AirTight Corporate Presentation _ July2013
•Download as PPTX, PDF•
0 likes•1,221 views
AirTightt Corporate Presentation _ July2013
Report
Share
Report
Share
Recommended
Considerations for a secure enterprise wlan data connectors 2013

Considerations for a Secure Enterprise WLAN - DataConnectors 2013 by Kaustubh Phanse
i7 pregerine7 - Agentless byod security for Enterprises

BYOD Security - 100% agentless (Zero-touch) and Zero-latency; Only tool that works at network layer (as opposed to on the device) discovering fingerprinting health-check for all personal devices and protecting corporate network from infected/malicious/compromised personal devices.
We also the only tool that complements MDM.
i7 Networks - Presentation at Zensar #TechShowcase - An iSPIRT ProductNation ...

i7 Networks - Presentation at Zensar #TechShowcase - An iSPIRT ProductNation ...ProductNation/iSPIRT
i7 Networks - Presentation at Zensar #TechShowcase - An iSPIRT ProductNation initiative. Started in June 2012; they work on the space of BYOD security; Their sweet spot is 100% Agentless device discovery, fingerprinting and health-check and then denying infected/malicious devices from connecting to corporate network.SAE 2014 - Cyber Security: Mission Critical for the Internet of Cars

Connected vehicles are becoming rolling data centers. More attack surfaces expose vehicles to cyber threats that have become common in the IT industry. Connected vehicles will require an end-to-end security architecture spanning from chip level to cloud based security services that protect vehicles over the entire life cycle.
Next-generation Zero Trust Cybersecurity for the Space Age

Space infrastructure has become an integral part of everyday life, with individuals, businesses and governments relying overwhelmingly on it. However, despite the space industry’s technical sophistication, its cybersecurity efforts have lagged behind that of other high-tech sectors.
Block Armour has developed a next-gen Zero Trust Cybersecurity solution explicitly designed for connected devices, integrated IoT systems and related communication networks. And, is extending the solution to deliver Zero Trust Cybersecurity for Software-defined Space based Systems.
Intelligence Driven Security

Virtualization Forum 2015, Praha, 7.10.2015
sál A
Jestliže SlideShare nezobrazí prezentaci korektně, můžete si ji stáhnout ve formátu .ppsx nebo .pdf.
Building the Internet of Everything 

At Cisco Connect Toronto a big focus of ours was building the internet of everything.
Delivering the IoT ecosystem

Presentation by Andres Escribano, Telefónica Director of IoT Connectivity Business, at MWC 2018. For more information, please visit: https://iot.telefonica.com
Recommended
Considerations for a secure enterprise wlan data connectors 2013

Considerations for a Secure Enterprise WLAN - DataConnectors 2013 by Kaustubh Phanse
i7 pregerine7 - Agentless byod security for Enterprises

BYOD Security - 100% agentless (Zero-touch) and Zero-latency; Only tool that works at network layer (as opposed to on the device) discovering fingerprinting health-check for all personal devices and protecting corporate network from infected/malicious/compromised personal devices.
We also the only tool that complements MDM.
i7 Networks - Presentation at Zensar #TechShowcase - An iSPIRT ProductNation ...

i7 Networks - Presentation at Zensar #TechShowcase - An iSPIRT ProductNation ...ProductNation/iSPIRT
i7 Networks - Presentation at Zensar #TechShowcase - An iSPIRT ProductNation initiative. Started in June 2012; they work on the space of BYOD security; Their sweet spot is 100% Agentless device discovery, fingerprinting and health-check and then denying infected/malicious devices from connecting to corporate network.SAE 2014 - Cyber Security: Mission Critical for the Internet of Cars

Connected vehicles are becoming rolling data centers. More attack surfaces expose vehicles to cyber threats that have become common in the IT industry. Connected vehicles will require an end-to-end security architecture spanning from chip level to cloud based security services that protect vehicles over the entire life cycle.
Next-generation Zero Trust Cybersecurity for the Space Age

Space infrastructure has become an integral part of everyday life, with individuals, businesses and governments relying overwhelmingly on it. However, despite the space industry’s technical sophistication, its cybersecurity efforts have lagged behind that of other high-tech sectors.
Block Armour has developed a next-gen Zero Trust Cybersecurity solution explicitly designed for connected devices, integrated IoT systems and related communication networks. And, is extending the solution to deliver Zero Trust Cybersecurity for Software-defined Space based Systems.
Intelligence Driven Security

Virtualization Forum 2015, Praha, 7.10.2015
sál A
Jestliže SlideShare nezobrazí prezentaci korektně, můžete si ji stáhnout ve formátu .ppsx nebo .pdf.
Building the Internet of Everything 

At Cisco Connect Toronto a big focus of ours was building the internet of everything.
Delivering the IoT ecosystem

Presentation by Andres Escribano, Telefónica Director of IoT Connectivity Business, at MWC 2018. For more information, please visit: https://iot.telefonica.com
Internet of everything 

The future of Engineering & Everything in Factories, Access every machine online.
Xirrus - The Best Wi-Fi on the Planet

Xirrus is the leading provider of high-performance wireless networks. Xirrus solutions perform under the most demanding circumstances, offering consistent “wired-like” performance with superior coverage and security.
Звиад Кардава. Интернет вещей - модное слово или реальность? РИФ-Воронеж 2016

