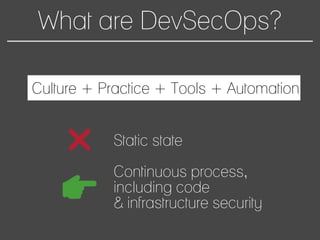
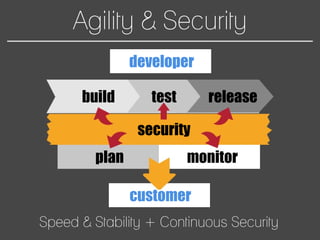
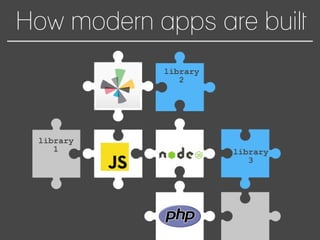
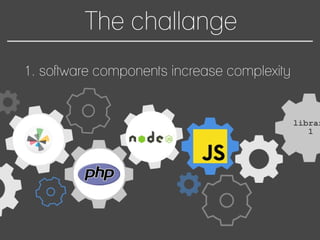
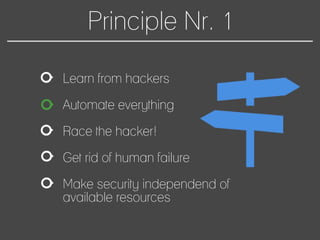
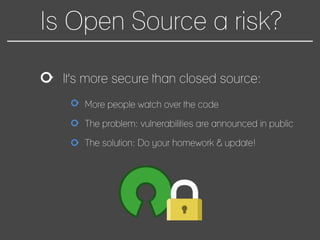
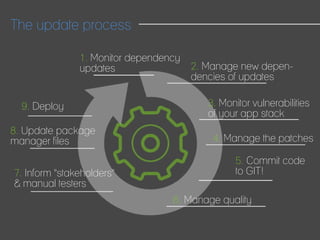
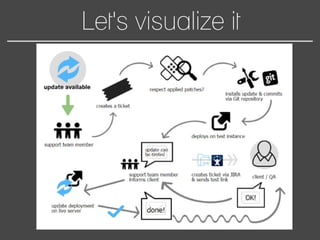
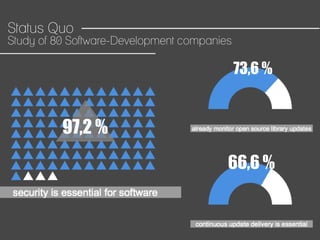
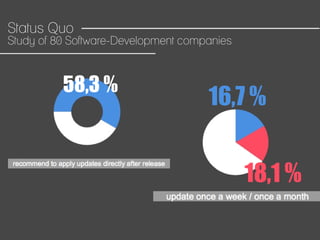
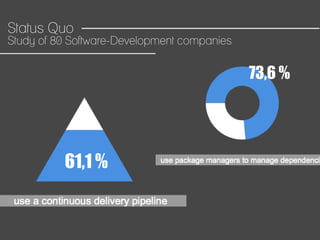
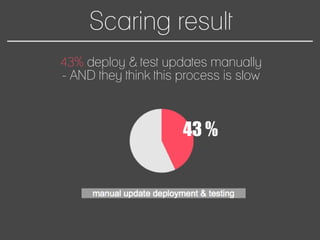
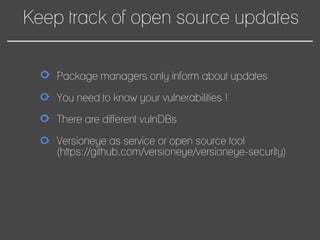
This document discusses how to automate DevSecOps successfully. It outlines what DevSecOps is and how modern applications are built using many software components and libraries. This complexity increases risks from vulnerabilities in dependencies. The document recommends automating security practices like monitoring for vulnerabilities, updating dependencies continuously, and deploying updates immediately to "race the hacker." It advocates learning from hackers by automating everything to eliminate human errors. Specific automation approaches discussed include using containers and infrastructure as code, continuous integration/delivery pipelines, and monitoring tools to track open source updates and vulnerabilities. The goal is to fully automate the update and deployment process so that any new vulnerabilities can be addressed instantly regardless of available resources.