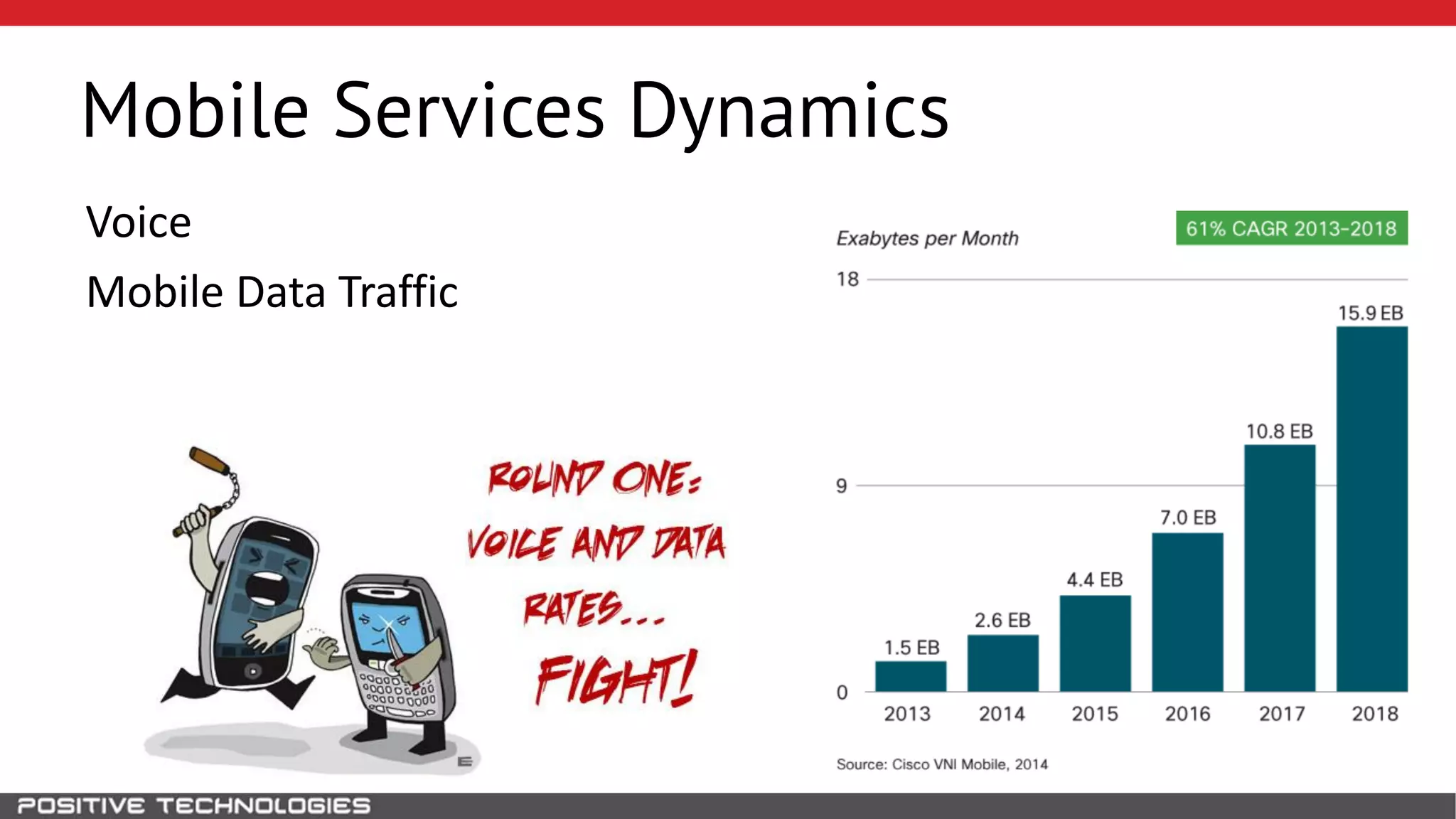
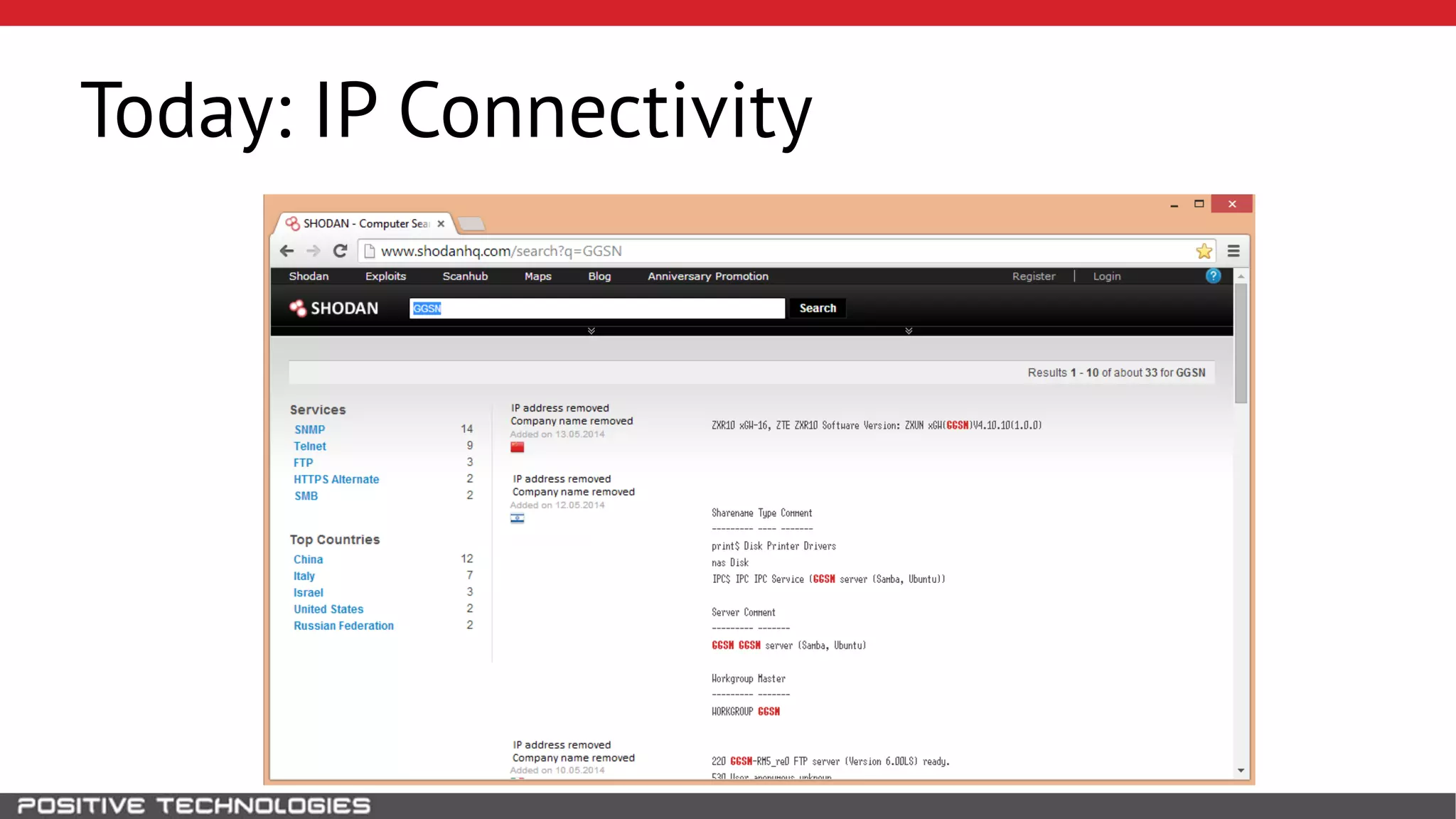
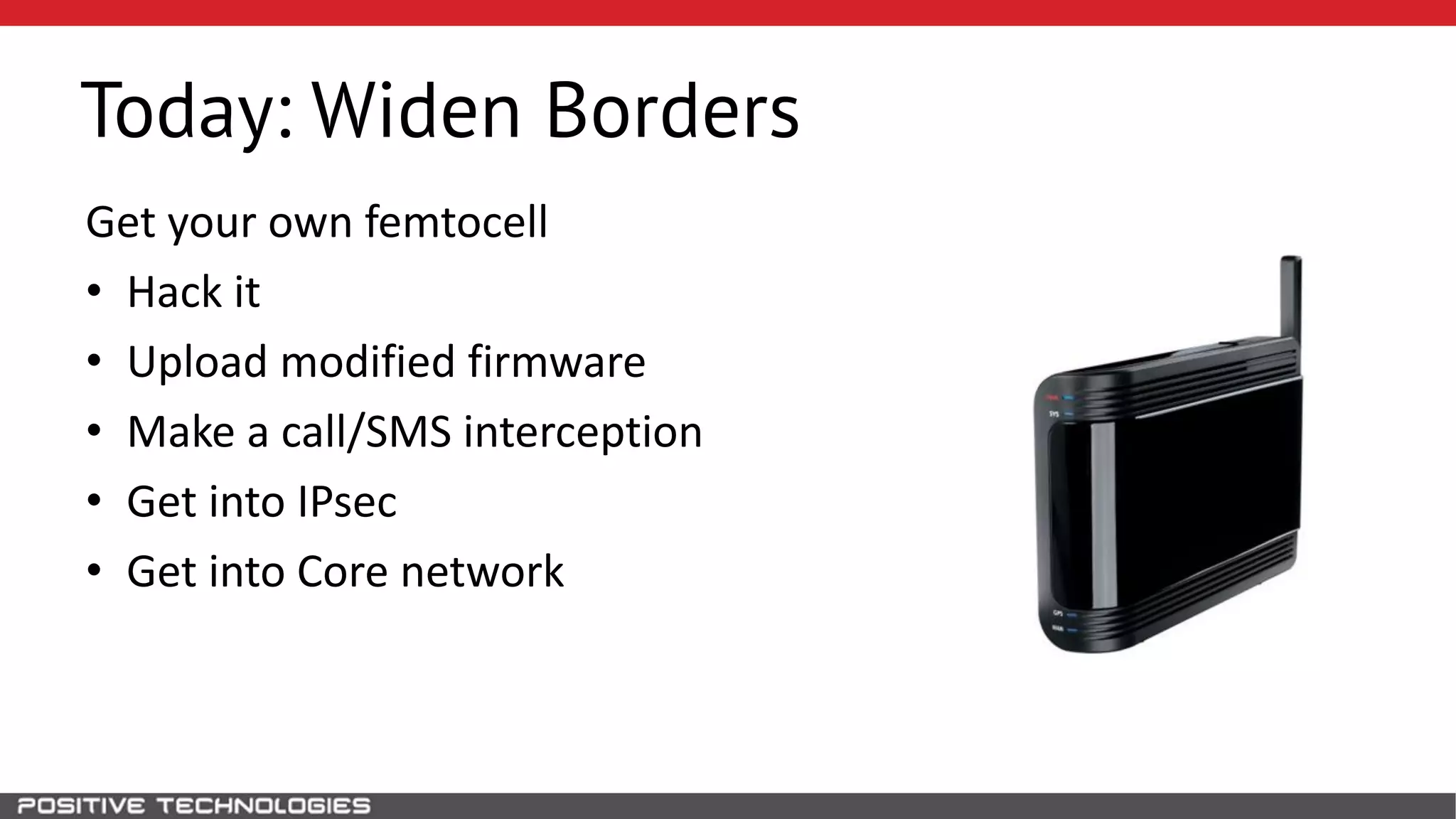
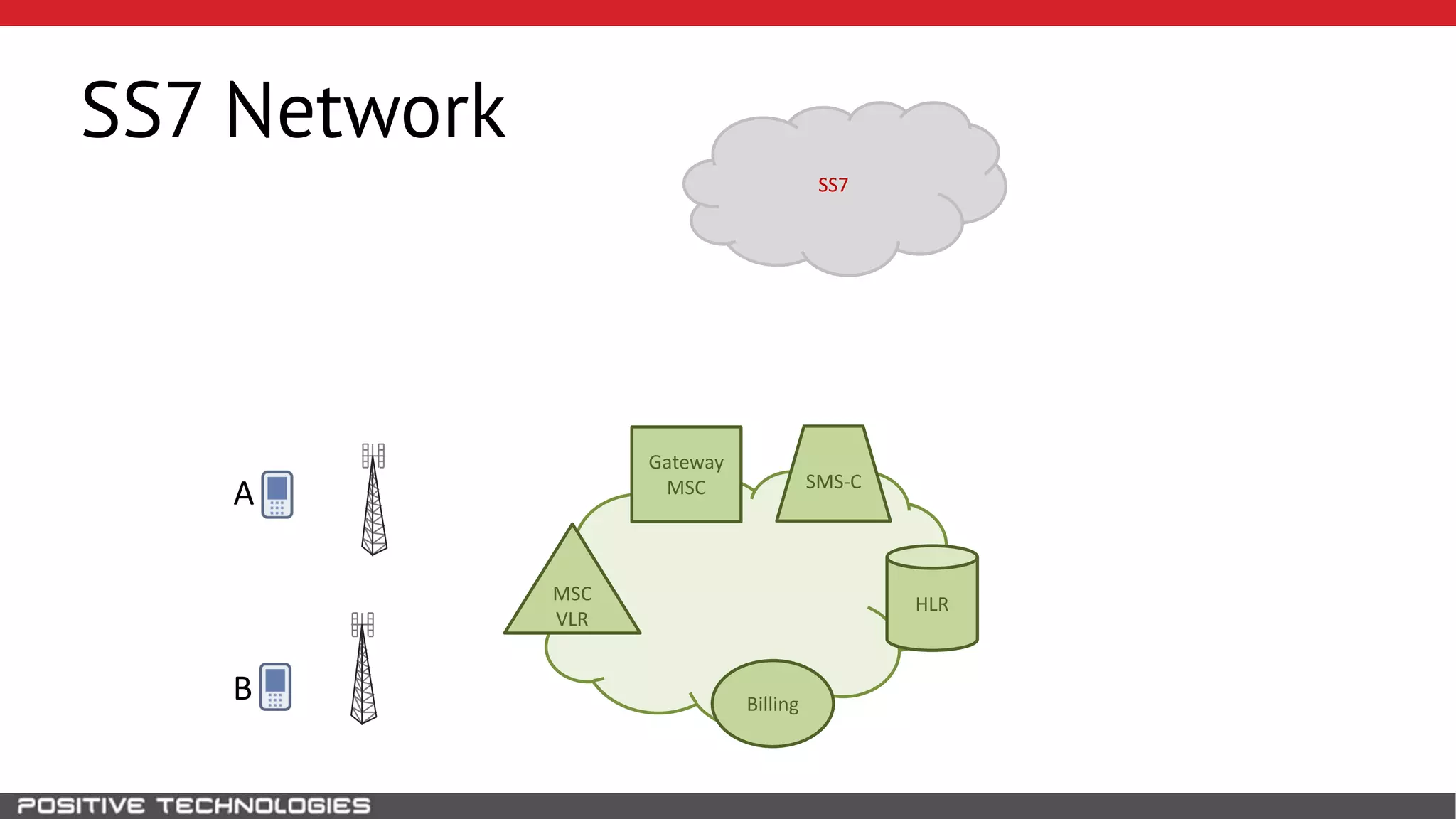
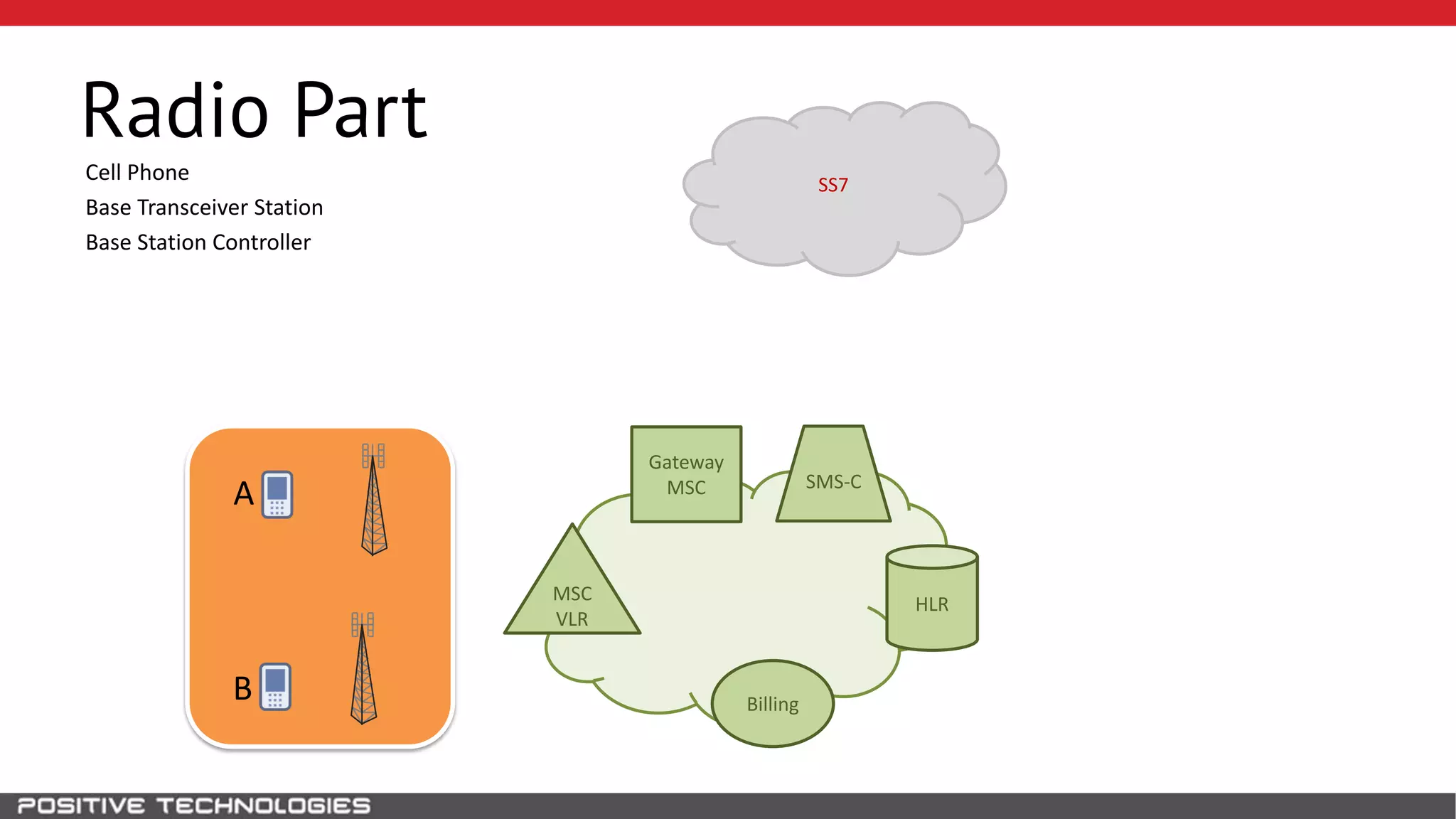
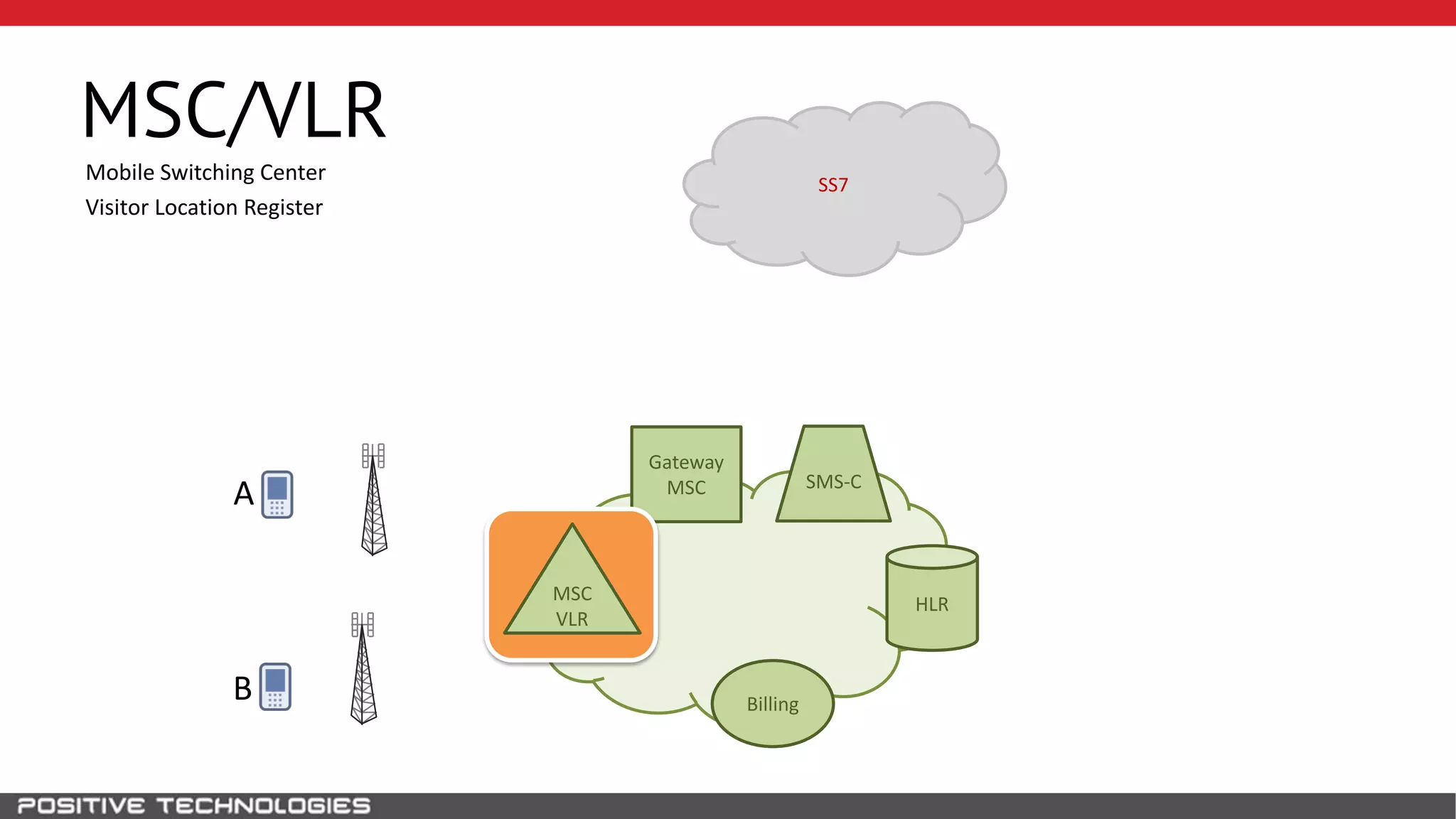
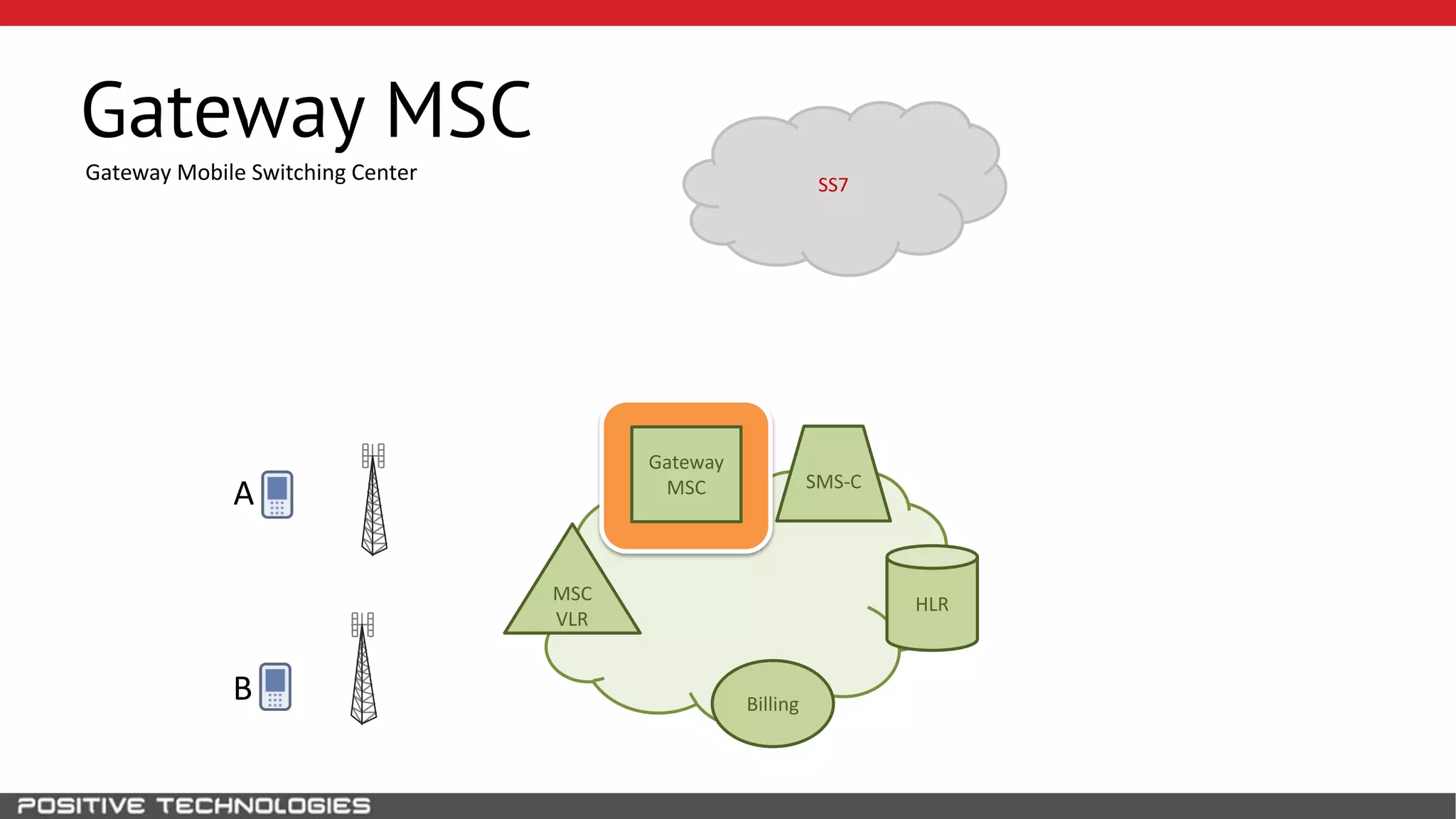
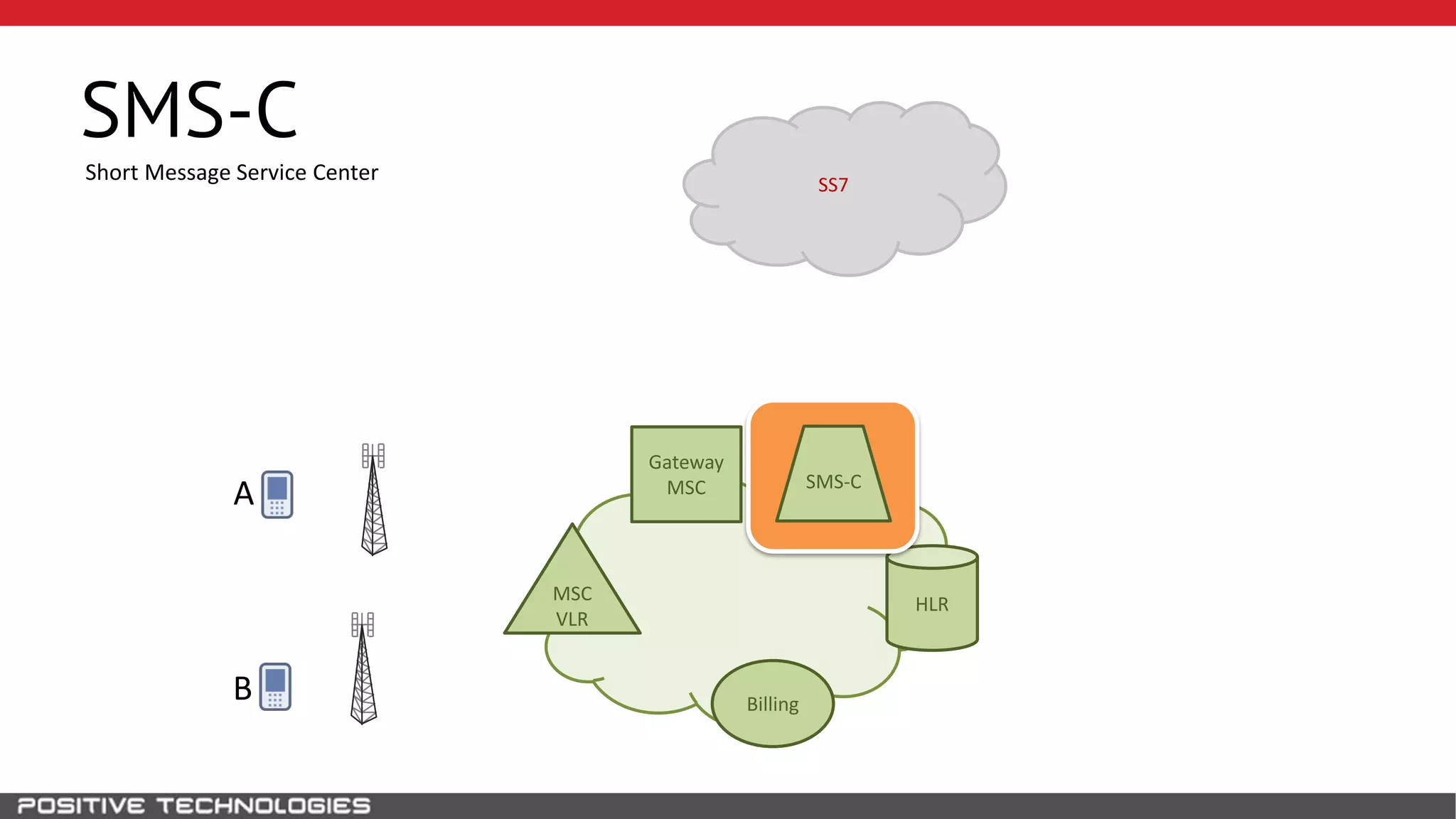
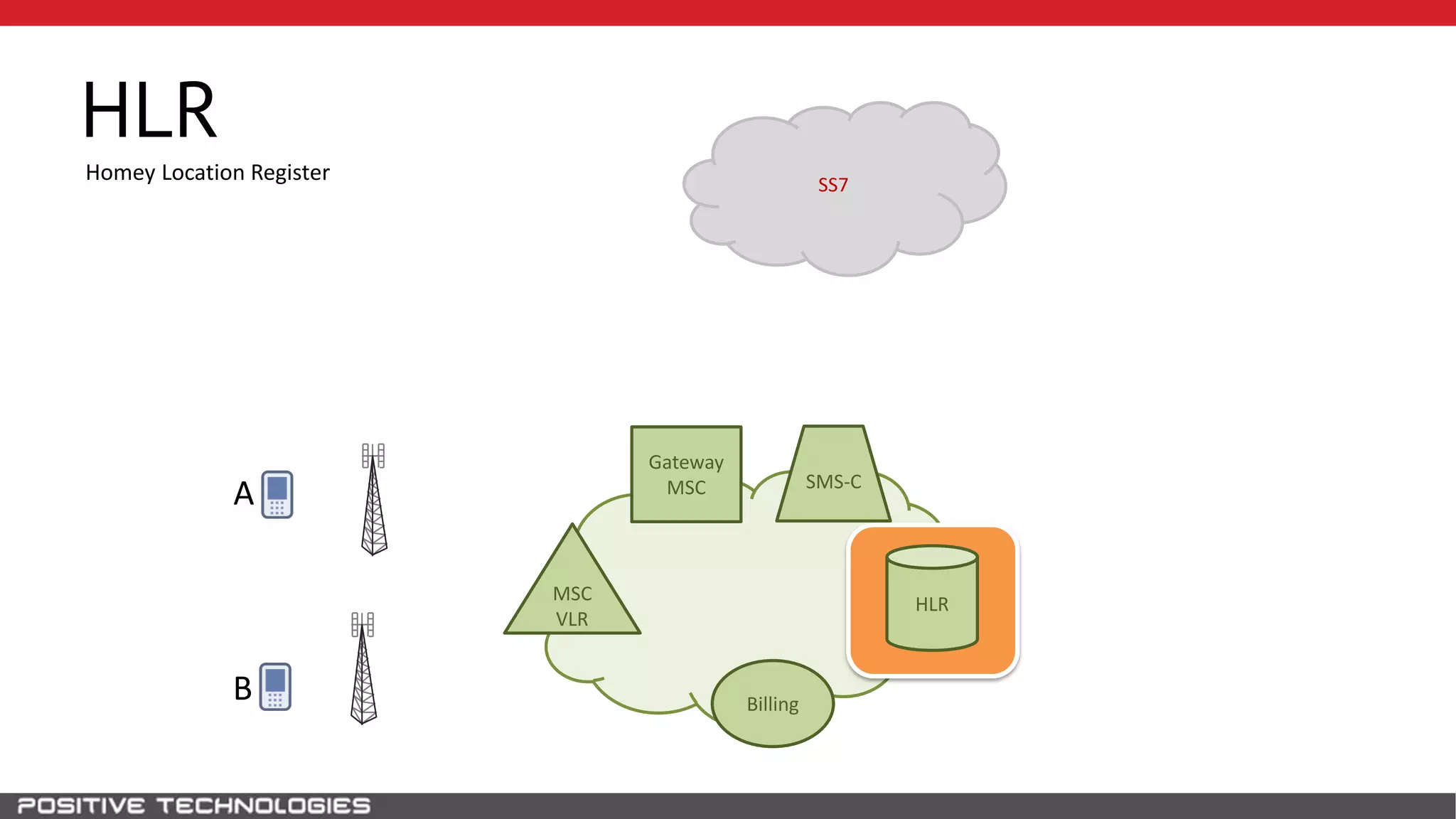
