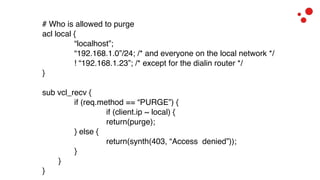
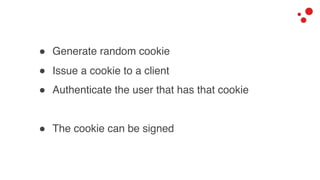
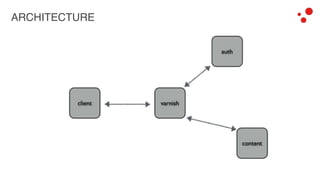
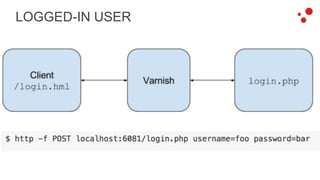
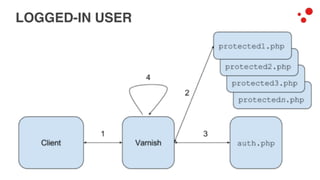
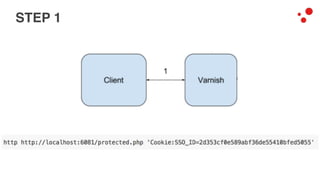
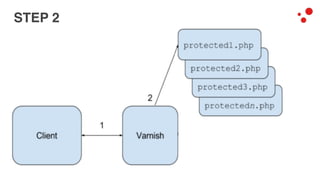
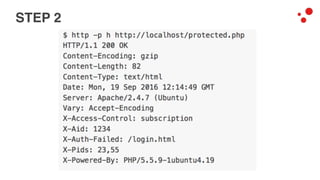
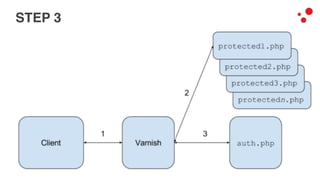
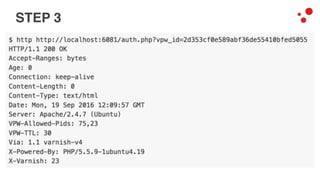
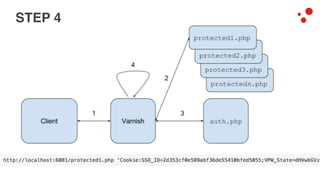
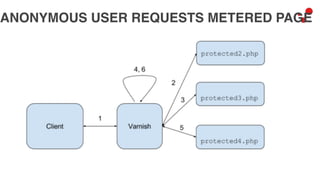
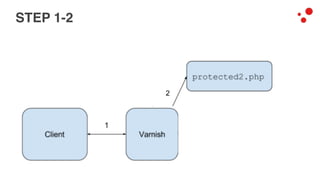
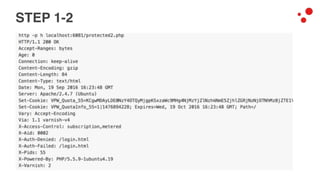
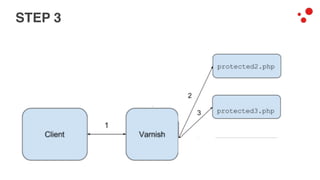
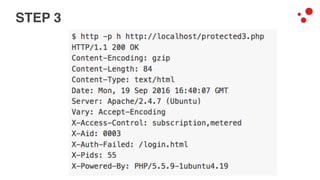
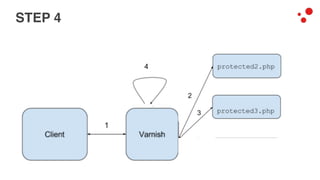
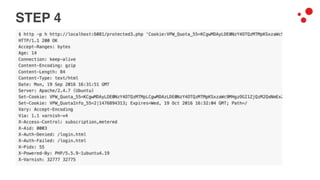
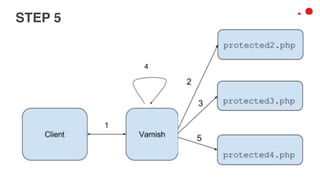
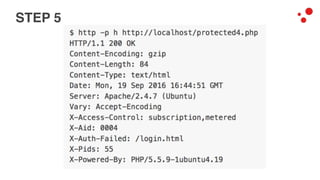
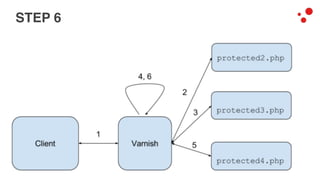
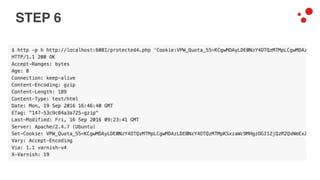
This document discusses different access control methods for purging content in Varnish, including IP-based access control, basic authentication, and cookie-based access control. It argues that cookie-based access control provides the optimal solution, describing how to generate and authenticate random cookies signed with a secret key to control access. The document then outlines how this approach is used to build a "Varnish auth tool kit" or "VARNISH PAYWALL" system for metered or subscription-based access control of content.