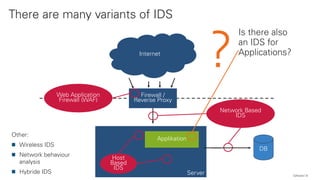
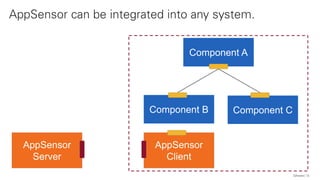
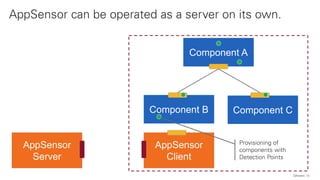
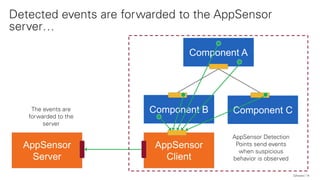
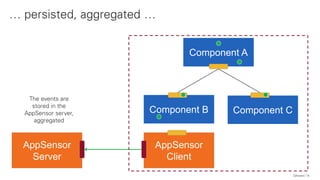
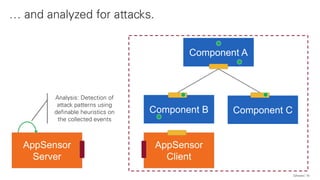
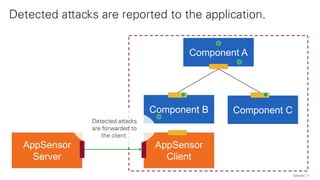
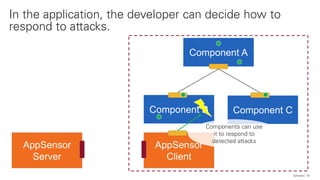
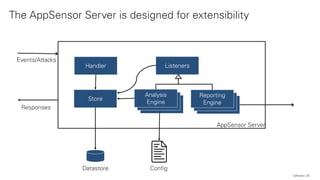
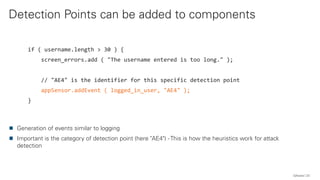
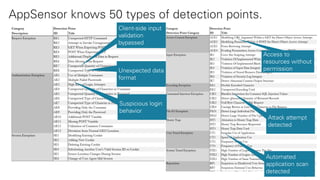
The document discusses the OWASP AppSensor framework, which aims to detect attacks in applications by integrating intrusion detection into the application's logic. It highlights the limitations of traditional IDS systems and suggests a context-sensitive approach that uses log-like detection points for automated attack detection. Additionally, it notes that while AppSensor's development has stalled, the conceptual framework can still be implemented using standard methods and tools.