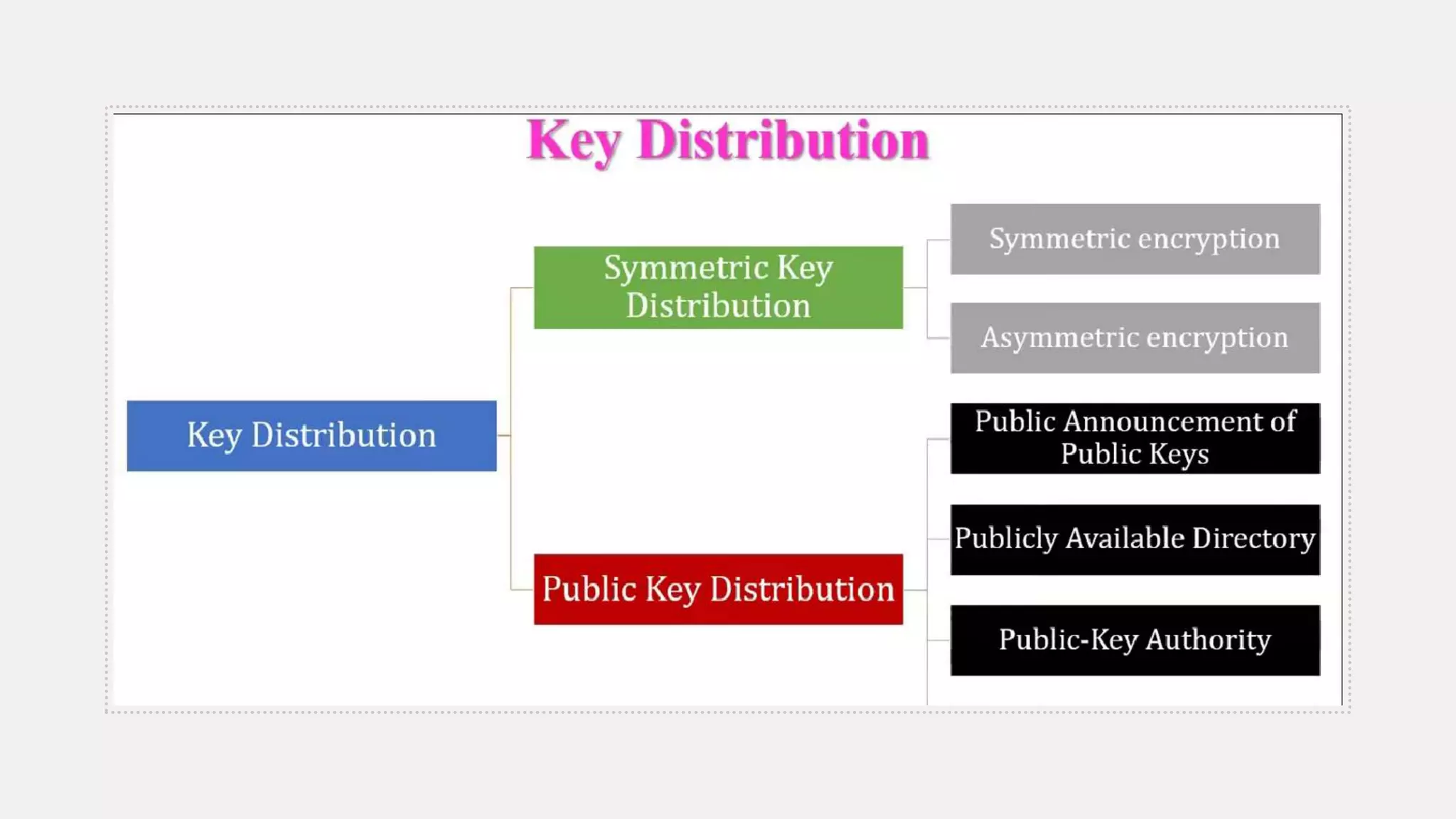
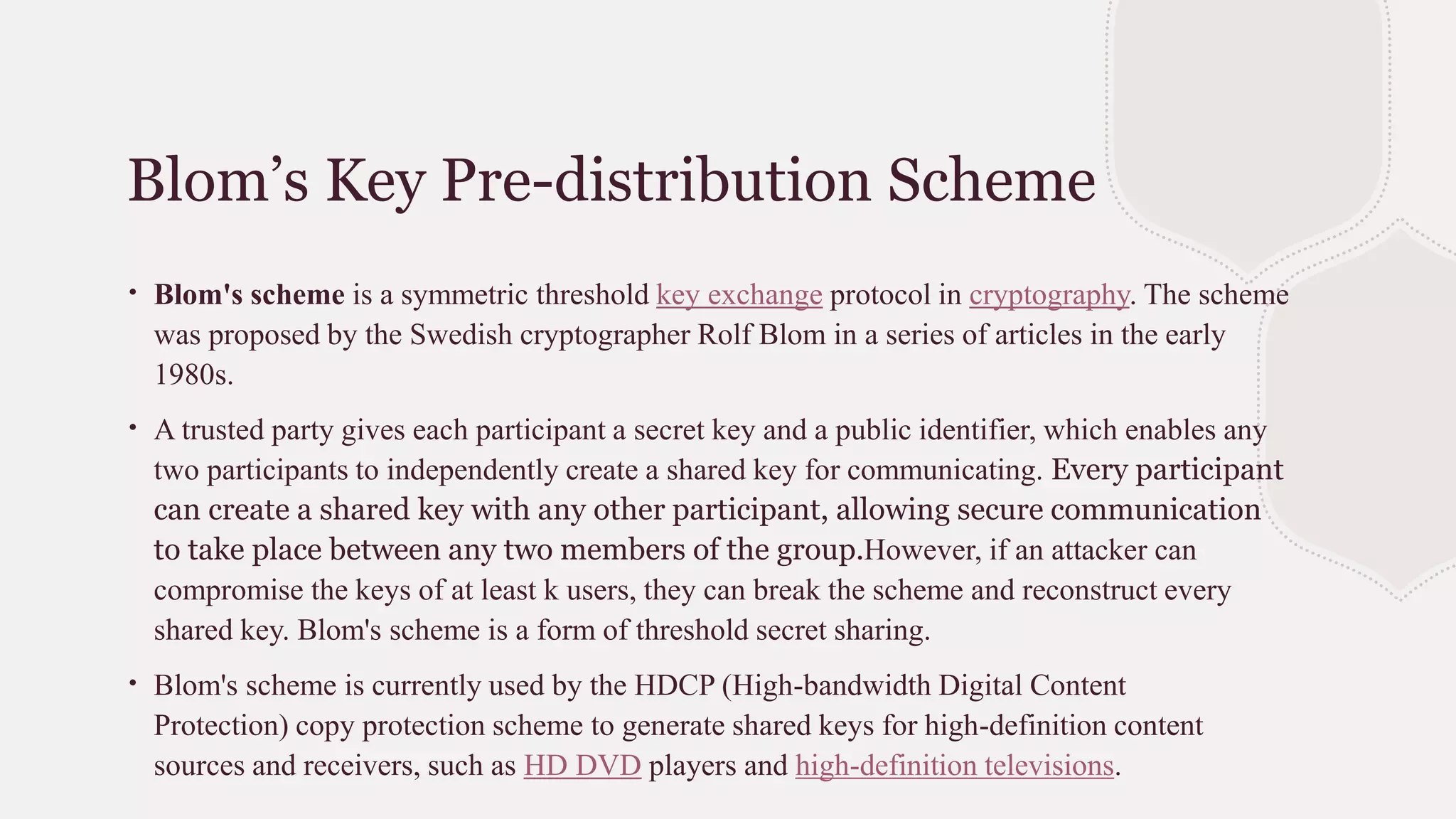
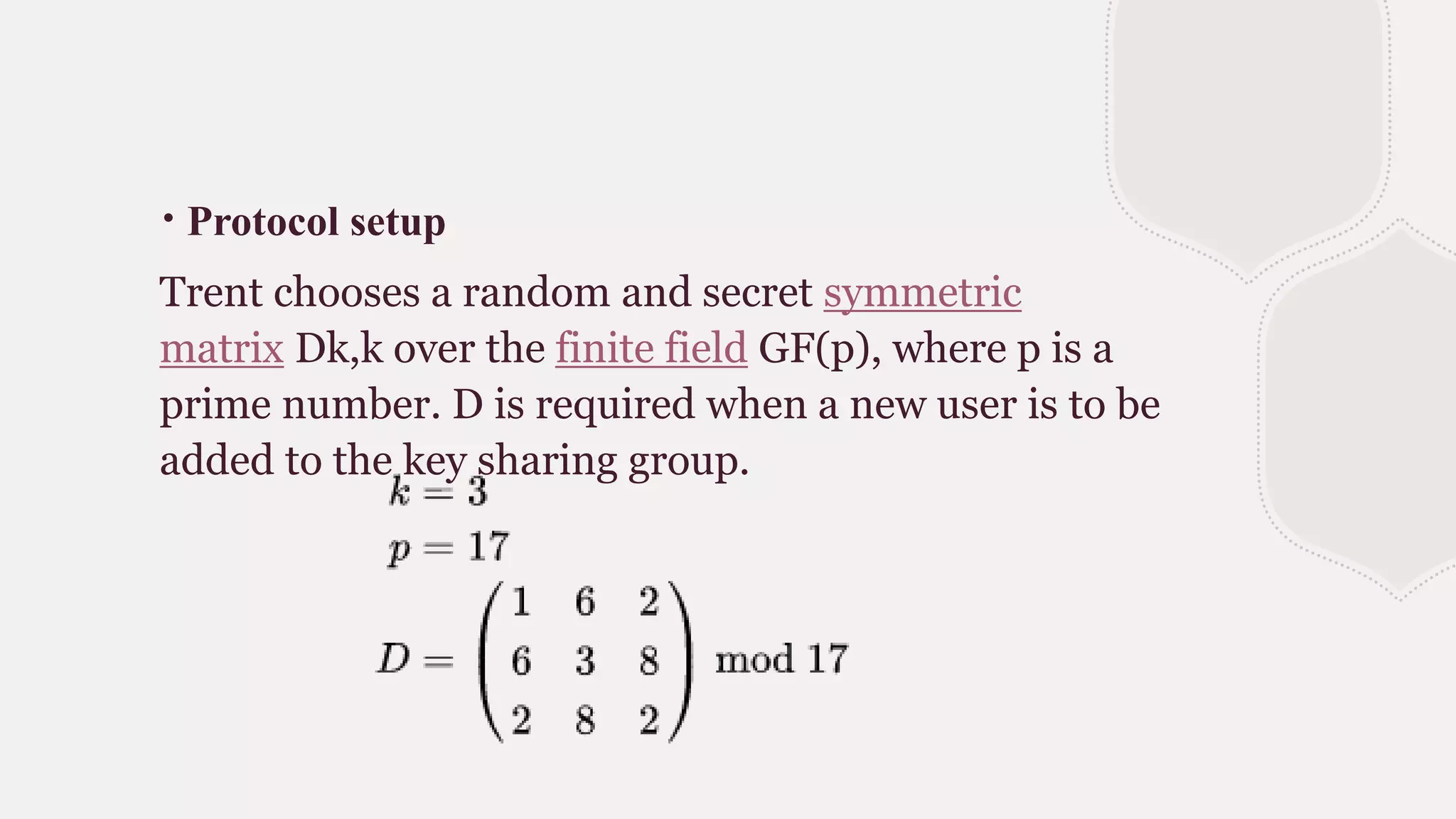
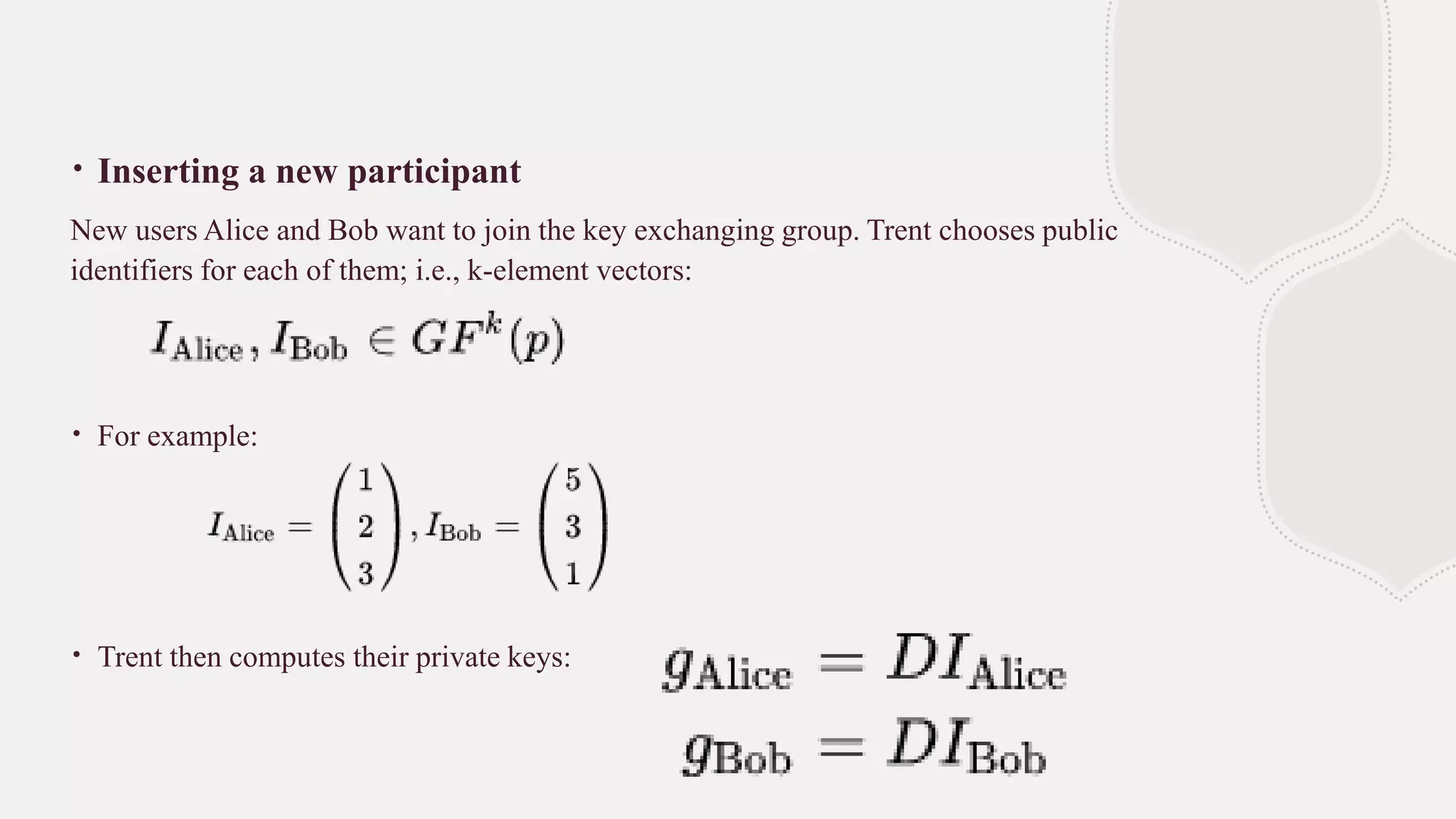
