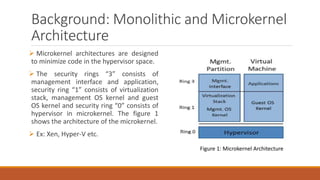
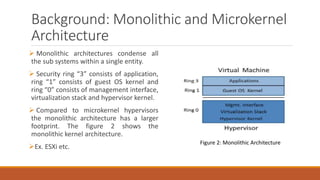
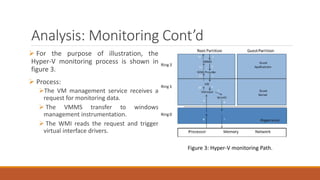
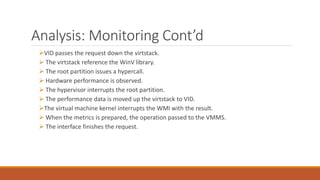
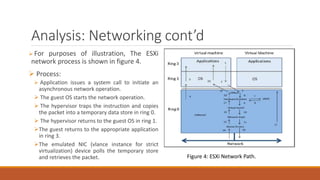
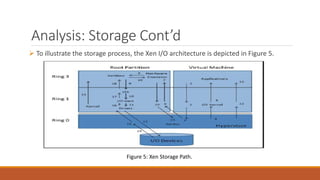
The document analyzes monolithic and microkernel hypervisor architectures, focusing on their security implications and the tradeoffs involved. It evaluates six architectural features, highlighting how both designs present vulnerabilities and unique strengths. Ultimately, the study concludes that neither architecture can be deemed more secure due to their inherent weaknesses.