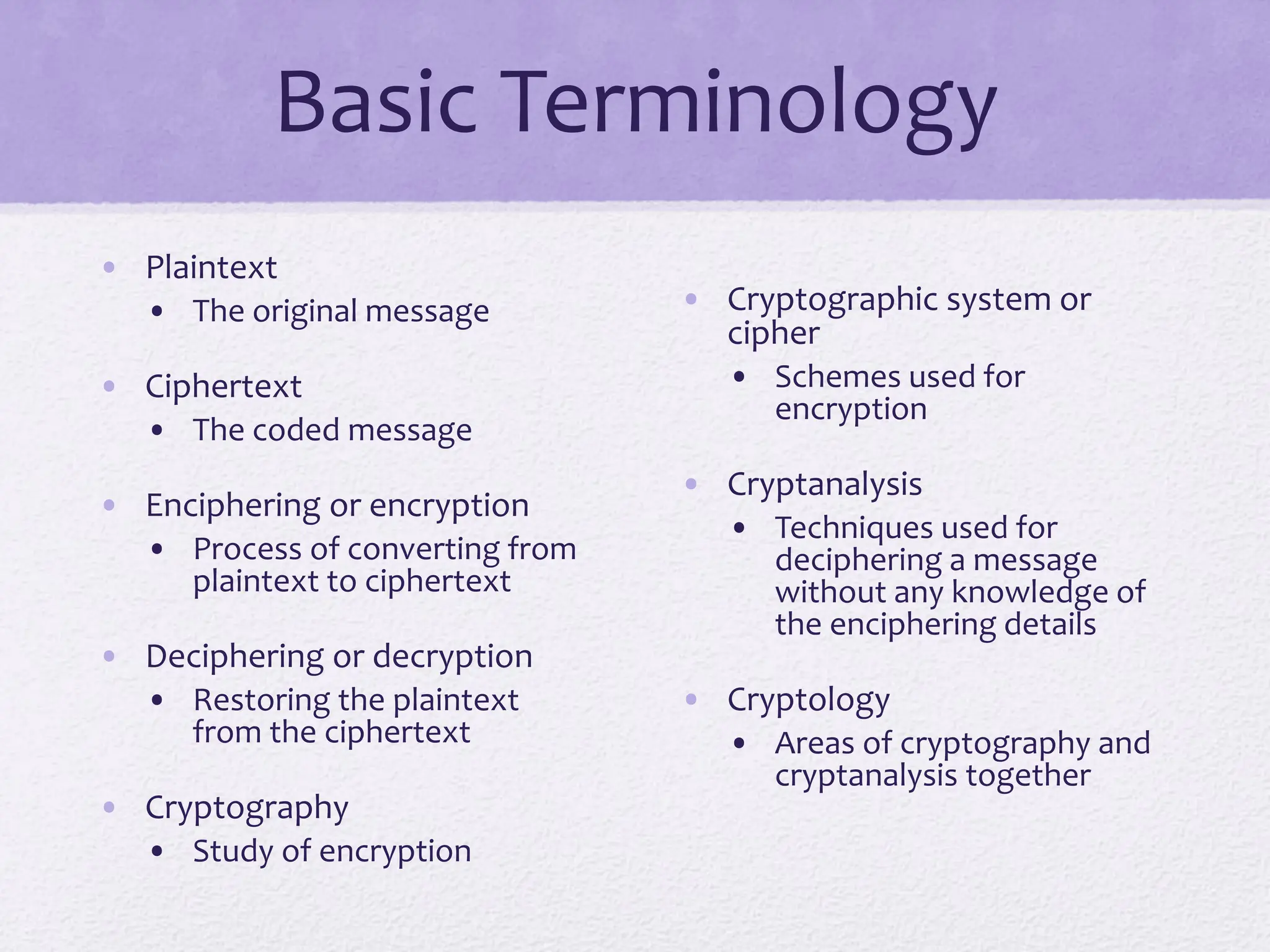
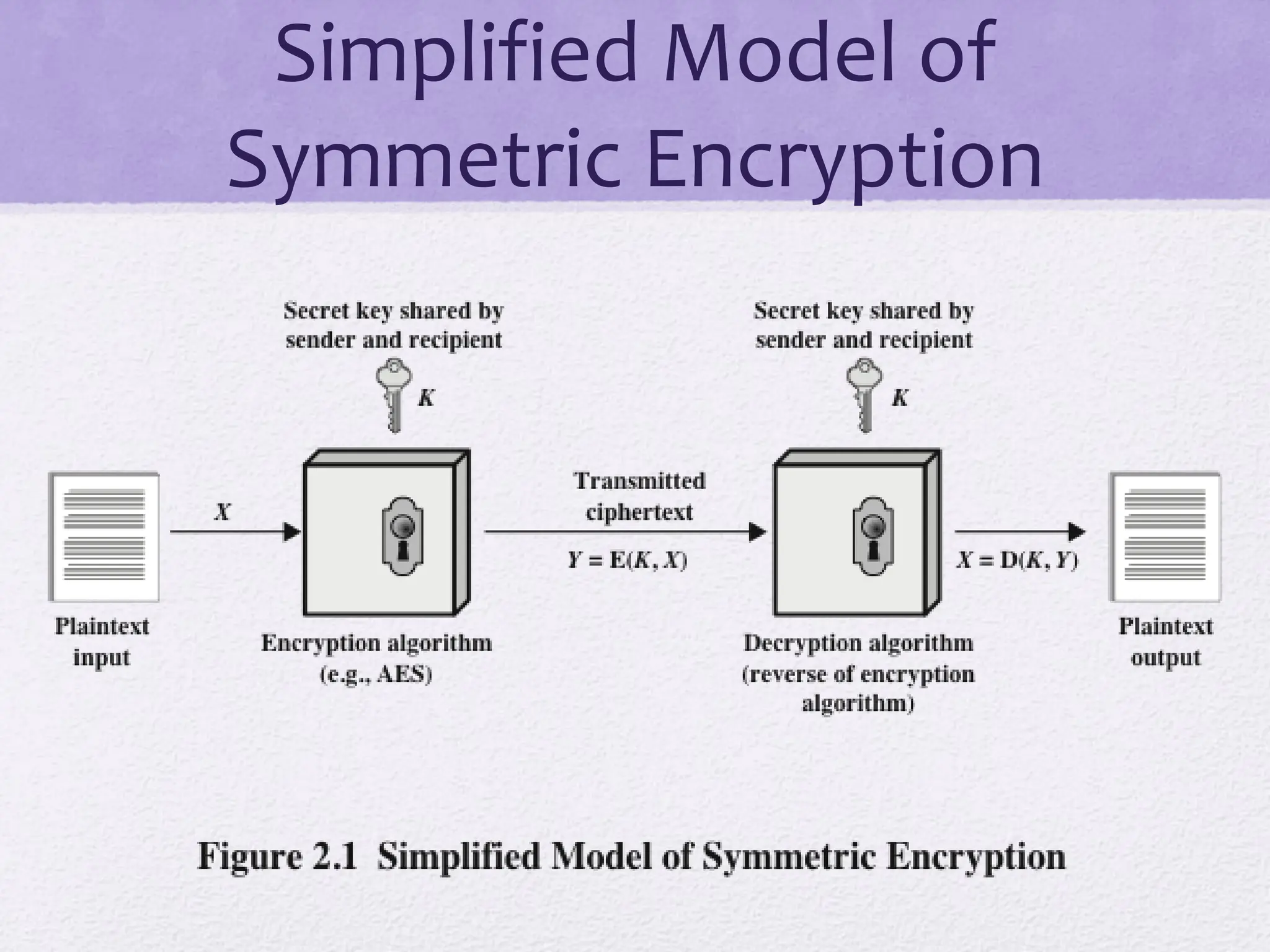
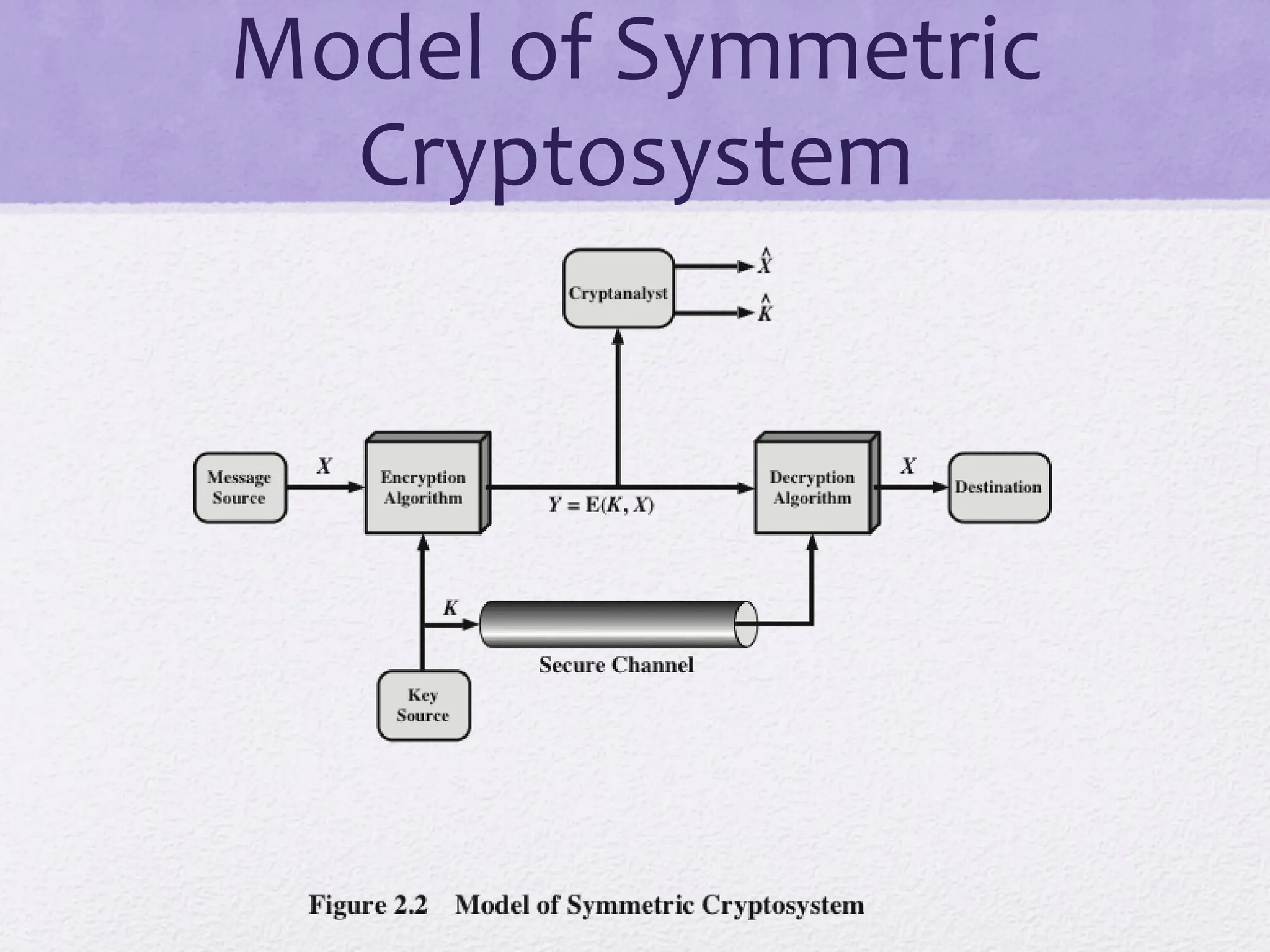
