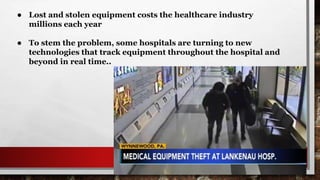
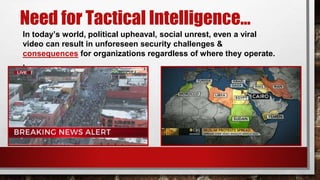
This document provides an overview of asset protection from the perspective of David, a security expert with over 15 years of experience. It discusses the principles of asset protection and provides examples from various industries, including healthcare, education, fast food, telecom, and aerospace. Effective asset protection requires understanding threats, vulnerabilities, and risks and implementing measures to deter, detect, deny and delay threats while defending assets. It emphasizes the importance of mitigating risk through timely tactical intelligence that allows organizations to plan safe evacuations and take proactive steps to continue operations.