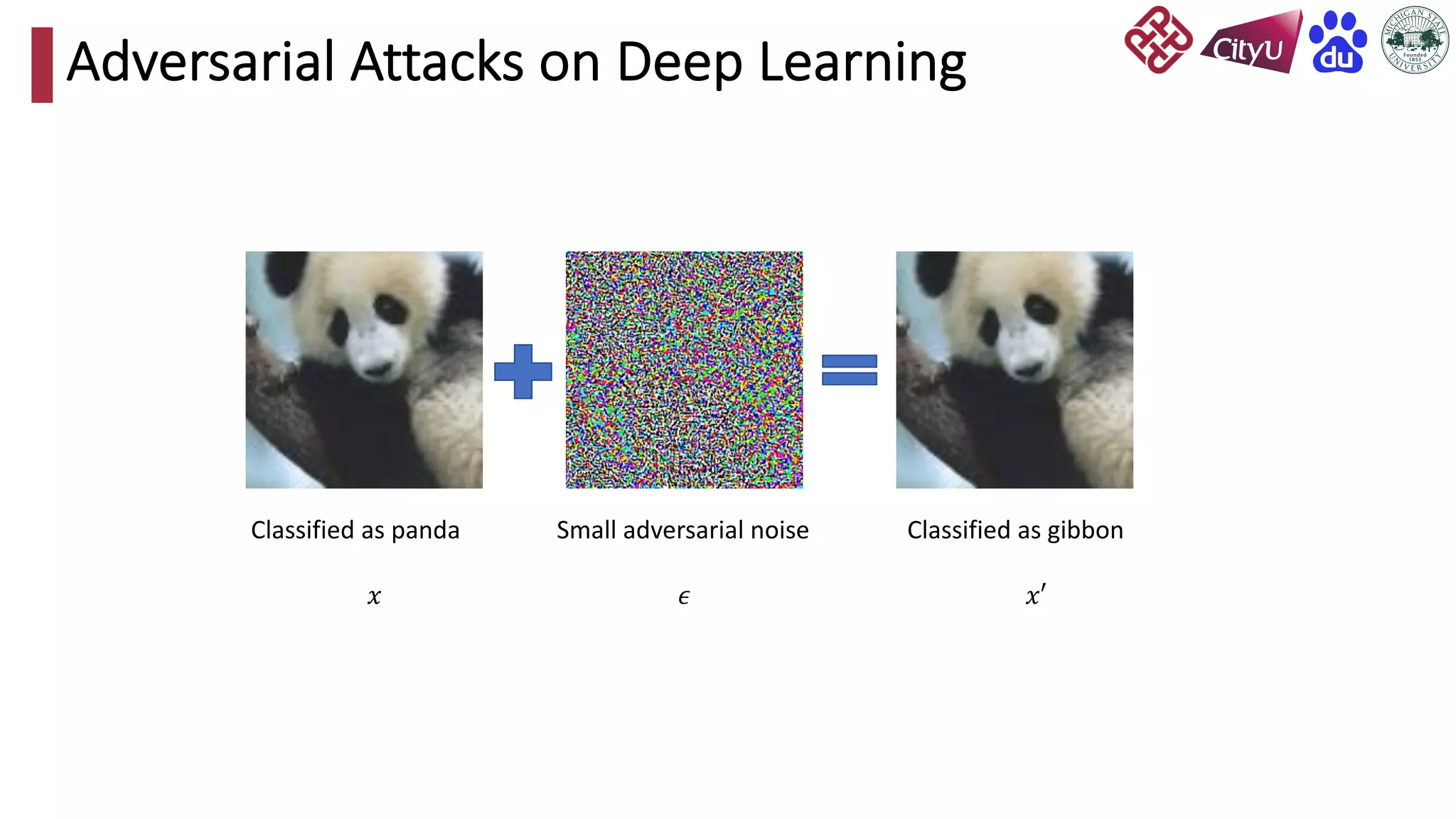
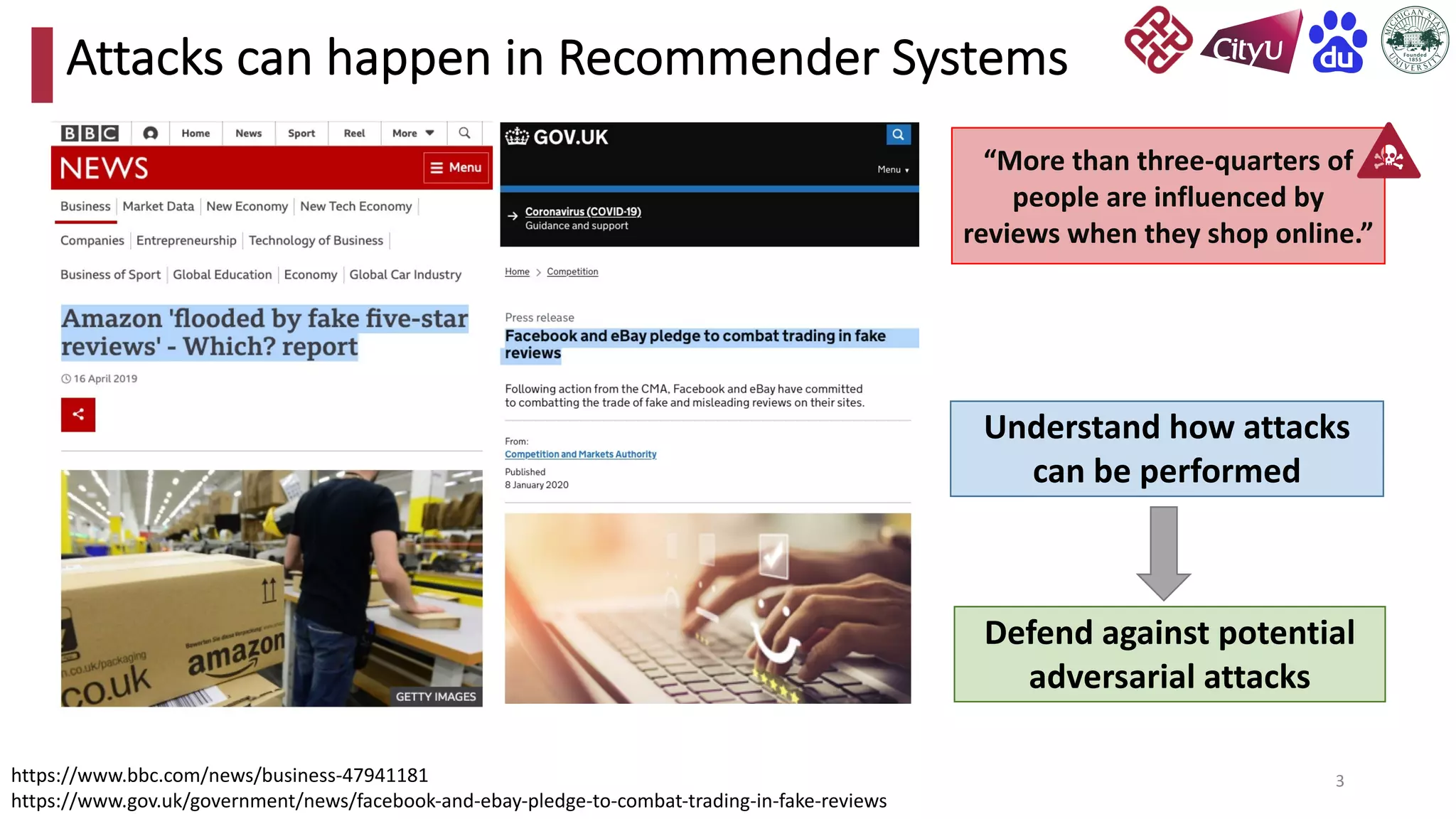
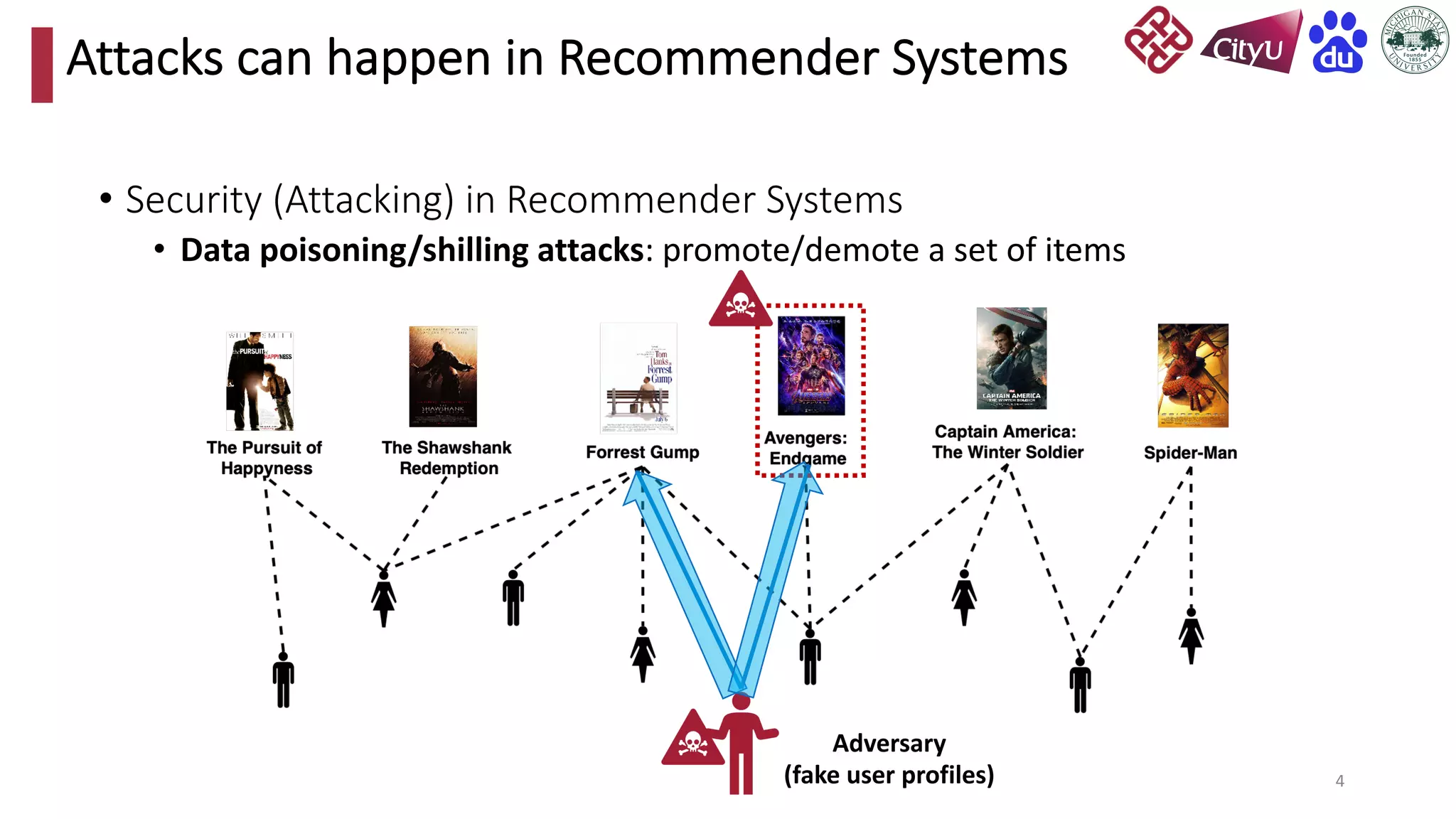
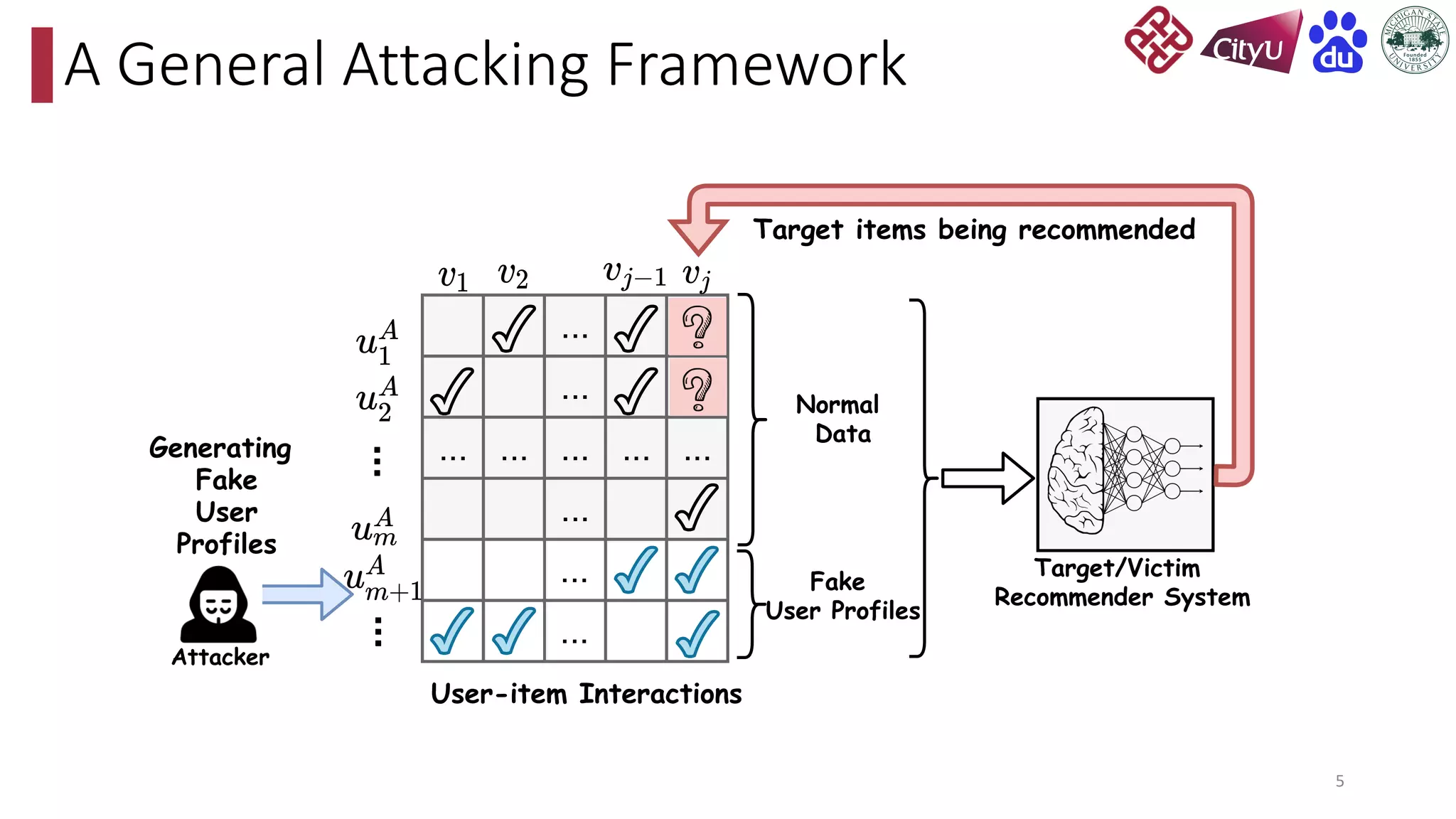
