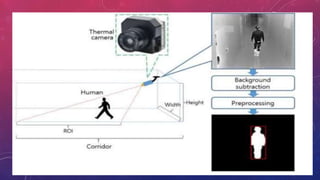
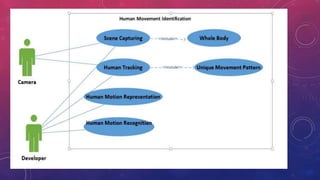
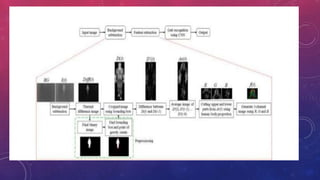
The document presents a method for human identification based on body movements, particularly when facial recognition is not possible. It emphasizes using a thermal camera to capture and preprocess images for identifying individuals even if their faces are obscured. The methodology includes image processing techniques like noise filtering and morphological operations to accurately detect and recognize human movements.