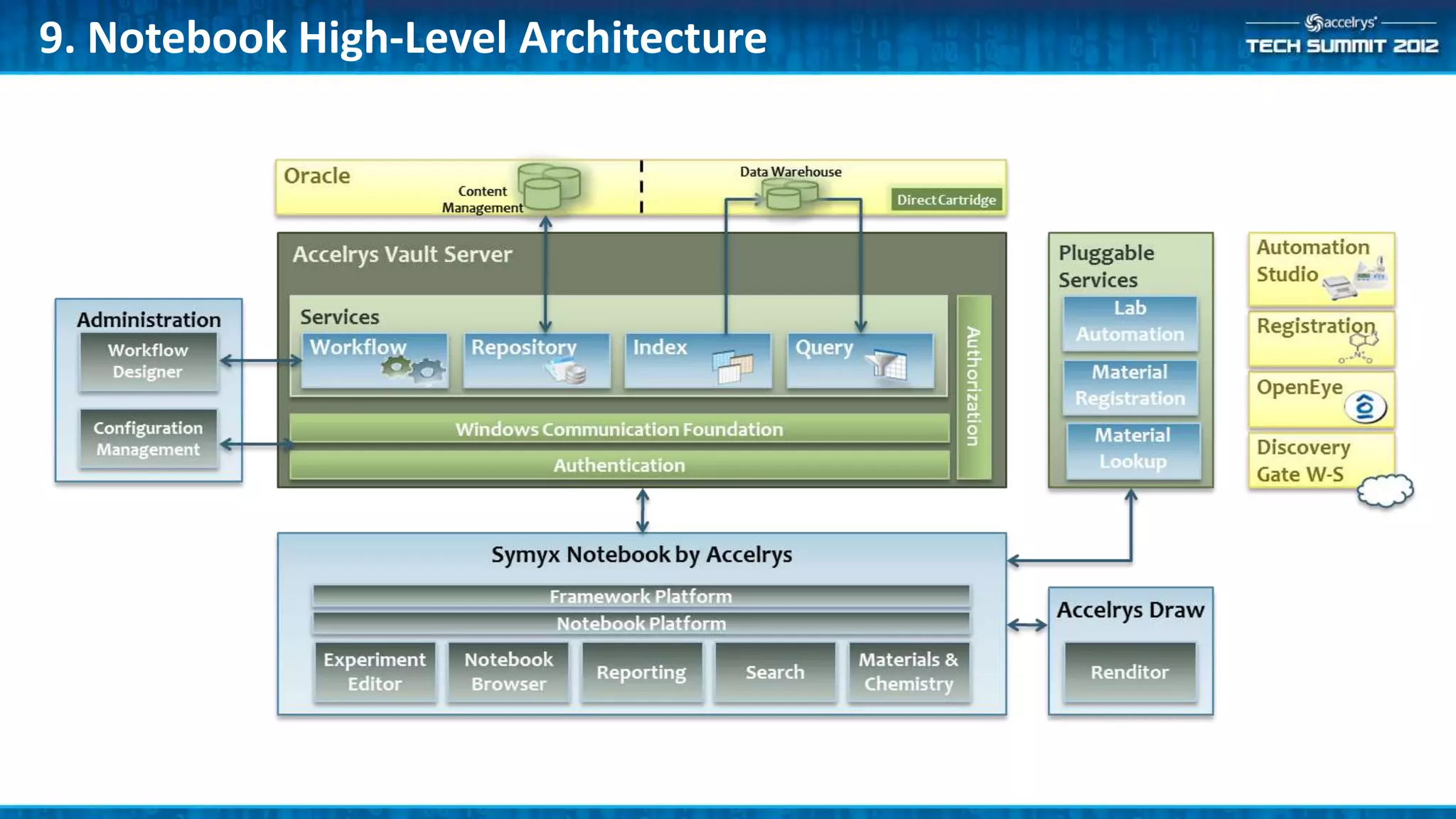
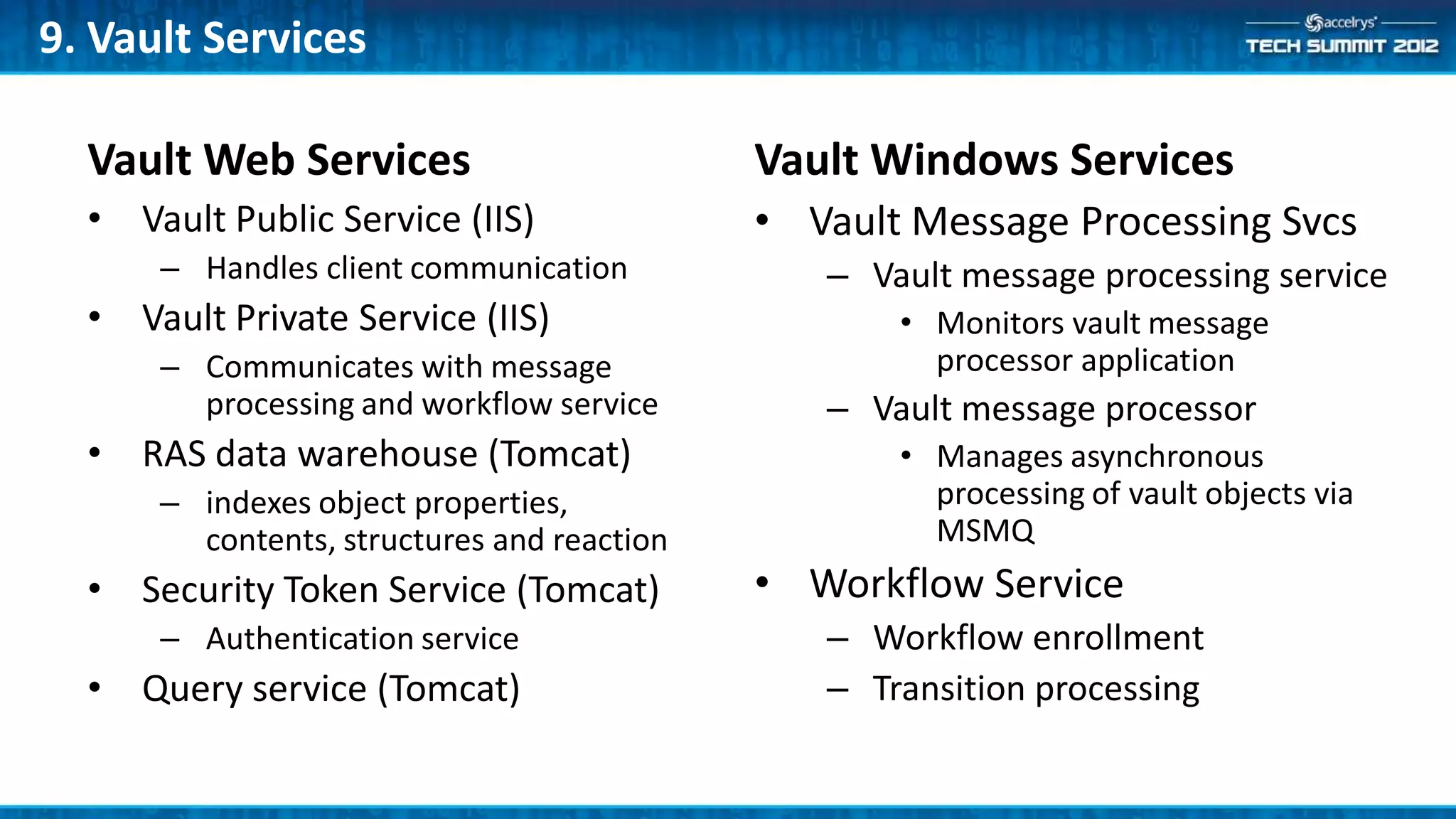
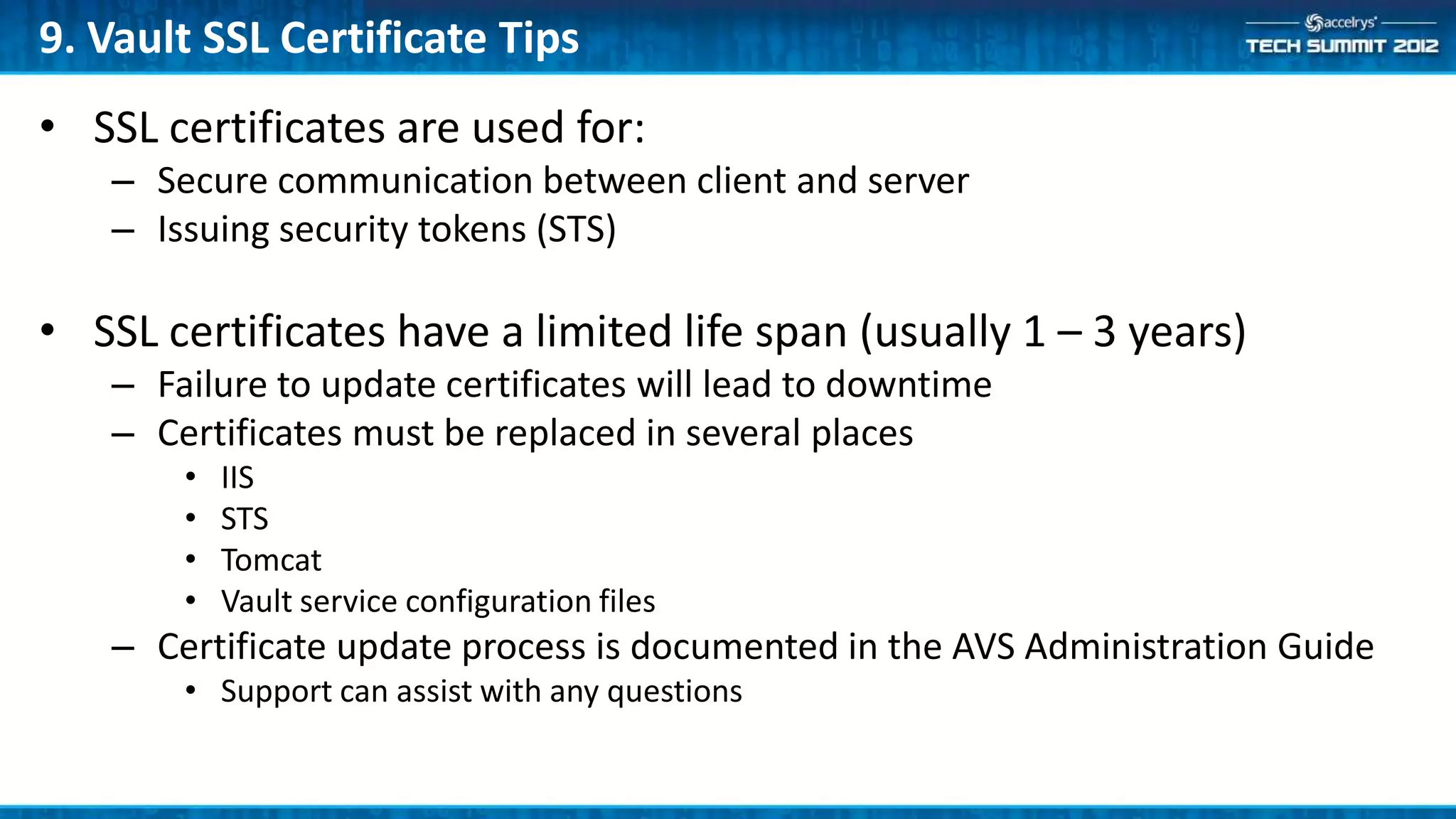