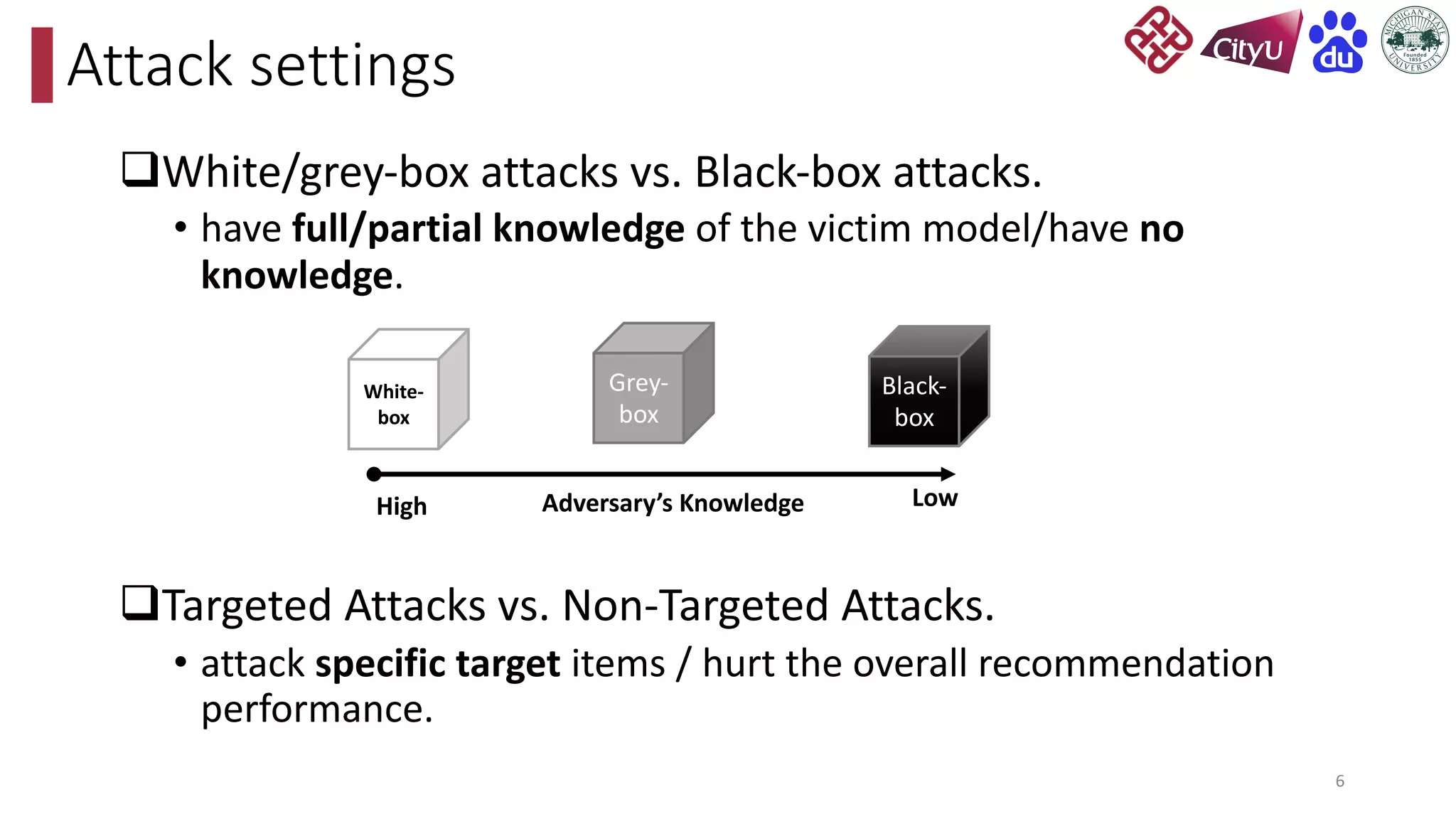
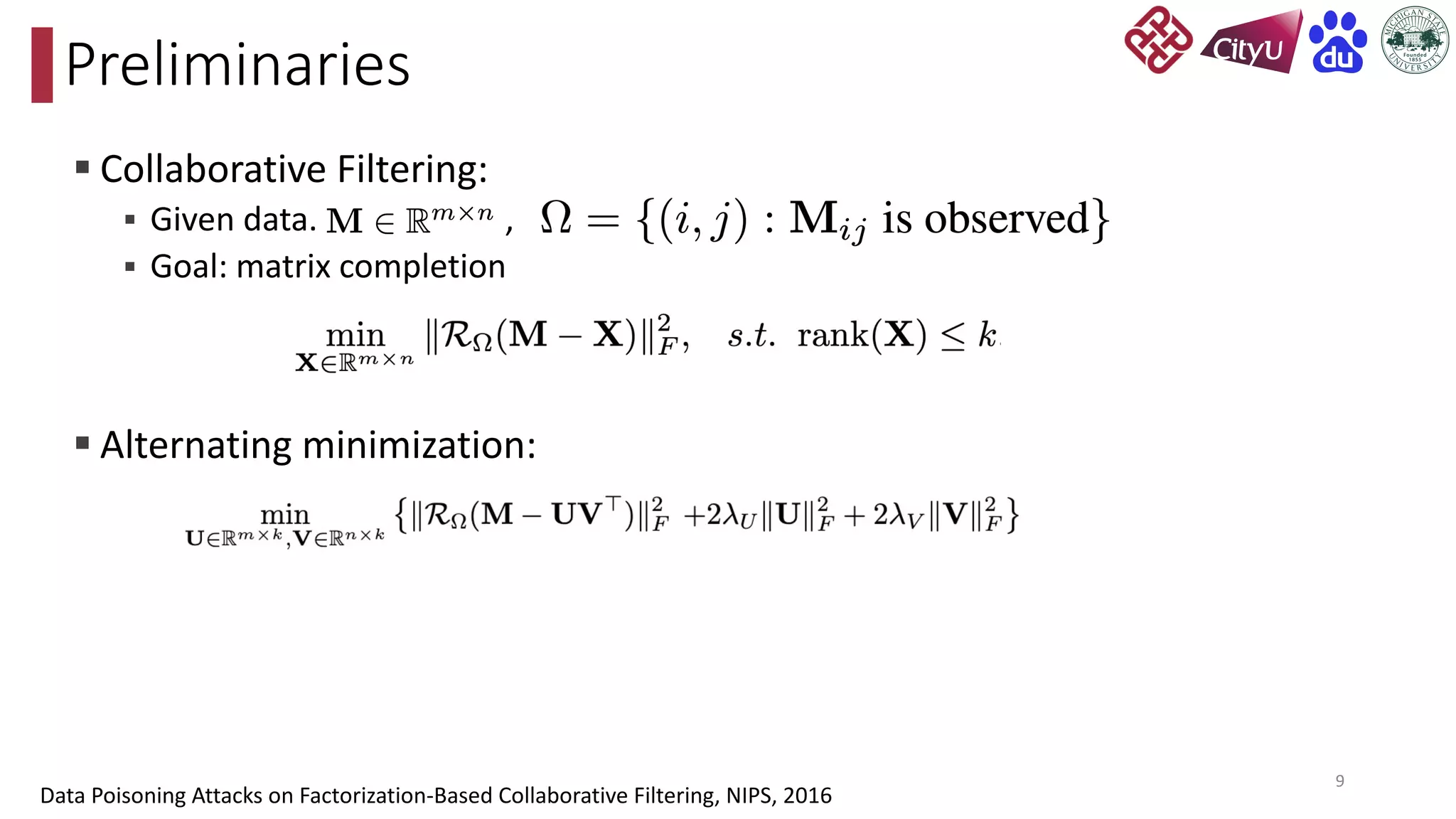
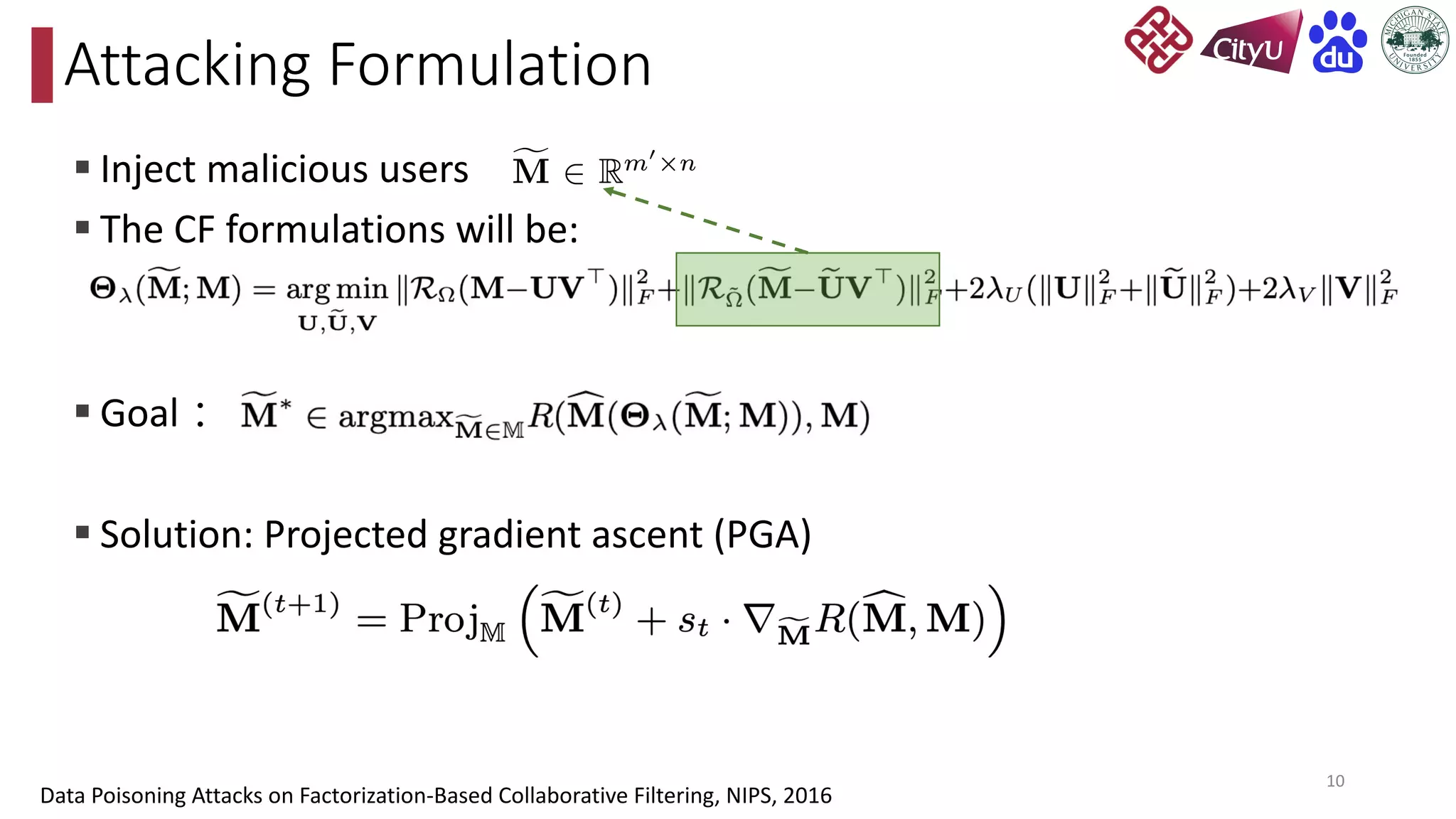
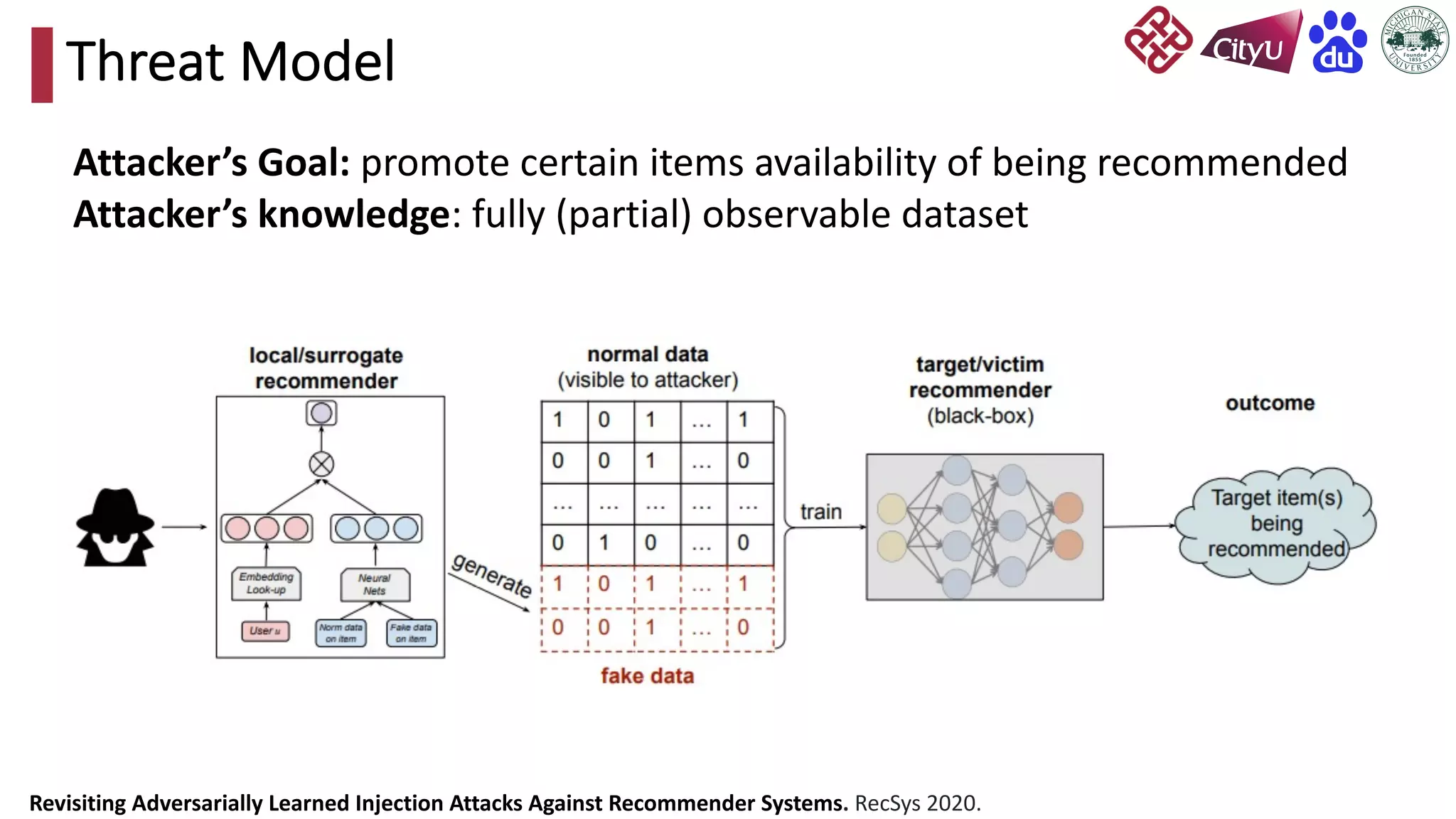
