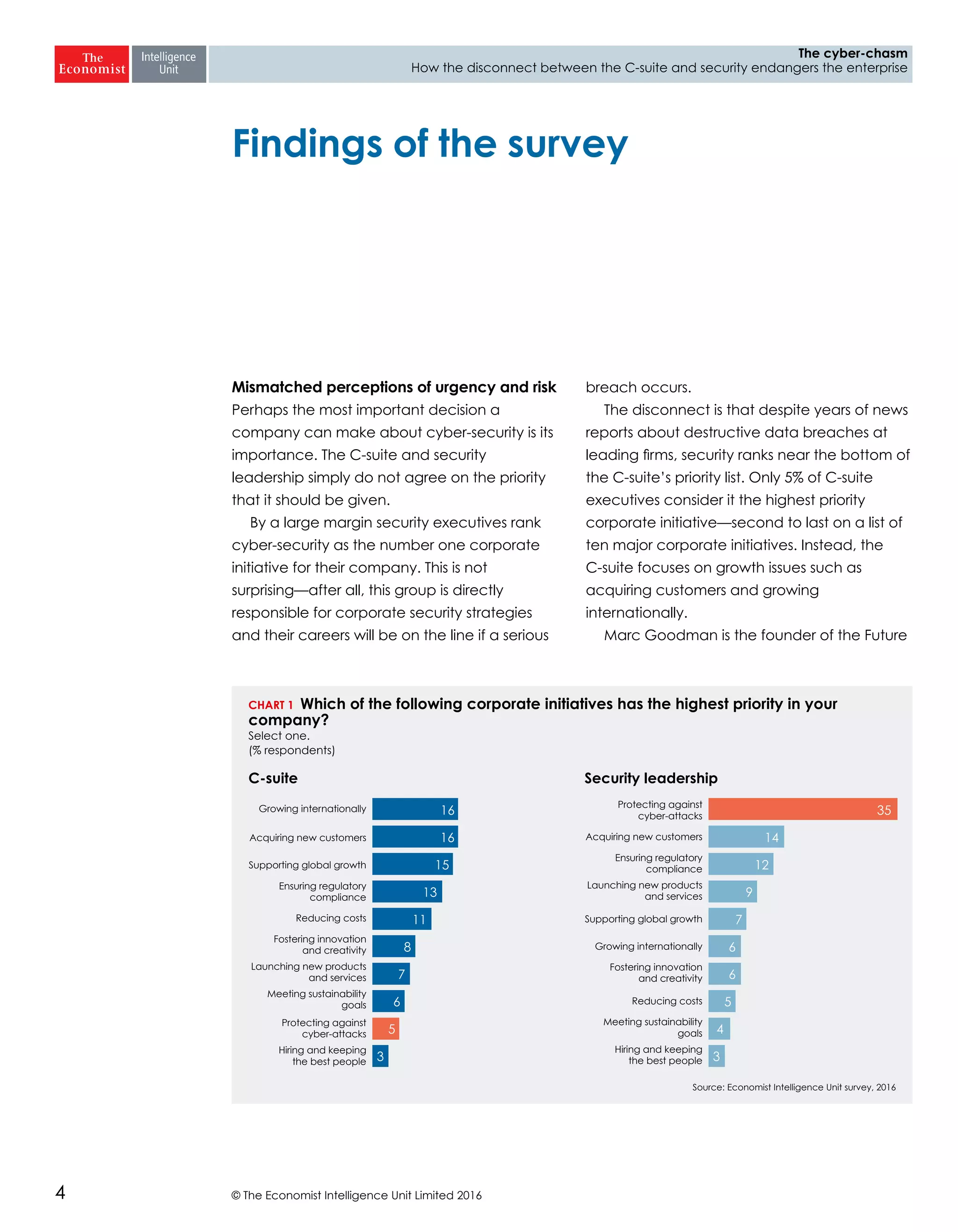
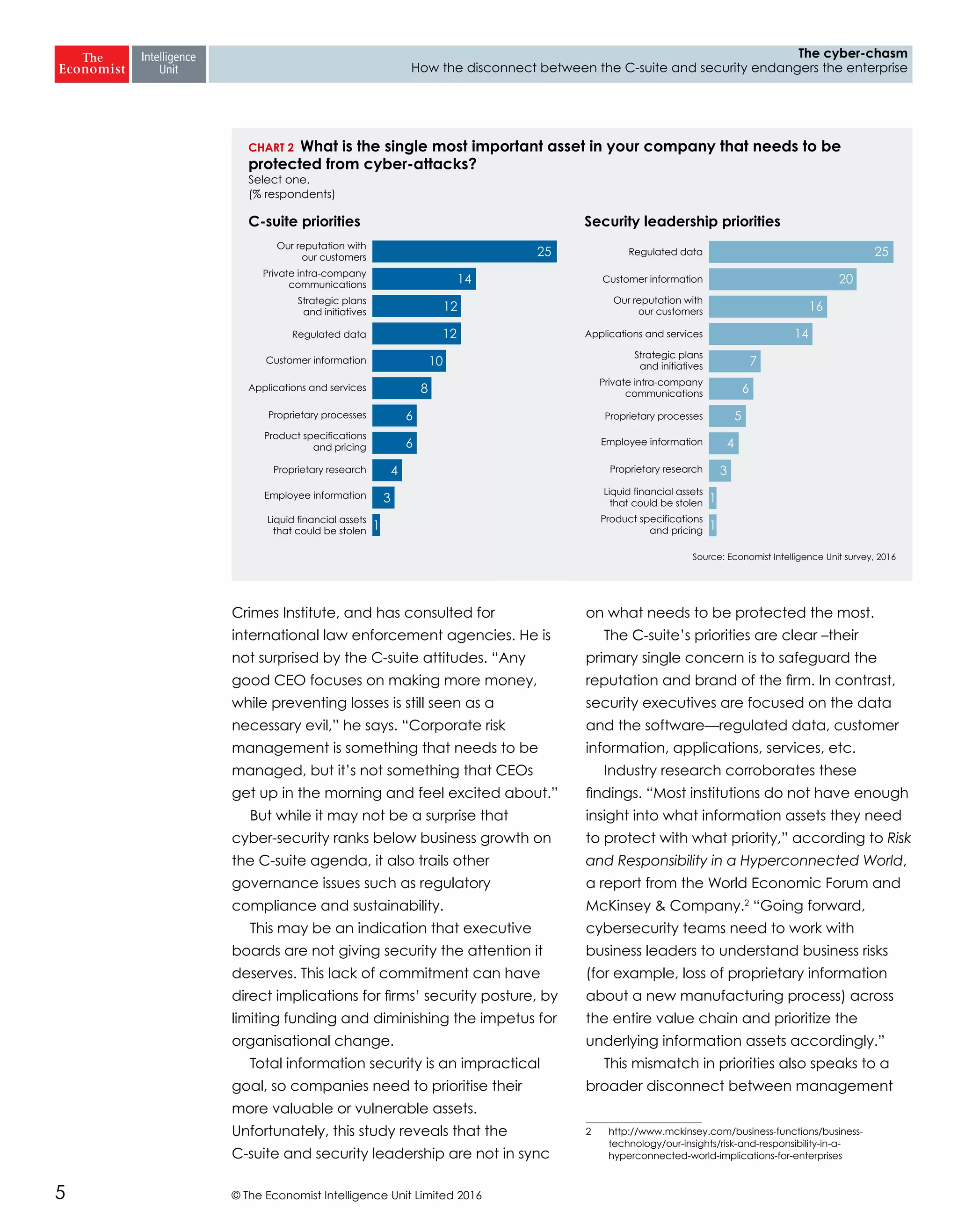
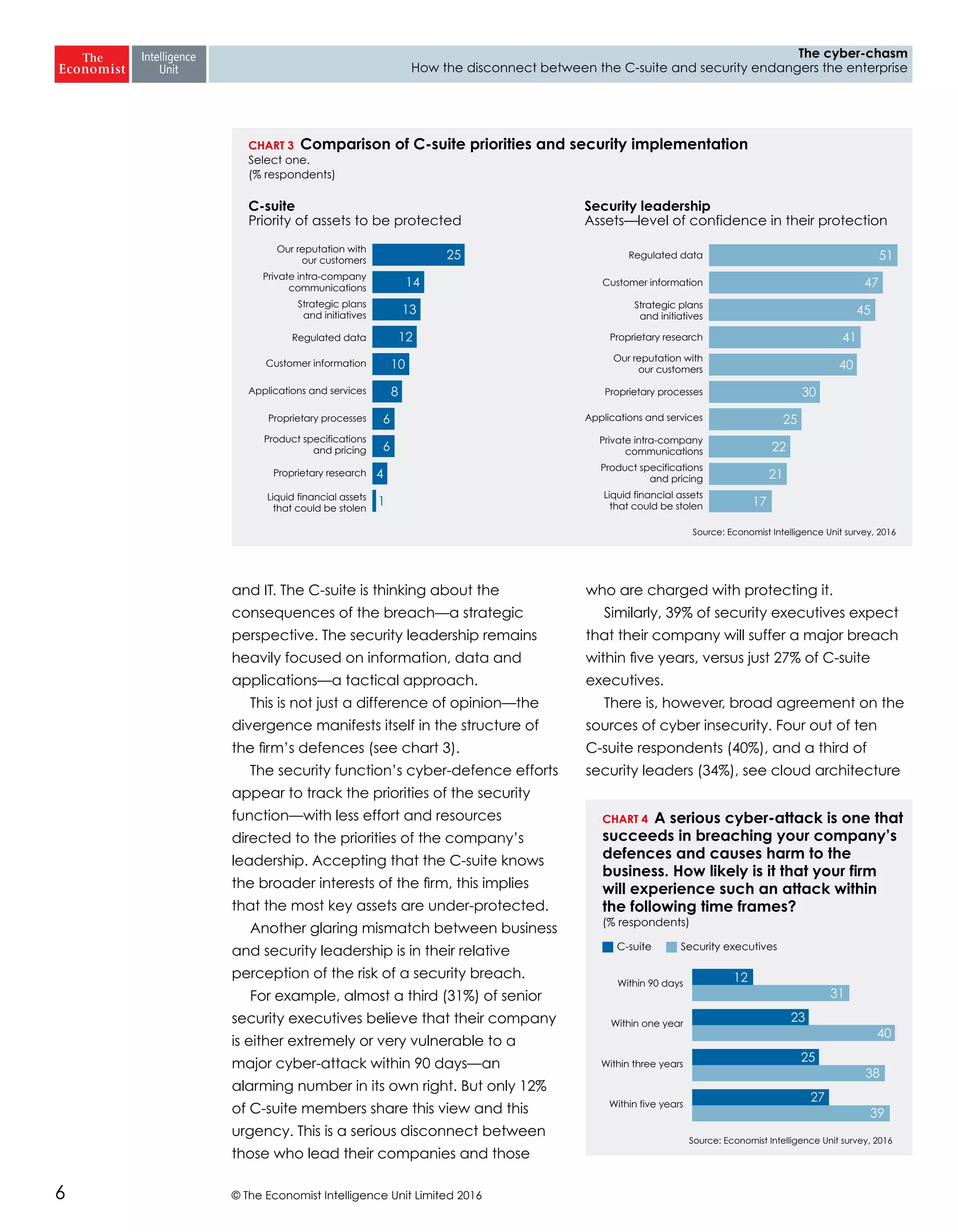
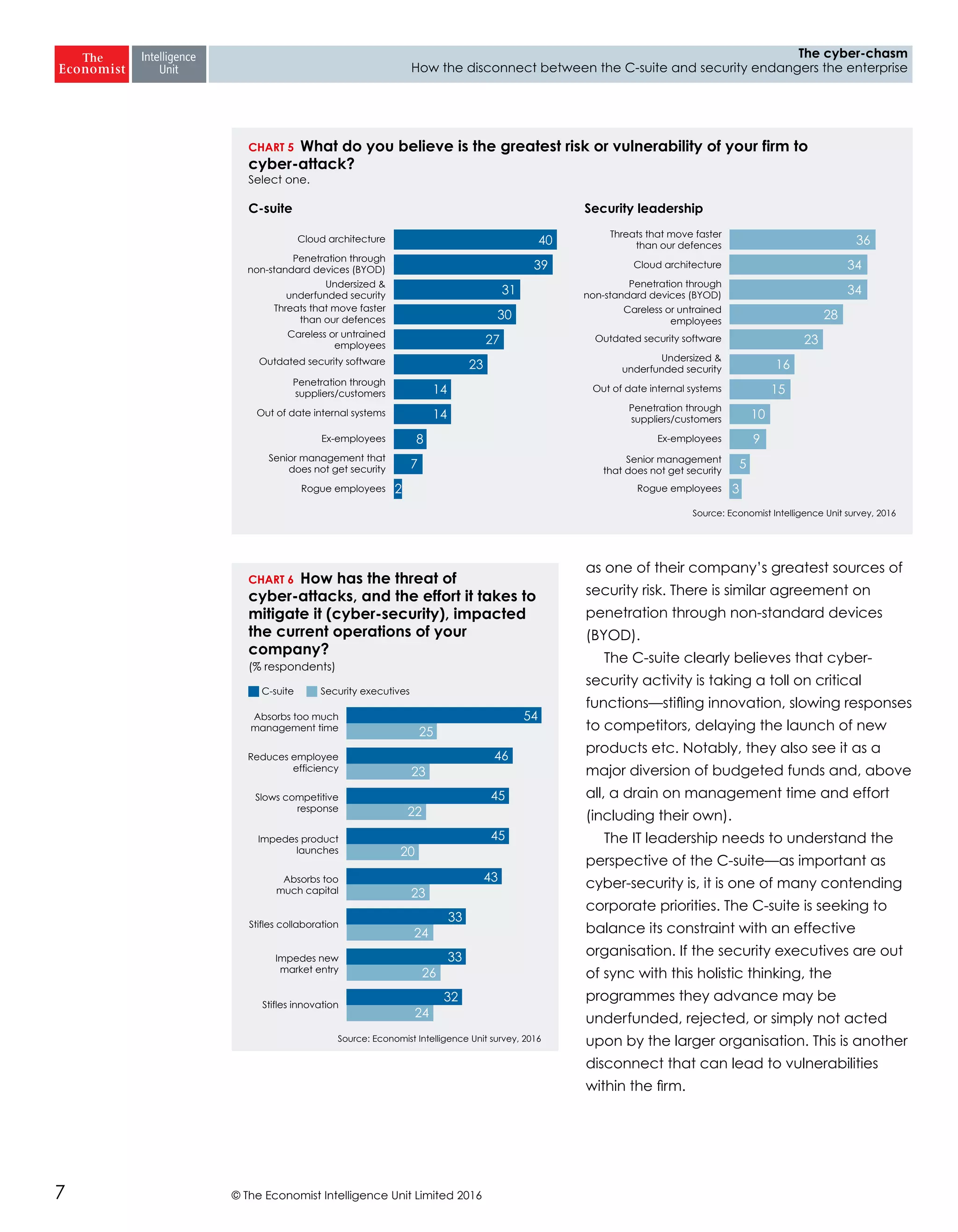
