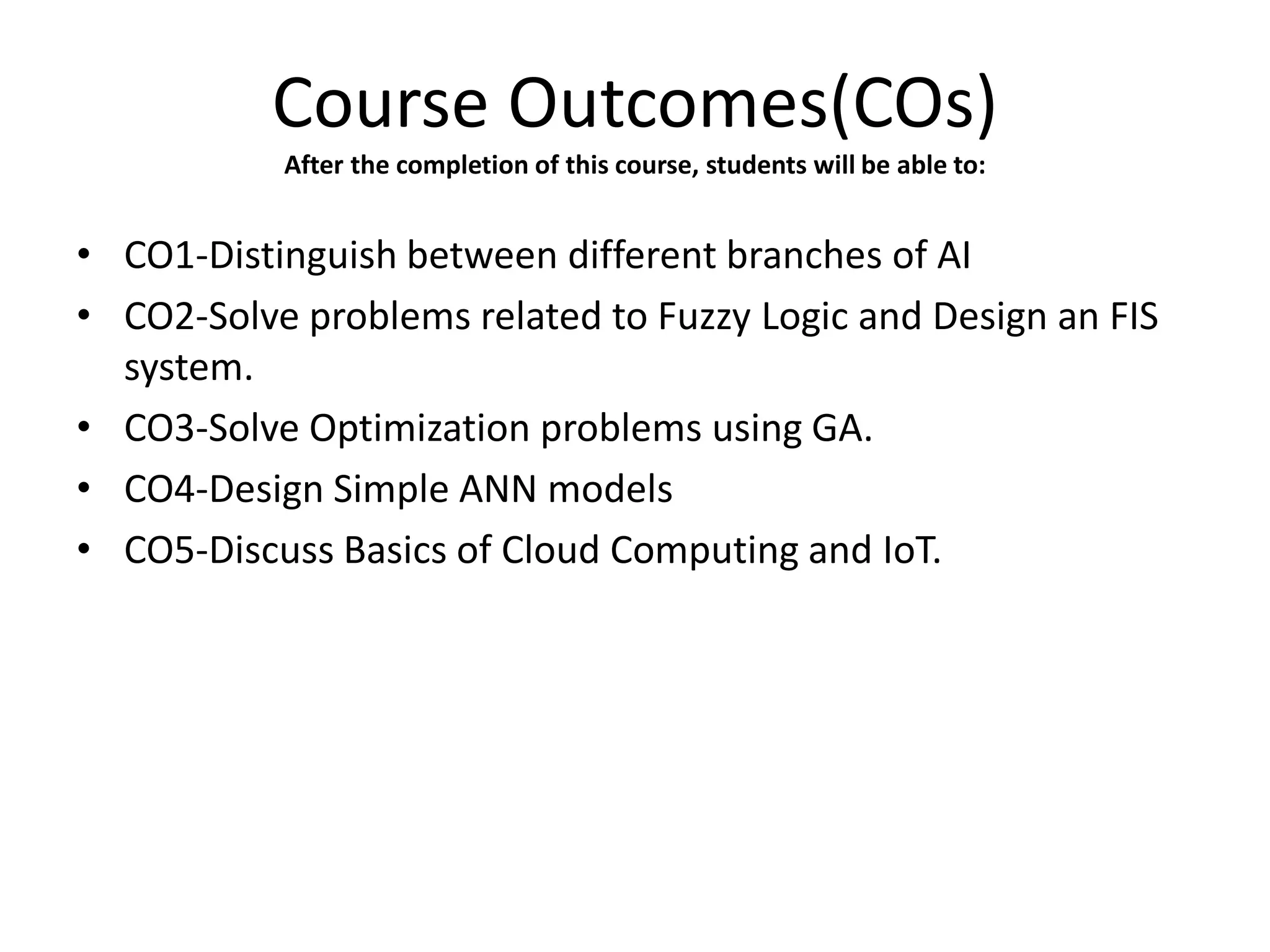
This document provides an overview of the IT201 Basics of Intelligent Computing course. It outlines the course outcomes, which include being able to distinguish AI branches, solve problems using techniques like fuzzy logic and genetic algorithms, design neural networks, and discuss cloud computing and IoT. It also describes the various modules that make up the course, including introductions to computing, intelligent computing, and artificial intelligence concepts. Specific techniques discussed for solving AI problems include search, use of knowledge, and abstraction. The document provides examples of different programming approaches for problems like tic-tac-toe and question answering.



