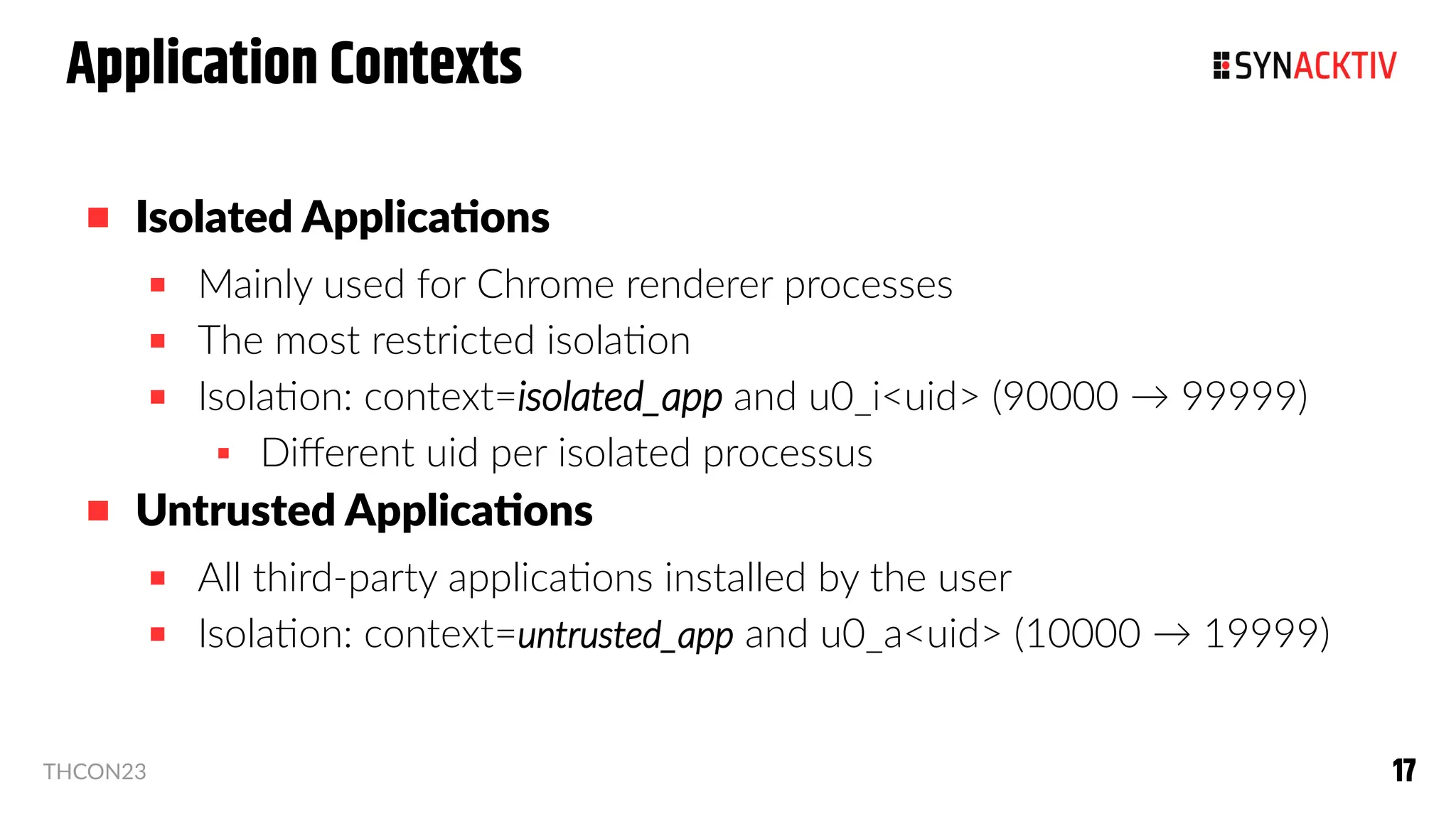
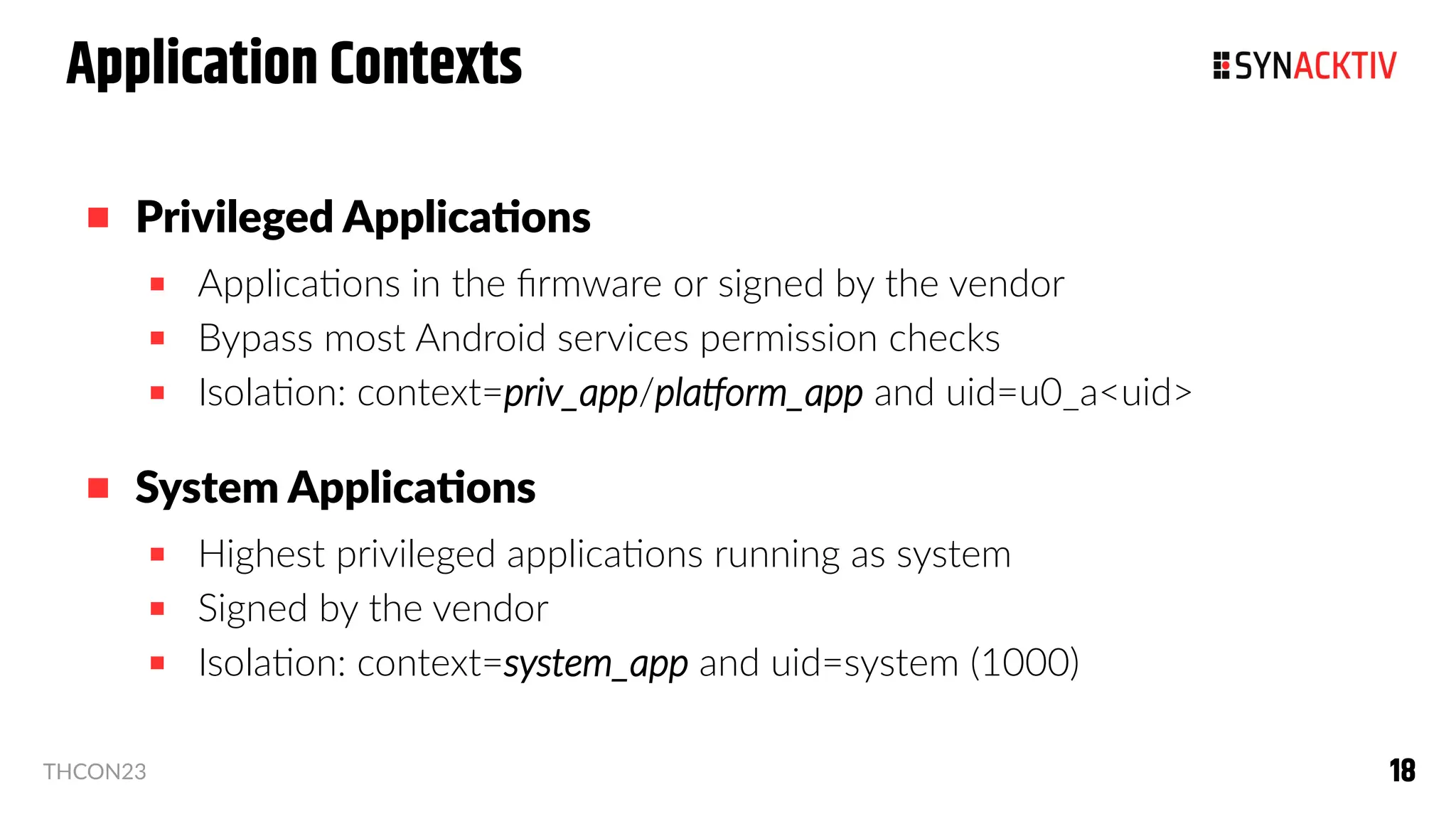
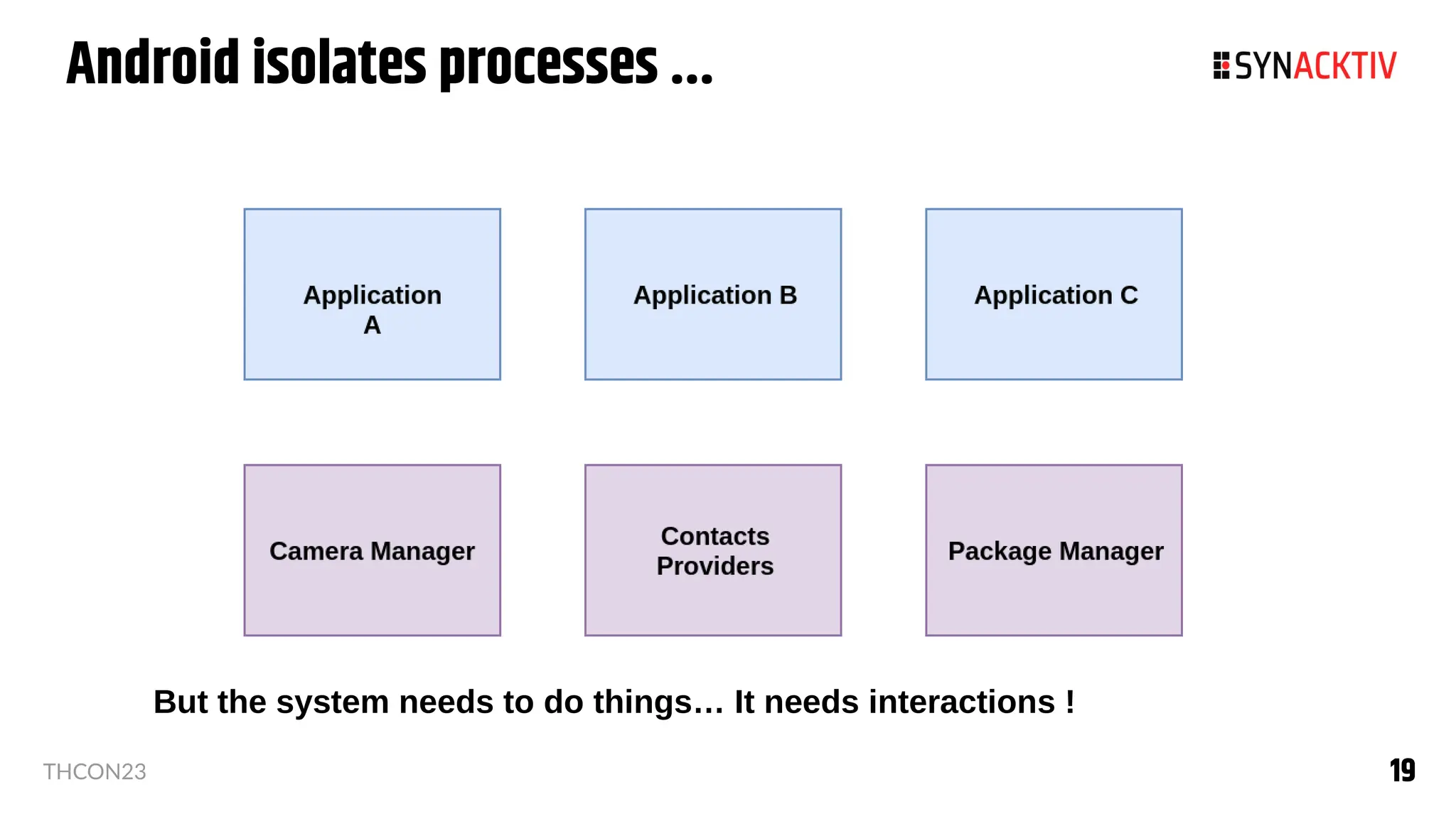
