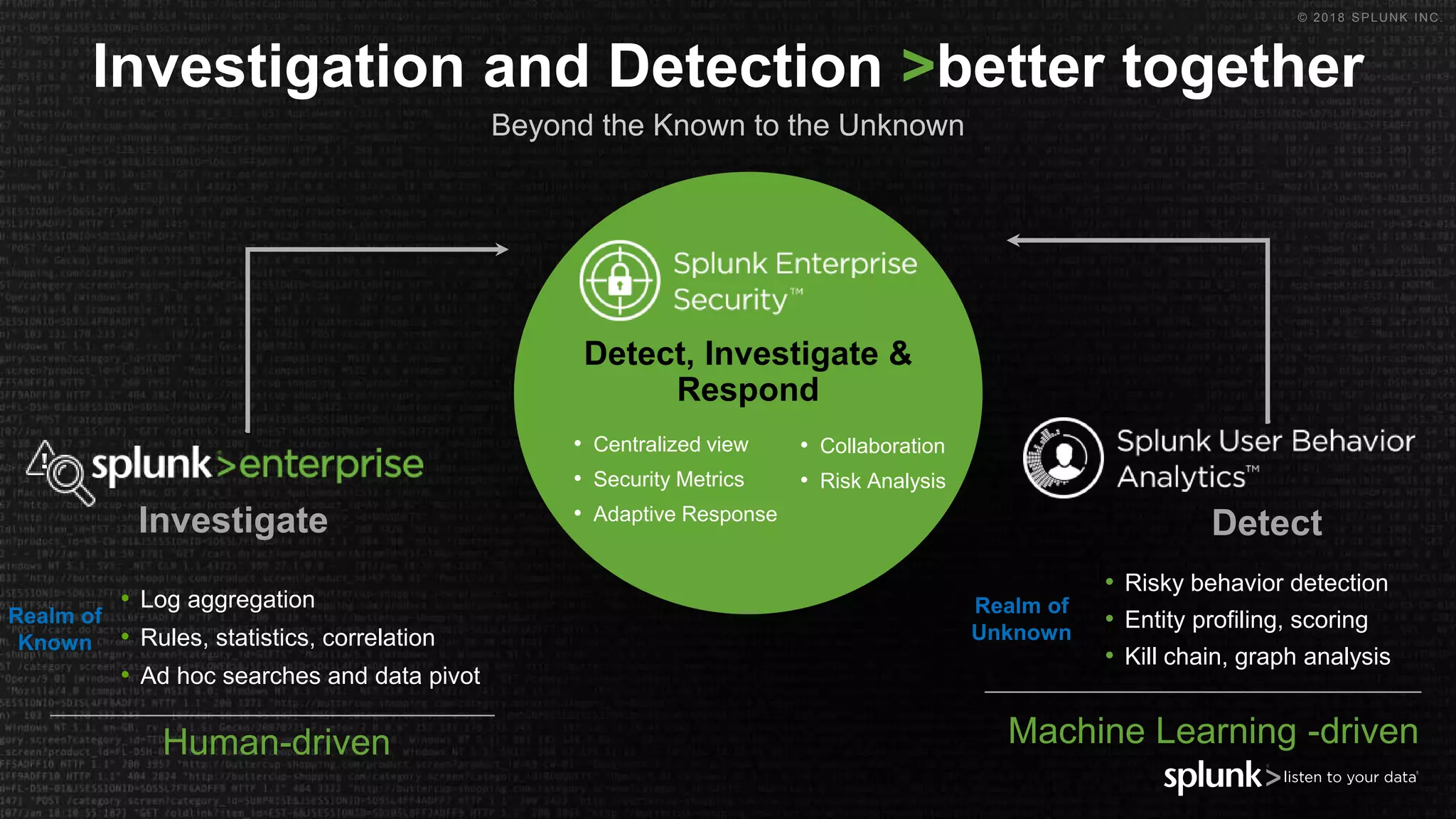
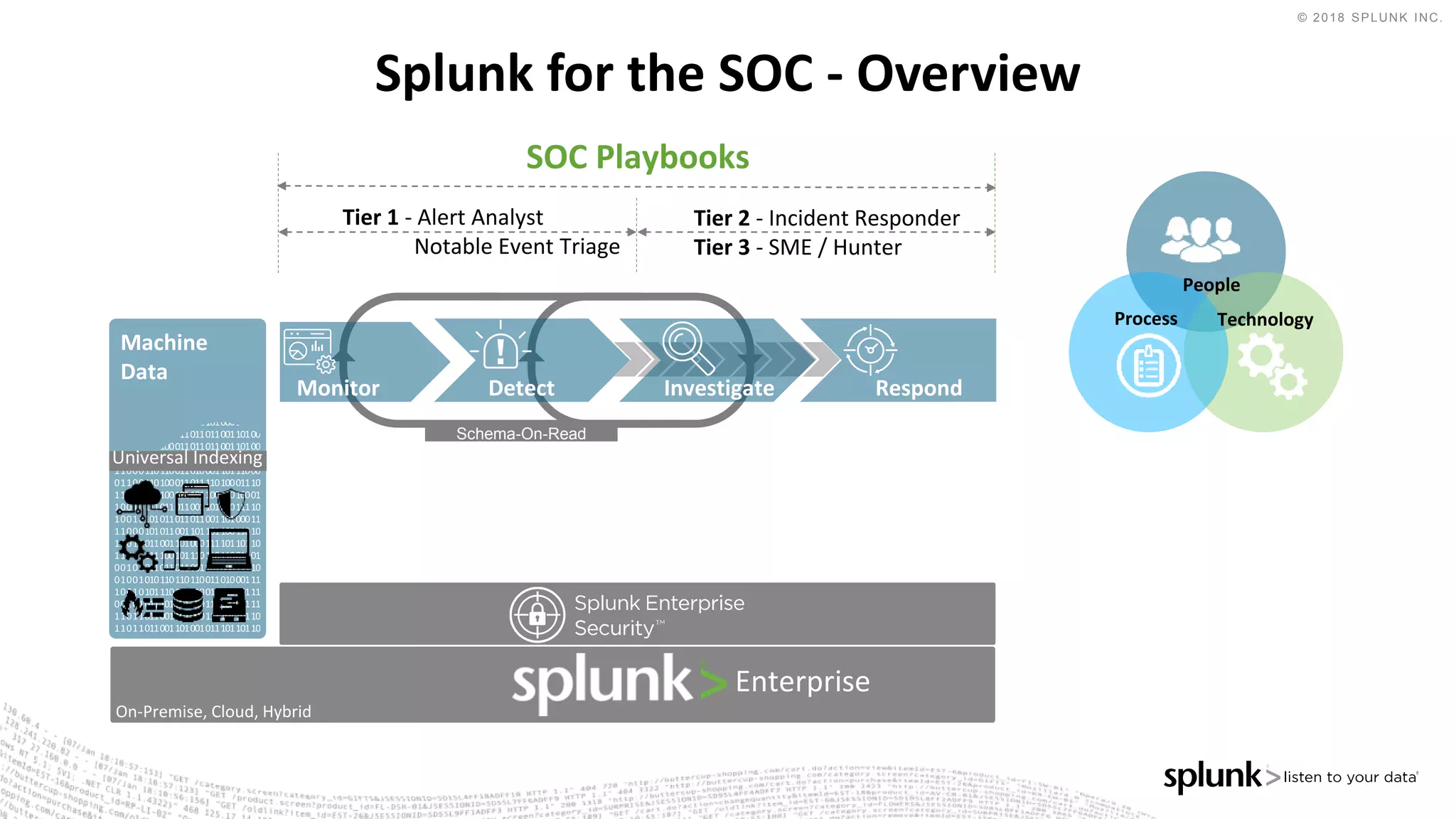
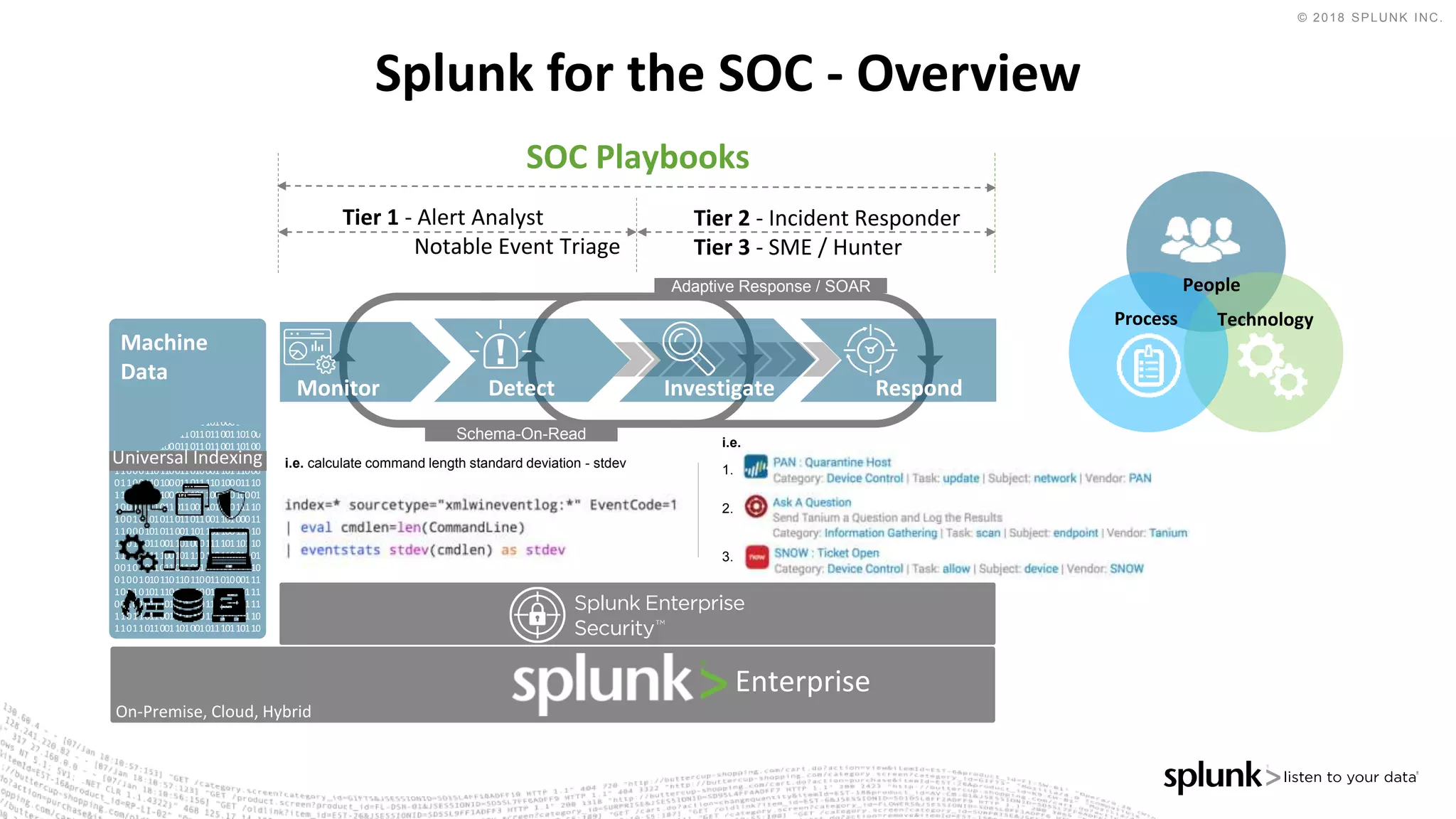
