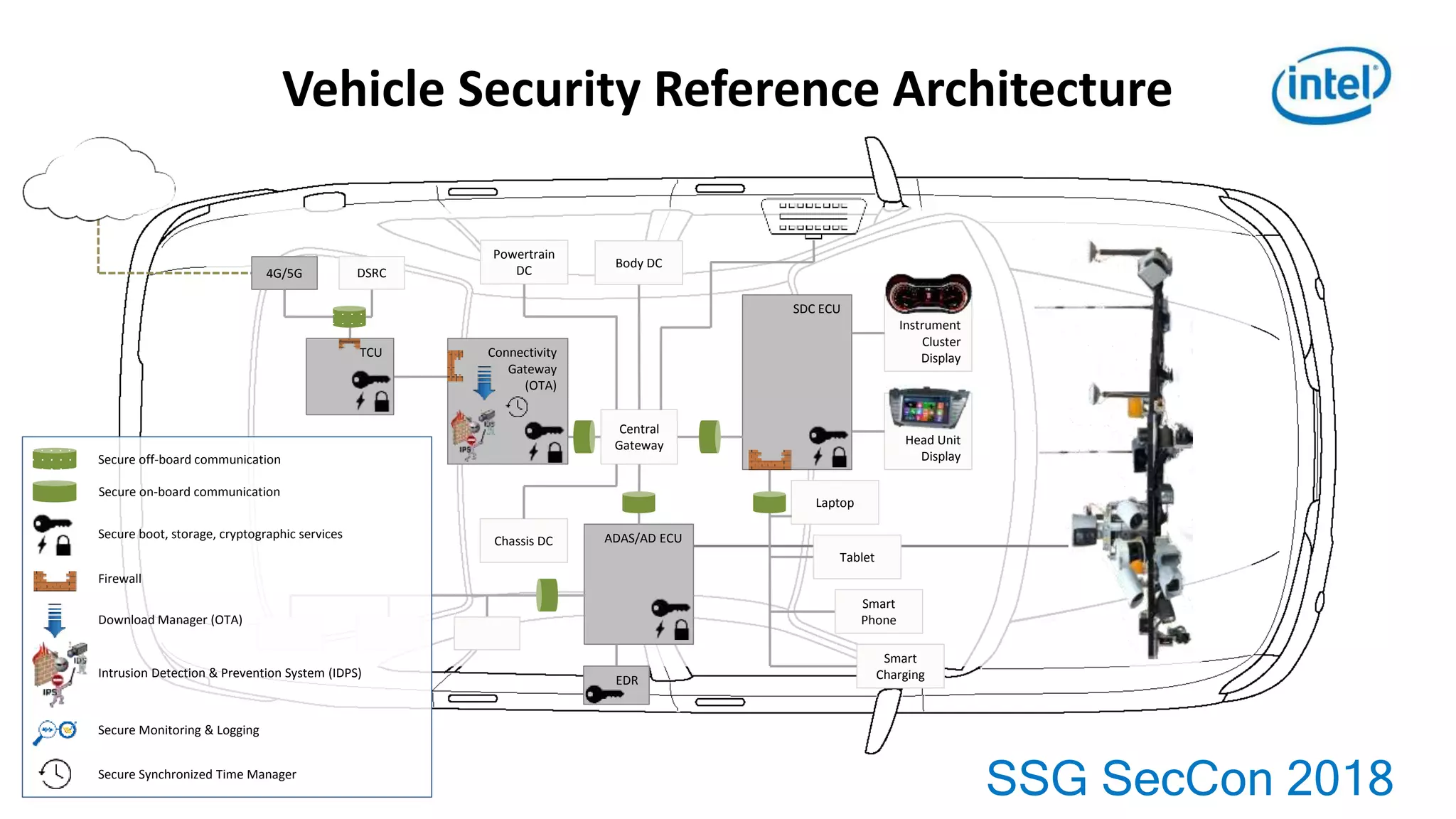
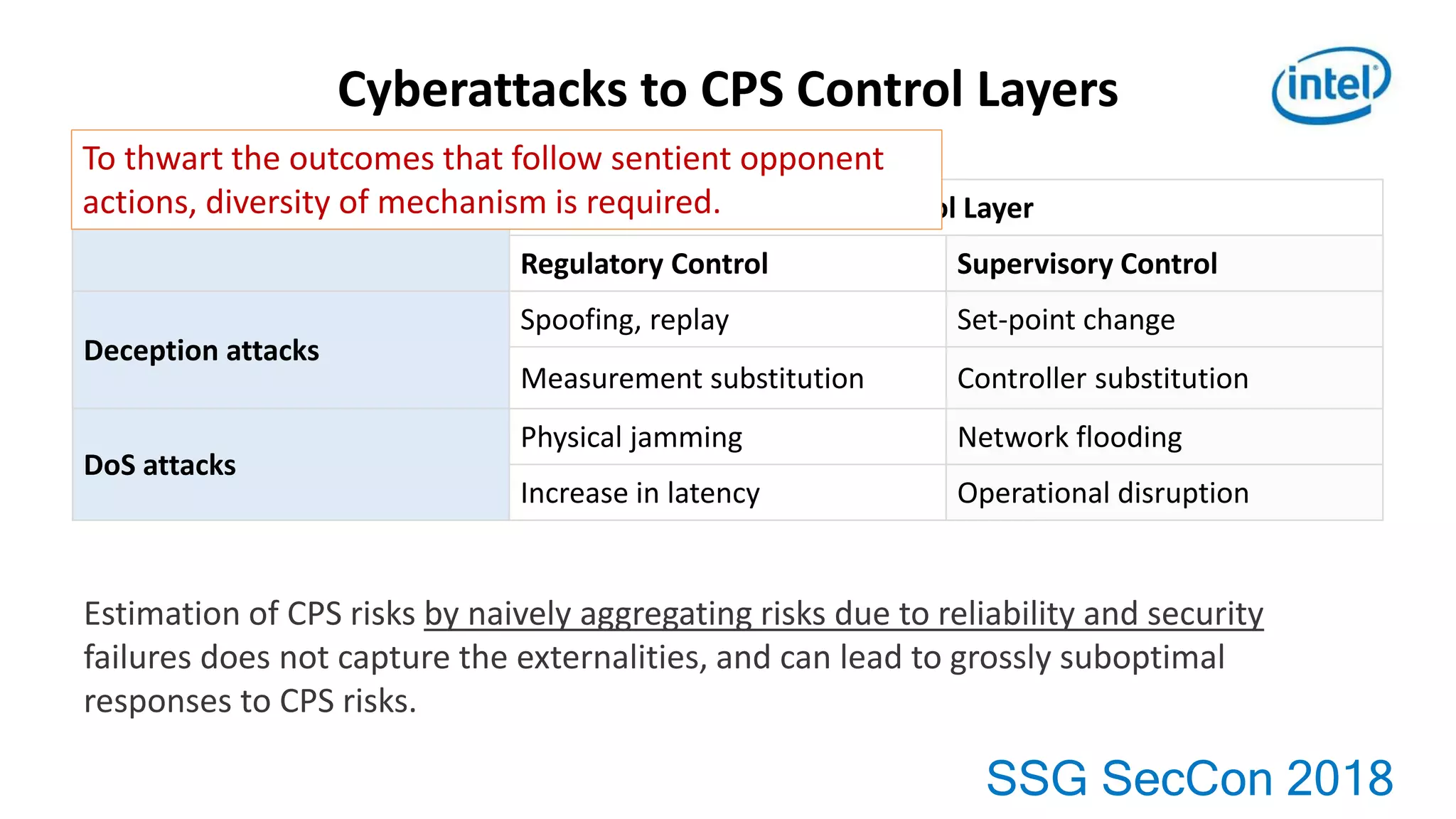