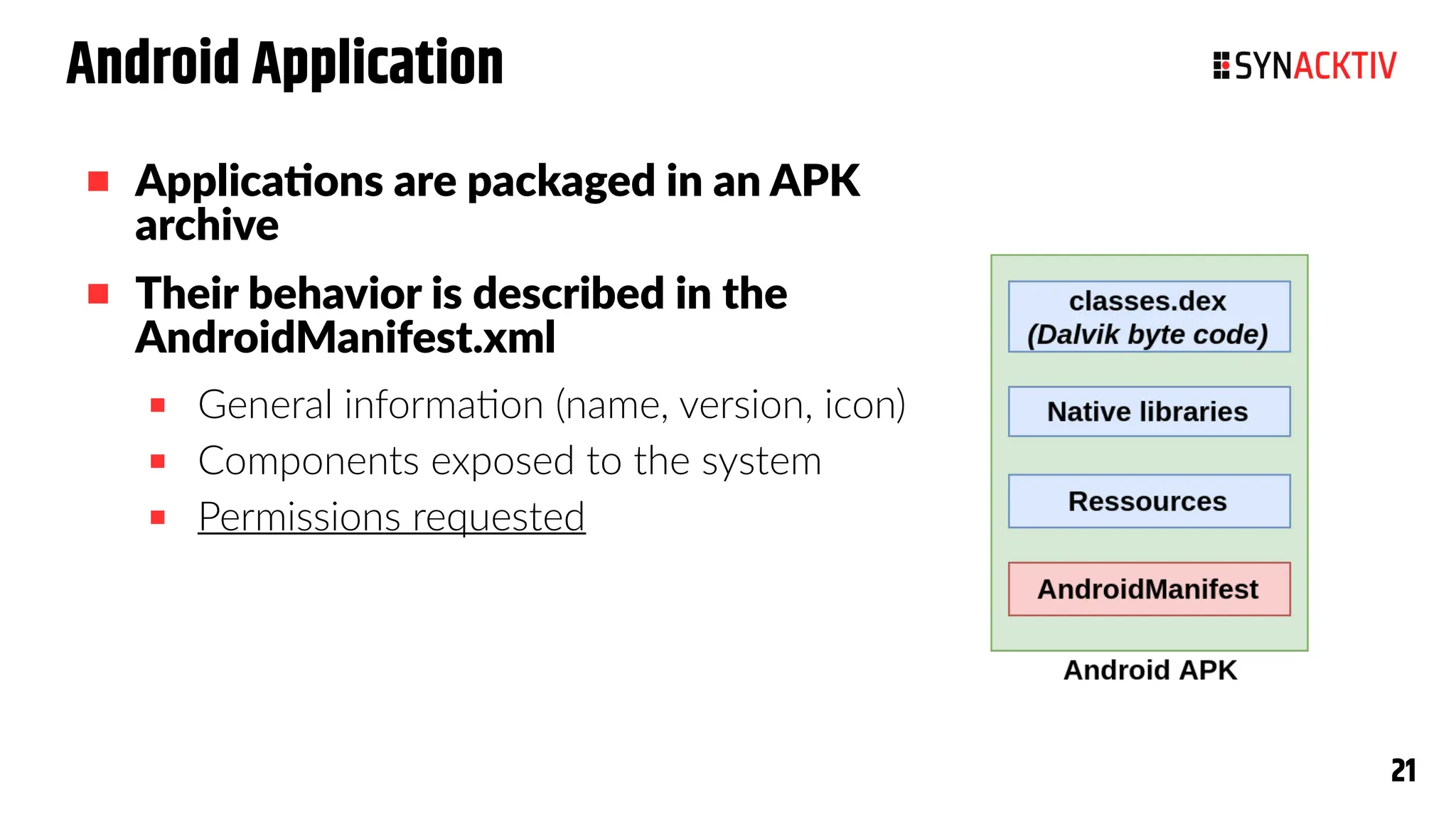
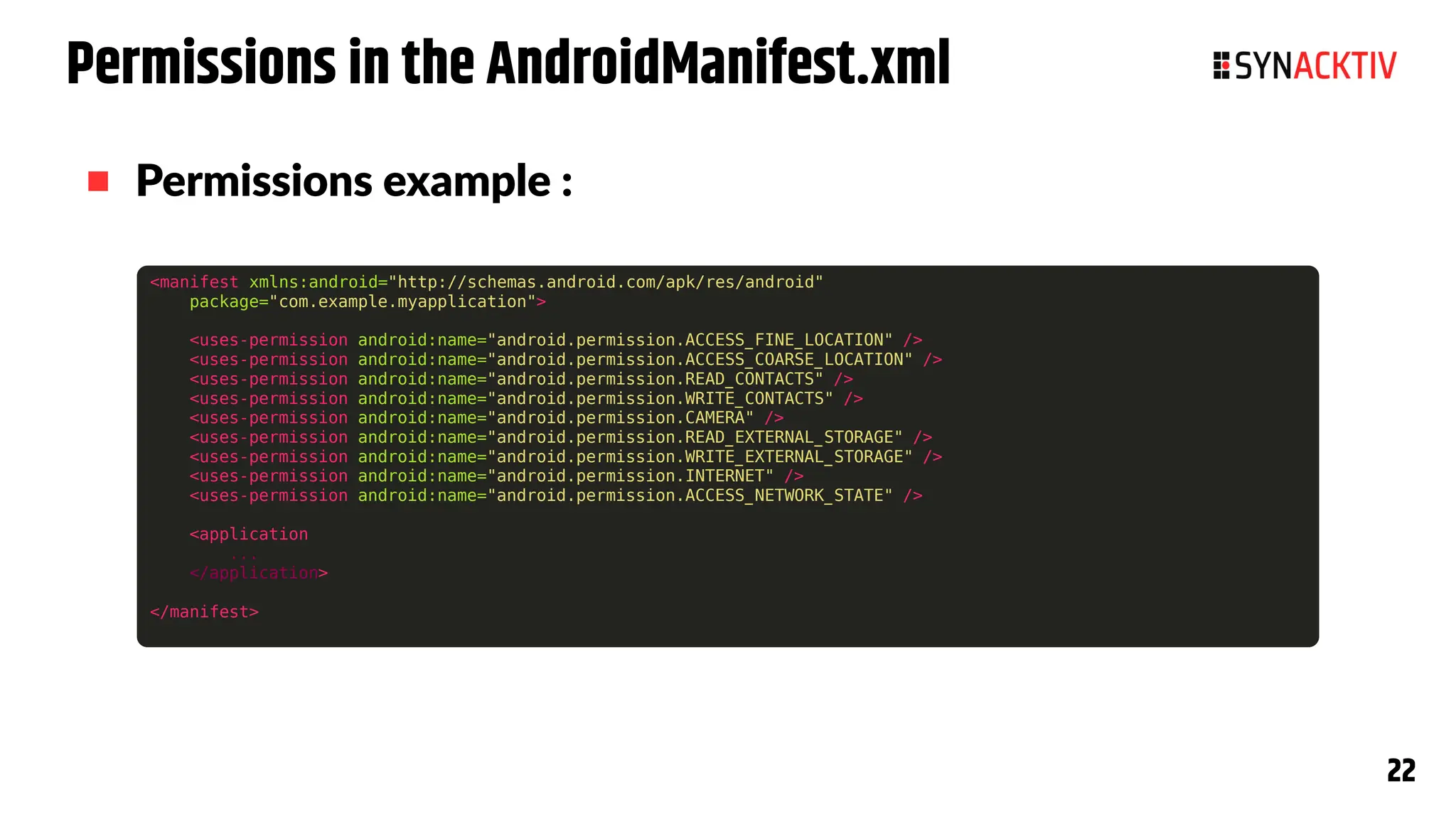