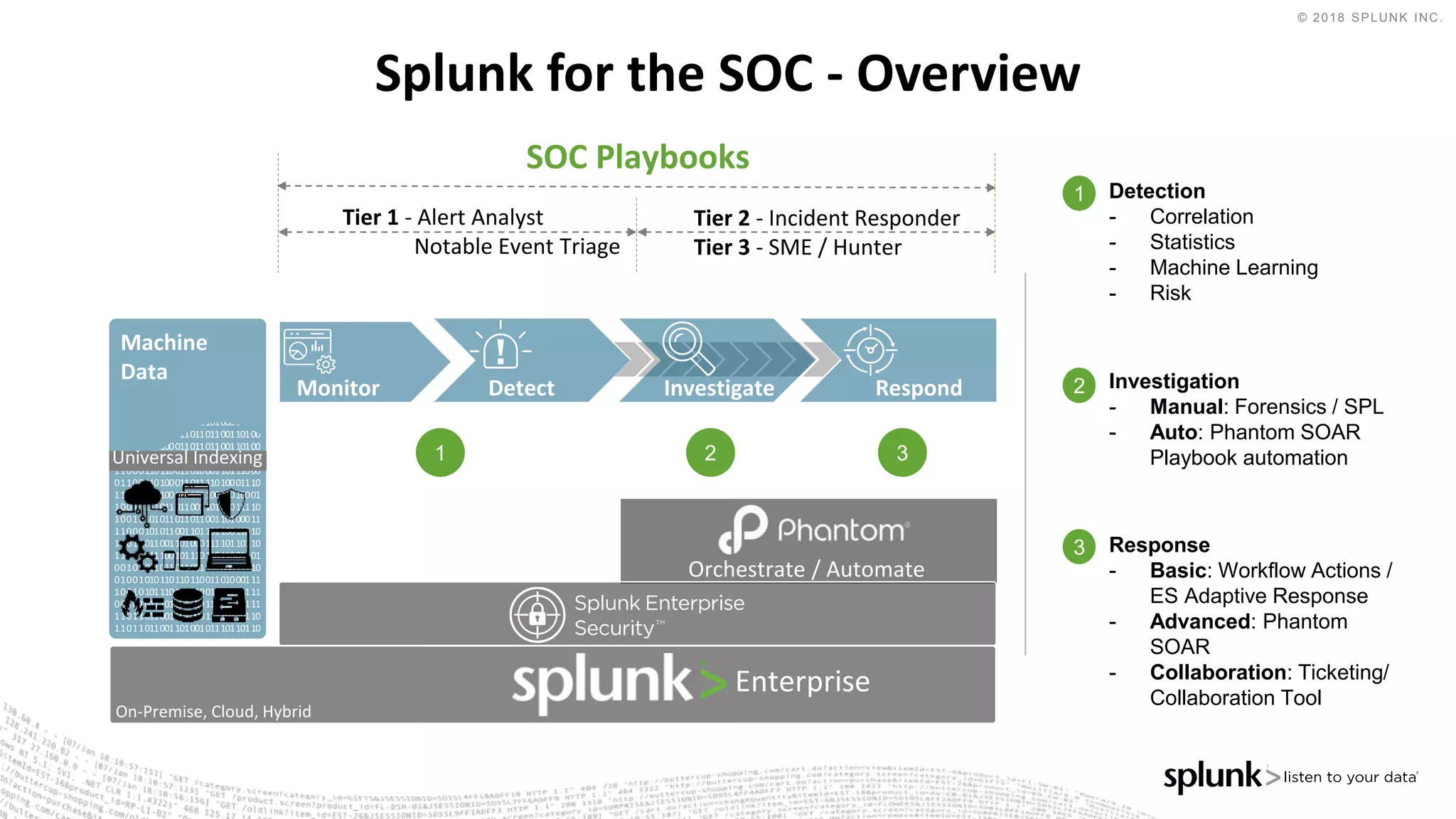
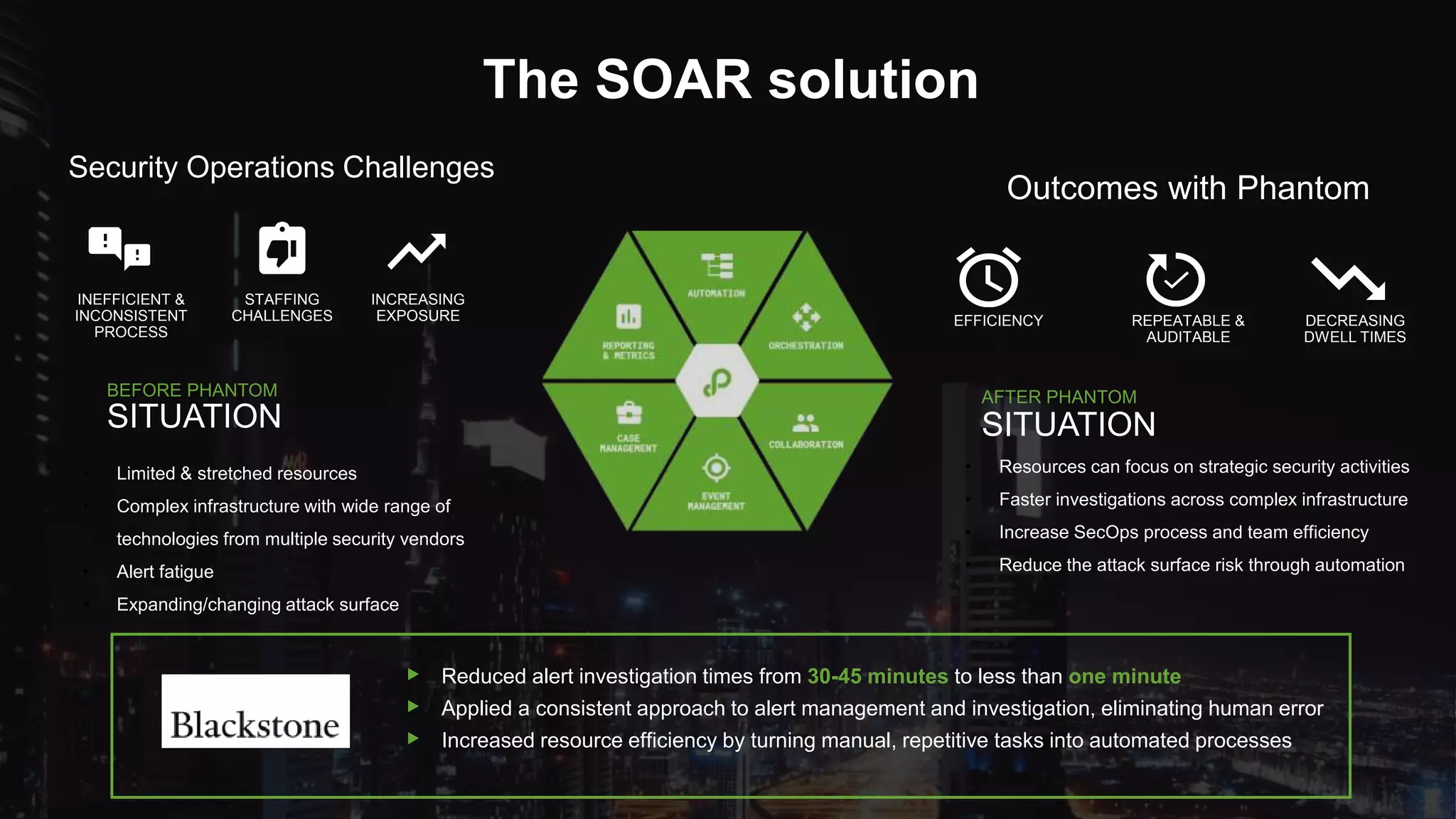
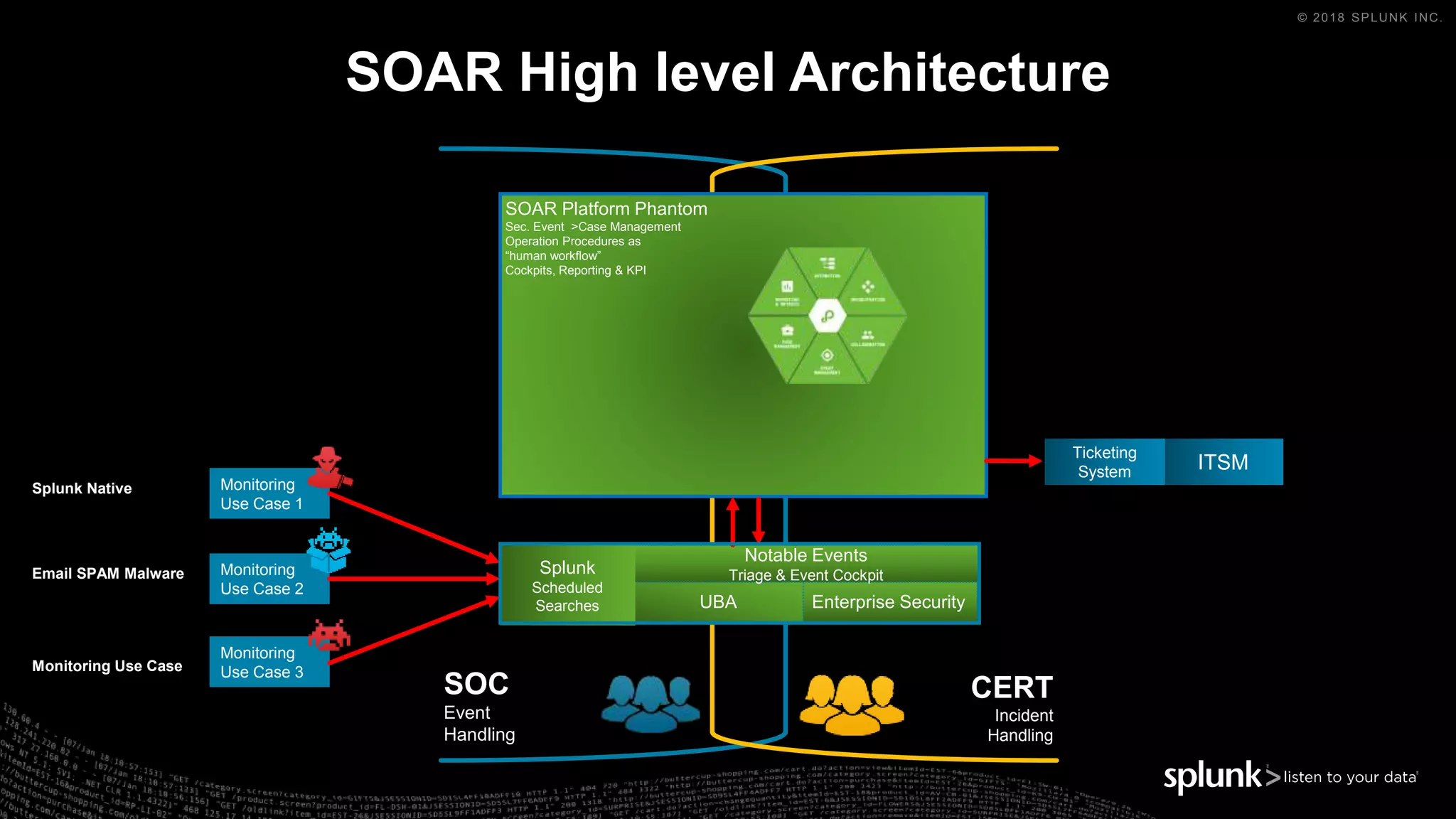