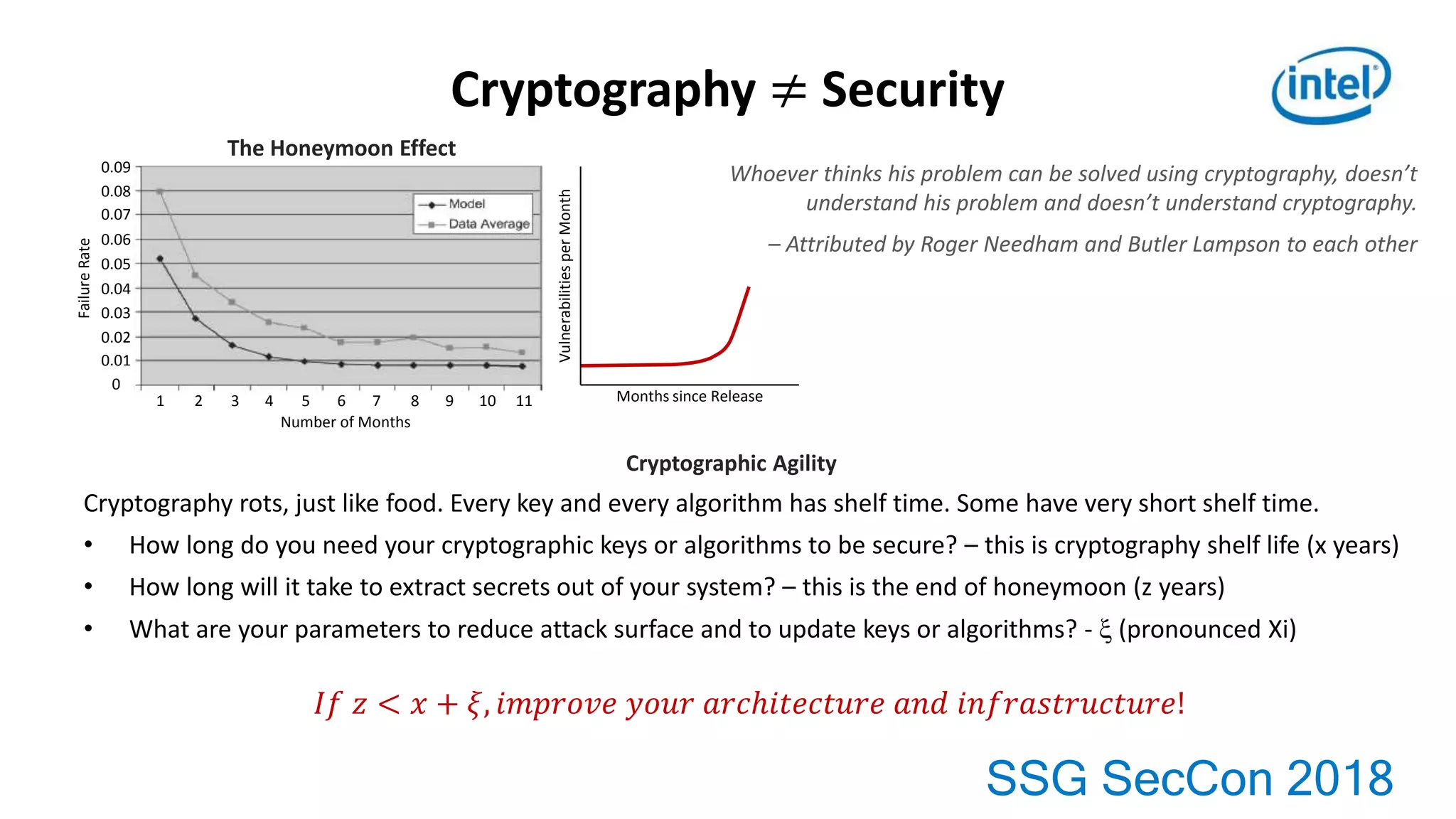
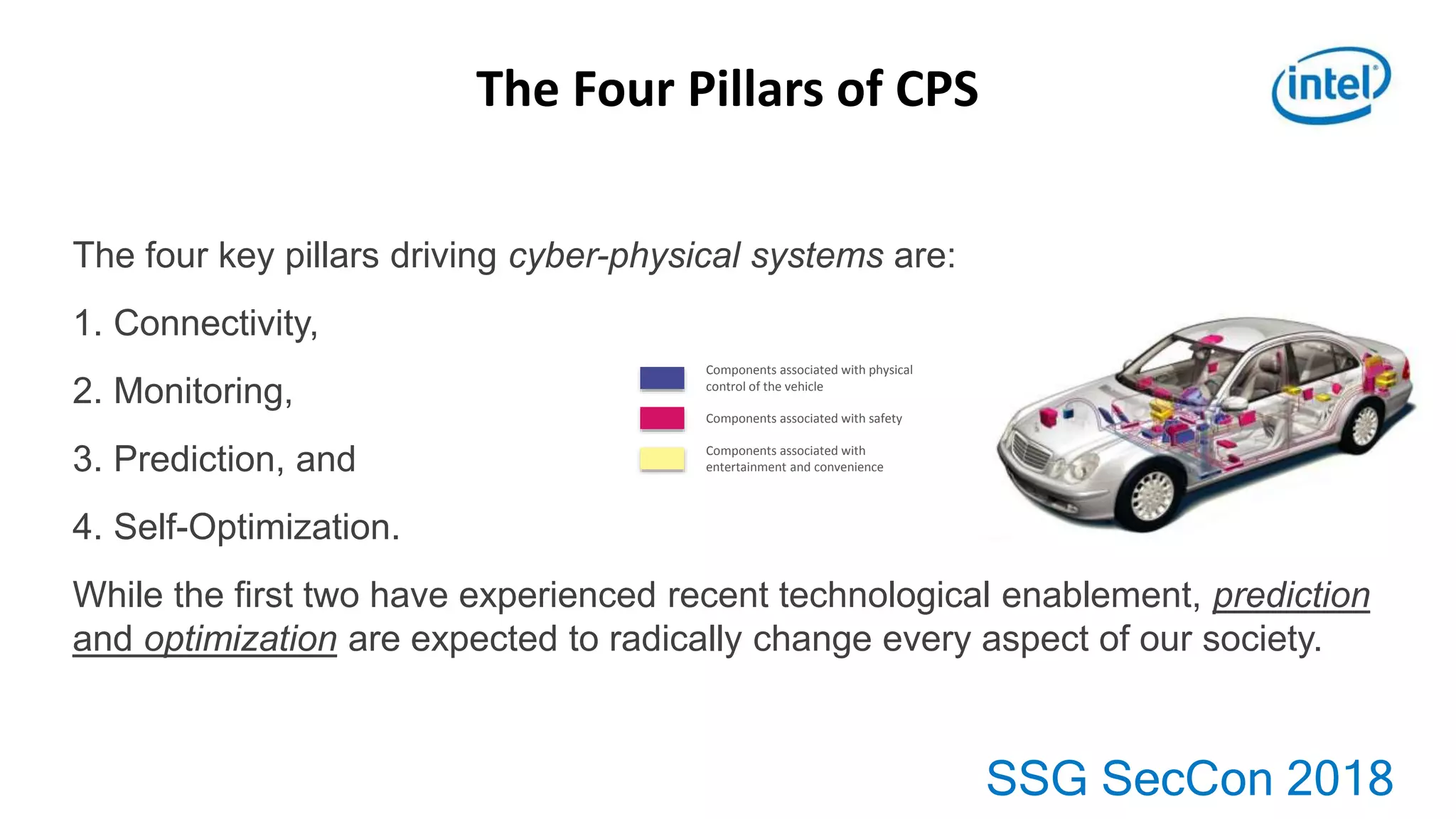
