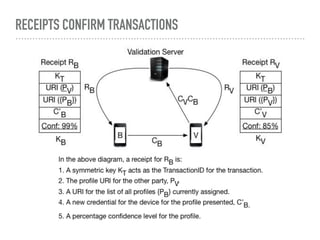
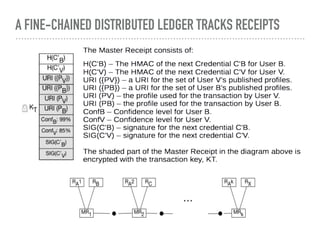
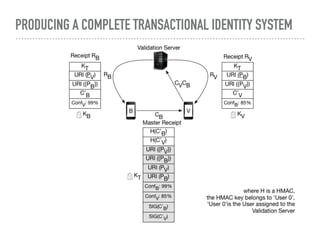
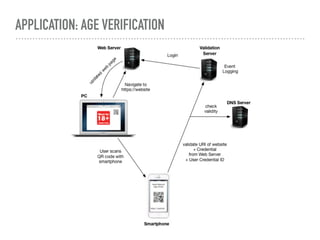
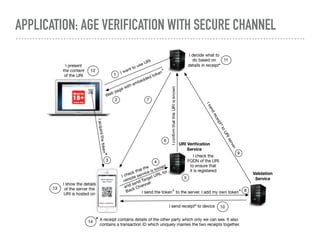
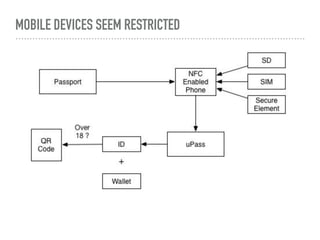
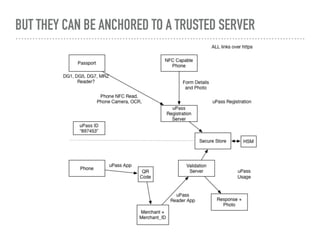
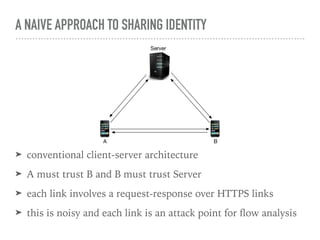
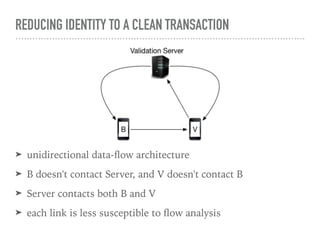
The document discusses the quest for a global digital identity system that is secure, embraces anonymity, and can scale to global needs while adhering to common law principles. It critiques current identity solutions and proposes a unidirectional data-flow architecture to enhance security and reduce points of vulnerability. The document also outlines managing identities through immutable profiles, anchored documents, and a fine-chained distributed ledger for transaction tracking.






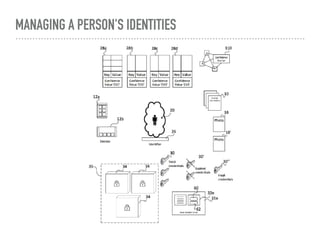
![MANAGING A PERSON'S IDENTITIES
➤ anchor documents
➤ passport, driving licence, identity card, ...
➤ biometric stream
➤ successions of biometric captures for the person
➤ profile set
➤ a choice of user profiles
➤ credentials
➤ large ephemeral random identifiers
➤ assigned to the [user | device | profile]](https://image.slidesharecdn.com/anonymitytrustaccountability-161123000221/85/Anonymity-trust-accountability-11-320.jpg)