Интернет вещей сегодня
Потребительский интернет вещей
Индустриальный интернет вещей
Практические примеры использования интернета вещей
Безопасность в интернете вещей
Интернет вещей и machine learning(машинное обучение)
Интернет вещей, connected cars и умные города.
Последние тренды и новости из мира IoT
BYOD Transforming the Enterprise

The rules of the game in IT are changing rapidly and companies facing these market transitions are looking for ways to build an intelligent network platform that can help lines of business capture new business opportunities. Cisco Borderless Networks is the architecture that allows enterprise of any size, to leverage technology transitions through our portfolio of services - rich, secure, and efficient products and solutions. Customers are able to connect anyone, anywhere, anytime, and on any device – securely, reliably, and seamlessly.
Enterprise-Grade Trust: Collaboration Without Compromise

In today’s agile work environment, customers need to collaborate in real time with partners, vendors, and customers, and they want the best collaboration tools possible. At the same time, they’re cognisant of potential accidental or intentional misuse of data and malicious attacks – and the ramifications they can have for their company’s finances and reputation.
Cisco provides best-in-class collaboration tools with true end-to-end encryption that enable secure cross-company collaboration. Find out more about the six considerations for collaboration security and the new Cisco Webex Extended Security Pack – which provides a full-functionality Cisco Cloudlock cloud access security broker for Webex Teams with native Webex anti-malware capabilities powered by Cisco Talos ClamAV.
Resources:
TechWiseTV: http://cs.co/9009DzrjN
AirTight Networks Evolution - Cloud & MSP

AirTight Networks Welcome from CTO Pravin Bhagwat and Chief Evangelist Devin Akin
Beginners: Fixed Wireless Access (FWA)

A high level introductory look at what is meant by Fixed Wireless Access or FWA that is being touted as one of the initial 5G use cases. This presentation (with embedded video) introduces FWA and looks at a practical deployment example.
6G Training Course Part 3: 6G Use Cases & Applications

After our successful launch of '5G for Absolute Beginners' course (http://bit.ly/5Gbegins) in 2020, we decided to create an introductory training course on 6G Mobile Wireless Communications technology. The course is ready and the best way to navigate it is via the Free 6G Training page at: https://bit.ly/6Gintro - this will ensure that you have the latest version of each video and also the most recent version of the 6G technologies videos as and they are added.
In this part we will look at some of the newer 6G use cases and applications as well as the existing ones that may not be satisfied with 5G. While we discuss some of the use cases in this video / presentation, you have to remember that the final use cases would be dependent on the requirements as well as the evolution of devices and other supporting technologies.
This course is part of #Free6Gtraining initiative (https://www.free6gtraining.com/)
All our #3G4G5G slides and videos are available at:
Videos: https://www.youtube.com/3G4G5G
Slides: https://www.slideshare.net/3G4GLtd
6G and Beyond-5G Page: https://www.3g4g.co.uk/6G/
Free Training Videos: https://www.3g4g.co.uk/Training/
Free 6G Training Blog: https://www.free6gtraining.com/
Conférence ARBOR ACSS 2018

Arbor, Securing the Future
Visibility + Automation & Integration
Moncef ZID
Territory Manager North Africa
Securing Smart Cities with Blockchain-enabled Zero Trust Cybersecuity

Securing IoT-enabled smart cities with blockchain-powered Zero Trust cybersecurity
Deliver The Latest Wave 2 Wi-Fi as a Service | The Future of Sophisticated Wi...

Xirrus is the leading provider of high-performance wireless networks. Xirrus solutions perform under the most demanding circumstances, offering consistent “wired-like” performance with superior coverage and security.
Cisco connect winnipeg 2018 introducing the network intuitive

Cisco connect winnipeg 2018 introducing the network intuitive
Mavenir: Evolution of Real-Time Machine Learning (RRML) in Core Network Secur...

5G security requirements, architecture, business channels, and workstreams. Presentation from 5G World 2019.
Open source IoT

Presentation by Ian Skerrett, VP Marketing at Eclipse Foundation given at IoT613 on Friday, September 30, 2016.
Opinion: Would 5G NSA undergo Sunset?

Description: In this presentation / video we look at the argument why 5G NSA Option 3 (EN-DC) may not be around for a very long time and may be turned off by the operators when 5G Core is up and running and all the initial issues have been sorted out.
Video link: https://youtu.be/ERnq8WLlse0
All our #3G4G5G slides and videos are available at:
Videos: https://www.youtube.com/3G4G5G
Slides: https://www.slideshare.net/3G4GLtd
5G Page: https://www.3g4g.co.uk/5G/
Free Training Videos: https://www.3g4g.co.uk/Training/
Prakash Padariya - IoT Cyber Warfare

IoT Cyber Warfare, Industrial Internet, IIoT, Cyber Security, Drone
Air Tight Airport Wi Fi Scan Analysis

AirTight Study at Worldwide Airports Reveals Wireless Security Risks for Travelers and Airport Operations
Safety reliability and security lessons from defense for IoT

Presentation by David Jedynak, CTO of Curtiss-Wright Defense Solutions. This was presented at IoT613 on Friday, September 30, 2016.
Decoding the IoT Ecosystem

Introducing a holistic view of how IoT applications are built.
Presentation delivered during the IPv6 Coordination Meeting organised by RIPE NCC in Beirut-Lebanon on November 5th 2015. It was updated for the RIPE NCC Levant Regional Meeting done on April 25th 2016 in Beirut.
Drive Revenue, Protect Data, & Automate PCI Compliance by Dwight Agriel | @Ai...