![What is Computing?[1]
• Computing is any activity that uses computers to
manage, process, and communicate information.
• It includes development of both hardware and
software.
• Computing has become a critical, integral
component of modern industrial technology.
[1] https://en.wikipedia.org/wiki/Computing](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-5-2048.jpg)
![Types of Computing Devices[2]
• Supercomputer.
• Mainframe.
• Server Computer.
• Workstation Computer.
• Personal Computer or PC.
• Microcontroller.
• Smartphone.
[2]https://en.wikiversity.org/wiki/Types_of_computers](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-6-2048.jpg)


![[1]https://www.youtube.com/watch?v=Pwy_f-Ke2hA
[2]https://www.practicereasoningtests.com/deductive-reasoning-questions/
[3] funwithpuzzles.com](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-9-2048.jpg)
![[1]fibonicci.com
[2] https://www.slideserve.com/zack/reasoning](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-10-2048.jpg)

![Comprehension
We talked about :Learning,Reasoning,Understanding and Now we talk about
Comprehension: Act of grasping truths, Capacity for understanding fully.
[1]https://slideplayer.com/slide/8597416/
[2] https://www.liveworksheets.com/](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-12-2048.jpg)





![Intelligent Computing /Computational Intelligence
• Can Computers be Intelligent?
1)In the mid-1900s, Alan Turing gave much thought to this question. He
believed that machines could be created that would mimic the processes of
the human brain.
2)In 1950 Turing published his test of computer intelligence, referred to as the
Turing test.
3)Computational Intelligence (CI) is the theory, design, application and
development of biologically and linguistically motivated computational
paradigms. Traditionally the three main pillars of CI have been Neural
Networks, Fuzzy Systems ,Evolutionary Computation.
[1]https://cis.ieee.org/about/what-is-ci
[2]Computational Intelligence: An Introduction, Second Edition A.P. Engelbrecht
2007 John Wiley & Sons, Ltd
[3] A. M. Turing (1950) Computing Machinery and Intelligence. Mind 49: 433-460.](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-18-2048.jpg)
![Turing Test (1950)"Can Machine think?"
[1] https://www.javatpoint.com/turing-test-in-ai
[2] A. M. Turing (1950) Computing Machinery and Intelligence. Mind 49: 433-460.
Alan Turing
Turing test is used to determine” weather or not machines can think intelligently like Humans](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-19-2048.jpg)
![Chinese Room Argument
• 1980-John Searle
[1]https://plato.stanford.edu/entries/chinese-room/
[2]Source: Wikicomms](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-20-2048.jpg)
![Necessity of Intelligent Computing
• Intelligent systems are revolutionizing a variety of industries, including
transportation and logistics, security, and manufacturing.
• Intelligent systems are complex and use a wide range of technologies – artificial
intelligence, cybersecurity, natural language processing, deep learning, embedded
CPUs, distributed storage, wireless networking and graphical signaling.
[1]https://online.lewisu.edu/mscs/resources/what-are-intelligent-systems](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-21-2048.jpg)

![Computational Intelligence paradigms
[1]Computational Intelligence: An Introduction, Second Edition A.P. Engelbrecht 2007 John Wiley
& Sons, Ltd](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-23-2048.jpg)

![[1]peace.saumag.edu › AIWashingtonMcKeeNelson.ppt.ppt
Birth of AI](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-25-2048.jpg)
![AI Problems
[1]E.Rich,K.Knight,S.B.Nair,Artificial Intelligence,3rd Ed,McGrawwHills,2009
[2]https://www.tutorialspoint.com/artificial_intelligence/artificial_intelligence_research_areas.htm](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-26-2048.jpg)




![To discuss:
• What are our underlying assumptions about
intelligence?
• What kind of techniques will be useful for solving AI
problems?
• At what level of detail, if at all, are we trying to
model human intelligence?
• How will we know when we have succeeded in
building an intelligent program?
[1]E.Rich,K.Knight,S.B.Nair,Artificial Intelligence,3rd Ed,McGrawwHills,2009](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-31-2048.jpg)













![Program 2:
Data Structure: Board-A nine element vector representing the board. But instead of
using 0,1 and 2 in each element, we store 2 for blank, 3 for X and 5 for O.
Turn:An integer indicating which move of the game is about to be played;1 indicates
the first move and 9 the last
The Algorithm:
Make2: returns 5 if the centre square is blank(Board[5]=2. Else any other blank sq
Posswin(p): Returns 0 if the player p cannot win on his next move; otherwise it
returns the number of the square that constitutes a winning move. If the product
is 18 (3x3x2), then X can win. If the product is 50 ( 5x5x2) then O can win.
Go(n): Makes a move in the square n.This procedure sets Board[n] to 3 if turn is odd,or
5 if Turn is even.It also increments Turn by one.
Strategy:
Turn = 1 Go(1)
Turn = 2 If Board[5] is blank, Go(5), else Go(1)
Turn = 3 If Board[9] is blank, Go(9), else Go(3)
Turn = 4 If Posswin(X) 0, then Go(Posswin(X)){i.e block opponents win],else
Go(Make2)
.......](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-45-2048.jpg)


