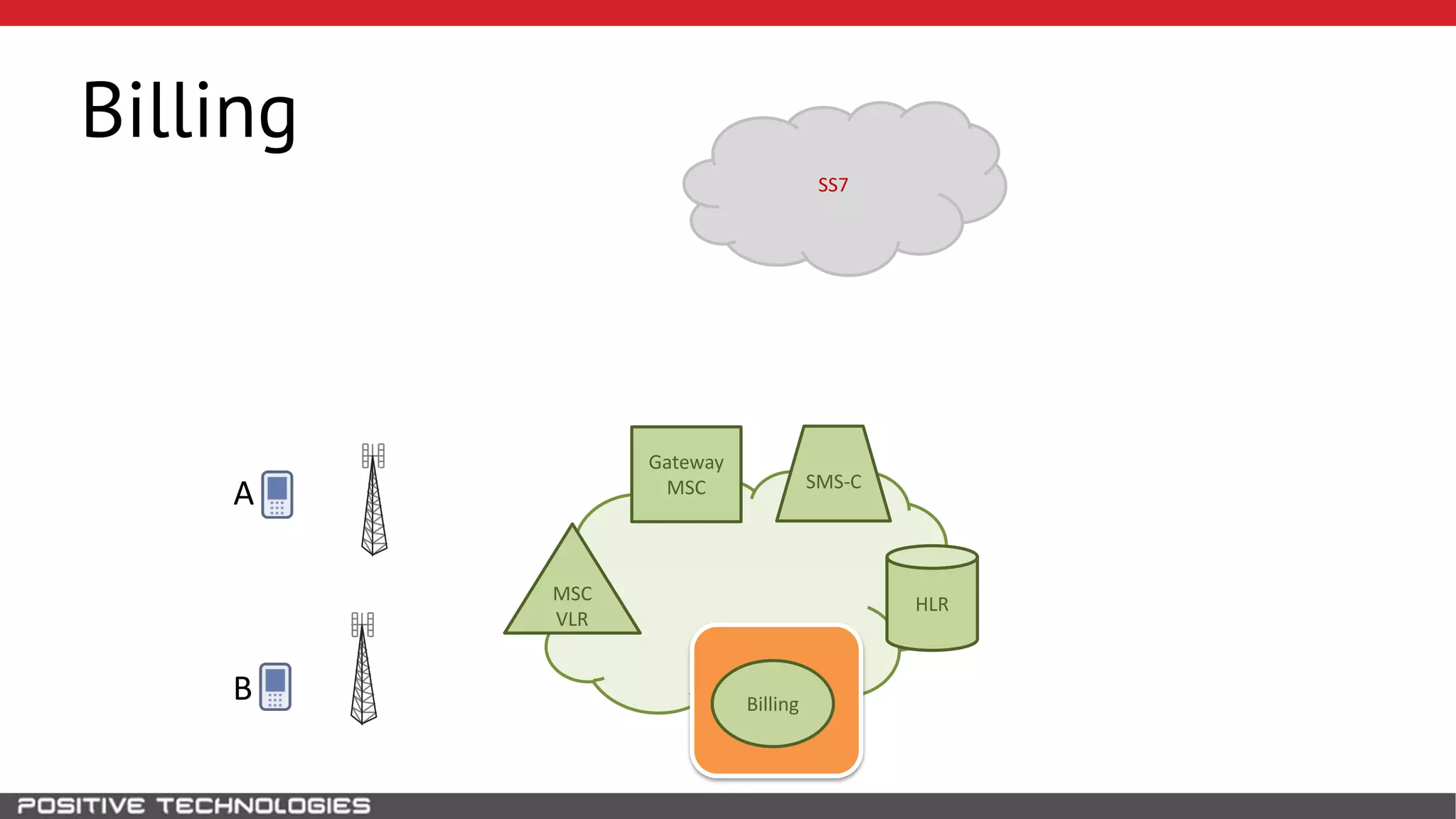
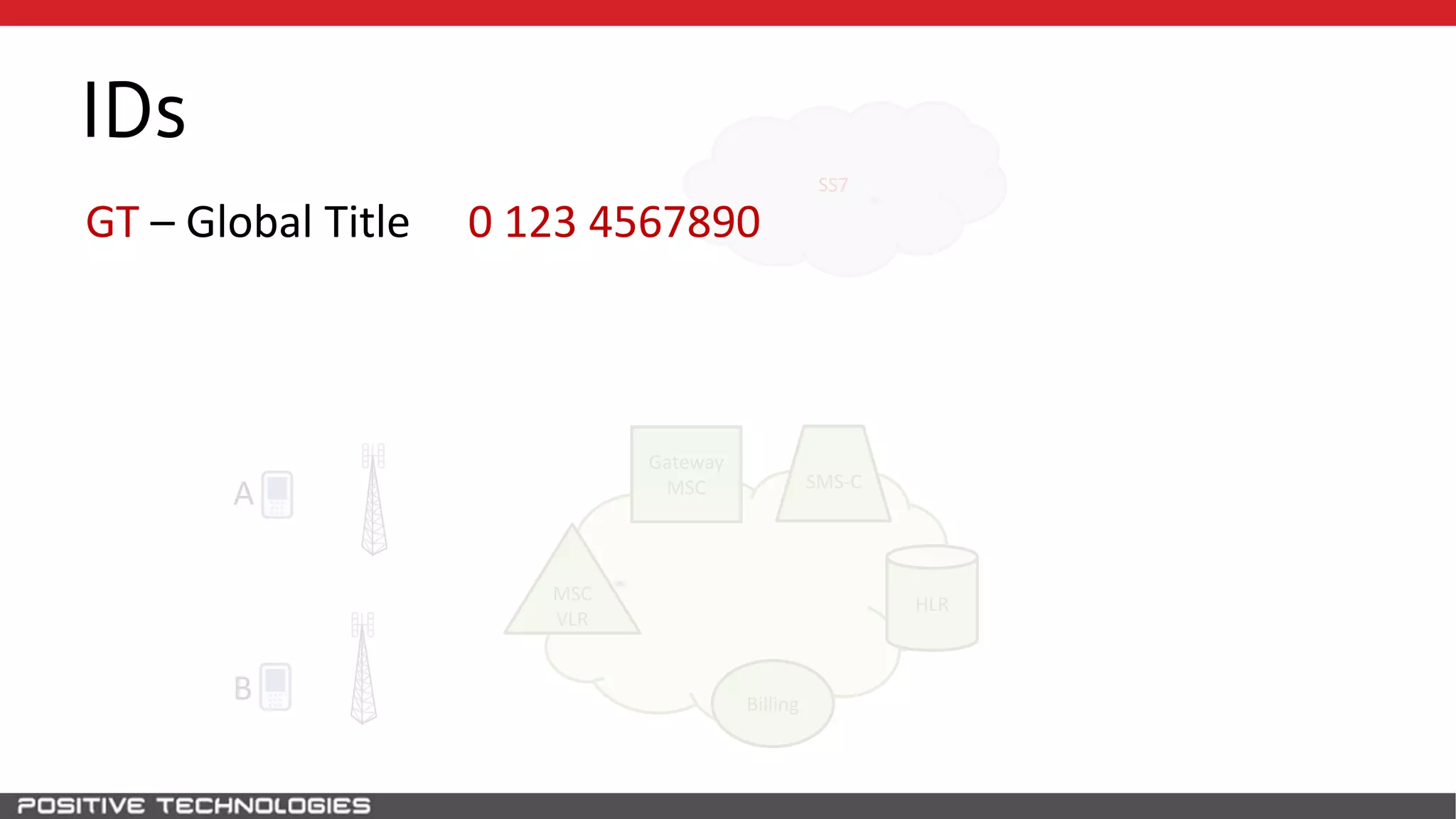
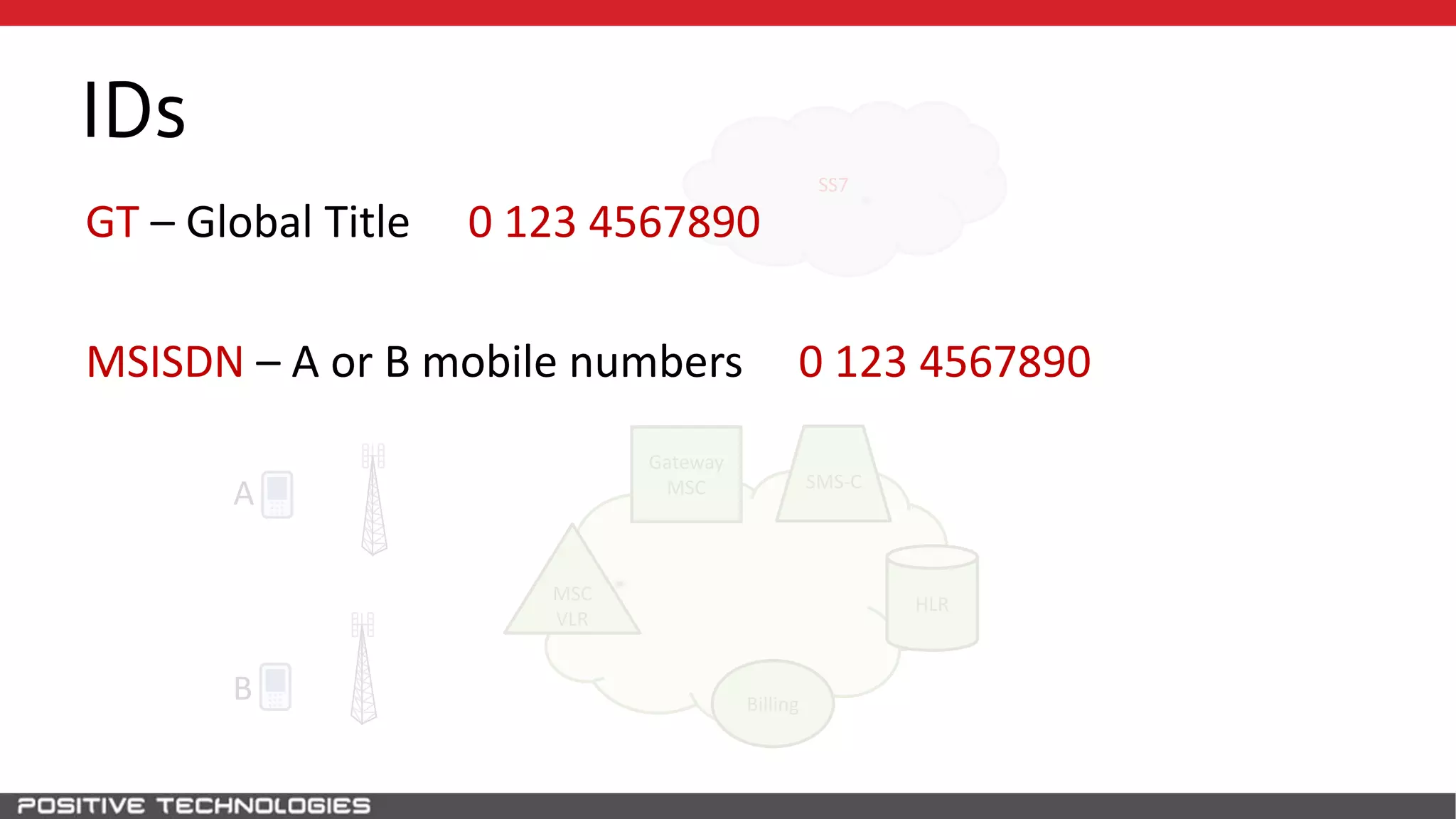
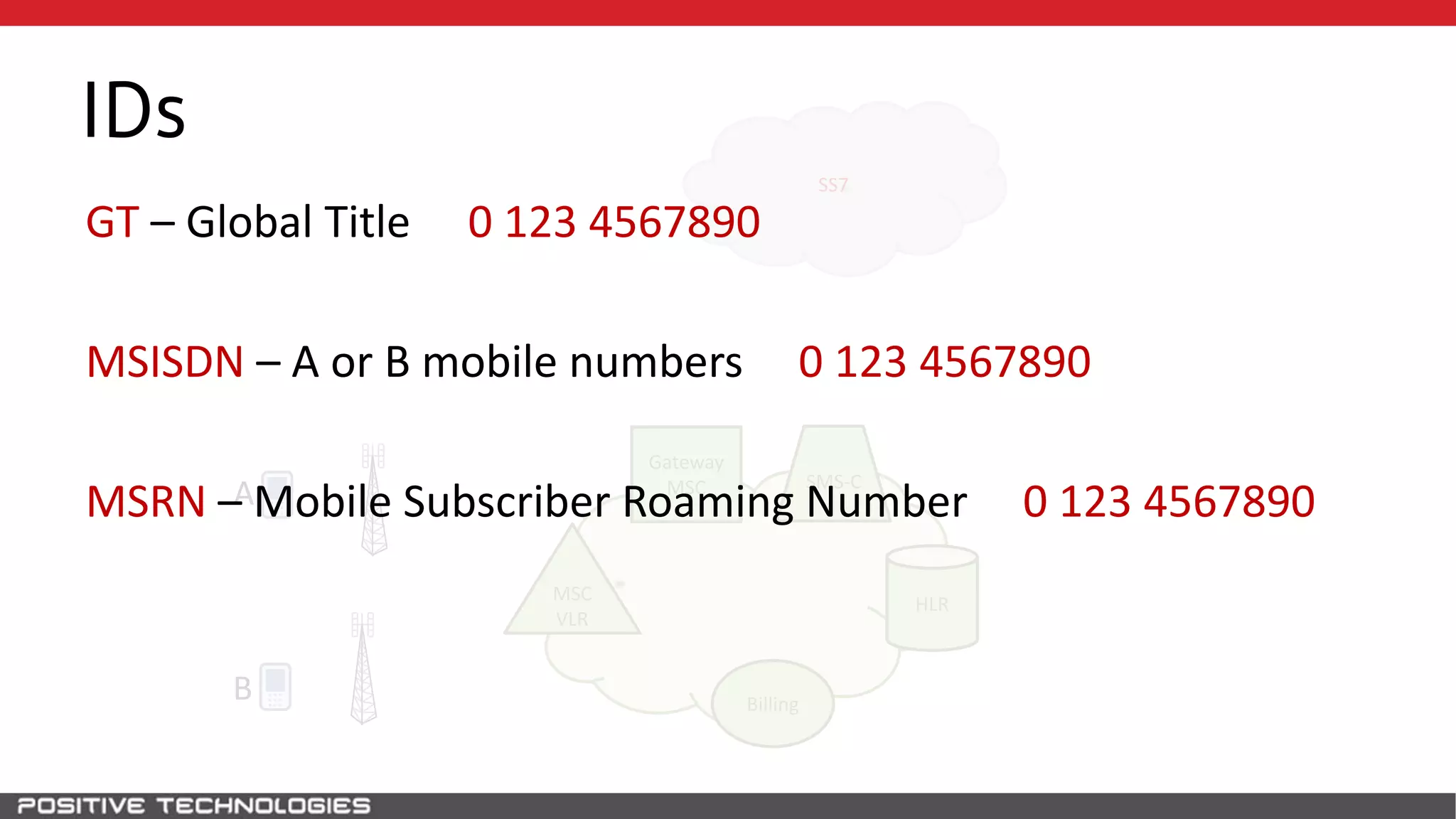
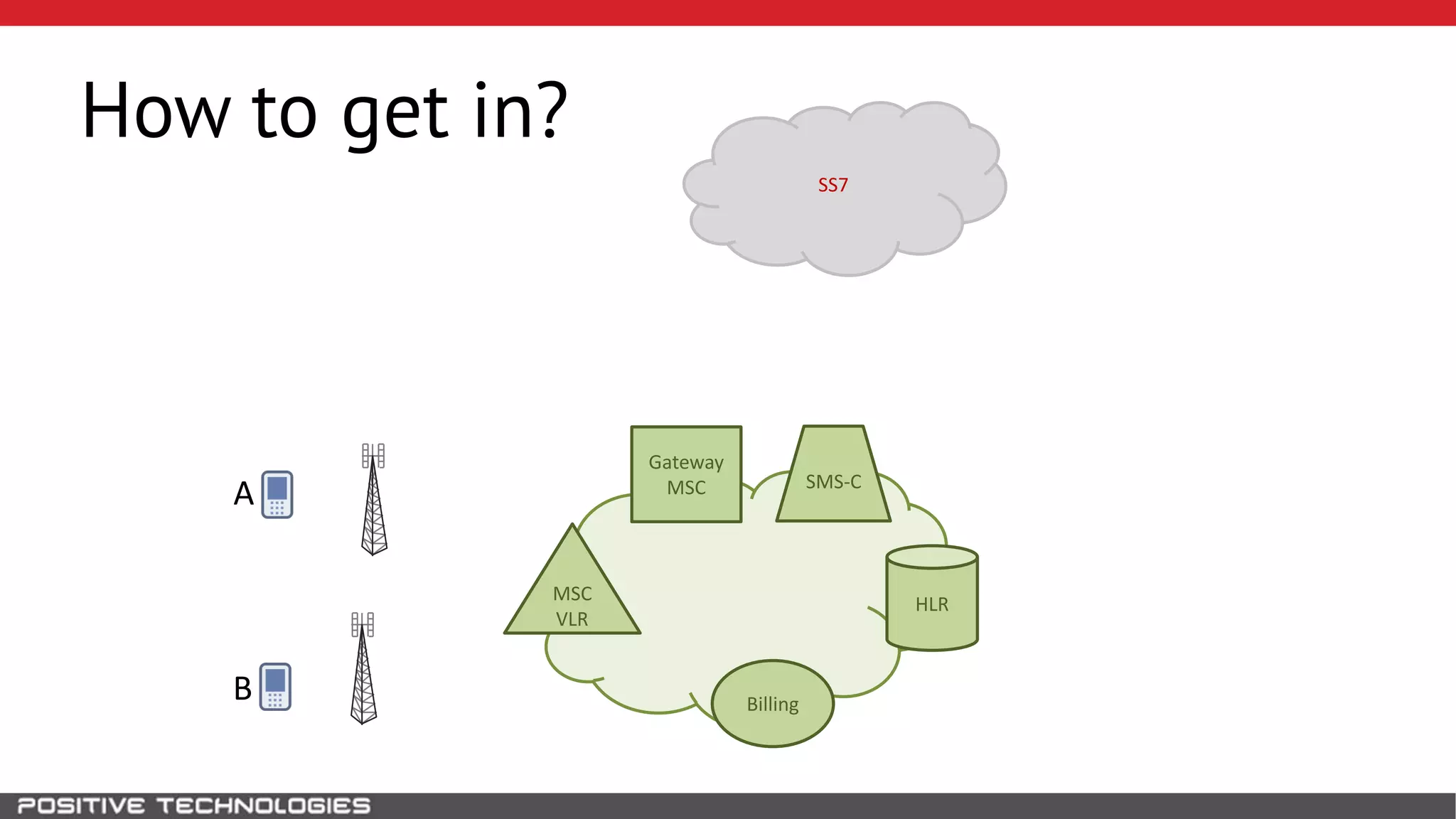
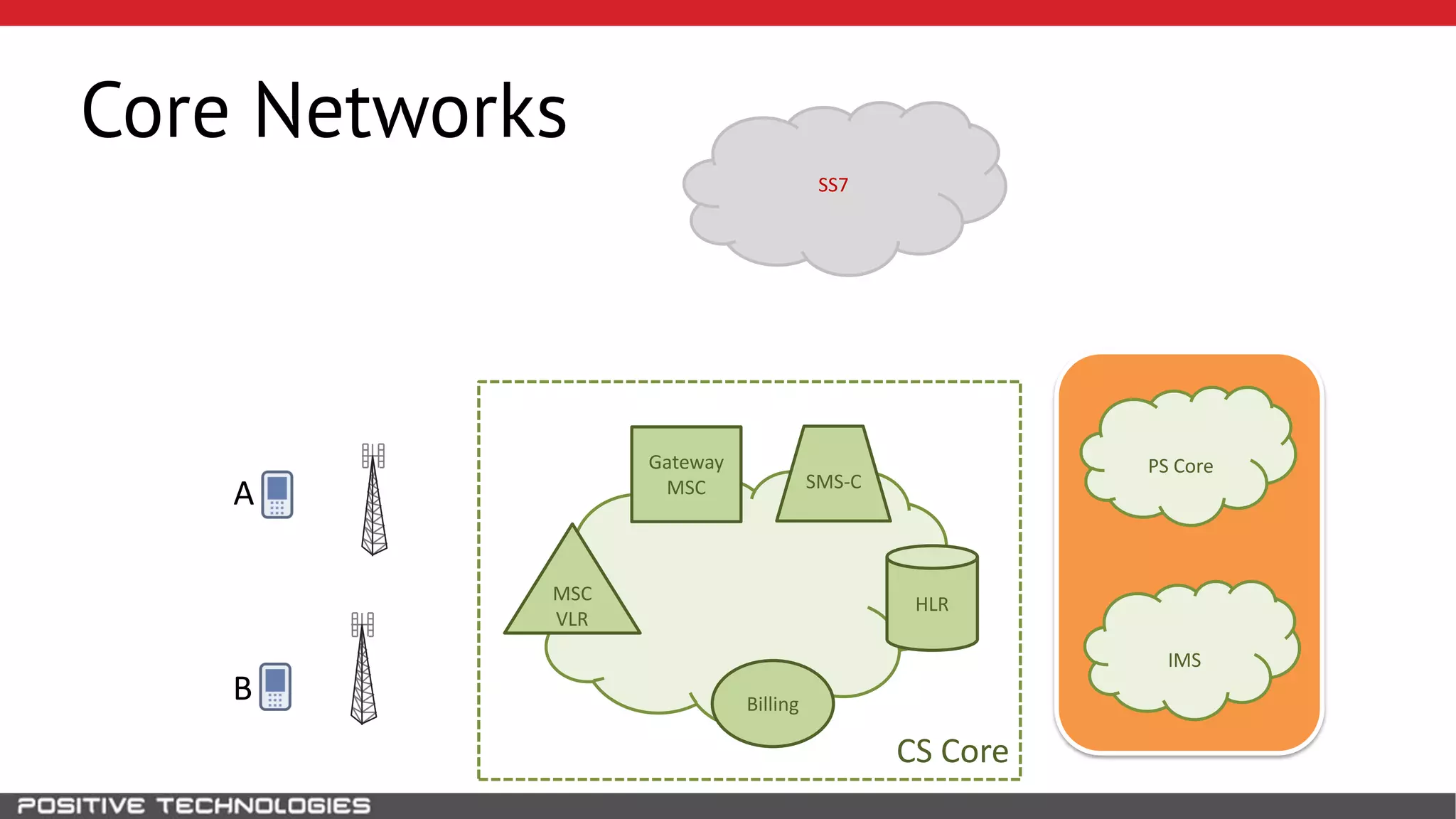
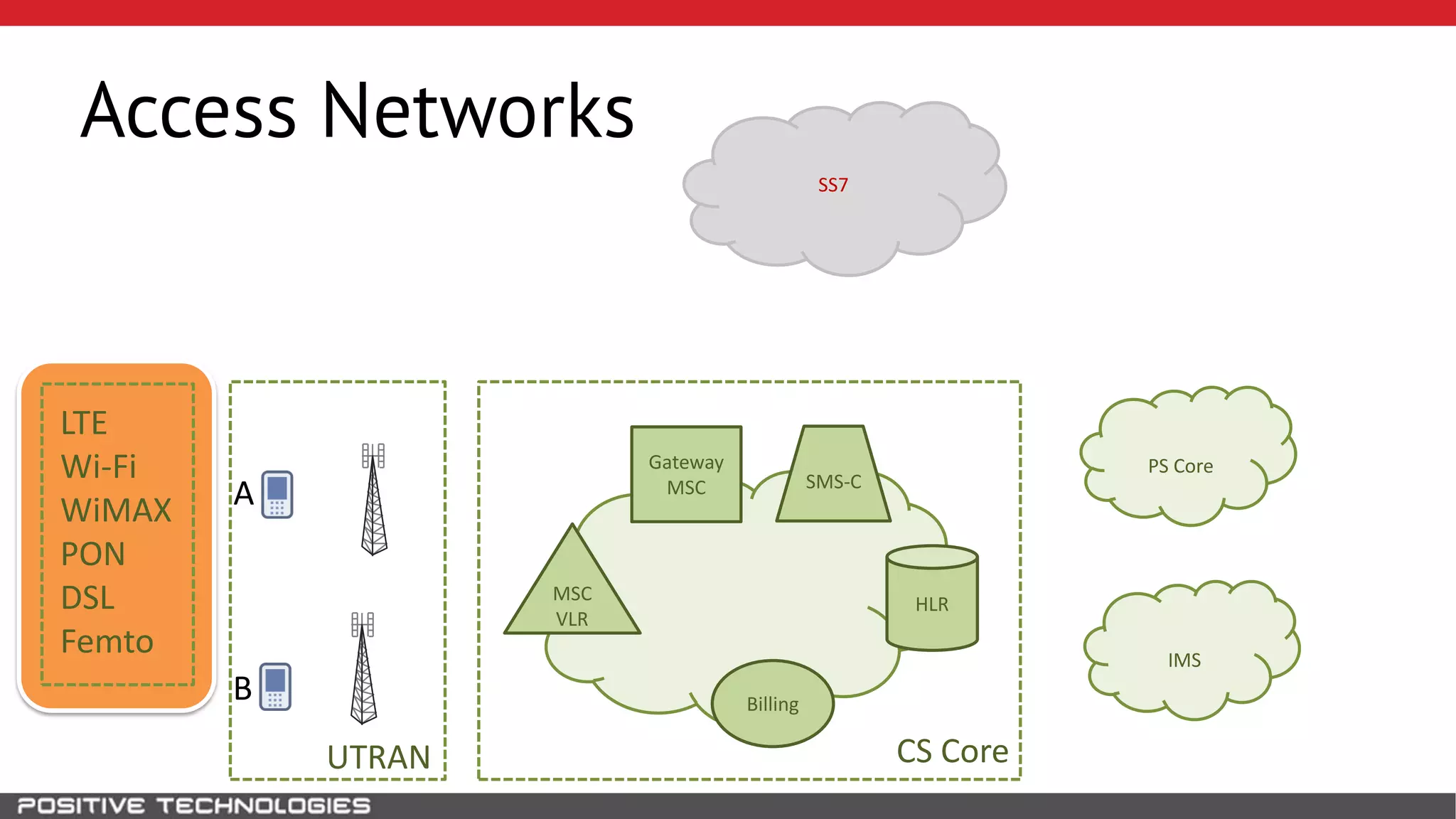
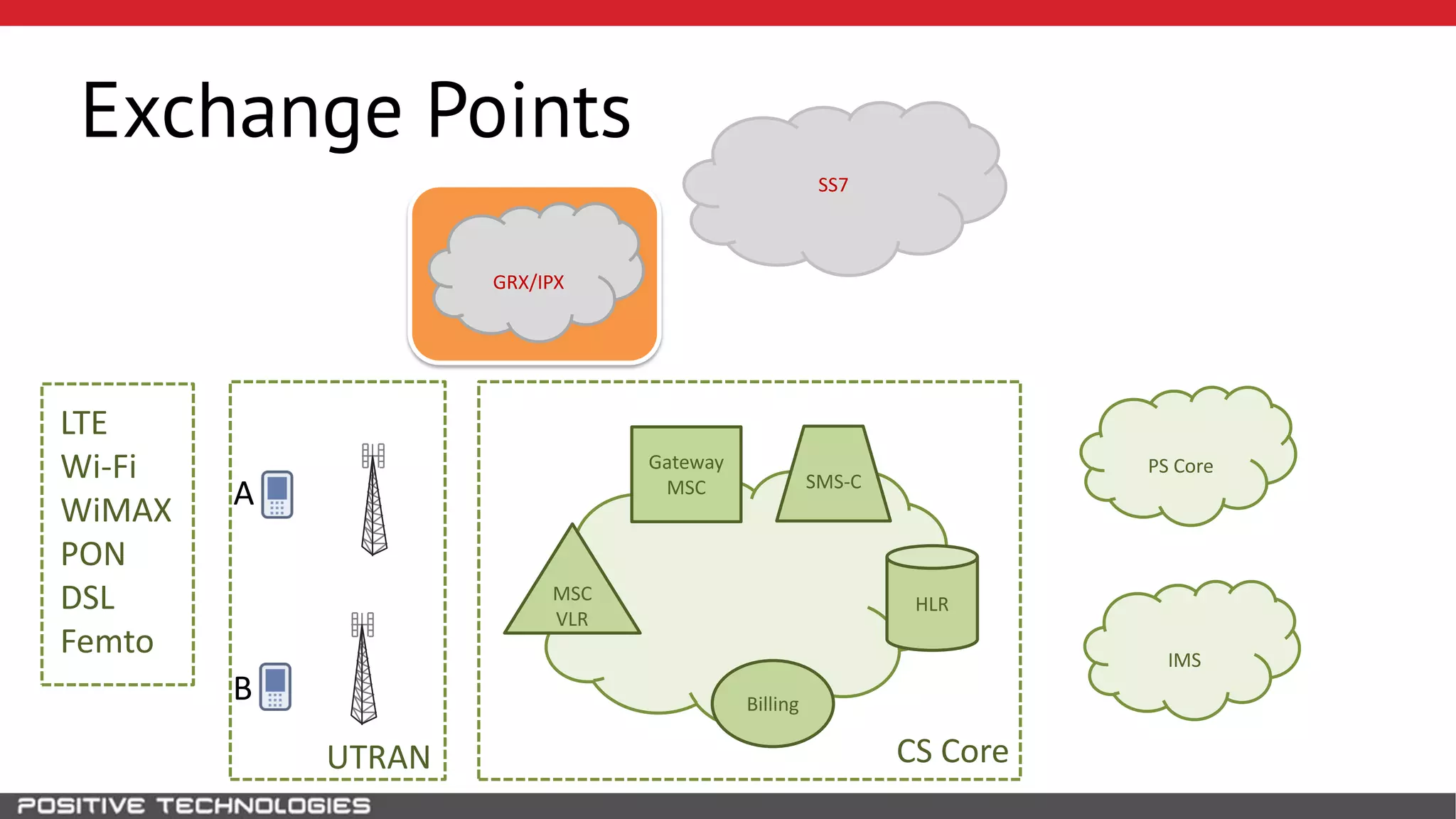
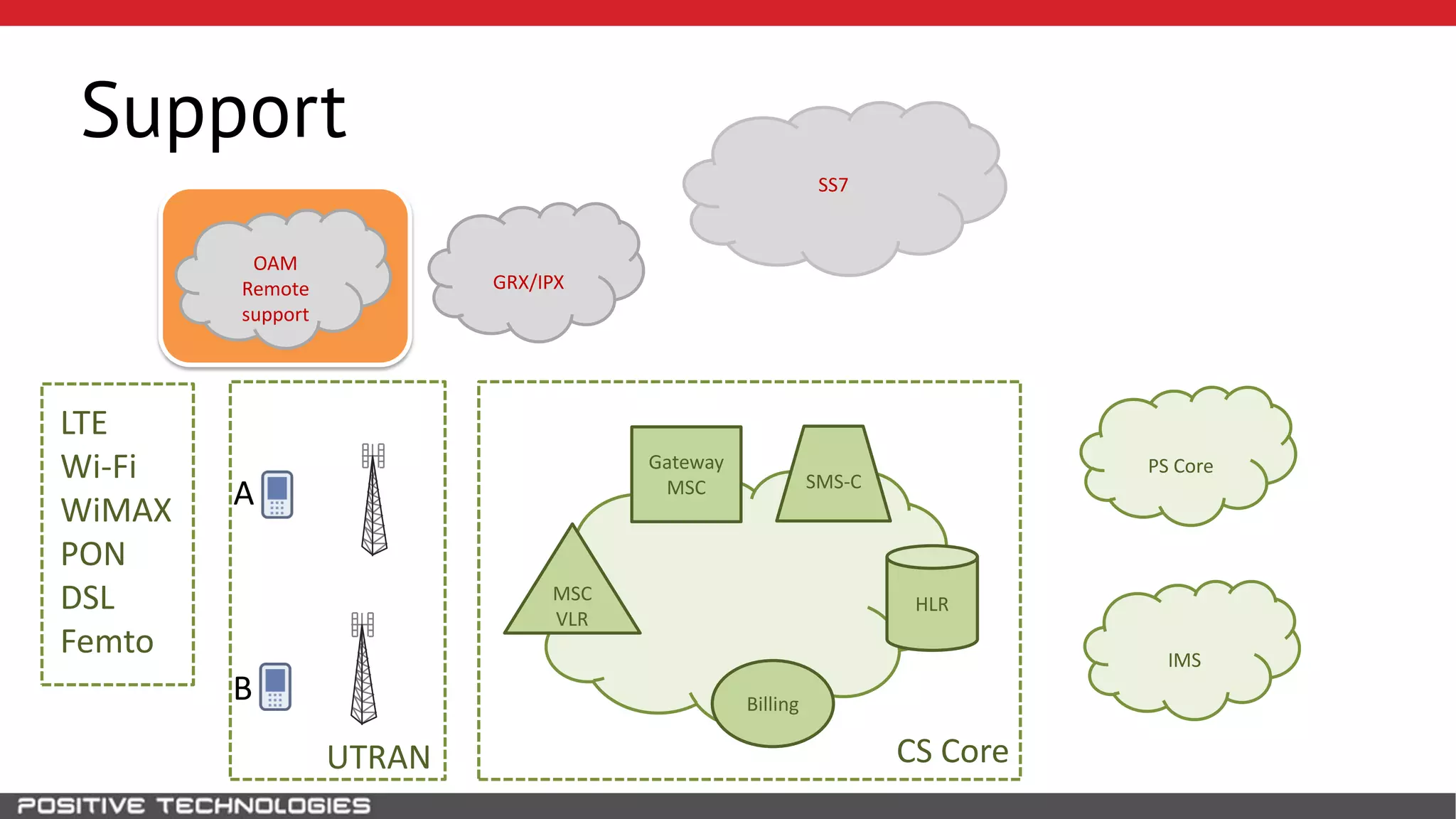
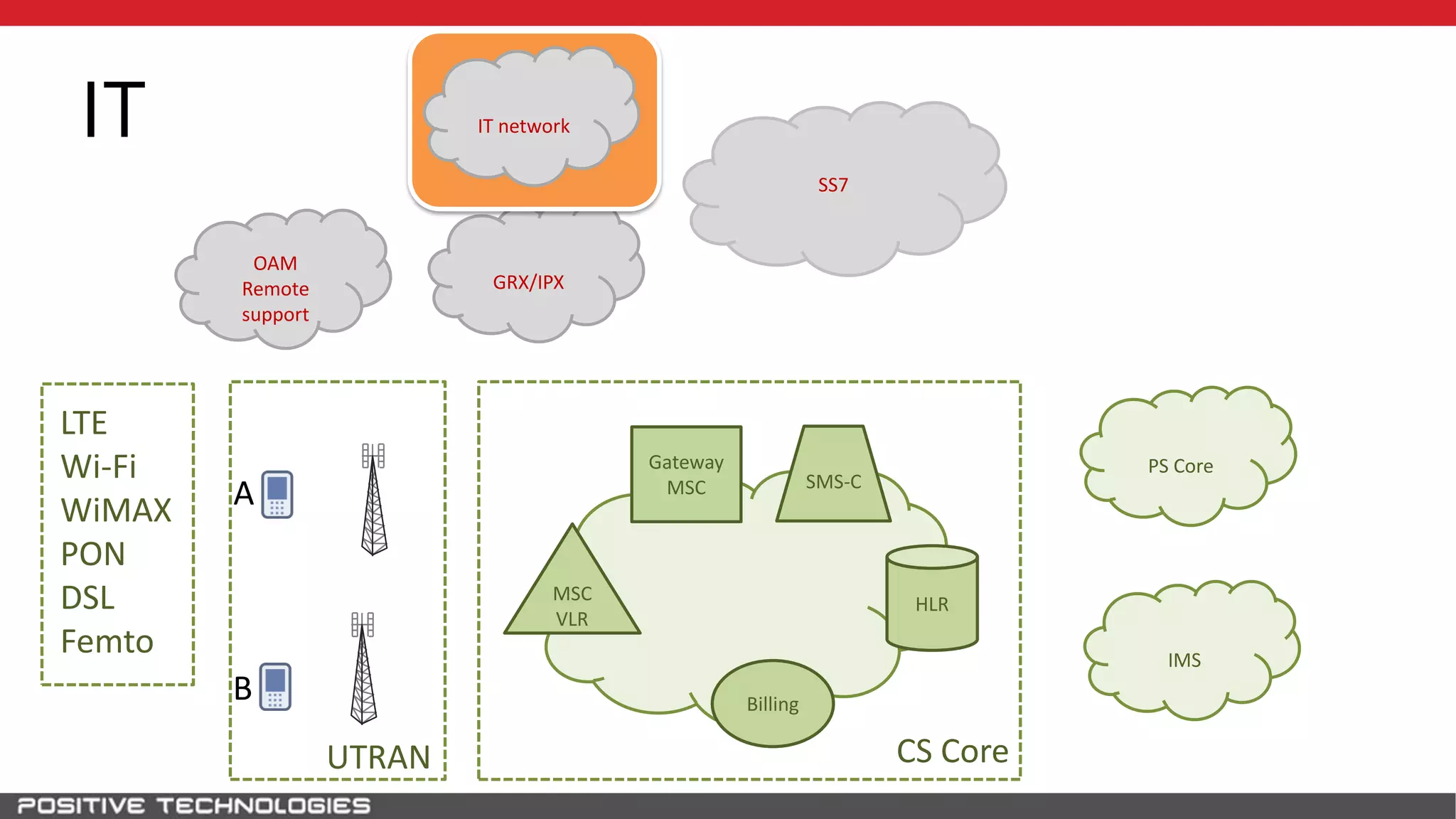