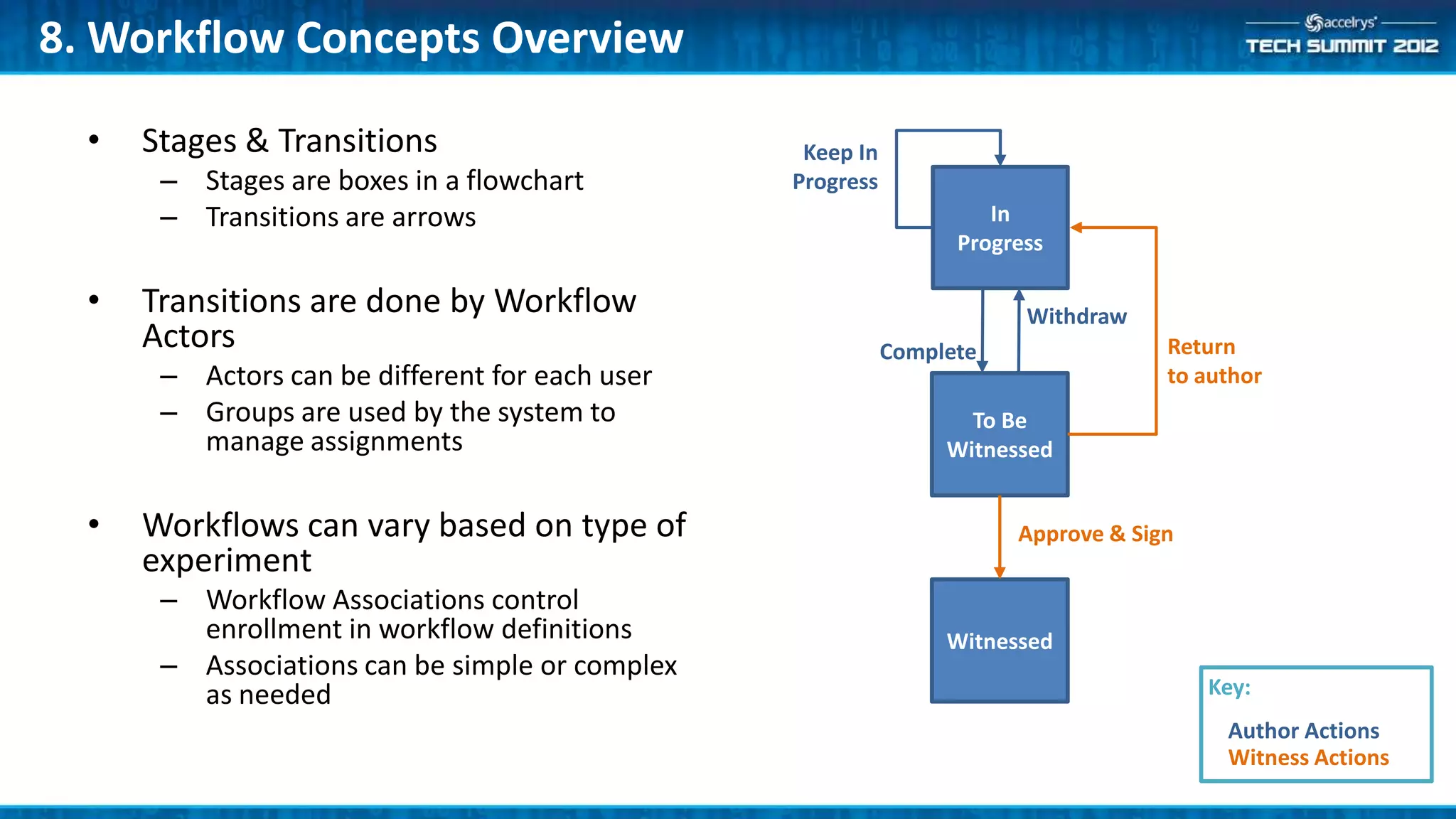
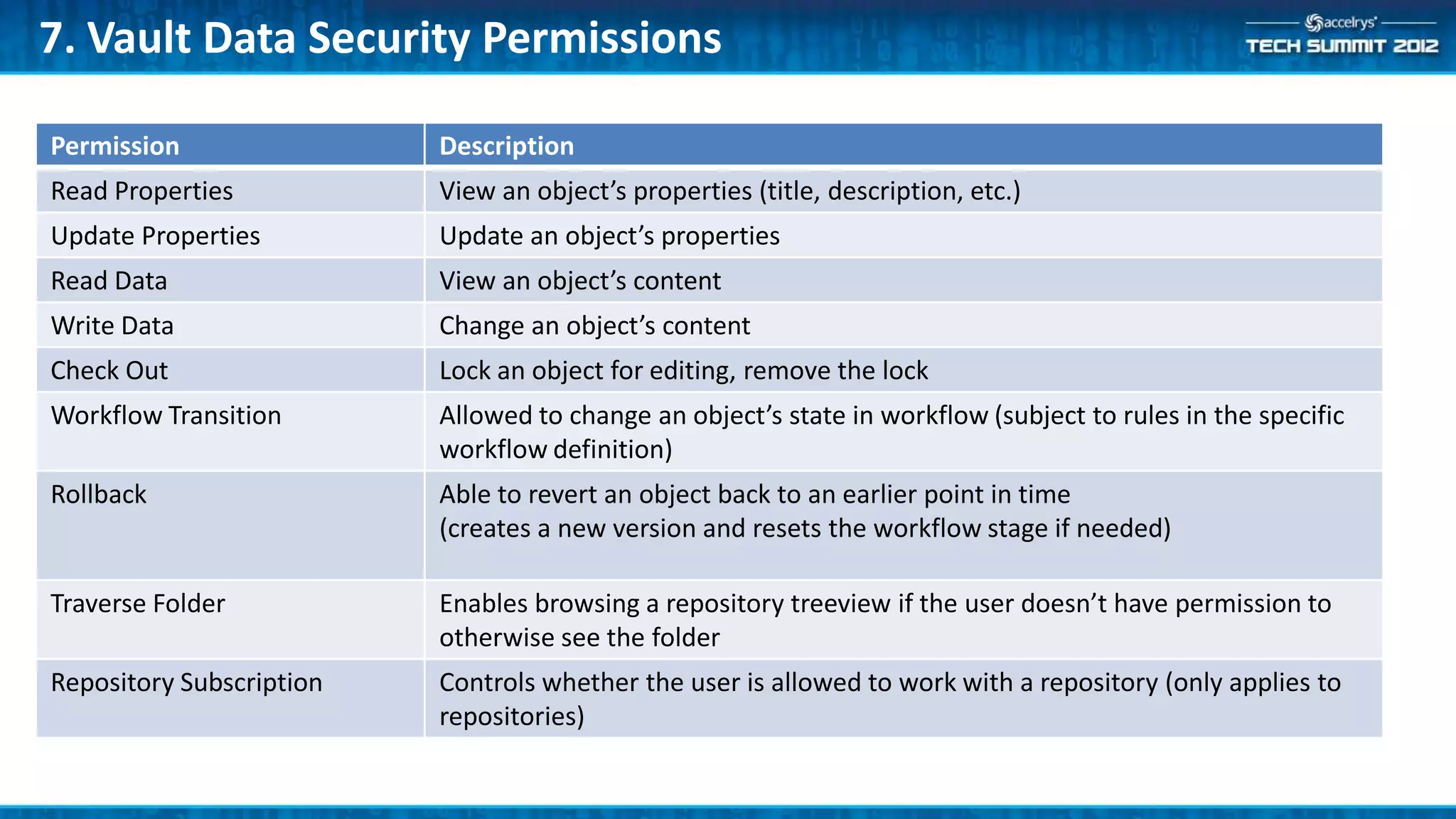