![Summary of Lecture 3
• Question Answering:(problem1)This program attempts
to answer questions using the literal input text.It
simply matches text fragments in the questions
against the input text.
• (problem2)uses structural representations.
• Important knowledge representation
systems(production rules, slot and filler structure,
statements in mathematical logic)
• (Problem3)uses tree structure(seeF ig1.3AI text
book)
[1]E.Rich,K.Knight,S.B.Nair,Artificial Intelligence,3rd Ed,McGrawwHills,2009](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-72-2048.jpg)
![We conclude That AI technique
requires:
• Search
• Use of Knowledge
• Abstraction
[1]E.Rich,K.Knight,S.B.Nair,Artificial Intelligence,3rd Ed,McGrawwHills,2009](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-73-2048.jpg)
![Problems,Problem Spaces and Search
[1]E.Rich,K.Knight,S.B.Nair,Artificial Intelligence,3rd Ed,McGrawwHills,2009](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-74-2048.jpg)
![[1]E.Rich,K.Knight,S.B.Nair,Artificial Intelligence,3rd Ed,McGrawwHills,2009](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-75-2048.jpg)

![Production Rules
[1]E.Rich,K.Knight,S.B.Nair,Artificial Intelligence,3rd Ed,McGrawwHills,2009](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-77-2048.jpg)
![One Solution to the Water Jug Problem
Galloons in the 4-Gallon
Jug
Gallons in the 3 –Gallon
Jug
Rule Applied
0 0
2
0 3
9
3 0
2
3 3
7
4 2
5or12
0 2
9or 11
2 0
[1]E.Rich,K.Knight,S.B.Nair,Artificial Intelligence,3rd Ed,McGrawwHills,2009](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-78-2048.jpg)
![Control Strategies
• First requirement-It causes motion.
• Second requirement-Systematic(global motion and local
motion)
[1]E.Rich,K.Knight,S.B.Nair,Artificial Intelligence,3rd Ed,McGrawwHills,2009](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-79-2048.jpg)












![Generate and Test
• Heuristic search,DFS with backtracking
Steps: 1-Generate a possible solution
2-Test to see if this is a actual solution
3-If the solution is found,quit,otherwise go to
step-1
Properties of generator:Complete,Non
Redundant,Informed
[1]E.Rich,K.Knight,S.B.Nair,Artificial Intelligence,3rd Ed,McGrawwHills,2009](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-92-2048.jpg)
























![Knowledge Base Creation
1)In order to solve the complex problems encountered in AI ,one
needs both a large amount of knowledge(Facts) and some
mechanisms for manipulating that knowledge to create solutions
to new problems.
a)Facts: Truths in some relevant world. These are the things we
want to represent.
b)Representations of facts in some chosen form. These are the
things we actually be able to manupulate.
[1]E.Rich,K.Knight,S.B.Nair,Artificial Intelligence,3rd Ed,McGrawHills,2009](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-117-2048.jpg)
![Mapping between Facts and Representations
Dog is an animal(english)
Dog(animal)(logical)
All animals have legs(english)
⩝ 𝑥: 𝑎𝑛𝑖𝑚𝑎𝑙 𝑥 → 𝑙𝑒𝑔𝑠 𝑥
Legs(dog) (logical )
dog has legs(english)
[1]E.Rich,K.Knight,S.B.Nair,Artificial Intelligence,3rd Ed,McGrawHills,2009
Fig .Representation of Facts
Abstract type
Concrete implementation](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-118-2048.jpg)











