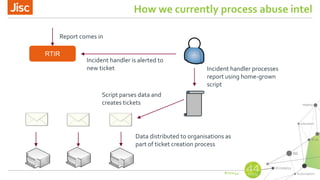
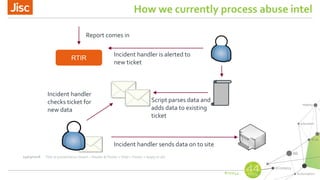
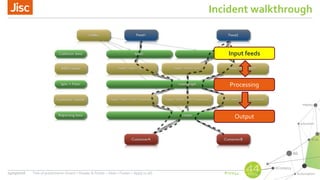
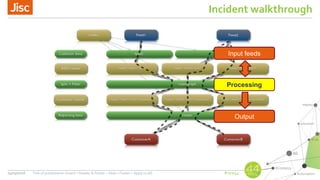
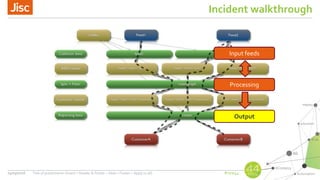
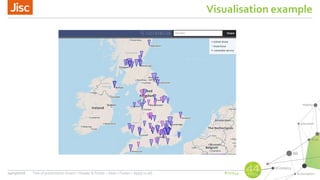
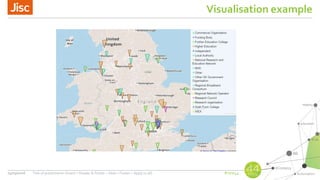
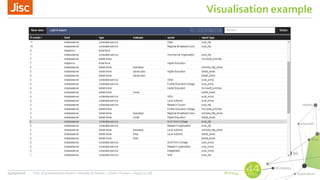
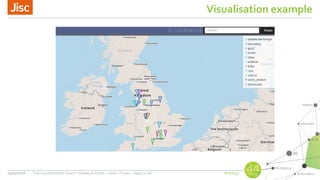
AbuseHelper is a tool that automates the collection, processing, and reporting of abuse data to help organizations secure their networks. It ingests data from various feeds, processes it by augmenting, sanitizing, de-duplicating, filtering, and adding additional data. It then distributes actionable reports to customers through various outputs like email and security systems. This improves over manual processes by providing faster processing, timely reporting of only relevant data, and clear communication needs for responses. It also provides situational awareness through data visualization.