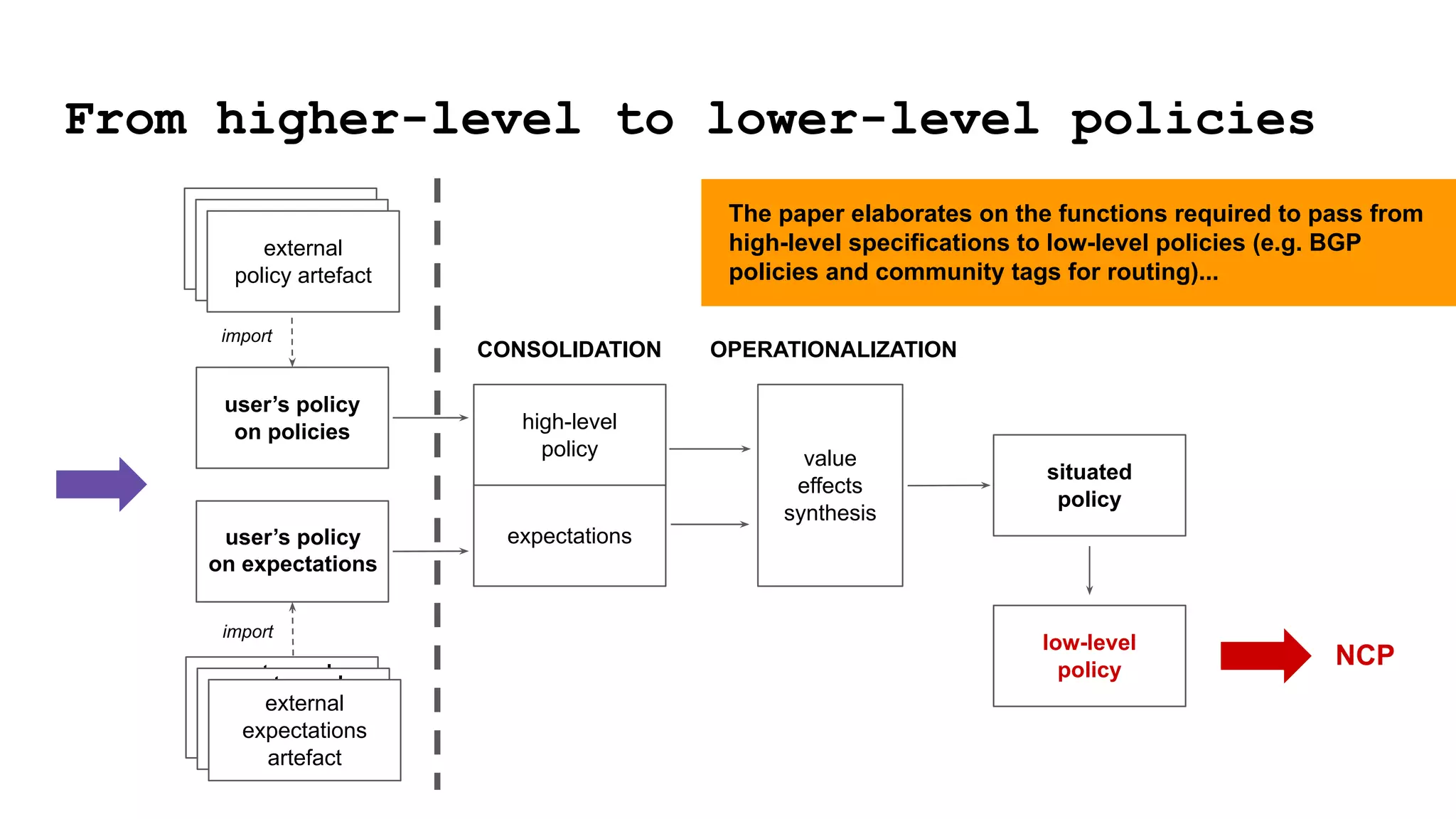
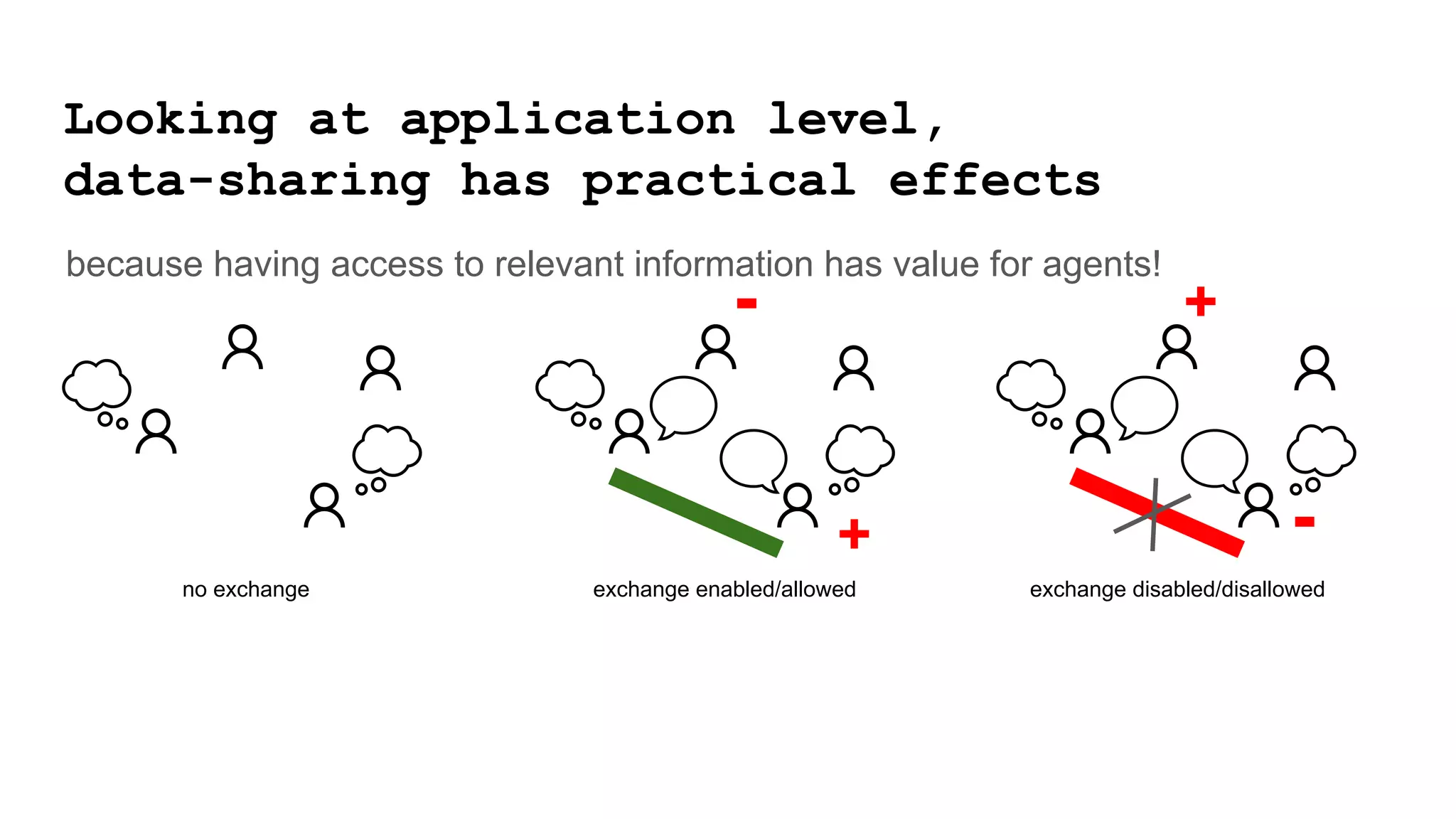
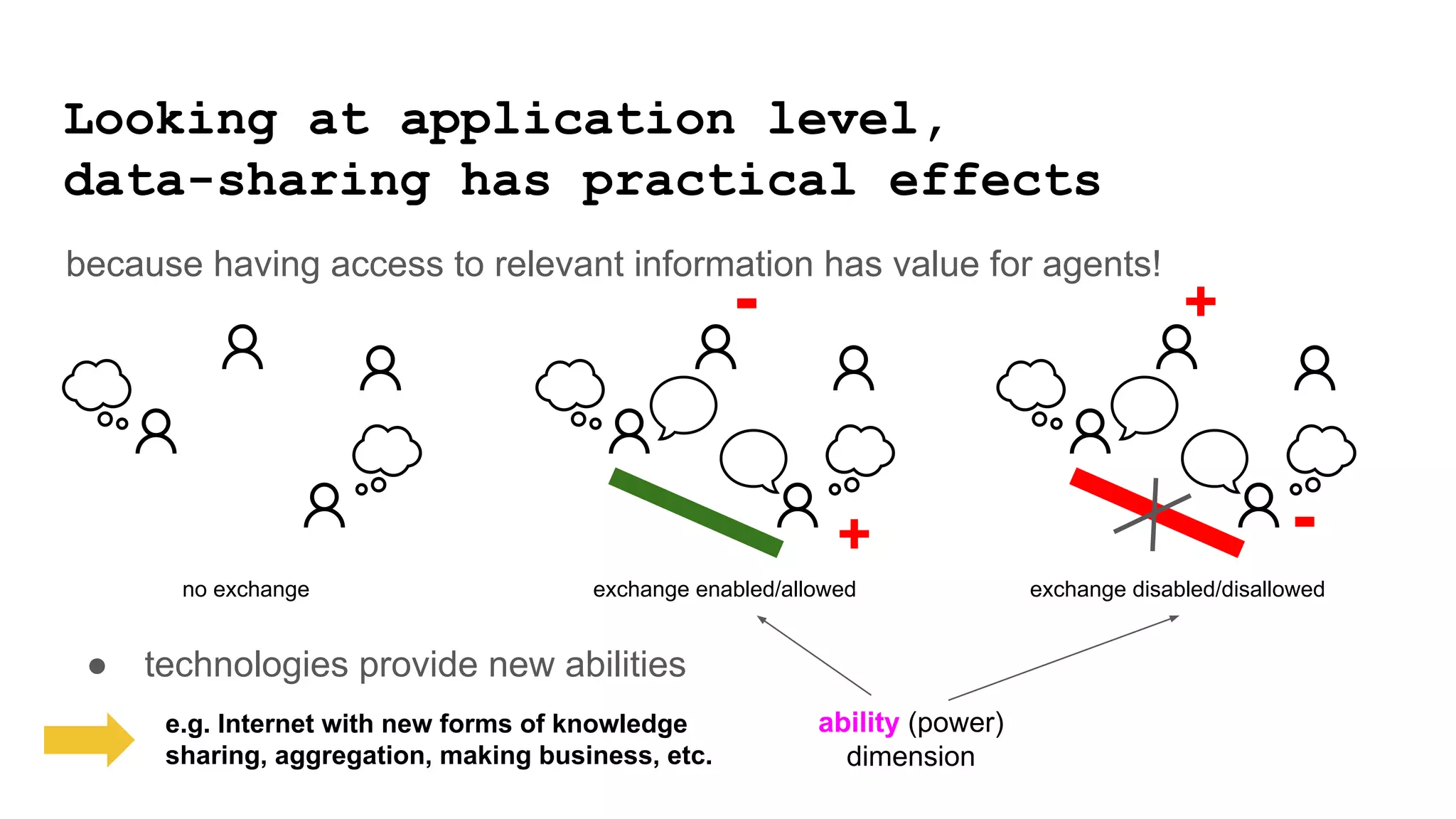
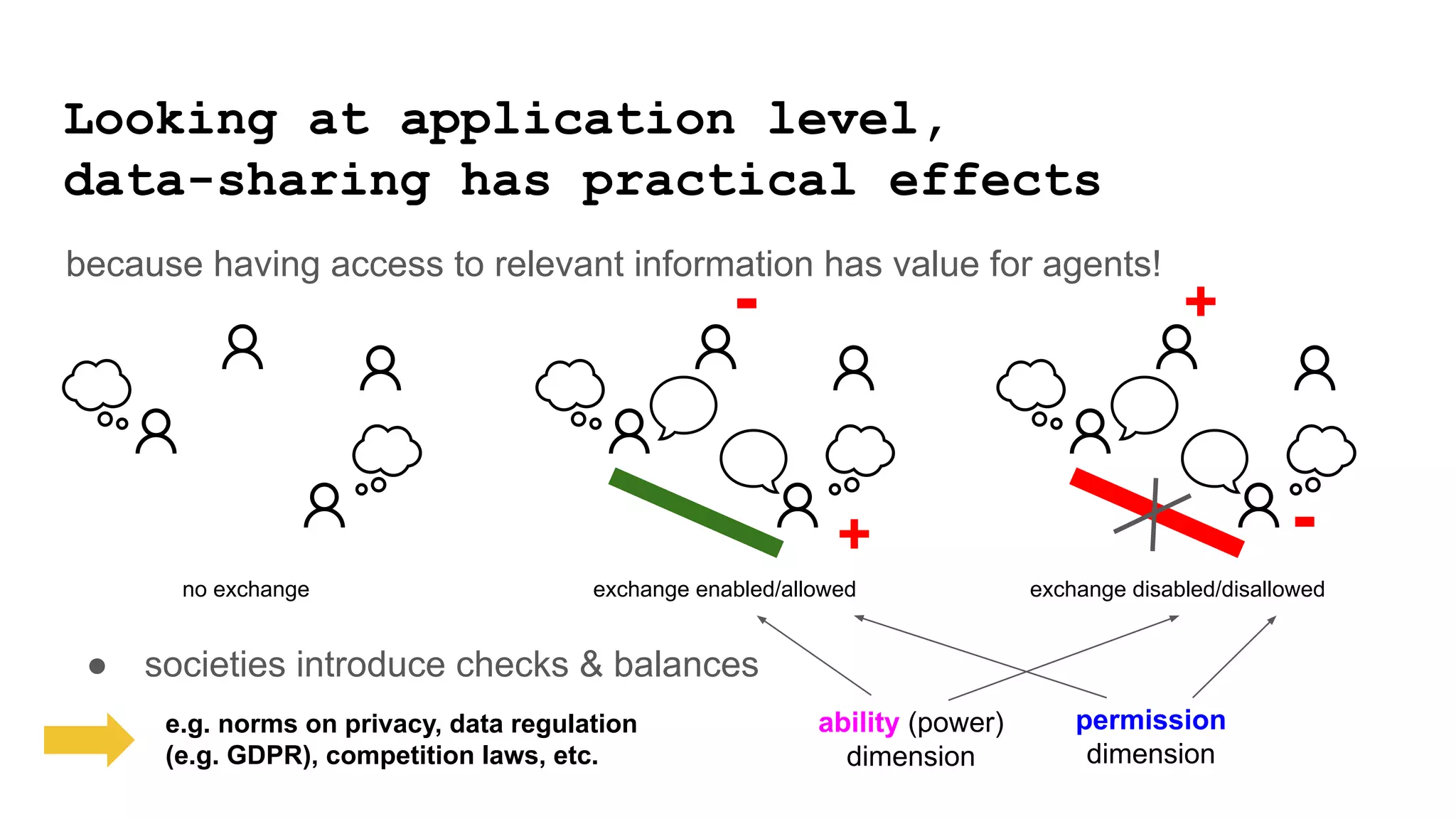
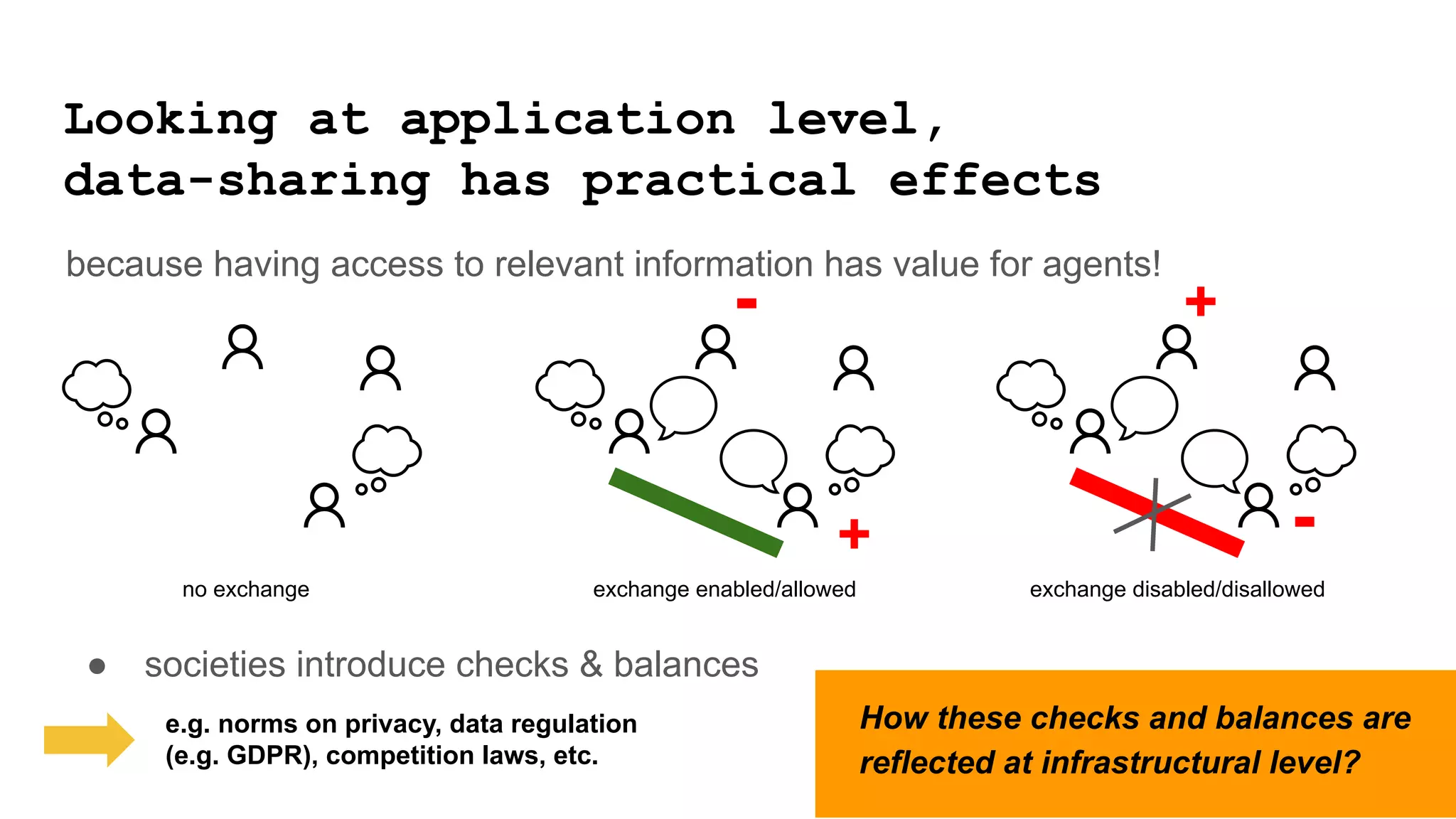
