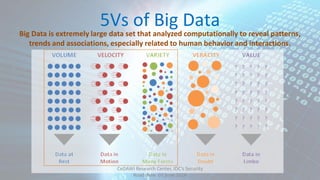
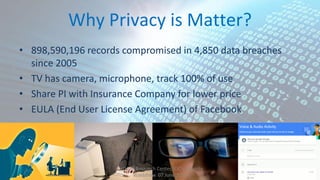
The document discusses the exponential growth of big data and its implications for privacy and security, detailing statistics from 2003 through 2020. It addresses the perspectives of businesses, consumers, and legislators regarding data collection, privacy concerns, and the ramifications of data breaches. Additionally, it outlines principles for data protection and relevant legislation aimed at balancing privacy rights with technological innovation.