This document provides an overview of key topics in automotive software and security:
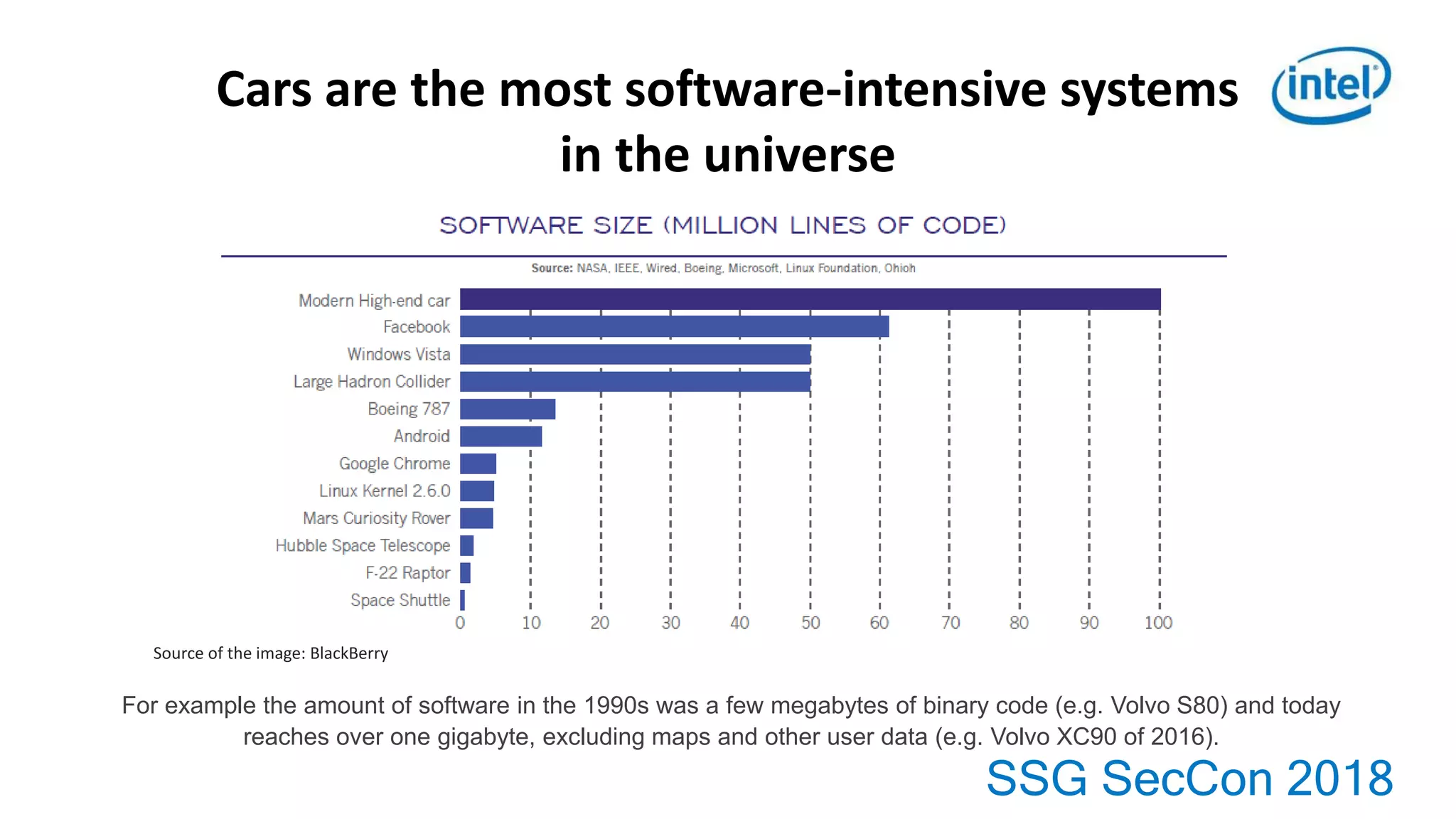
1. Cars now contain over 1 gigabyte of software code due to increasing automation, connectivity and data analytics capabilities.