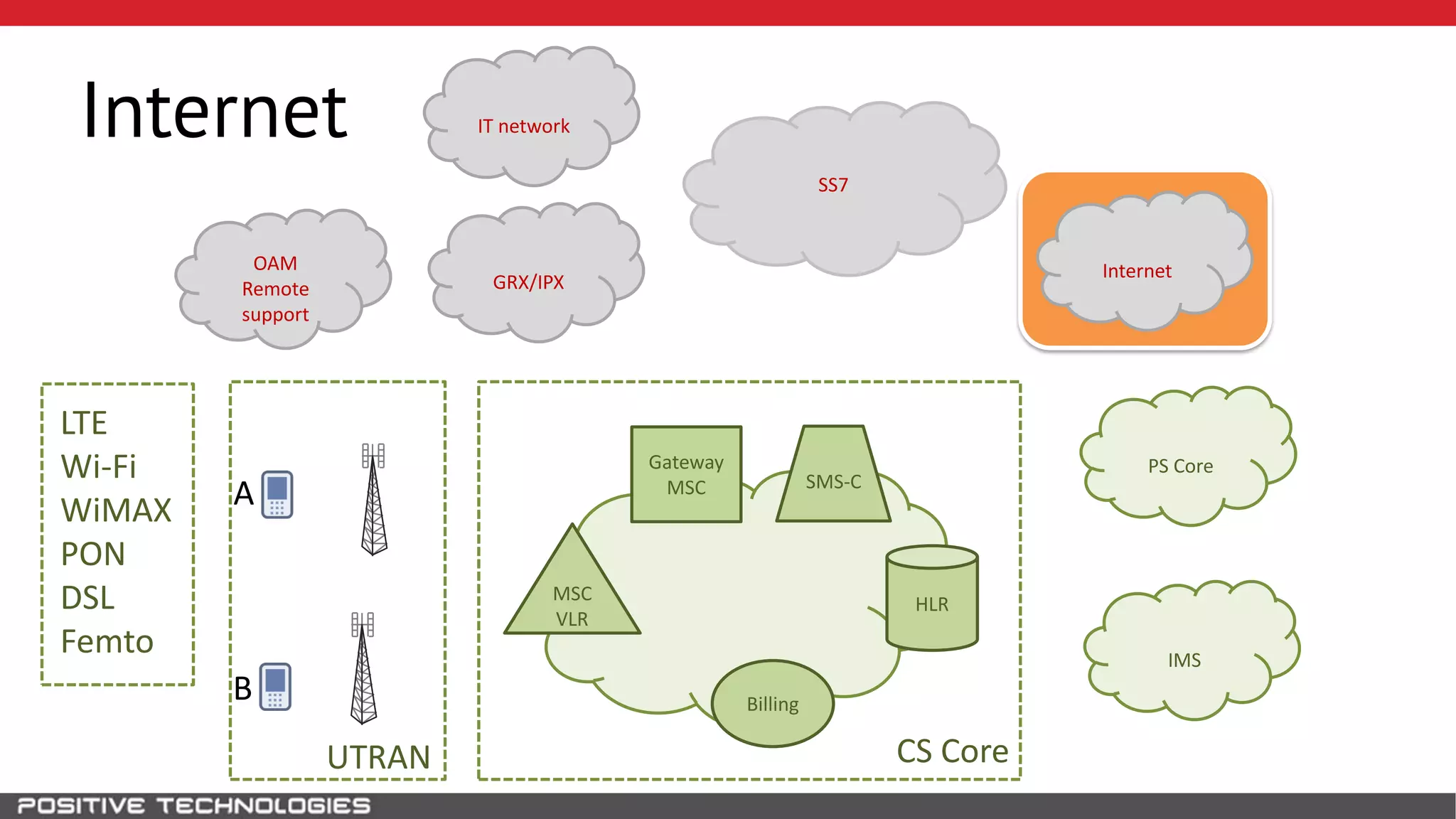
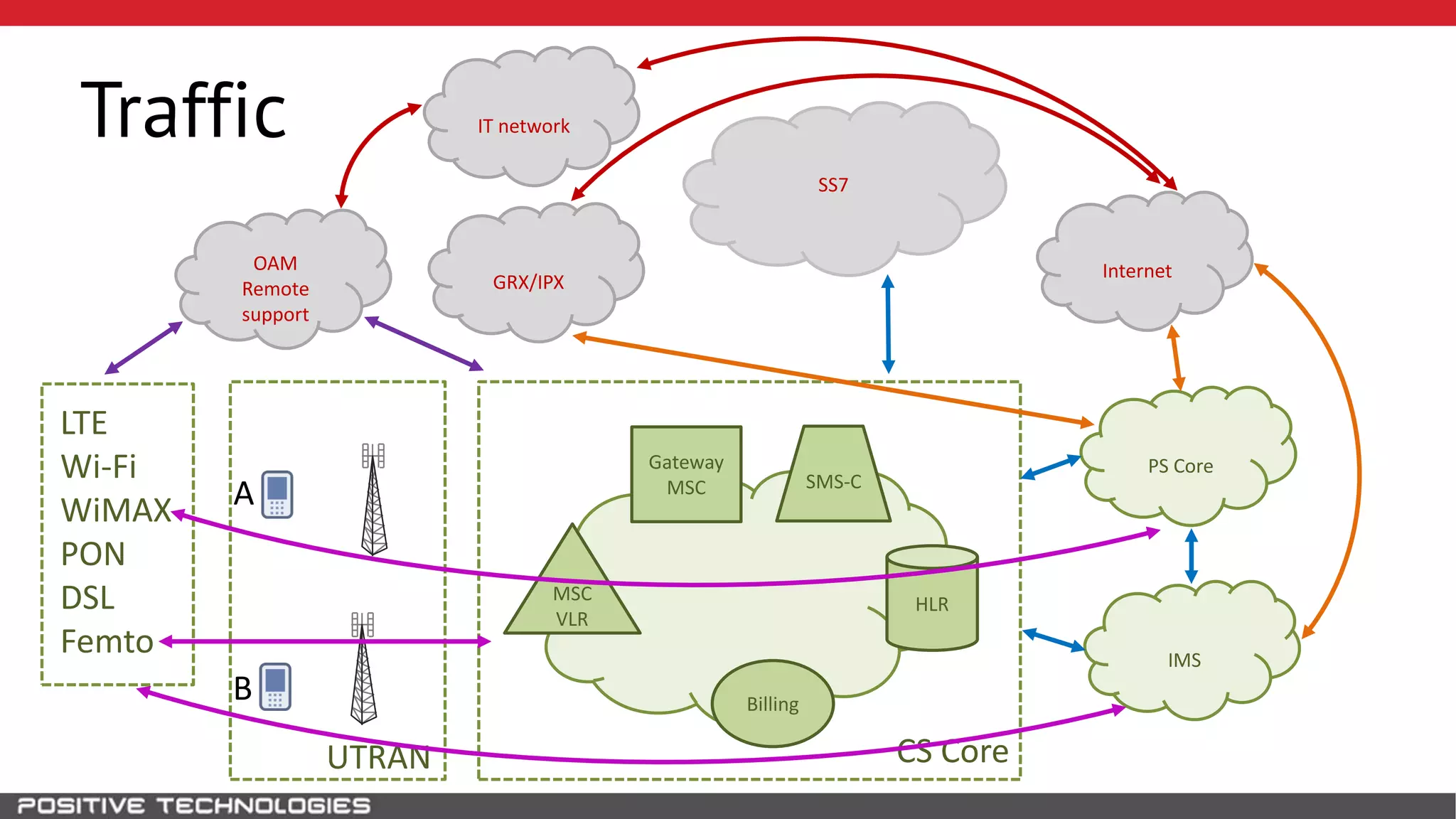
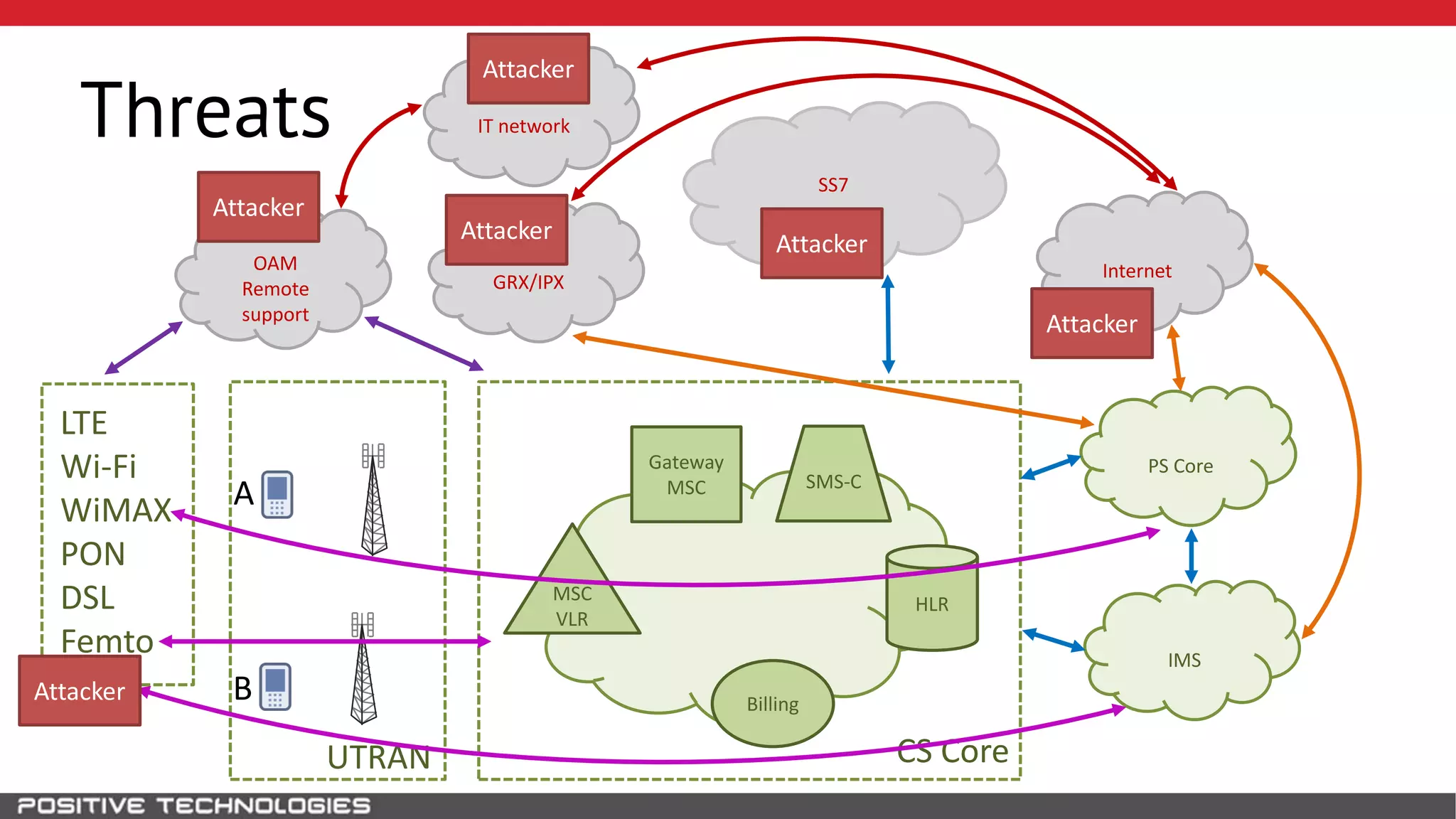
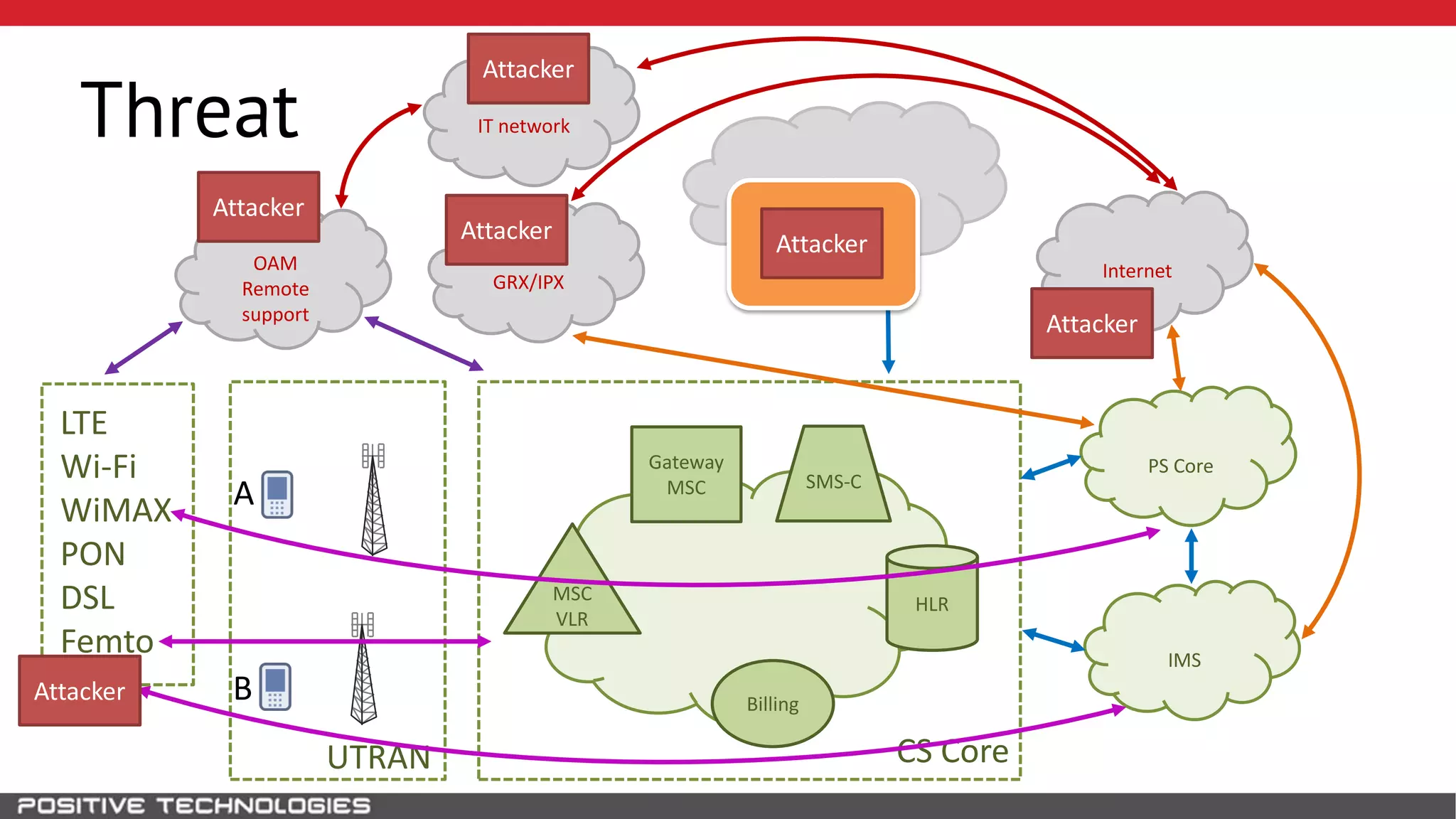
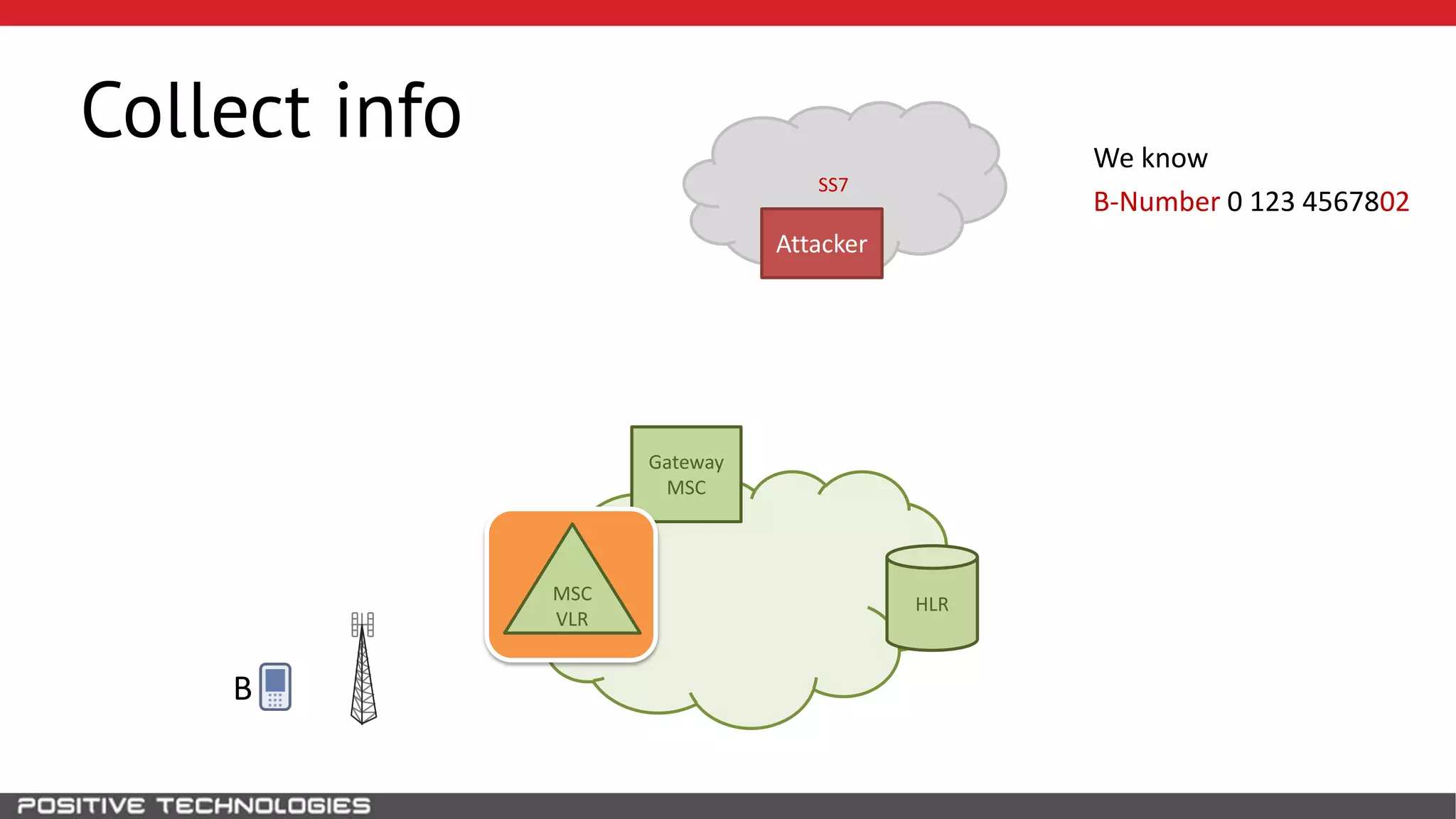
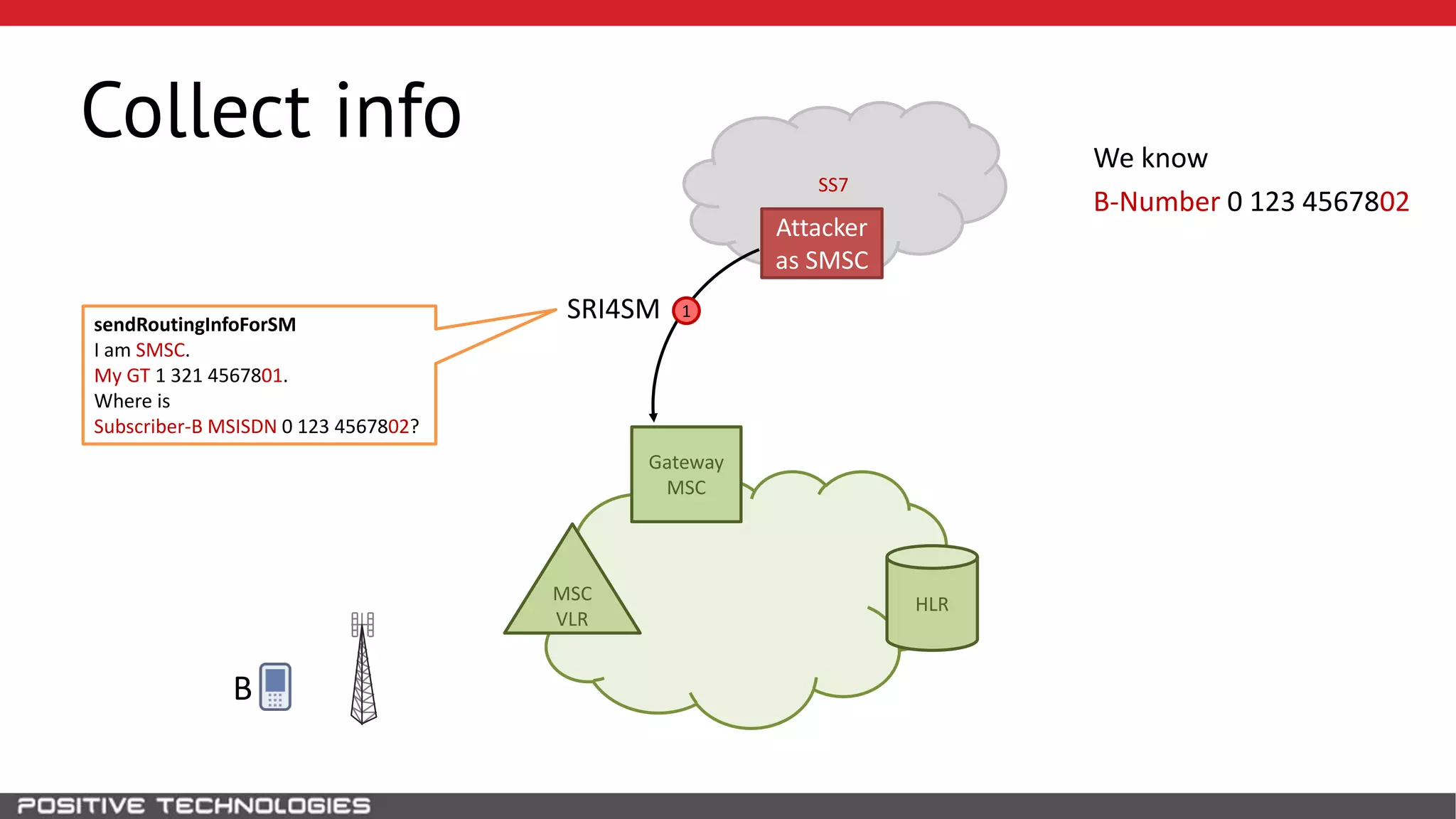
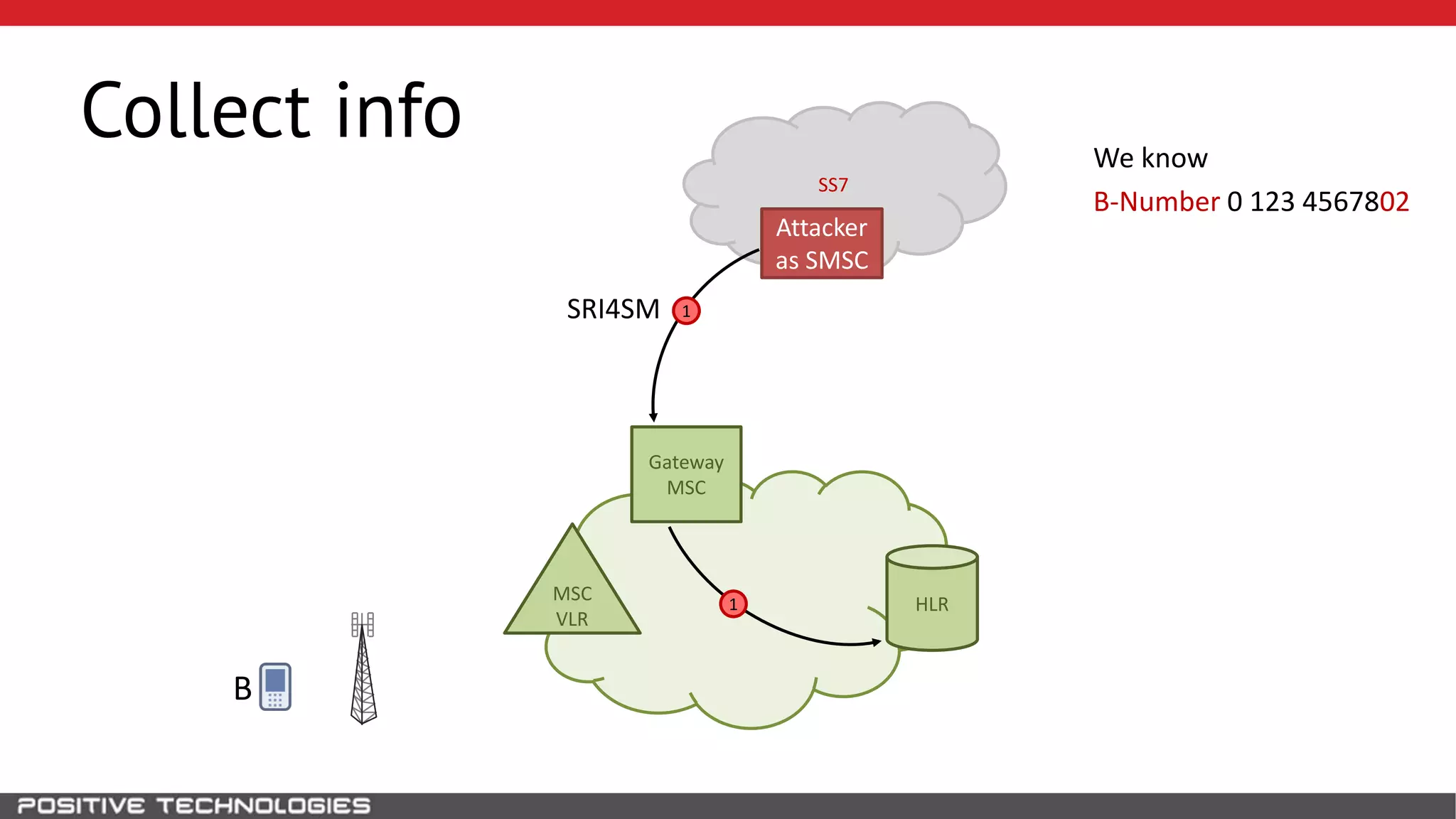
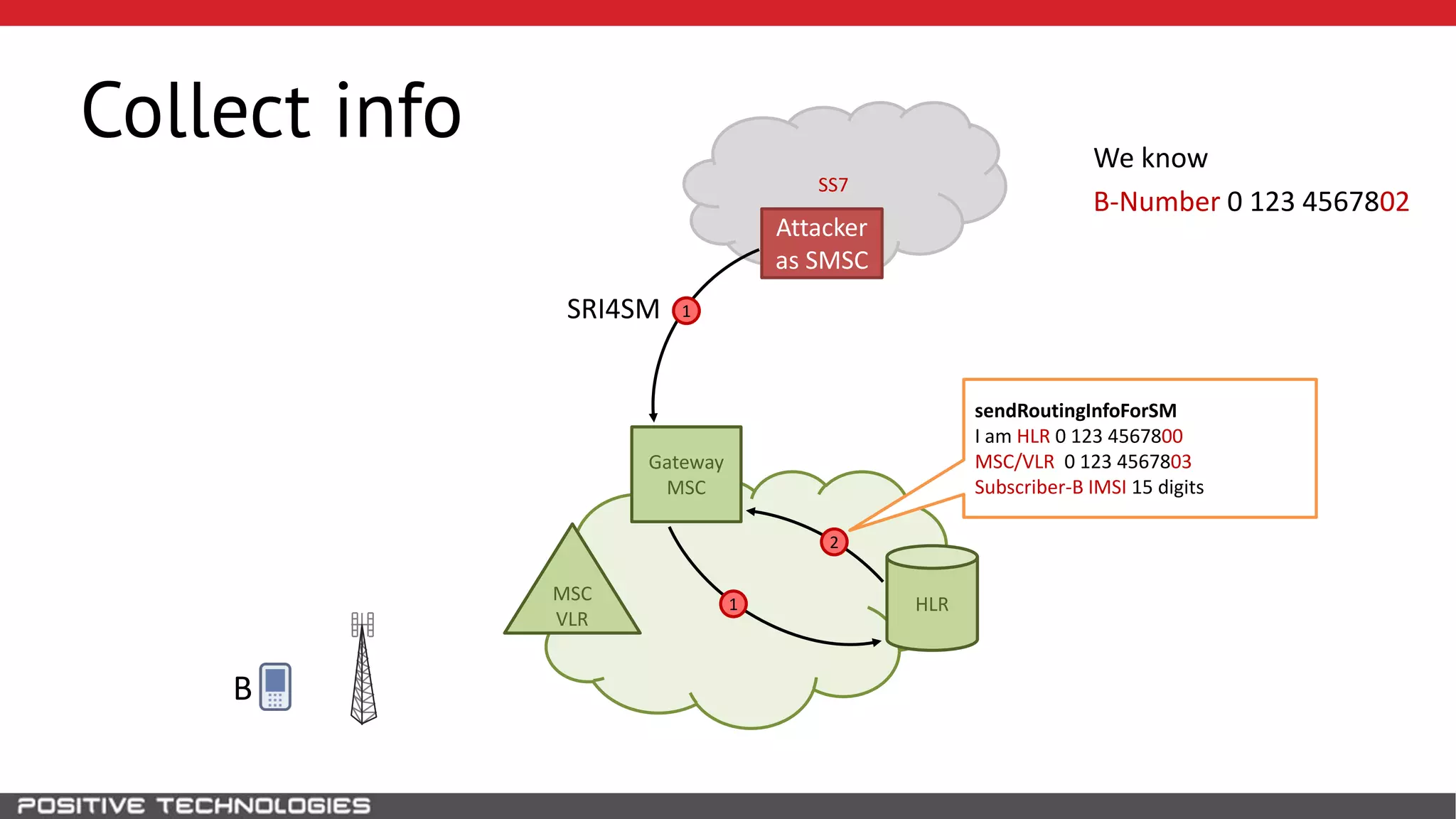
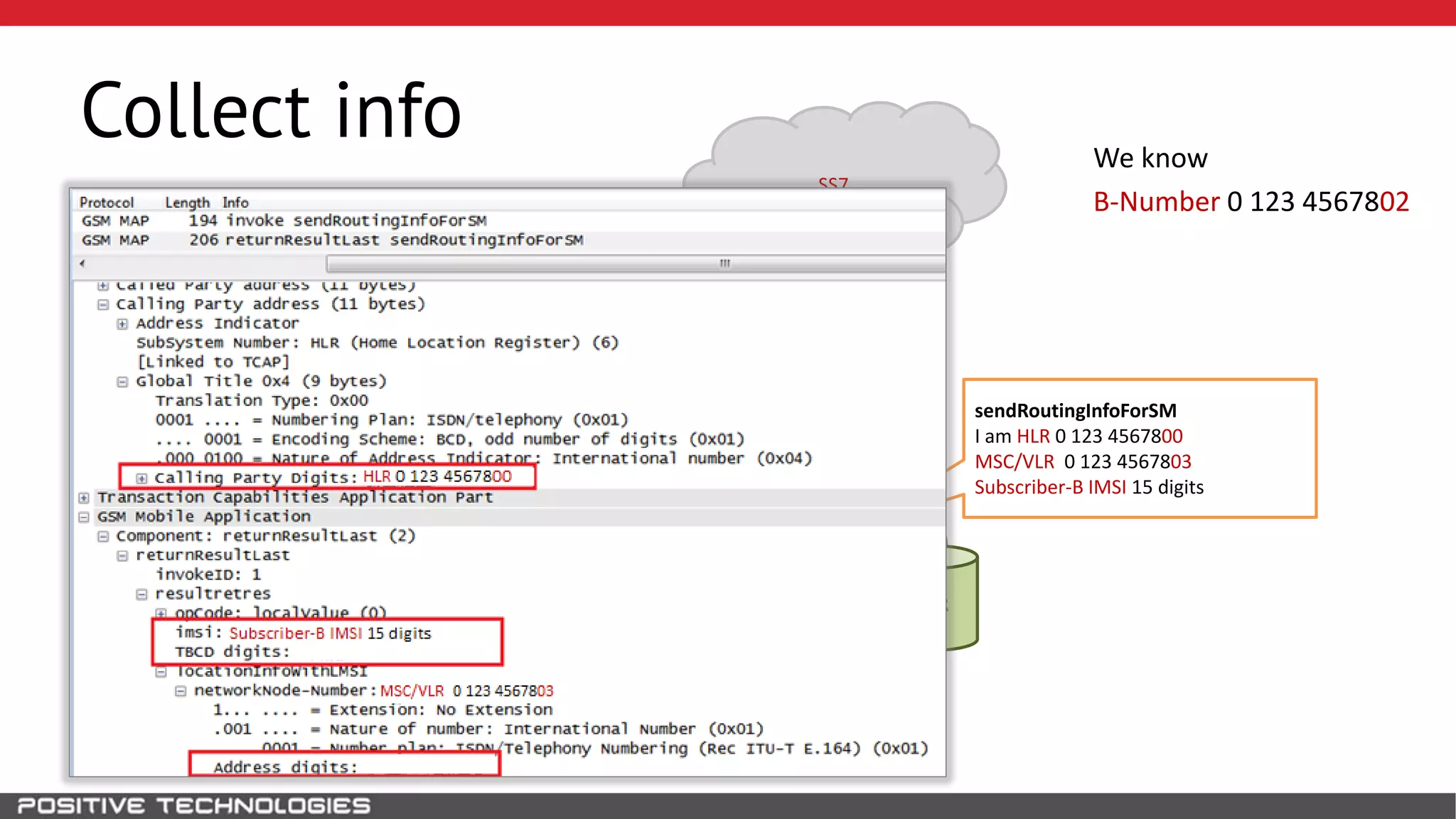
