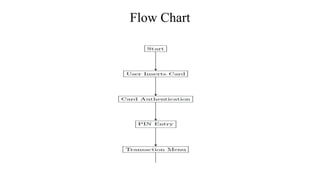
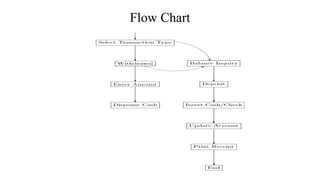
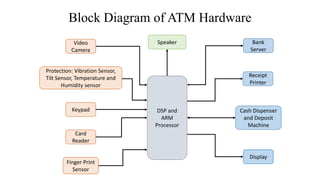
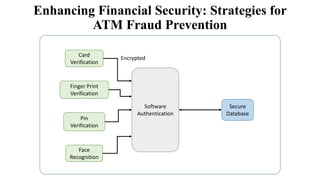
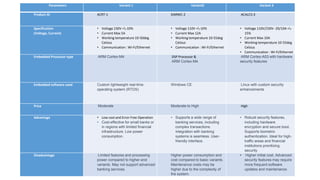
This document discusses an automated teller machine (ATM) and its components and functions. It describes how the first ATM was deployed in London in 1967 and the basic components of an ATM including its hardware components like a card reader, cash dispenser, display, and security features. It then discusses the software used in ATMs including user authentication, transaction processing, secure communication with banking servers, and error handling. Finally, it compares three variants of ATMs that differ in their specifications, processors, operating systems, prices, advantages, and disadvantages.