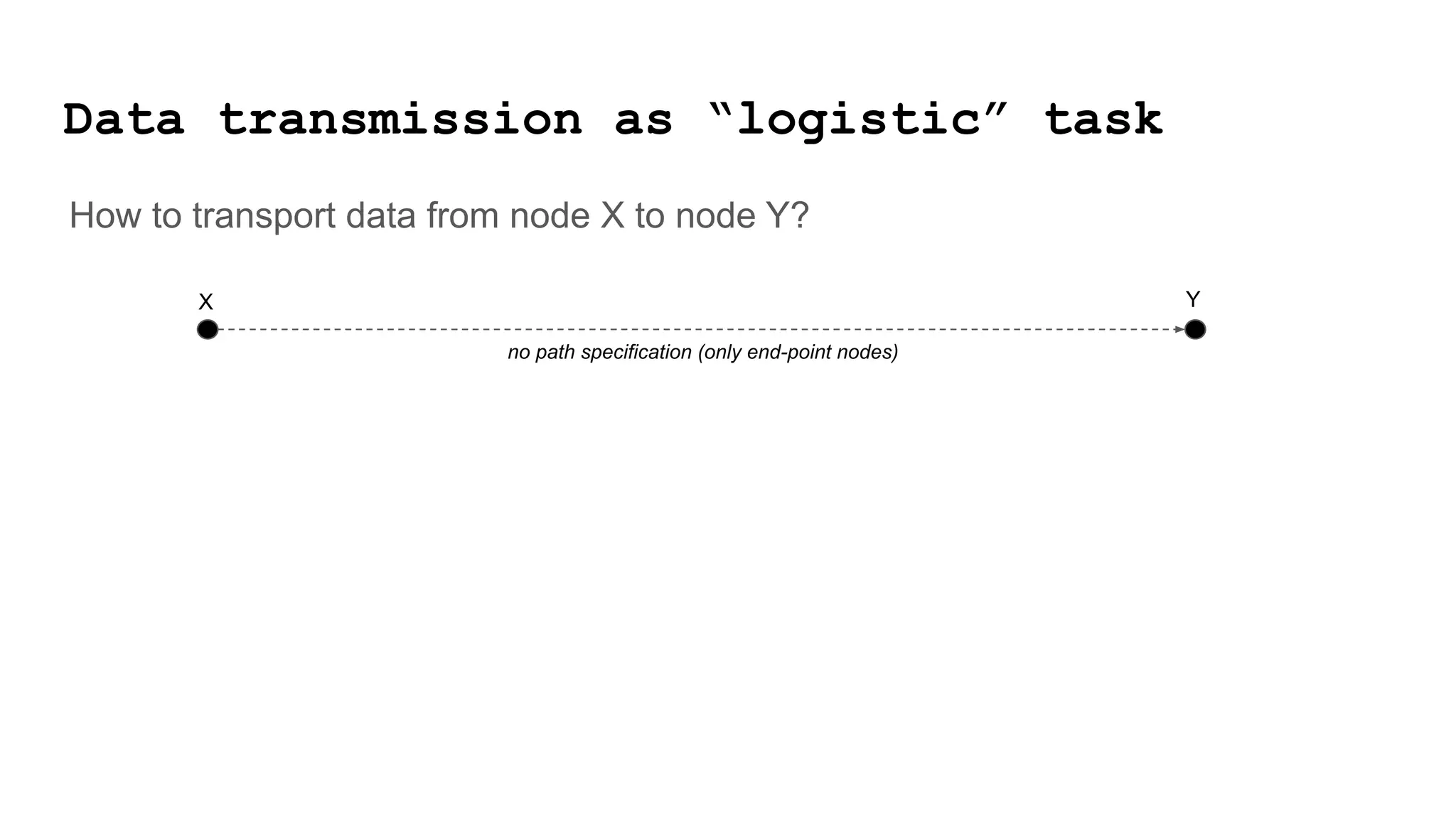
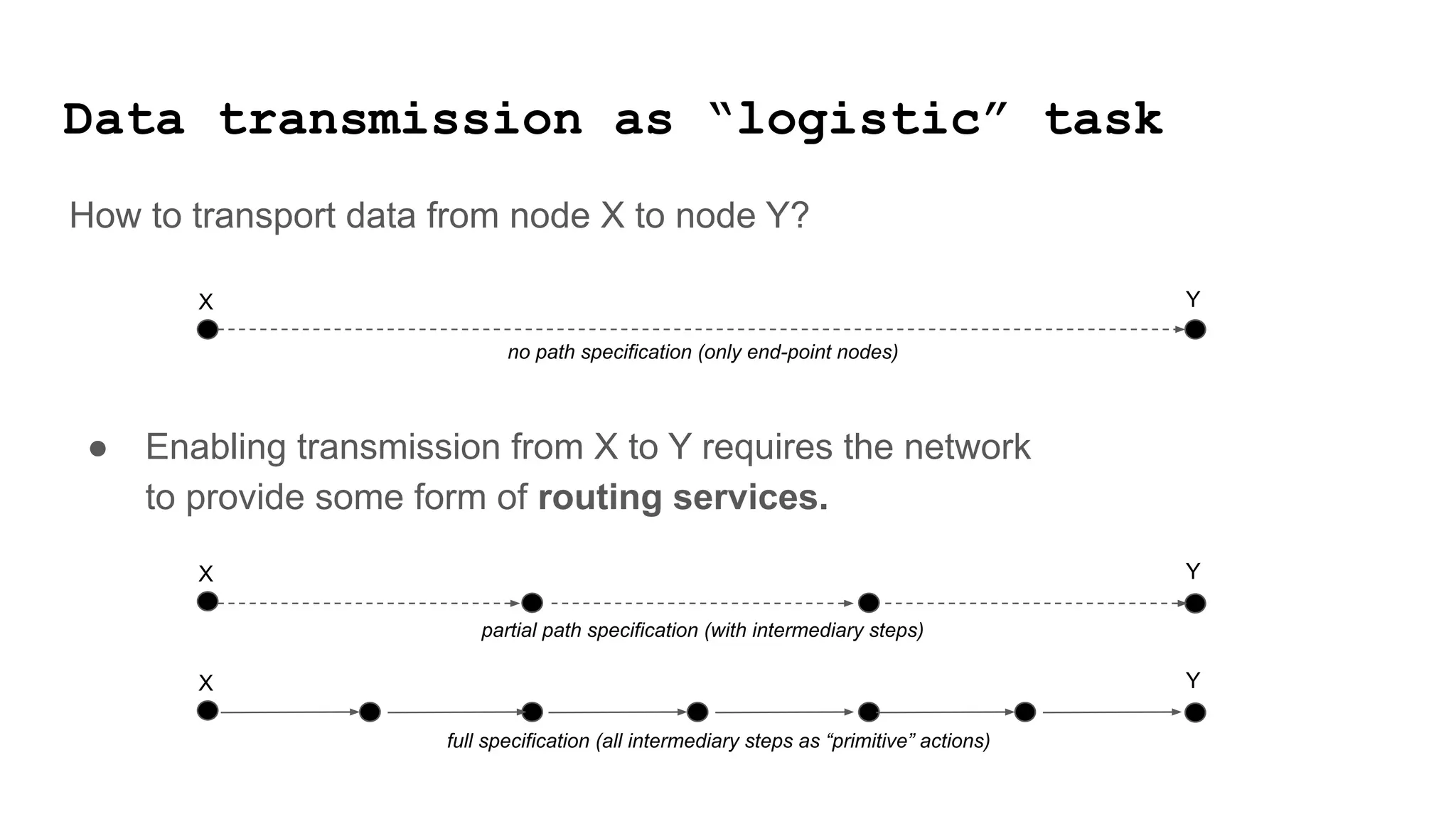
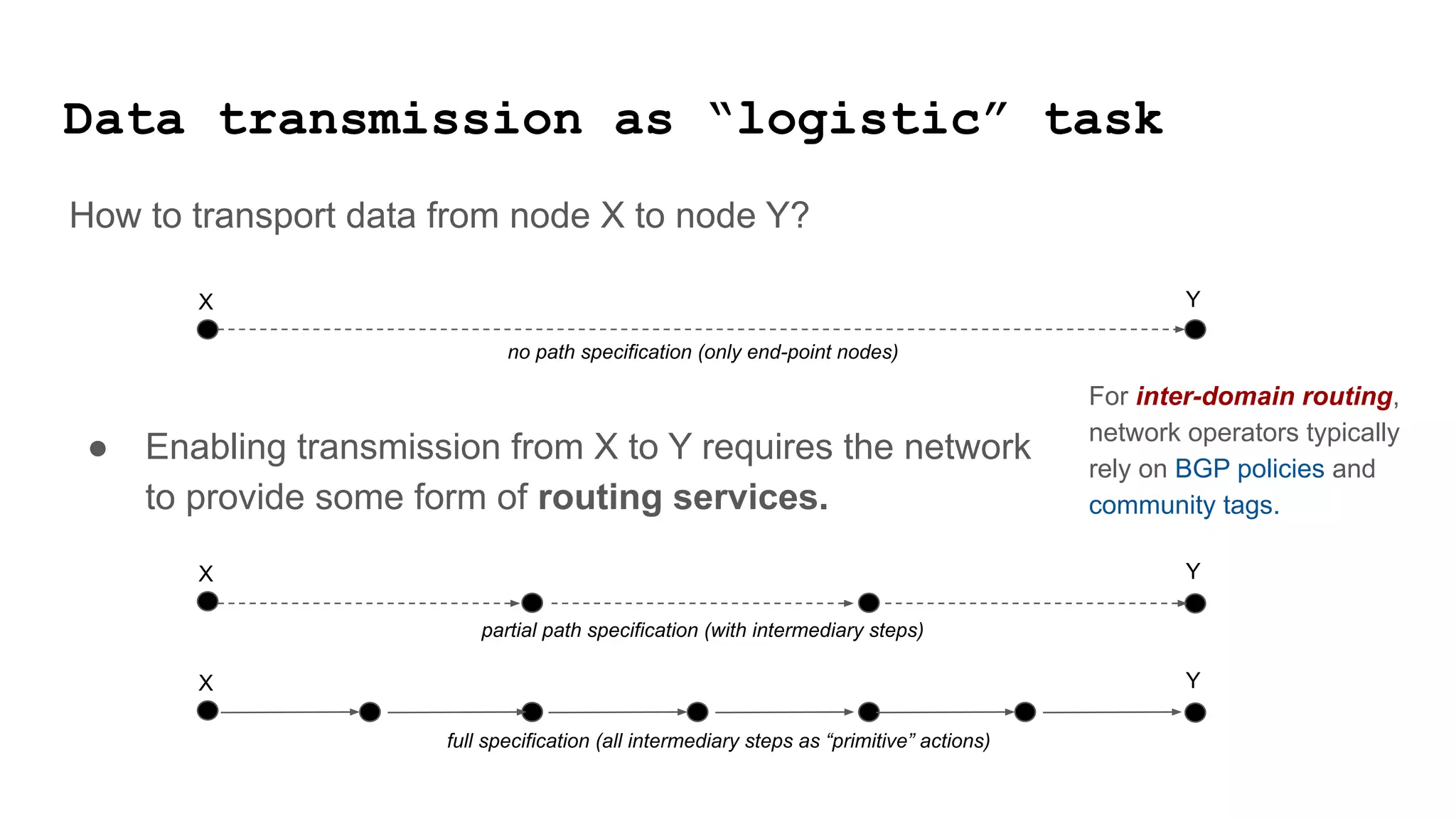
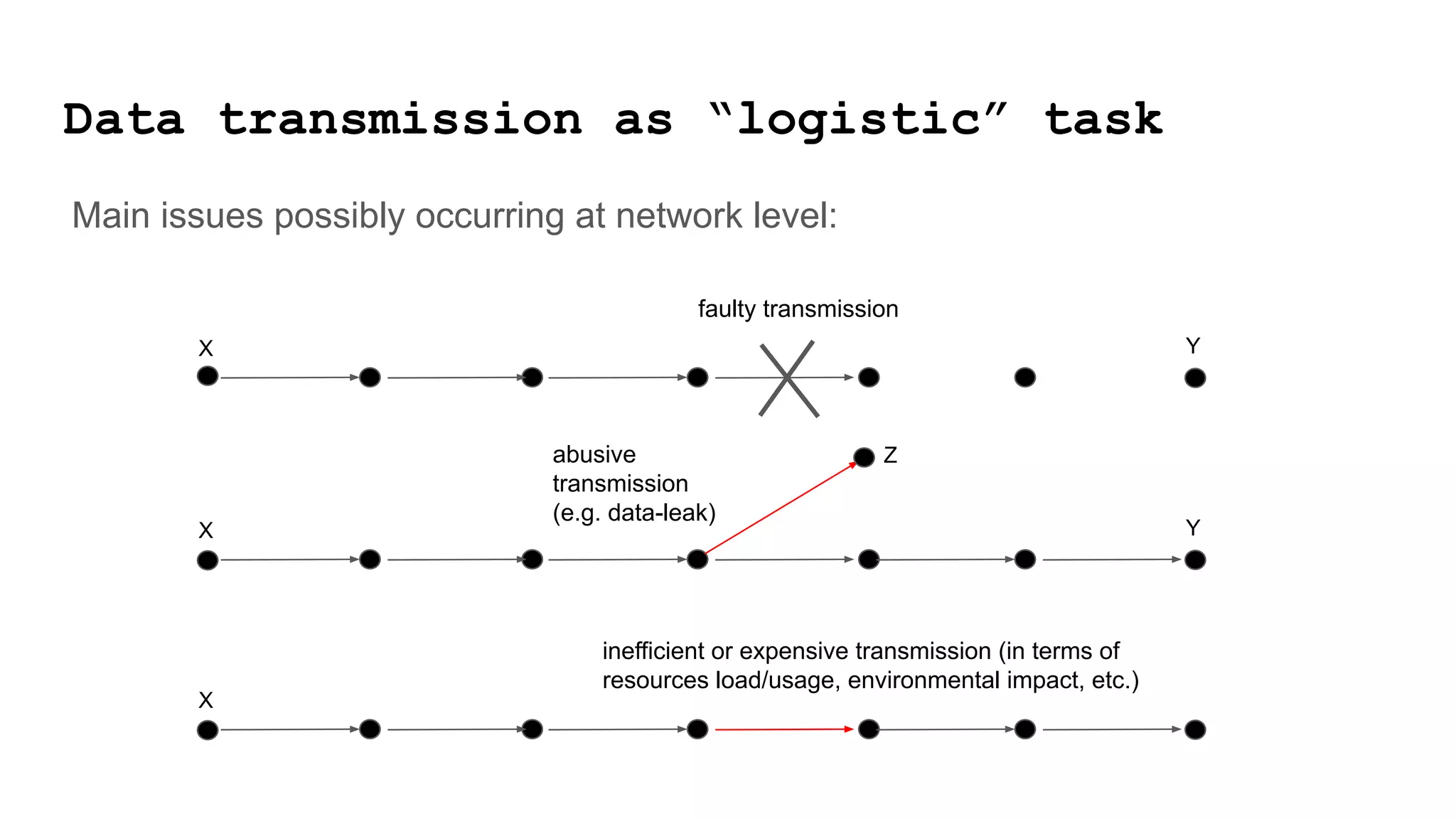
