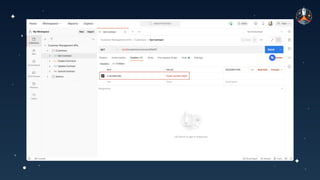
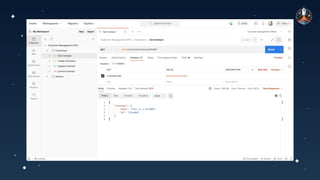
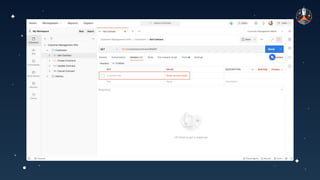
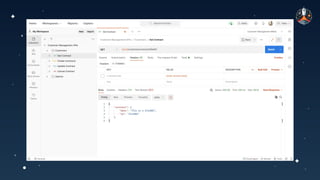
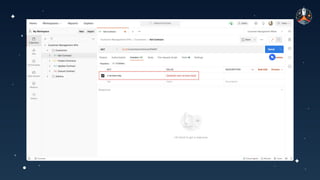
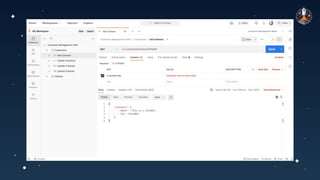
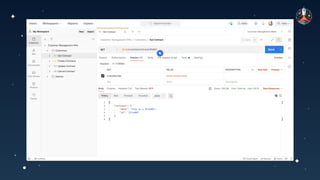
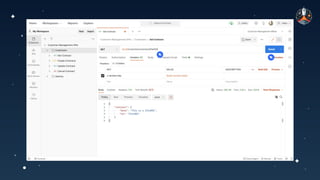
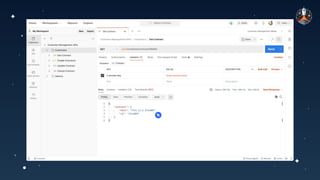
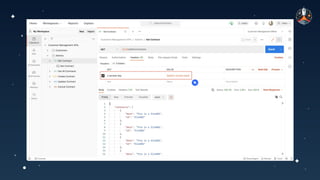
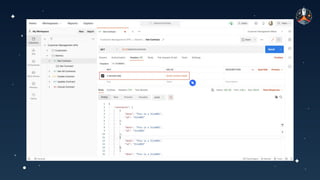
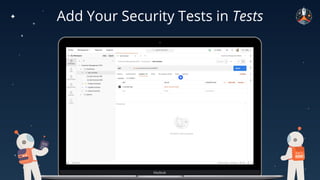
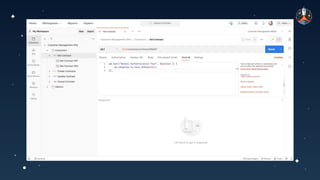
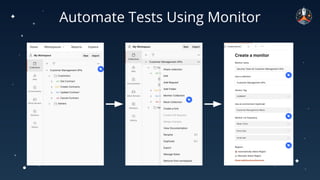
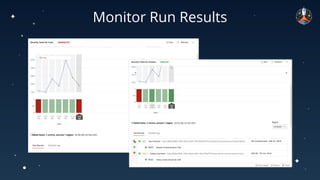
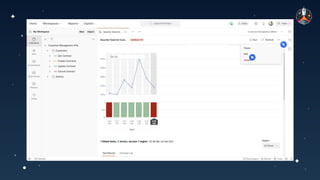
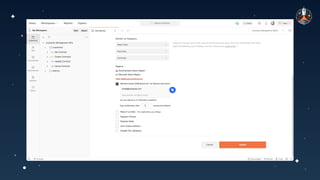
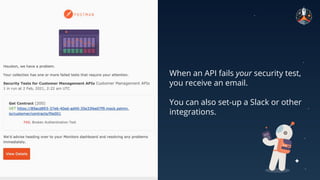
The document discusses common API vulnerabilities, their severity, and mitigation strategies using Postman. It highlights key vulnerabilities from the OWASP API Top 10 list, including broken authentication and authorization issues, and emphasizes the importance of an API-first workflow for security teams. The presentation also introduces automation techniques for security testing through Postman's monitoring features.