Drive Revenue, Protect Data, & Automate PCI Compliance with @AirTight Secure Wi-Fi and Analytics
More Related Content
What's hot
Internet of everything 

The future of Engineering & Everything in Factories, Access every machine online.
Xirrus - The Best Wi-Fi on the Planet

Xirrus is the leading provider of high-performance wireless networks. Xirrus solutions perform under the most demanding circumstances, offering consistent “wired-like” performance with superior coverage and security.
Звиад Кардава. Интернет вещей - модное слово или реальность? РИФ-Воронеж 2016

Интернет вещей сегодня
Потребительский интернет вещей
Индустриальный интернет вещей
Практические примеры использования интернета вещей
Безопасность в интернете вещей
Интернет вещей и machine learning(машинное обучение)
Интернет вещей, connected cars и умные города.
Последние тренды и новости из мира IoT
BYOD Transforming the Enterprise

The rules of the game in IT are changing rapidly and companies facing these market transitions are looking for ways to build an intelligent network platform that can help lines of business capture new business opportunities. Cisco Borderless Networks is the architecture that allows enterprise of any size, to leverage technology transitions through our portfolio of services - rich, secure, and efficient products and solutions. Customers are able to connect anyone, anywhere, anytime, and on any device – securely, reliably, and seamlessly.
Enterprise-Grade Trust: Collaboration Without Compromise

In today’s agile work environment, customers need to collaborate in real time with partners, vendors, and customers, and they want the best collaboration tools possible. At the same time, they’re cognisant of potential accidental or intentional misuse of data and malicious attacks – and the ramifications they can have for their company’s finances and reputation.
Cisco provides best-in-class collaboration tools with true end-to-end encryption that enable secure cross-company collaboration. Find out more about the six considerations for collaboration security and the new Cisco Webex Extended Security Pack – which provides a full-functionality Cisco Cloudlock cloud access security broker for Webex Teams with native Webex anti-malware capabilities powered by Cisco Talos ClamAV.
Resources:
TechWiseTV: http://cs.co/9009DzrjN
AirTight Networks Evolution - Cloud & MSP

AirTight Networks Welcome from CTO Pravin Bhagwat and Chief Evangelist Devin Akin
Beginners: Fixed Wireless Access (FWA)

A high level introductory look at what is meant by Fixed Wireless Access or FWA that is being touted as one of the initial 5G use cases. This presentation (with embedded video) introduces FWA and looks at a practical deployment example.
6G Training Course Part 3: 6G Use Cases & Applications

After our successful launch of '5G for Absolute Beginners' course (http://bit.ly/5Gbegins) in 2020, we decided to create an introductory training course on 6G Mobile Wireless Communications technology. The course is ready and the best way to navigate it is via the Free 6G Training page at: https://bit.ly/6Gintro - this will ensure that you have the latest version of each video and also the most recent version of the 6G technologies videos as and they are added.
In this part we will look at some of the newer 6G use cases and applications as well as the existing ones that may not be satisfied with 5G. While we discuss some of the use cases in this video / presentation, you have to remember that the final use cases would be dependent on the requirements as well as the evolution of devices and other supporting technologies.
This course is part of #Free6Gtraining initiative (https://www.free6gtraining.com/)
All our #3G4G5G slides and videos are available at:
Videos: https://www.youtube.com/3G4G5G
Slides: https://www.slideshare.net/3G4GLtd
6G and Beyond-5G Page: https://www.3g4g.co.uk/6G/
Free Training Videos: https://www.3g4g.co.uk/Training/
Free 6G Training Blog: https://www.free6gtraining.com/
Conférence ARBOR ACSS 2018

Arbor, Securing the Future
Visibility + Automation & Integration
Moncef ZID
Territory Manager North Africa
Securing Smart Cities with Blockchain-enabled Zero Trust Cybersecuity

Securing IoT-enabled smart cities with blockchain-powered Zero Trust cybersecurity
Deliver The Latest Wave 2 Wi-Fi as a Service | The Future of Sophisticated Wi...

Xirrus is the leading provider of high-performance wireless networks. Xirrus solutions perform under the most demanding circumstances, offering consistent “wired-like” performance with superior coverage and security.
Cisco connect winnipeg 2018 introducing the network intuitive

Cisco connect winnipeg 2018 introducing the network intuitive
Mavenir: Evolution of Real-Time Machine Learning (RRML) in Core Network Secur...

5G security requirements, architecture, business channels, and workstreams. Presentation from 5G World 2019.
Open source IoT

Presentation by Ian Skerrett, VP Marketing at Eclipse Foundation given at IoT613 on Friday, September 30, 2016.
Opinion: Would 5G NSA undergo Sunset?

