BASSET stands for "Bell's Advanced System Security Evaluation Tool" and performs detailed consistency and security checks on UNIX and Linux systems. It generates a report showing any potential problems found. On the system analyzed, BASSET performed over 48 million individual checks and generated a report file containing the results. BASSET is a scanning tool that makes no changes to the system and instead generates a report of findings for the administrator to review.

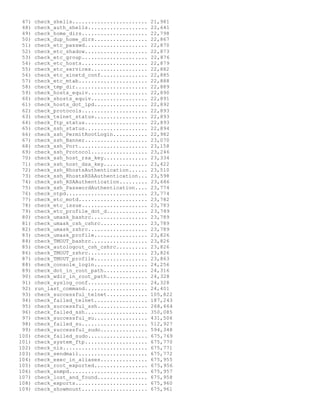
![USAGE: BASSET [ -f | -g | -r | -n | -s ]
-f => Turn ON file system object based tests (default is off). The -f option does an intensive series of
tests on every file on the local file systems. It can uncover some serious problems. Be aware that
the run time will increase. But these tests are well worth the time they take to run.
Please NOTE: By default, BASSETwill NOT traverse any "remote" file systems over "NFS" or
"SMB".
This "-f" switch IMPLIES the "-g" switch.
-g => GO... just run the program.
-r => Get a detailed listing of the rpm based software installed on this system. Default is do NOT get
the rpm listing.
-n => Turn ON the traversal of "NFS" and "SMB" type remote file systems (see the "-f" switch
above). Be aware that the run time will increase, perhaps dramatically. And you will almost surely
get MANY more hits in any function that is checking file ownership or group affiliation, etc.
This "-n" switch IMPLIES the "-f" switch, which in turn IMPLIES the "-g" switch.
-s => Turn ON the get_sys_info function. This gathers up quite a lot of usefull information about the
hardware and software, and appends it to the end of the report. You should run this at least once...
and save the report for future reference.
Why use BASSET?
If you don't understand why BASSETis good, and what it can do to help you secure your systems,
you probably should NOT try to use it. You will only find it confusing. I suggest you hire a UNIX
security expert instead. Let them run BASSETfor you, interpret the results, and make
recommendations.
***A cautionary note on the run time of BASSET, and the amount of temporary file system space
needed while BASSETis executing.
BASSET should run just fine with 20 MBytes or so of free disk space on the file system where it is
located.
All the temporary files are created in the directory from which BASSET is being run. All the temporary
files are removed as BASSETfinishes with them. The report files themselves are generally small -
something on the order of 70 KBytes to 200 KBytes depending on the number of issues found.
BASSET keeps the report files from building up over time in an unbounded fashion by removing any
reports over 120 days old.
The run time is dependent on CPU speed, available free memory, the speed of the disk(s), the load
on the system, the type and number of NFS, SMB, or other remotely mounted file systems, etc.](https://image.slidesharecdn.com/5213d4ab-5236-46f1-84a3-6f31b7d7b9fd-150214084503-conversion-gate02/85/BASSET_README-2-320.jpg)