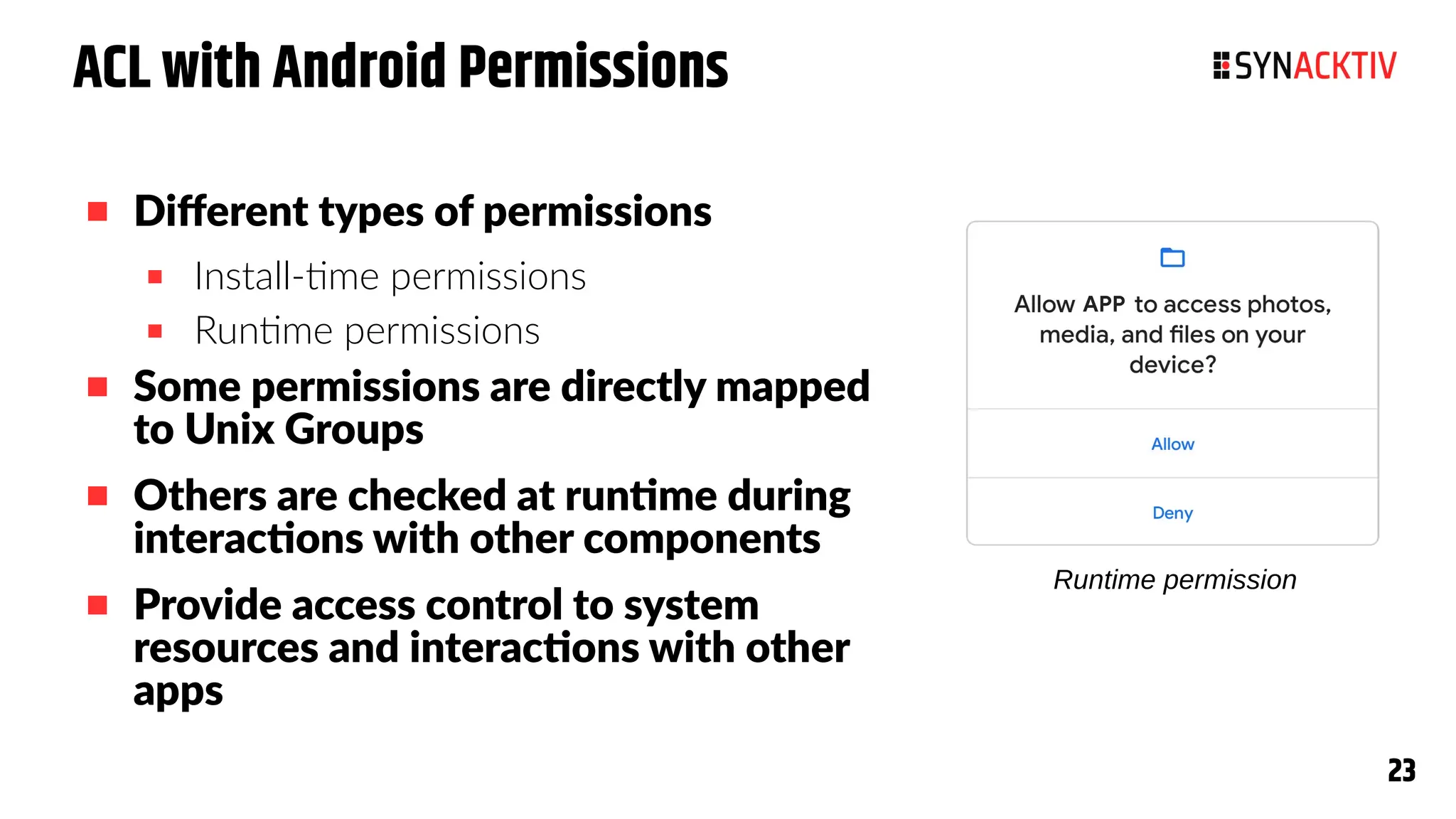
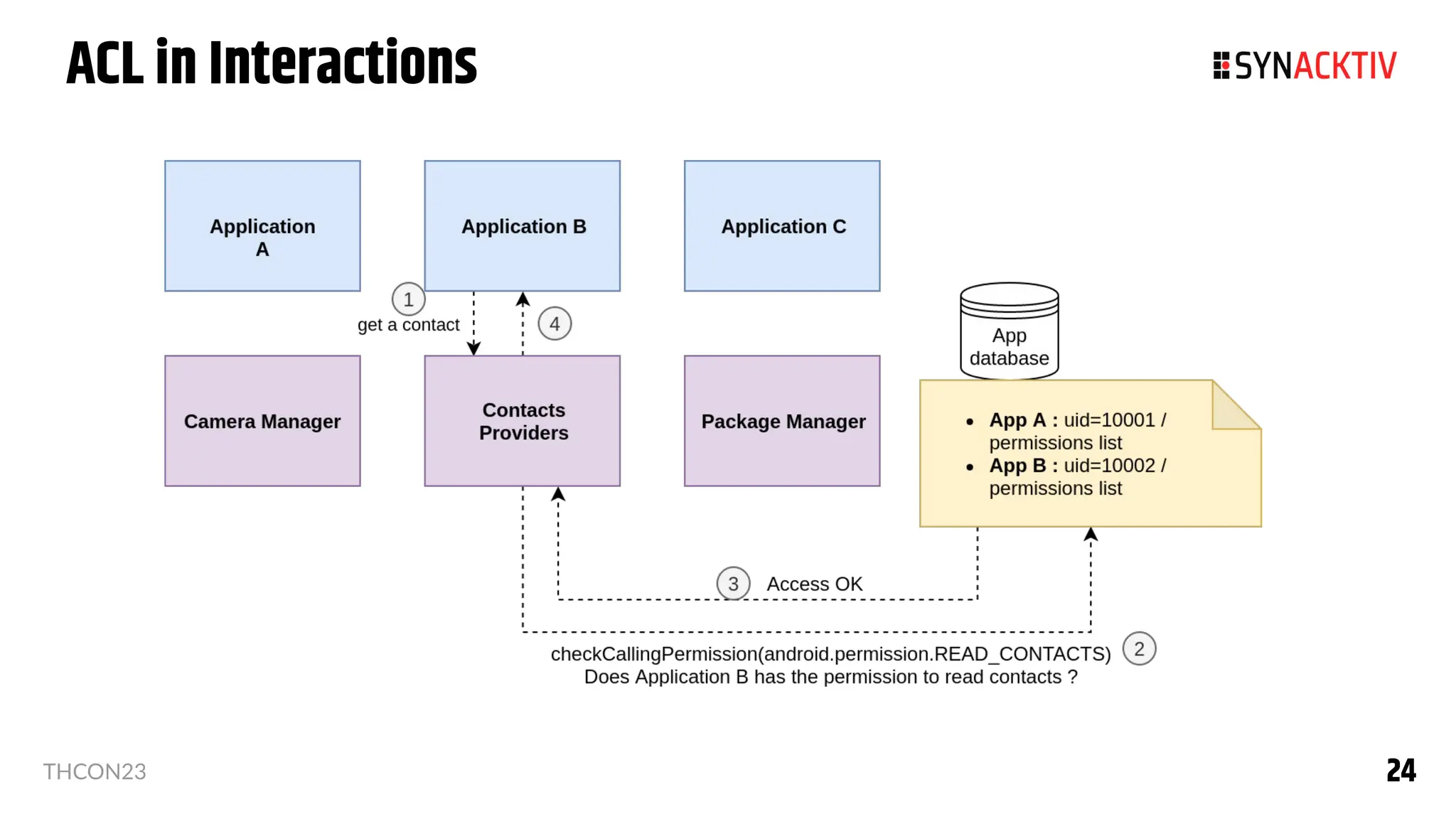
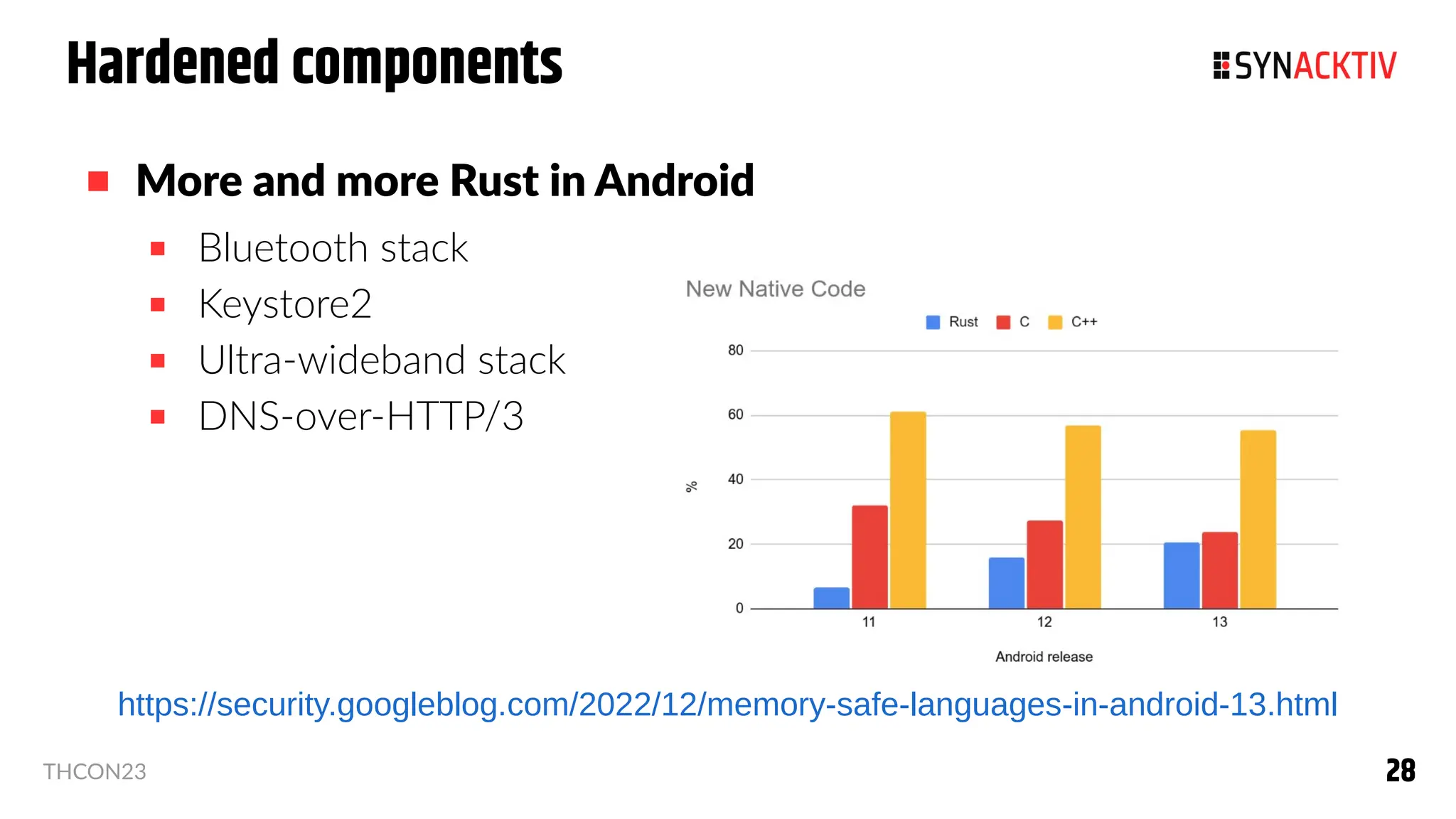
The document summarizes the Android security model. It describes how Android isolates applications using Linux users and groups, SELinux, and SECCOMP filtering to restrict syscalls. It also discusses how permissions are used to control interactions between applications and access to sensors and data. The security model is strengthened over time with measures like ASLR, CFI, and compiler sanitizers to mitigate vulnerabilities.