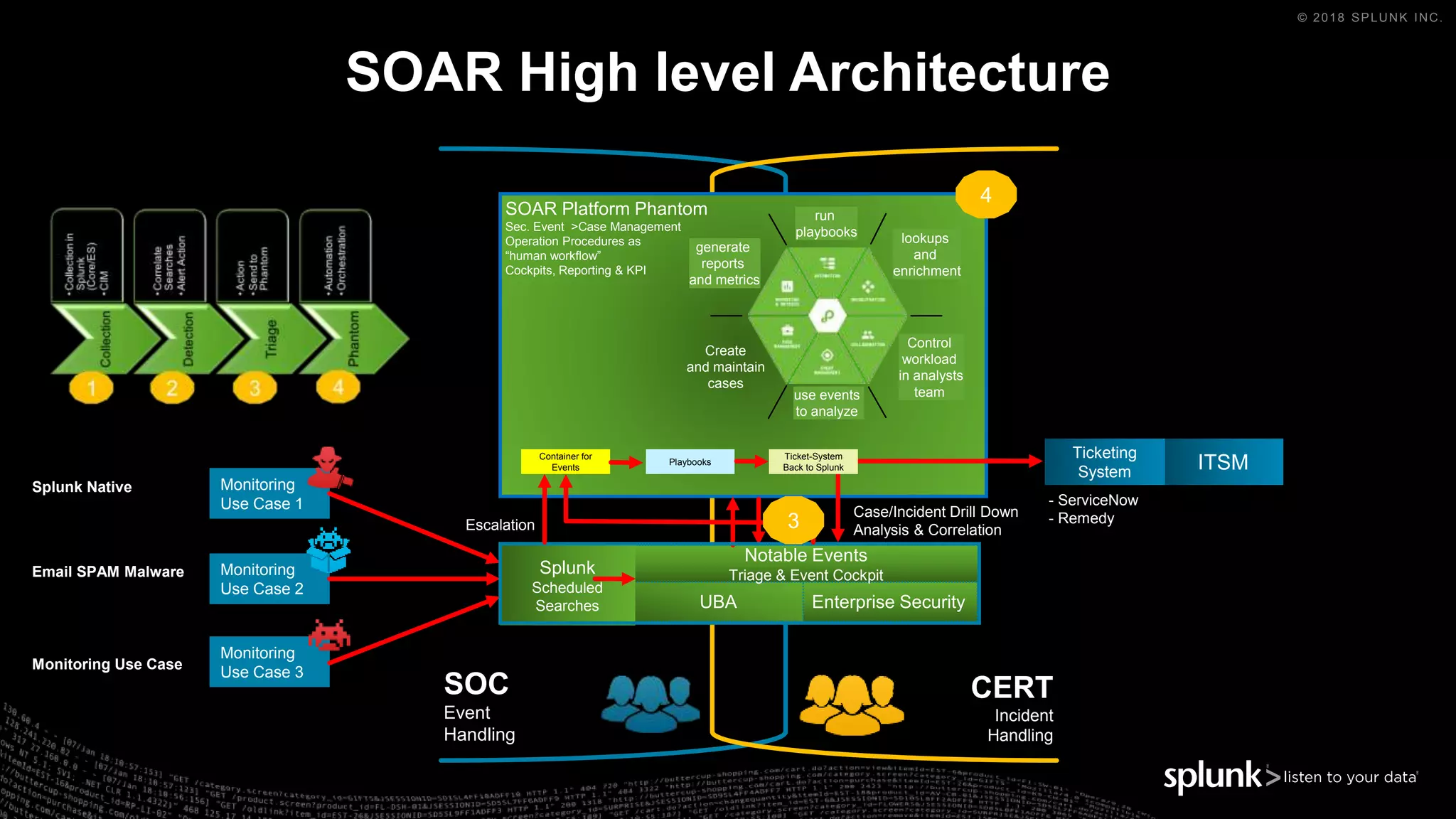
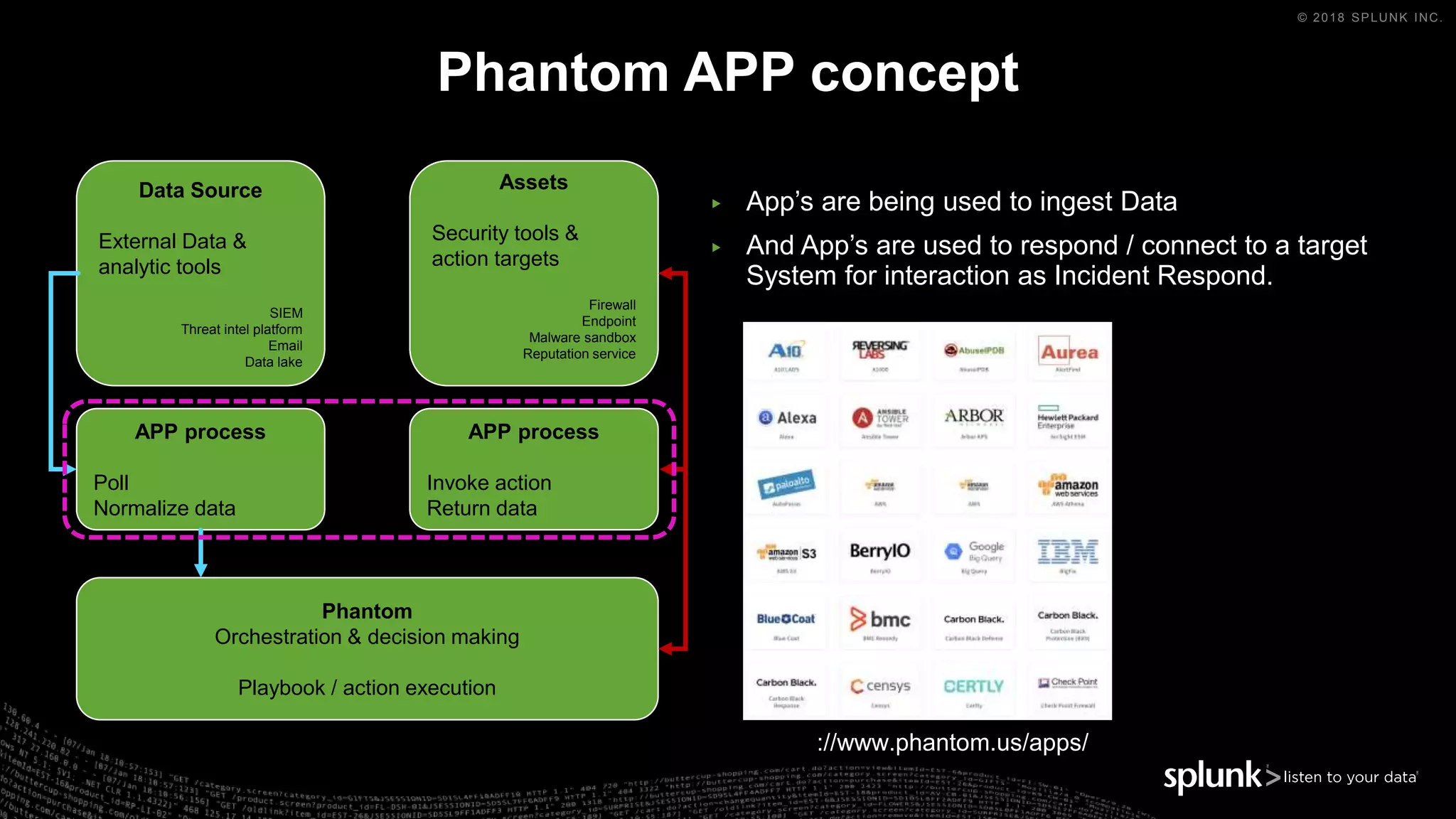
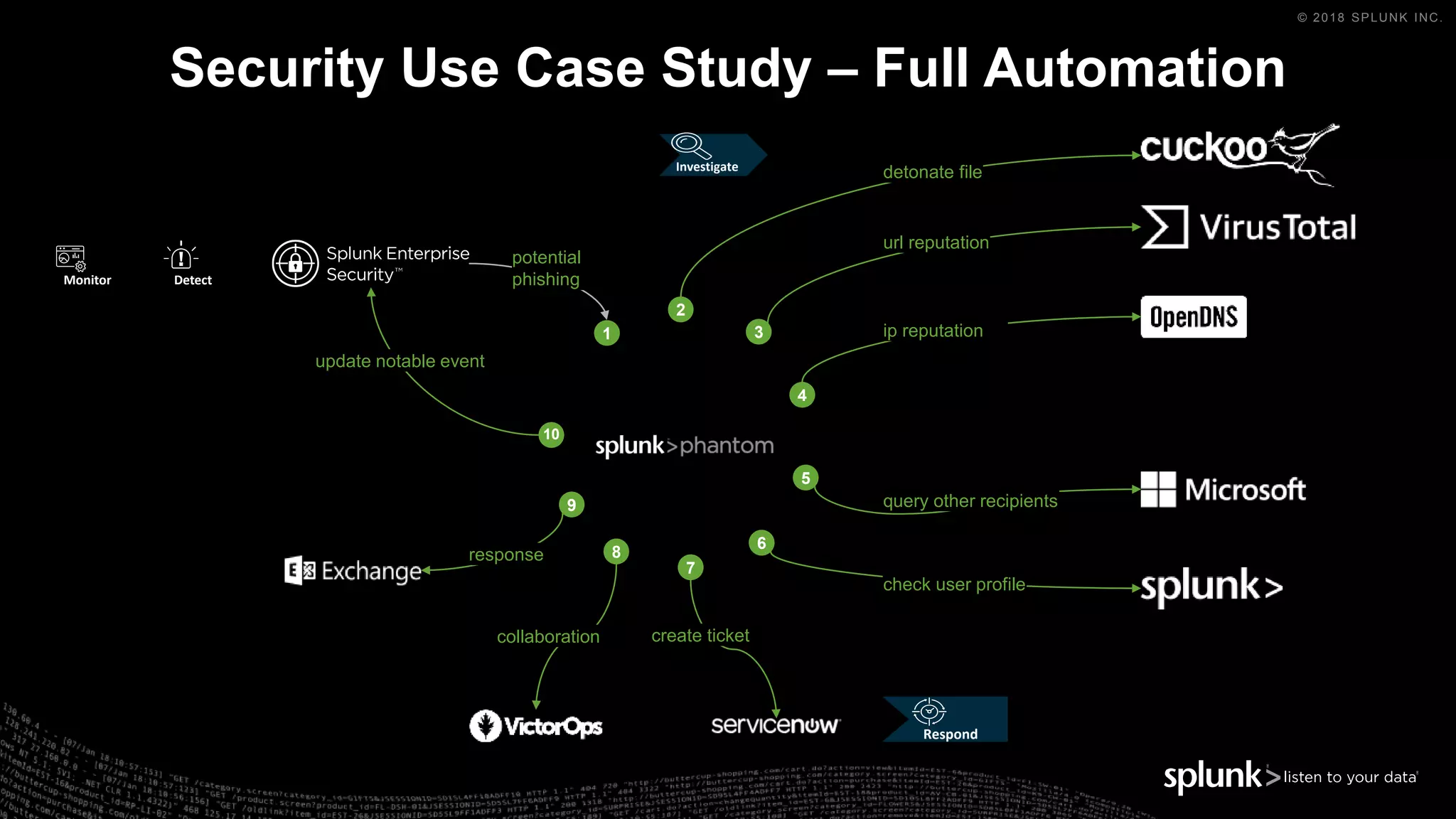