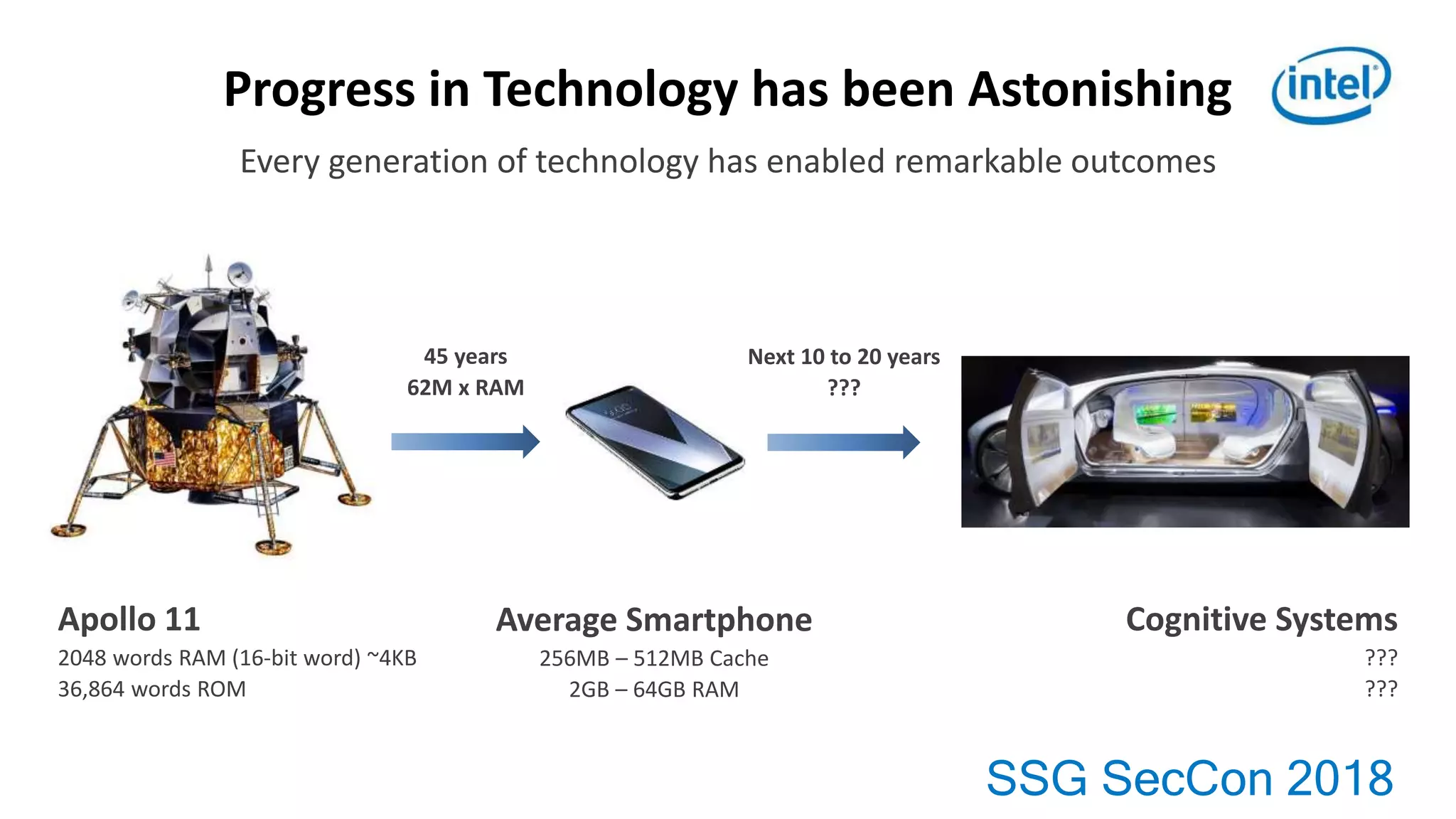
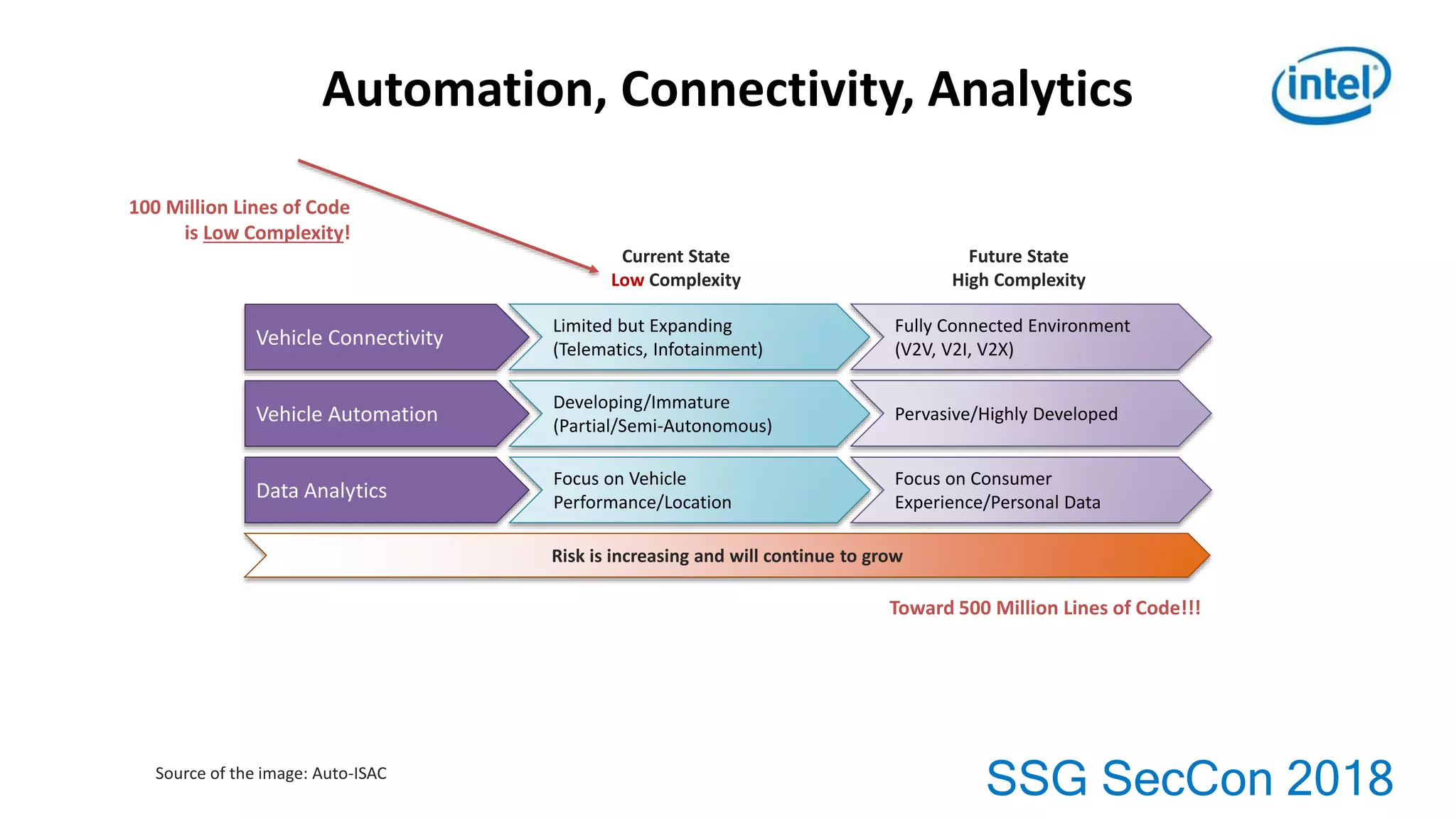
2. As vehicles become more connected and automated, software complexity and security risks will continue growing substantially over the next 10-20 years.