Description: In this presentation / video we look at the argument why 5G NSA Option 3 (EN-DC) may not be around for a very long time and may be turned off by the operators when 5G Core is up and running and all the initial issues have been sorted out.
Video link: https://youtu.be/ERnq8WLlse0
All our #3G4G5G slides and videos are available at:
Videos: https://www.youtube.com/3G4G5G
Slides: https://www.slideshare.net/3G4GLtd
5G Page: https://www.3g4g.co.uk/5G/
Free Training Videos: https://www.3g4g.co.uk/Training/
Prakash Padariya - IoT Cyber Warfare

IoT Cyber Warfare, Industrial Internet, IIoT, Cyber Security, Drone
Air Tight Airport Wi Fi Scan Analysis

AirTight Study at Worldwide Airports Reveals Wireless Security Risks for Travelers and Airport Operations
Safety reliability and security lessons from defense for IoT

Presentation by David Jedynak, CTO of Curtiss-Wright Defense Solutions. This was presented at IoT613 on Friday, September 30, 2016.
Decoding the IoT Ecosystem

Introducing a holistic view of how IoT applications are built.
Presentation delivered during the IPv6 Coordination Meeting organised by RIPE NCC in Beirut-Lebanon on November 5th 2015. It was updated for the RIPE NCC Levant Regional Meeting done on April 25th 2016 in Beirut.
What's hot (20)
Звиад Кардава. Интернет вещей - модное слово или реальность? РИФ-Воронеж 2016

Звиад Кардава. Интернет вещей - модное слово или реальность? РИФ-Воронеж 2016
Enterprise-Grade Trust: Collaboration Without Compromise

Enterprise-Grade Trust: Collaboration Without Compromise
6G Training Course Part 3: 6G Use Cases & Applications

6G Training Course Part 3: 6G Use Cases & Applications
Securing Smart Cities with Blockchain-enabled Zero Trust Cybersecuity

Securing Smart Cities with Blockchain-enabled Zero Trust Cybersecuity
Deliver The Latest Wave 2 Wi-Fi as a Service | The Future of Sophisticated Wi...

Deliver The Latest Wave 2 Wi-Fi as a Service | The Future of Sophisticated Wi...
Cisco connect winnipeg 2018 introducing the network intuitive

Cisco connect winnipeg 2018 introducing the network intuitive
Mavenir: Evolution of Real-Time Machine Learning (RRML) in Core Network Secur...

Mavenir: Evolution of Real-Time Machine Learning (RRML) in Core Network Secur...
Safety reliability and security lessons from defense for IoT

Safety reliability and security lessons from defense for IoT
Similar to AirTight Corporate Presentation _ July2013
Drive Revenue, Protect Data, & Automate PCI Compliance by Dwight Agriel | @Ai...

Drive Revenue, Protect Data, & Automate PCI Compliance with @AirTight Secure Wi-Fi and Analytics
1. How will the IoT help your business - cisco

Internet of Everything and Internet of Things
The quest for the next “killer” application
What it would take to make IoT work?
How does it all come together?
Q&A
Securing the edge with AWS IoT services - FND330 - AWS re:Inforce 2019 

Edge computing is one of the most important enablers of the future. It saves lives, democratizes resources, and reduces costs in scenarios where near real-time action is required. This session covers how to keep edge computing secure. We dive deep into how AWS IoT Greengrass authenticates and encrypts device data for local and cloud communications so that data is never exchanged without proven identity. You can leverage hardware-secured, end-to-end encryption for messages exchanged between devices, an AWS IoT Greengrass core, and the AWS Cloud, and for messages between an AWS IoT Greengrass core and other local devices using the AWS IoT device SDK.
Lorna Slott ATT new frontier

Presentation by Lorna Slott, AT&T during the session "Small Cells, DAS Wi-Fi - the New Frontier
Did Your Wi-Fi Performance Expire Before the Warranty Did? | Steps to Providi...

You’re just two years in with a new Wi-Fi network and it’s already straining under the load, what happened? Bottom-line is everyone knew Wi-Fi usage was rapidly increasing, however the actual growth was unprecedented.
In just a few years the inundation of new devices, higher densities, Social Media and BYOD initiatives overwhelmed traditional Wi-Fi infrastructures, as a result wireless performance, and more importantly its reliability degraded substantially. Yeah, we all saw it happening and in truth it’s no one’s fault, however it’s not a scenario anyone wants to repeat.
So before you go requesting additional budget for the next upgrade, arm yourself with the knowledge to make sure the next wireless solution supports not only what you expect, but also has the scalability/upgradability to address the unexpected too.
Internet of Cars, Andreas Mai, Cisco Systems

Connecting vehicles will create the Internet of Cars, transform the automotive industry, enable big data infomediaries, and spawn new businesses.
Management Briefing Seminars, Traverse City August 5, 2013
Snowflake Data Science and AI/ML at Scale

Slides from the June 2020 St. Louis Big Data IDEA meetup featuring using Snowflake for Data Science and AI/ML at Scale.
Introducing MSite Mobile for Lenel (Feb14)

Adam Page, Reseller Account Manager at HRS, recently presented to the Lenel EMEA Sales Team (DL CCS EMEA Lenel Sales) and Lenel EMEA PM/PMM to introduce MSite Mobile - our mobile extension to Lenel's Onguard access control section.
Leadership Session: AWS IoT (IOT218-L) - AWS re:Invent 2018

