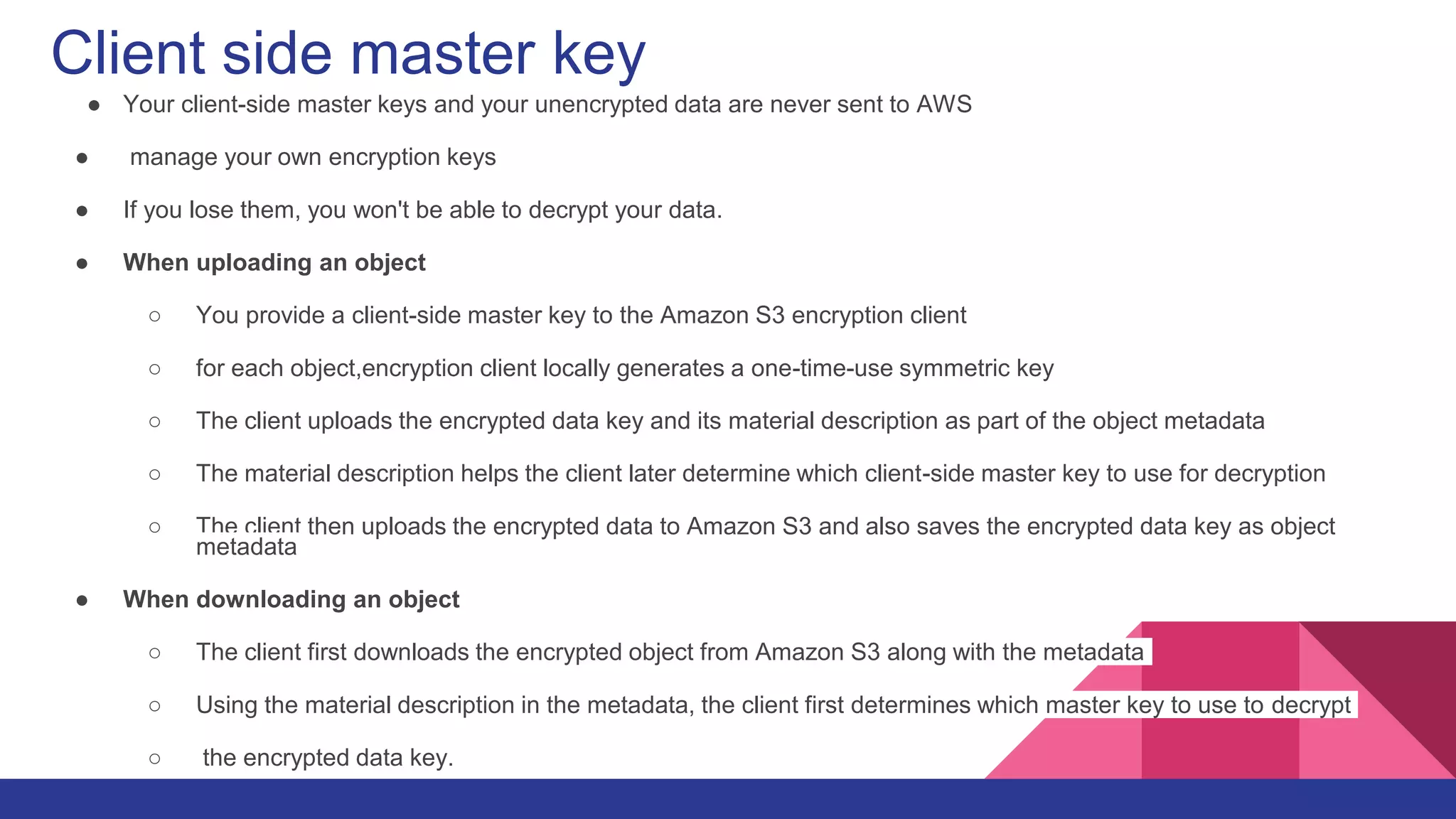
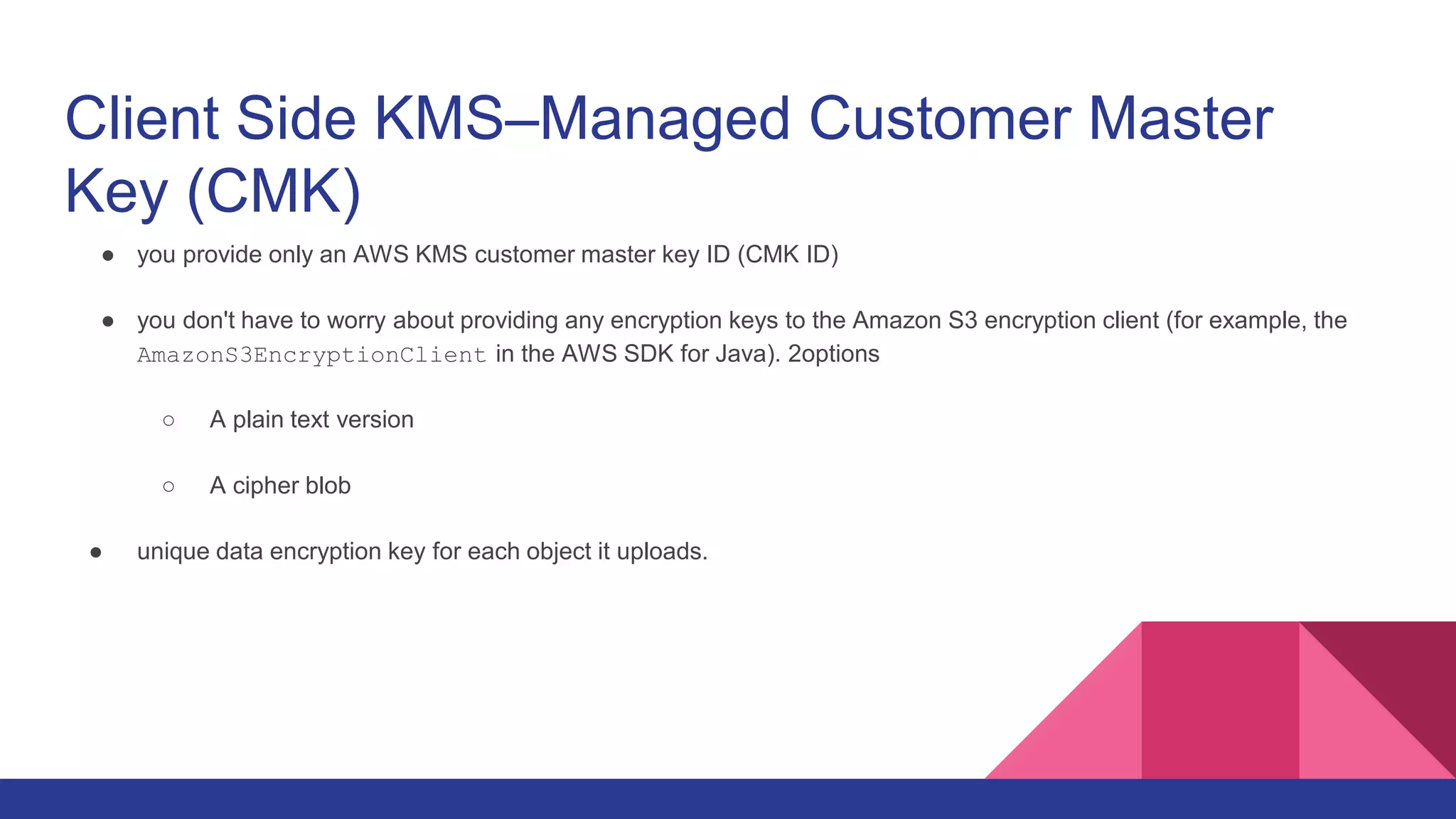
The document outlines security considerations for protecting data in Amazon S3, focusing on encryption methods for data in transit and at rest. It details server-side encryption (SSE) and client-side encryption options, emphasizing the management of encryption keys and different encryption techniques such as AWS KMS-managed keys. Additionally, it mentions various safeguards to enhance security, including VPNs and access controls.