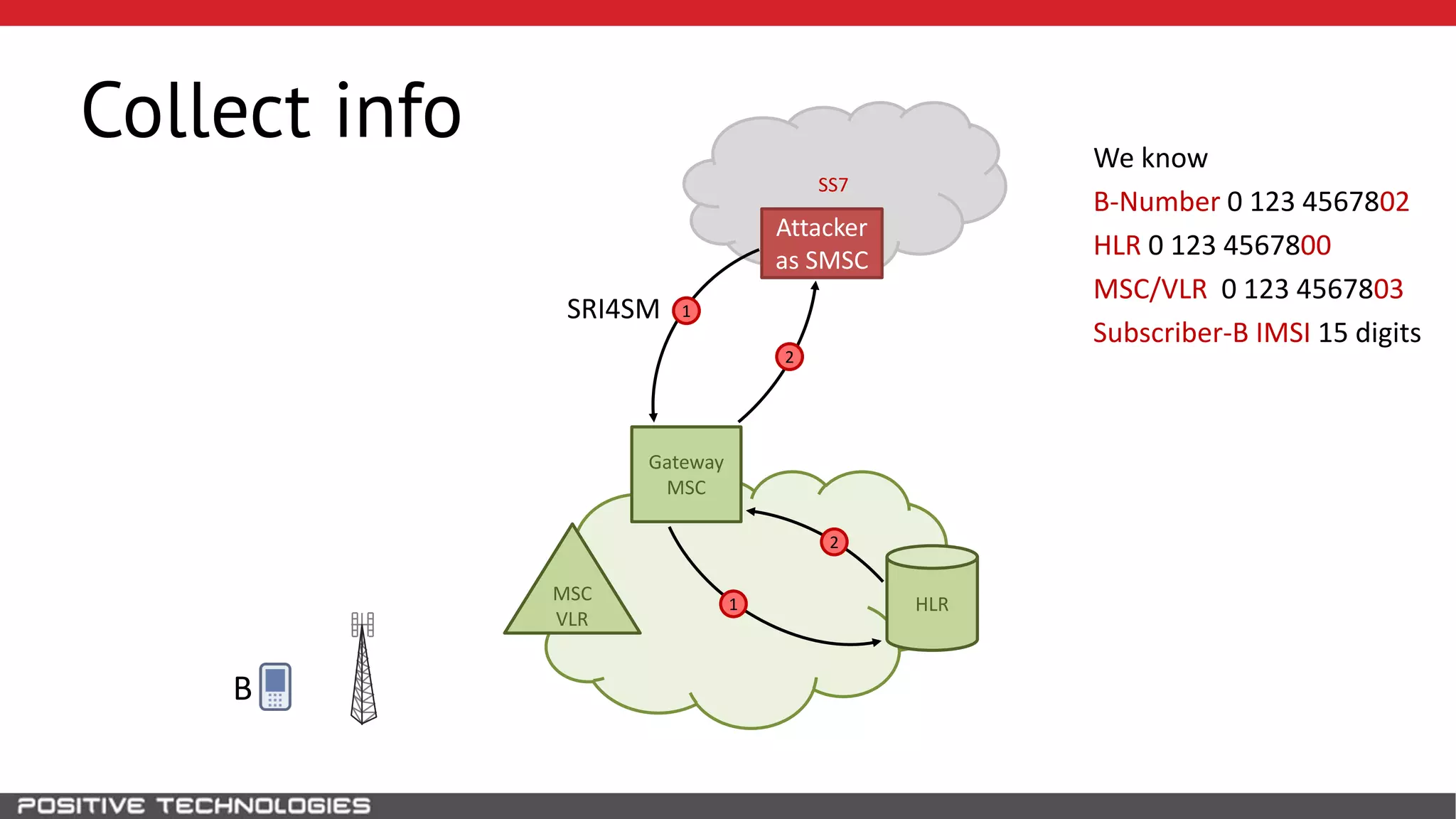
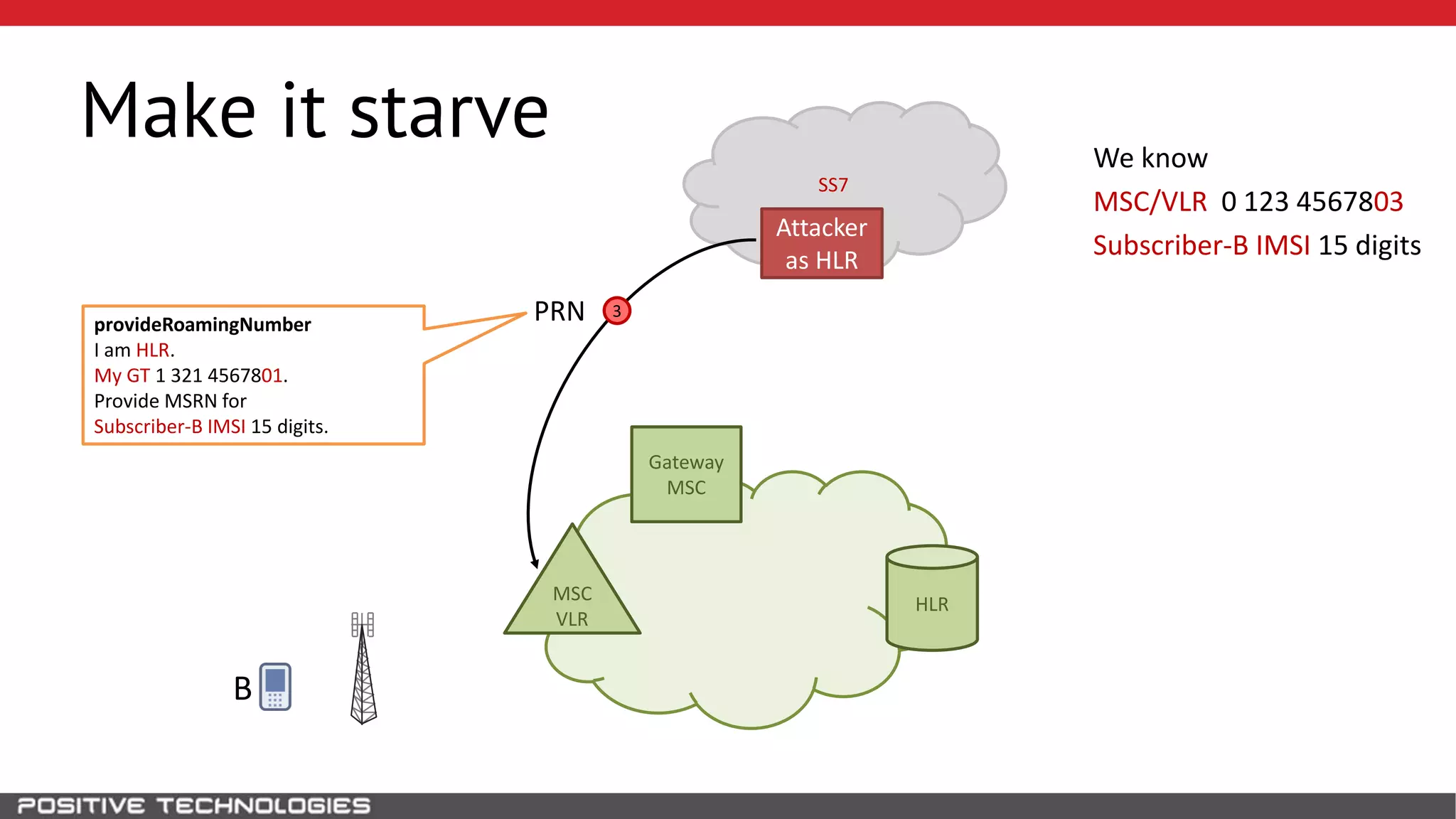
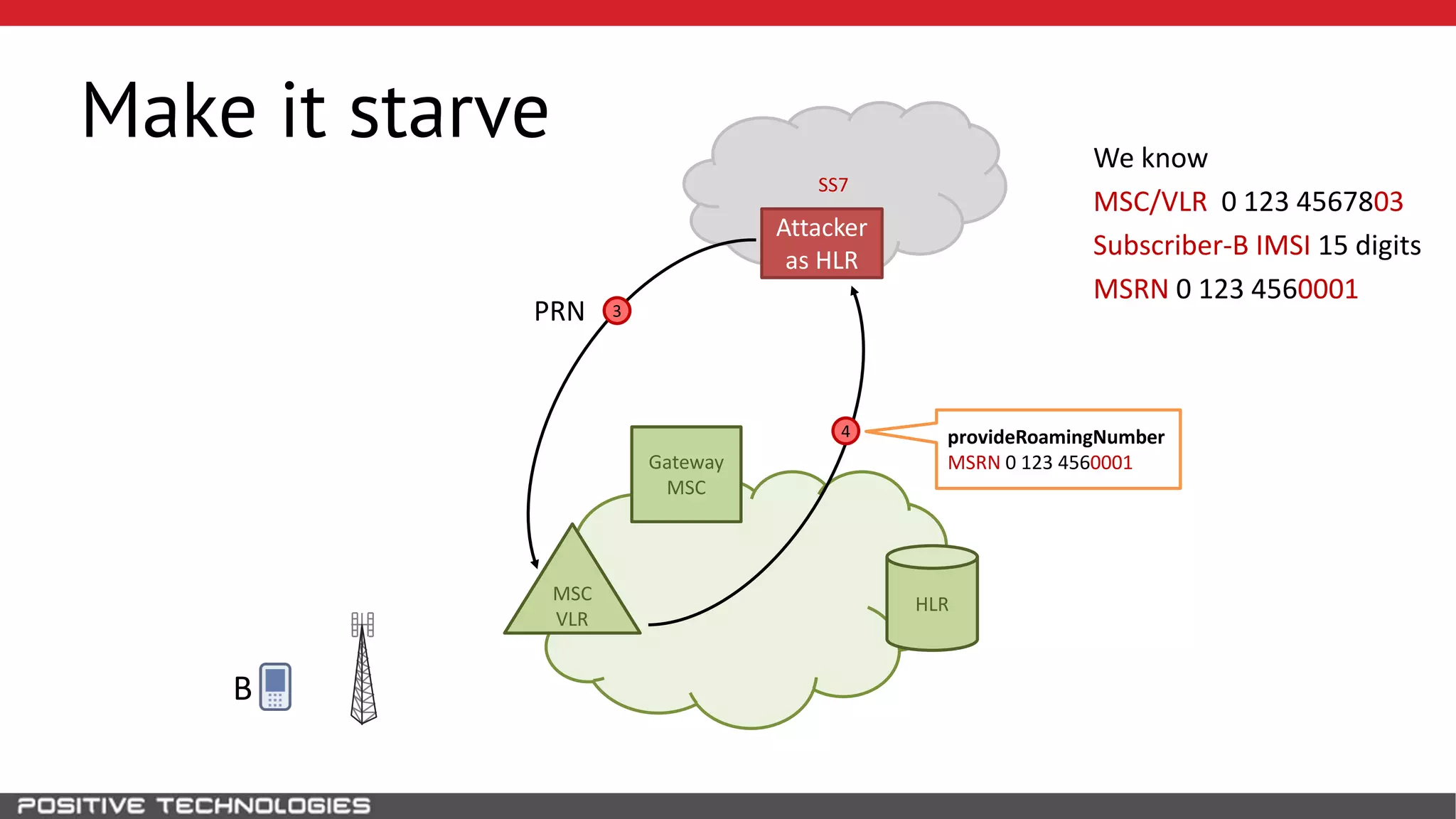
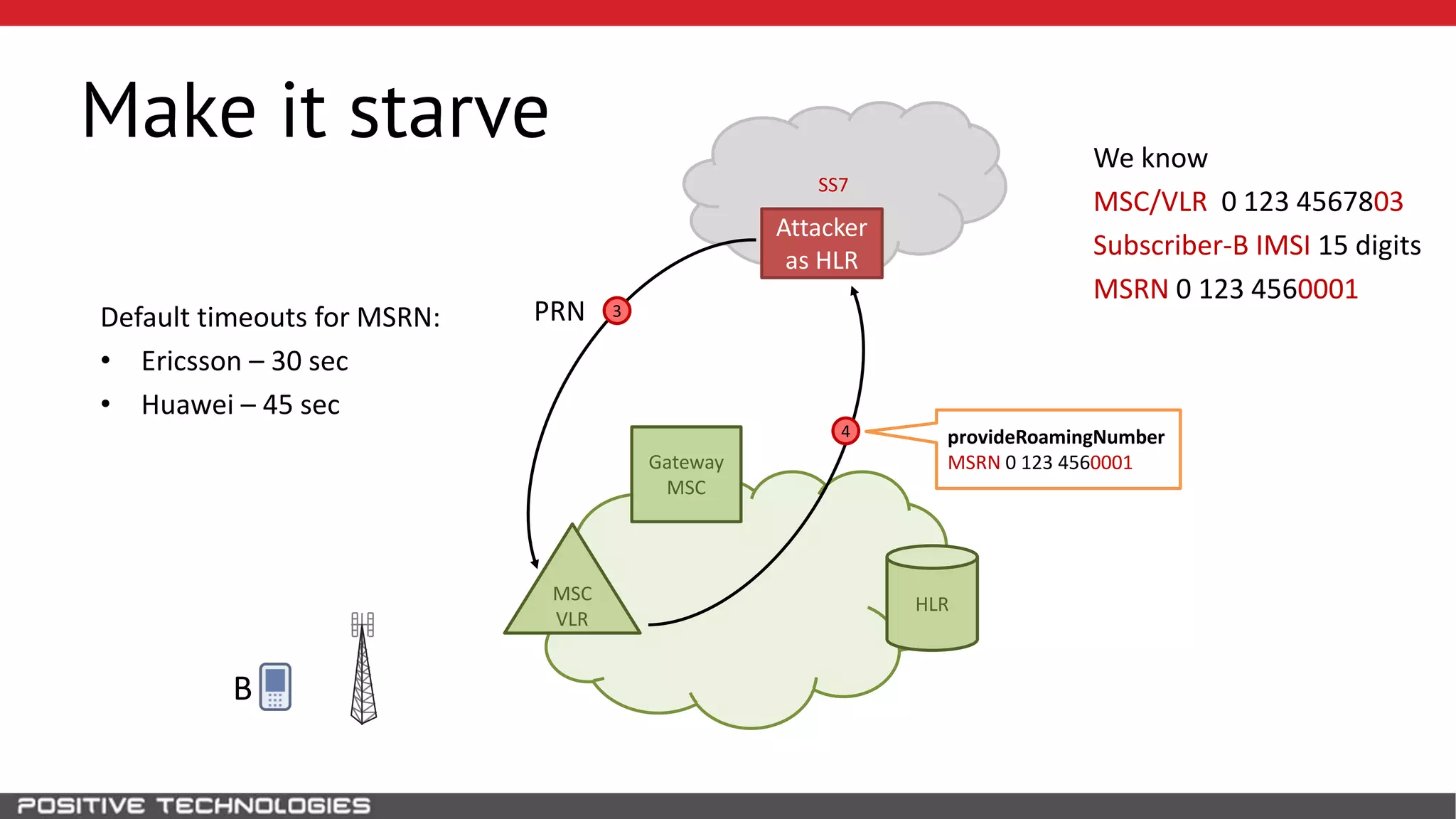
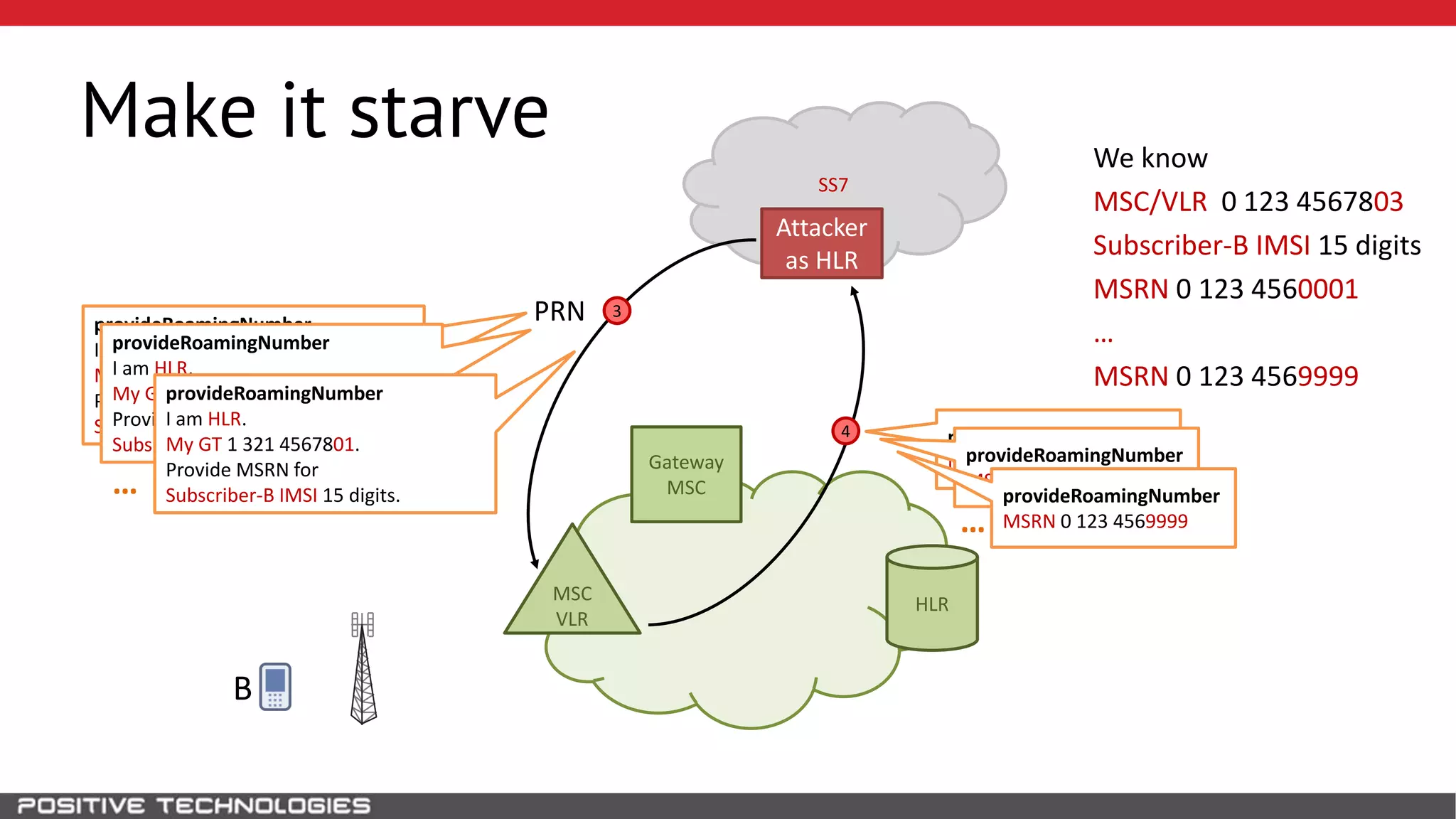
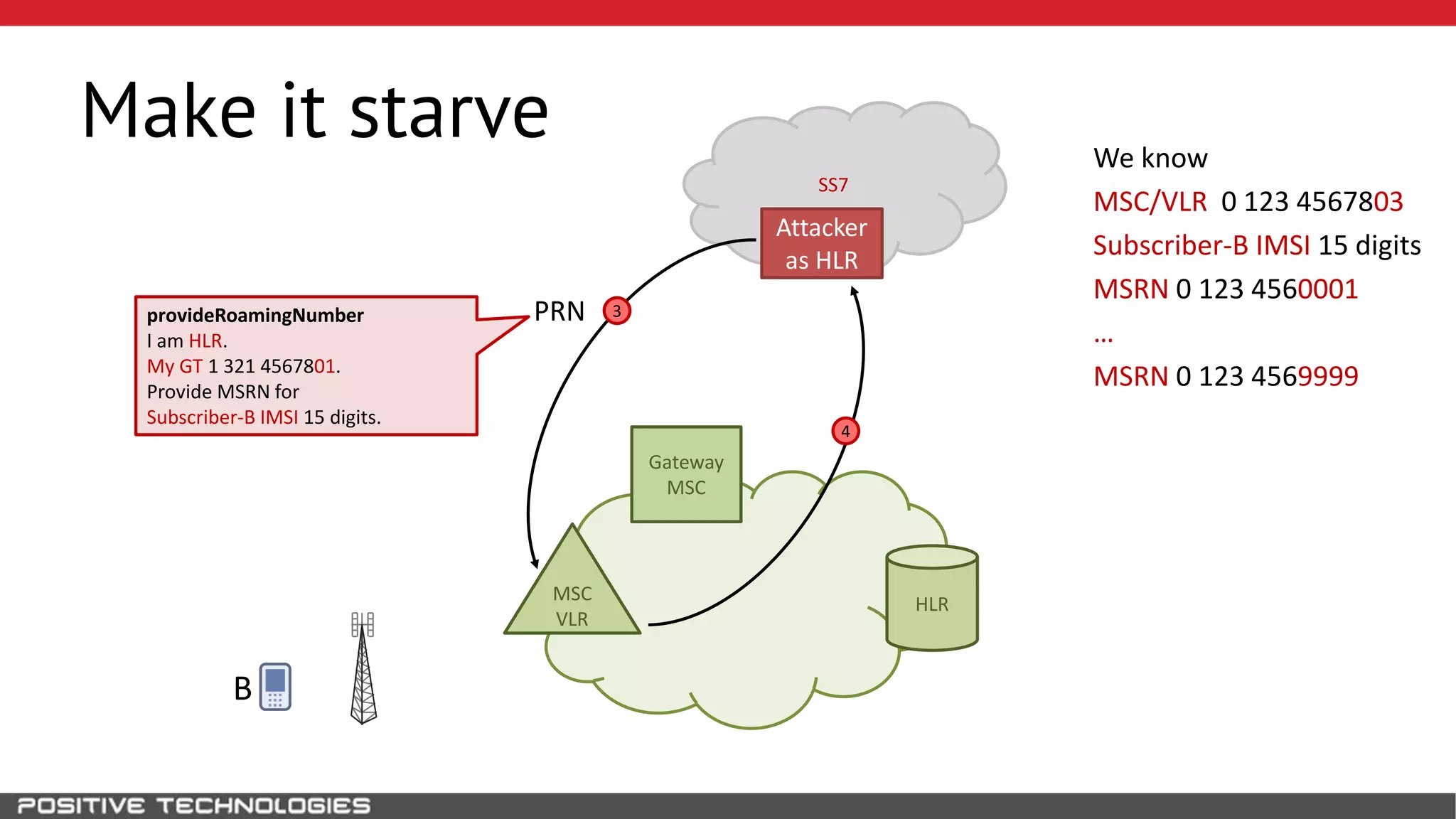
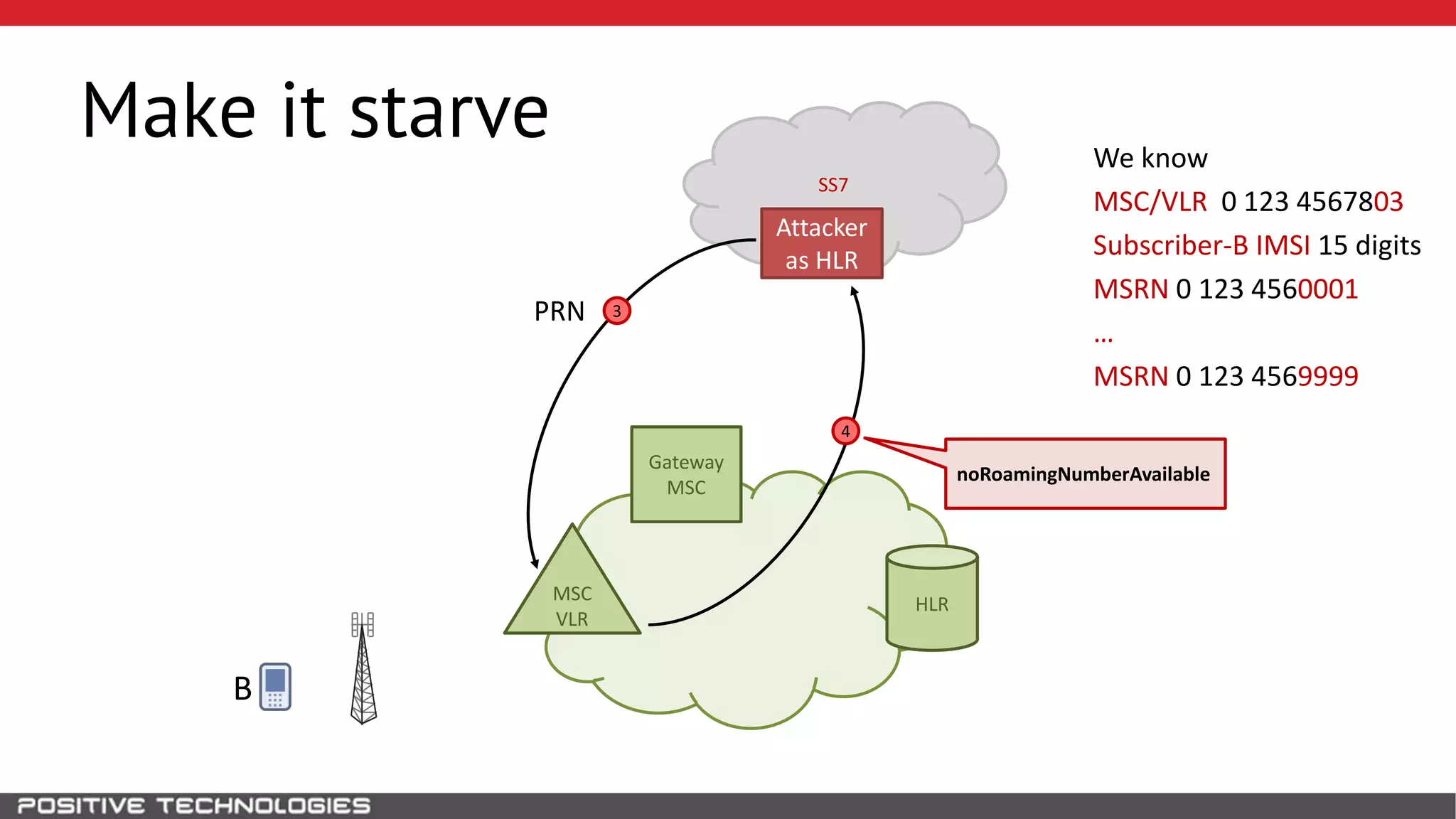
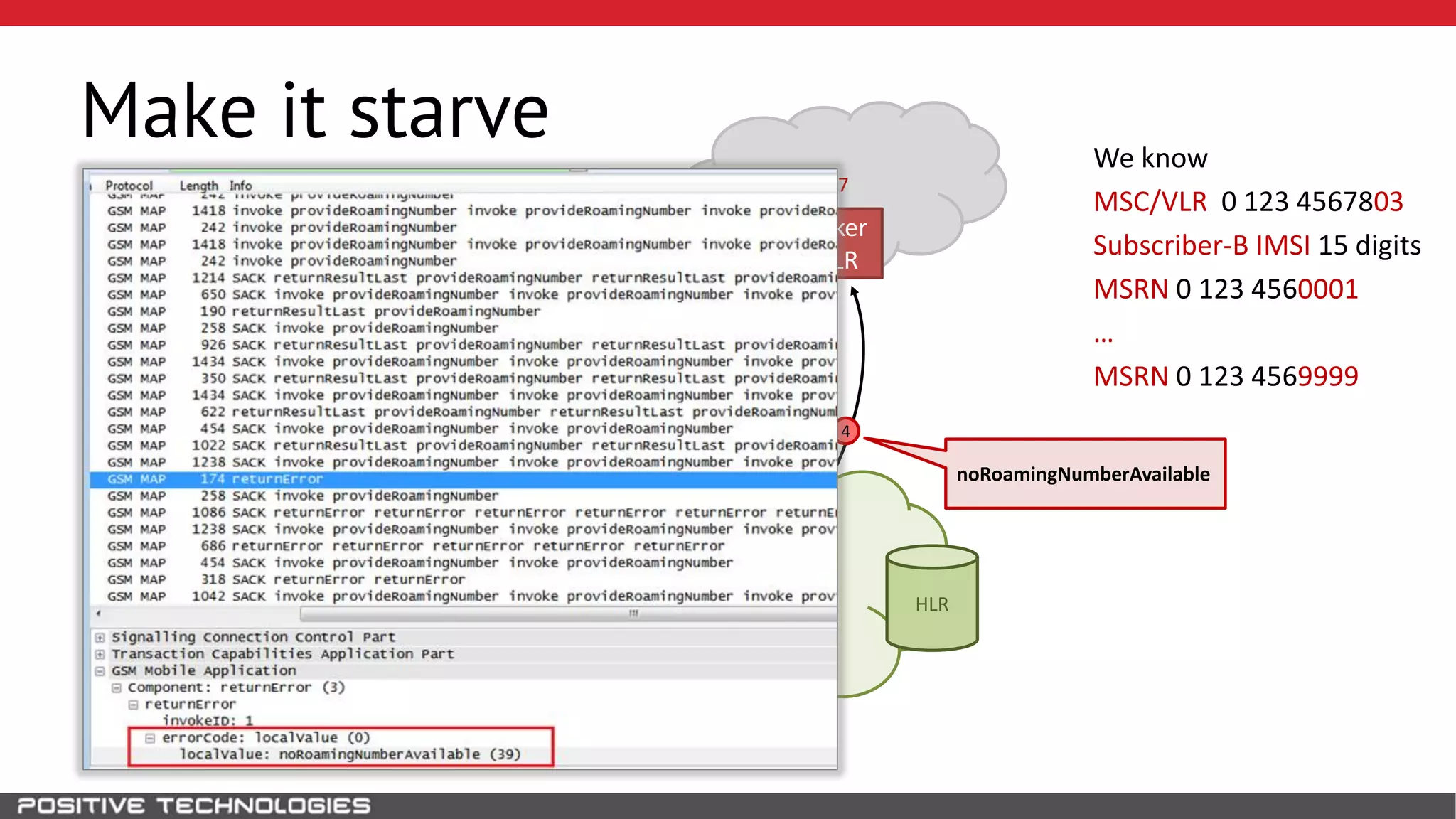
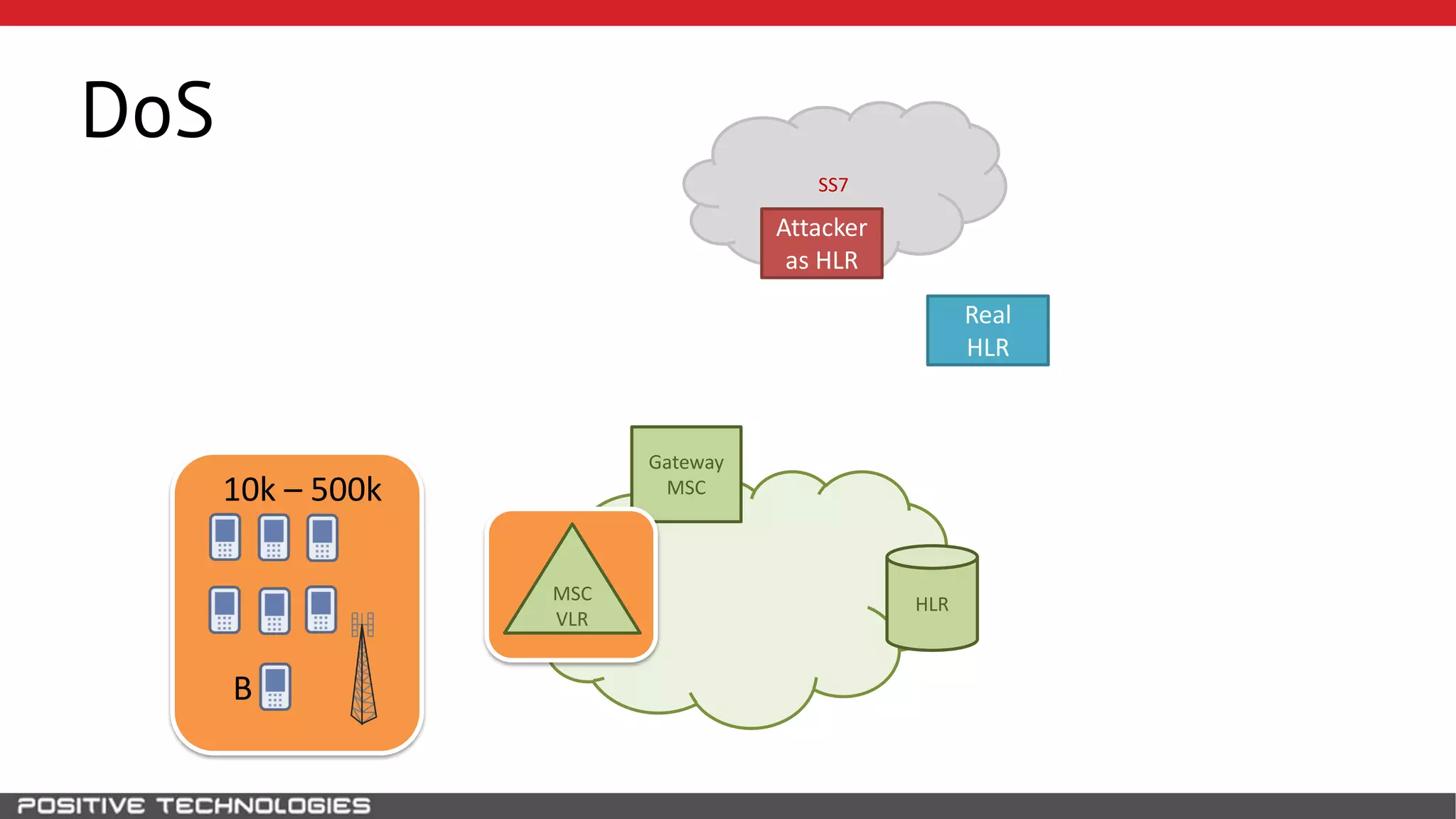
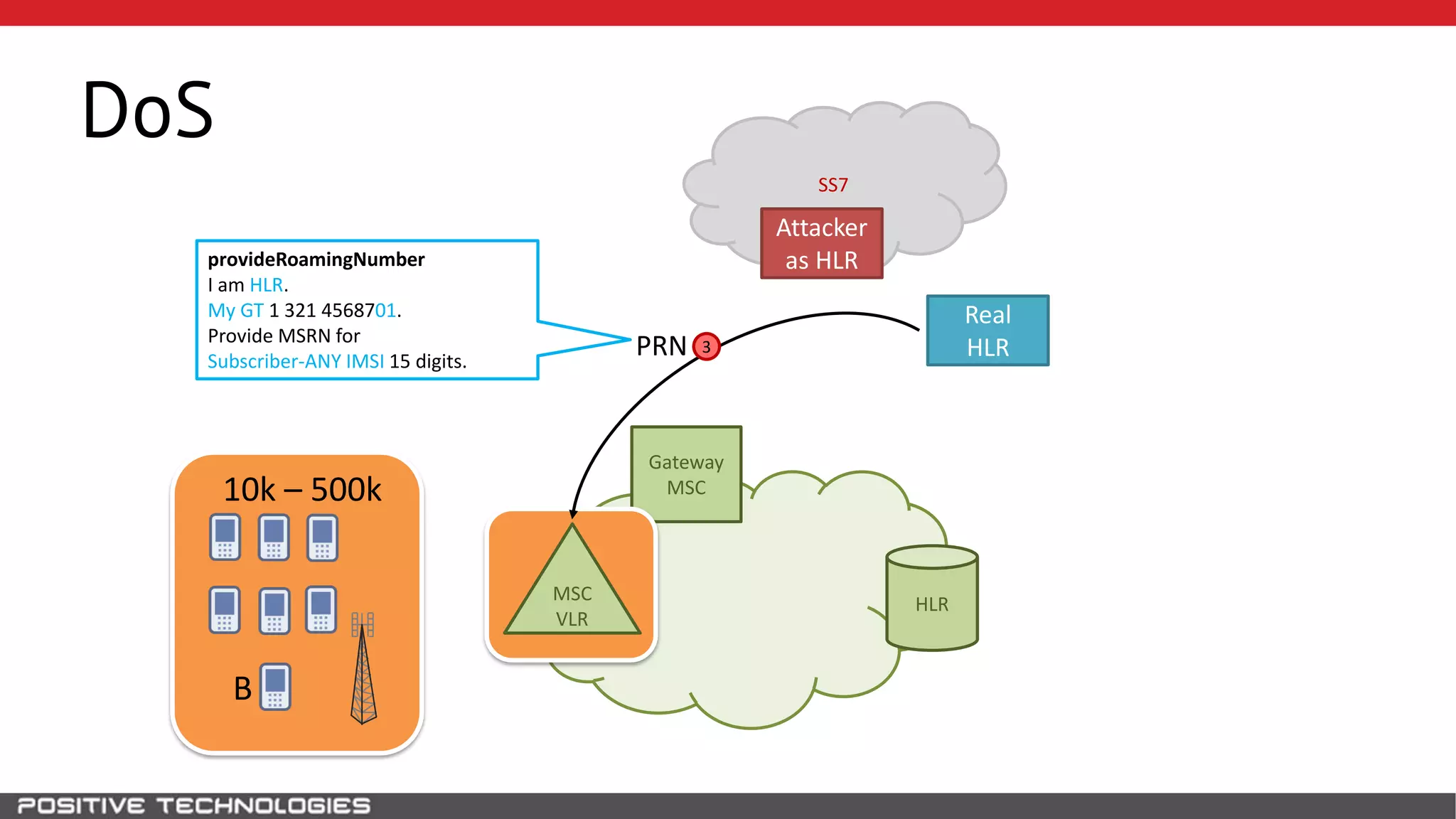