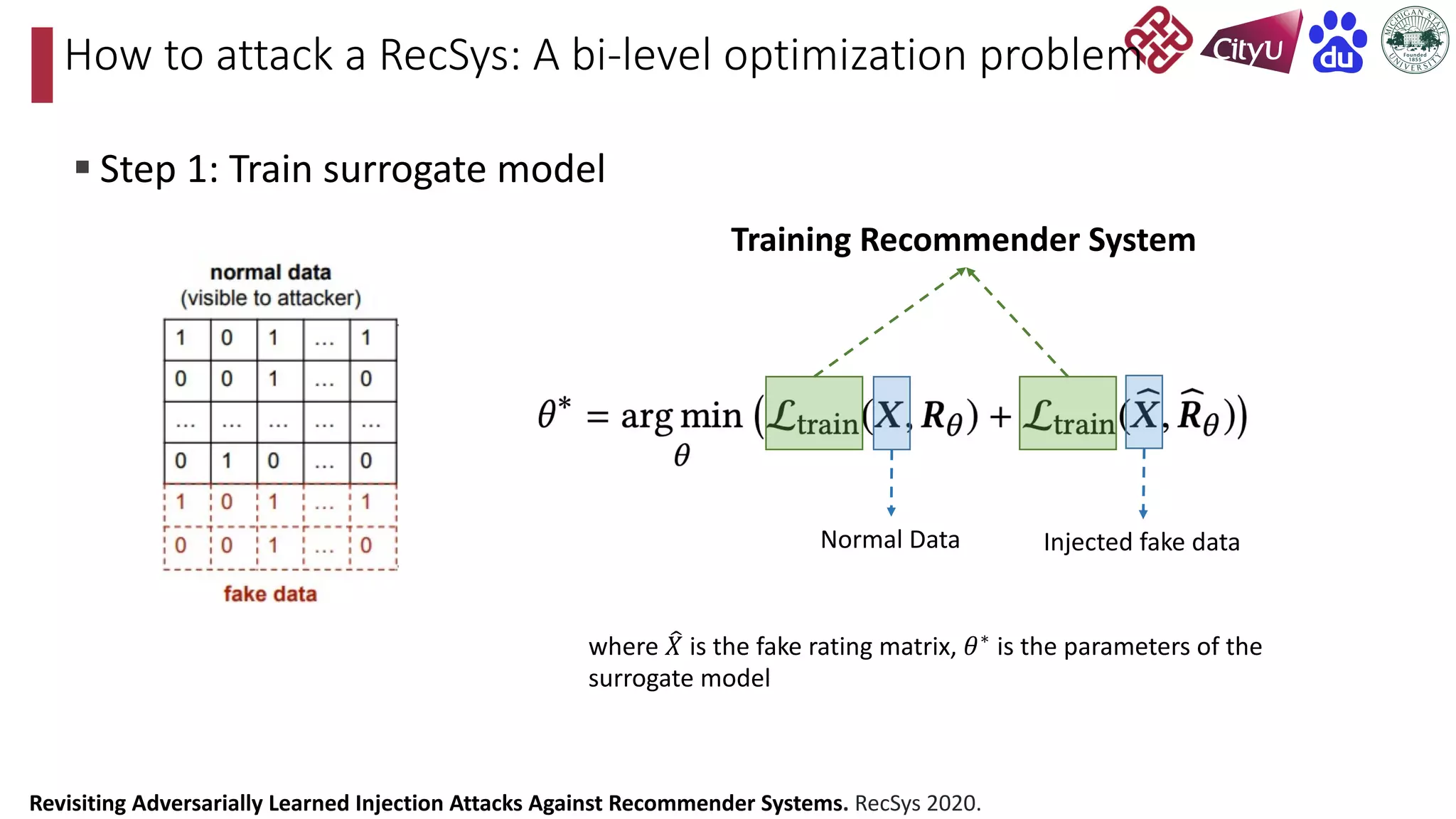
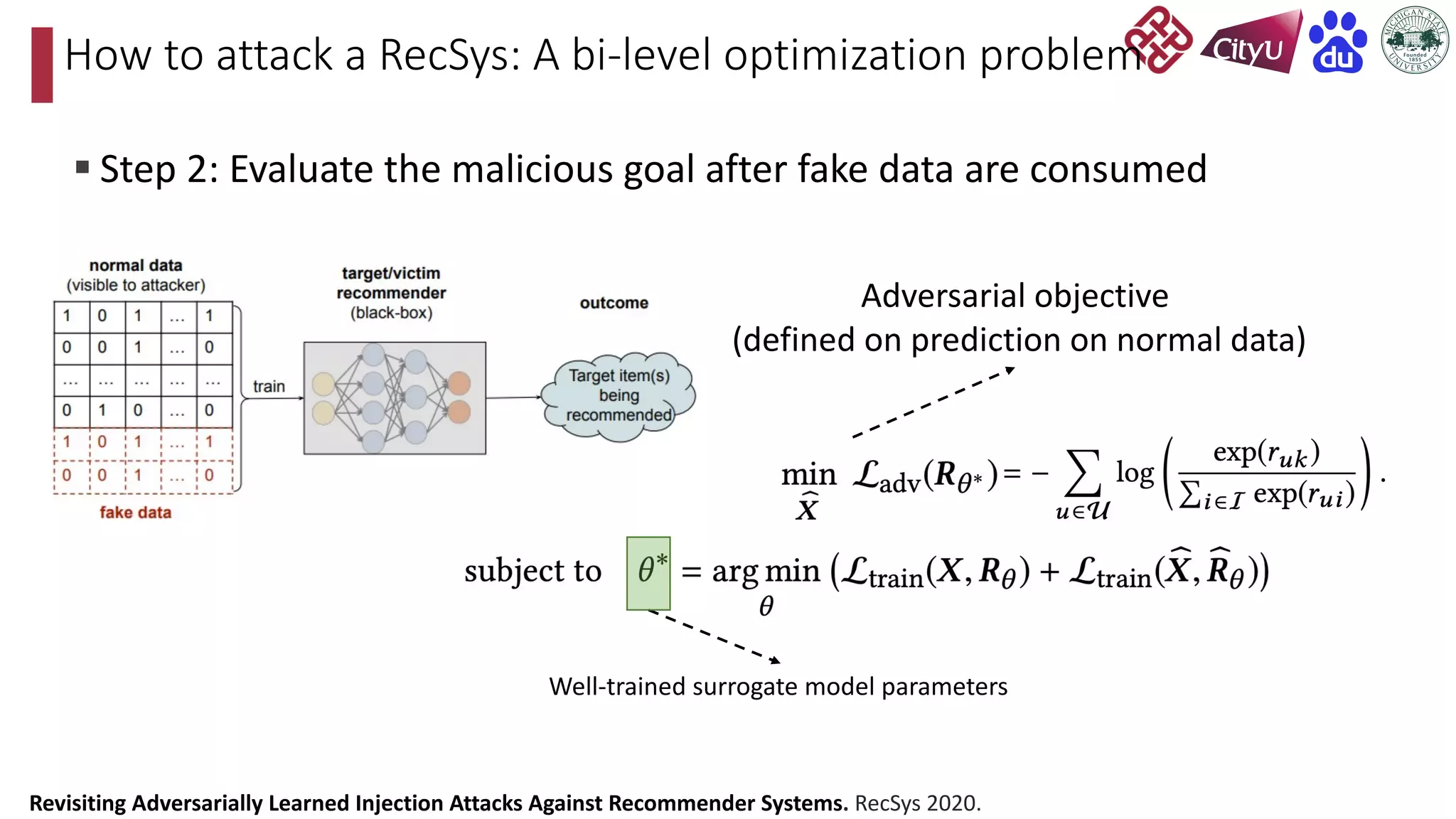
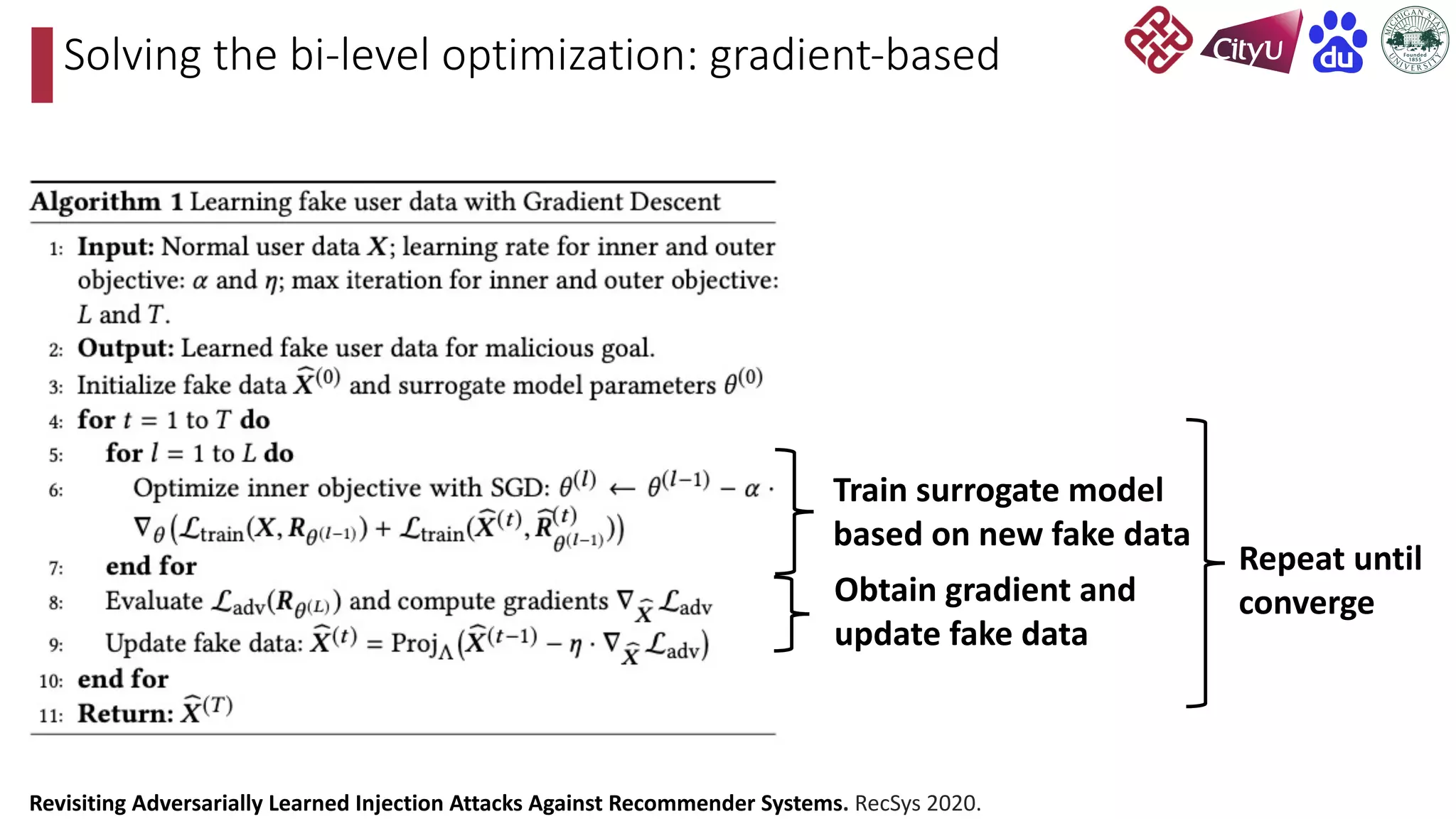