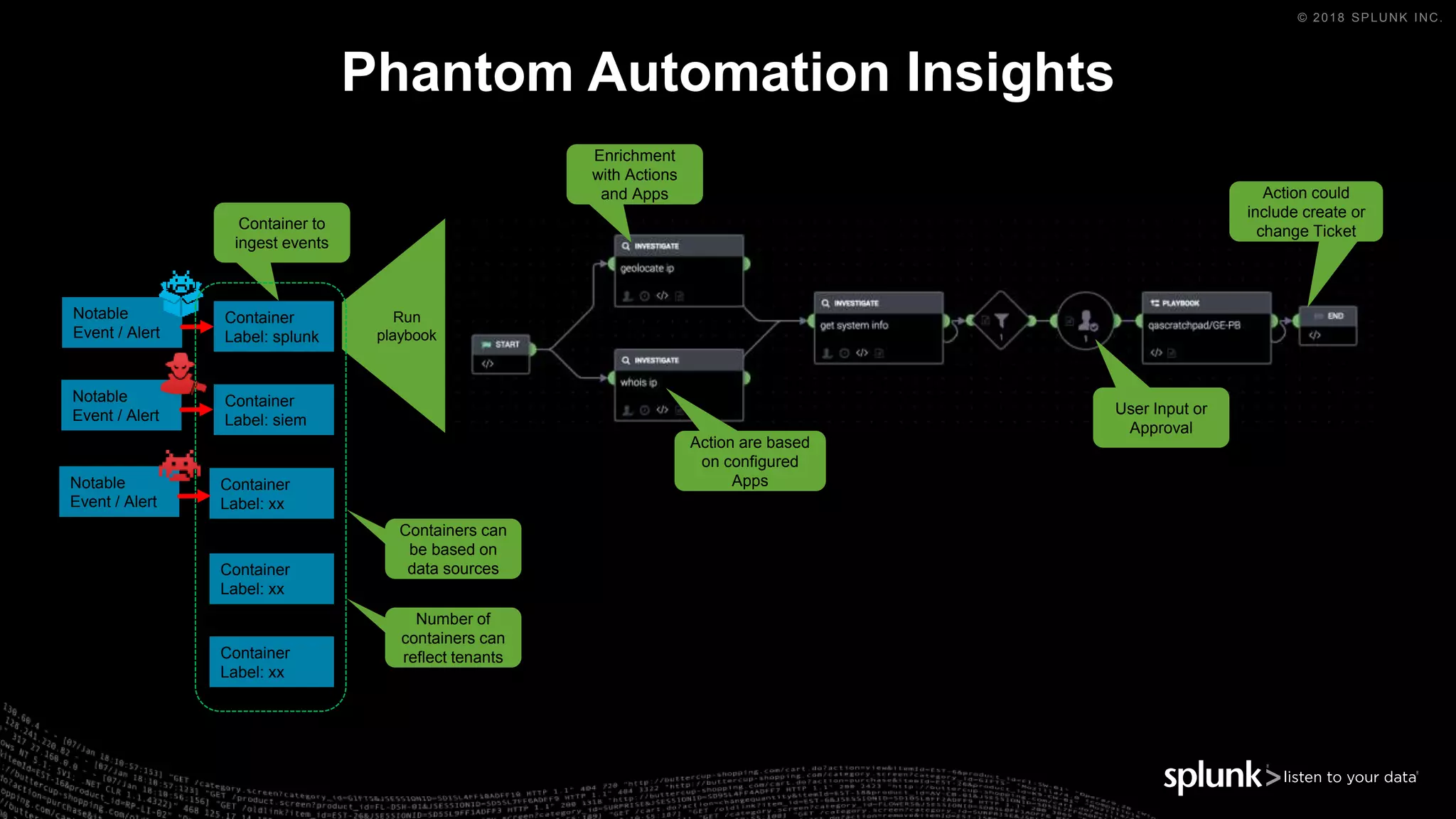
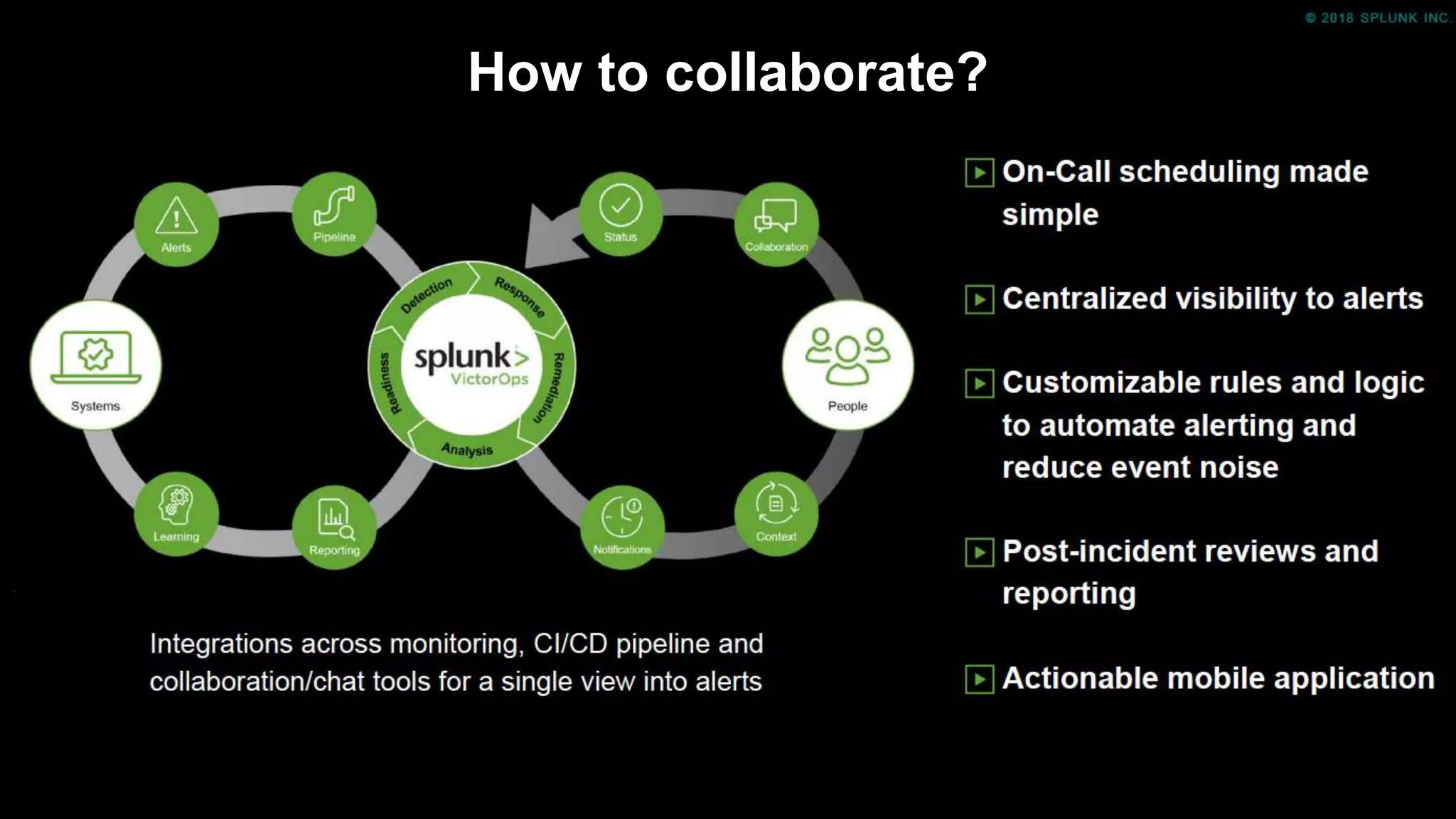
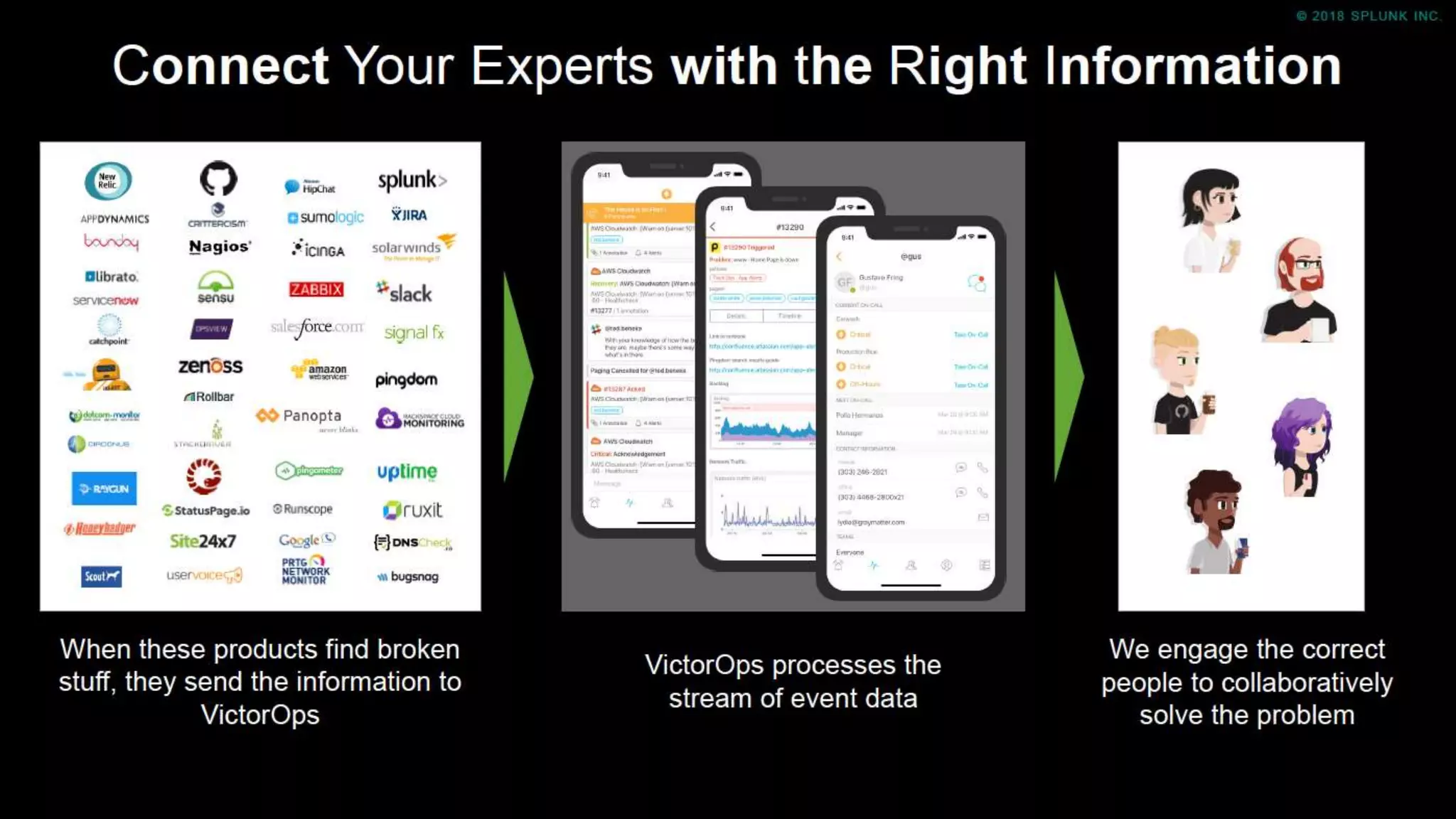
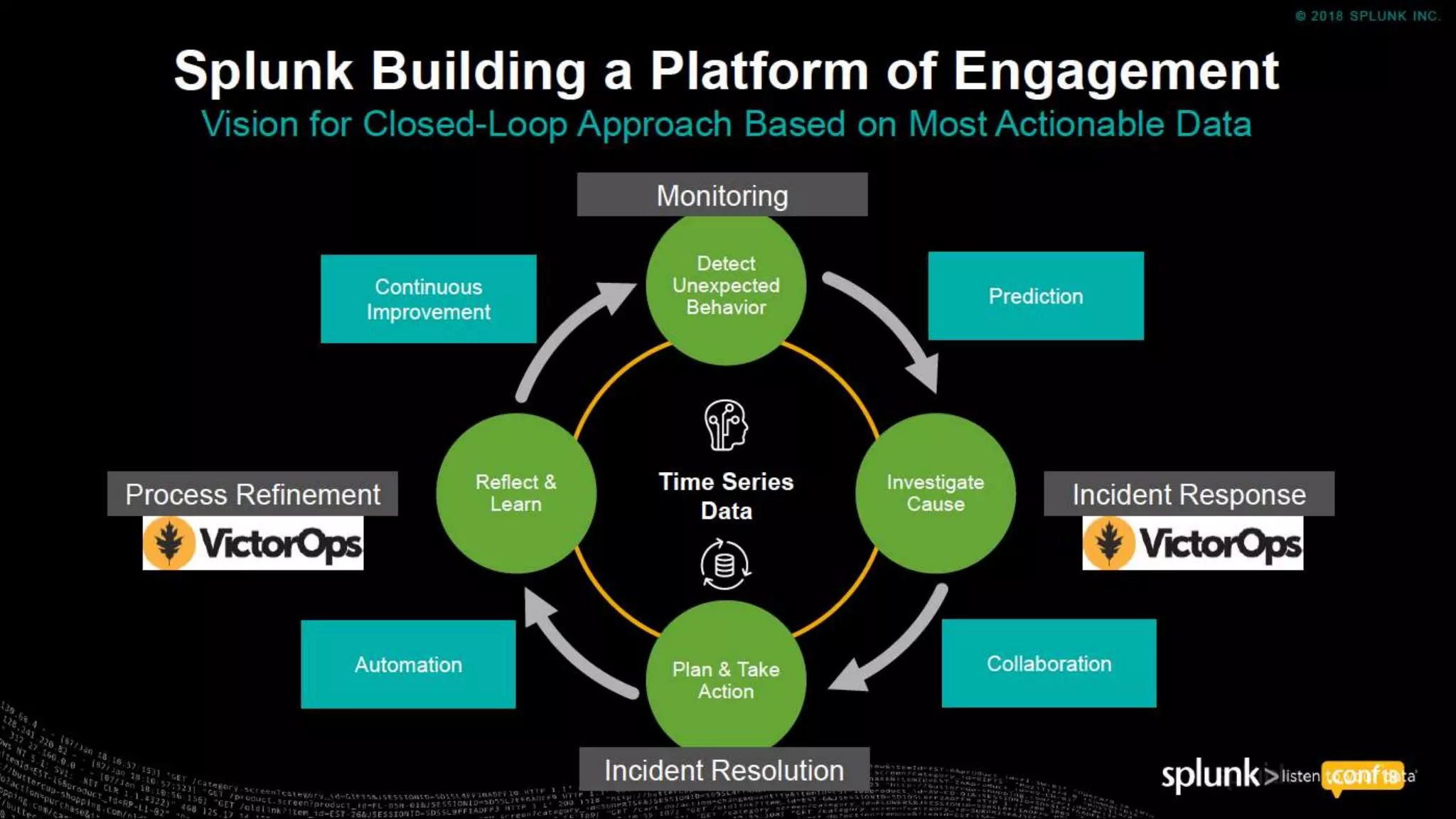
The document outlines the Splunk Aisecops initiative, focusing on automated incident response and security operations using Splunk's products. It includes an agenda for a presentation that details how to utilize machine data for security automation, highlights the challenges in security investigations, and showcases Splunk's roadmap and innovations in the field. The document emphasizes the importance of adapting to complex security threats through analytics, machine learning, and automated processes.