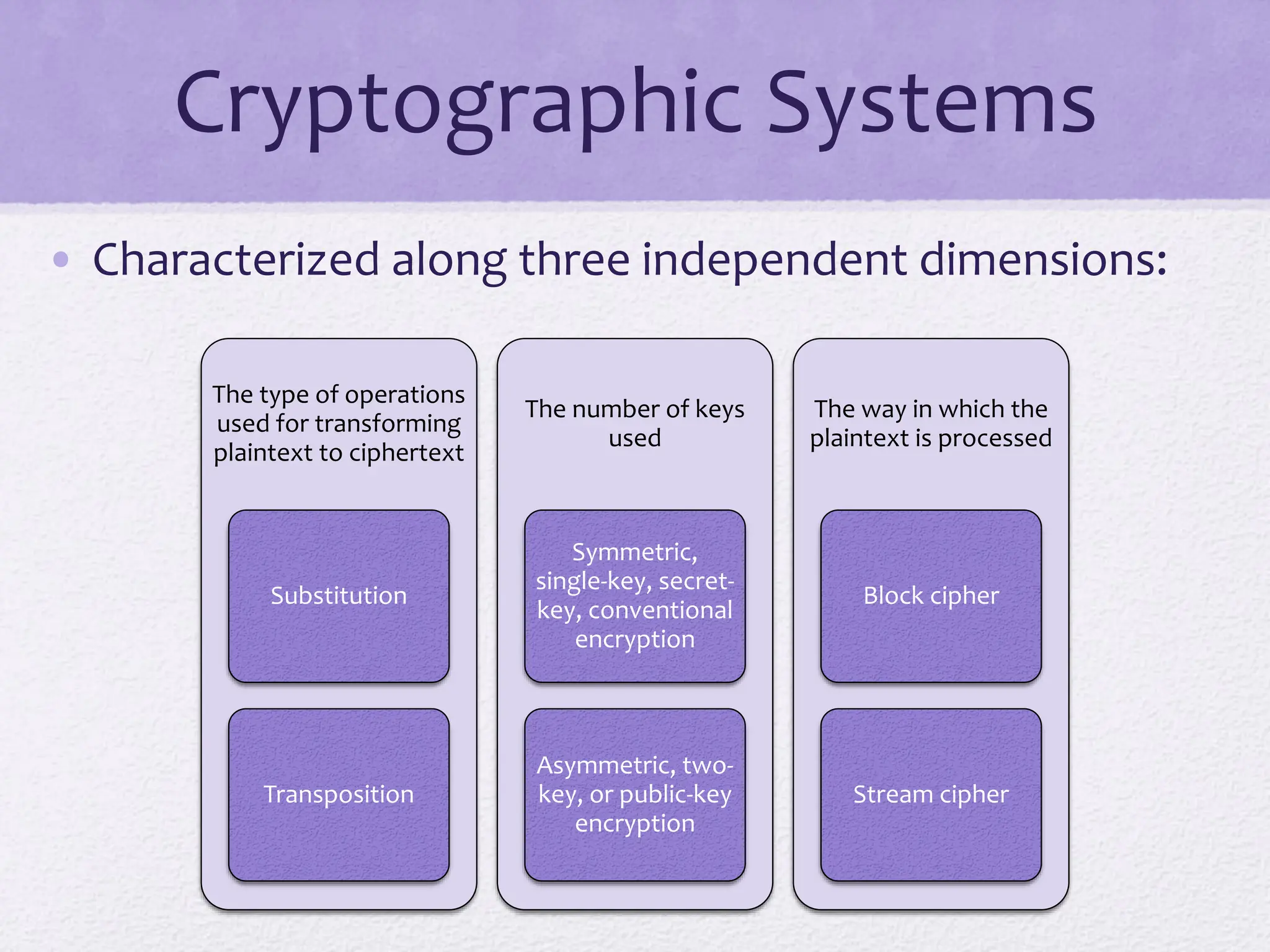
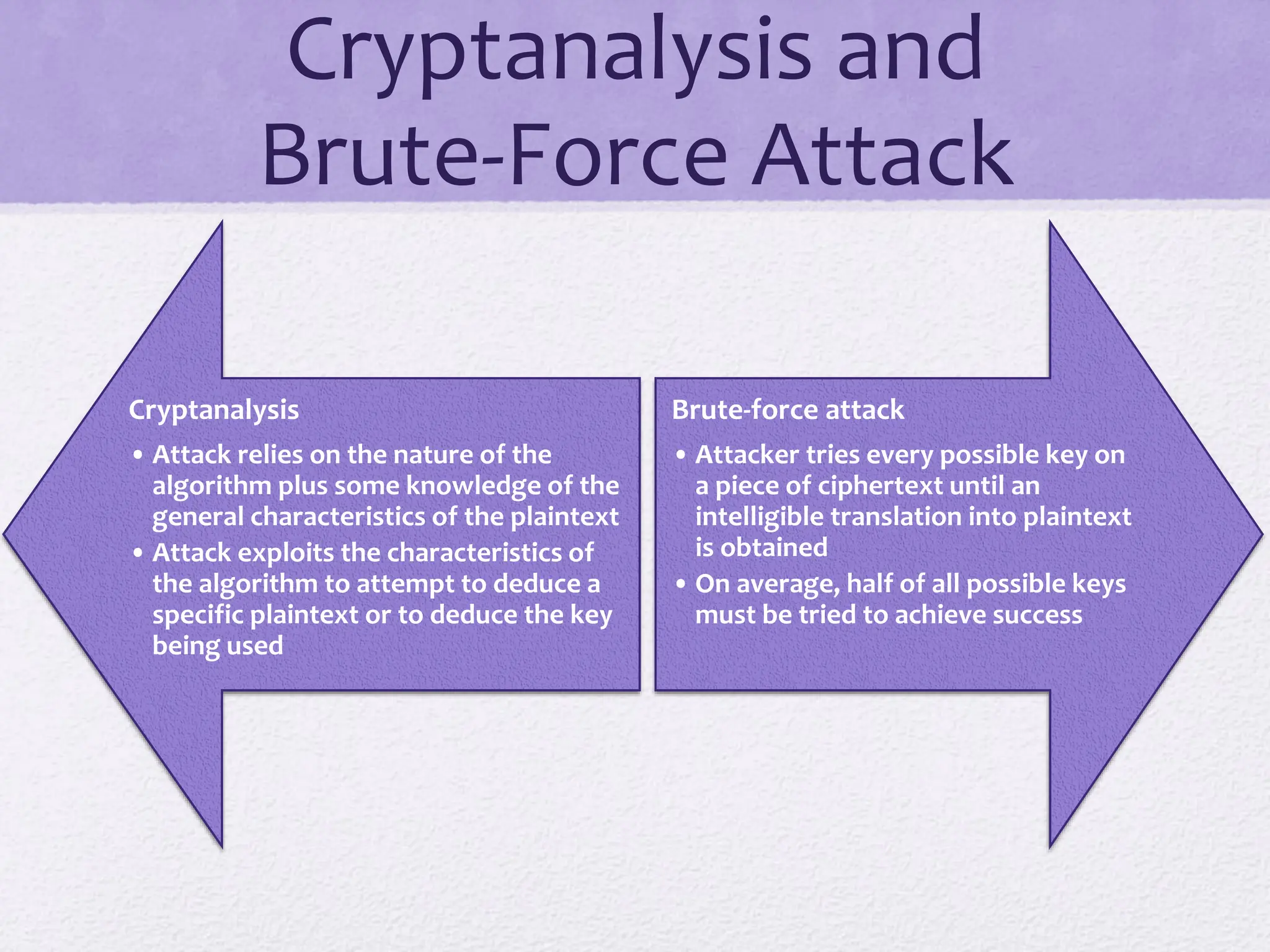