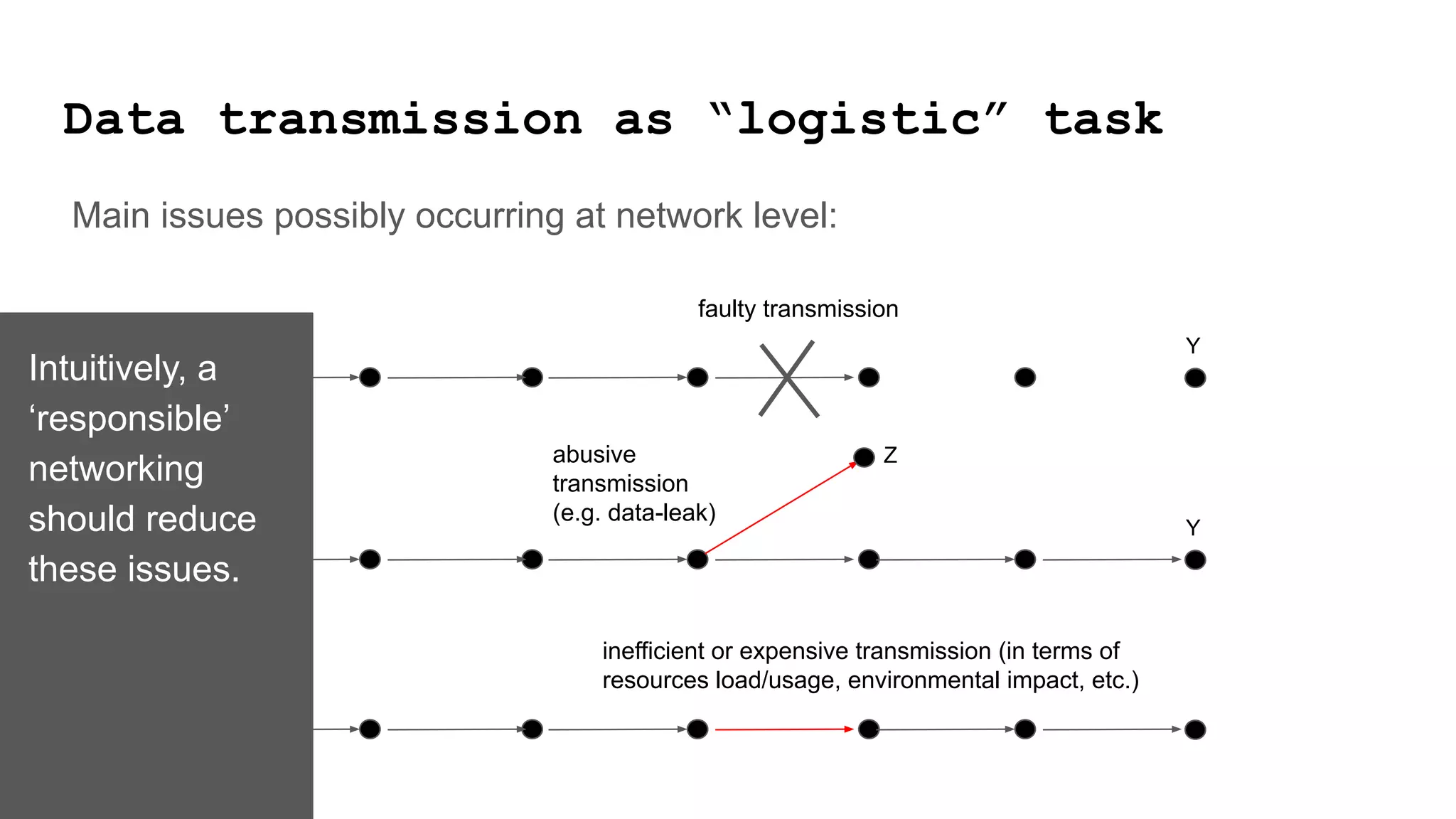
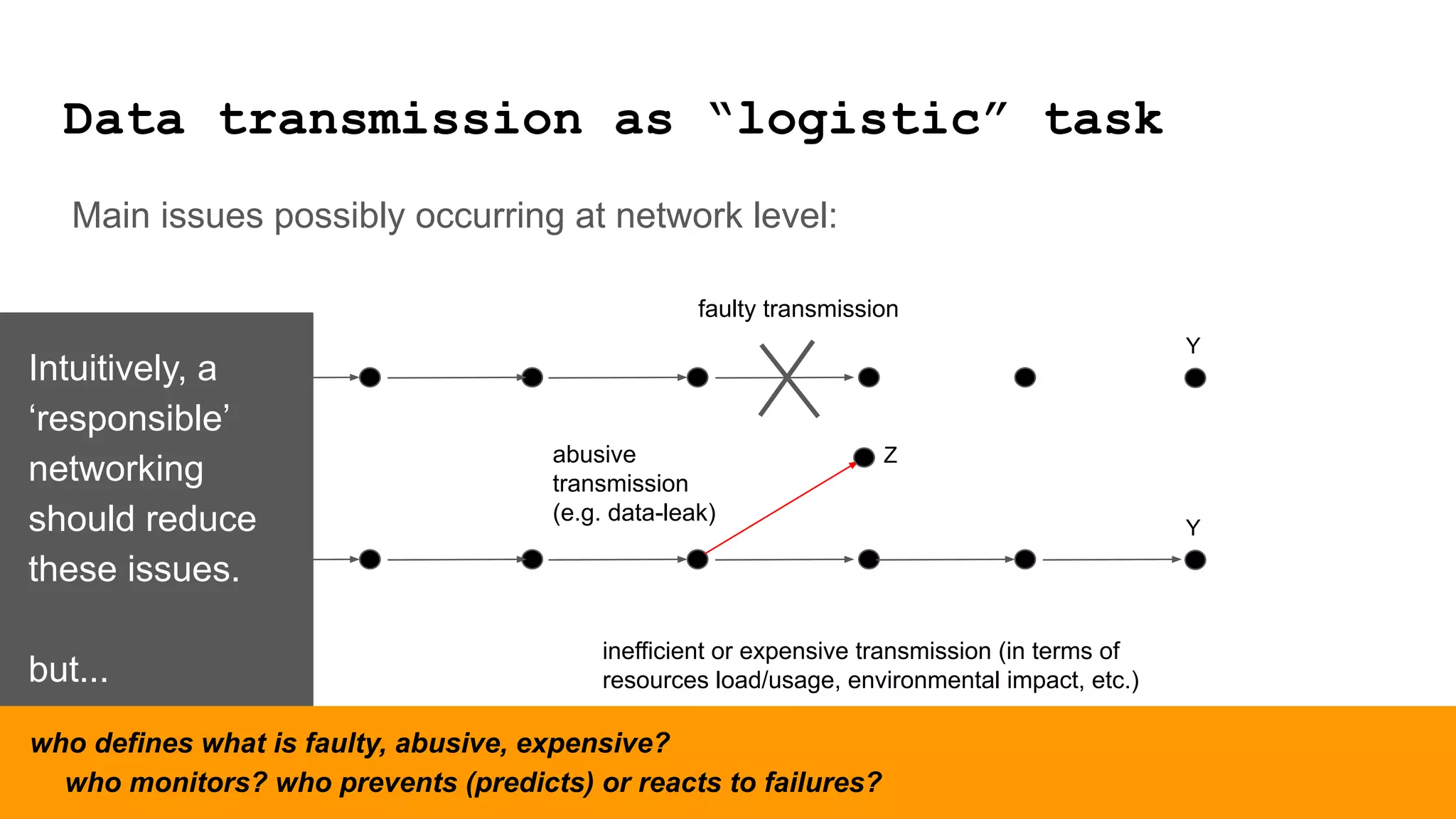
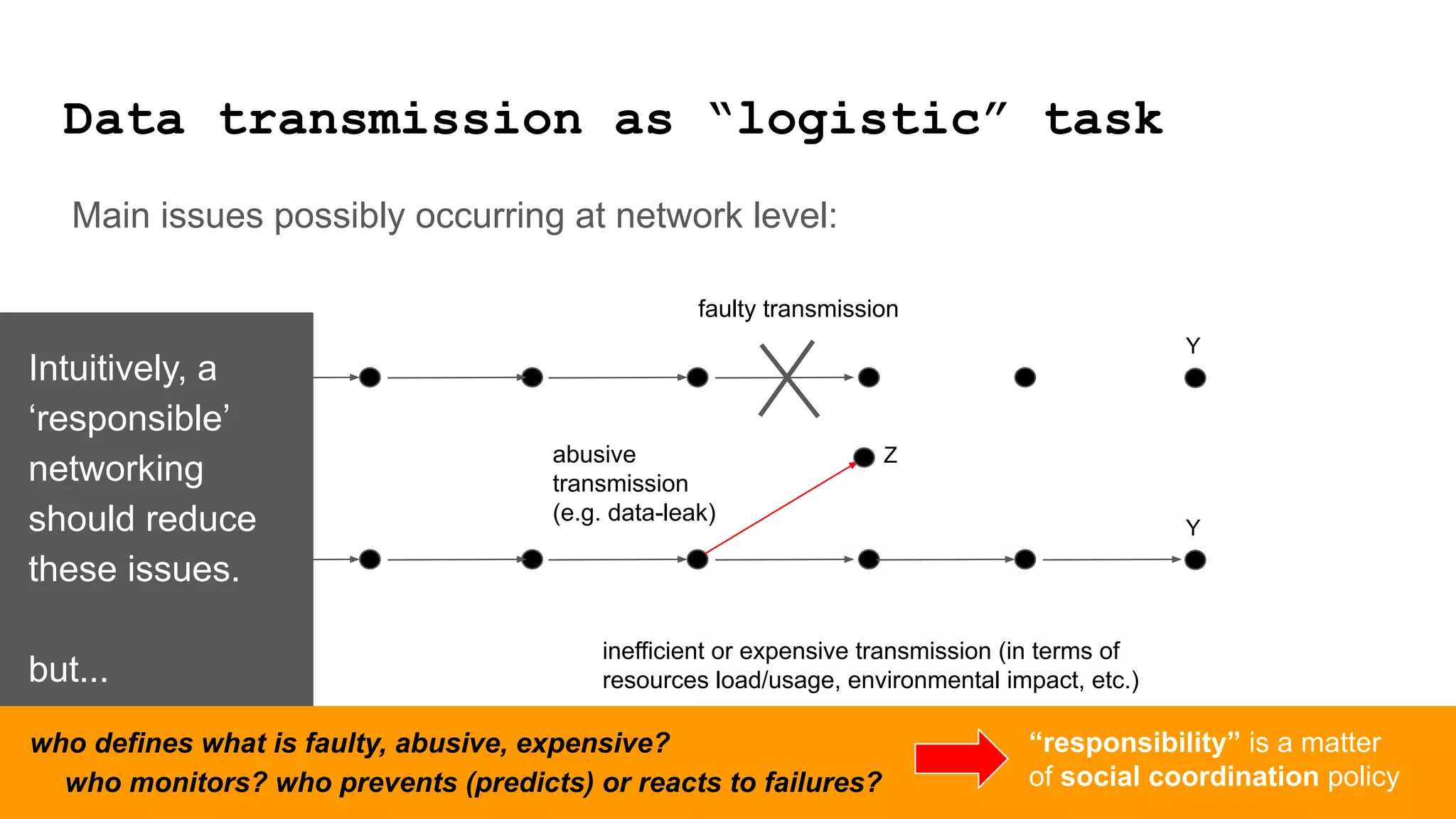
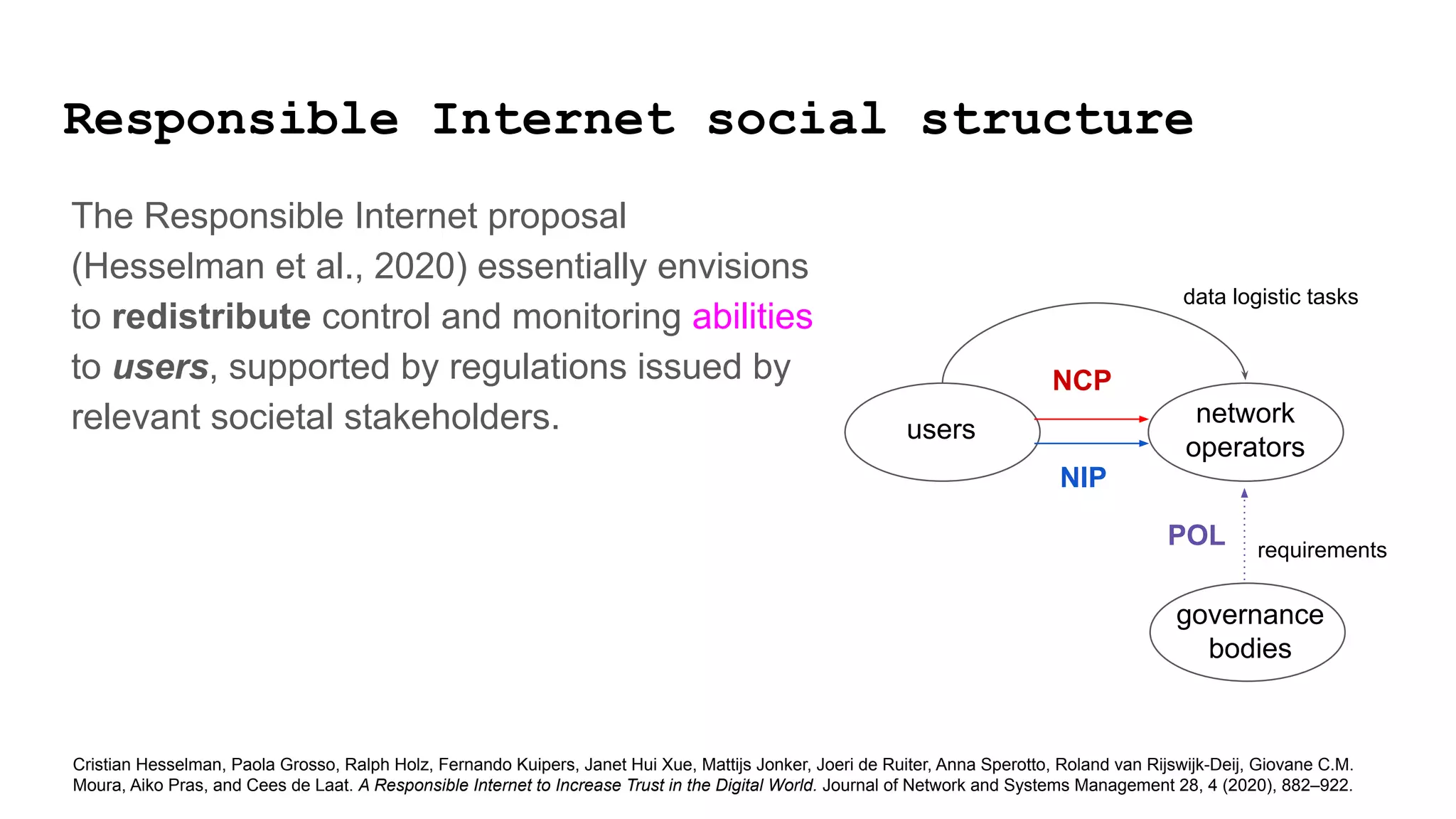
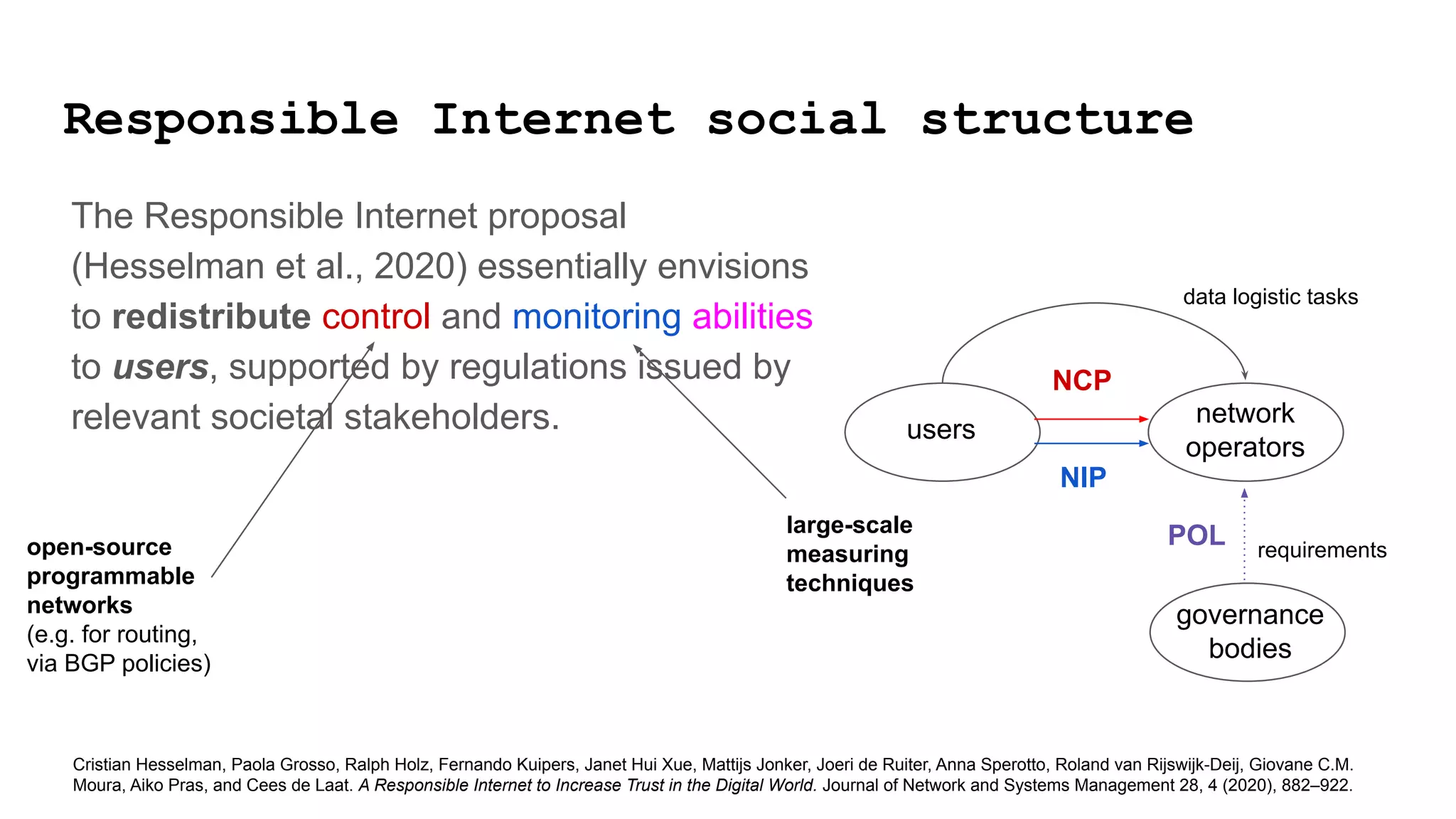