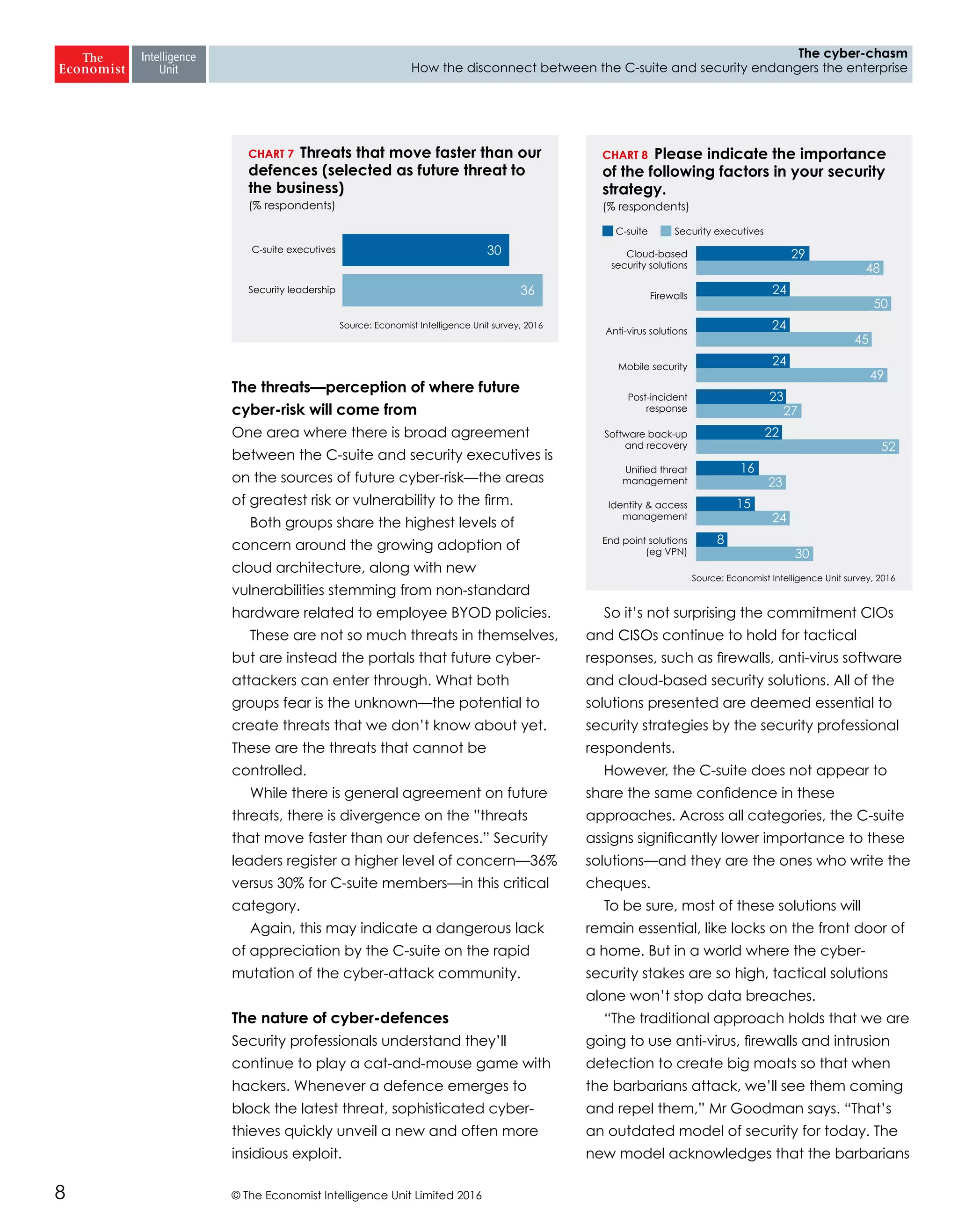
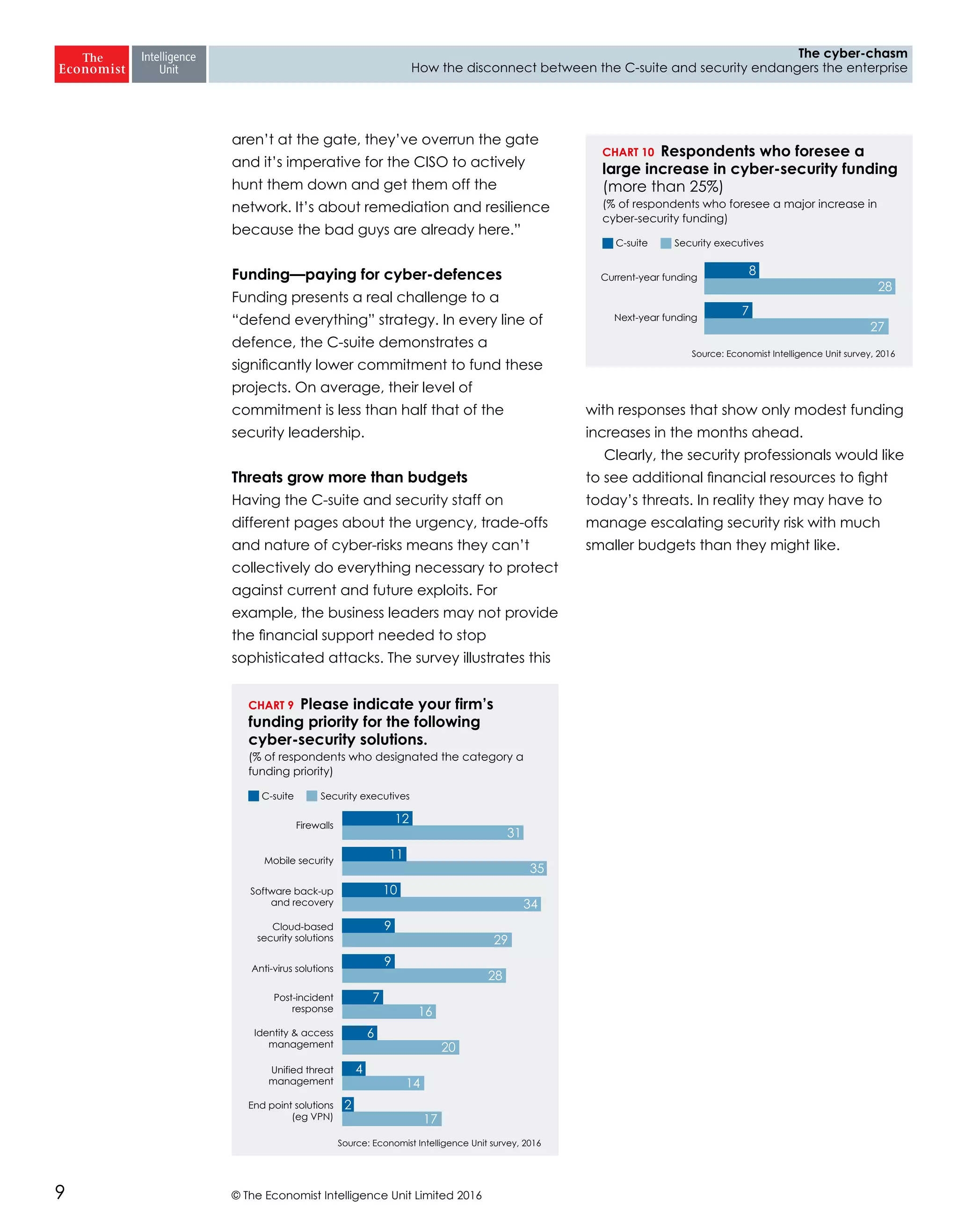
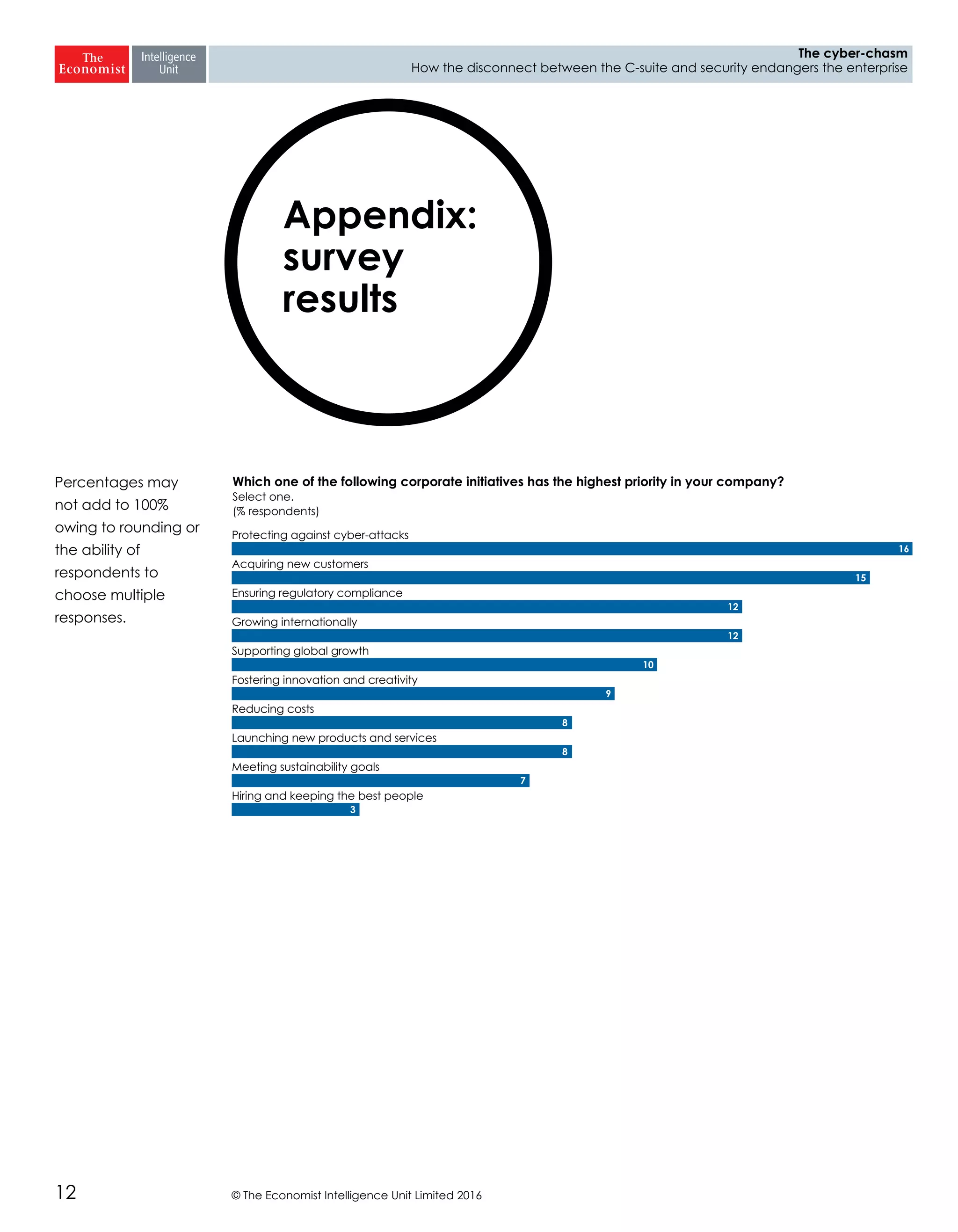
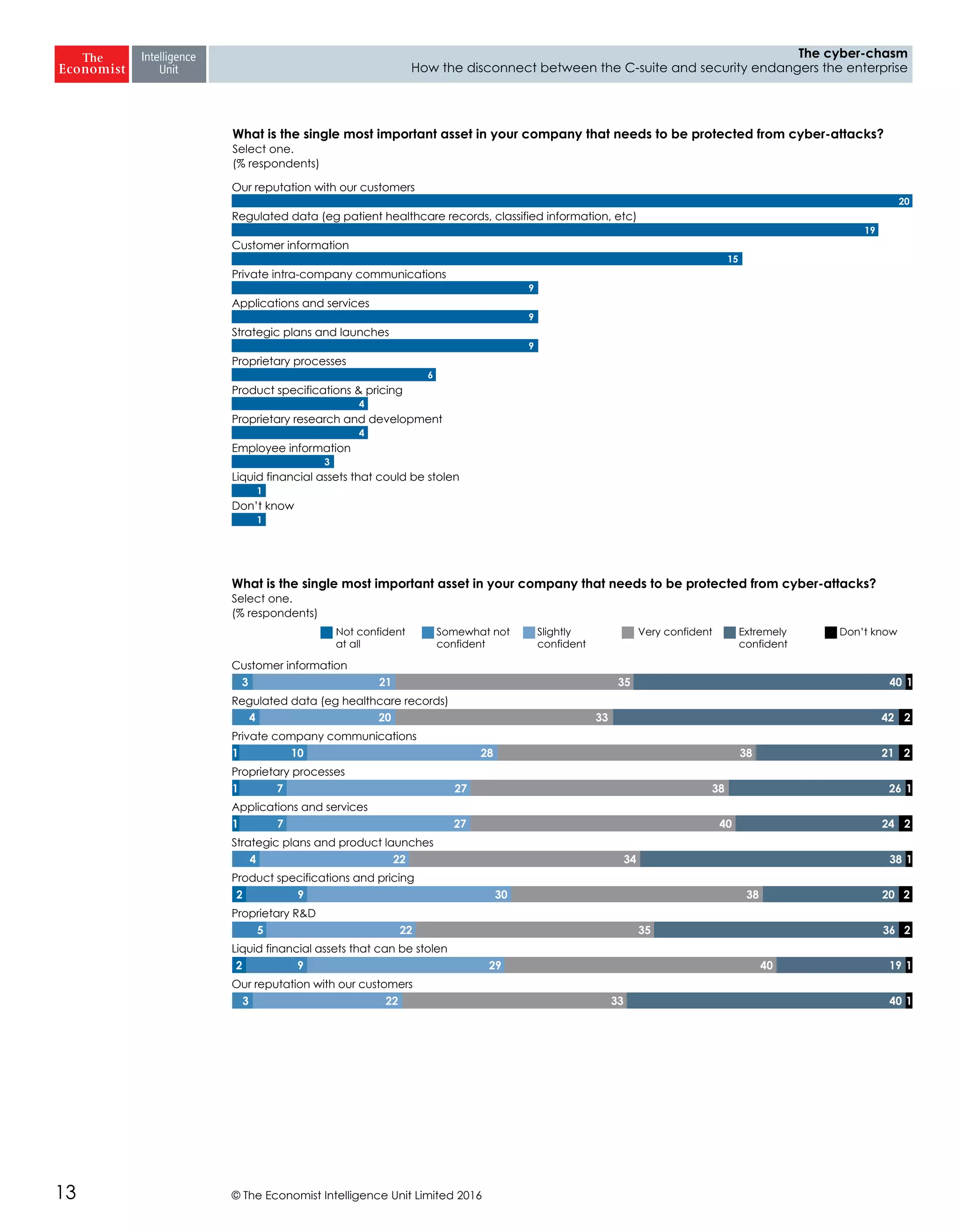