In this session delivered by the VP of AWS IoT, we cover how AWS IoT is being deployed across consumer, commercial, and industrial applications. See how customers are securely connecting and managing devices and creating analytics and machine learning (ML) based on IoT data. AWS IoT applications run in the cloud to enable massive scalablity or at the edge to enable real-time local action. Come away with an understanding how IoT is transforming business and what's new from AWS IoT.
The Inside Story: Leveraging the IIC's Industrial Internet Security Framework

The Inside Story: Leveraging the IIC's Industrial Internet Security FrameworkReal-Time Innovations (RTI)
Originally presented on January 17, 2017
Watch replay: https://vts.inxpo.com/Launch/QReg.htm?ShowKey=35540&AffiliateData=rti
Top 5 predictions webinar

As security professionals, how can we be sure that we’re ready for 2019? After the last few years, when our practices and conventions have been tested again and again, it’s a little daunting to consider what may face us in the year ahead. Will attackers set their sights on cloud apps? Will hackers join forces with organized crime? Will governments look to the private sector to deal with the skills gap? What will happen to cybersecurity budgets? Join us to get answers to these questions and more.
The Four Horsemen of Mobile Security

Watch the webinar recording: http://hubs.ly/y0XwTS0
In this RSA Conference webcast, security experts Adi Sharabani and Yair Amit describe the current threat landscape for mobile devices and discuss security strategies.
Similar to AirTight Corporate Presentation _ July2013 (20)
Drive Revenue, Protect Data, & Automate PCI Compliance by Dwight Agriel | @Ai...

Drive Revenue, Protect Data, & Automate PCI Compliance by Dwight Agriel | @Ai...
Securing the edge with AWS IoT services - FND330 - AWS re:Inforce 2019 

Securing the edge with AWS IoT services - FND330 - AWS re:Inforce 2019
Did Your Wi-Fi Performance Expire Before the Warranty Did? | Steps to Providi...

Did Your Wi-Fi Performance Expire Before the Warranty Did? | Steps to Providi...
Leadership Session: AWS IoT (IOT218-L) - AWS re:Invent 2018

Leadership Session: AWS IoT (IOT218-L) - AWS re:Invent 2018
The Inside Story: Leveraging the IIC's Industrial Internet Security Framework

The Inside Story: Leveraging the IIC's Industrial Internet Security Framework
Recently uploaded
The Art of the Pitch: WordPress Relationships and Sales

Clients don’t know what they don’t know. What web solutions are right for them? How does WordPress come into the picture? How do you make sure you understand scope and timeline? What do you do if sometime changes?
All these questions and more will be explored as we talk about matching clients’ needs with what your agency offers without pulling teeth or pulling your hair out. Practical tips, and strategies for successful relationship building that leads to closing the deal.
20240605 QFM017 Machine Intelligence Reading List May 2024

Everything I found interesting about machines behaving intelligently during May 2024
By Design, not by Accident - Agile Venture Bolzano 2024

As presented at the Agile Venture Bolzano, 4.06.2024
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Monitoring and observability aren’t traditionally found in software curriculums and many of us cobble this knowledge together from whatever vendor or ecosystem we were first introduced to and whatever is a part of your current company’s observability stack.
While the dev and ops silo continues to crumble….many organizations still relegate monitoring & observability as the purview of ops, infra and SRE teams. This is a mistake - achieving a highly observable system requires collaboration up and down the stack.
I, a former op, would like to extend an invitation to all application developers to join the observability party will share these foundational concepts to build on:
Removing Uninteresting Bytes in Software Fuzzing

Imagine a world where software fuzzing, the process of mutating bytes in test seeds to uncover hidden and erroneous program behaviors, becomes faster and more effective. A lot depends on the initial seeds, which can significantly dictate the trajectory of a fuzzing campaign, particularly in terms of how long it takes to uncover interesting behaviour in your code. We introduce DIAR, a technique designed to speedup fuzzing campaigns by pinpointing and eliminating those uninteresting bytes in the seeds. Picture this: instead of wasting valuable resources on meaningless mutations in large, bloated seeds, DIAR removes the unnecessary bytes, streamlining the entire process.
In this work, we equipped AFL, a popular fuzzer, with DIAR and examined two critical Linux libraries -- Libxml's xmllint, a tool for parsing xml documents, and Binutil's readelf, an essential debugging and security analysis command-line tool used to display detailed information about ELF (Executable and Linkable Format). Our preliminary results show that AFL+DIAR does not only discover new paths more quickly but also achieves higher coverage overall. This work thus showcases how starting with lean and optimized seeds can lead to faster, more comprehensive fuzzing campaigns -- and DIAR helps you find such seeds.
- These are slides of the talk given at IEEE International Conference on Software Testing Verification and Validation Workshop, ICSTW 2022.
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

Neha Bajwa, Vice President of Product Marketing, Neo4j
Join us as we explore breakthrough innovations enabled by interconnected data and AI. Discover firsthand how organizations use relationships in data to uncover contextual insights and solve our most pressing challenges – from optimizing supply chains, detecting fraud, and improving customer experiences to accelerating drug discoveries.
Communications Mining Series - Zero to Hero - Session 1

This session provides introduction to UiPath Communication Mining, importance and platform overview. You will acquire a good understand of the phases in Communication Mining as we go over the platform with you. Topics covered:
• Communication Mining Overview
• Why is it important?
• How can it help today’s business and the benefits
• Phases in Communication Mining
• Demo on Platform overview
• Q/A
Securing your Kubernetes cluster_ a step-by-step guide to success !

