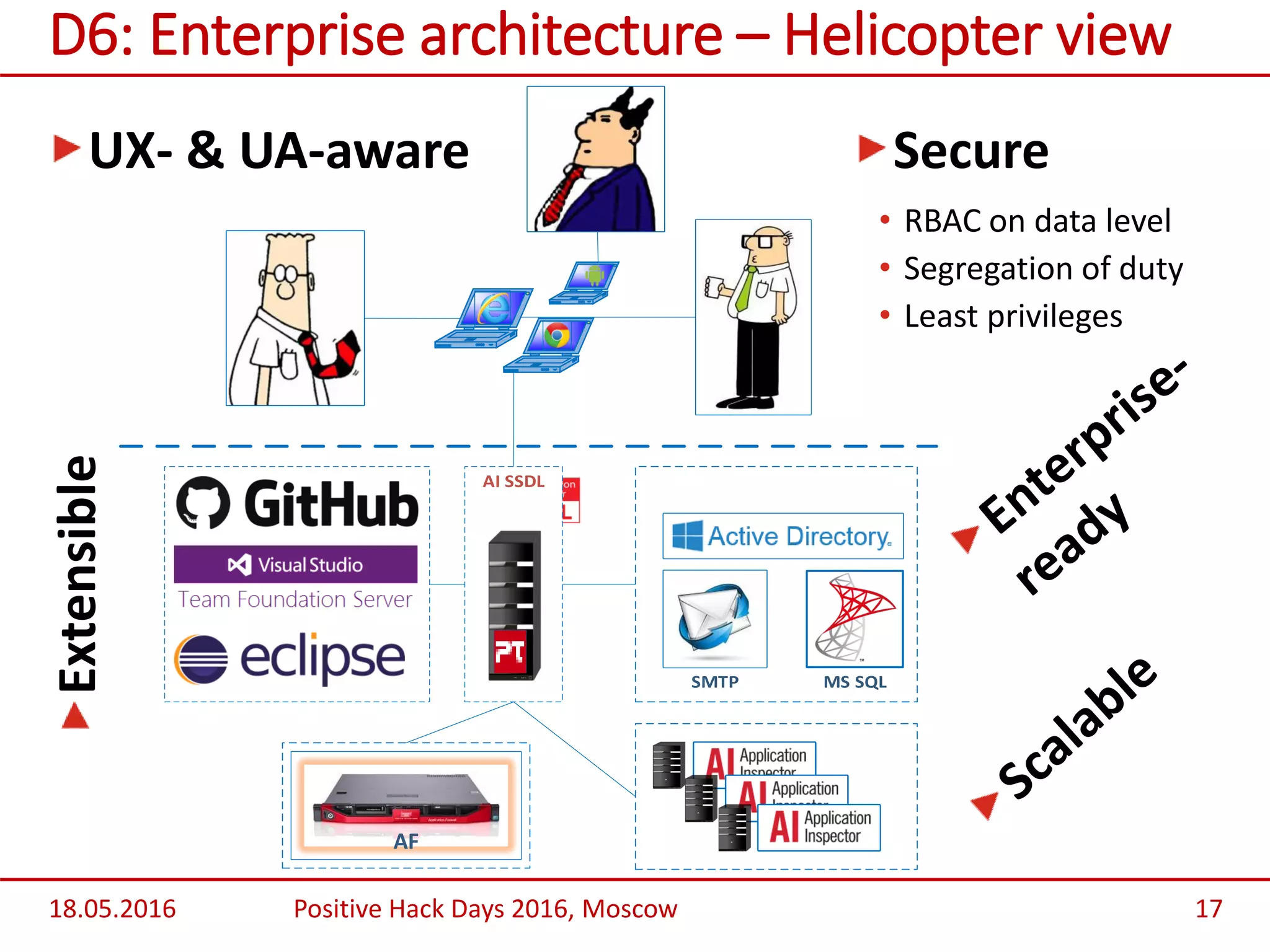
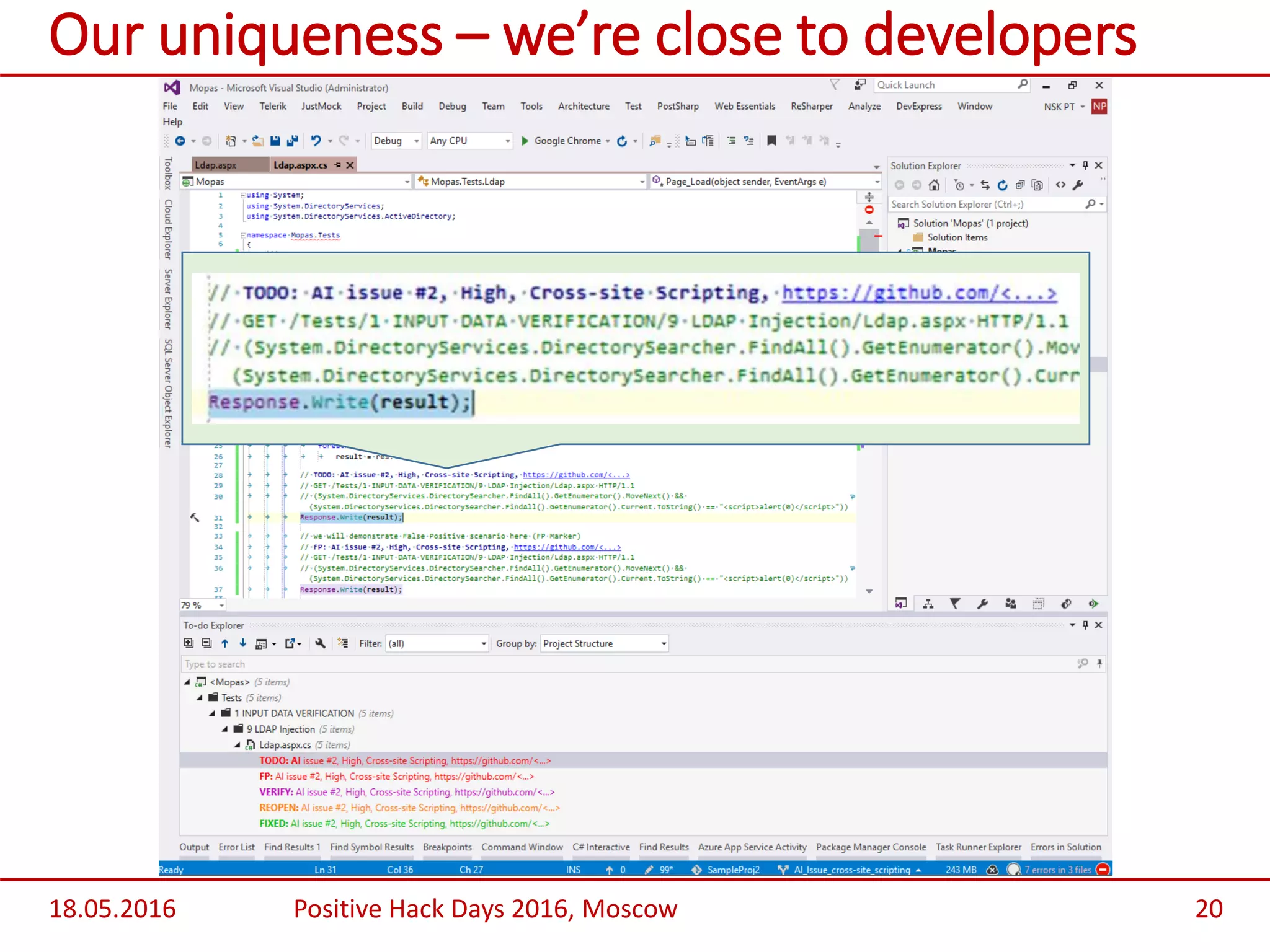
Valery Boronin presented on Application Inspector SSDL Edition, an application security testing tool. He began with an overview of common problems with application security like poor code quality costing over $500 billion annually. He then demonstrated Application Inspector SSDL Edition's capabilities like automated scanning, issue tracking, role-based access controls, and guidance for developers on fixing vulnerabilities. Benefits highlighted were helping develop more secure software through interaction with developers and automatic validation of fixes. Future plans include integration with build servers, IDEs, and providing more customization, compliance support, and analytics.