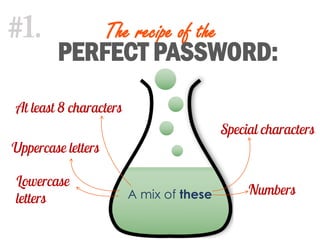
The document provides tips on computer security, emphasizing the importance of creating strong passwords that are at least 8 characters long and include a mix of uppercase letters, lowercase letters, and special characters. It advises against sharing passwords, recommends changing them regularly, and stresses the necessity of deleting unnecessary passwords. Additionally, it highlights the need for software compliance by using only approved and licensed software.