Today, after several years of existence, an extremely active community and an ultra-dynamic ecosystem, Kubernetes has established itself as the de facto standard in container orchestration. Thanks to a wide range of managed services, it has never been so easy to set up a ready-to-use Kubernetes cluster.
However, this ease of use means that the subject of security in Kubernetes is often left for later, or even neglected. This exposes companies to significant risks.
In this talk, I'll show you step-by-step how to secure your Kubernetes cluster for greater peace of mind and reliability.
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

Do you want to learn how to model and simulate an electrical network from scratch in under an hour?
Then welcome to this PowSyBl workshop, hosted by Rte, the French Transmission System Operator (TSO)!
During the webinar, you will discover the PowSyBl ecosystem as well as handle and study an electrical network through an interactive Python notebook.
PowSyBl is an open source project hosted by LF Energy, which offers a comprehensive set of features for electrical grid modelling and simulation. Among other advanced features, PowSyBl provides:
- A fully editable and extendable library for grid component modelling;
- Visualization tools to display your network;
- Grid simulation tools, such as power flows, security analyses (with or without remedial actions) and sensitivity analyses;
The framework is mostly written in Java, with a Python binding so that Python developers can access PowSyBl functionalities as well.
What you will learn during the webinar:
- For beginners: discover PowSyBl's functionalities through a quick general presentation and the notebook, without needing any expert coding skills;
- For advanced developers: master the skills to efficiently apply PowSyBl functionalities to your real-world scenarios.
Epistemic Interaction - tuning interfaces to provide information for AI support

Paper presented at SYNERGY workshop at AVI 2024, Genoa, Italy. 3rd June 2024
https://alandix.com/academic/papers/synergy2024-epistemic/
As machine learning integrates deeper into human-computer interactions, the concept of epistemic interaction emerges, aiming to refine these interactions to enhance system adaptability. This approach encourages minor, intentional adjustments in user behaviour to enrich the data available for system learning. This paper introduces epistemic interaction within the context of human-system communication, illustrating how deliberate interaction design can improve system understanding and adaptation. Through concrete examples, we demonstrate the potential of epistemic interaction to significantly advance human-computer interaction by leveraging intuitive human communication strategies to inform system design and functionality, offering a novel pathway for enriching user-system engagements.
Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...

The choice of an operating system plays a pivotal role in shaping our computing experience. For decades, Microsoft's Windows has dominated the market, offering a familiar and widely adopted platform for personal and professional use. However, as technological advancements continue to push the boundaries of innovation, alternative operating systems have emerged, challenging the status quo and offering users a fresh perspective on computing.
One such alternative that has garnered significant attention and acclaim is Nitrux Linux 3.5.0, a sleek, powerful, and user-friendly Linux distribution that promises to redefine the way we interact with our devices. With its focus on performance, security, and customization, Nitrux Linux presents a compelling case for those seeking to break free from the constraints of proprietary software and embrace the freedom and flexibility of open-source computing.
National Security Agency - NSA mobile device best practices

Threats to mobile devices are more prevalent and increasing in scope and complexity. Users of mobile devices desire to take full advantage of the features
available on those devices, but many of the features provide convenience and capability but sacrifice security. This best practices guide outlines steps the users can take to better protect personal devices and information.
Video Streaming: Then, Now, and in the Future

In his public lecture, Christian Timmerer provides insights into the fascinating history of video streaming, starting from its humble beginnings before YouTube to the groundbreaking technologies that now dominate platforms like Netflix and ORF ON. Timmerer also presents provocative contributions of his own that have significantly influenced the industry. He concludes by looking at future challenges and invites the audience to join in a discussion.
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

Sudheer Mechineni, Head of Application Frameworks, Standard Chartered Bank
Discover how Standard Chartered Bank harnessed the power of Neo4j to transform complex data access challenges into a dynamic, scalable graph database solution. This keynote will cover their journey from initial adoption to deploying a fully automated, enterprise-grade causal cluster, highlighting key strategies for modelling organisational changes and ensuring robust disaster recovery. Learn how these innovations have not only enhanced Standard Chartered Bank’s data infrastructure but also positioned them as pioneers in the banking sector’s adoption of graph technology.
UiPath Test Automation using UiPath Test Suite series, part 4

Welcome to UiPath Test Automation using UiPath Test Suite series part 4. In this session, we will cover Test Manager overview along with SAP heatmap.
The UiPath Test Manager overview with SAP heatmap webinar offers a concise yet comprehensive exploration of the role of a Test Manager within SAP environments, coupled with the utilization of heatmaps for effective testing strategies.
Participants will gain insights into the responsibilities, challenges, and best practices associated with test management in SAP projects. Additionally, the webinar delves into the significance of heatmaps as a visual aid for identifying testing priorities, areas of risk, and resource allocation within SAP landscapes. Through this session, attendees can expect to enhance their understanding of test management principles while learning practical approaches to optimize testing processes in SAP environments using heatmap visualization techniques
What will you get from this session?
1. Insights into SAP testing best practices
2. Heatmap utilization for testing
3. Optimization of testing processes
4. Demo
Topics covered:
Execution from the test manager
Orchestrator execution result
Defect reporting
SAP heatmap example with demo
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
Recently uploaded (20)
The Art of the Pitch: WordPress Relationships and Sales