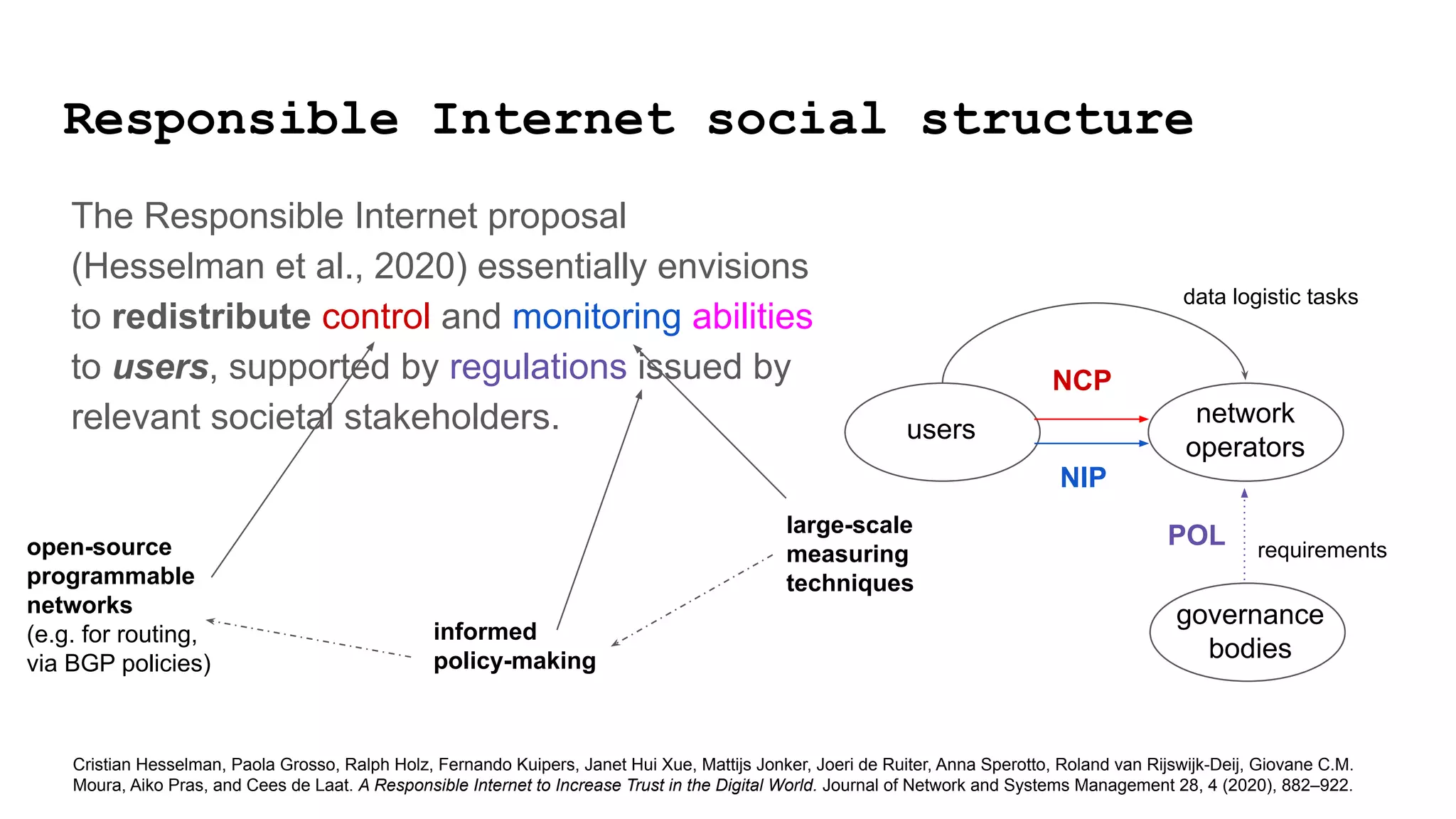
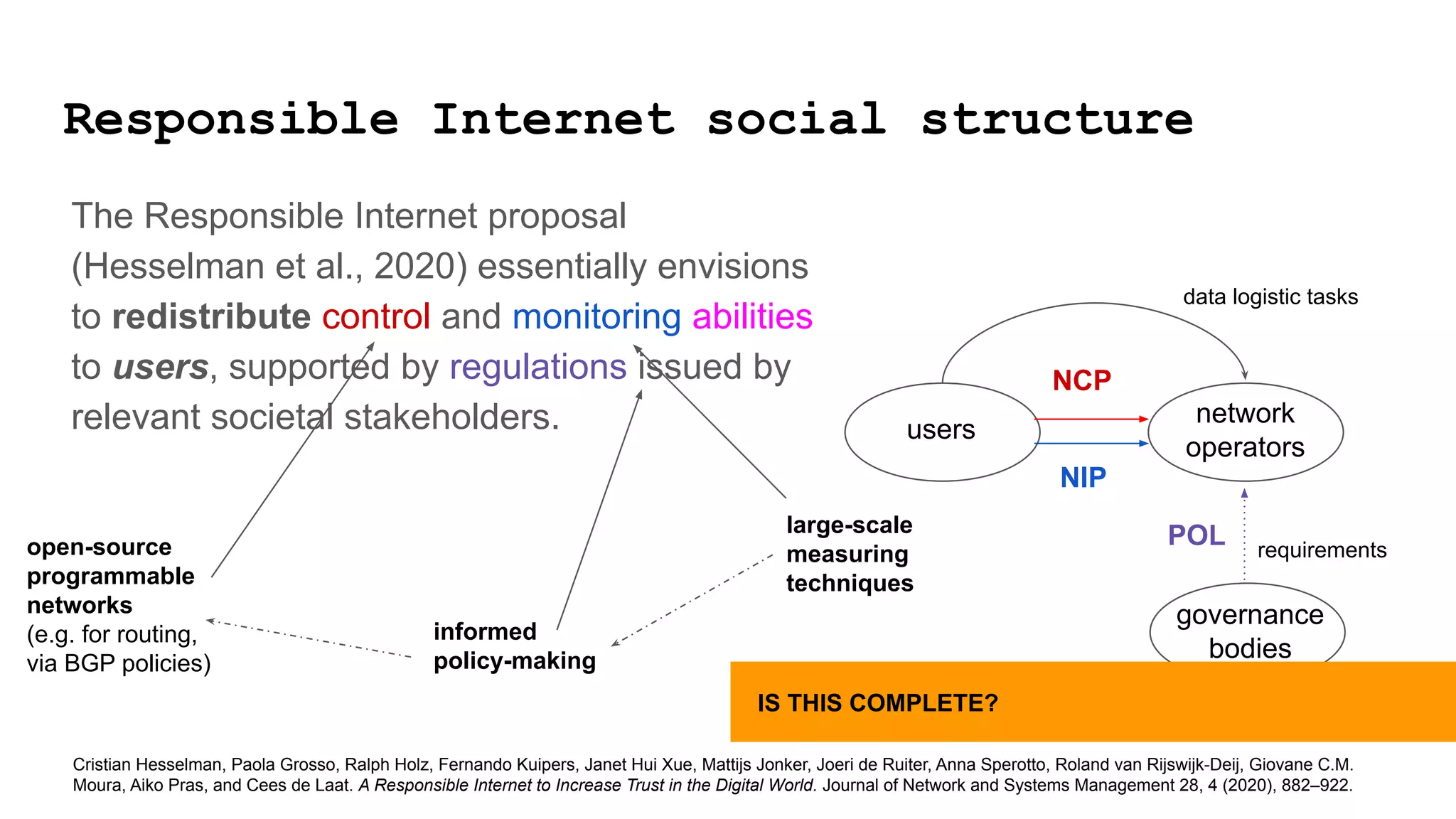
The document discusses approaches to achieving a "responsible internet" through redistributing