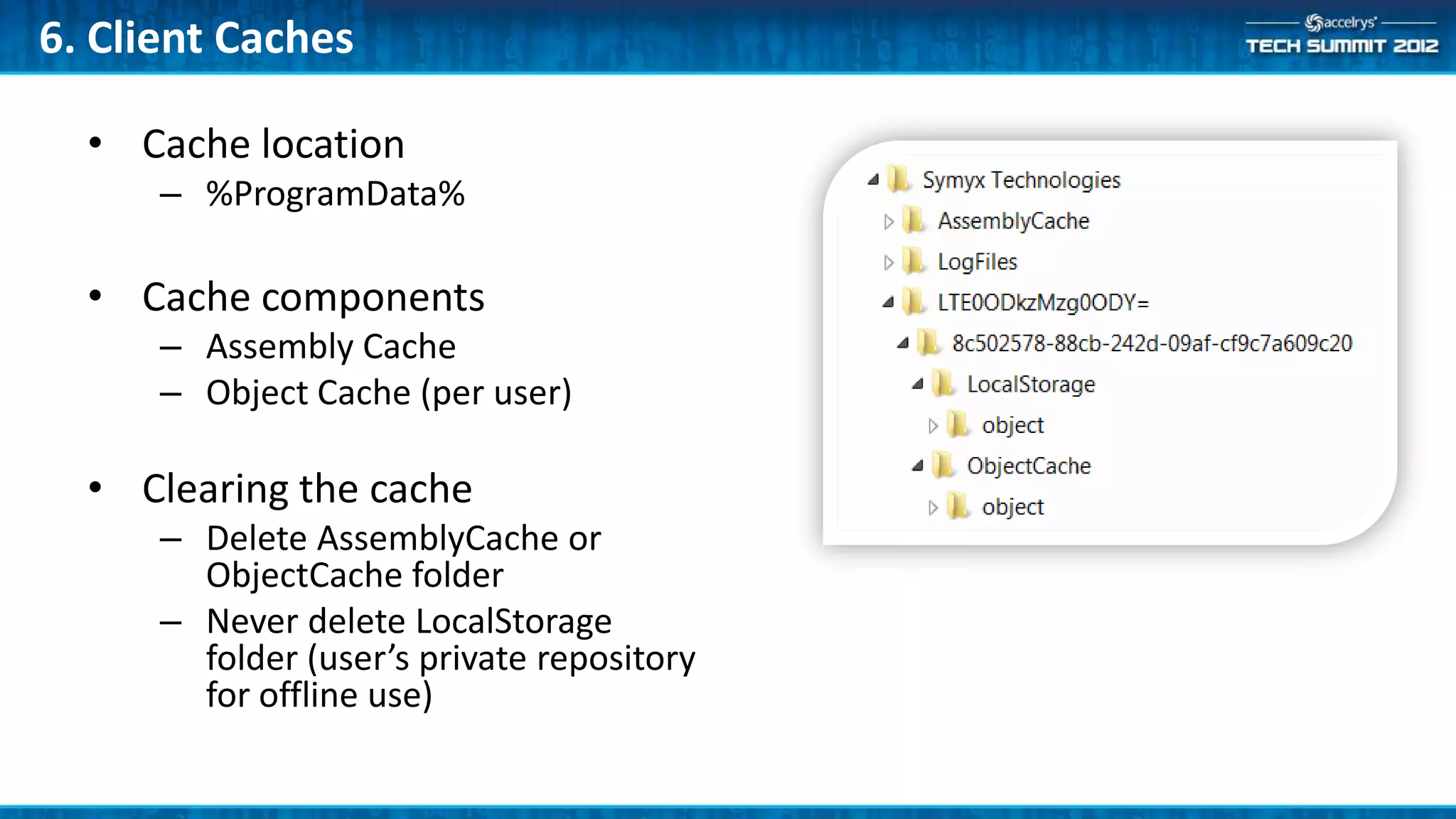
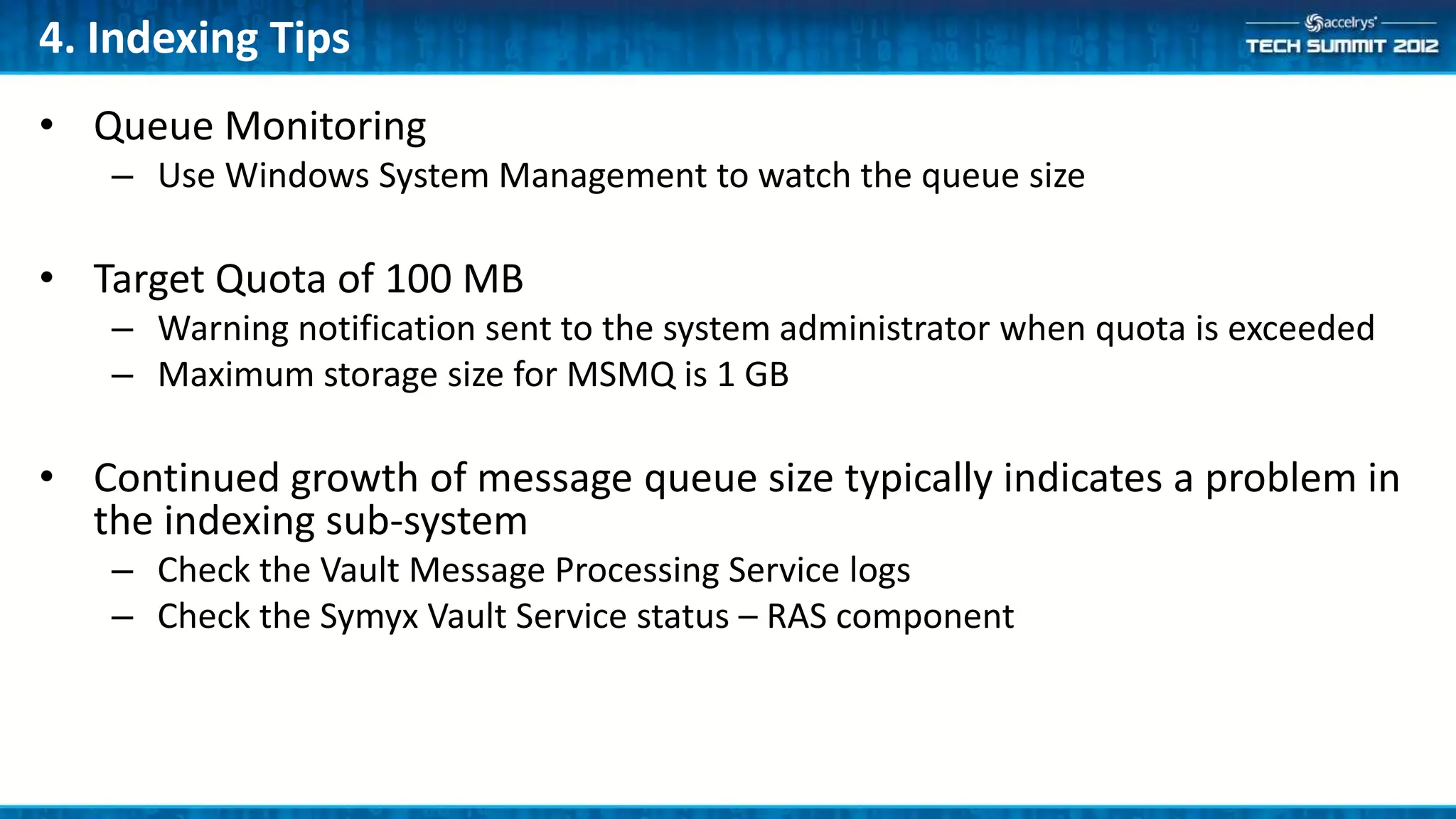
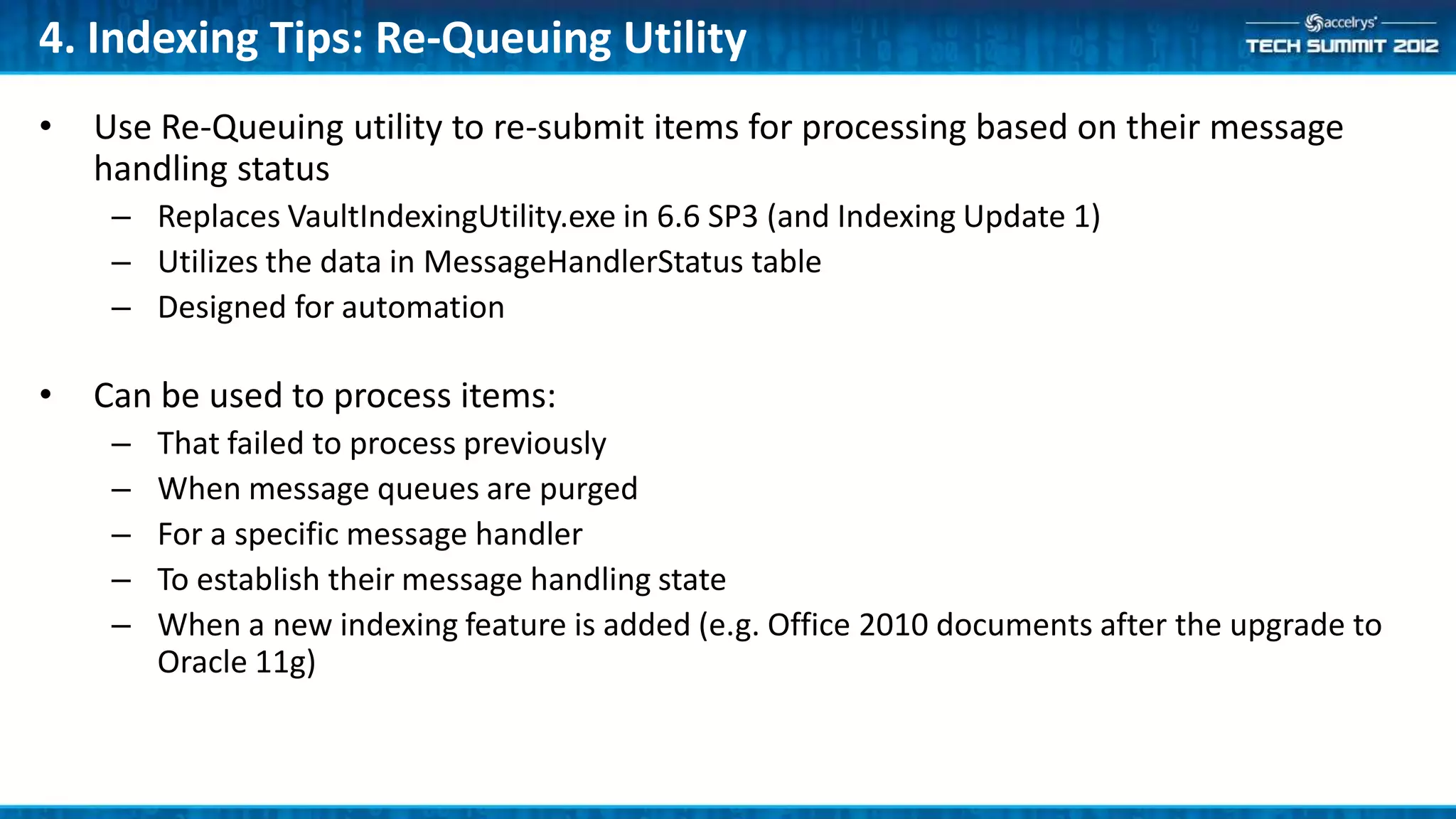