![2 variable Predicate
loves(x,y)- x loves y
John loves Marry-loves(John, Marry)
John loves everyone- ⩝x: likes(John, x)
Everyone loves everyone- ⩝y ⩝x: likes( y,x)
Someone likes someone- ∃𝑥 ∃𝑦: 𝑙𝑖𝑘𝑒𝑠(𝑥, 𝑦), john likes someone-∃𝑦: 𝑙𝑖𝑘𝑒𝑠(𝑗𝑜ℎ𝑛, 𝑦)
Someone likes everyone- ∃𝑦 :[⩝x: 𝑙𝑖𝑘𝑒𝑠(𝑦, 𝑥)],john likes everyone-⩝x: likes(John, x)
Everyone likes someone-⩝x: ∃𝑦: 𝑙𝑖𝑘𝑒𝑠(𝑥, 𝑦)
Nobody likes everyone- lets us see- john doesn't like everyone- ¬ [⩝x likes(john,x)]
⩝y[ ¬ [⩝x likes(y,x)]]
Marcus was a man- man(marcus)
All Pompeians were Romans- ⩝x:Pompeians(x)→Roman(x)
All romans were either loyal to Caesar or hated him-
⩝x:Roman(x)→[(loyalto(x,Caesar)˅ hate(x,Caesar))˄ ¬(loyalto(x,Caesar)˅
hate(x,Caesar))]
https://www.youtube.com/watch?v=2juspgYR7as](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-130-2048.jpg)
![Exercises
Gold and Silver ornaments are precious.
Given:
G(x) :x is a gold ornament.
S(x):x is a silver ornament
P(x):x is precious.
Ans-⩝x(G(x)˅S(x)→p(x))
Every teacher is liked by some student
⩝x:*Teacher(x)→ ∃𝑦:student(y)˄likes(y,x)]
Some boys in the class are taller than all the girls
∃x *boys(x) ˄ ⩝y[girls(y)→taller(y,x)]]
https://www.youtube.com/watch?v=xR2YzdGzf9k,GATE,CSE-2009,2005,2004](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-131-2048.jpg)
















































![ Classical Set vs Fuzzy set
A
x
A
x
x
f
X
x
f A
A
if
,
0
if
,
1
)
(
where
},
1
,
0
{
:
)
(
Let X be the universe of discourse and its elements be denoted as x.
In the classical set theory, crisp set A of X is defined as function fA(x) called the
the characteristic function of A
In the fuzzy theory, fuzzy set A of universe of discourse X is defined by function
called the membership function of set A
)
(x
A
.
in
partly
is
if
1
)
(
0
;
in
not
is
if
0
)
(
;
in
totally
is
if
1
)
(
],
1
,
0
[
:
)
(
A
x
x
A
x
x
A
x
x
where
X
x
A
A
A
A
](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-180-2048.jpg)



![ Given a universal set X, a fuzzy set is defined by a
function of the form
This kind of fuzzy sets are called ordinary fuzzy
sets(type 1 fuzzy set).
L-fuzzy set is ,
L is partial order set
Interval-valued fuzzy sets:
◦ The membership functions of ordinary fuzzy sets are often
overly precise. We may be able to identify appropriate
membership functions only approximately.
◦ .
]
1
,
0
[
:
X
A
12
:
A X L
](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-184-2048.jpg)
![• Interval-valued fuzzy sets: a fuzzy set whose
membership functions does not assign to each
element of the universal set one real number, but a
closed interval of real numbers between the
identified lower and upper bounds.
]),
1
,
0
([
:
X
A](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-185-2048.jpg)


![ Fuzzy sets of type 2:
◦ : the set of all ordinary fuzzy sets that can be defined
with the universal set [0,1].
◦ is also called a fuzzy power set of [0,1].
16](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-188-2048.jpg)
































































































































































































































































































































































































































































































































![• public class Publisher
• {
• public static void main(String[] args) throws Exception
• {
• // get the initial context
• InitialContext ctx = new InitialContext();
•
• // lookup the topic object
• Topic topic = (Topic) ctx.lookup("topic/topic0");
•
• // lookup the topic connection factory
• TopicConnectionFactory connFactory = (TopicConnectionFactory) ctx.
• lookup("topic/connectionFactory");
•
• // create a topic connection
• TopicConnection topicConn = connFactory.createTopicConnection();
•
• // create a topic session
• TopicSession topicSession = topicConn.createTopicSession(false,
• Session.AUTO_ACKNOWLEDGE);
•
•](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-701-2048.jpg)


![• public class Subscriber
• {
• public static void main(String[] args) throws Exception
• {
• // get the initial context
• InitialContext ctx = new InitialContext();
•
• // lookup the topic object
• Topic topic = (Topic) ctx.lookup("topic/topic0");
•
• // lookup the topic connection factory
• TopicConnectionFactory connFactory = (TopicConnectionFactory) ctx.
• lookup("topic/connectionFactory");
•
• // create a topic connection
• TopicConnection topicConn = connFactory.createTopicConnection();
•
• // create a topic session
• TopicSession topicSession = topicConn.createTopicSession(false,
• Session.AUTO_ACKNOWLEDGE);](https://image.slidesharecdn.com/basicsofintelligentcomputing-230811043342-e3f2e120/75/Basics-of-Intelligent-Computing-pdf-704-2048.jpg)















































