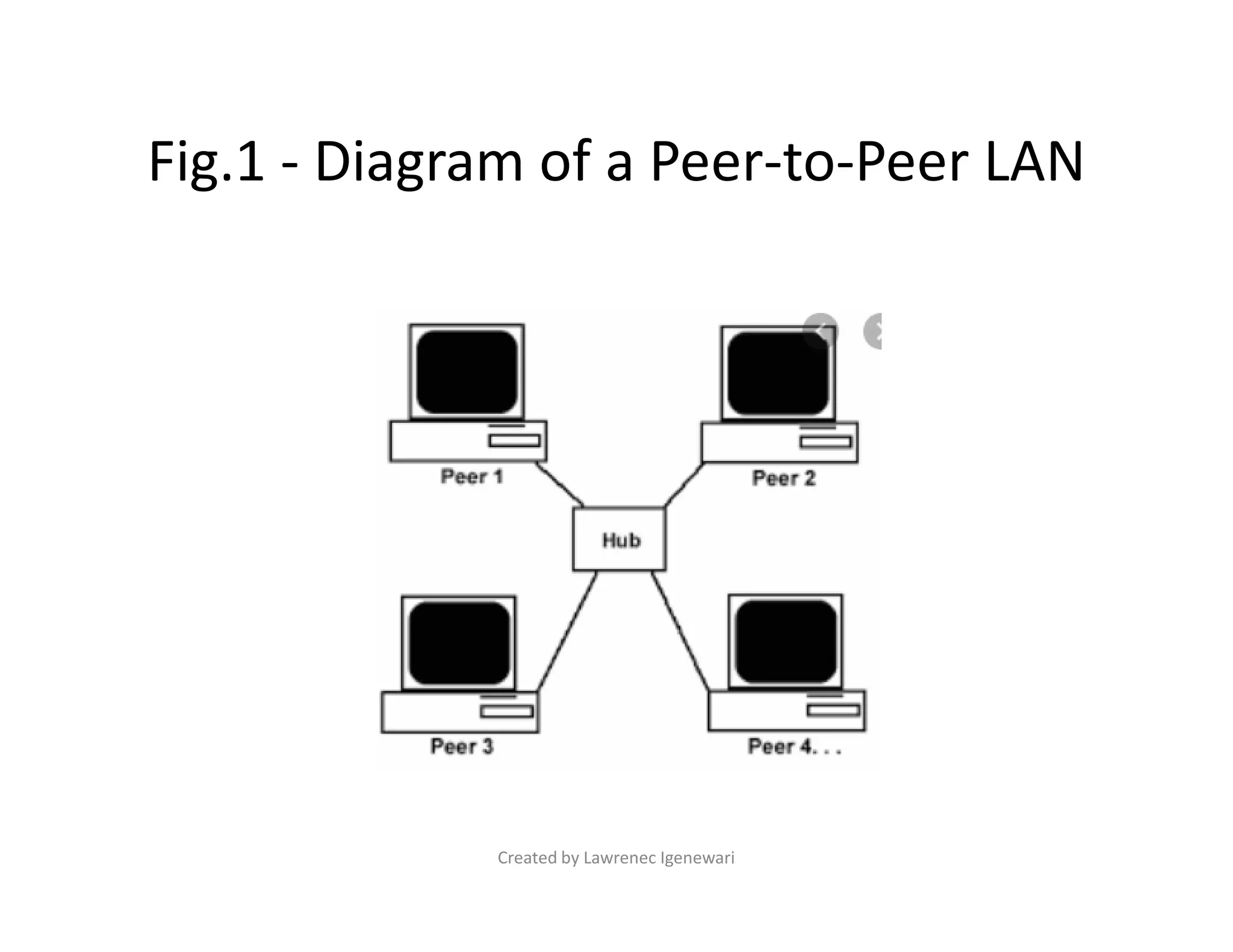
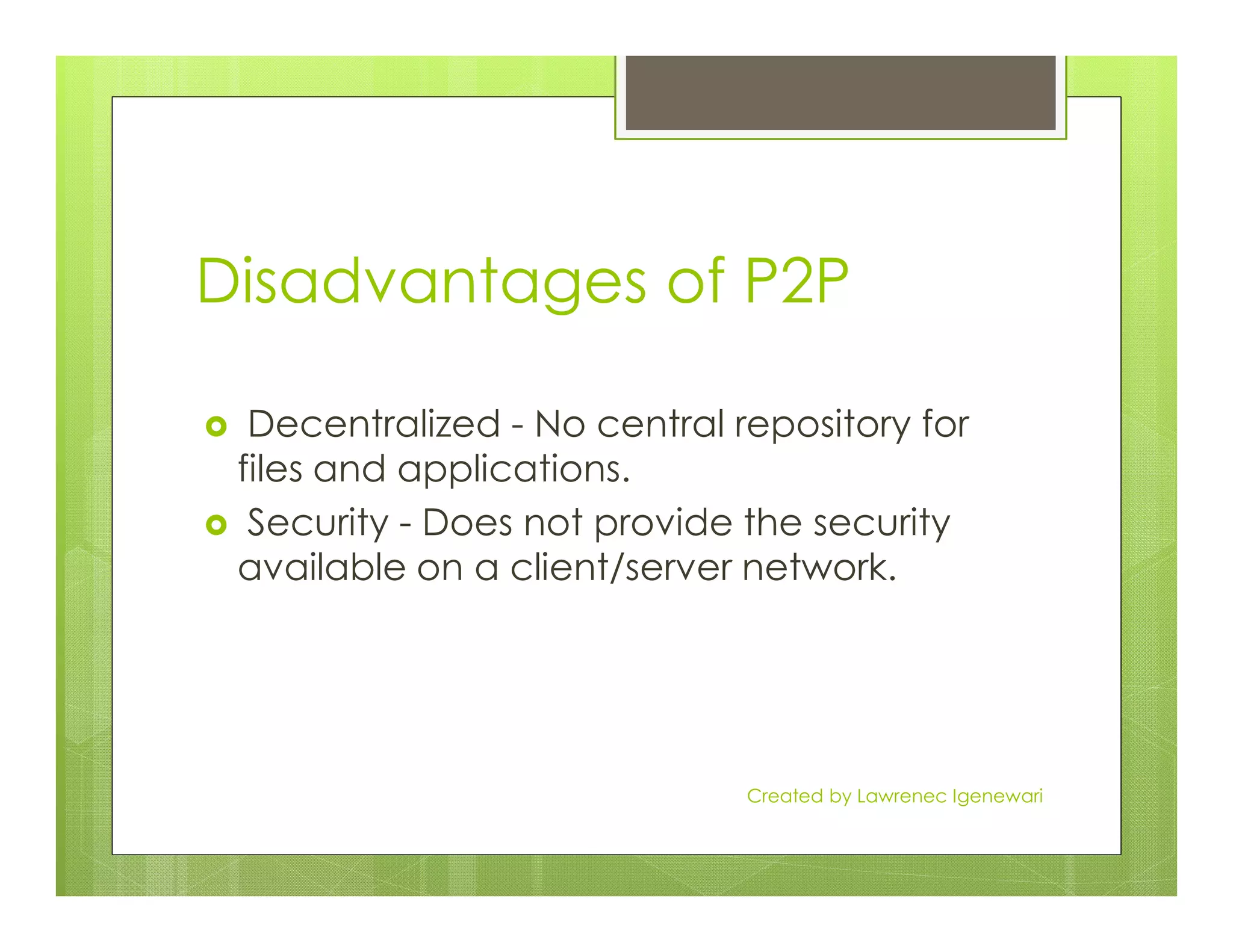
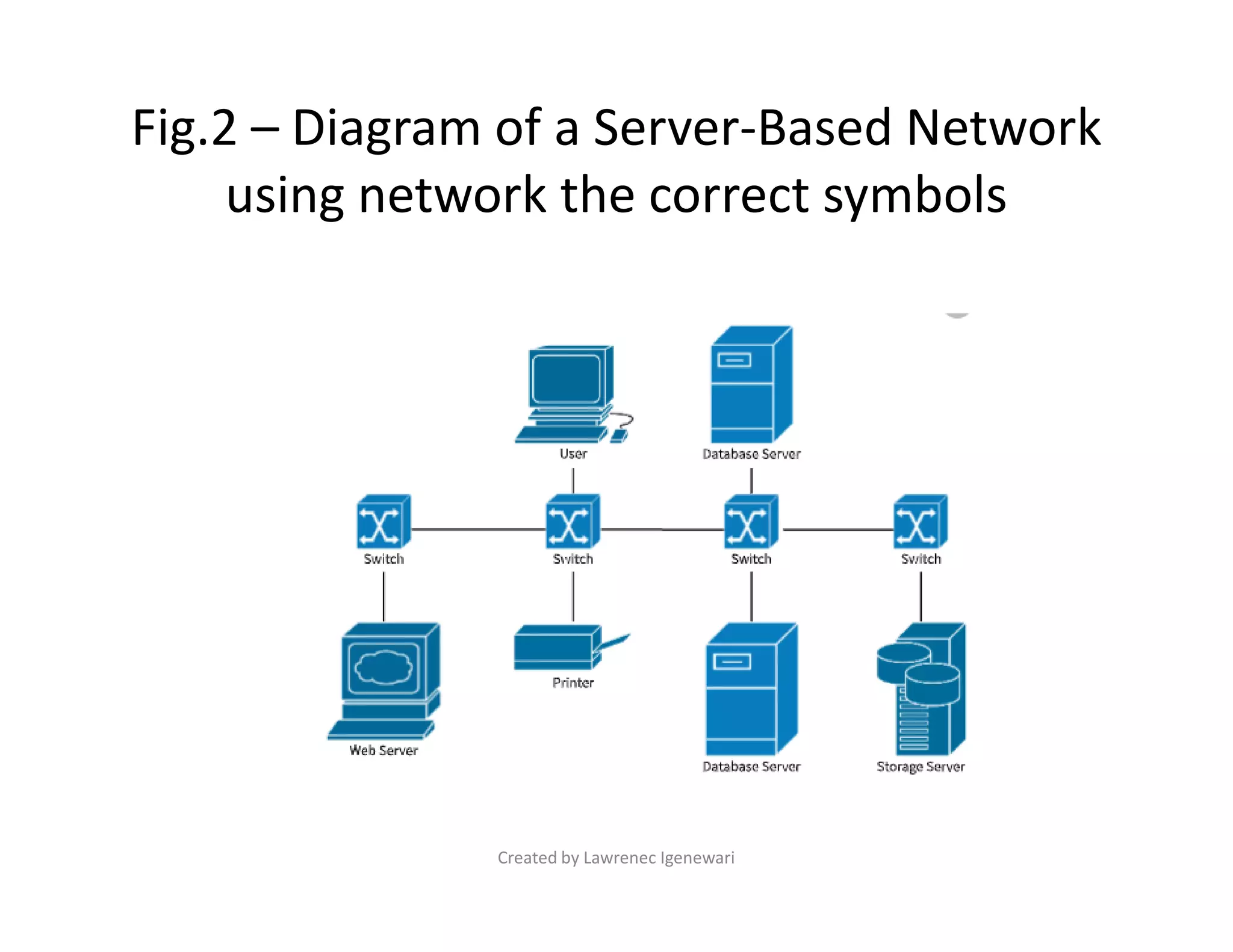
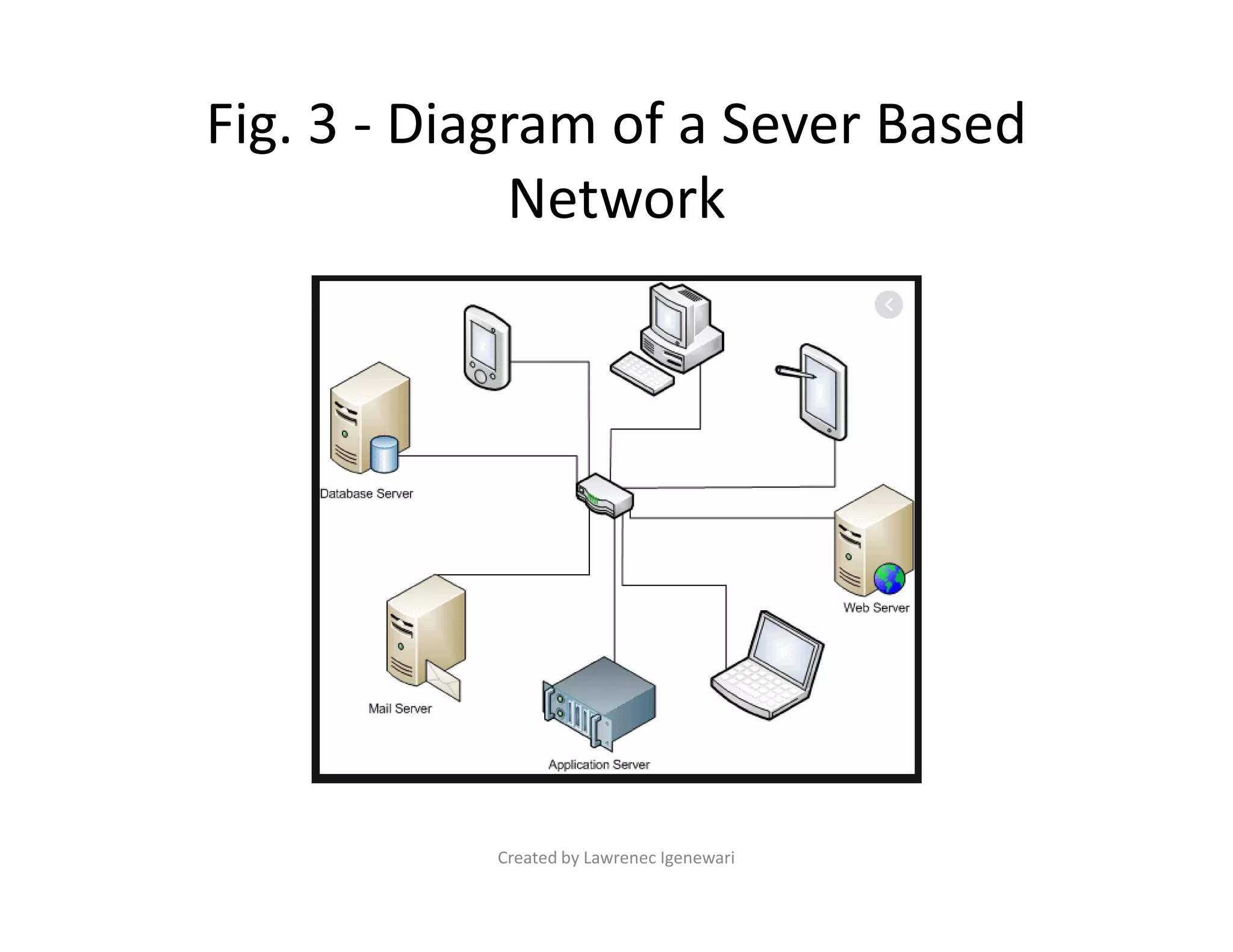
The document discusses two primary types of Local Area Networks (LANs): peer-to-peer (P2P) and server-based networks. Peer-to-peer networks allow computers to share resources equally without a centralized server, while server-based networks rely on a dedicated server for resource management and security. The document outlines the advantages and disadvantages of each network type, including costs, security, and scalability.