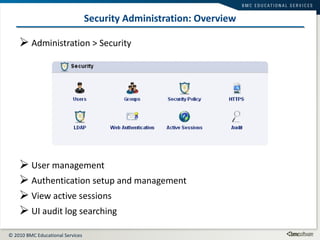
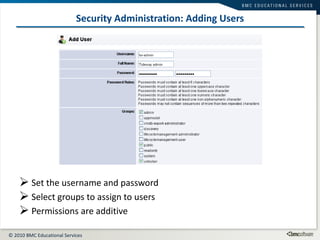
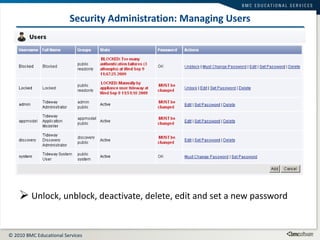
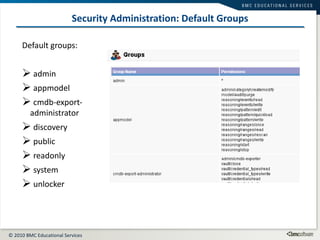
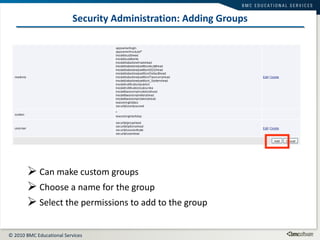
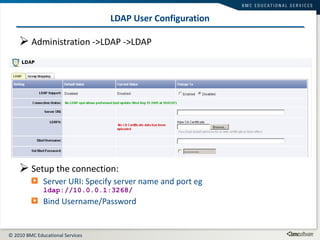
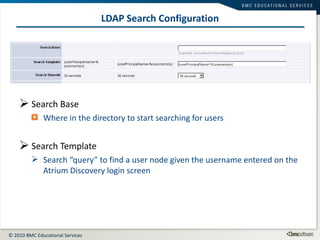
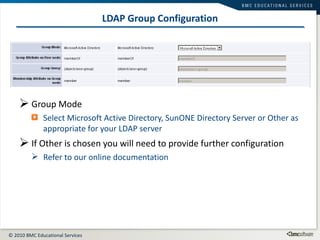
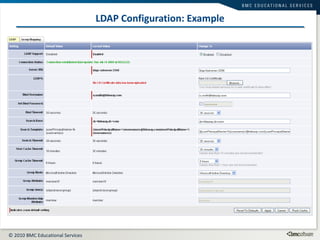
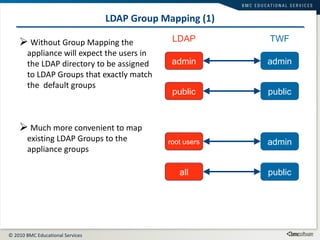
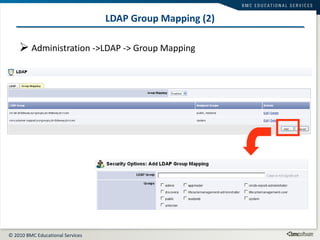
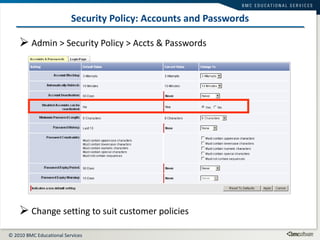
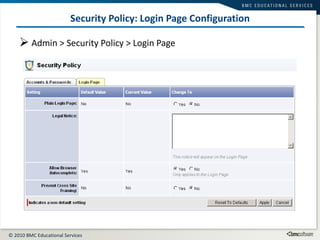
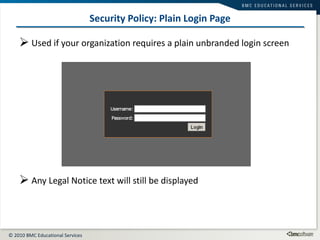
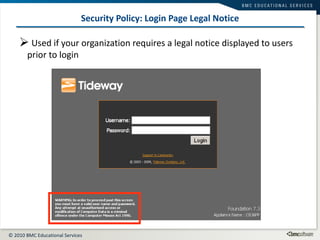
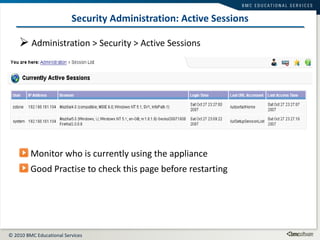
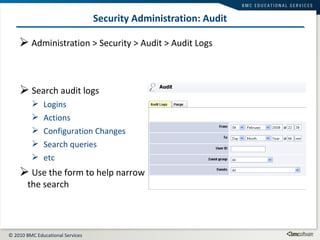
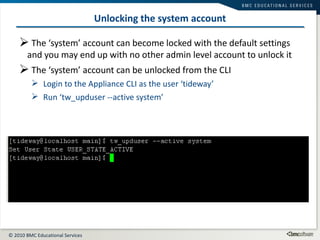
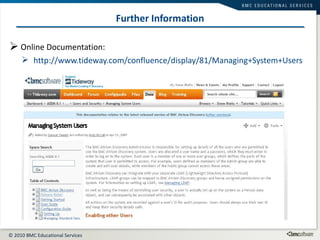
This document summarizes user administration and system security features in Tideway Foundation. It discusses user management including adding and managing users and groups. It also covers LDAP integration for authentication, configuring security policies like login pages and auditing, and managing active sessions and audit logs. System level accounts on the CLI are also mentioned.