The document discusses advanced DNS services focusing on application security and user privacy, presenting the 'getdns' library that supports new DNS protocol features and enhancements like DNSSEC for authenticity. It highlights various network protocol changes, the importance of public key infrastructure (PKI), and issues like certificate misissuance and censorship by network intermediaries. Additionally, it addresses DNS privacy challenges and solutions, such as using TLS transport and avoid filtering by middleboxes, while providing resources and upcoming events for further engagement in these topics.






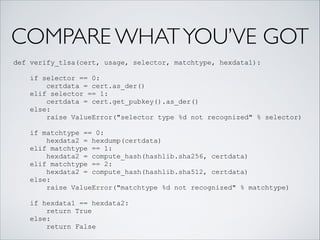
![ENTER GETDNS
shore@birch:~/src/tmp$ cat simple.py
import getdns, sys
!
context = getdns.Context()
ext = { 'dnssec_return_only_secure': getdns.EXTENSION_TRUE }
r = context.address(sys.argv[1], extensions=ext)
if r.status == getdns.RESPSTATUS_GOOD:
for addr in r.just_address_answers:
print(addr['address_data'])
if r.status == getdns.RESPSTATUS_NO_SECURE_ANSWERS:
print("No secure answers”)
!
shore@birch:~/src/tmp$ python simple.py getdnsapi.net
2a04:b900:0:100::37
185.49.141.37
!
shore@birch:~/src/tmp$ python simple.py google.com
No secure answers
shore@birch:~/src/tmp$](https://image.slidesharecdn.com/pycongetdns-160601011314/85/getdns-PyCon-presentation-11-320.jpg)






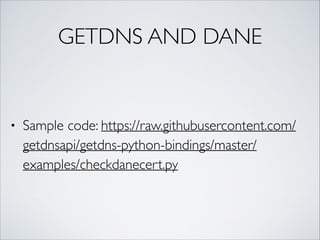
![GETTHE SERVER CERT
connection = SSL.Connection(sslctx, sock=sock)
connection.connect((ipaddr, port))
chain = connection.get_peer_cert_chain()
cert = chain[0]](https://image.slidesharecdn.com/pycongetdns-160601011314/85/getdns-PyCon-presentation-19-320.jpg)
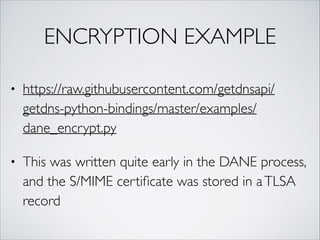
![PULL DATA OUT OFTHE
RECORD
def get_tlsa_rdata_set(replies, requested_usage=None):
tlsa_rdata_set = []
for reply in replies:
for rr in reply['answer']:
if rr['type'] == getdns.RRTYPE_TLSA:
rdata = rr['rdata']
usage = rdata['certificate_usage']
selector = rdata['selector']
matching_type = rdata['matching_type']
cadata = rdata['certificate_association_data']
cadata = str(cadata).encode('hex')
if usage == requested_usage:
tlsa_rdata_set.append(
(usage, selector, matching_type, cadata) )
return tlsa_rdata_set](https://image.slidesharecdn.com/pycongetdns-160601011314/85/getdns-PyCon-presentation-20-320.jpg)


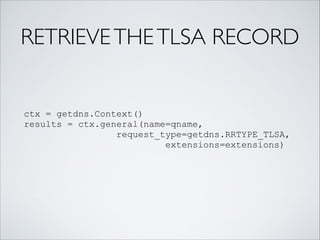
![PRIVACY PROTECTION
• TLS transport:
context.dns_transport_list =
[ getdns.TRANSPORT_TLS ]
• Padding:
context.tls_query_padding_blocksize = 256](https://image.slidesharecdn.com/pycongetdns-160601011314/85/getdns-PyCon-presentation-26-320.jpg)