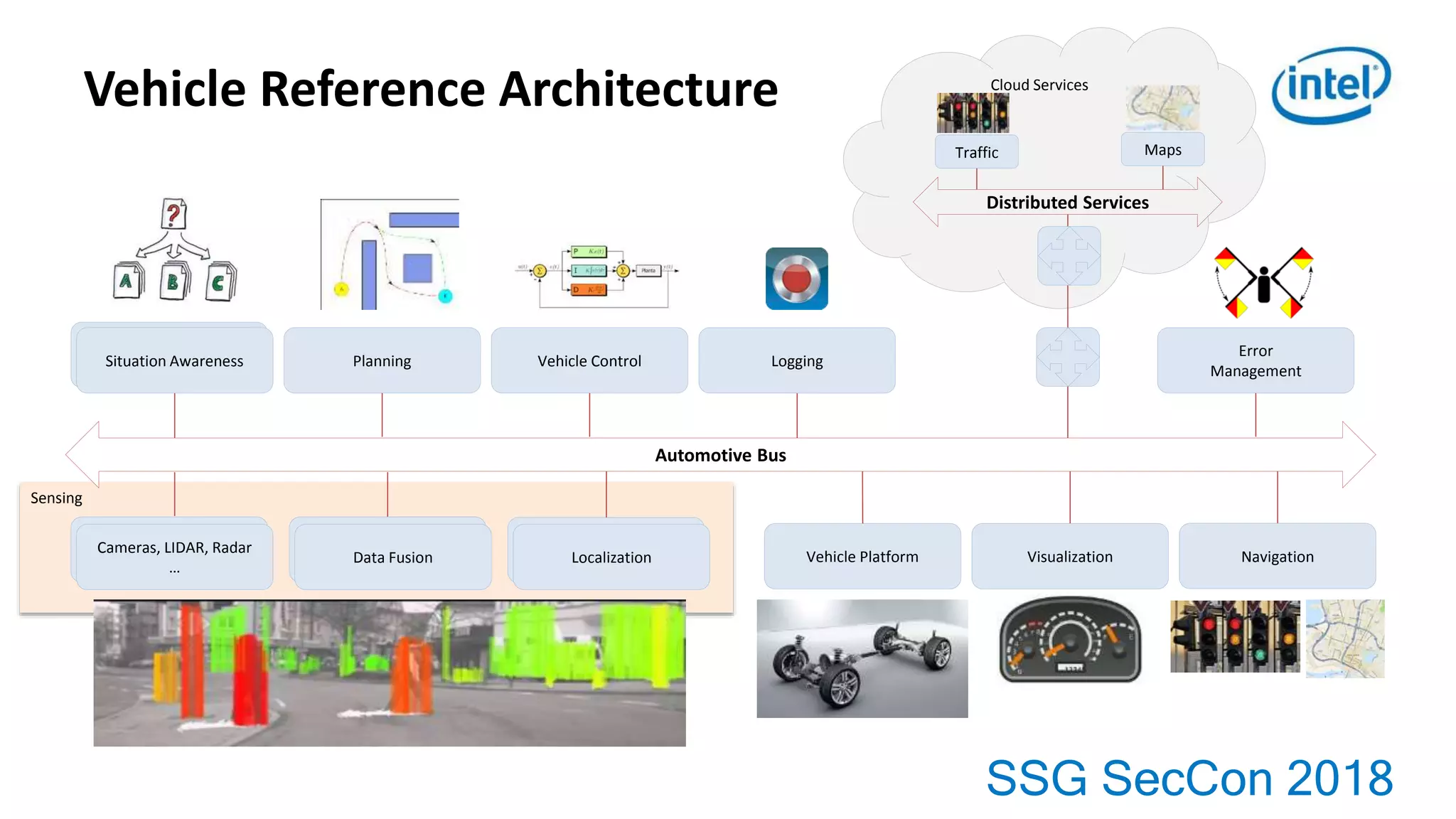
3. Developing highly reliable and secure automotive software requires addressing challenges across computing, embedded systems, and functional safety.