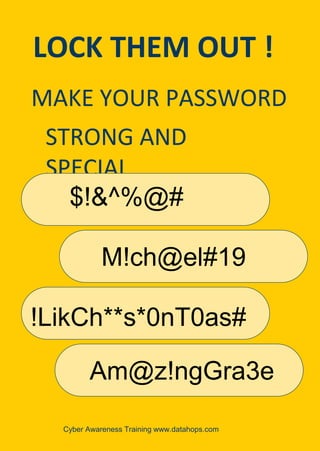
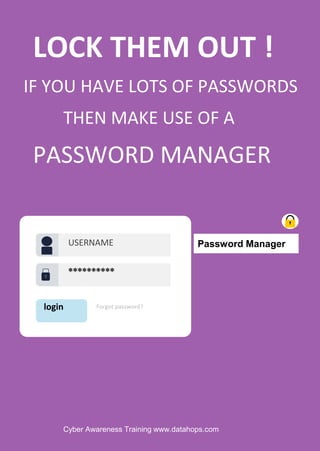
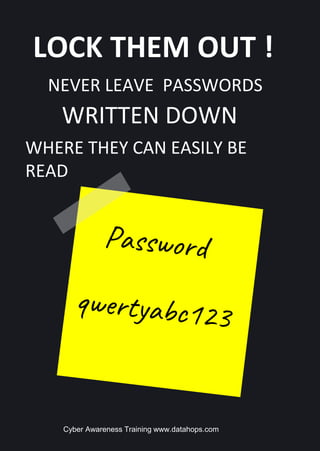
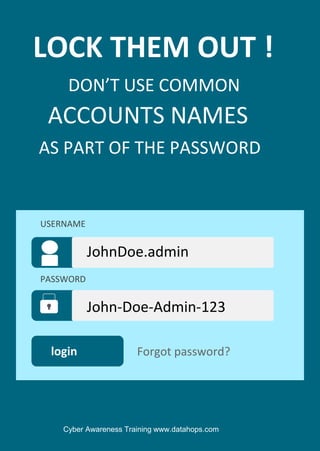
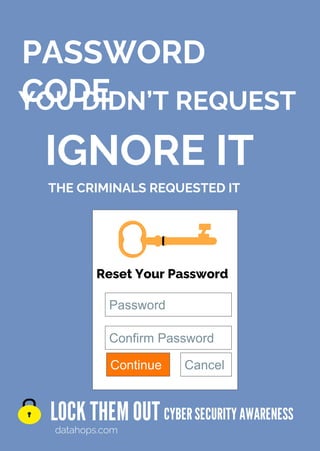
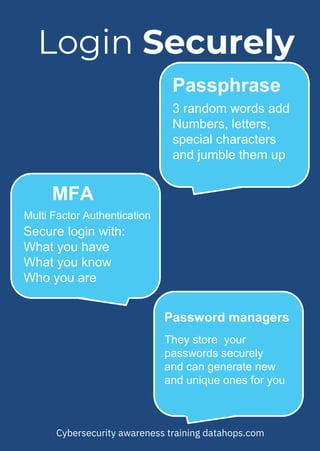
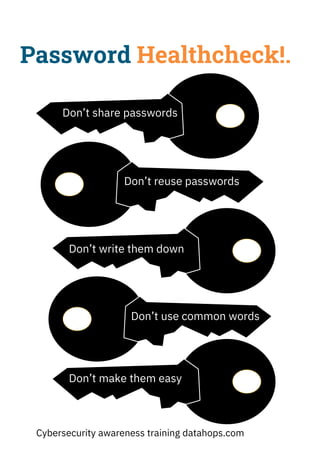
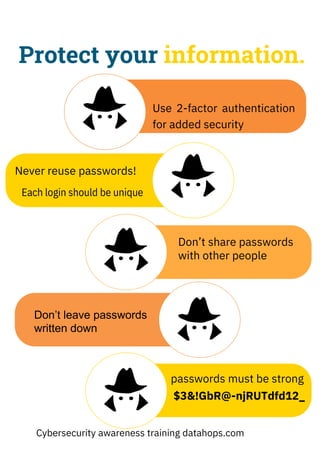
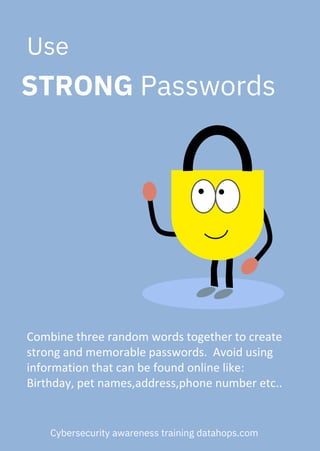
The document emphasizes the importance of creating strong, unique passwords to enhance cybersecurity. Key recommendations include using a password manager, enabling two-step authentication, and avoiding easily guessable information. Regularly updating passwords and using complex combinations of characters are also advised for optimal security.