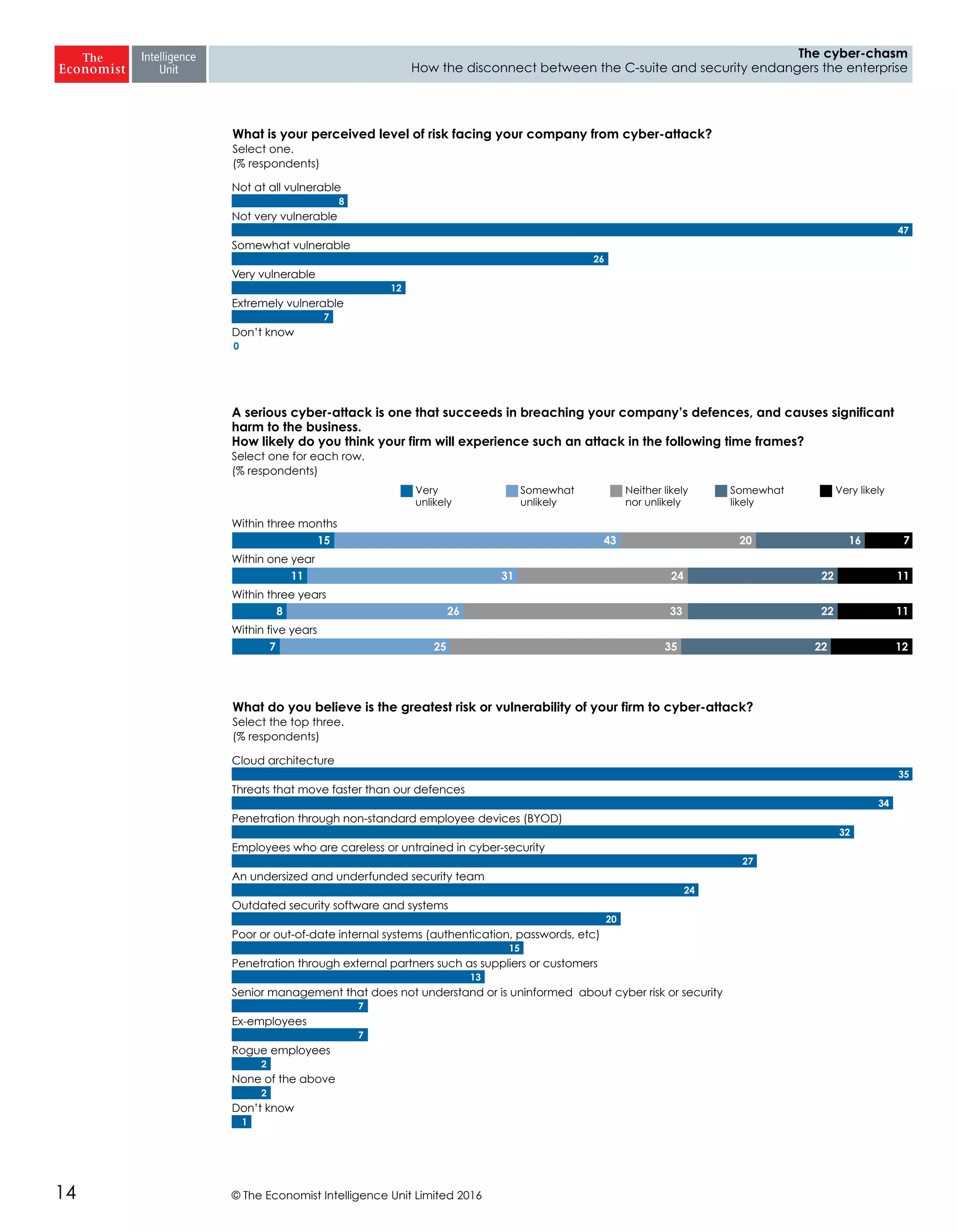
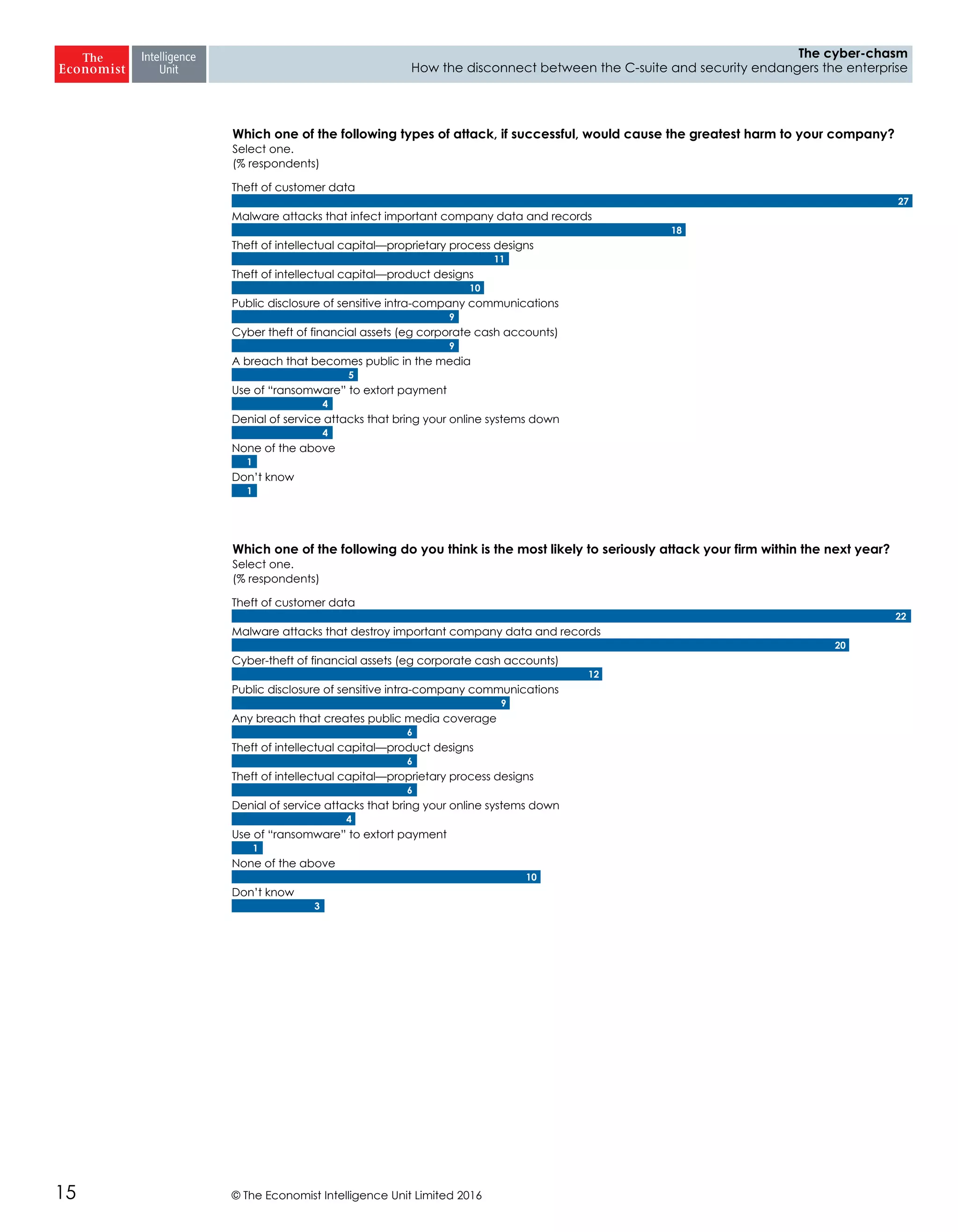
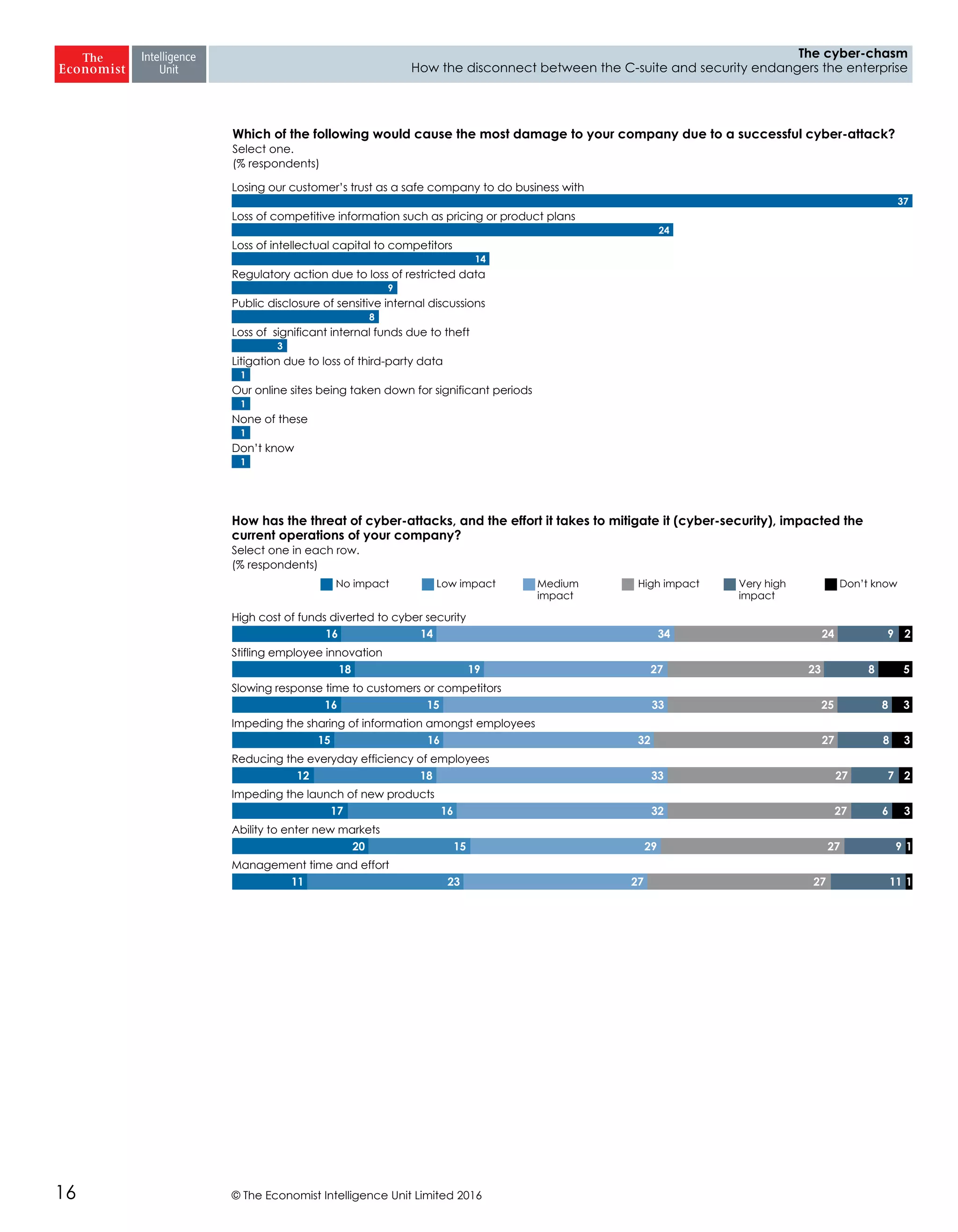