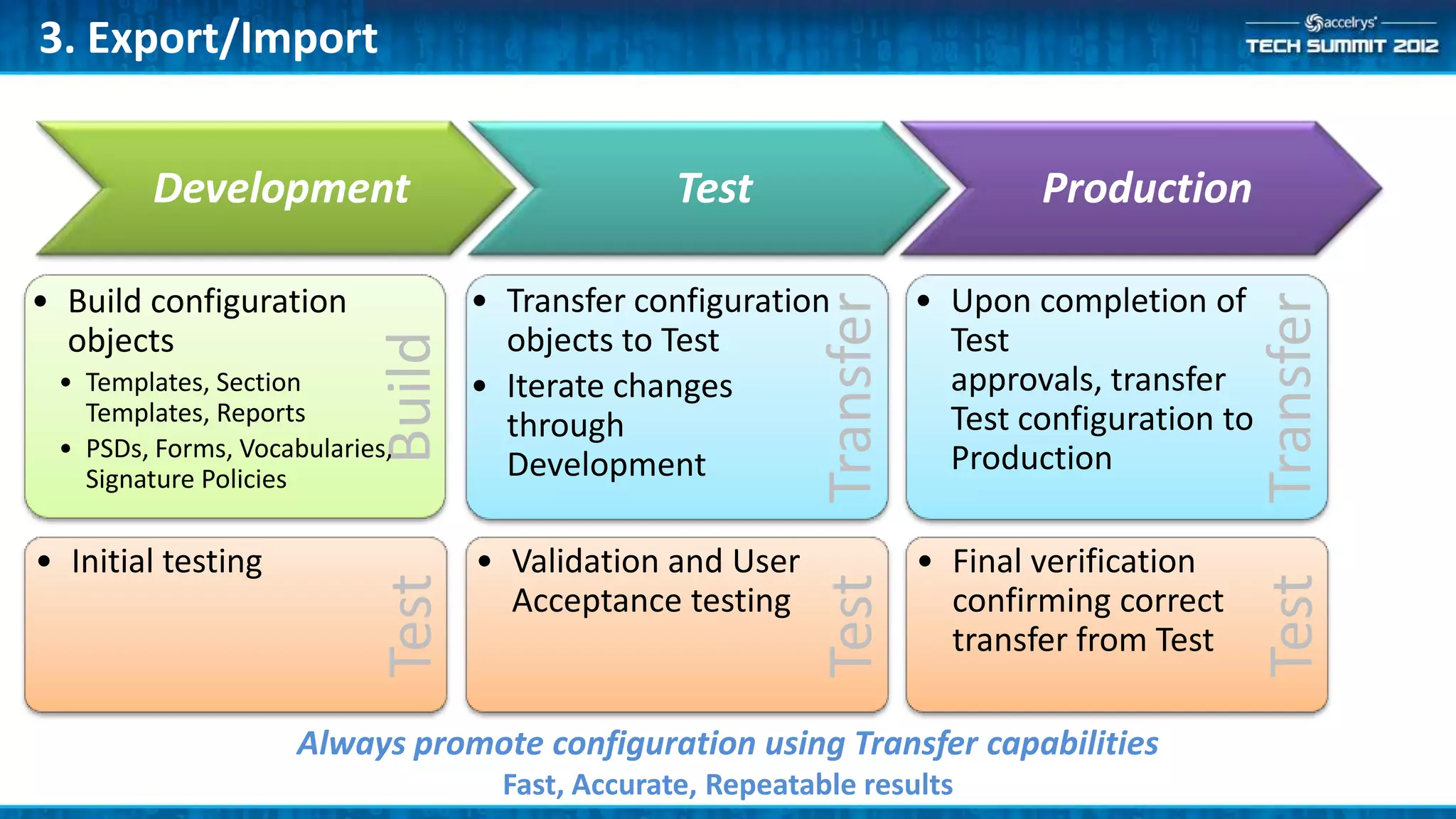
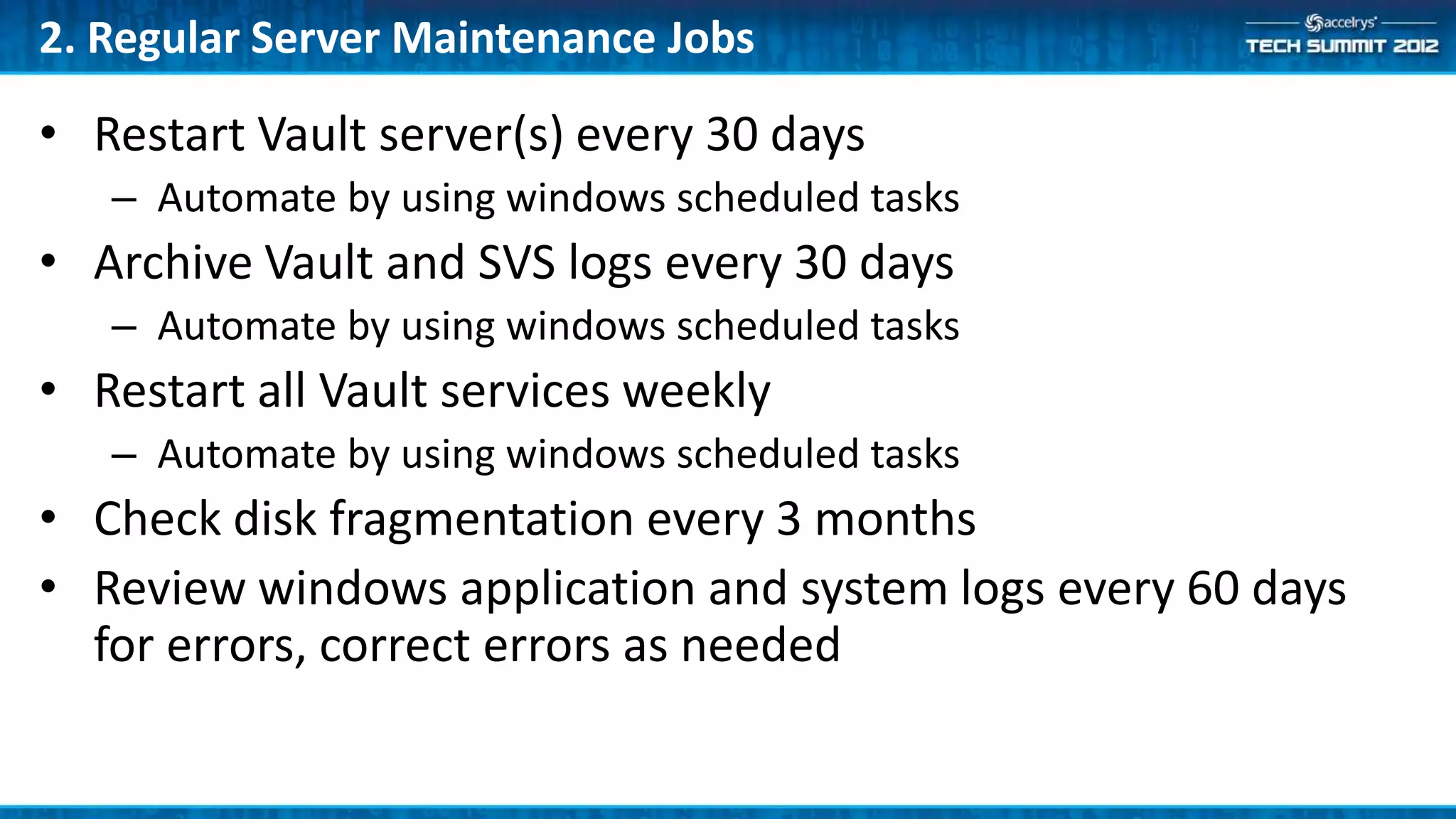