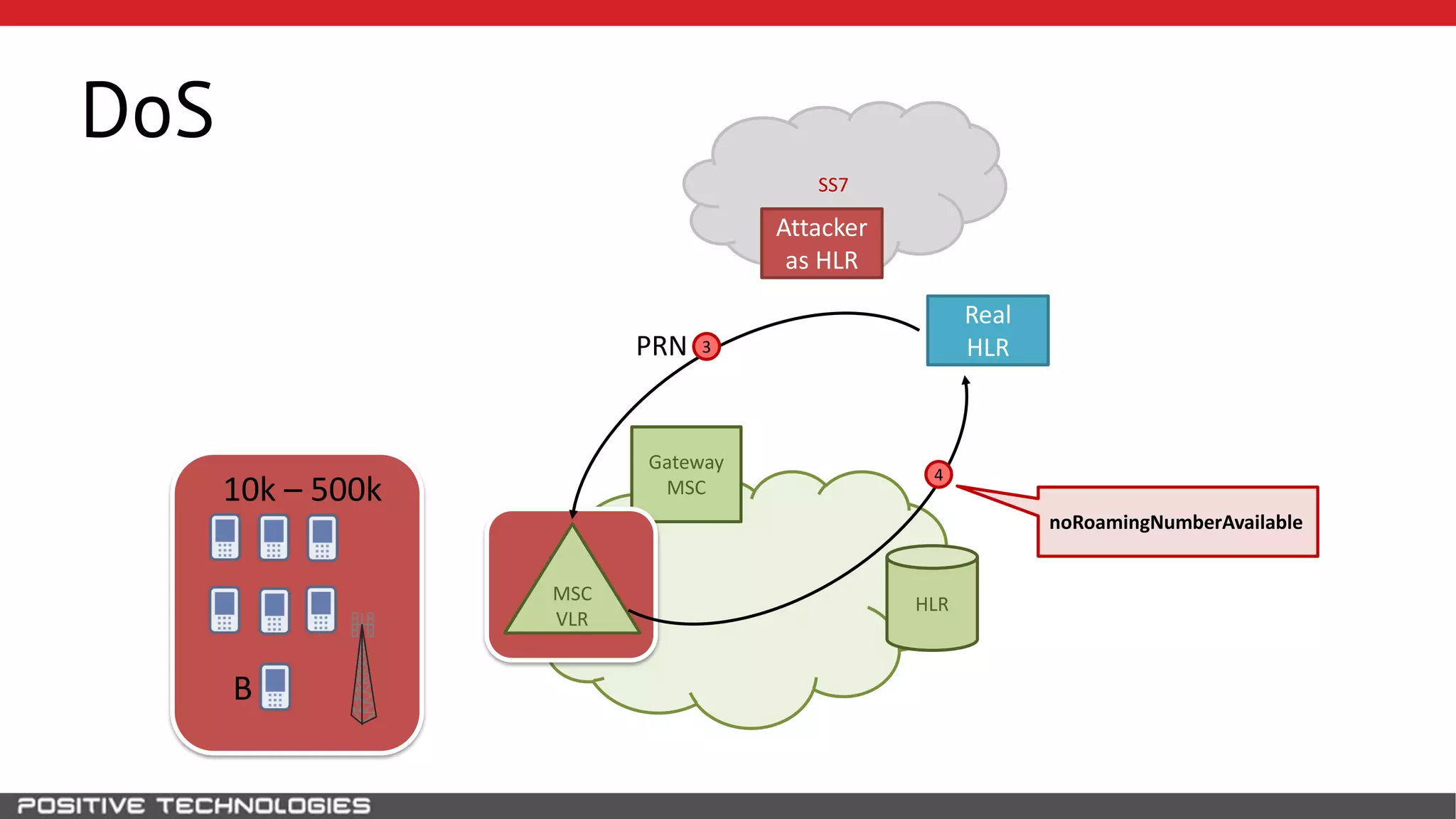
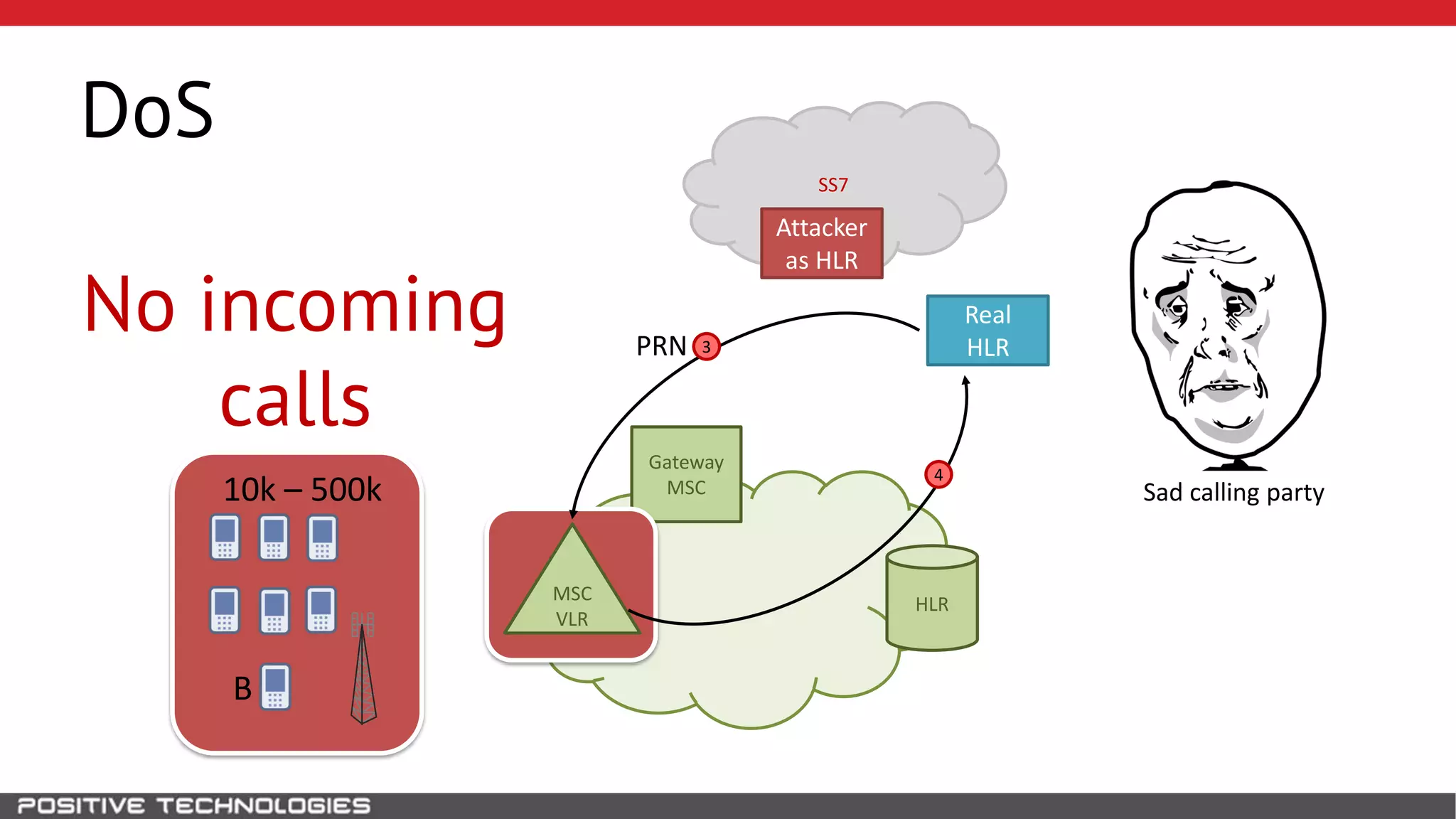
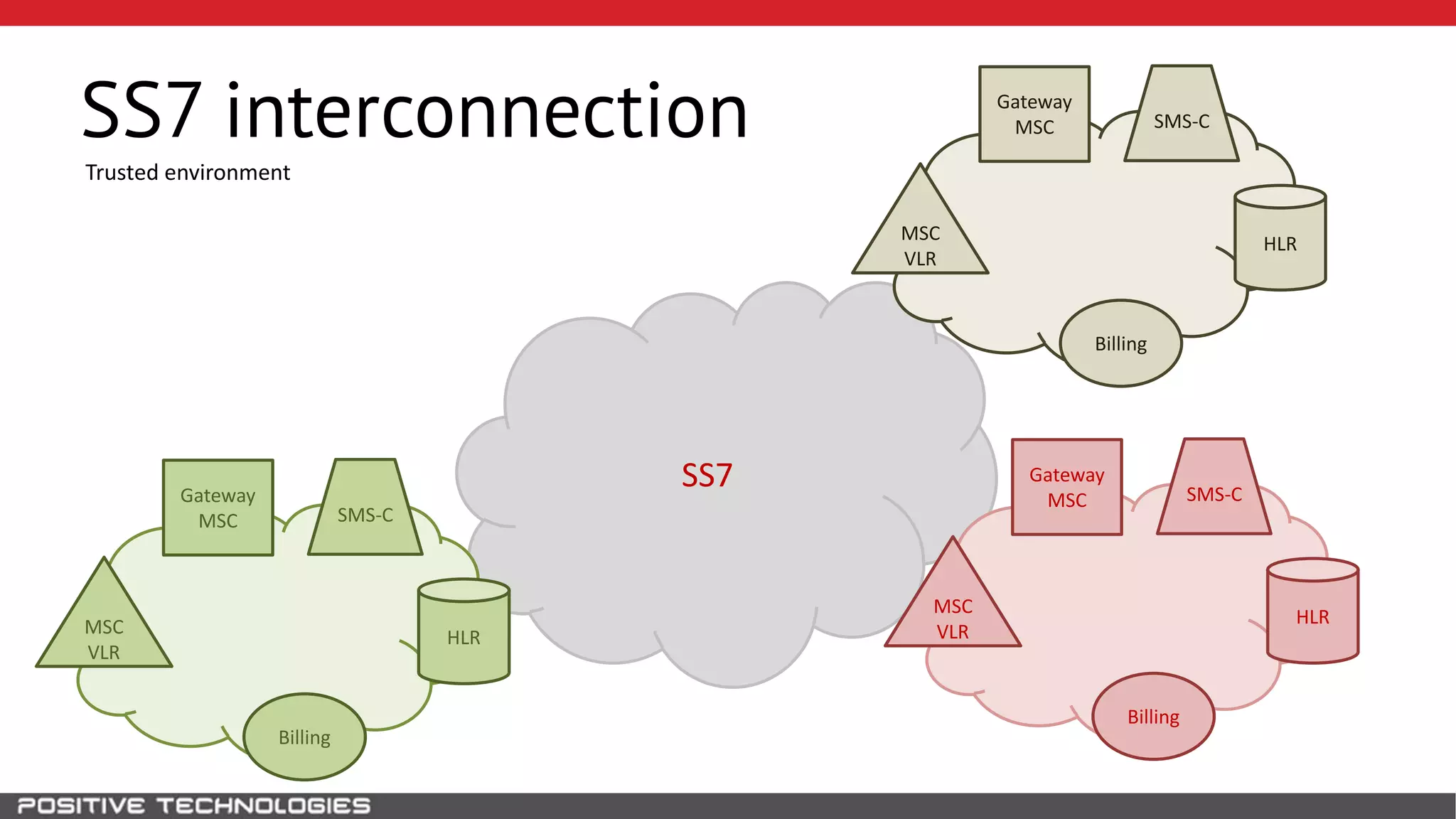
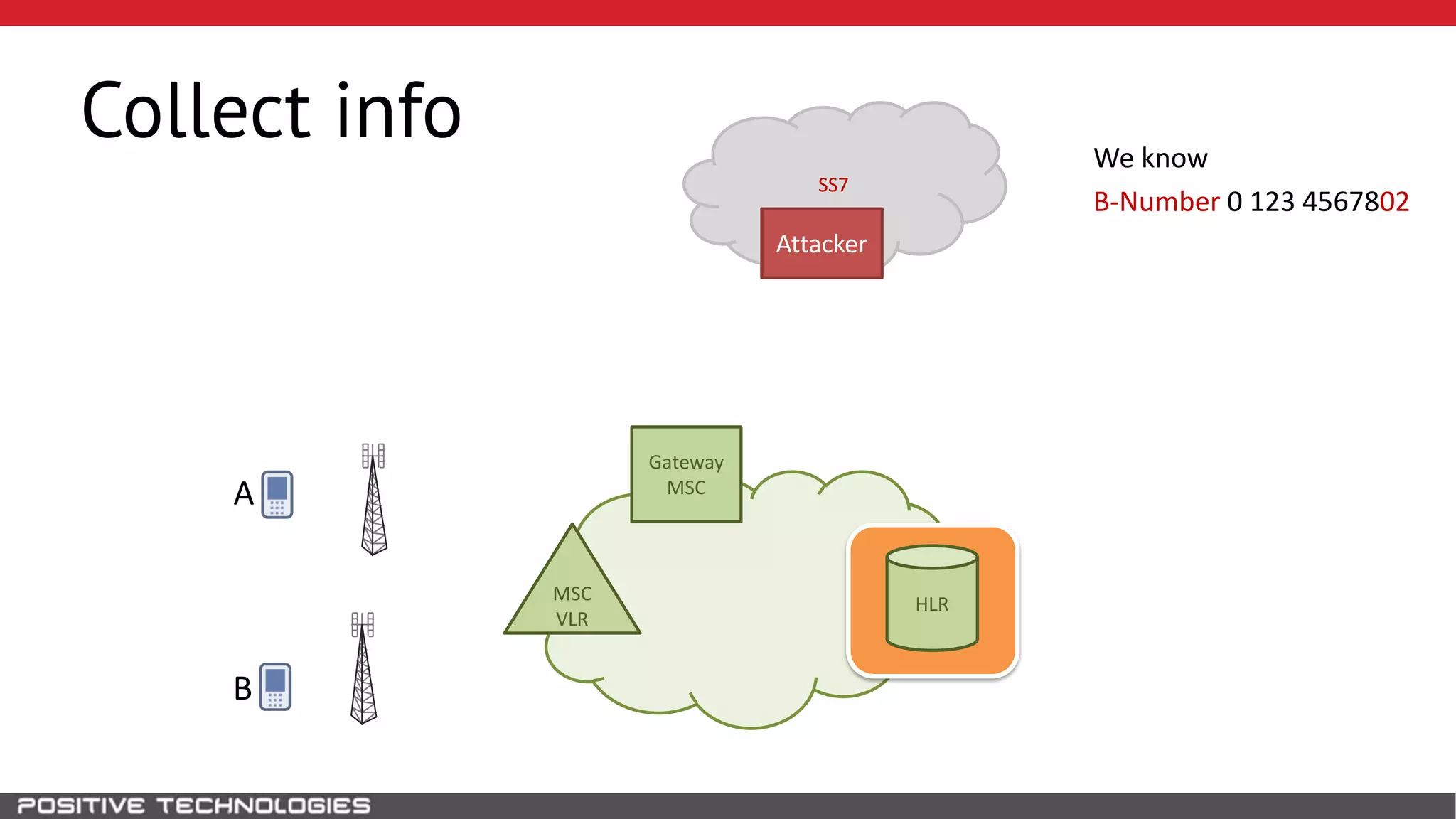
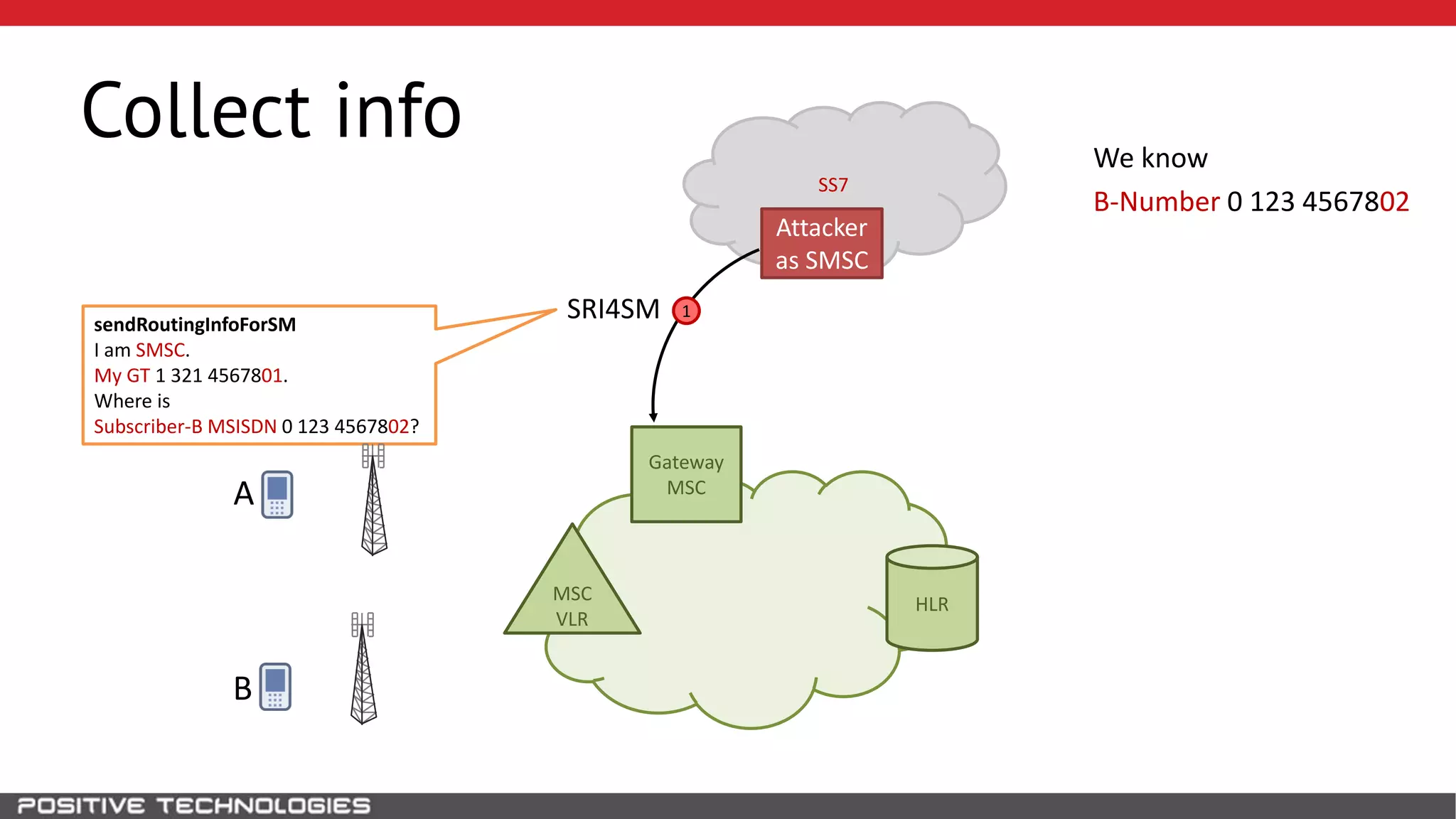
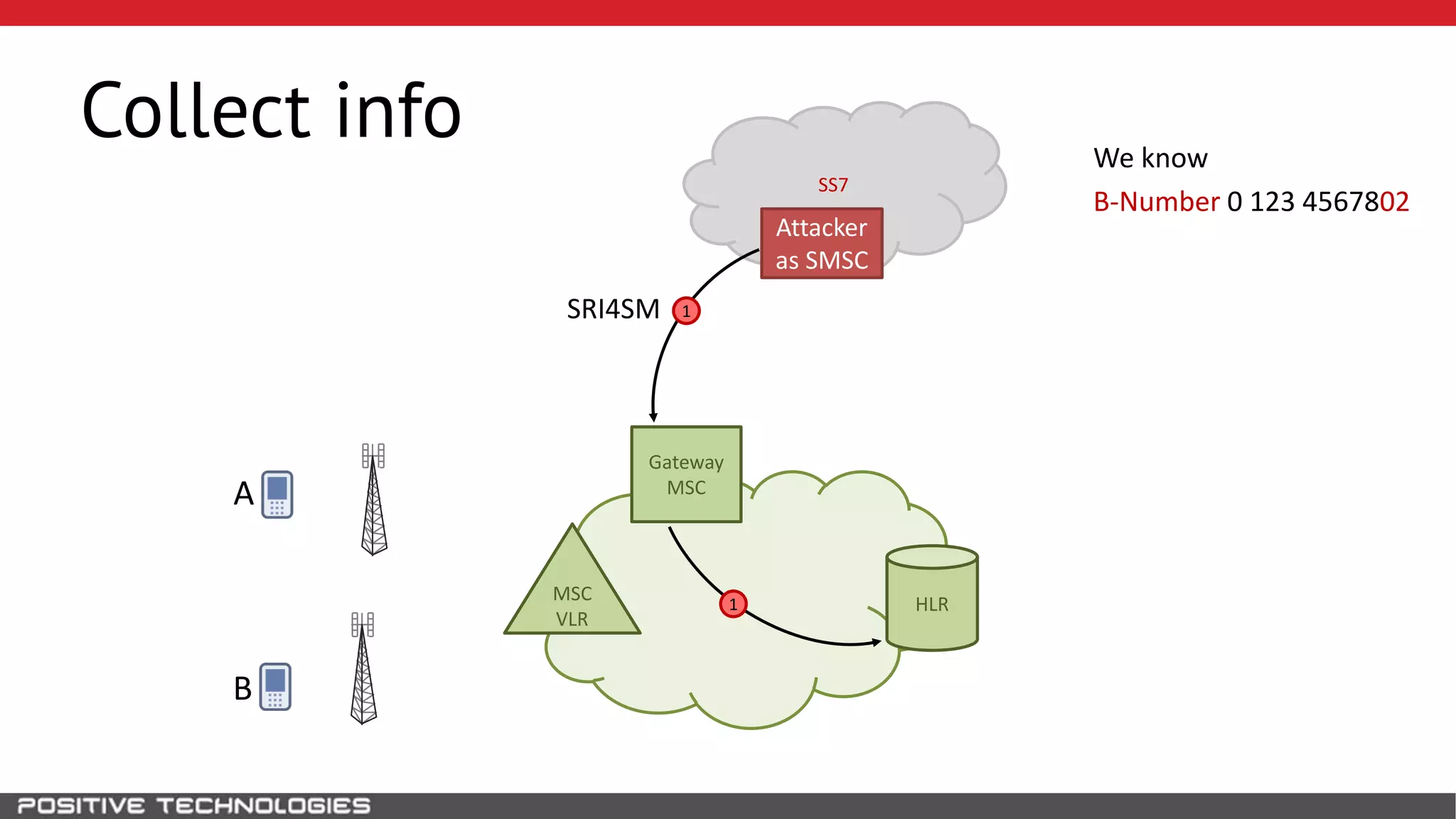
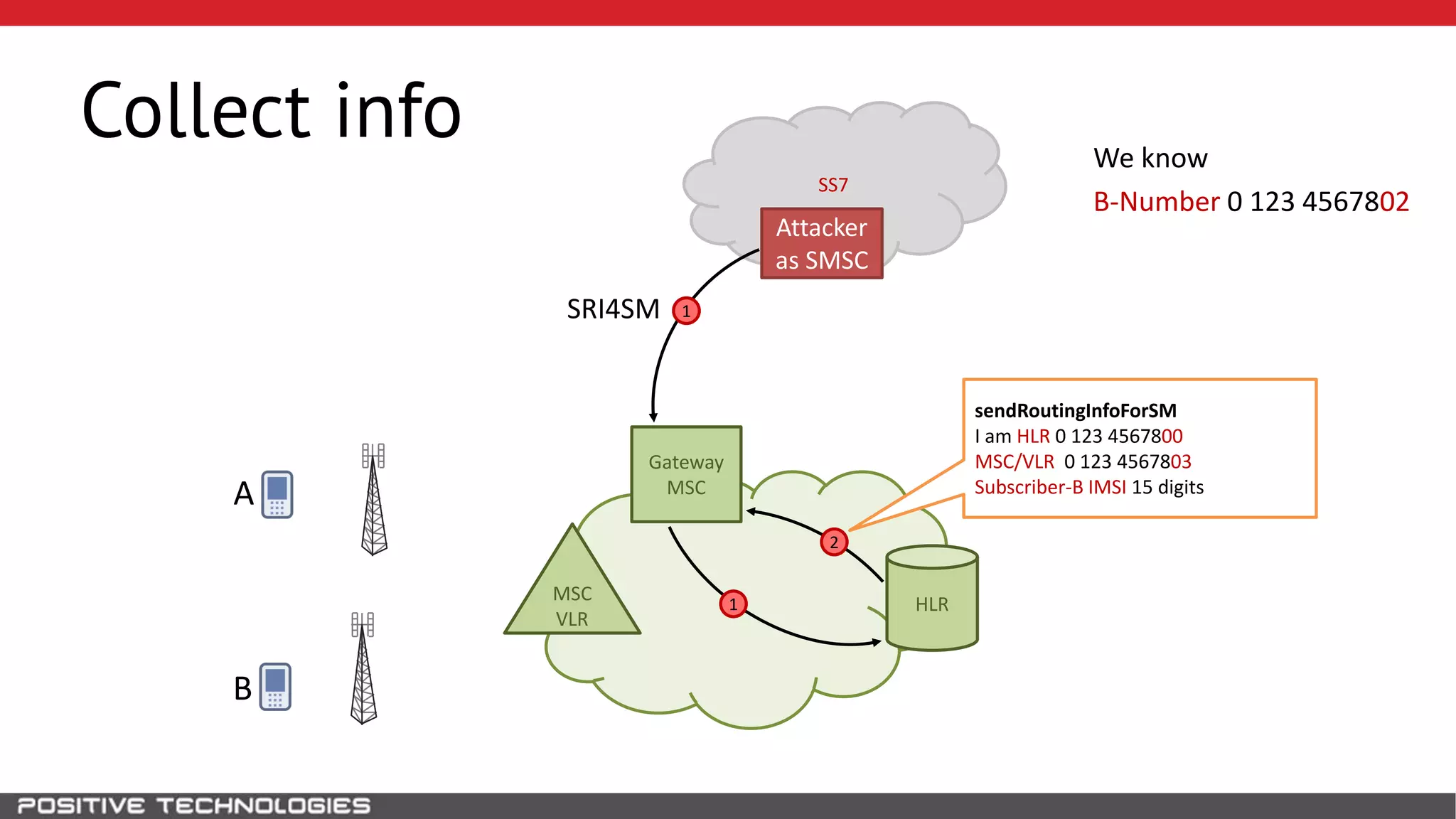
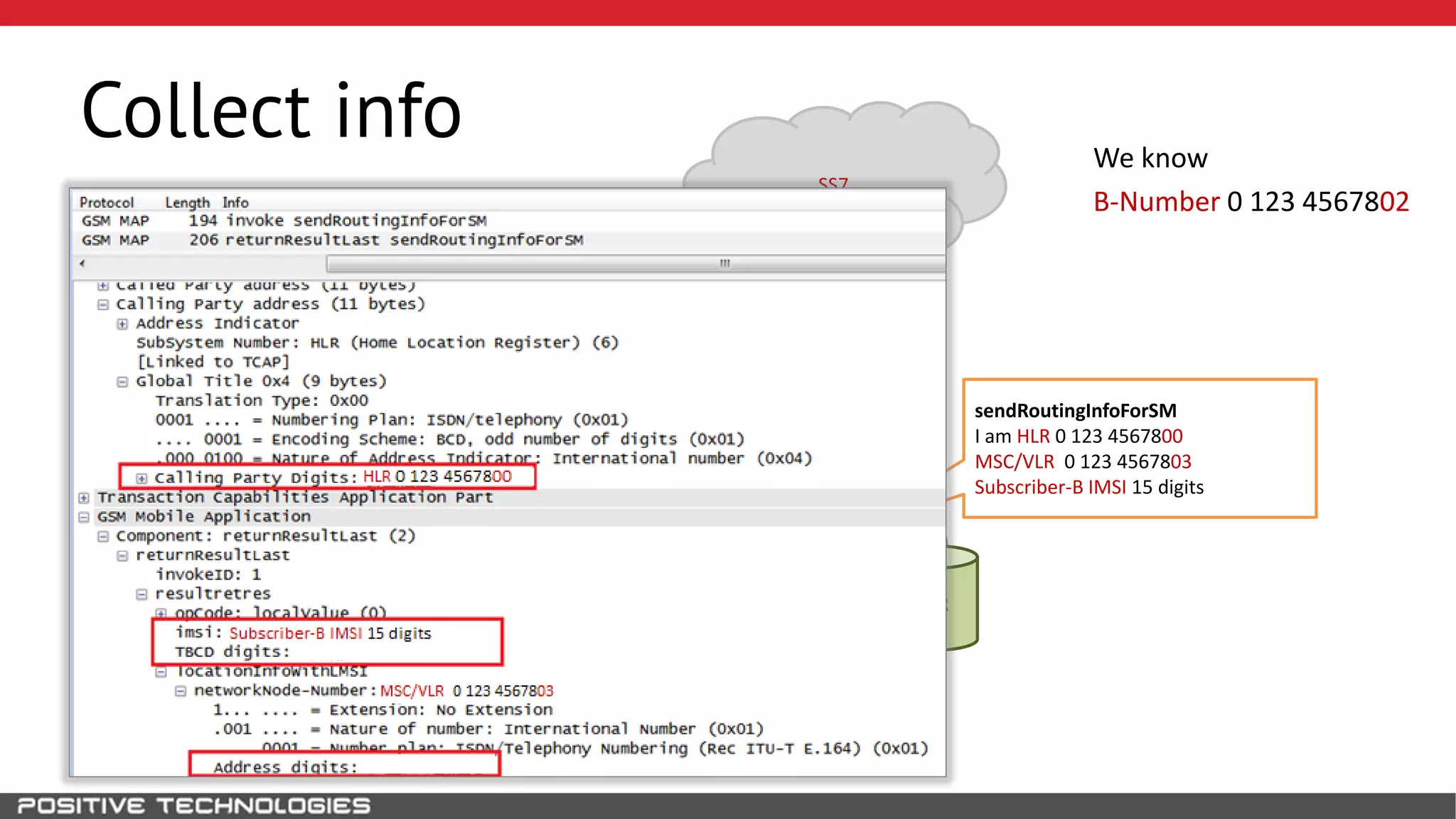
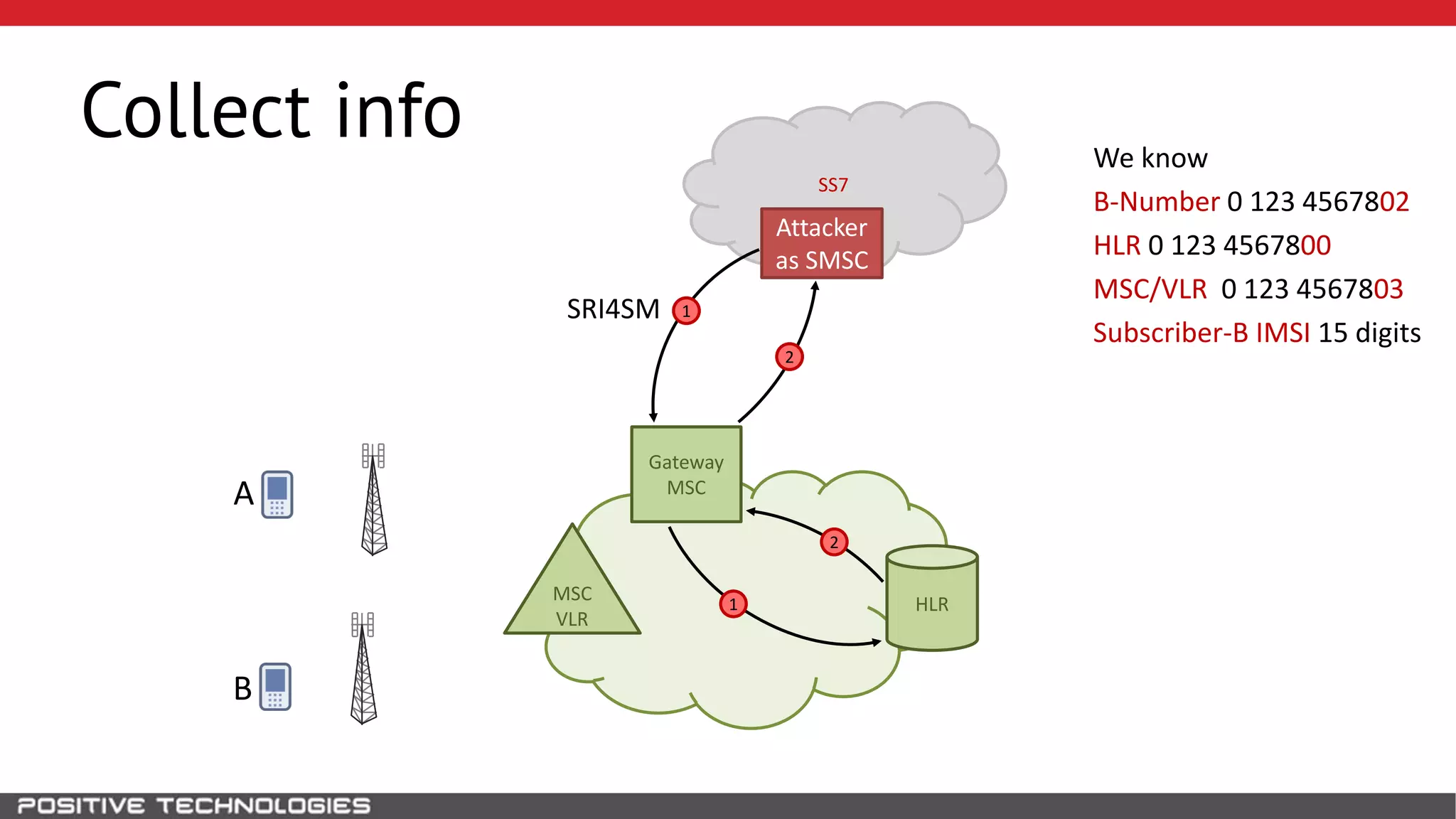