control and monitoring abilities to users. It identifies two issues with the existing "Responsible Internet" proposal:
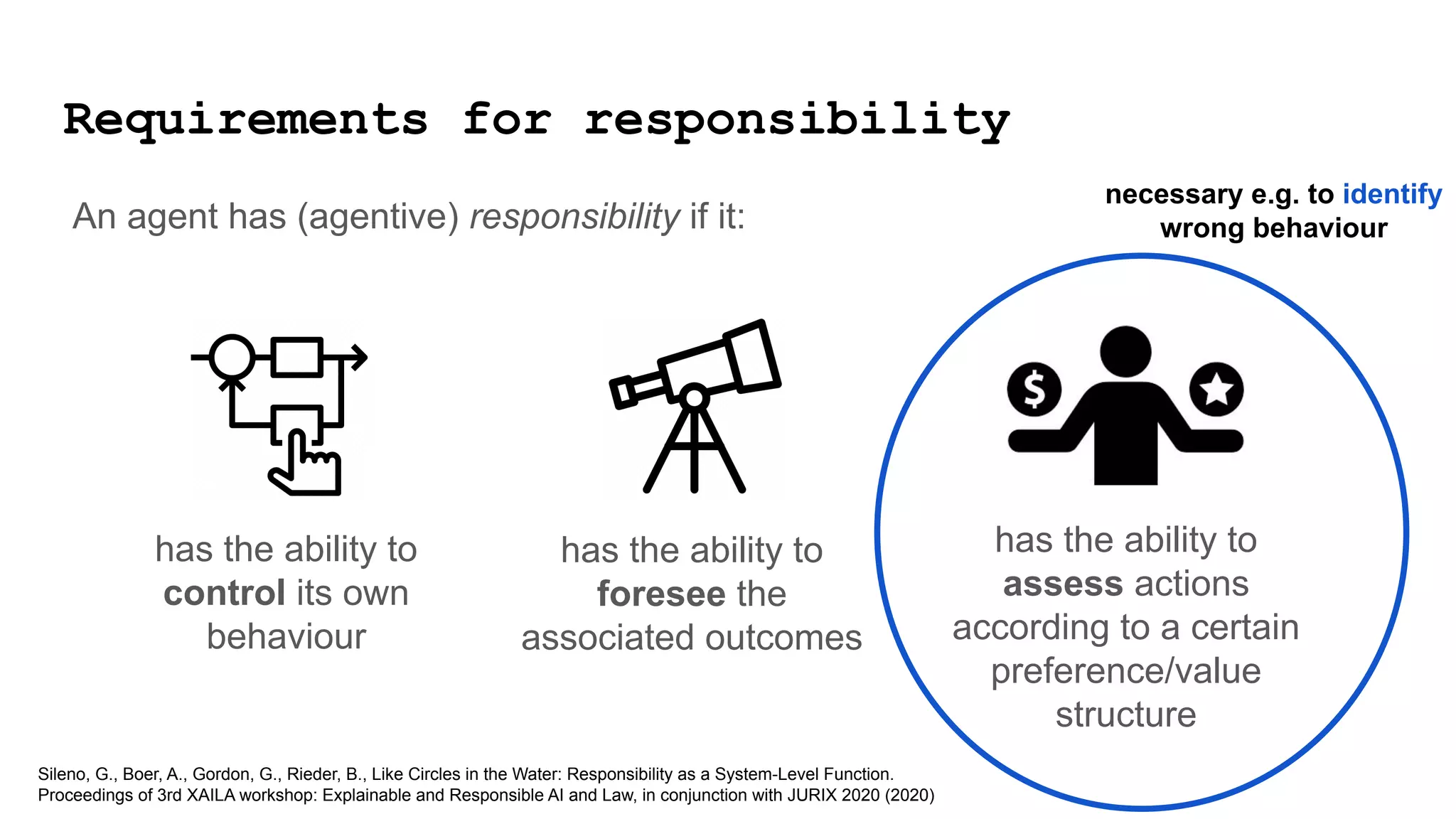
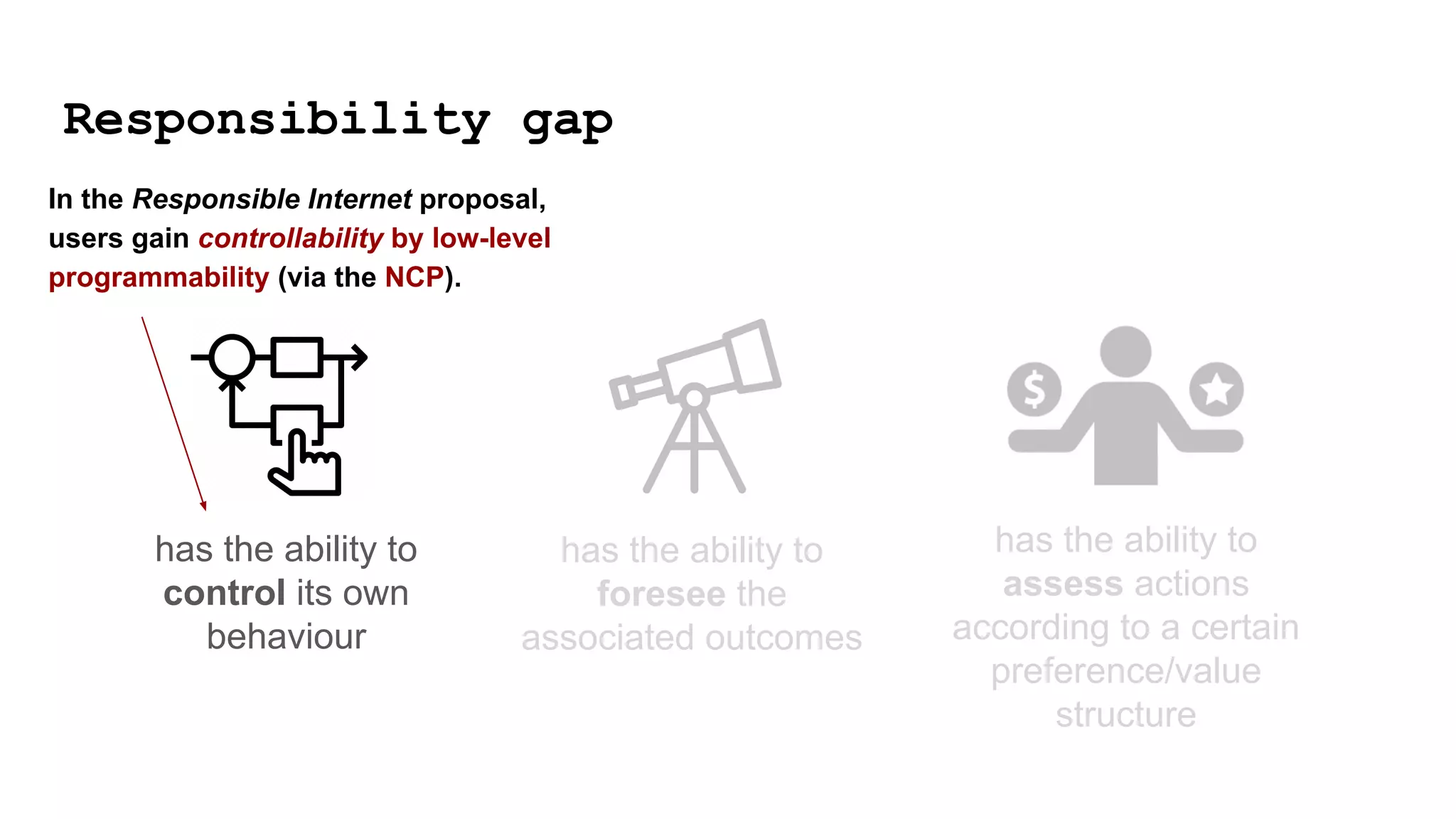
1) A "responsibility gap" exists because low-level programmability for users does not address their ability to foresee outcomes or assess actions according to values.
