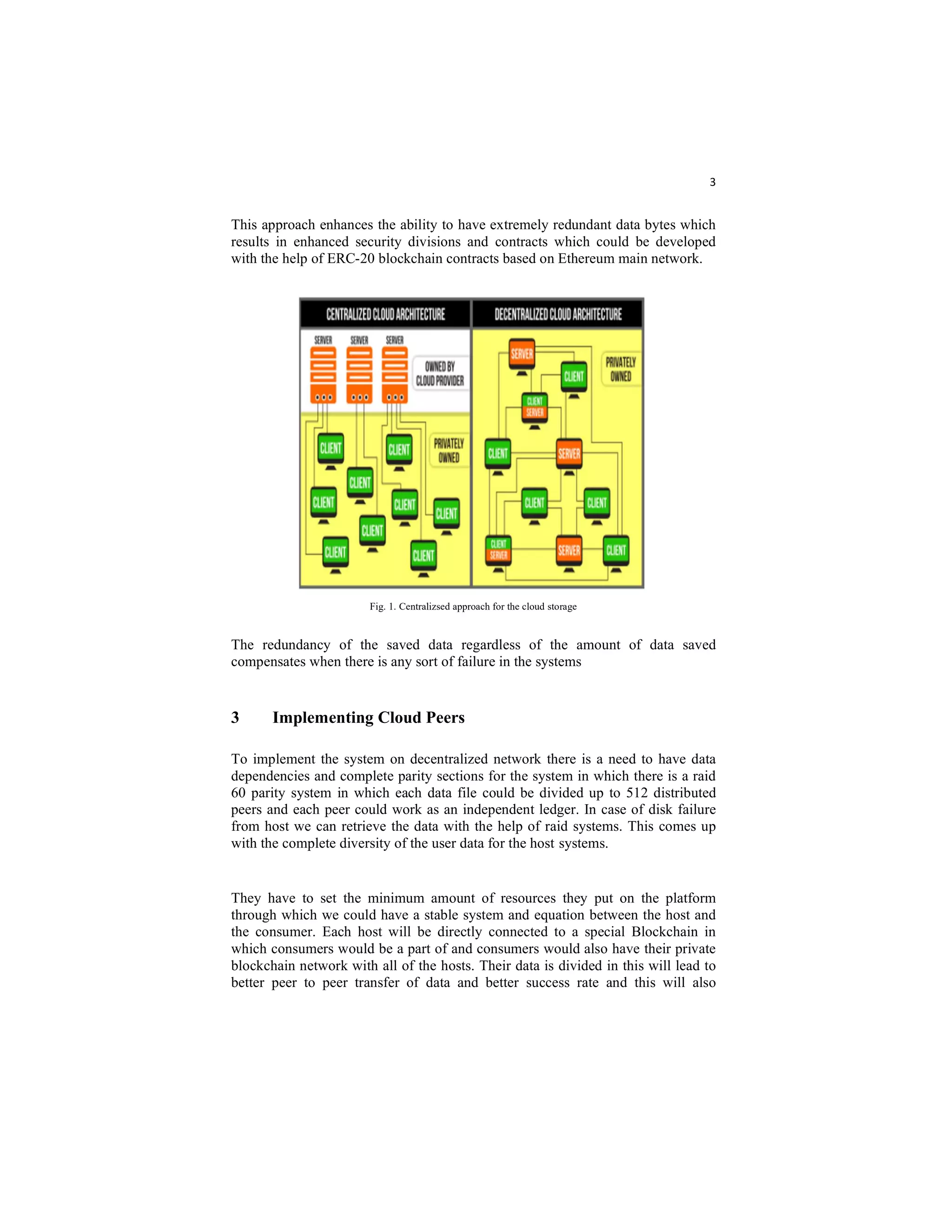
This document proposes a decentralized cloud storage system using blockchain technology and cryptocurrency payments. It describes a prototype that divides files into fragments stored across multiple peer nodes to improve security, availability and performance over centralized cloud storage. Access control is provided through attribute-based encryption without a centralized authority. Payments between users and peer nodes hosting storage are handled through a custom cryptocurrency implemented with Ethereum smart contracts and the ERC-20 standard. The system aims to provide transparent, redundant and censorship-resistant cloud storage without high upfront costs through a decentralized peer-to-peer network model.