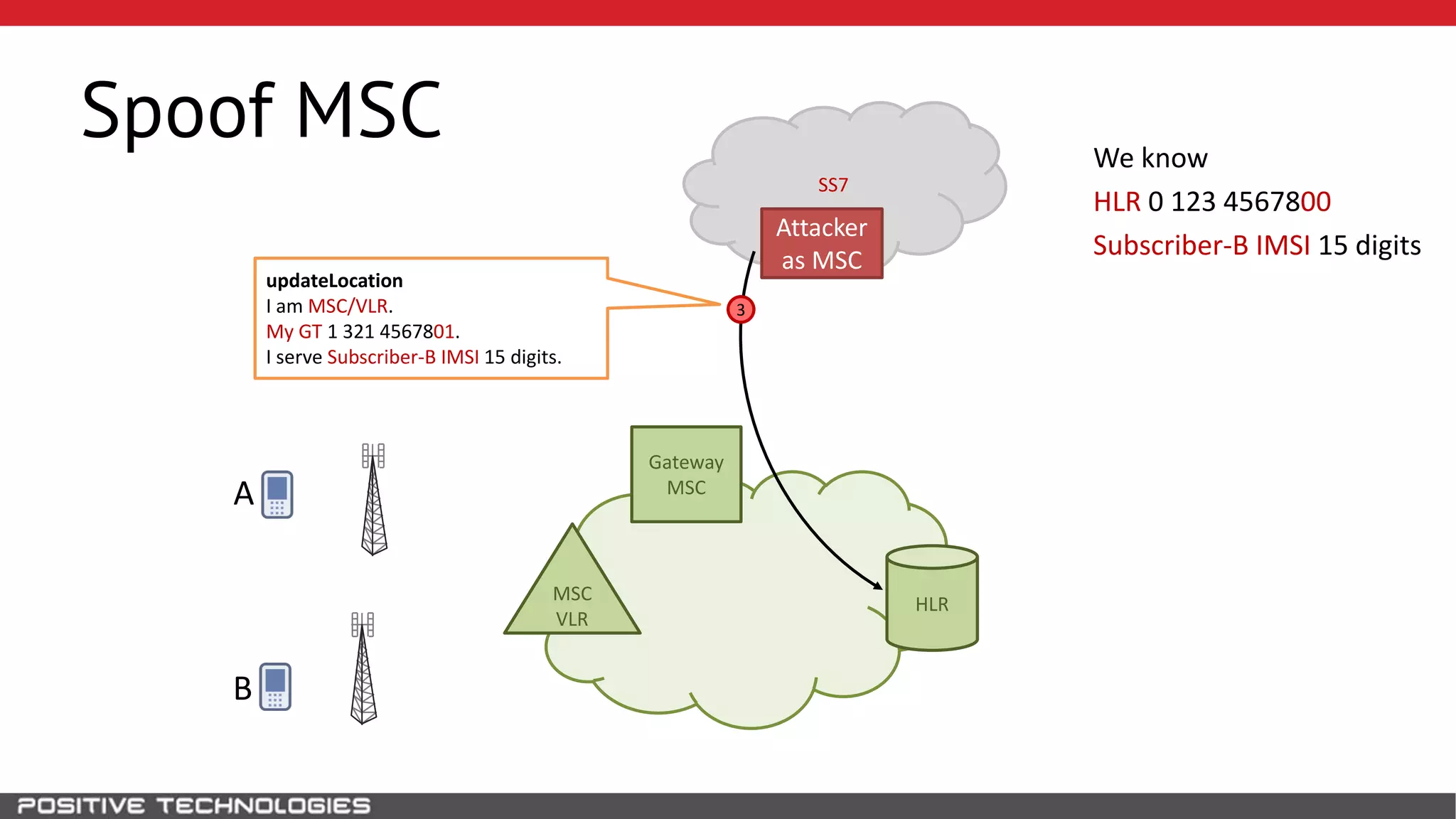
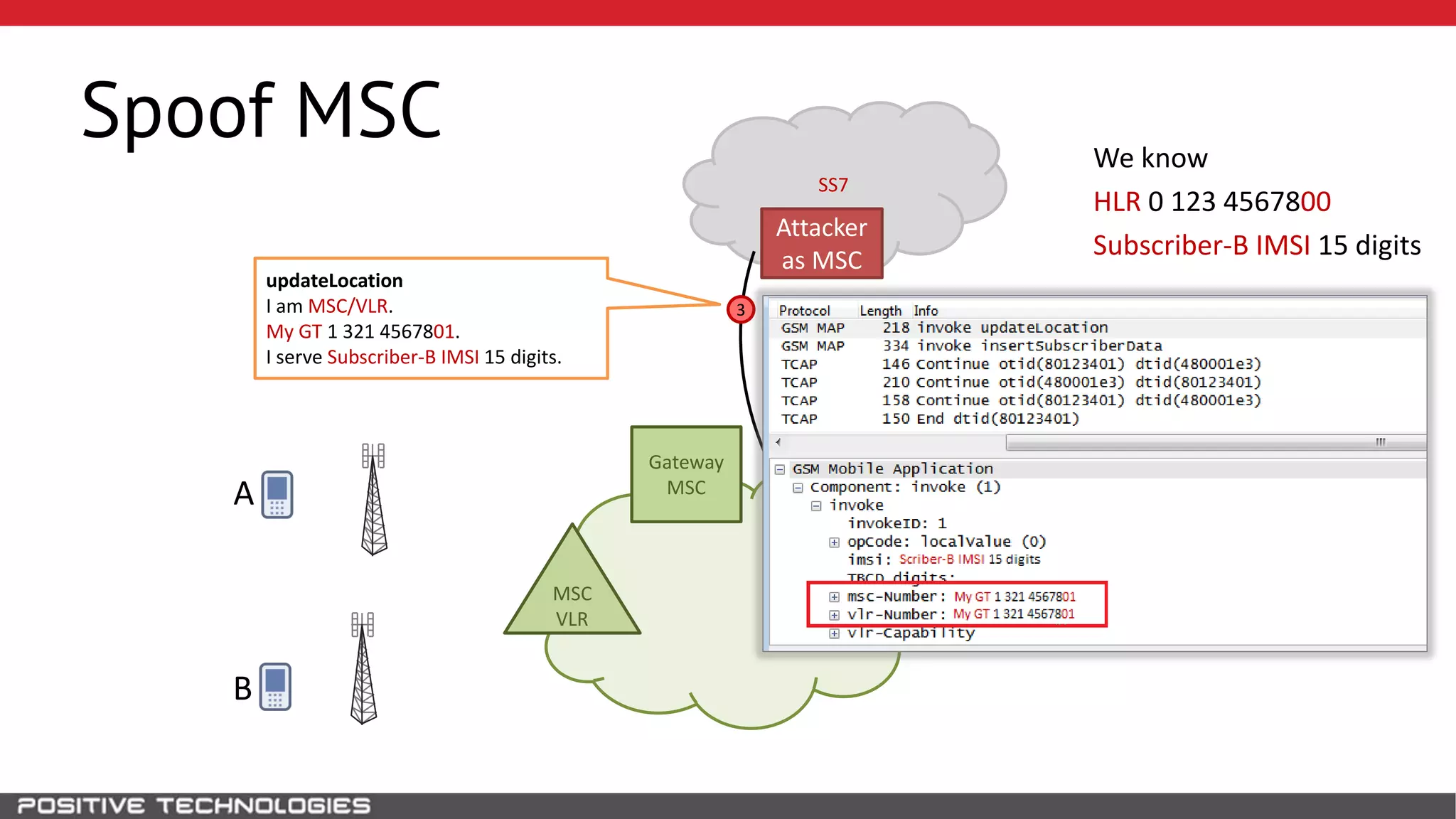
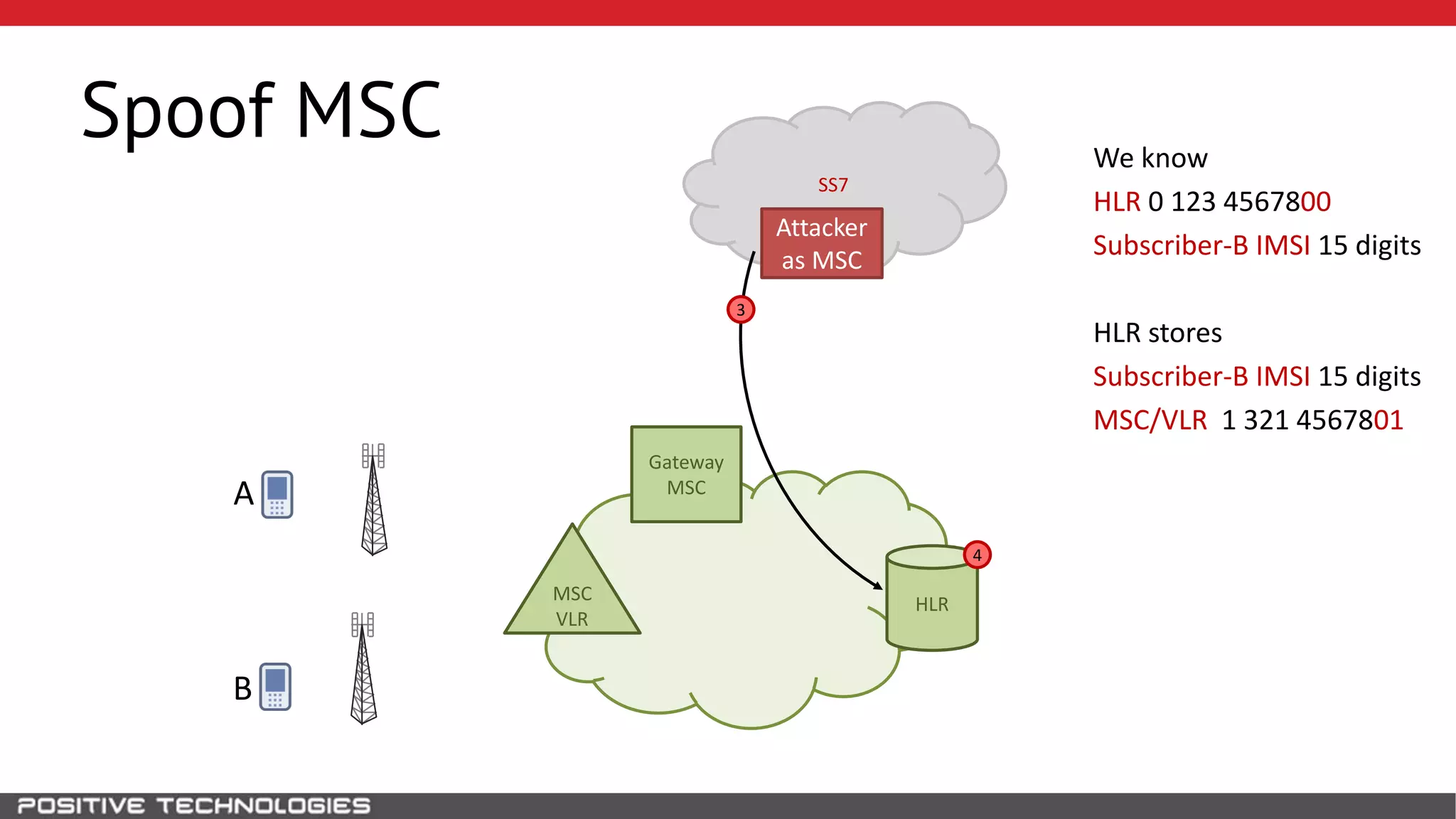
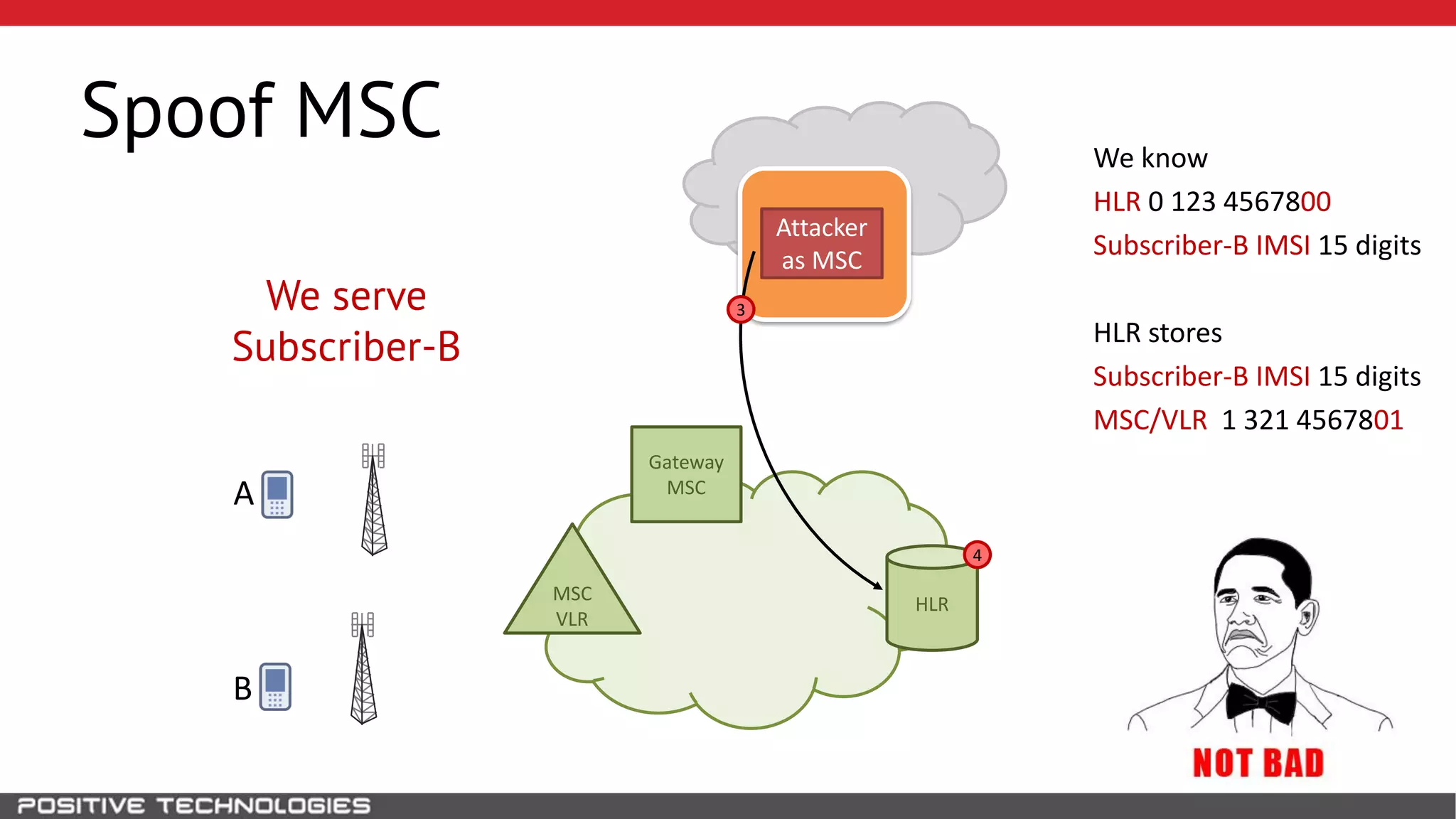
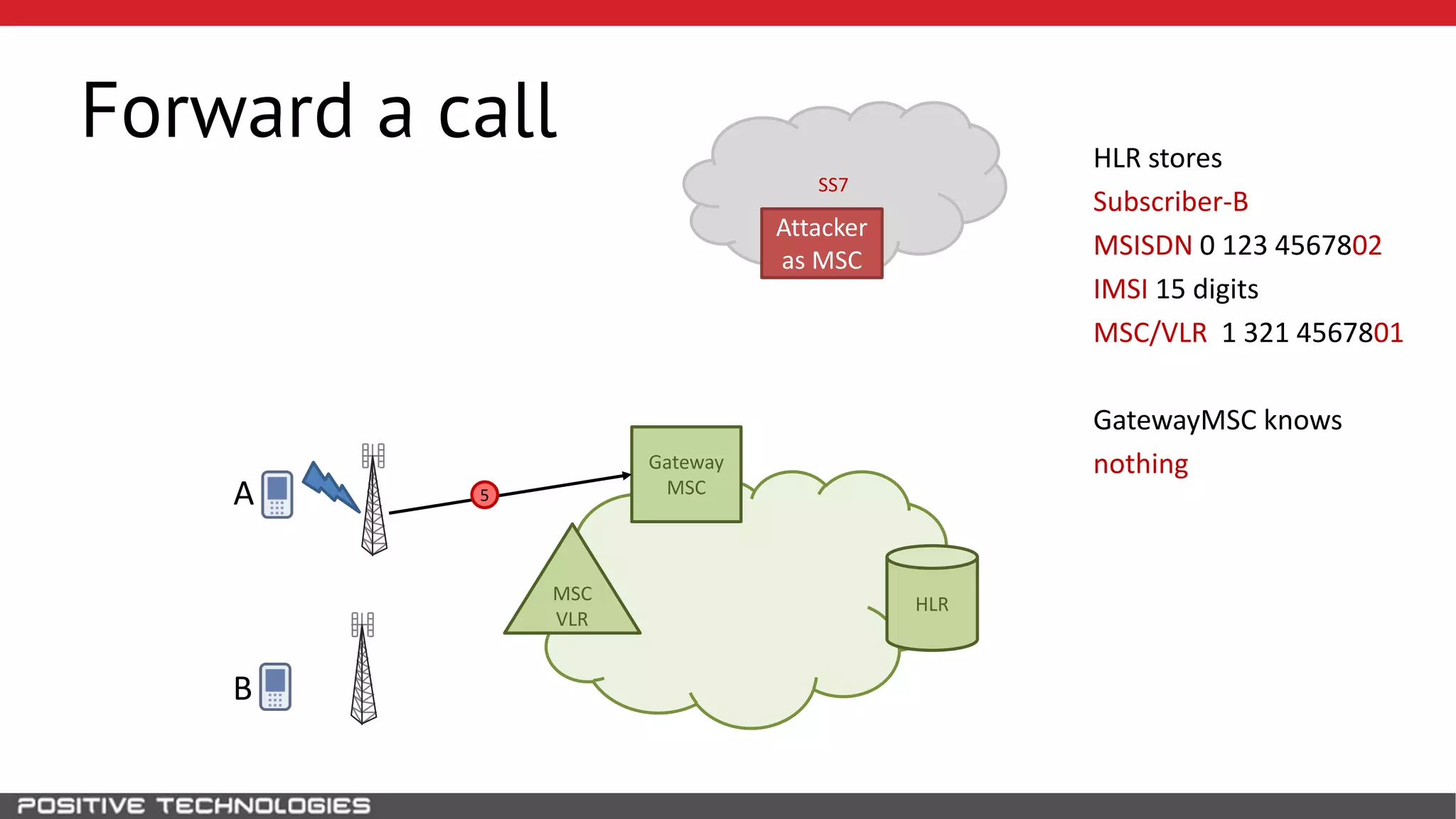
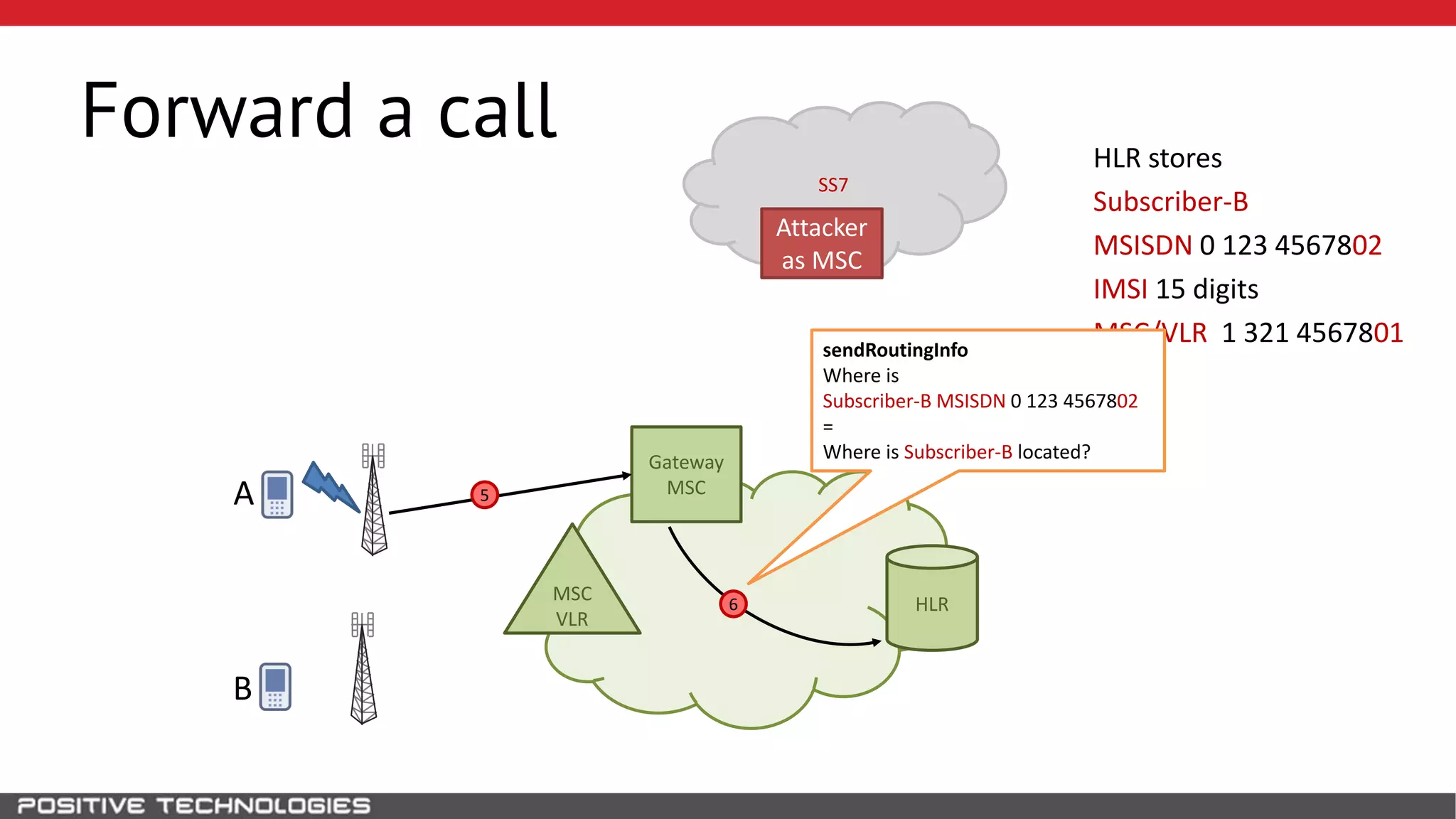
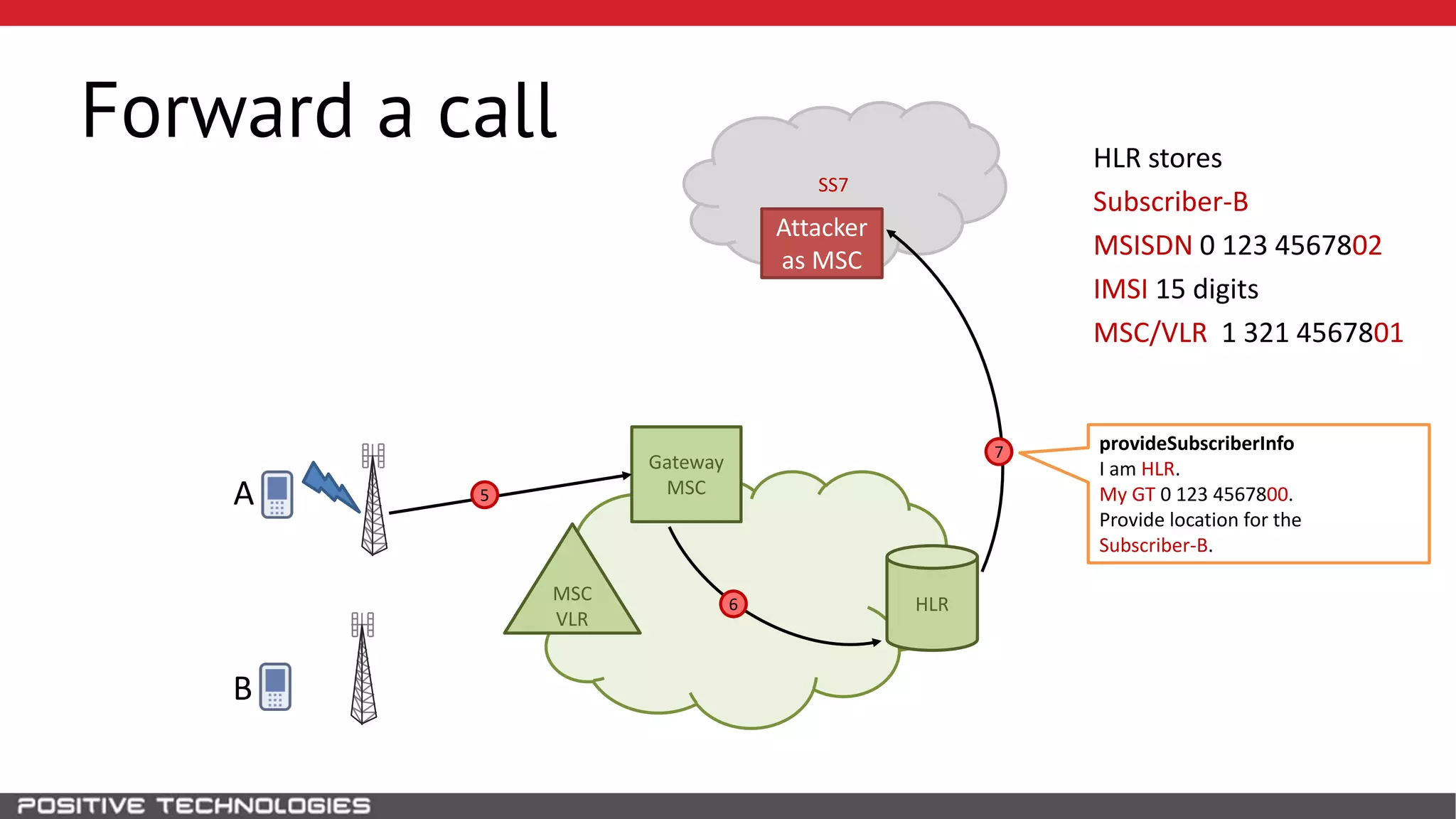
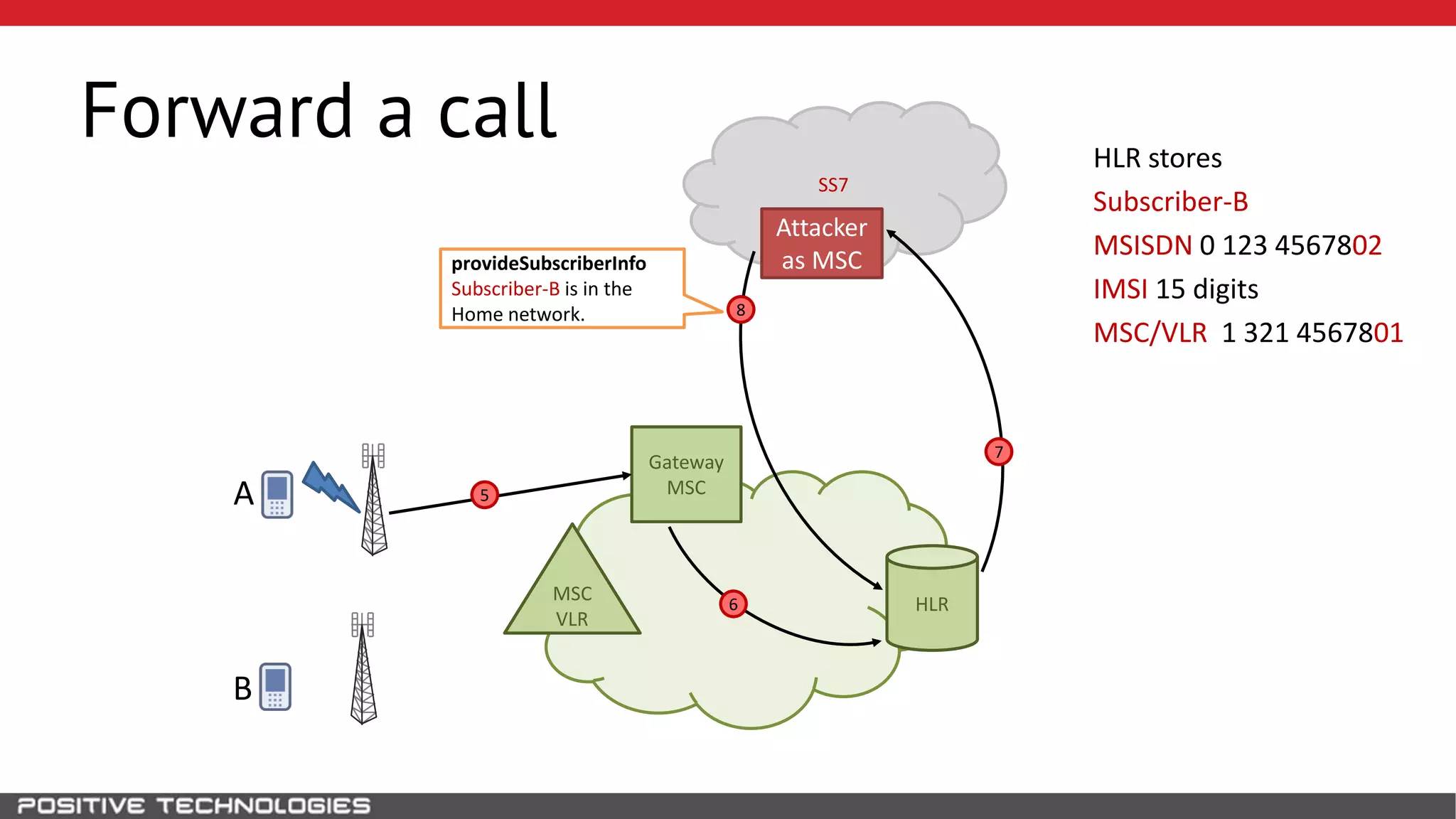
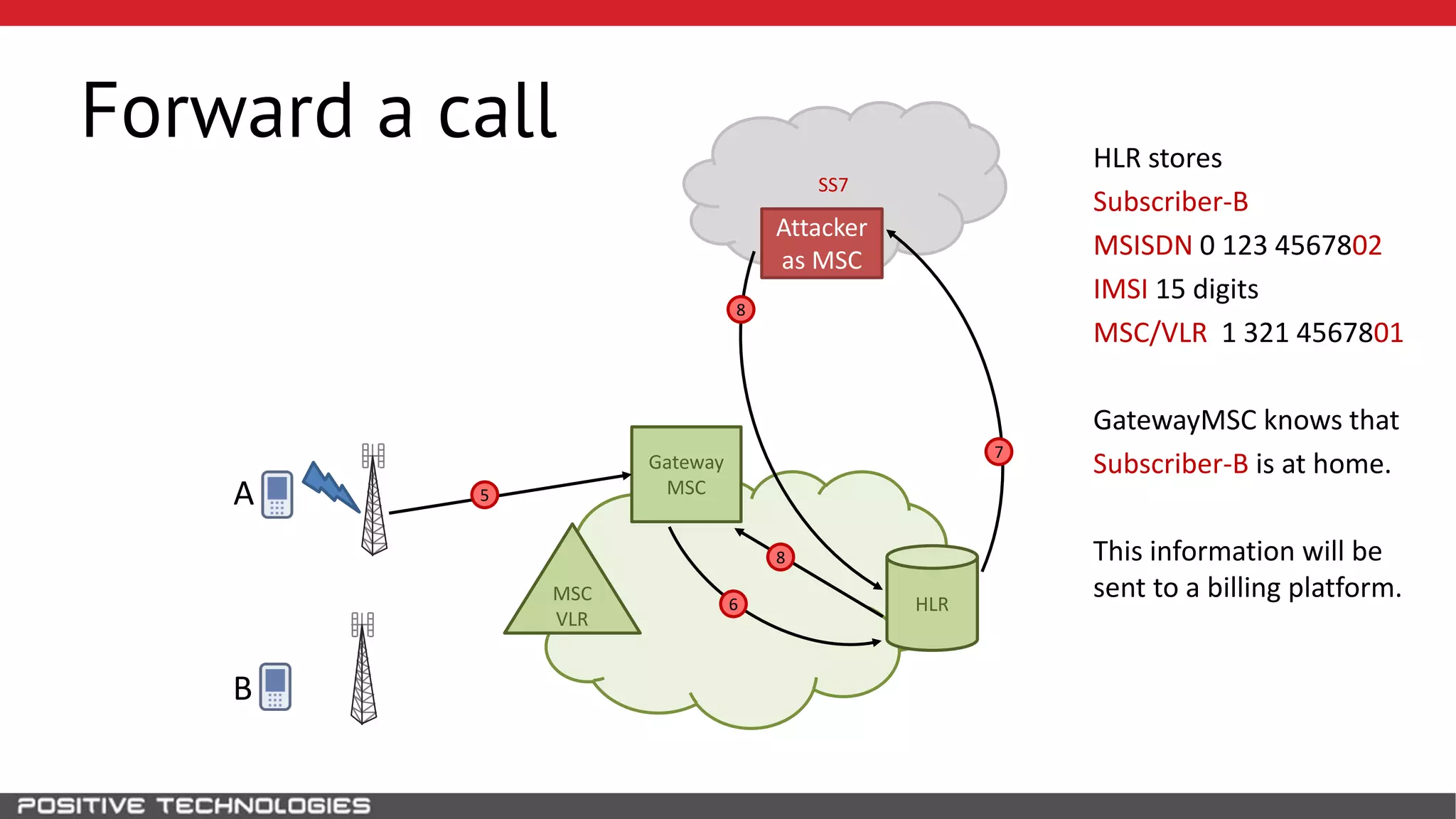
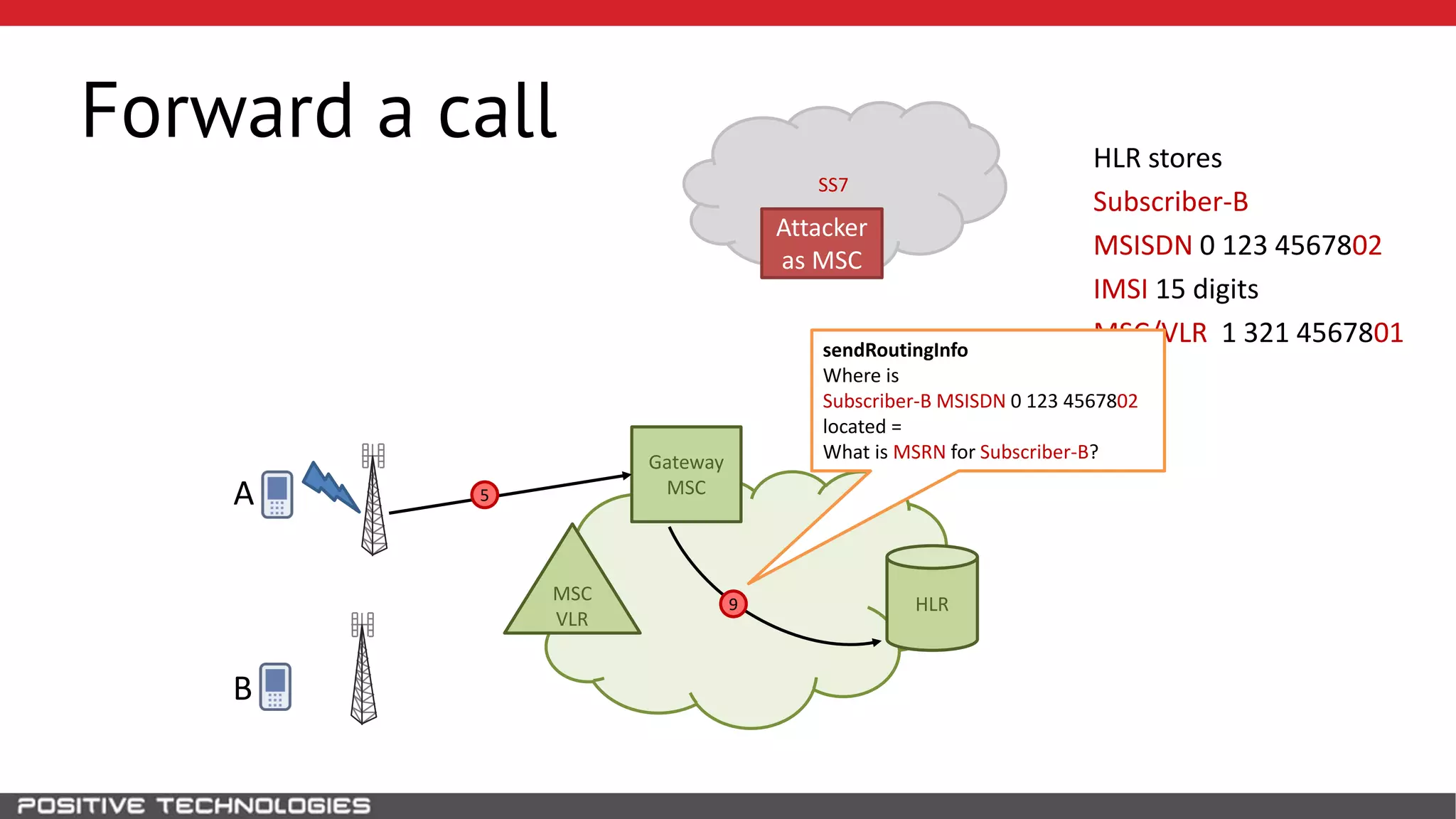