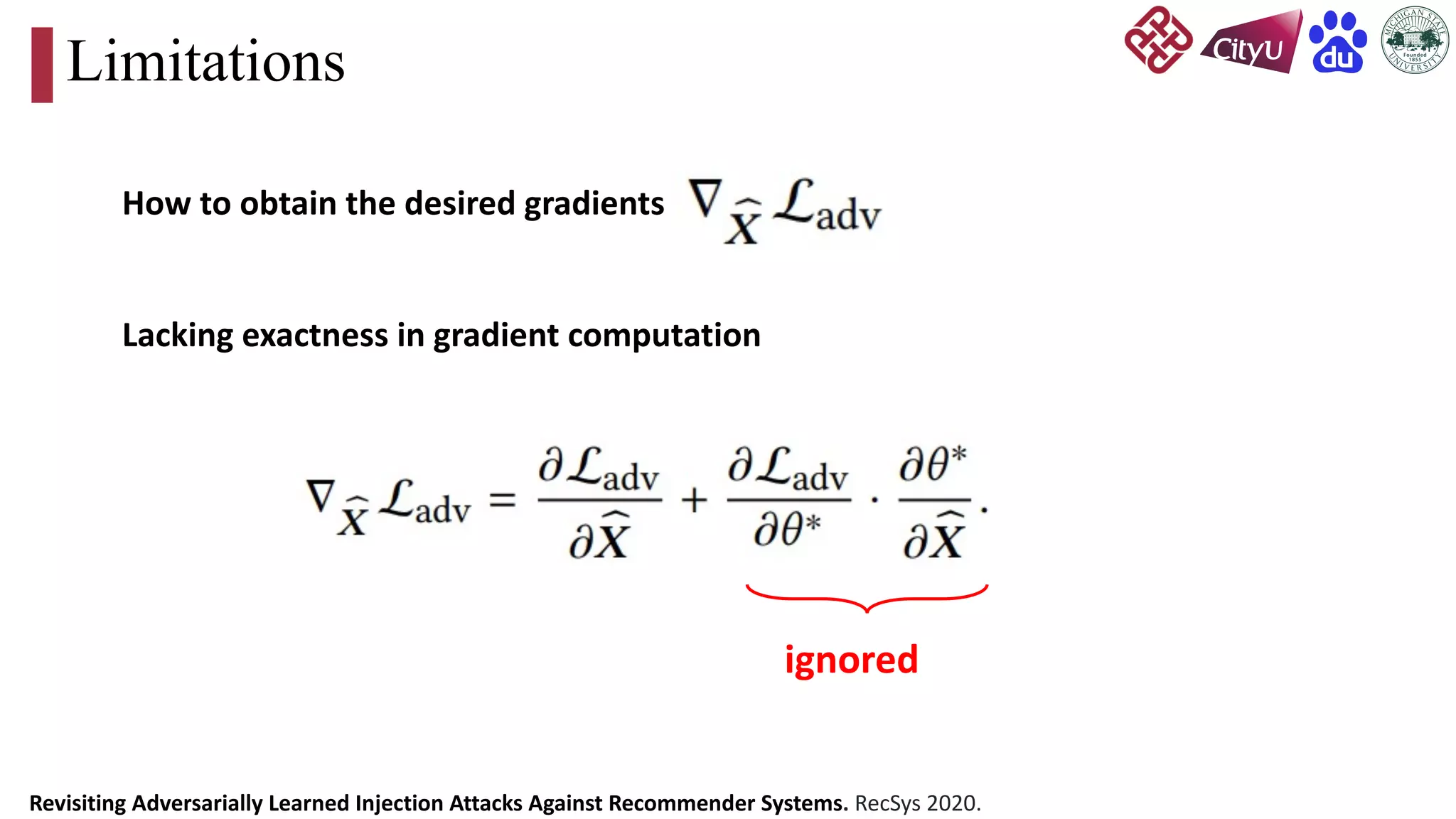
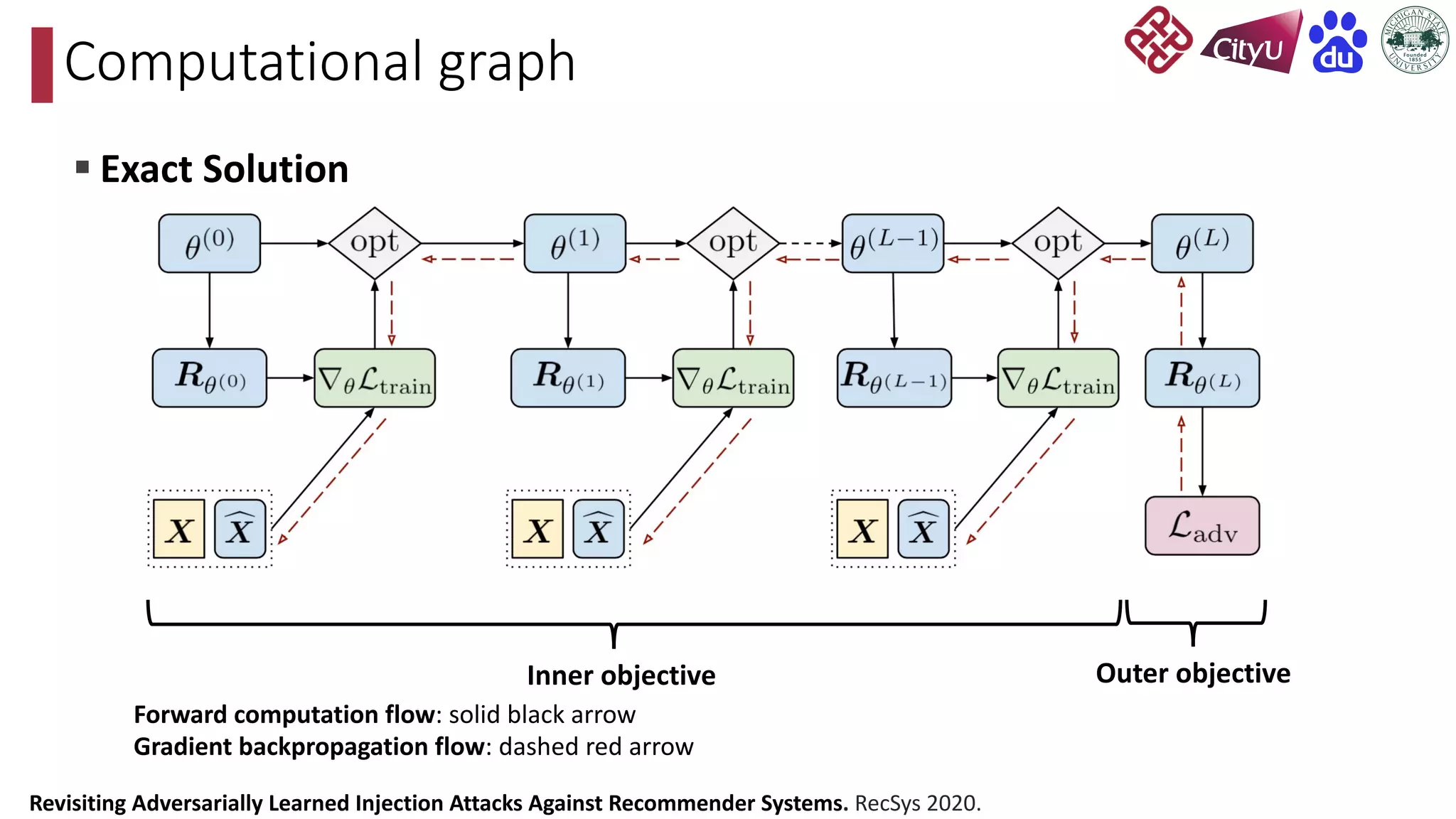
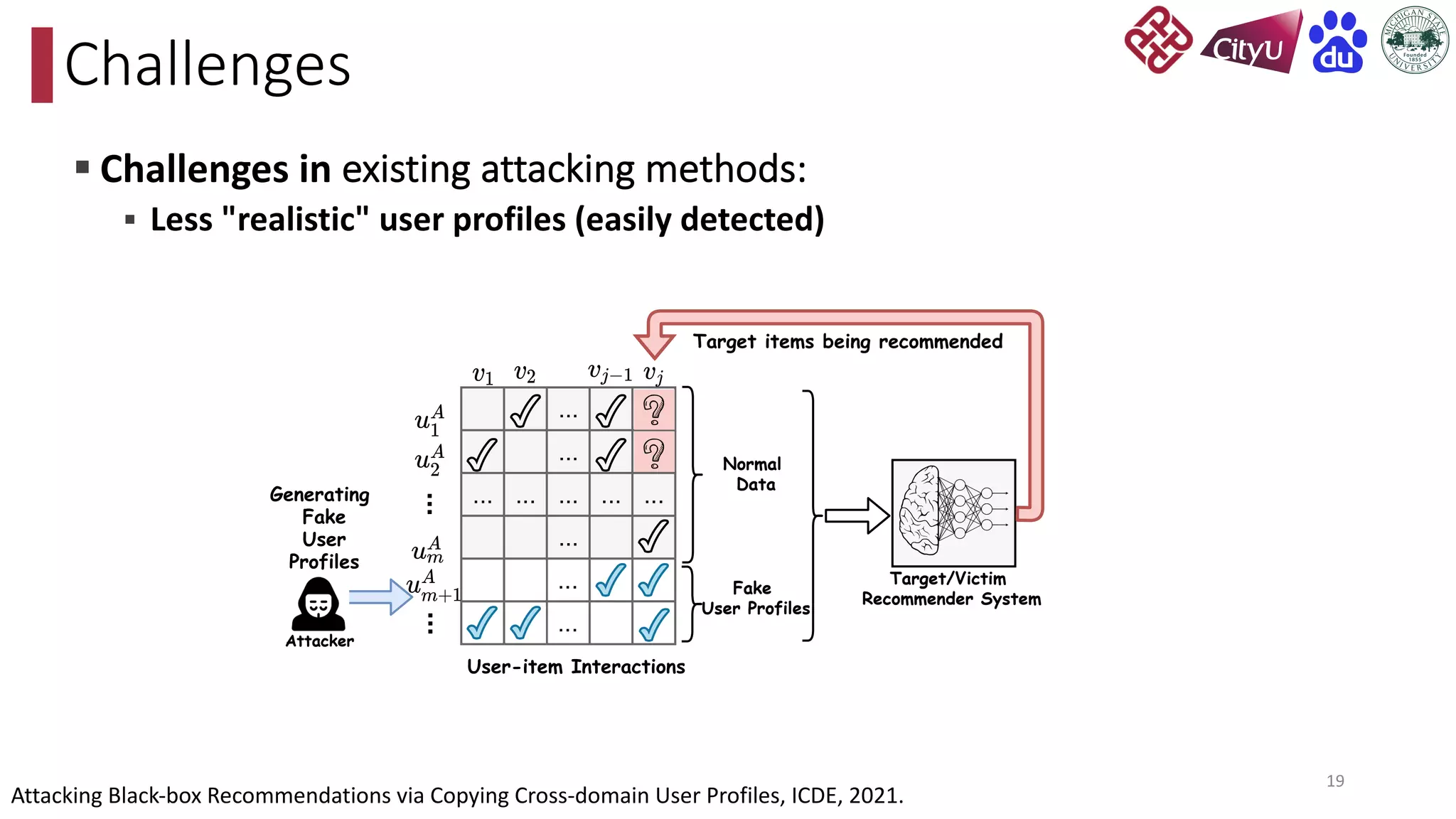
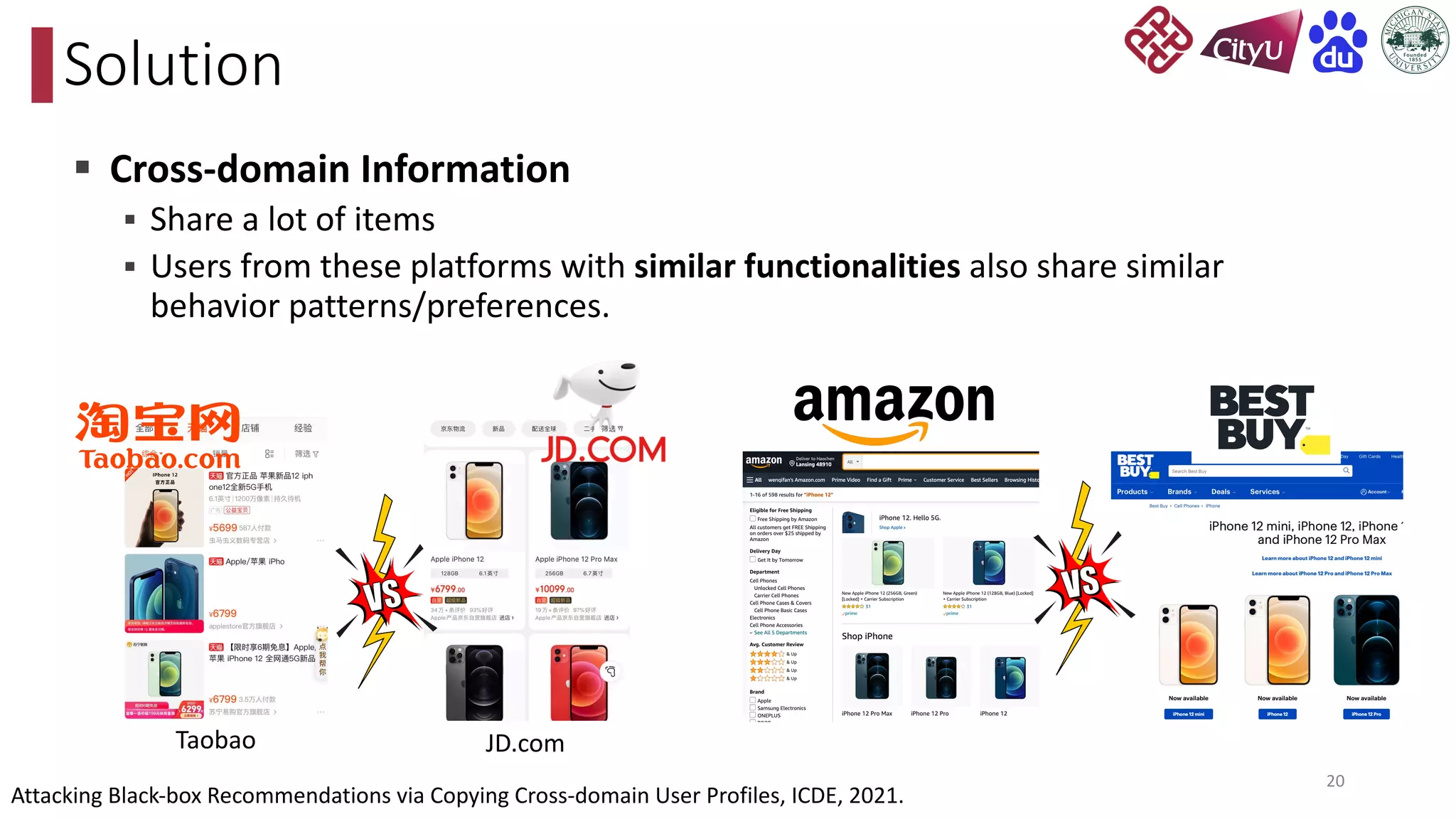