![12
12
THCON23
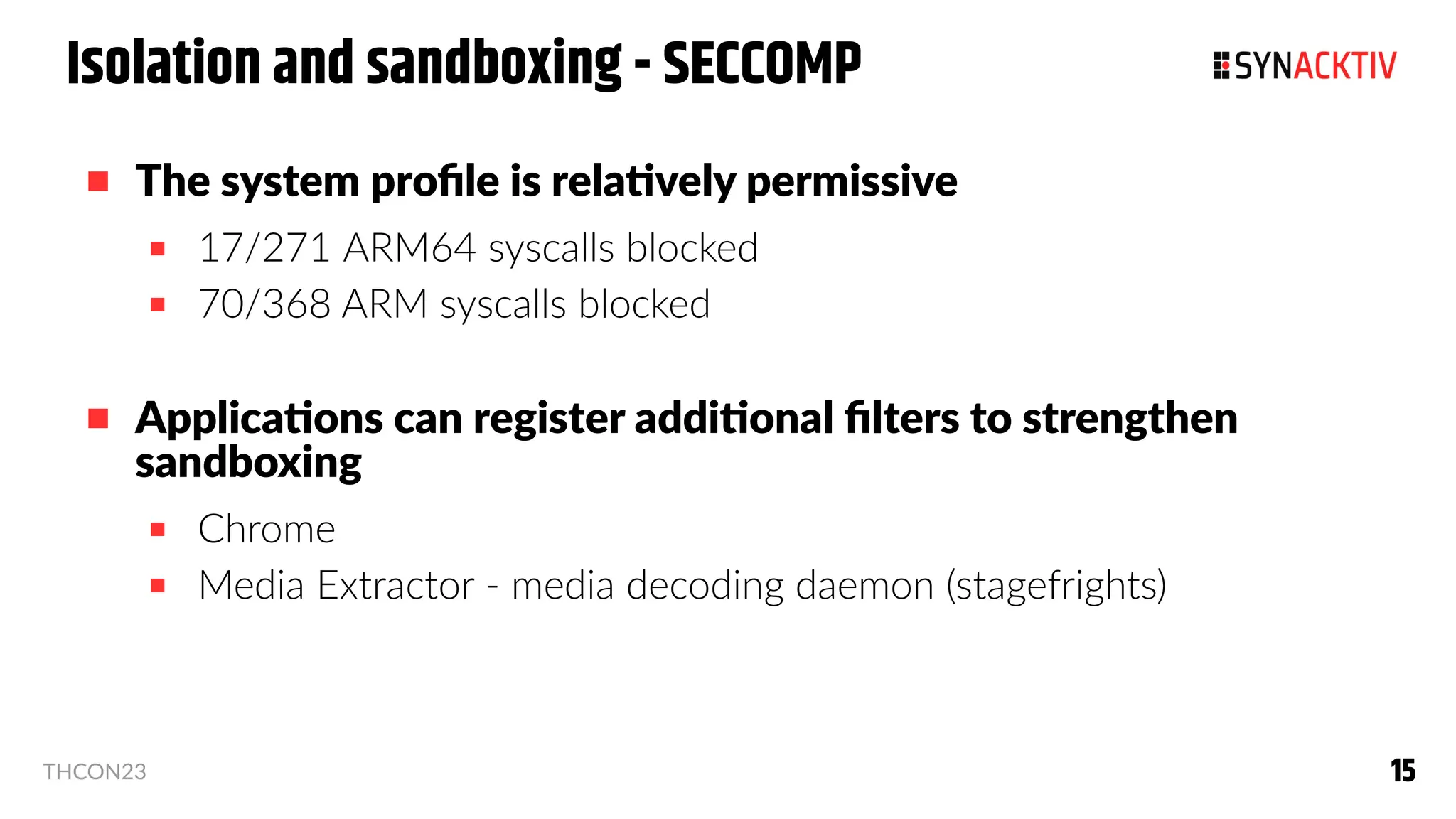
Isolation and sandboxing - SELinux
SELinux: Security Enhanced Linux
Enforced starting with Android 4.4 (2013)
Implemented as a Linux Security Module (LSM)
Implements security filtering hooks which are called inside the kernel
// Extract of fs/ioctl.c
SYSCALL_DEFINE3(ioctl, unsigned int, fd, unsigned int, cmd, unsigned long, arg)
{
struct fd f = fdget(fd);
int error;
if (!f.file)
return -EBADF;
error = security_file_ioctl(f.file, cmd, arg);
if (error)
goto out;
error = do_vfs_ioctl(f.file, fd, cmd, arg);
// [...]](https://image.slidesharecdn.com/thcon23theandroidsecuritymodel-231022130926-5712f4e7/75/thcon23_The_Android_Security_Model-pdf-12-2048.jpg)