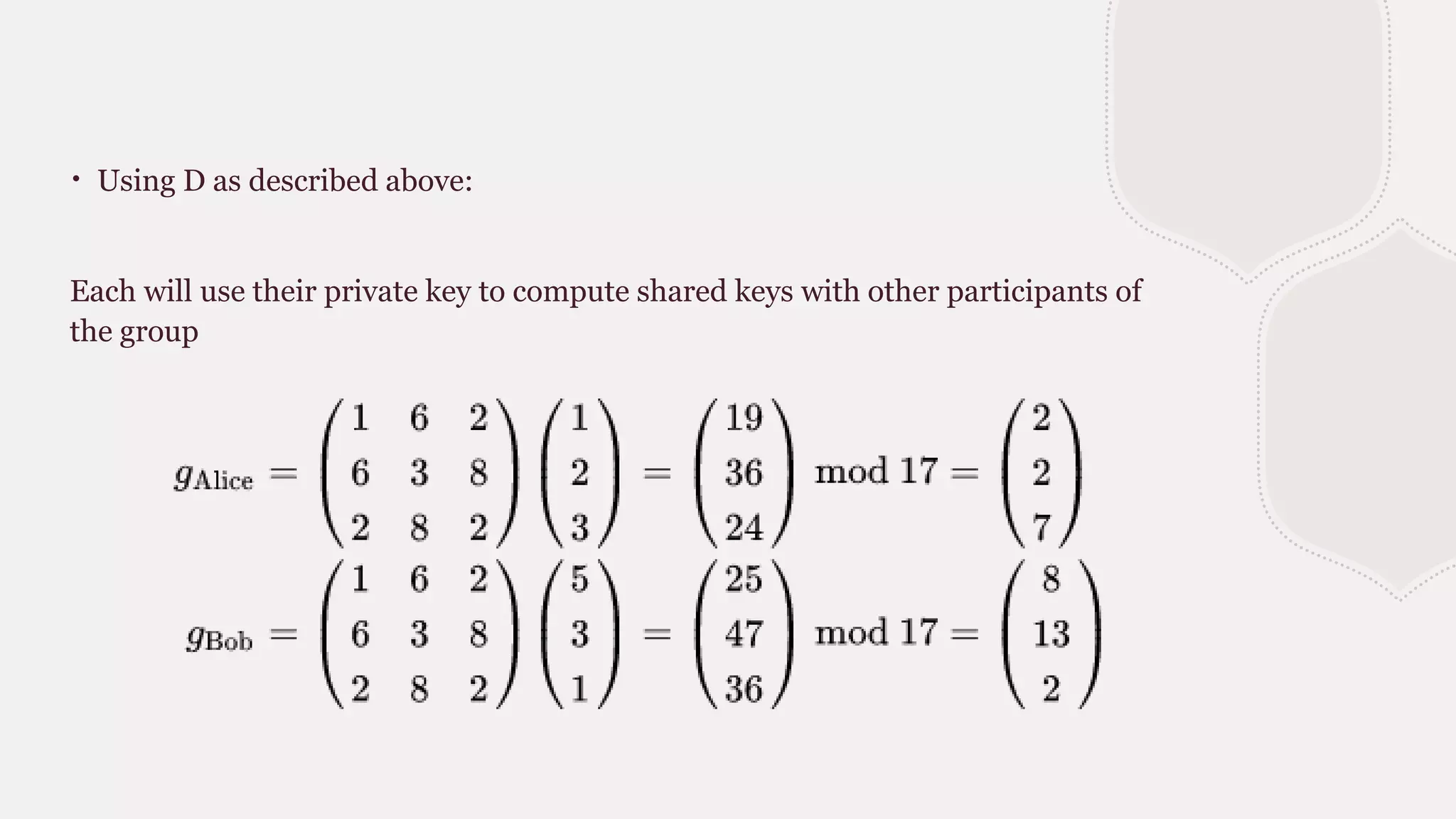
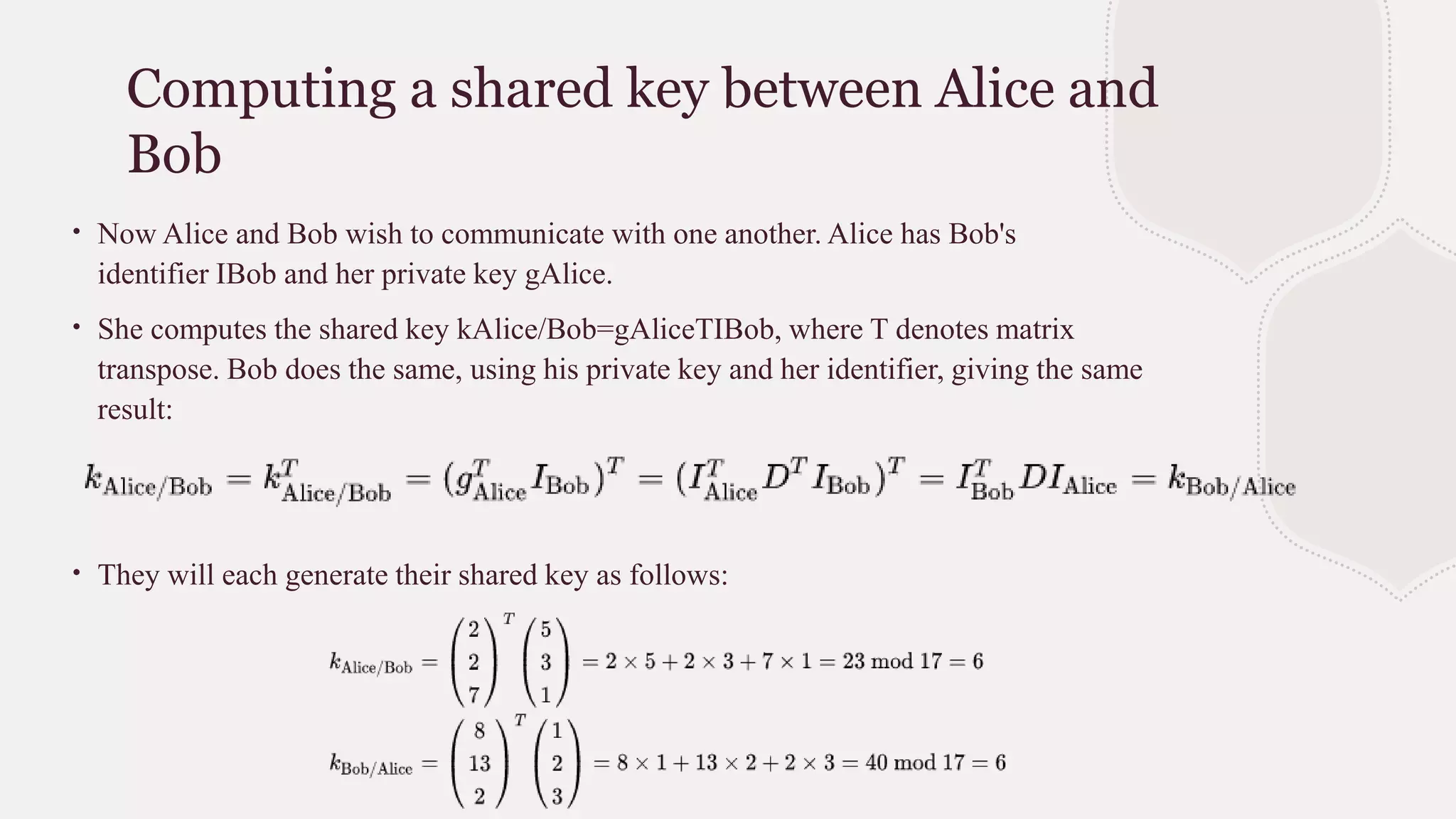
Blom's key pre-distribution scheme is a symmetric threshold key exchange protocol that allows any two participants who receive a secret key from a trusted party to independently create a shared key for secure communication. The trusted party chooses a random secret matrix and uses it to compute private keys for each new participant based on their public identifier. Any two participants can then use their private key and the other's public identifier to compute the same shared key. The scheme provides security as long as fewer than k private keys are compromised, since k linearly independent identifiers are needed to compute other keys.