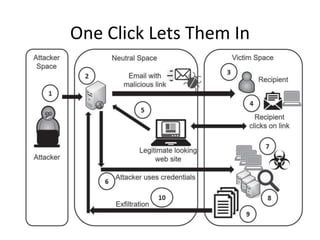
Threat actors range from script kiddies with little expertise to well-funded nation states. Malware types include viruses, worms, Trojans, ransomware and more. Common attacks are phishing, spear phishing, whaling, and privilege escalation. Organizations block malware using tools like antivirus software, firewalls, spam filters and user education on threats.