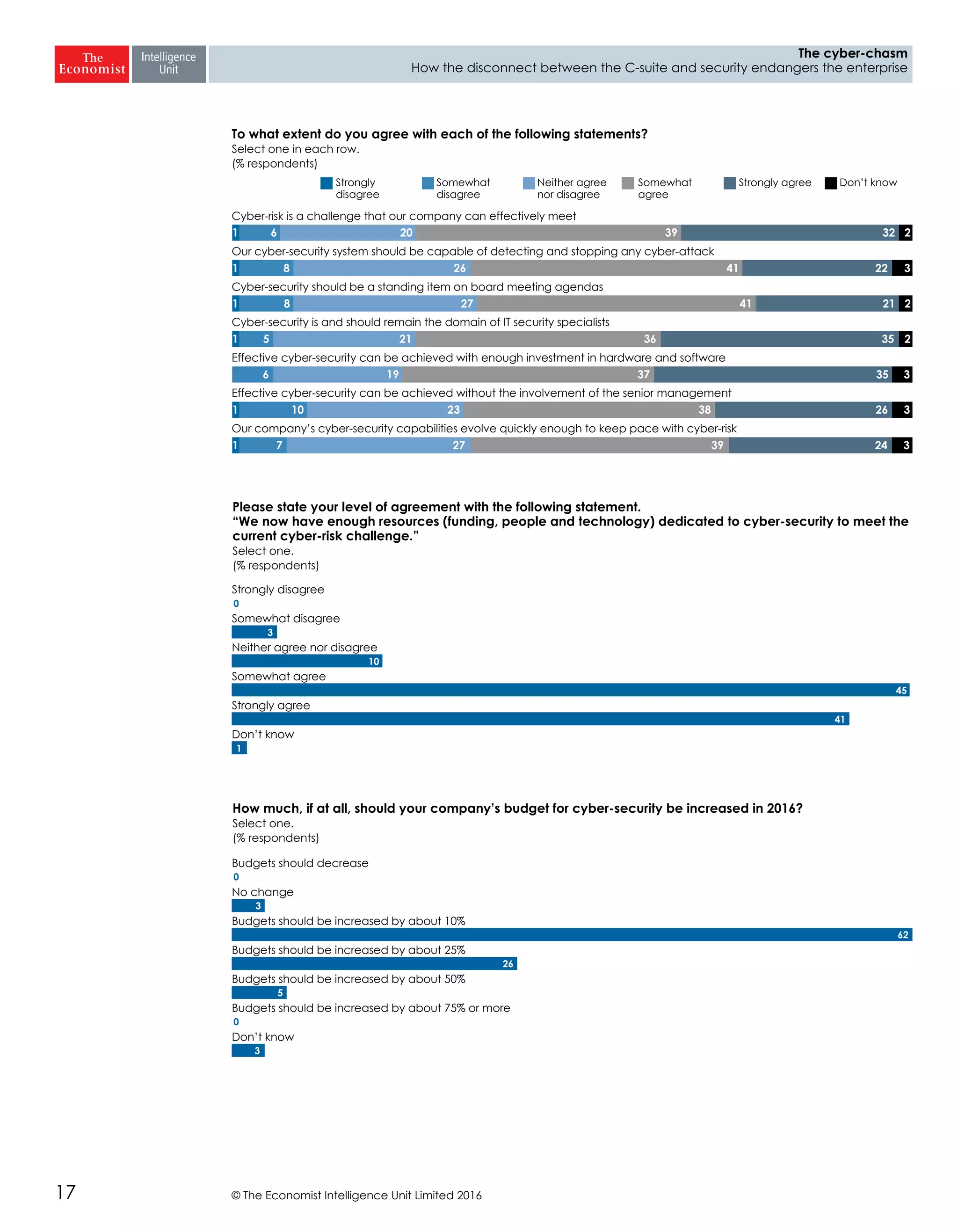
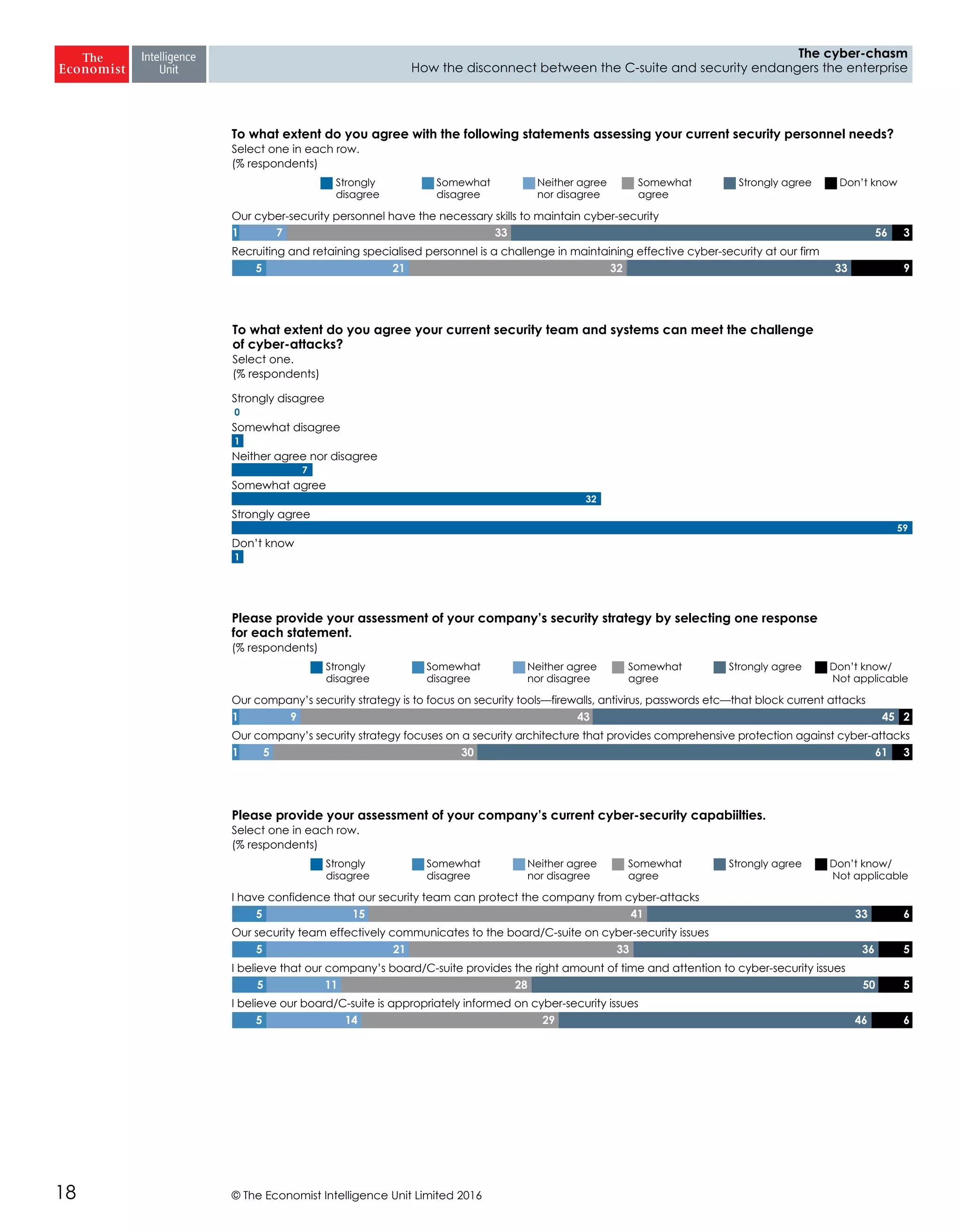
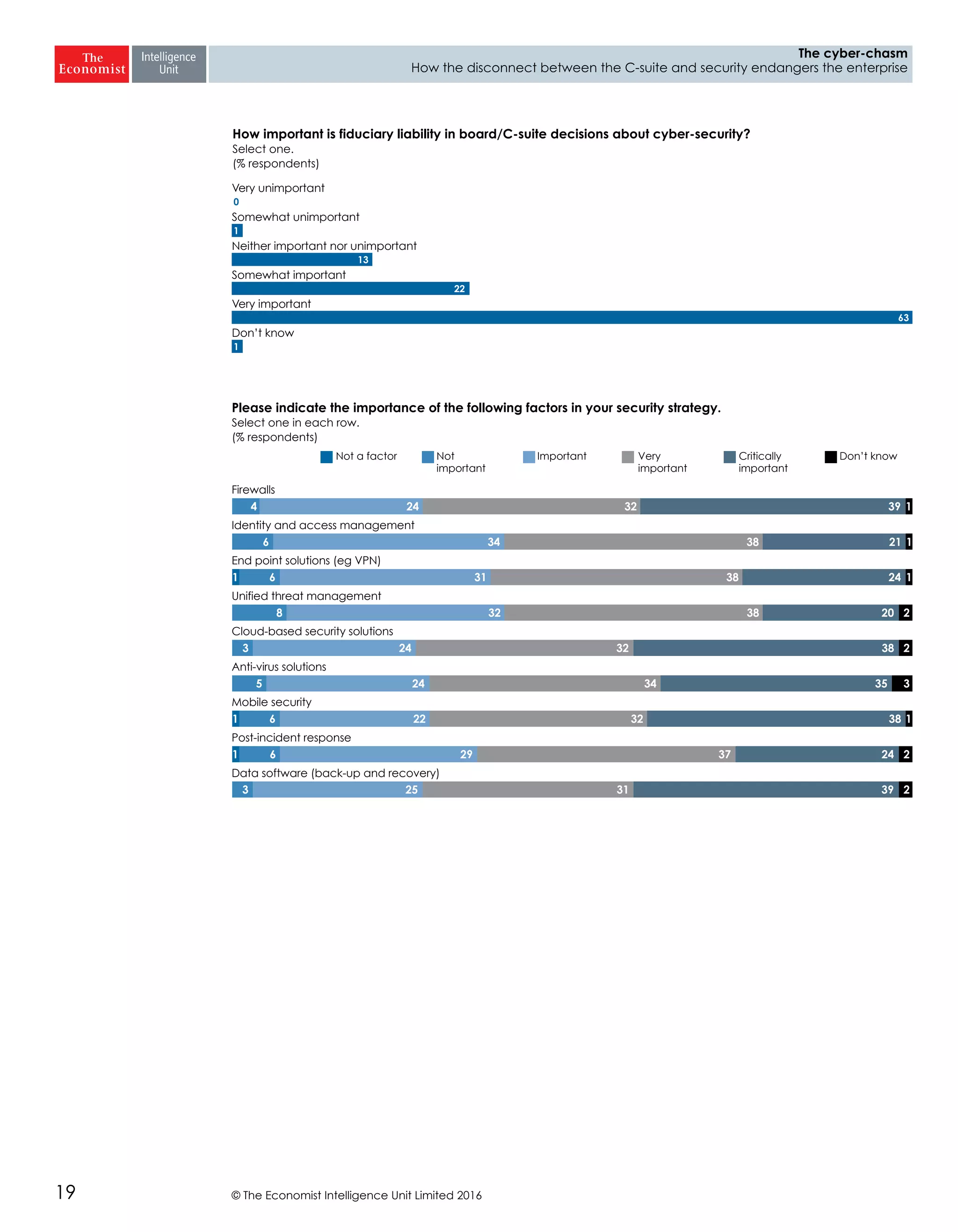
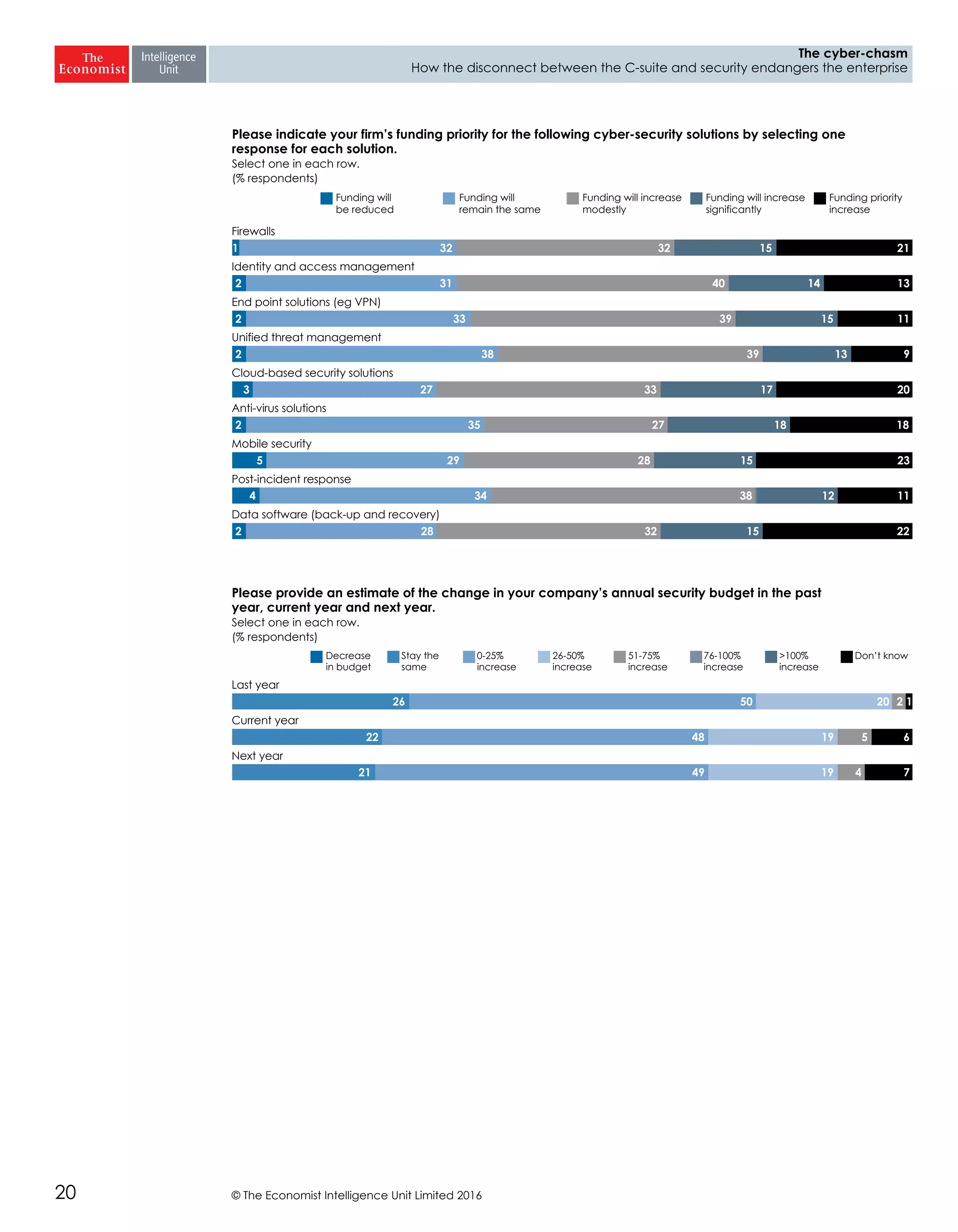