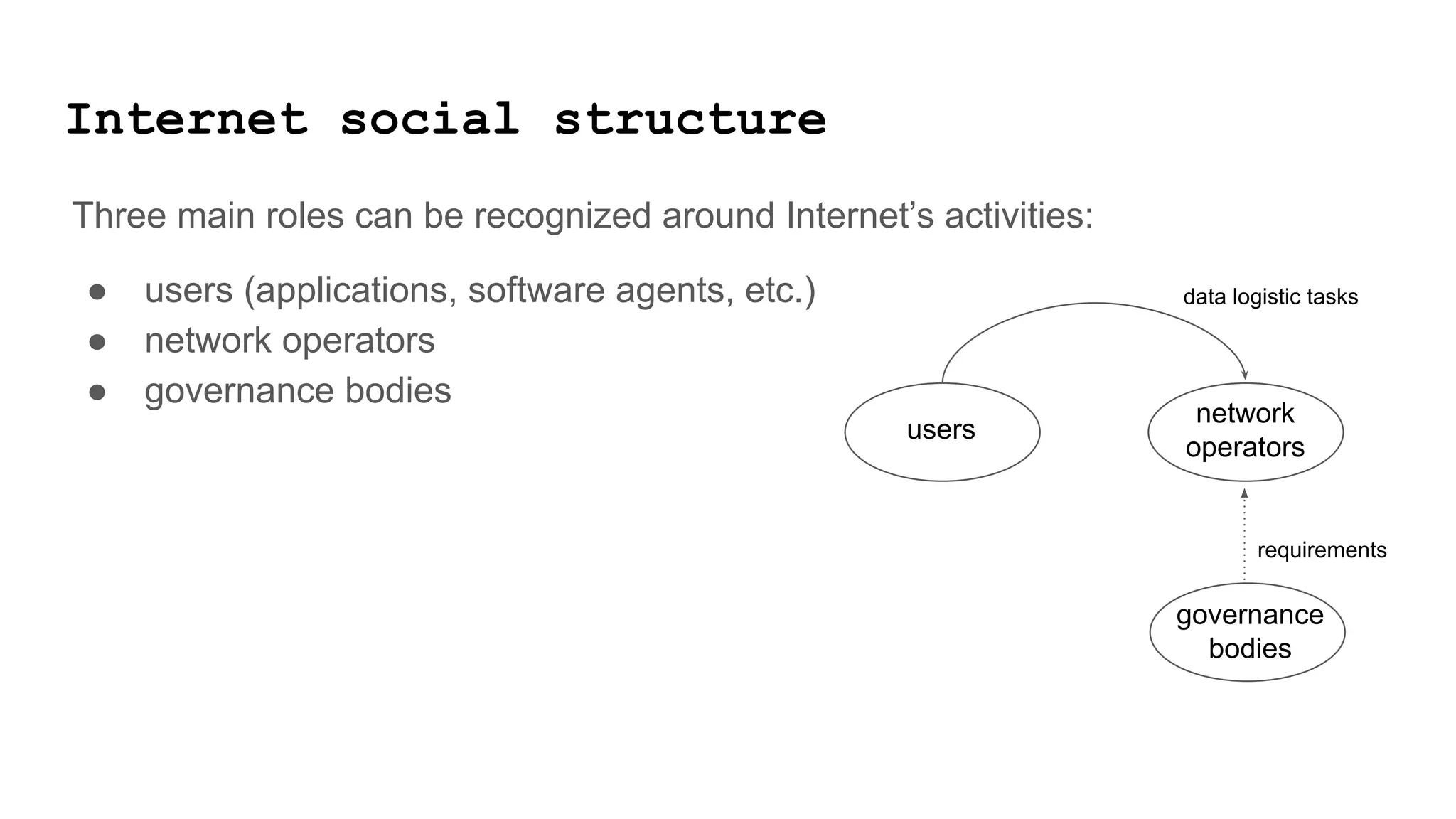
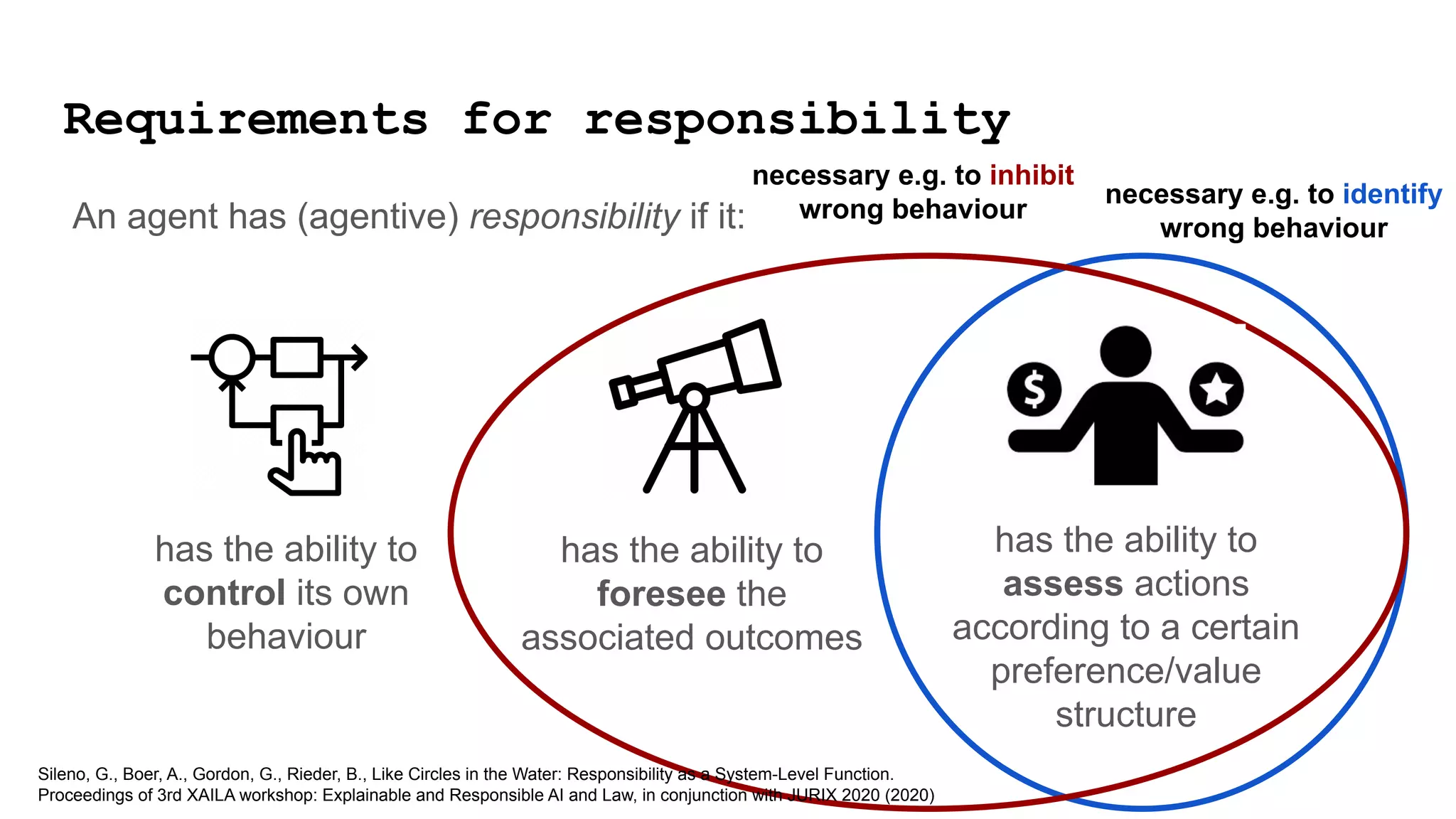
2) The power relationships between users, network operators, and governance bodies are not partially programmable, requiring models of how the world functions and what is valuable, as well as mechanisms for consolidating norms from multiple sources into policies at different levels.