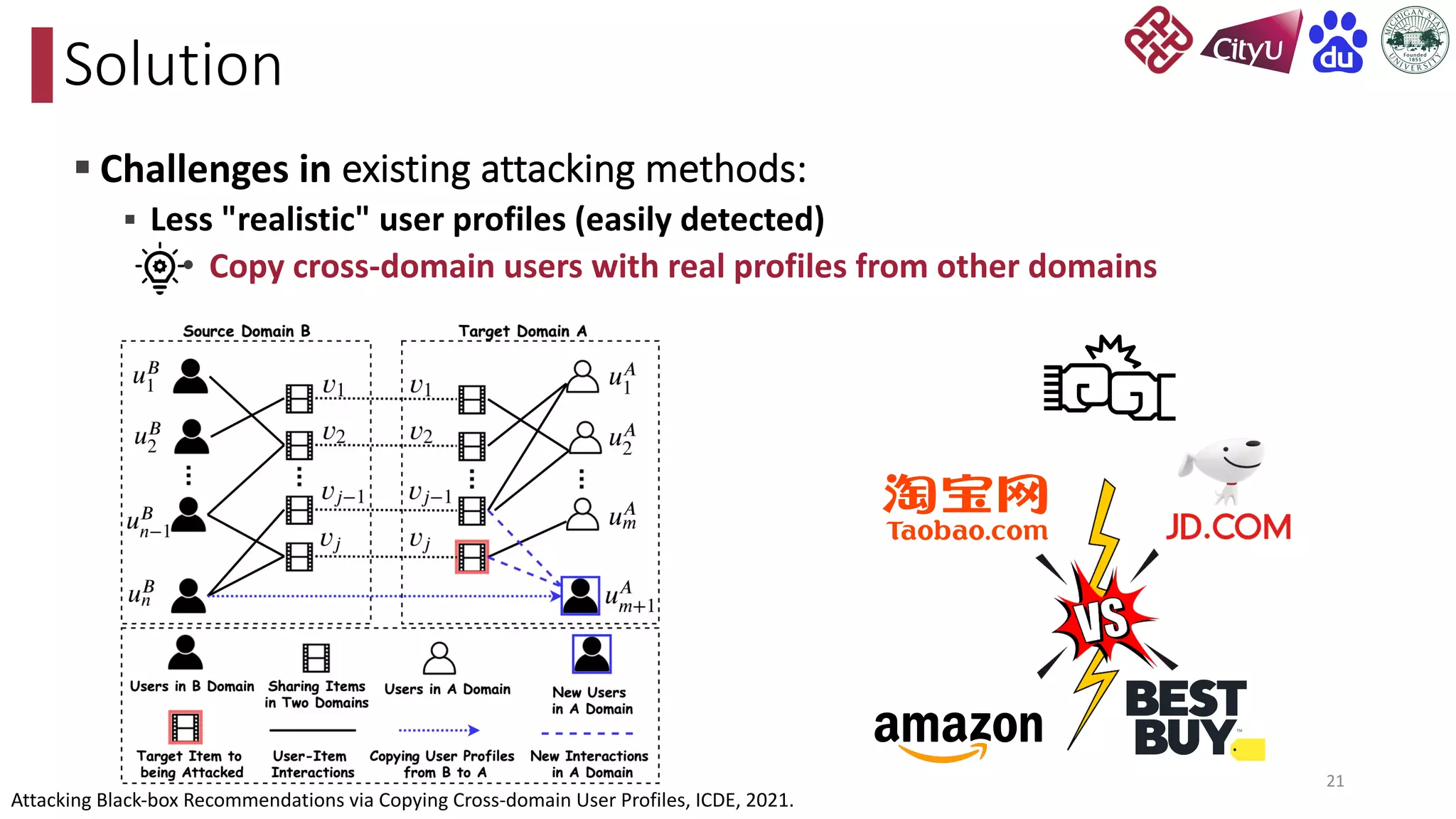
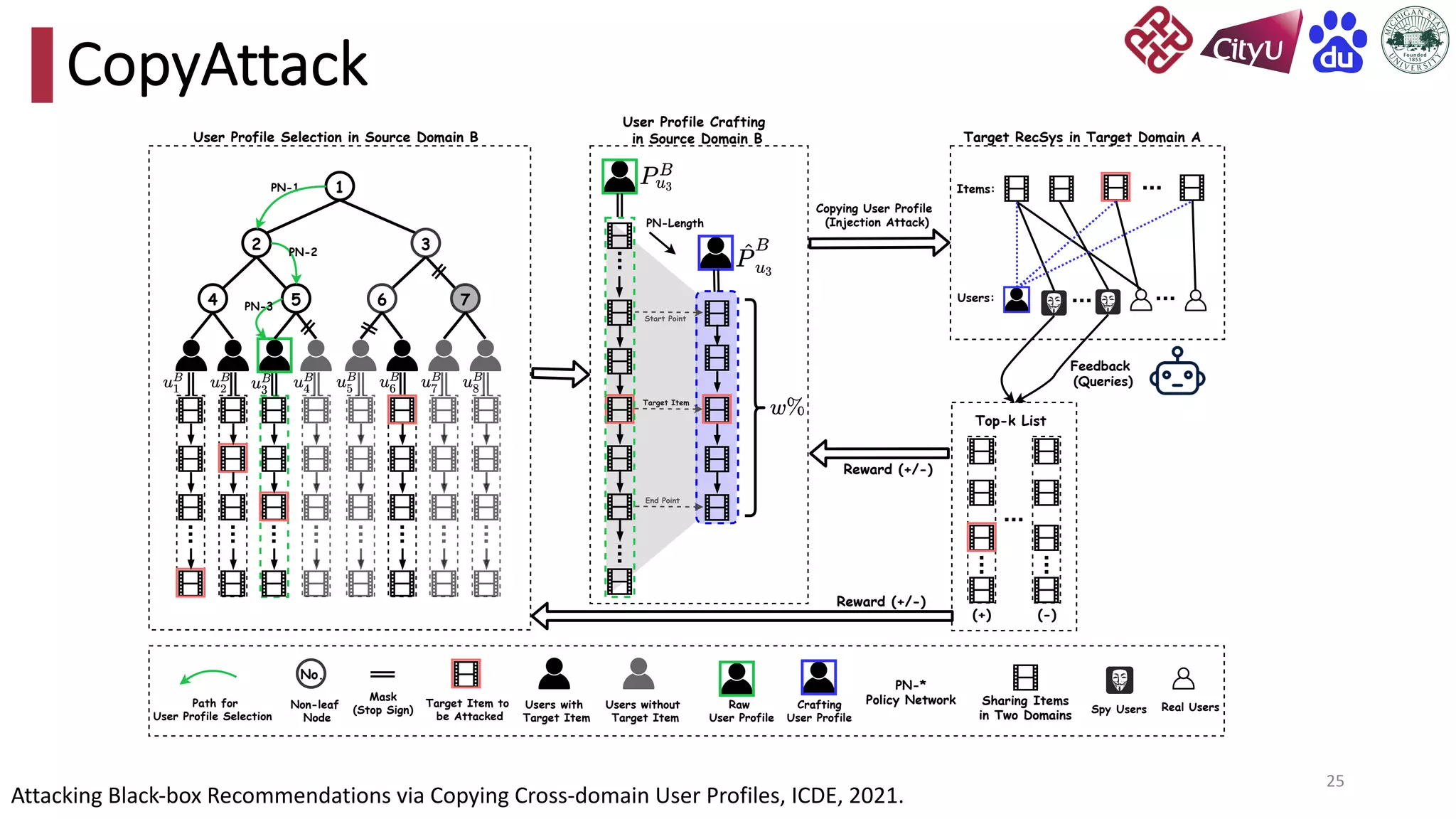
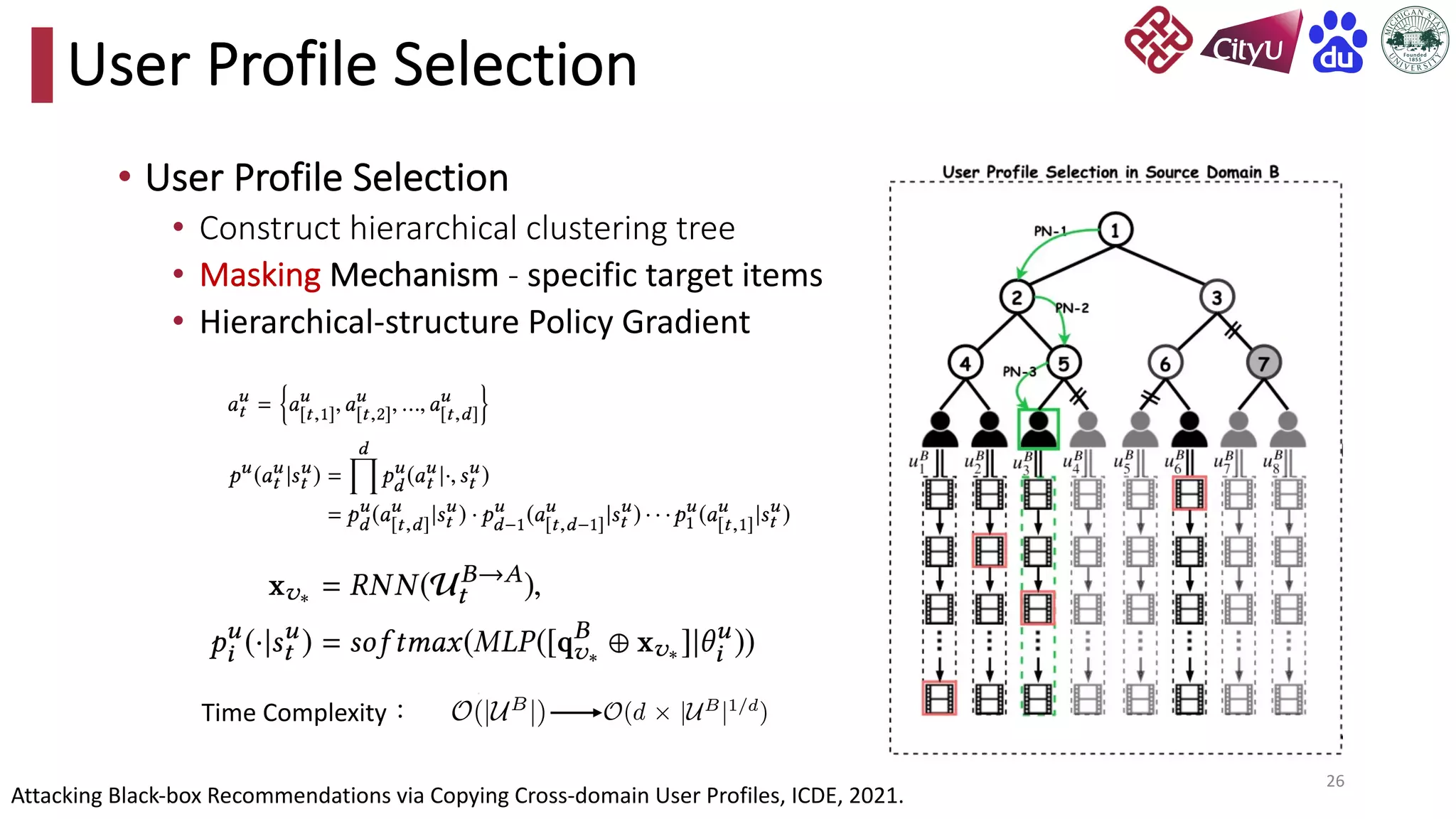
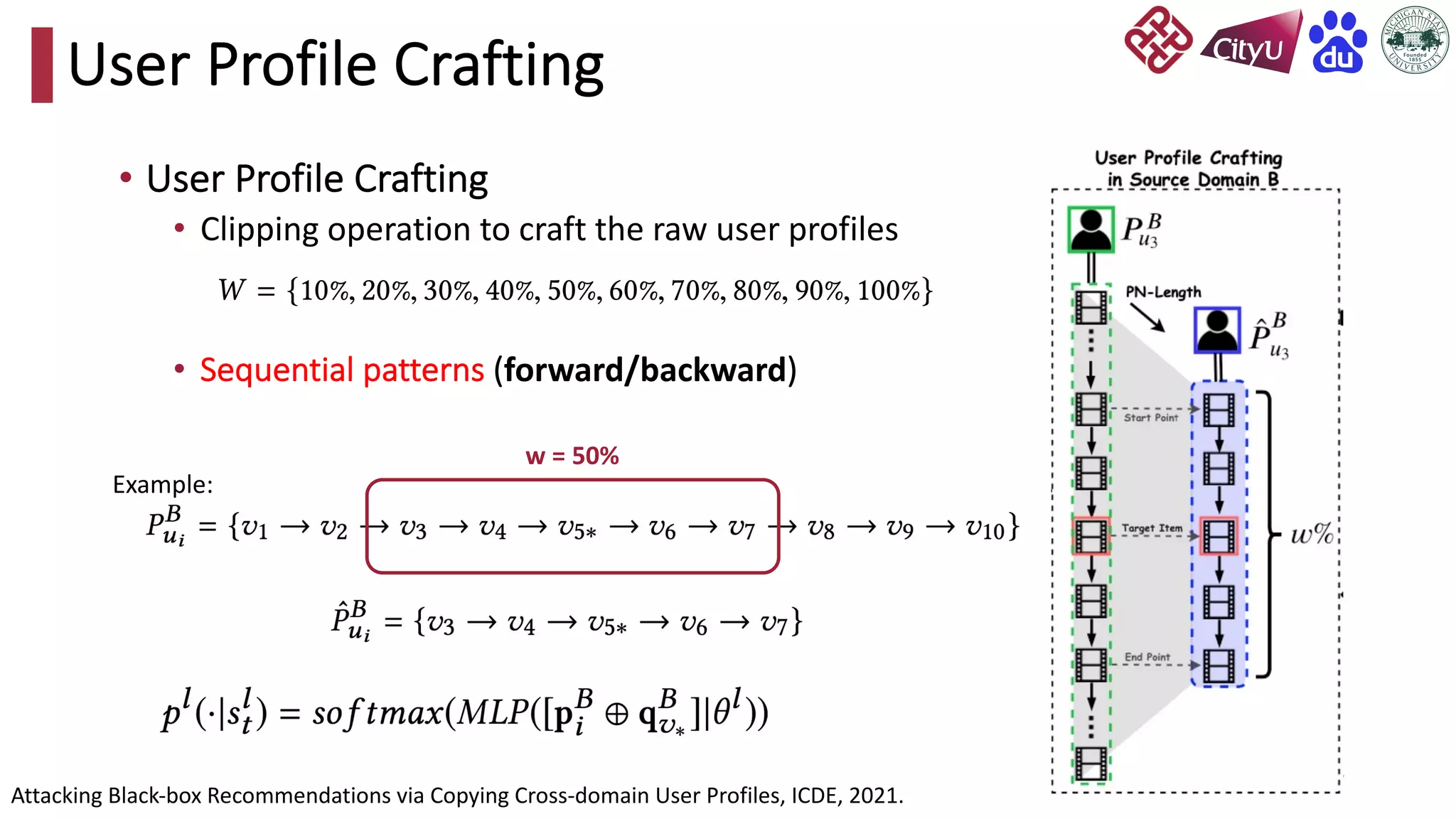