The Art of the Pitch: WordPress Relationships and Sales
20240605 QFM017 Machine Intelligence Reading List May 2024

20240605 QFM017 Machine Intelligence Reading List May 2024
By Design, not by Accident - Agile Venture Bolzano 2024

By Design, not by Accident - Agile Venture Bolzano 2024
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf
Free Complete Python - A step towards Data Science

Free Complete Python - A step towards Data Science
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024
Communications Mining Series - Zero to Hero - Session 1

Communications Mining Series - Zero to Hero - Session 1
Securing your Kubernetes cluster_ a step-by-step guide to success !

Securing your Kubernetes cluster_ a step-by-step guide to success !
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...
Epistemic Interaction - tuning interfaces to provide information for AI support

Epistemic Interaction - tuning interfaces to provide information for AI support
Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...

Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...
National Security Agency - NSA mobile device best practices

National Security Agency - NSA mobile device best practices
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...
UiPath Test Automation using UiPath Test Suite series, part 4

UiPath Test Automation using UiPath Test Suite series, part 4
AirTight Corporate Presentation _ July2013
- 1. © 2013 AirTight Networks, Inc. All rights reserved. AirTight Networks The Global Leader in Secure Cloud Wi-Fi
- 2. © 2013 AirTight Networks, Inc. All rights reserved. 2 2002-20032000-2001 2004-2005 Encryption Authentication Wireless intrusion detection AirTight Networks Wireless IDS circa 2004
- 3. © 2013 AirTight Networks, Inc. All rights reserved. 3 AirTight Growth Story 2005 World’s first WIPS - fully automated 2008 World’s first cloud based WIPS & 802.11n WIPS 2007 Widely recognized as WIPS leader Social Wi-Fi and Analytics Super-Tenant Cloud Wi-Fi access and concurrent 24/7 WIPS in one platform 2012 2006 2011 Largest cloud- managed Wi-Fi deployment 2010 2009 Most affordable and efficient wireless PCI solution Wireless Intrusion Prevention 29 patents granted 9 patents pending 2013
- 4. © 2013 AirTight Networks, Inc. All rights reserved. Trusted by Thousands of Customers Worldwide 4 Government TransportationTelco Manufacturing Technology HealthcareRetailServicesFinancial Hospitality
- 5. © 2013 AirTight Networks, Inc. All rights reserved. Yum! Brands: Hungry for Wi-Fi AirTight Wi-Fi being rolled out across 17,000+ locations across North America
- 6. © 2013 AirTight Networks, Inc. All rights reserved. Growing AirTight Wi-Fi Customer Base 6
- 7. © 2013 AirTight Networks, Inc. All rights reserved. AirTight Sales/Distribution Expansion 7 Americas EMEA APAC Access IT Accuvant ACR Cadre Fishnet FutureCom Insight IPC M&K Presidio Transparent Technoogy Telus Vandis Verizon Business Virtual Graffiti … A fast growing base of 1000+ channel partners and MSPs Aditinet B-Able Comguard Computerlinks Data Equipment e92Plus Head Technology iSecure IT Way Kappa Data New Edge Secure Data Selcoms Synetix VADition … ASL Bright Nexus Dataworld Dimension Data Docutek Energy One Fortress HPKom Hyundai HDS LG U-Plus Marubeni Muhan mForce NetOne Netpolean Observatory Crest Quantum Samsung S1 SKC&C SoftBank Synergy Teamsun Toshiba TTSS uFinite Uninet Viet Distribution Wavelink … Global MSPs: AT&T, Dell, Earthlink, Hughes, IBM, ISS, …
- 8. © 2013 AirTight Networks, Inc. All rights reserved. AirTight Cloud – Salient Features 8 Built-in High Availability & Fault-Tolerance SAS70 Type II Certified Data Centers Drop-Ship, Plug-n-Play Deployment Location-based Administration Massively Scalable, Multi-Tenant Elastic Cloud Architecture Single Console Centralized Management
- 9. © 2013 AirTight Networks, Inc. All rights reserved. Industry’s Largest Global Cloud Footprint 9 Massively scalable, multi-tenant, fault-tolerant cloud architecture serving over 25,000 customer sites
- 10. © 2013 AirTight Networks, Inc. All rights reserved. Undisputed Global Leader in Wireless Security 10 Rated at the top in all six Gartner MarketScope reports on WLAN IPS US DoD Approved
