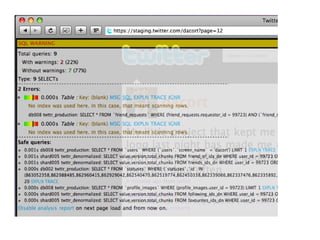
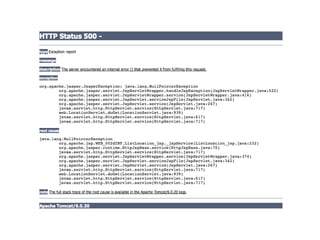
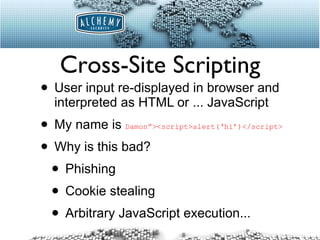
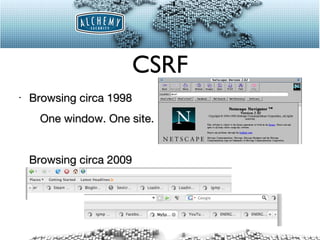
The document discusses common web application security issues such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF), highlighting how these vulnerabilities can be exploited. It emphasizes the importance of input sanitization, data encoding, and system updates to mitigate risks. The text also notes specific challenges related to social media APIs, particularly in the context of protecting user data and privacy.


![SQL Injection $sql = “SELECT * FROM users WHERE username = ‘“ . $_POST[‘username’] . “‘ AND password = ‘“ . $_POST[‘password’] . “‘“; What if username is: “dpc’ or ‘a’=’a” ? ... username = ‘ dpc’ or ‘a’=’a ‘ ... SQL Server 2000 && xp_cmdshell](https://image.slidesharecdn.com/buildingsecuretwitterapps-091012155906-phpapp02/85/Building-Secure-Twitter-Apps-4-320.jpg)







![Retrieve Username $.getJSON(" http://twitter.com /statuses/user_timeline?count=1&callback=? ", function(data) { alert("Username is: " + data[0].user.screen_name ) }); {"text":"Pretty sure humans have kneecaps so we can slam them into tables. *ow*","truncated":false, "user" :{"following":null,"time_zone":"Pacific Time (US & Canada)","description":"Prof. Computer Security Consultant with a passion for breaking things and generating statistics (see http:\/\/tweetstats.com and http:\/\/ratemytalk.com).", "screen_name":"dacort" ,"utc_offset":-28800,"profile_sidebar_border_color":"87bc44","notifications":null,"created_at":"Thu Dec 21 07:14:05 +0000 2006","profile_text_color":"000000","url":"http:\/\/dcortesi.com","name":"Damon Cortesi","statuses_count":21385,"profile_background_image_url":"http:\/\/static.twitter.com\/images\/themes\/theme1\/bg.gif","followers_count":4441,"protected":false,"profile_link_color":"A100FF","profile_background_tile":false,"friends_count":1775,"profile_background_color":"000000","verified":false,"favourites_count":202,"profile_image_url":"http:\/\/s3.amazonaws.com\/twitter_production\/profile_images\/90802743\/Famous_Glasses_normal.jpg","location":"Seattle, WA","id":99723,"profile_sidebar_fill_color":"e0ff92"},"in_reply_to_status_id":null,"created_at":"Mon Jul 27 21:37:53 +0000 2009","in_reply_to_user_id":null,"favorited":false,"in_reply_to_screen_name":null,"id":2877957719,"source":"<a href=\"http:\/\/ www.atebits.com \/\">Tweetie<\/a>"}](https://image.slidesharecdn.com/buildingsecuretwitterapps-091012155906-phpapp02/85/Building-Secure-Twitter-Apps-15-320.jpg)