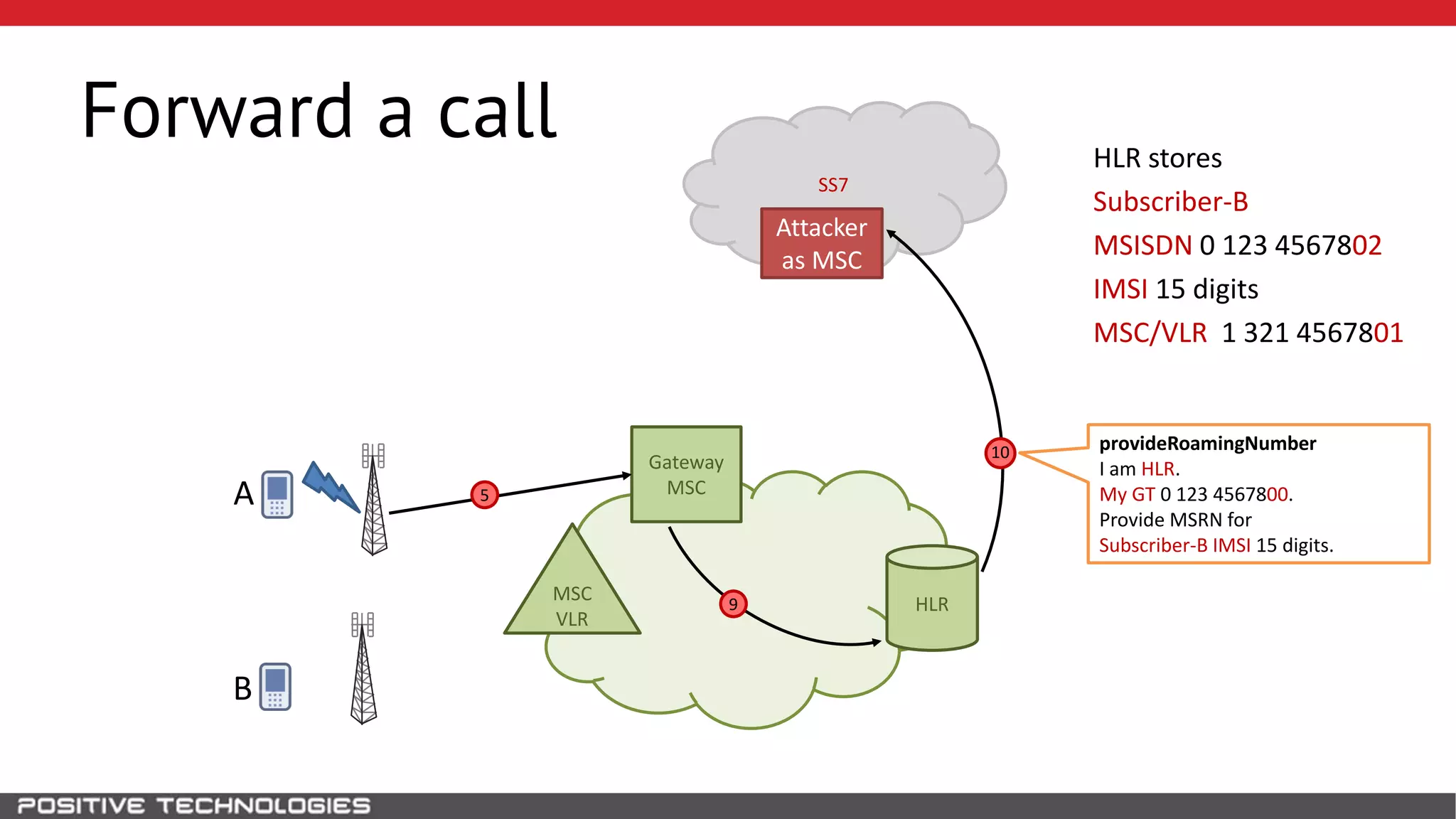
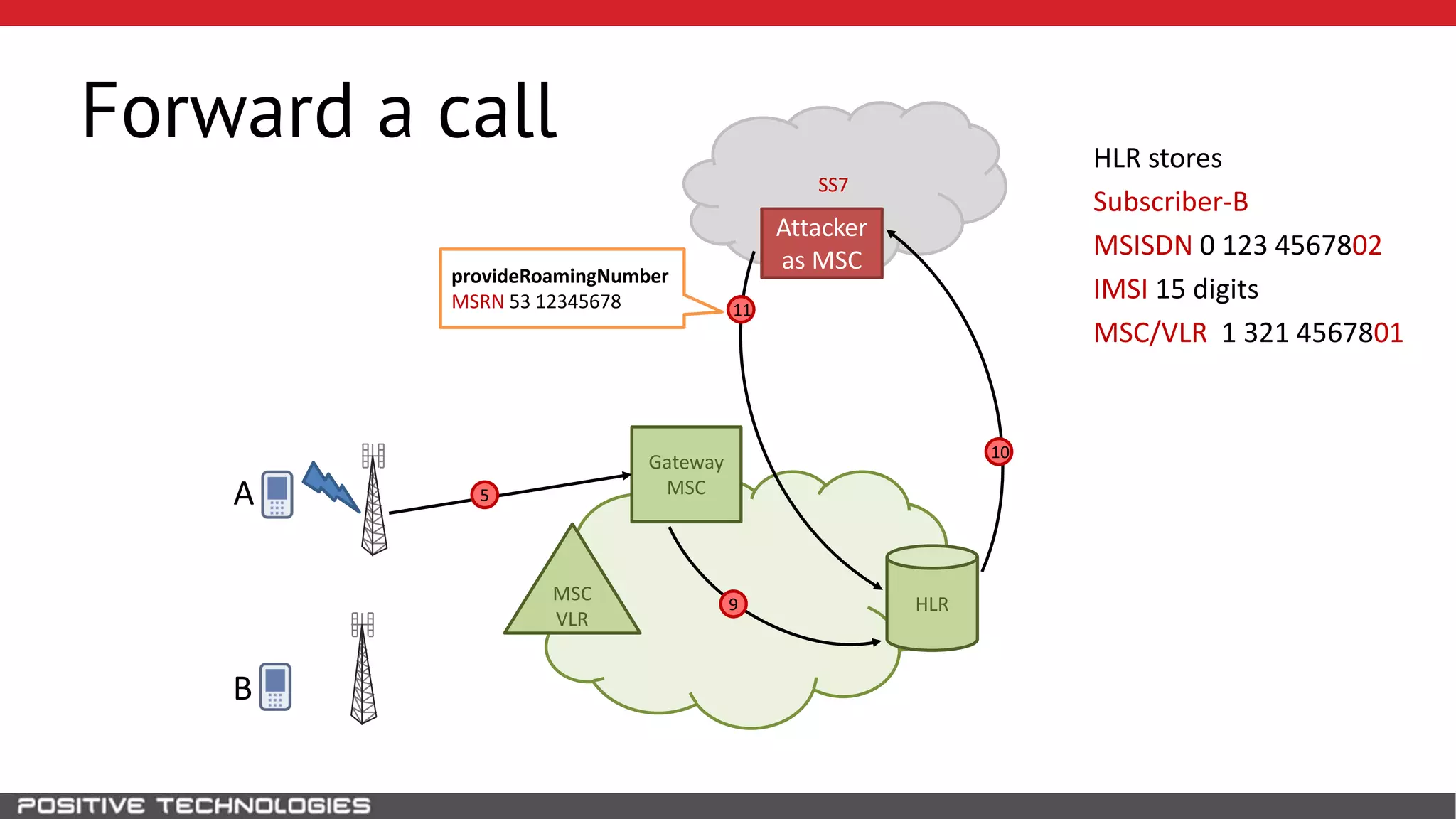
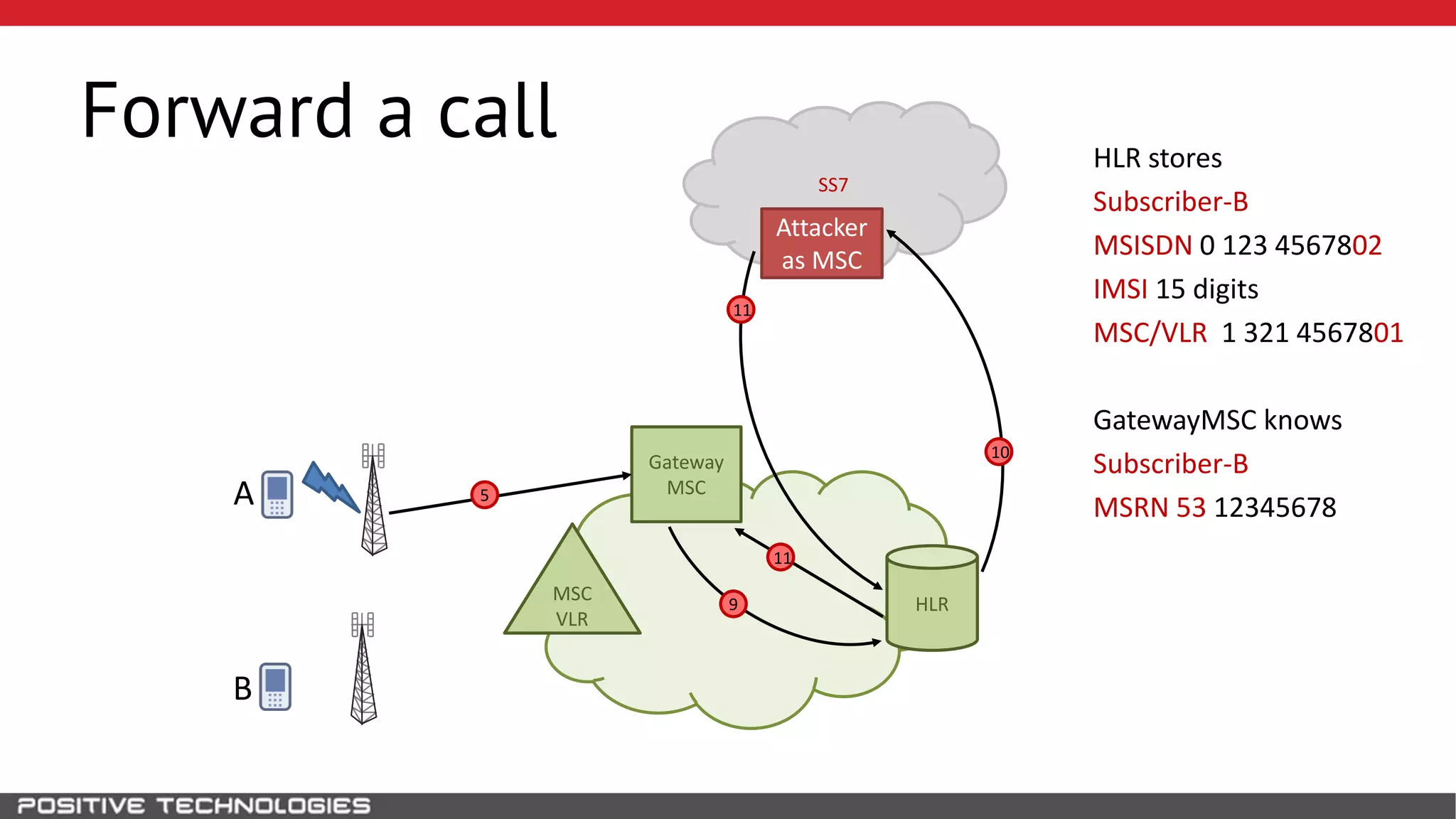
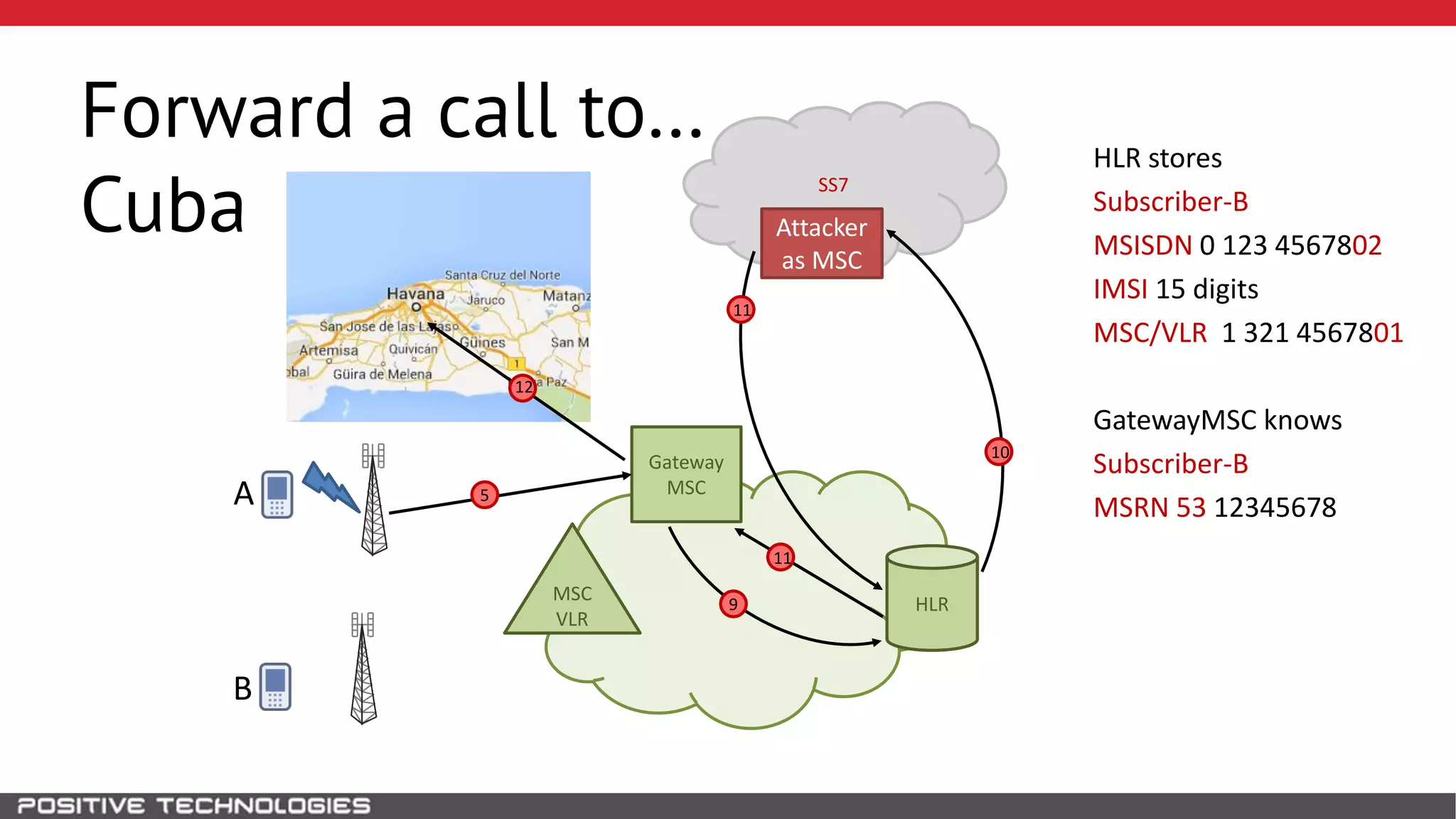
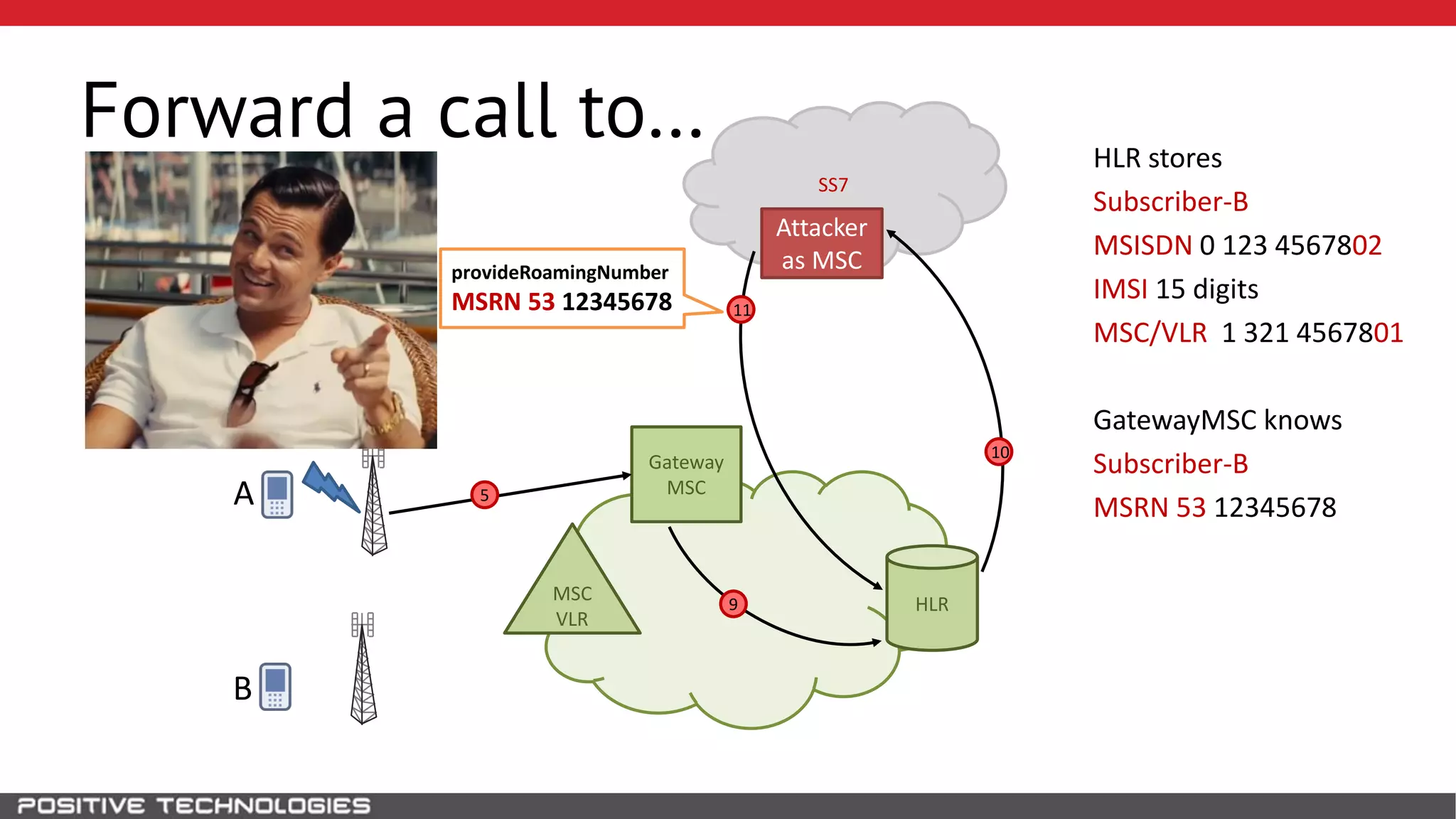
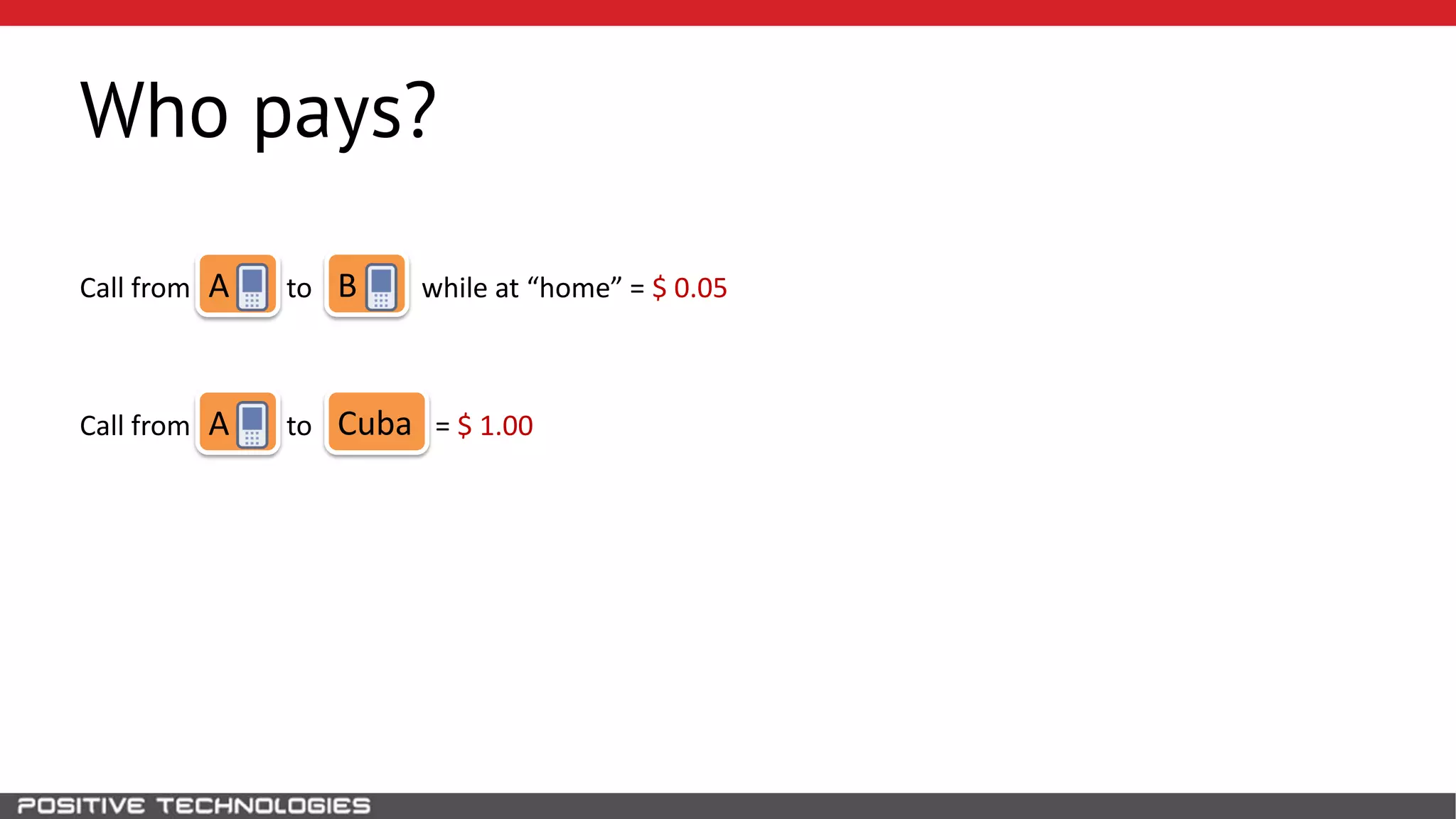
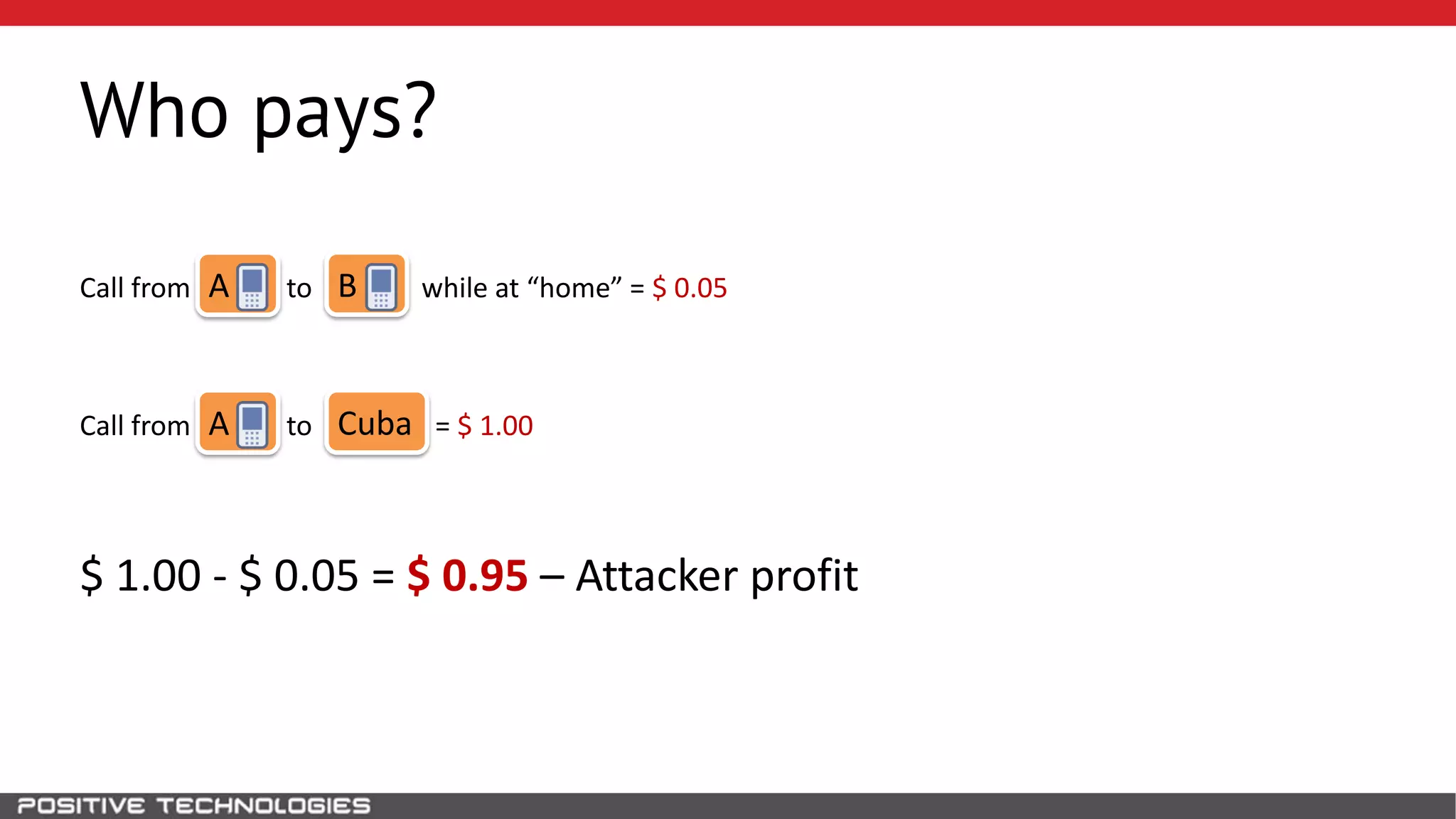
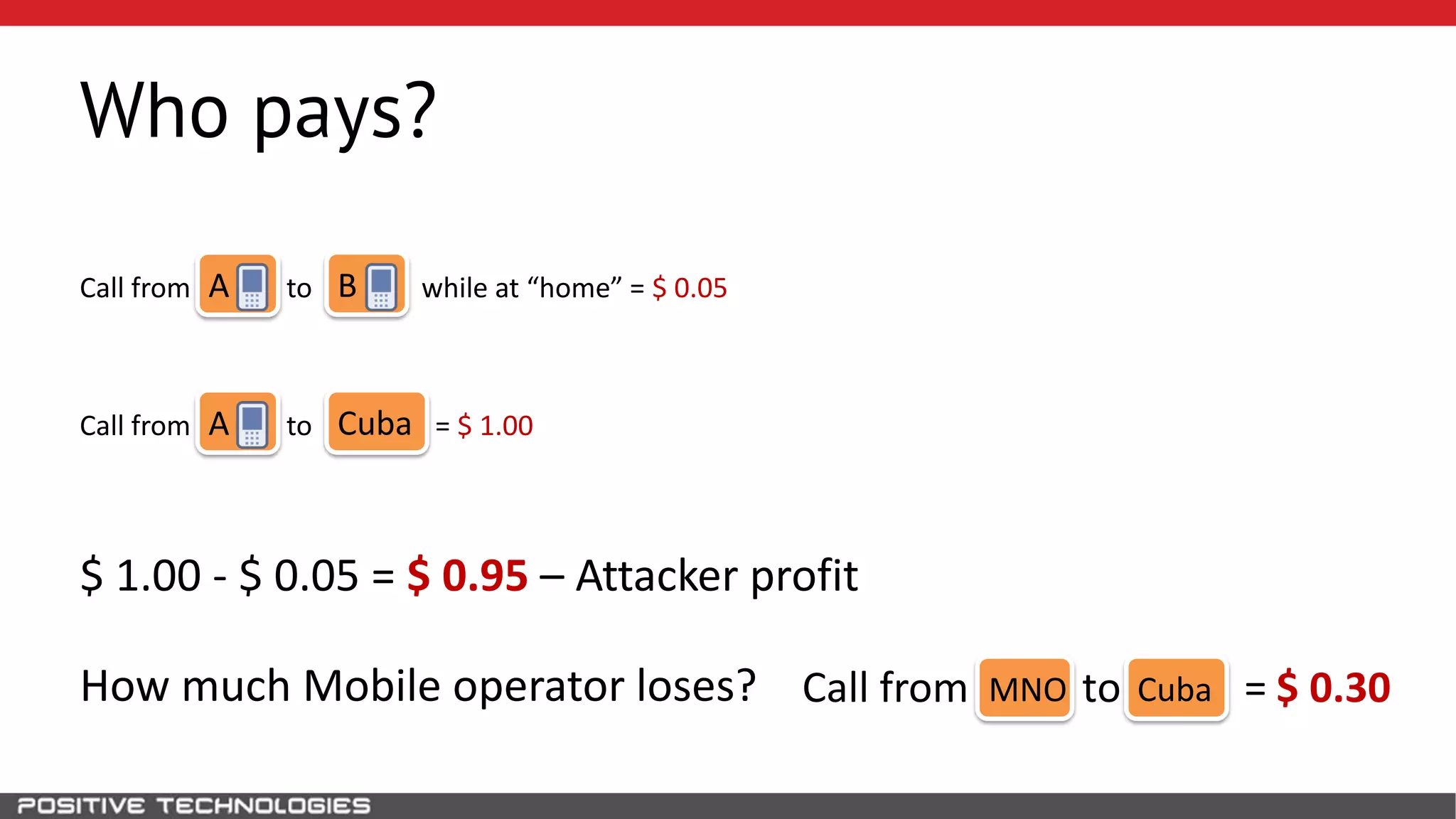
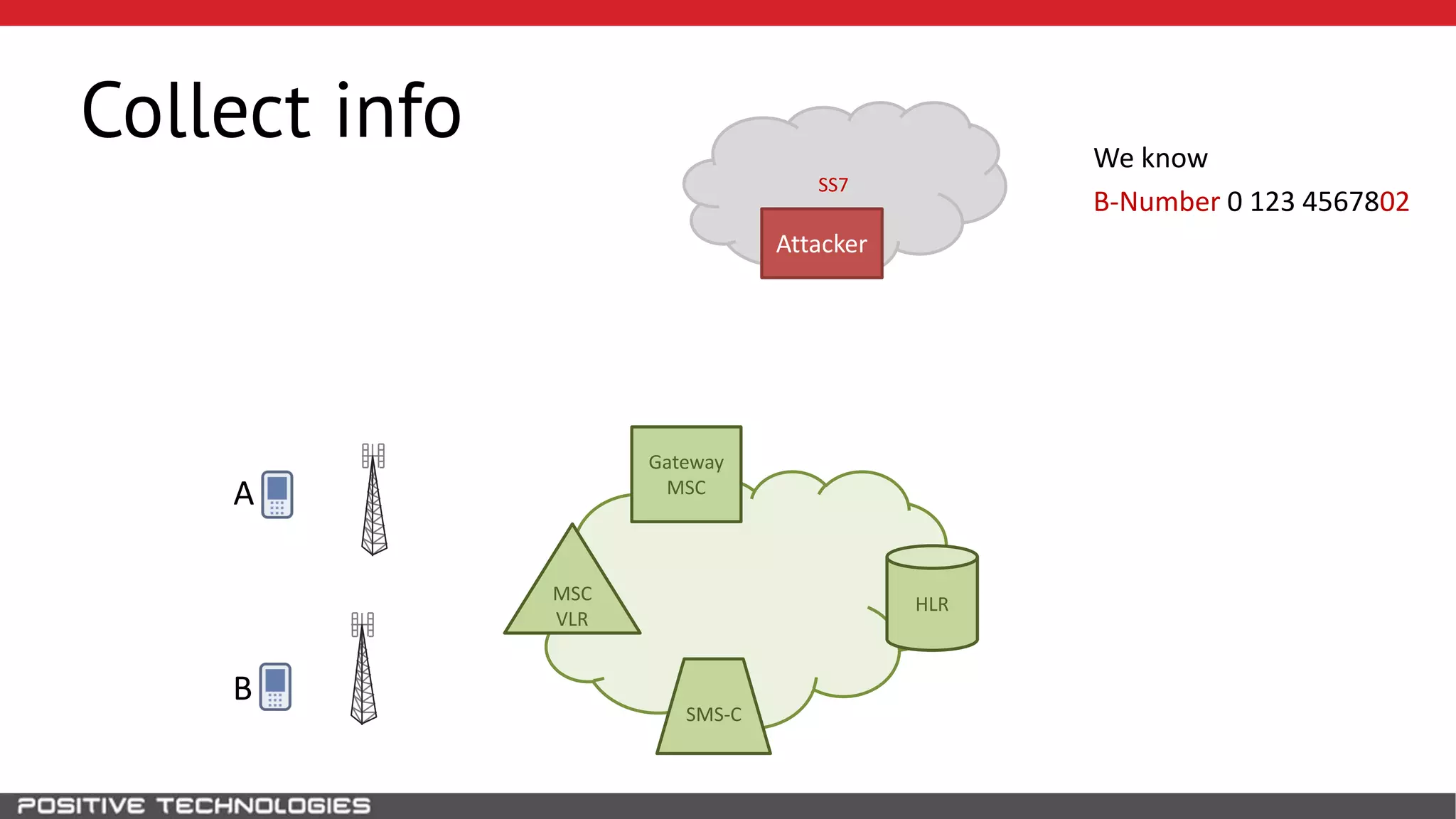