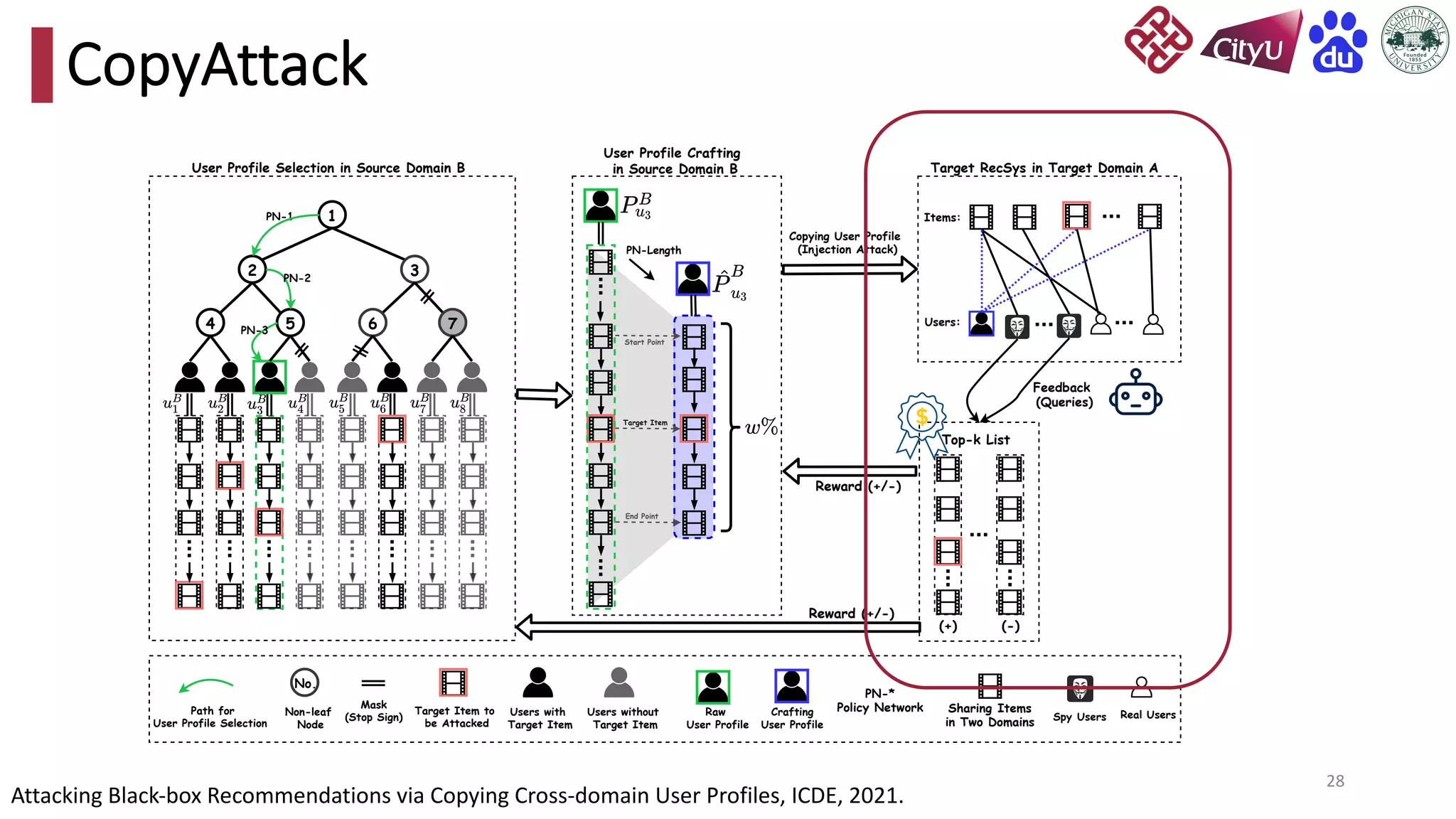
This document discusses adversarial attacks on recommendation systems, detailing various attack methodologies including data poisoning and user profile manipulation. It categorizes attacks into white-box, grey-box, and black-box types, highlighting the challenges and strategies for each approach. The content emphasizes the importance of understanding these attacks to defend against potential risks in recommender systems.