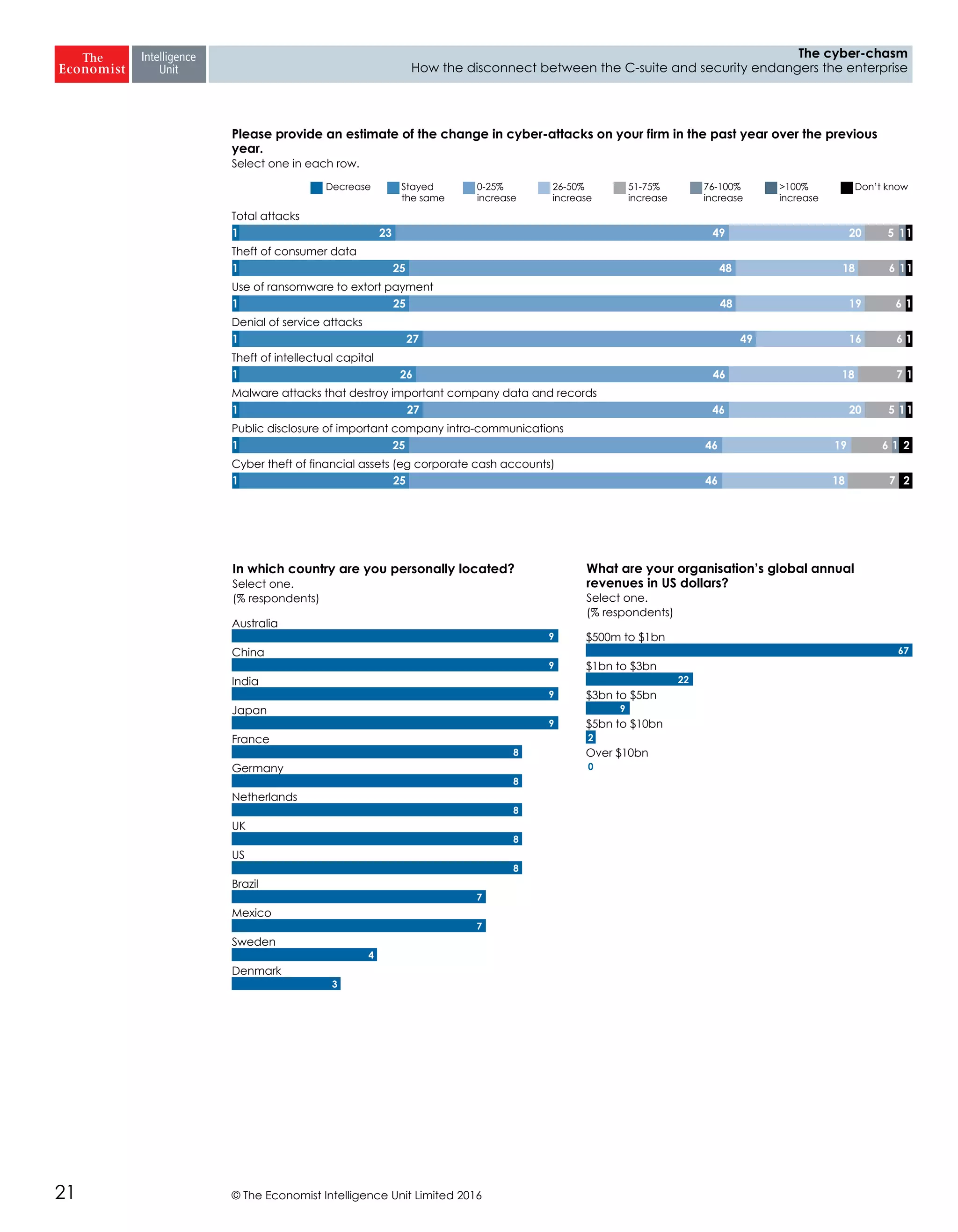
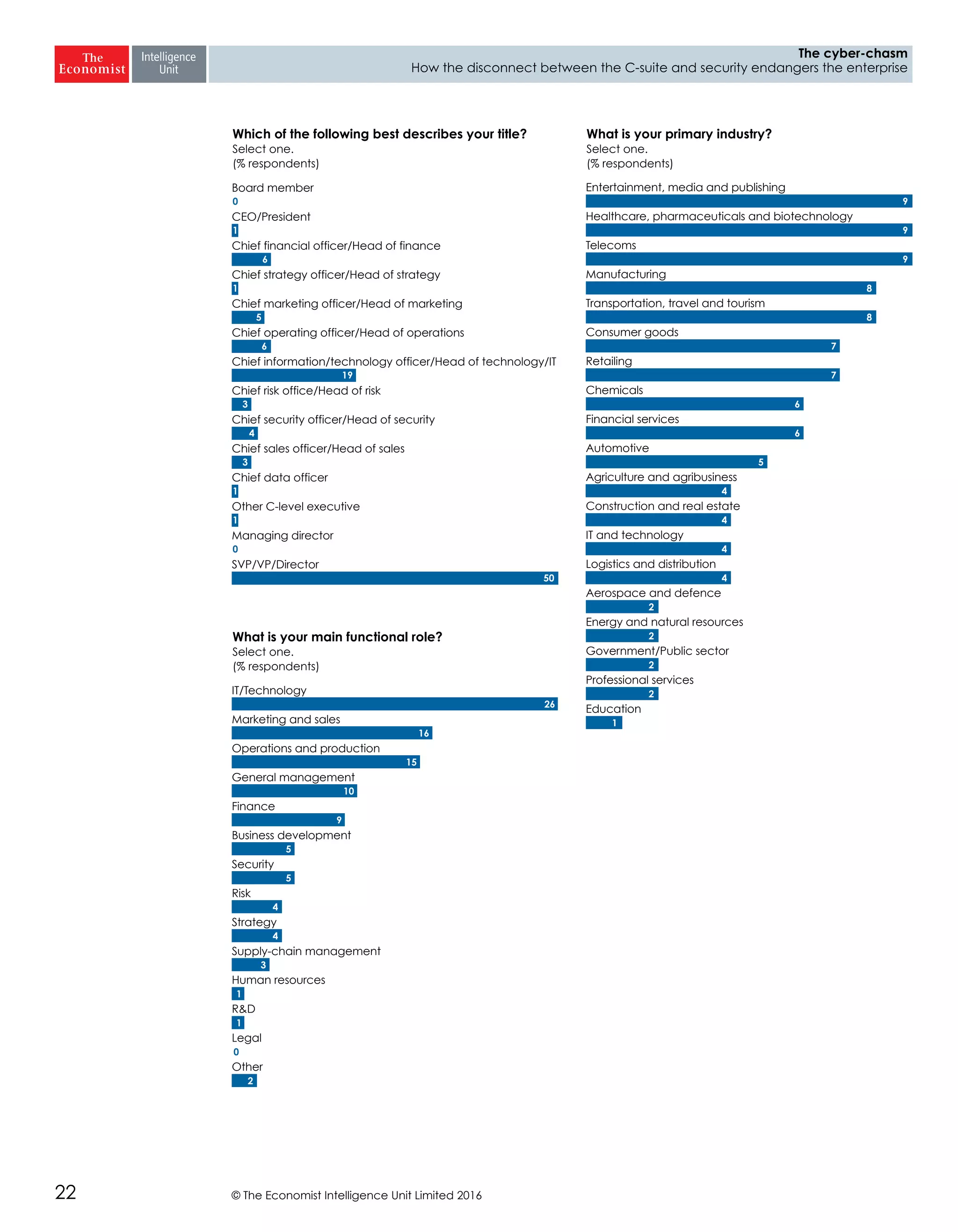
The report highlights a significant disconnect between the C-suite executives and security leaders in organizations, indicating that while cybersecurity is the top priority for security professionals, it ranks much lower for the C-suite. This misalignment poses a risk to corporate security, as the C-suite focuses more on strategic business impacts rather than the tactical needs of security. As a result, there is a lack of urgency among executives to allocate necessary resources, which could lead to increased vulnerability to cyber threats.