- 11. © 2013 AirTight Networks, Inc. All rights reserved. Wireless Intrusion Prevention System (WIPS) 11 Automatic Device Classification Comprehensive Threat Coverage Reliable Threat Prevention Accurate Location Tracking BYOD Policy Enforcement Automated Compliance Reporting
- 12. © 2013 AirTight Networks, Inc. All rights reserved. AirTight Wi-Fi – Salient Features 12 High Speed 802.11n Access with Built-in WIPS Guest Wi-Fi with Analytics and Social Media Integration Intelligent Edge, Controller- less, Fault Tolerant Architecture Multiple SSIDs and VLANs per AP Content Filtering, Firewall, QoS, BYOD Controls per SSID Software-Defined Band Unlocked Radios 2.4 GHZ 5 GHZ Wi-Fi Wi-Fi with background WIPS Dedicated WIPS
- 13. © 2013 AirTight Networks, Inc. All rights reserved. The AirTight Advantage 13
- 14. © 2013 AirTight Networks, Inc. All rights reserved. AirTight Social Wi-Fi and Analytics 14
- 15. © 2013 AirTight Networks, Inc. All rights reserved. Empowering Guest Wi-Fi with Social Media 15 Engage your customers and turn them into loyal promoters
- 16. © 2013 AirTight Networks, Inc. All rights reserved. AirTight Social Wi-Fi™ Workflow 16 1. Custom branded captive portal 2. Customers turn loyal promoters 3. Engage your customers
- 17. © 2013 AirTight Networks, Inc. All rights reserved. AirTight Analytics for Business Intelligence 17 Presence Analytics • Total Foot Traffic • Catchment Area Visitor Traffic • Dwell Time (or Visit Duration) Loyalty Analytics • Repeat Visitors • Visit Frequency • Visit Recency Engagement Analytics • Conversion and Bounce Rates • Social Wi-Fi Demographics • Social Wi-Fi Visitor Logs Wi-Fi Usage Analytics • Device Types • Data Traffic • Session Duration Intra-day or times of the day Daily, weekly, monthly trends Specific store or across selected stores Raw data (to generate custom reports) How We Can Report What We Can Measure
- 18. © 2013 AirTight Networks, Inc. All rights reserved. Social Analytics for Opt-in Customers 18
- 19. © 2013 AirTight Networks, Inc. All rights reserved. Identity Analytics for Opt-in Customers 19
- 20. © 2013 AirTight Networks, Inc. All rights reserved. Sample Presence Analytics 20 No.ofvisitorsNo.ofvisitors Dwell Time Total Foot Traffic
- 21. © 2013 AirTight Networks, Inc. All rights reserved. Sample Presence Analytics 21 !" #!" $!!" $#!" %!!" %#!" &"'()*+(,-./" &01*2)!$#33#" &45*2)!%367$" &48*2)!!9:%7" &4;*2)!%3<73" &=4*2)!%:<%%" &>?*2)!!%96:" &@A*2)!%!<$!" &?@*2)!%3#!3" &?;*2)!!$:$3" &5B*2)!%36#6" &5C*2)!!%769" !"#$%&'()'*%+,-%.' /( -01( 234 ,.%'5 ,36,'7.%&.'899': ; &'<='3'9>': ; &'<=?' 6( D ","$$( D " $$( D ","$ED " $ED ",": ED " : ED ","6ED " 6ED ","$$ED " $$ED ","6( D " ! " #! " $! ! " $#! " %! ! " %#! " !"#$%&'()'*%+,-%.' /( -01( 234 ,.%'5 ,36,'7 .%&.'899': ; &'<='3'9>': ; &'<=?' &5B*2)!%36#6" &5C*2)!!%769" /( -01( 234 ,.%'5 ,36,'7 .%&.'899': ; &'<='3'9>': ; &'<=?' 6( D ","$$( D " $$( D ","$ED " $ED ",": ED " : ED ","6ED " 6ED ","$$ED " $$ED ","6( D " Unique Visitors by Location Distribution of No. of Visits
- 22. © 2013 AirTight Networks, Inc. All rights reserved. AirTight APs/Sensors 22 AT-C10 DoD approved WIPS Sensor Common Criteria FIPS 140-2 DISA APL AT-C55 Dual band dual radio 2x2 AP + background scanning Dedicated WIPS sensor AT-C50 Dual band single radio 2x3 AP + background scanning Dedicated WIPS sensor AT-C60 Dual band dual radio 3x3 AP + background scanning Dedicated WIPS sensor Concurrent AP + Dedicated WIPS
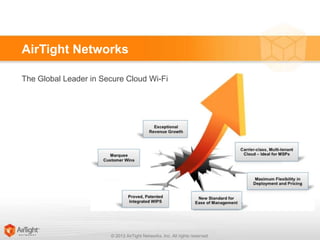
- 23. © 2013 AirTight Networks, Inc. All rights reserved. AT-C60: Industry’s Most Flexible Wi-Fi Platform 23 Software-defined, band-unlocked radios – an industry first Concurrent Wi-Fi access and 24/7 WIPS – an industry first
- 24. © 2013 AirTight Networks, Inc. All rights reserved. AirTight Deployment Choices 24 Public Cloud Private Cloud VMware Appliance Zero Capex Bundled Capex Deployment Pricing No feature based licensing! No user based licensing! AT-C10 AT-C50 AT-C60 Platforms AT-C55
- 25. © 2013 AirTight Networks, Inc. All rights reserved. Thank You! 25 Cloud Managed Secure Wi-Fi Solutions www.airtightnetworks.com info@airtightnetworks.com @AirTight +1 877 424 7844