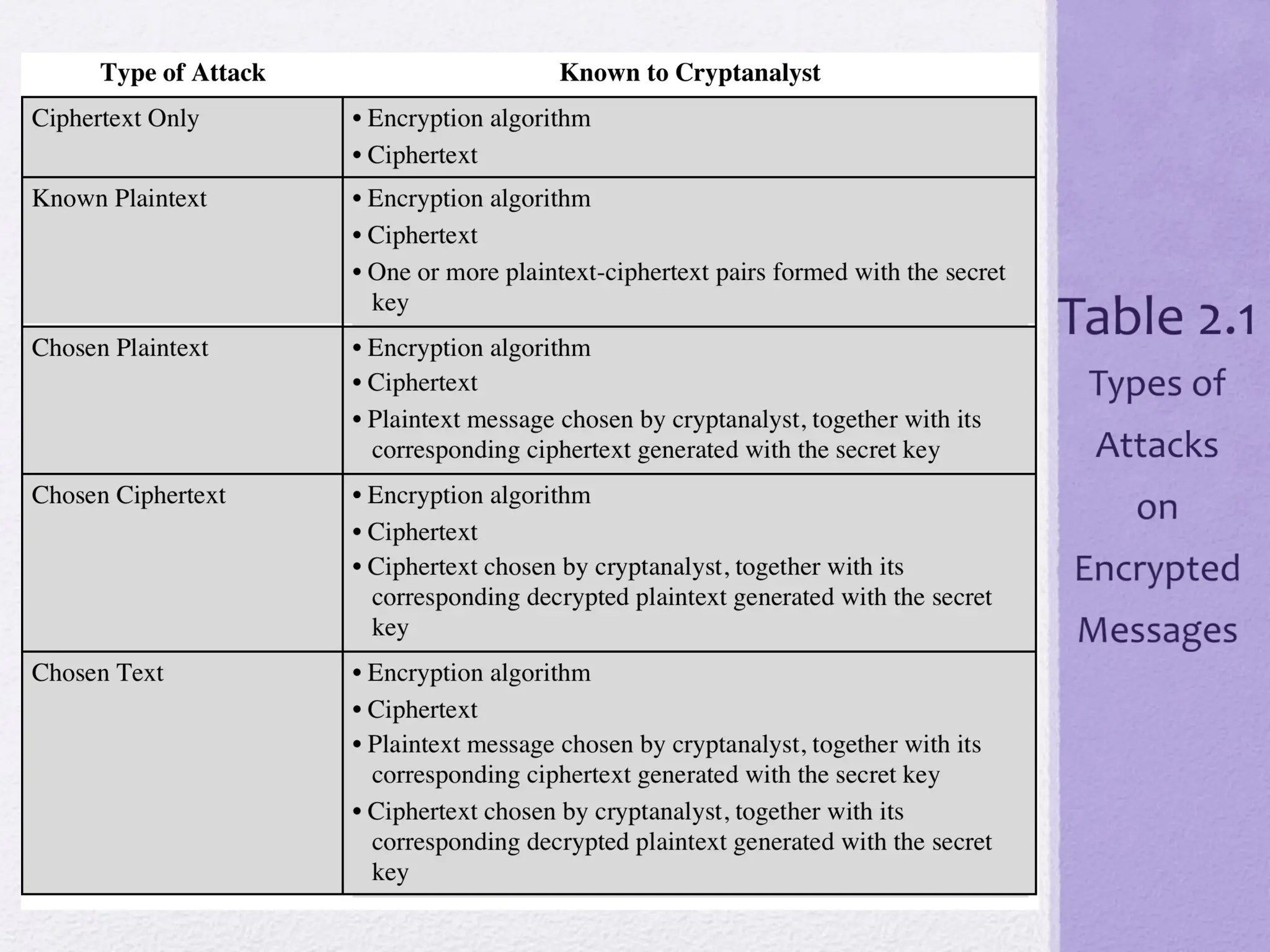
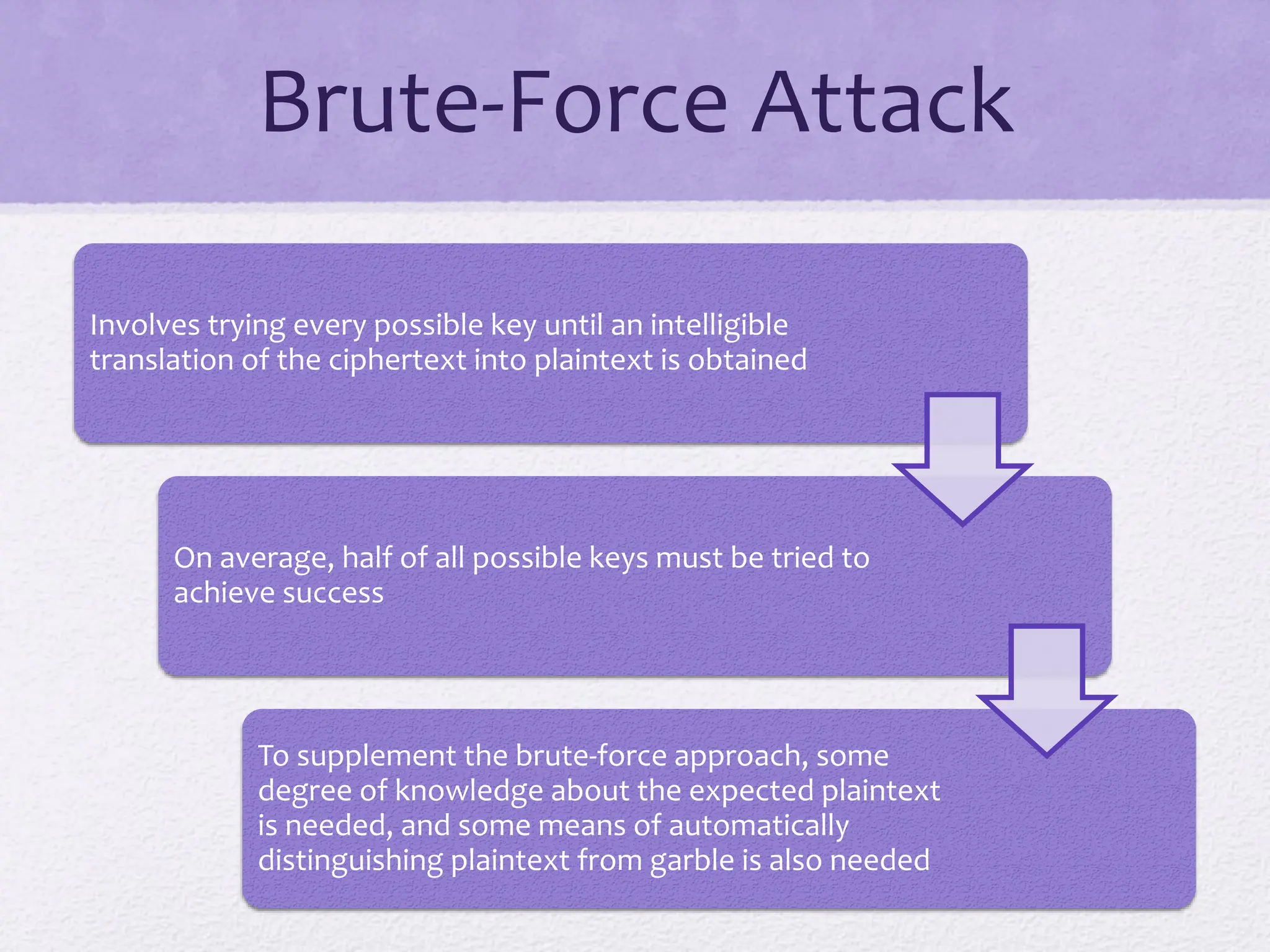
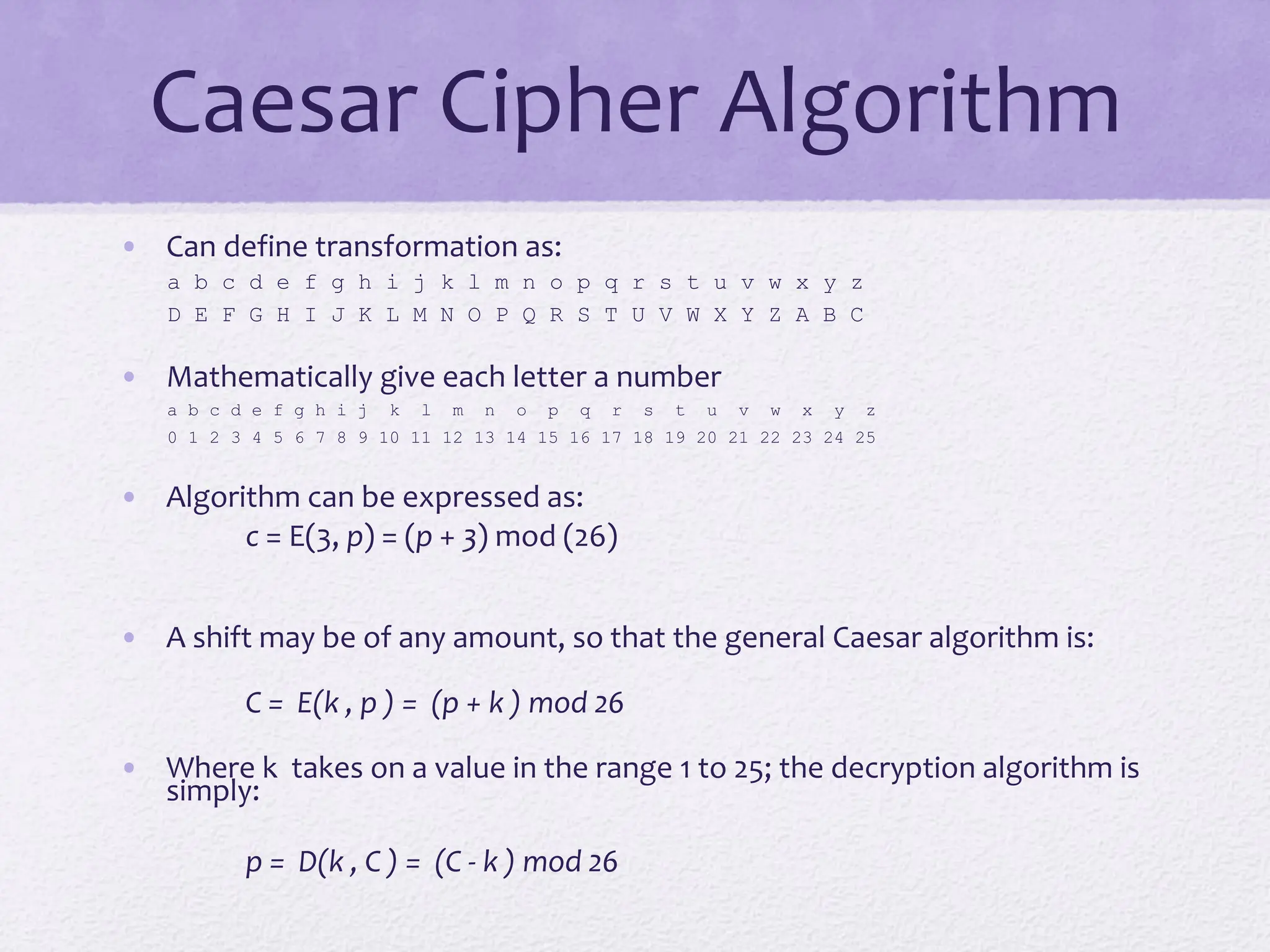