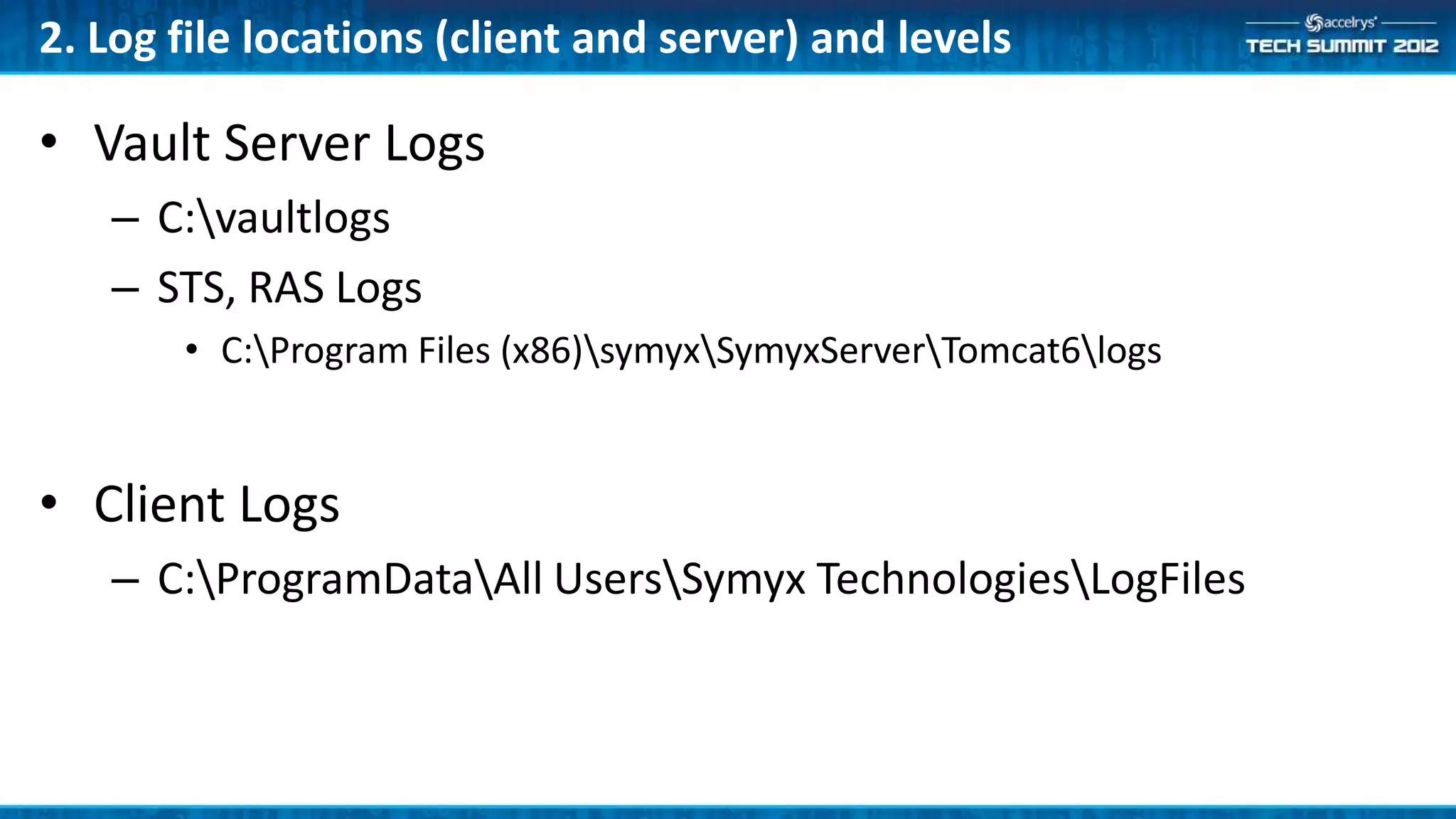
This document provides a summary of the top 10 things every Symyx Notebook administrator should know. It covers documentation locations, the Notebook architecture, vault services, SSL certificates, workflow concepts, security, indexing, exporting/importing, server maintenance, and usage of global administrators. Regular server maintenance and contacting support are also discussed.