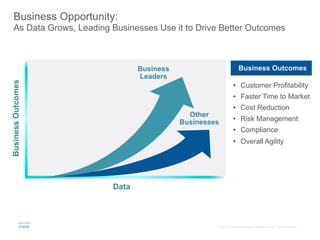
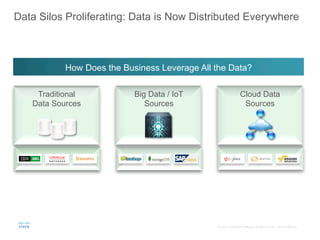
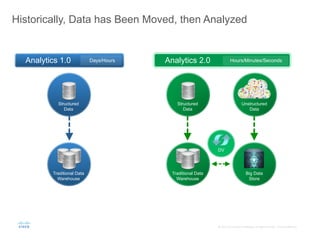
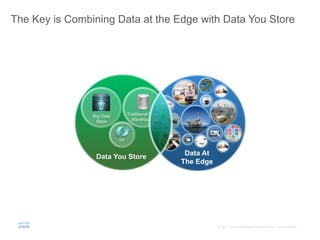
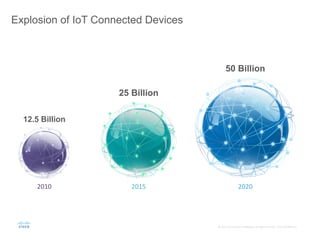
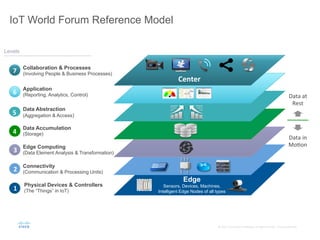
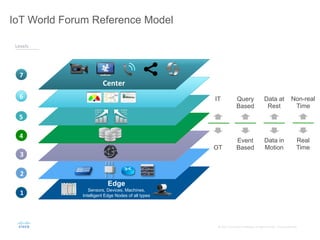
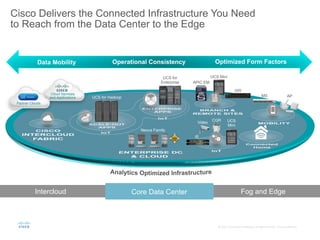
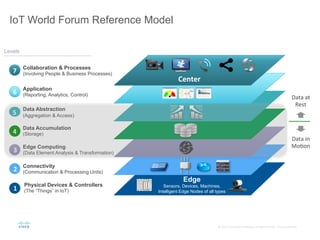
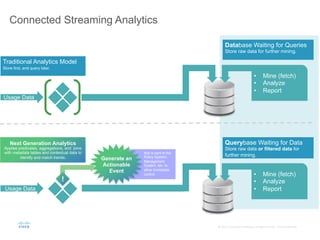
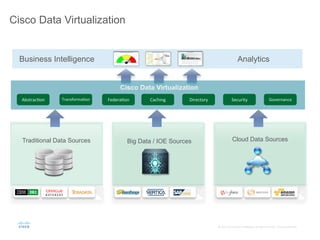
The document provides an overview of a briefing on data virtualization and its impact on enterprise software, emphasizing the significance of integrating data from various sources, including IoT and traditional data channels. It features insights from Cisco's Chief Technology Officer, David Besemer, regarding the evolution of data analytics and the importance of real-time streaming capabilities in managing distributed data. The session aims to engage vendors, analysts, and audience members in discussing innovative technologies and business opportunities arising from effective data management.