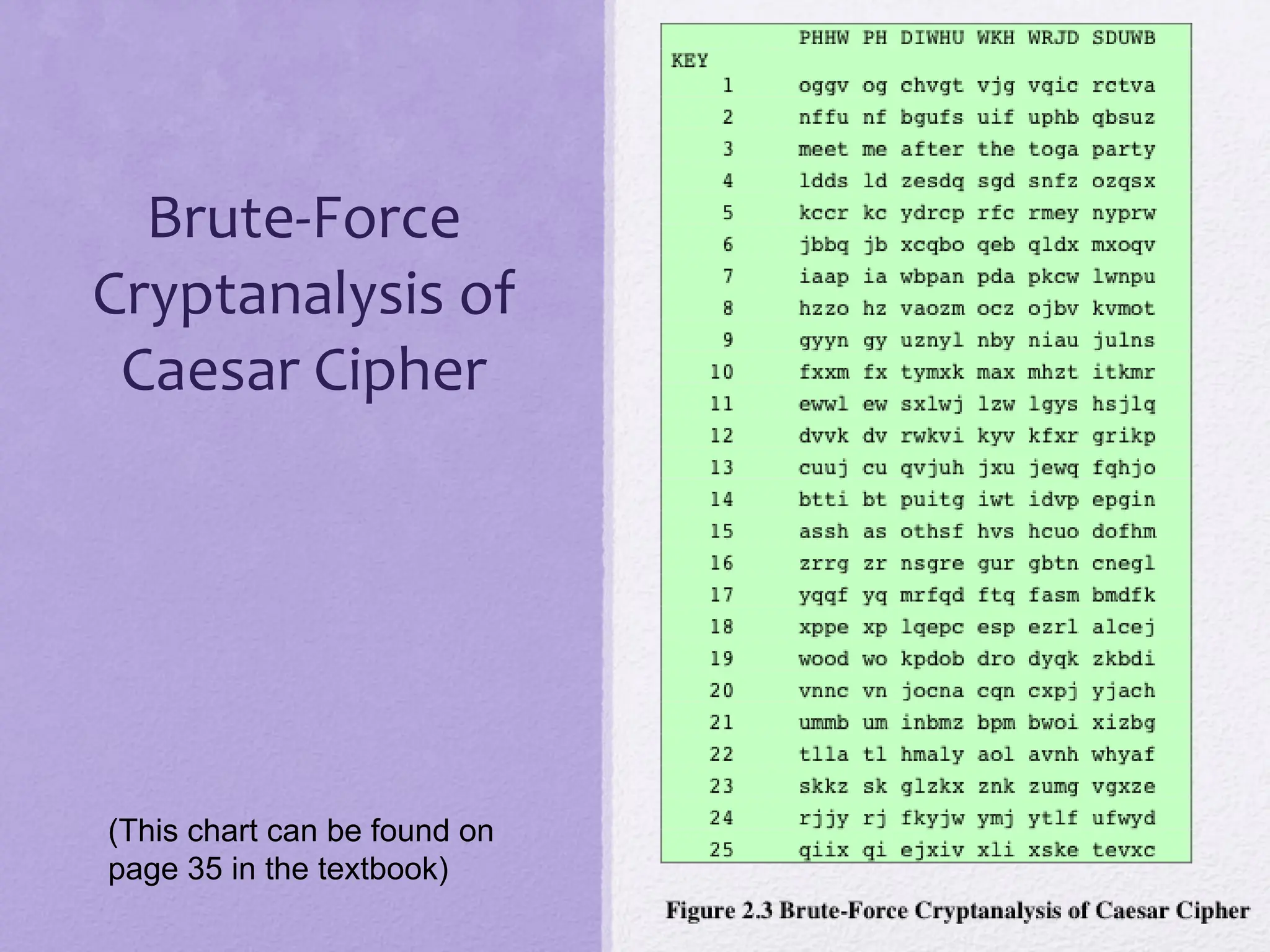
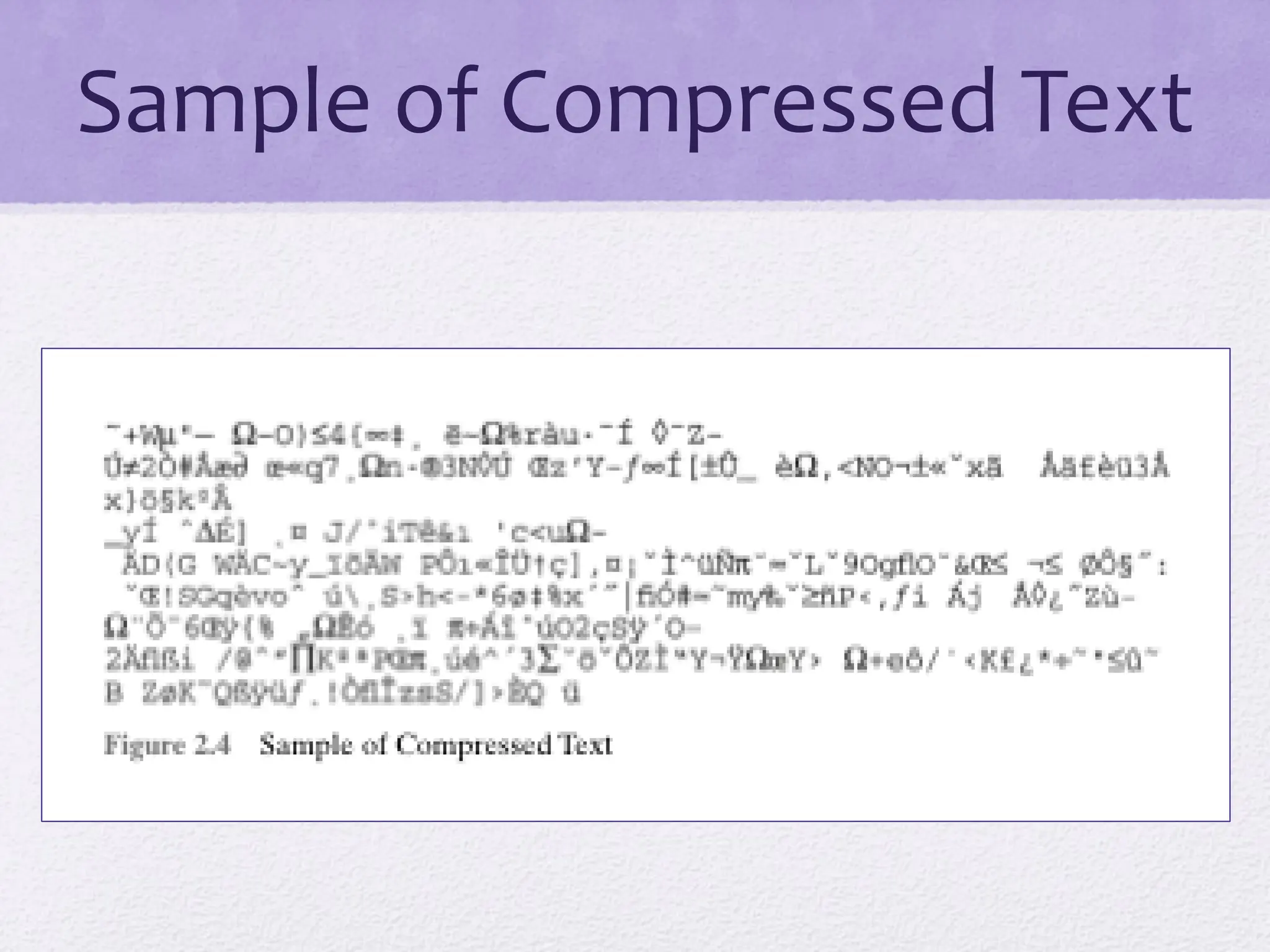
The document discusses classical encryption techniques, focusing on symmetric encryption, which is characterized by single-key usage and remains widely used. It outlines key concepts such as plaintext, ciphertext, enciphering, and various attack methods like cryptanalysis and brute-force attacks. Additionally, it covers specific ciphers including the Caesar cipher, monoalphabetic ciphers, and the Playfair cipher, along with steganography techniques.