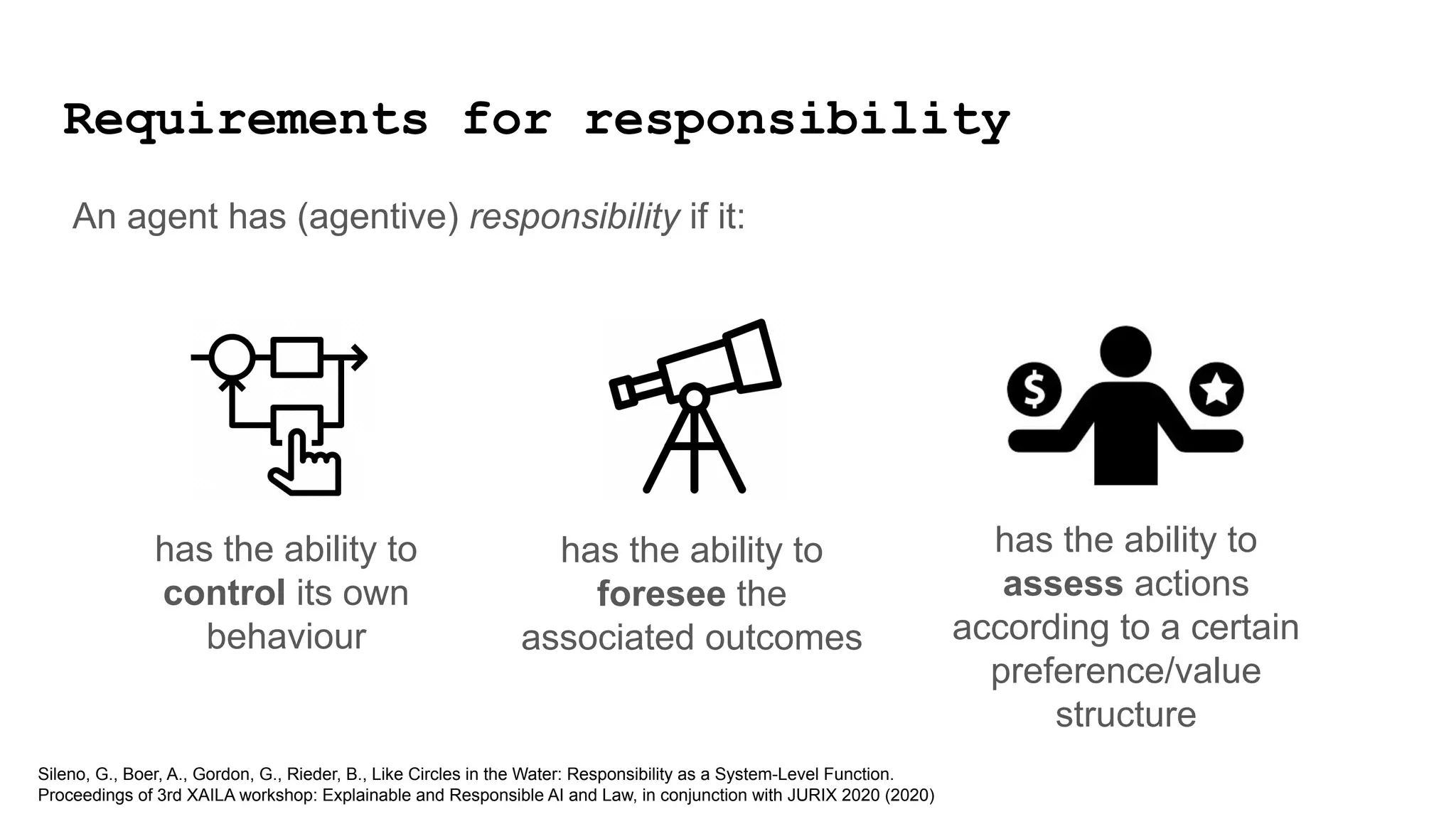
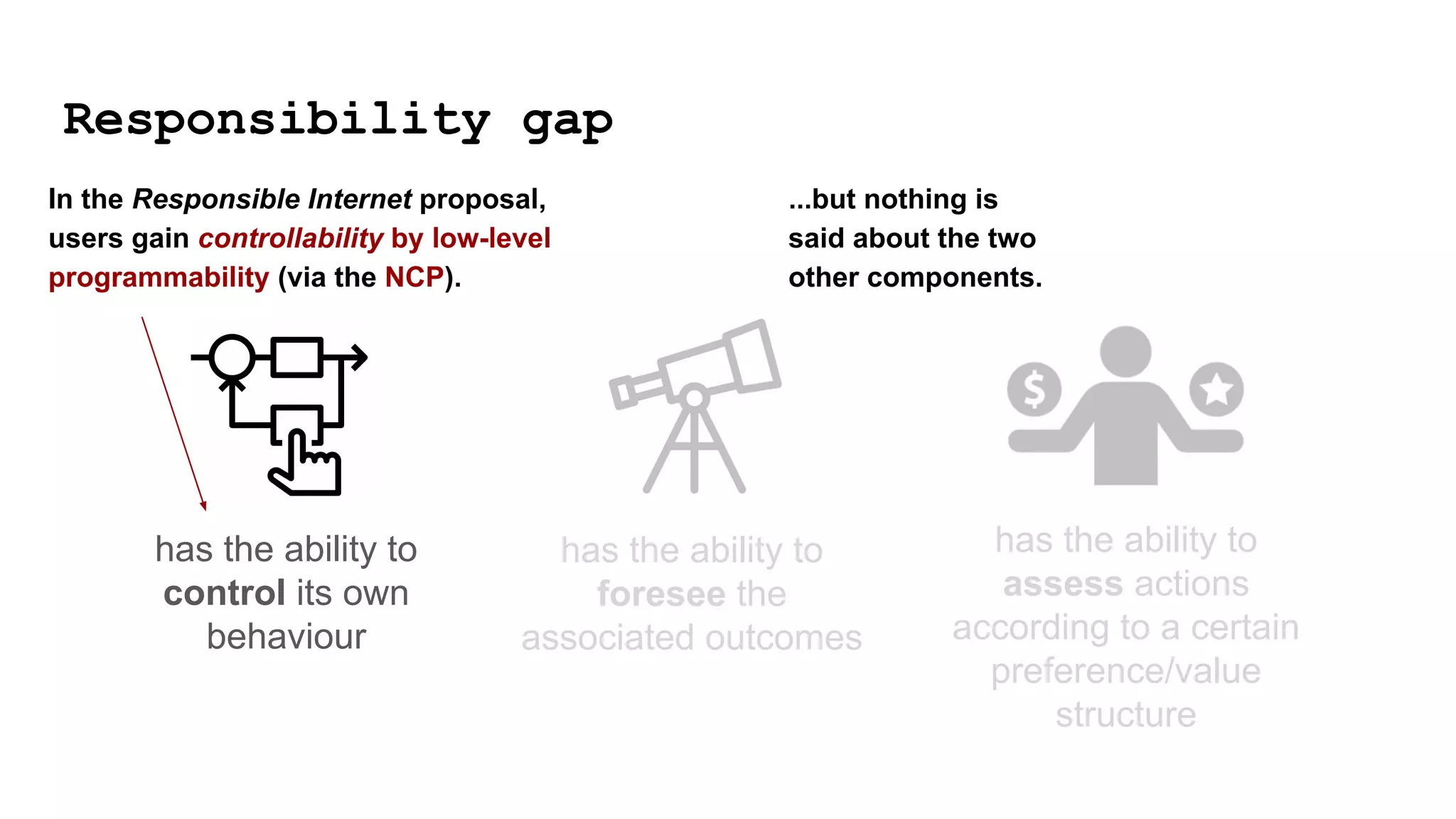
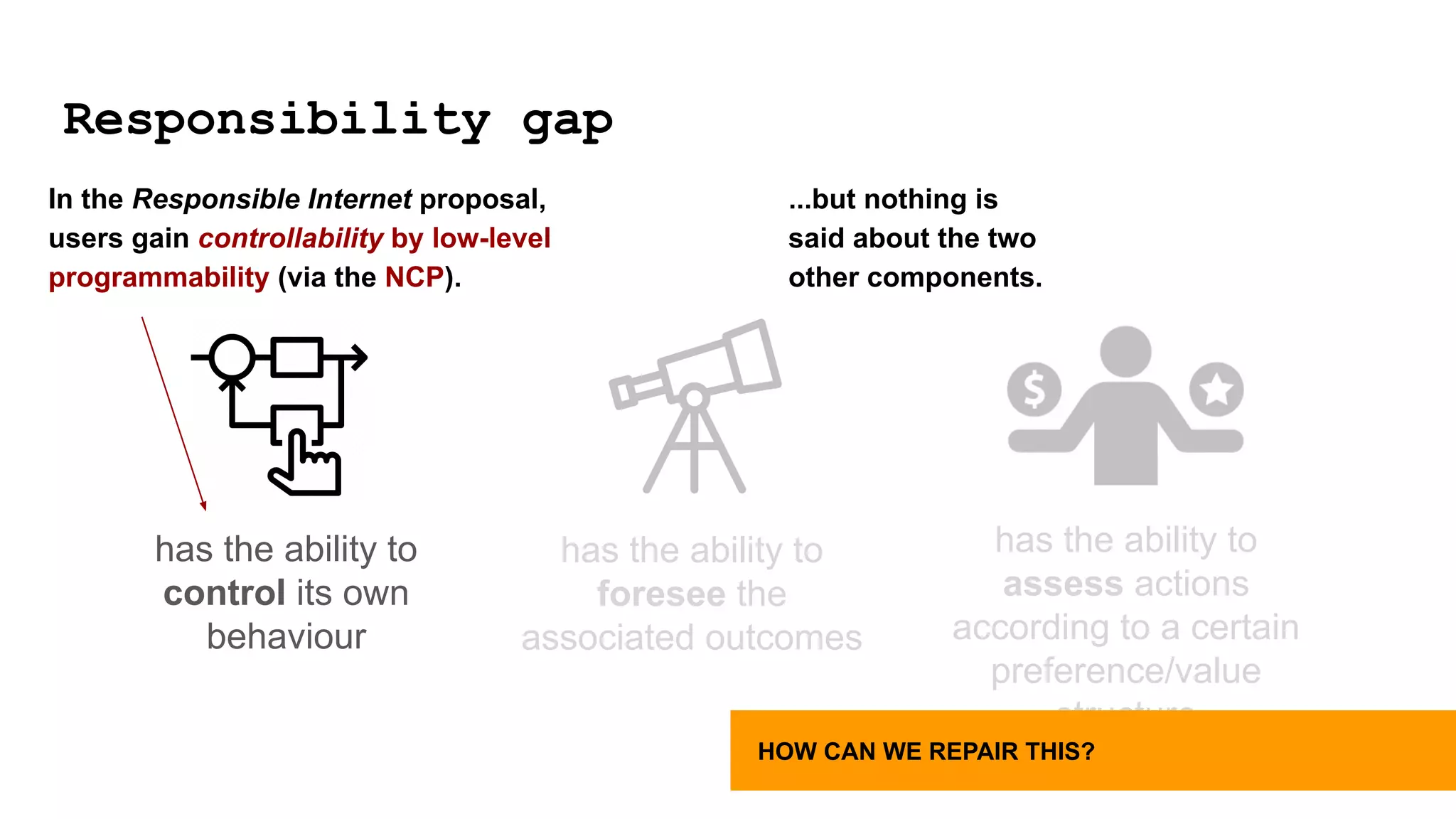
![has the ability to
control its own
behaviour
has the ability to
foresee the
associated outcomes
has the ability to
assess actions
according to a certain
preference/value
structure
[1] We need a model of how
the world functions.
EXPECTATIONS artefact
Reducing the responsibility gap](https://image.slidesharecdn.com/taurin20218-210920214415/75/Accounting-Value-Effects-for-Responsible-Networking-31-2048.jpg)
![has the ability to
control its own
behaviour
has the ability to
foresee the
associated outcomes
has the ability to
assess actions
according to a certain
preference/value
structure
[1] We need a model of how
the world functions.
EXPECTATIONS artefact
[2] We need a model of what is
valuable in the world.
high-level POLICY artefact
Reducing the responsibility gap](https://image.slidesharecdn.com/taurin20218-210920214415/75/Accounting-Value-Effects-for-Responsible-Networking-32-2048.jpg)
![Reducing the responsibility gap
has the ability to
control its own
behaviour
has the ability to
foresee the
associated outcomes
has the ability to
assess actions
according to a certain
preference/value
structure
[1] We need a model of how
the world functions.
EXPECTATIONS artefact
[2] We need a model of what is
valuable in the world.
high-level POLICY artefact
norm as in
normal
norm as in
normative](https://image.slidesharecdn.com/taurin20218-210920214415/75/Accounting-Value-Effects-for-Responsible-Networking-33-2048.jpg)
![Reducing the responsibility gap
has the ability to
control its own
behaviour
has the ability to
foresee the
associated outcomes
has the ability to
assess actions
according to a certain
preference/value
structure
[1] We need a model of how
the world functions.
EXPECTATIONS artefact(s)
[2] We need a model of what is
valuable in the world.
high-level POLICY artefact(s)
norm as in
normal
norm as in
normative
norm pluralism
[3] We need to take into account
several external sources of norms](https://image.slidesharecdn.com/taurin20218-210920214415/75/Accounting-Value-Effects-for-Responsible-Networking-34-2048.jpg)
![Reducing the responsibility gap
has the ability to
control its own
behaviour
has the ability to
foresee the
associated outcomes
has the ability to
assess actions
according to a certain
preference/value
structure
[1] We need a model of how
the world functions.
EXPECTATIONS artefact(s)
[2] We need a model of what is
valuable in the world.
high-level POLICY artefact(s)
norm as in
normal
norm as in
normative
[3] We need to take into account
several external sources of norms
need for “normware” technology
norm pluralism](https://image.slidesharecdn.com/taurin20218-210920214415/75/Accounting-Value-Effects-for-Responsible-Networking-35-2048.jpg)