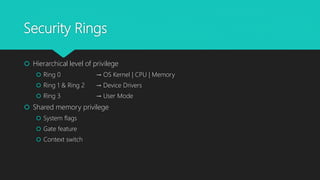
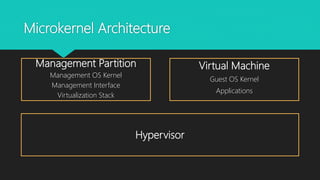
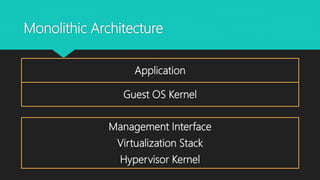
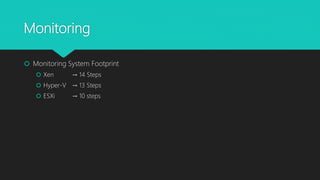
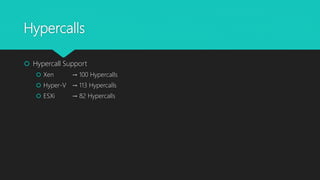
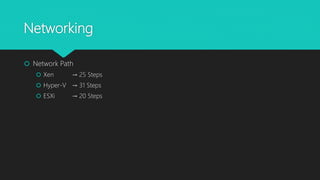
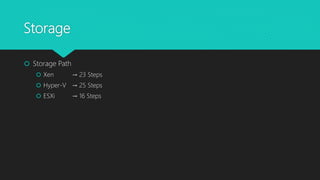
The document analyzes monolithic and microkernel hypervisor architectures in the context of secure hypervisor design, highlighting their structural differences and security implications. It compares features such as management interfaces, monitoring capabilities, and the management of hypercalls and interrupts across various platforms like ESXi, Xen, and Hyper-V. The conclusion emphasizes that well-written kernel code enhances security regardless of architecture.