Embed presentation
Downloaded 54 times

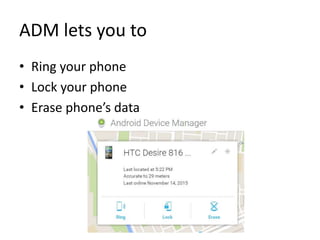
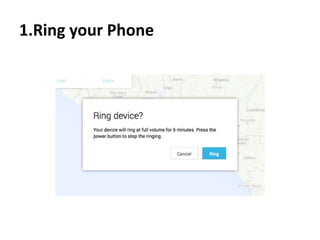
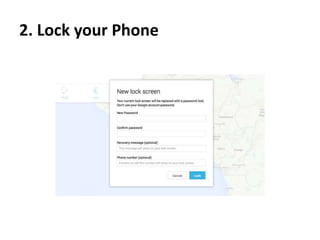

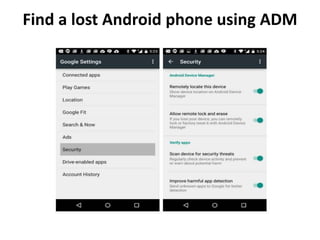
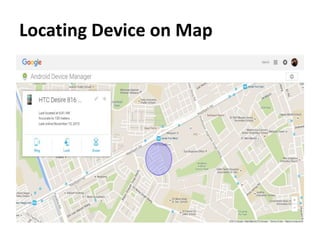
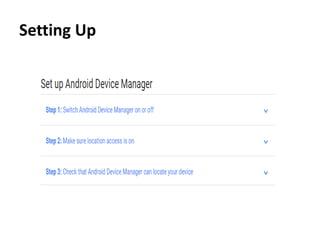


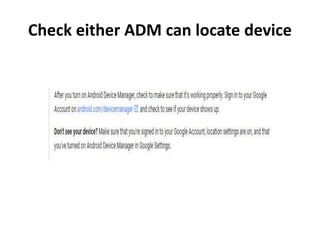

The document outlines the features of the Android Device Manager (ADM), which helps users locate lost devices and protect data. Key functionalities include ringing the phone, locking it, and erasing data. Additionally, it provides instructions for setting up ADM and switching on location access.