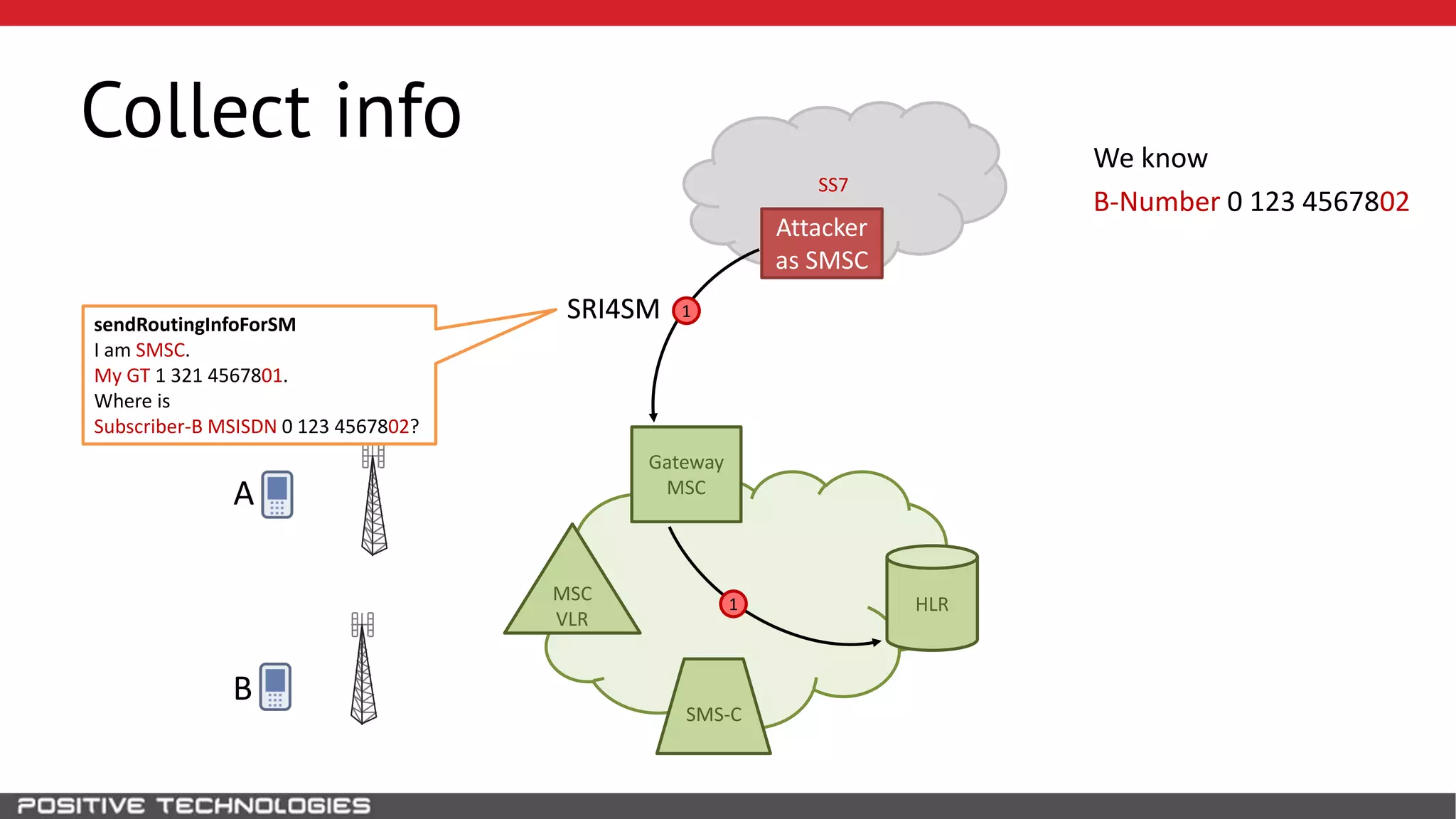
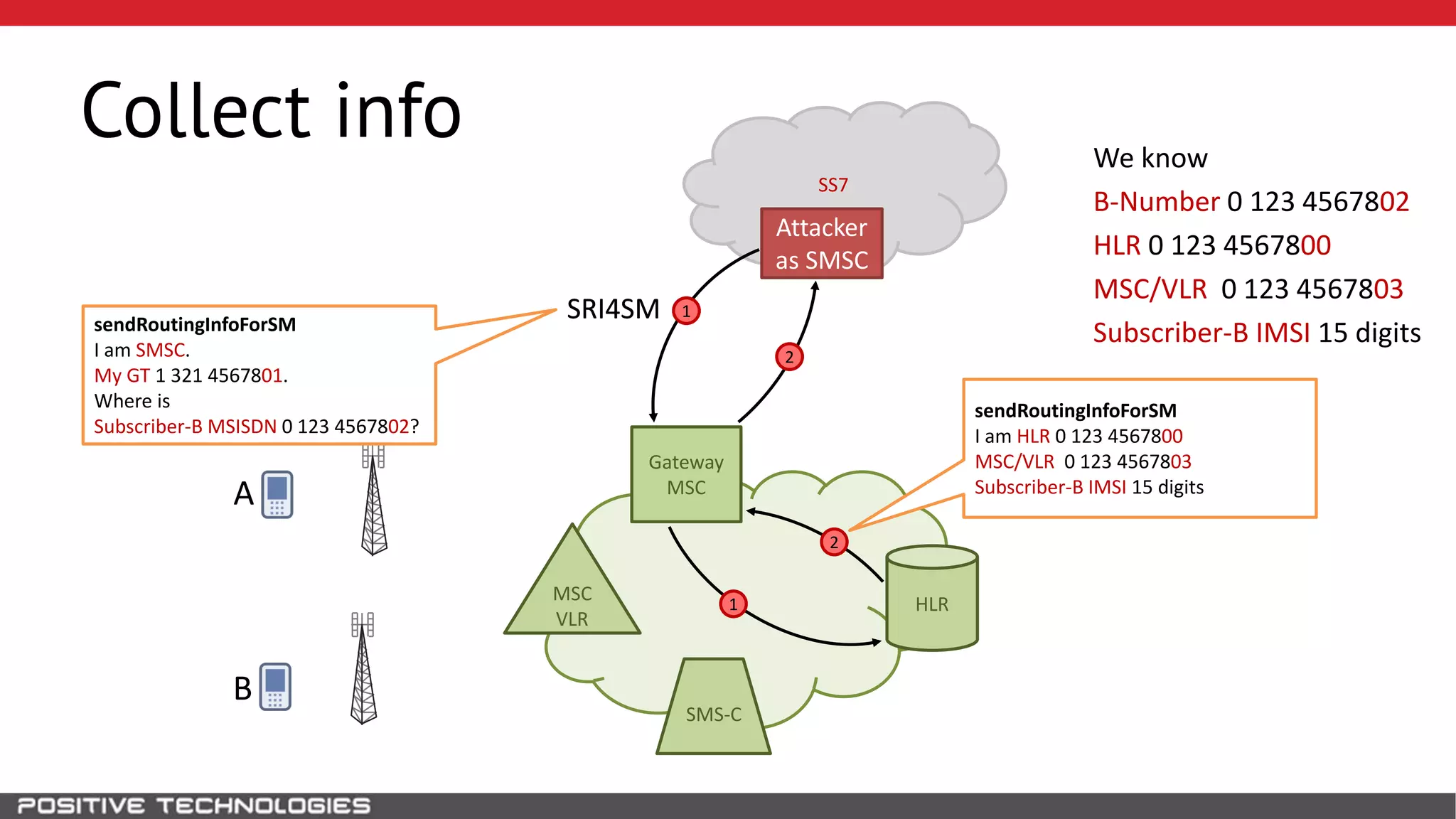
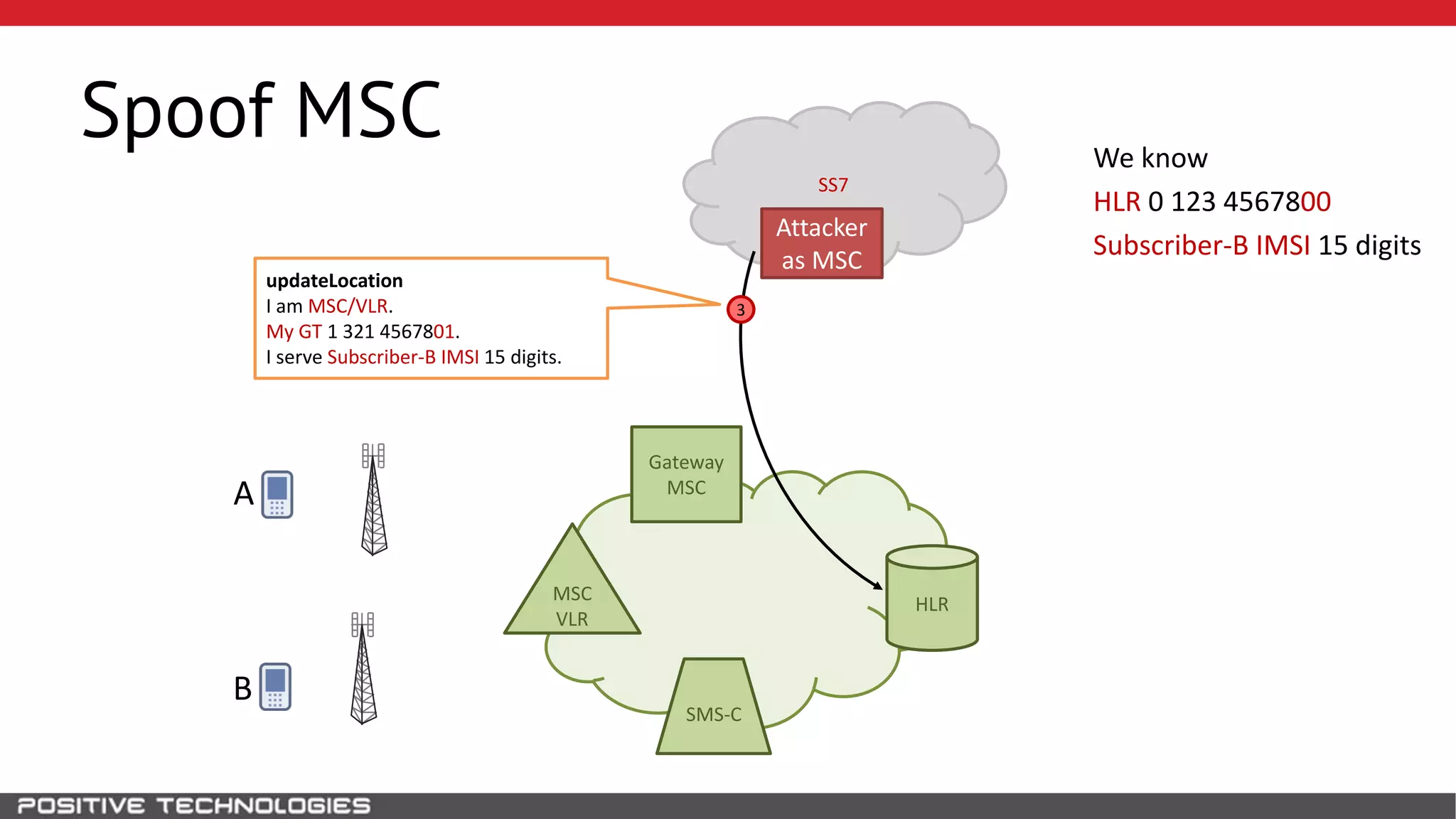
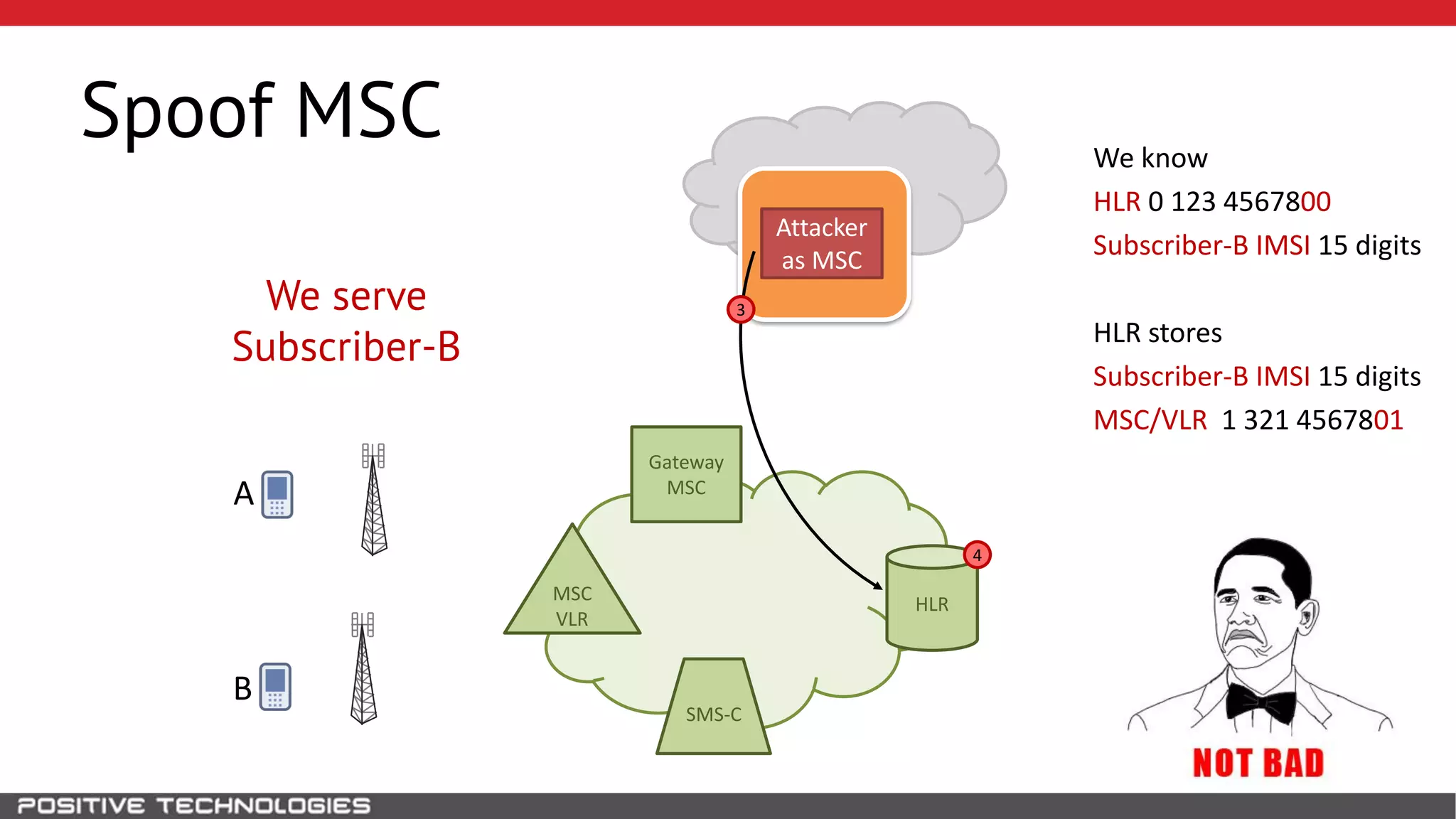
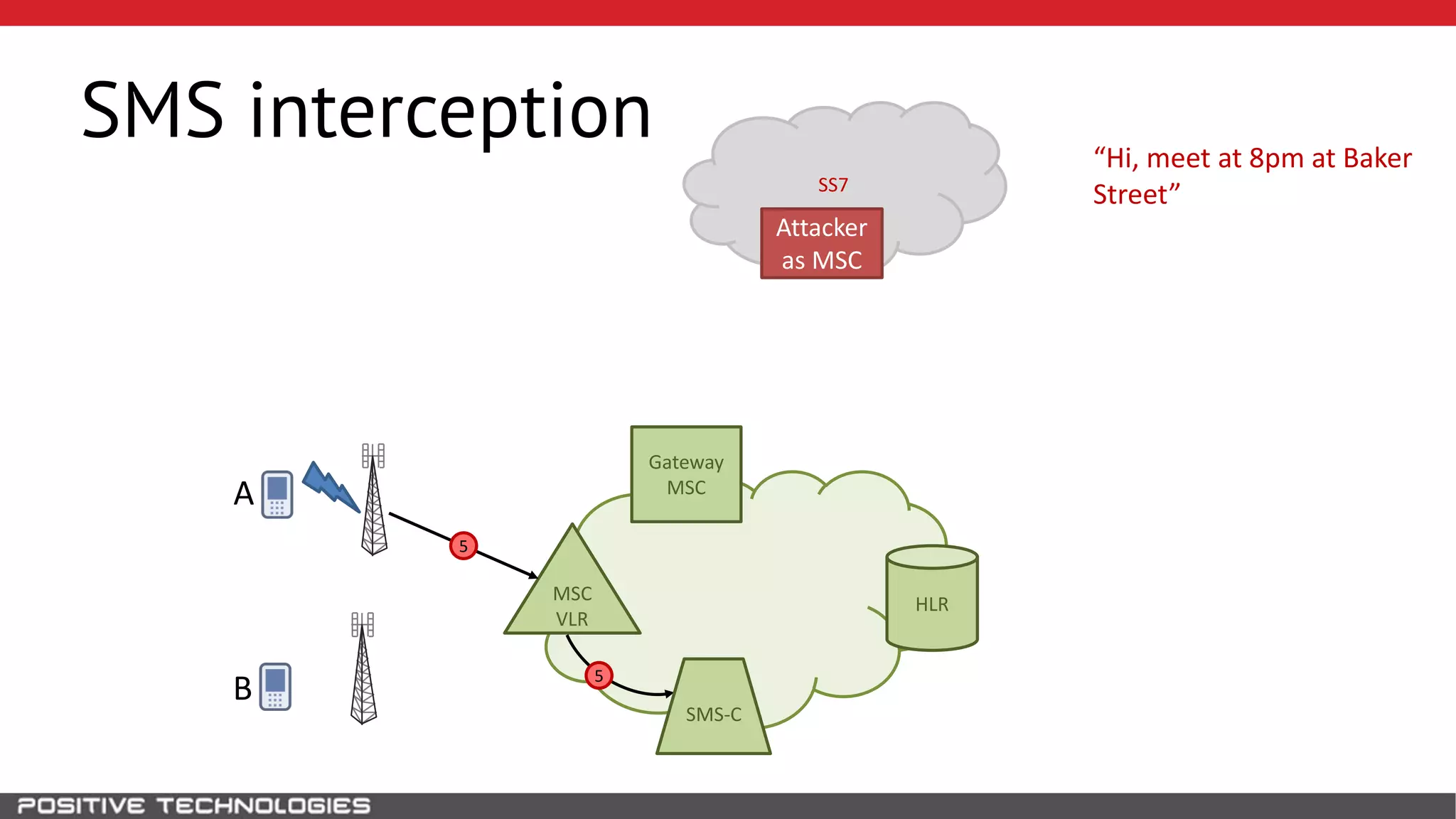
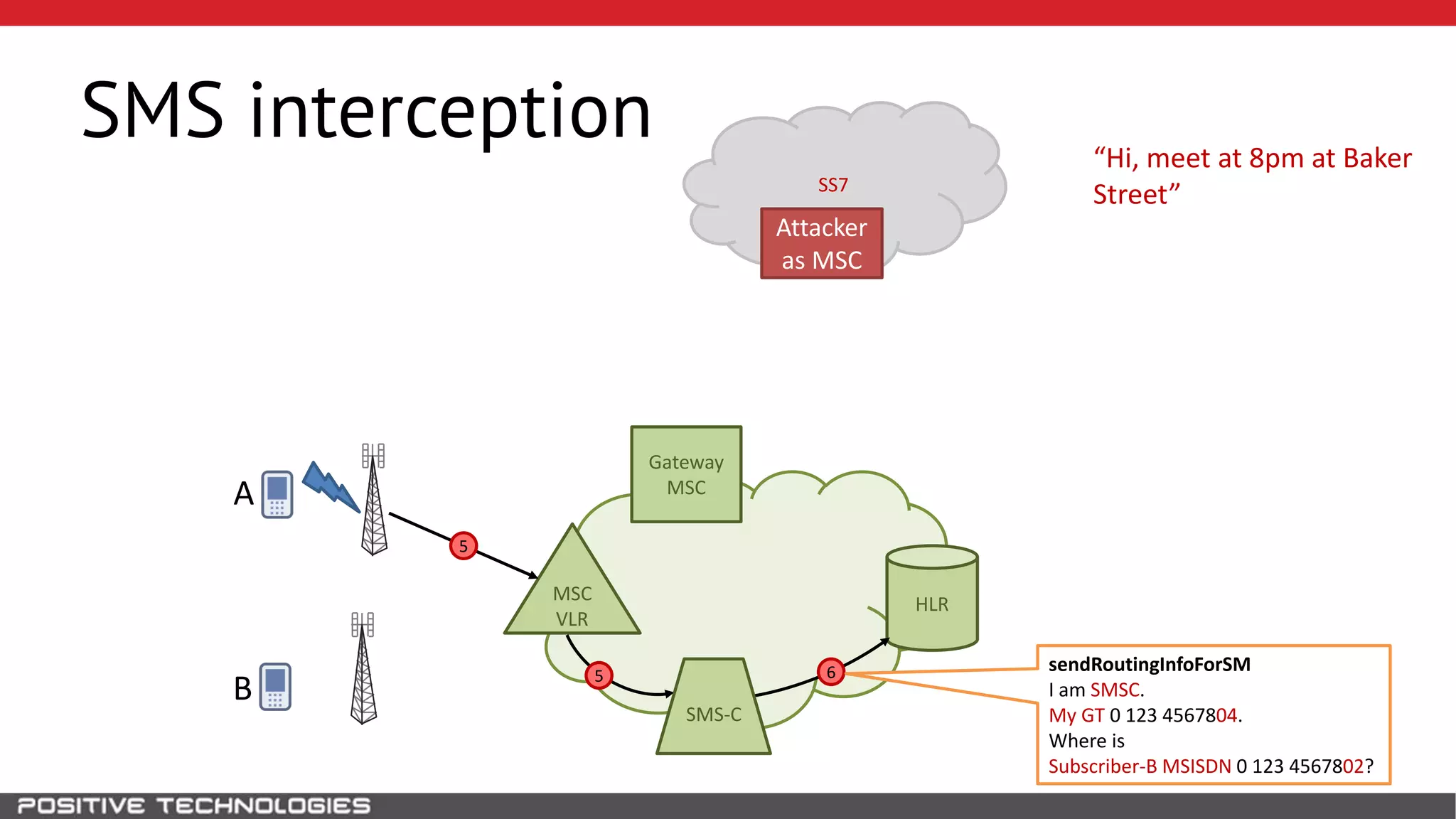
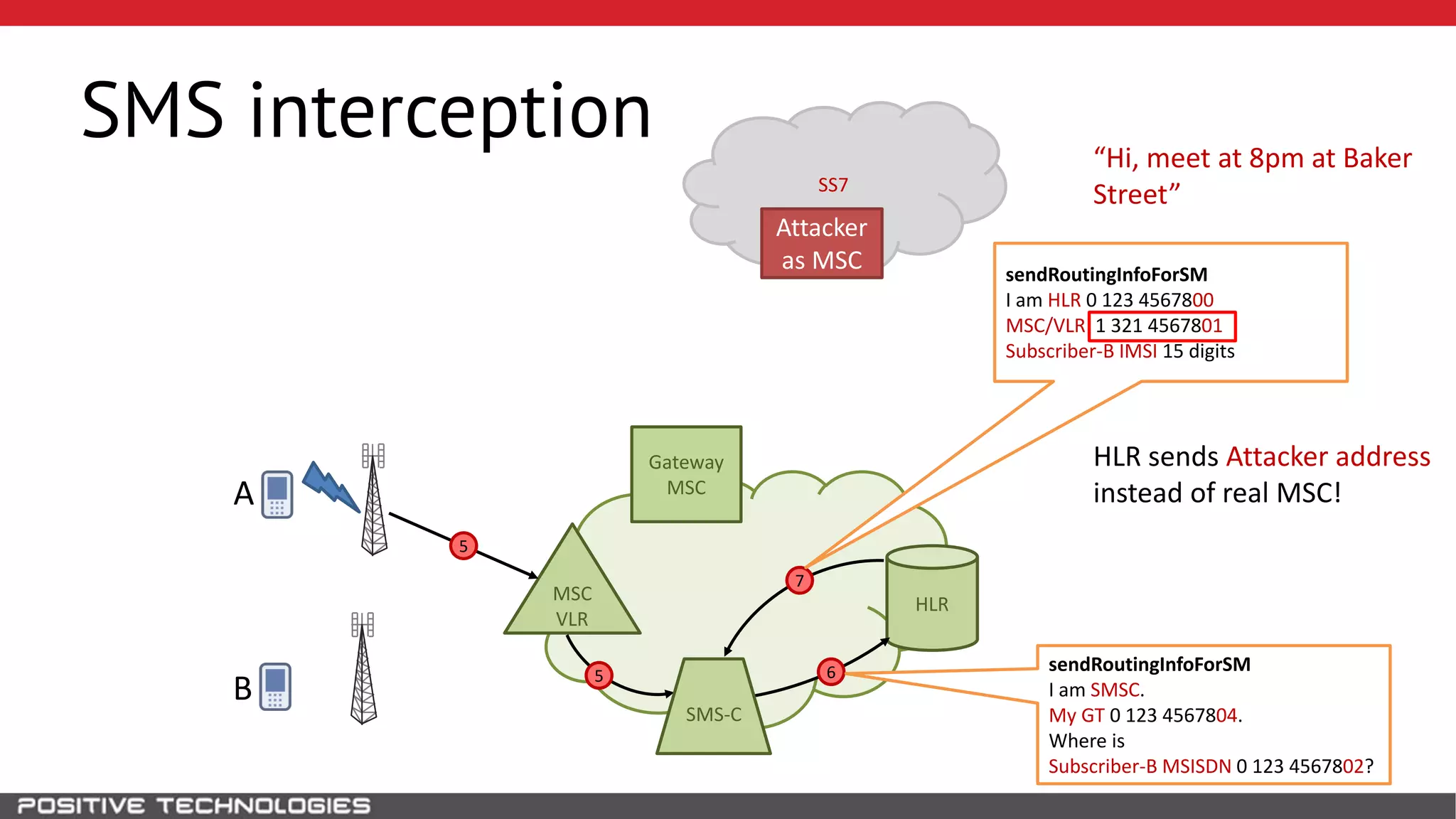
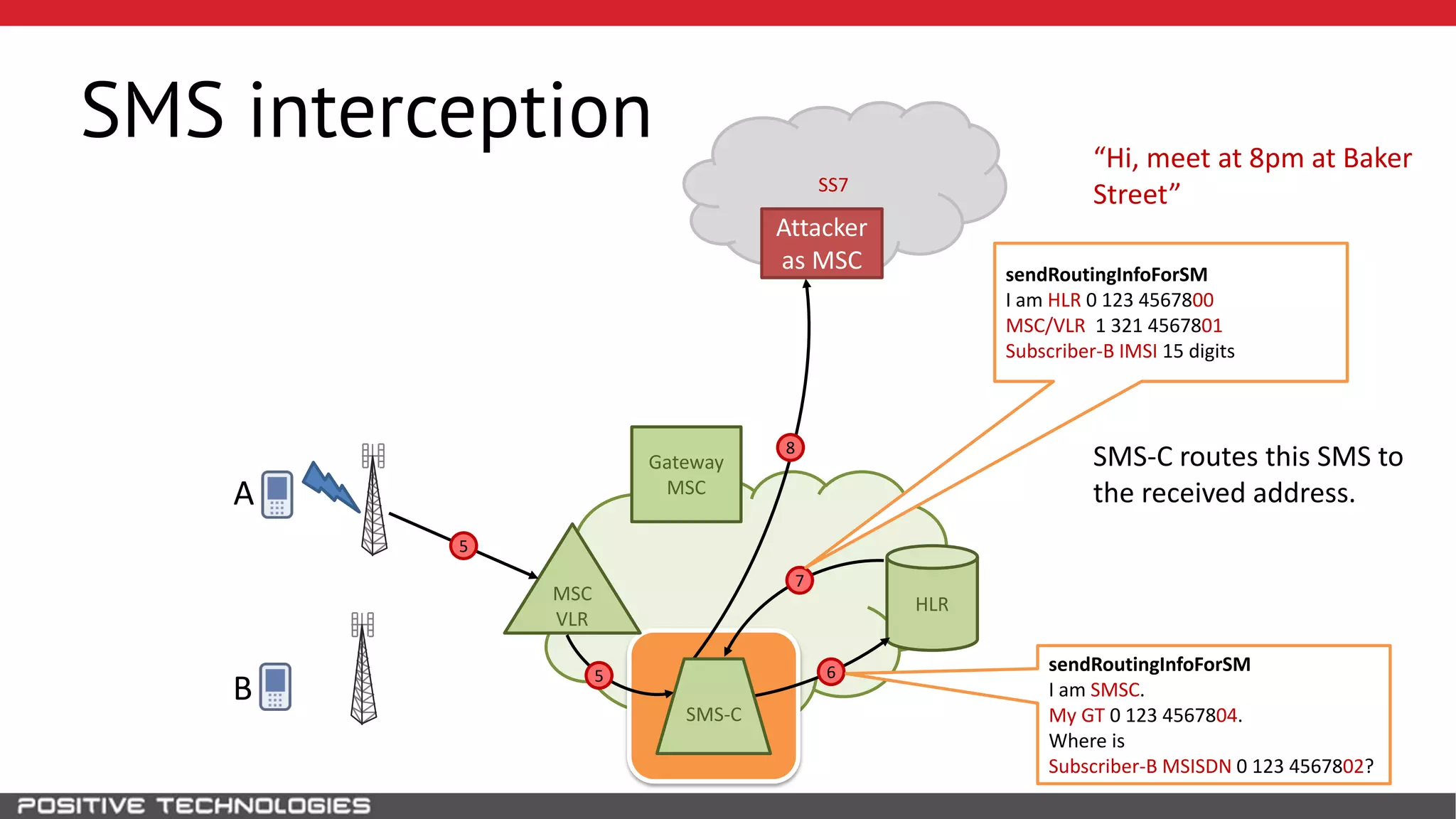
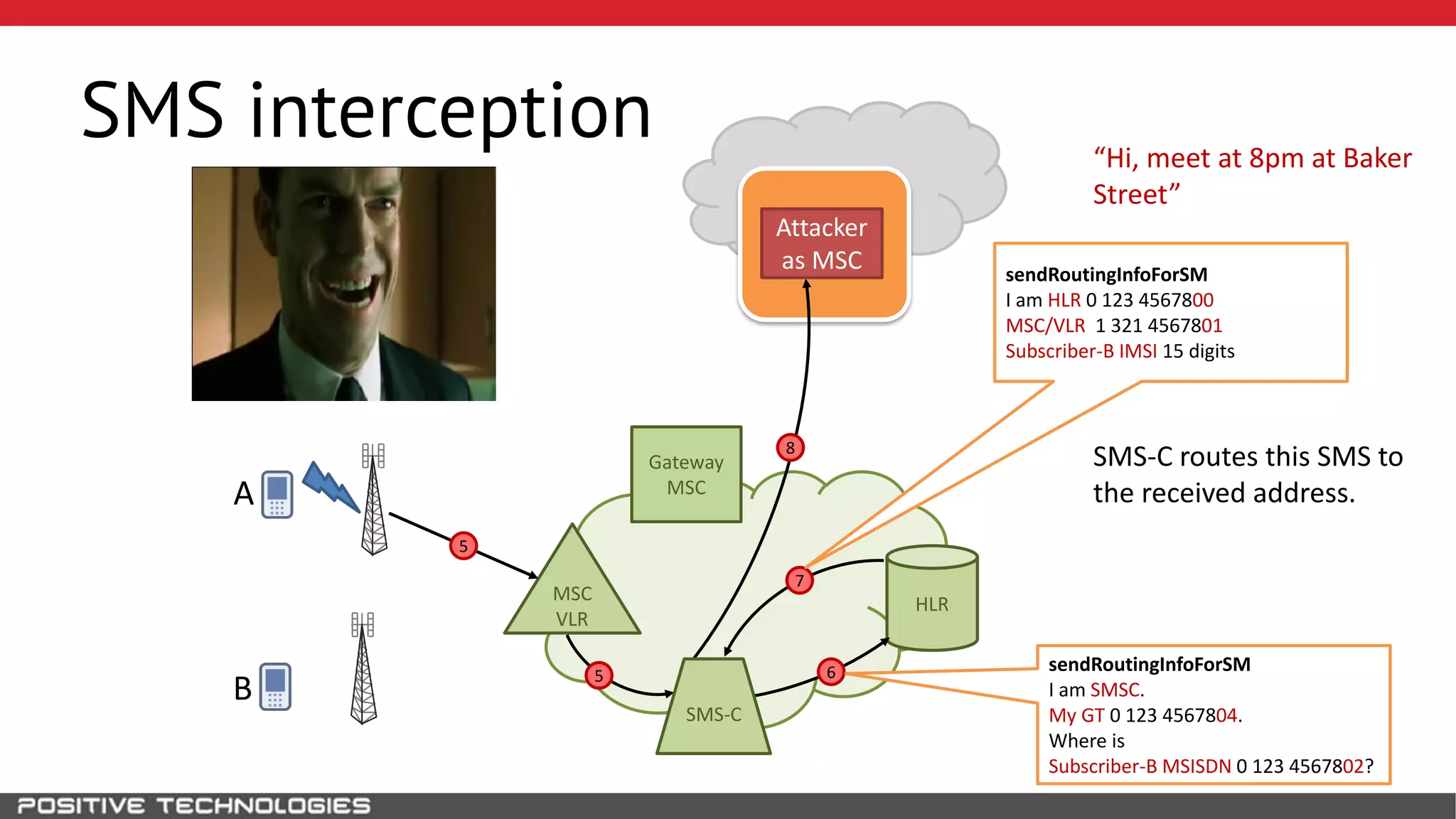
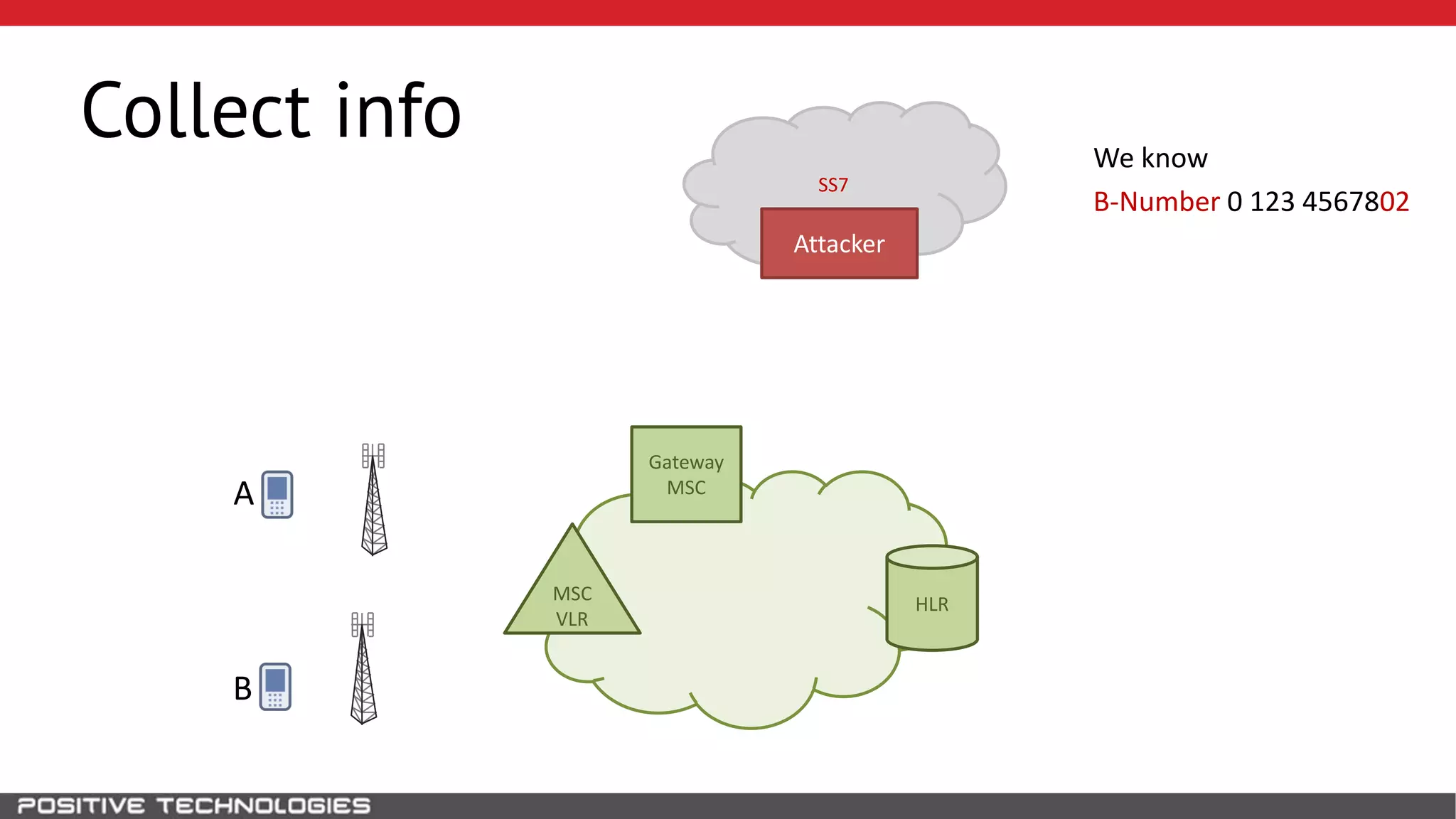
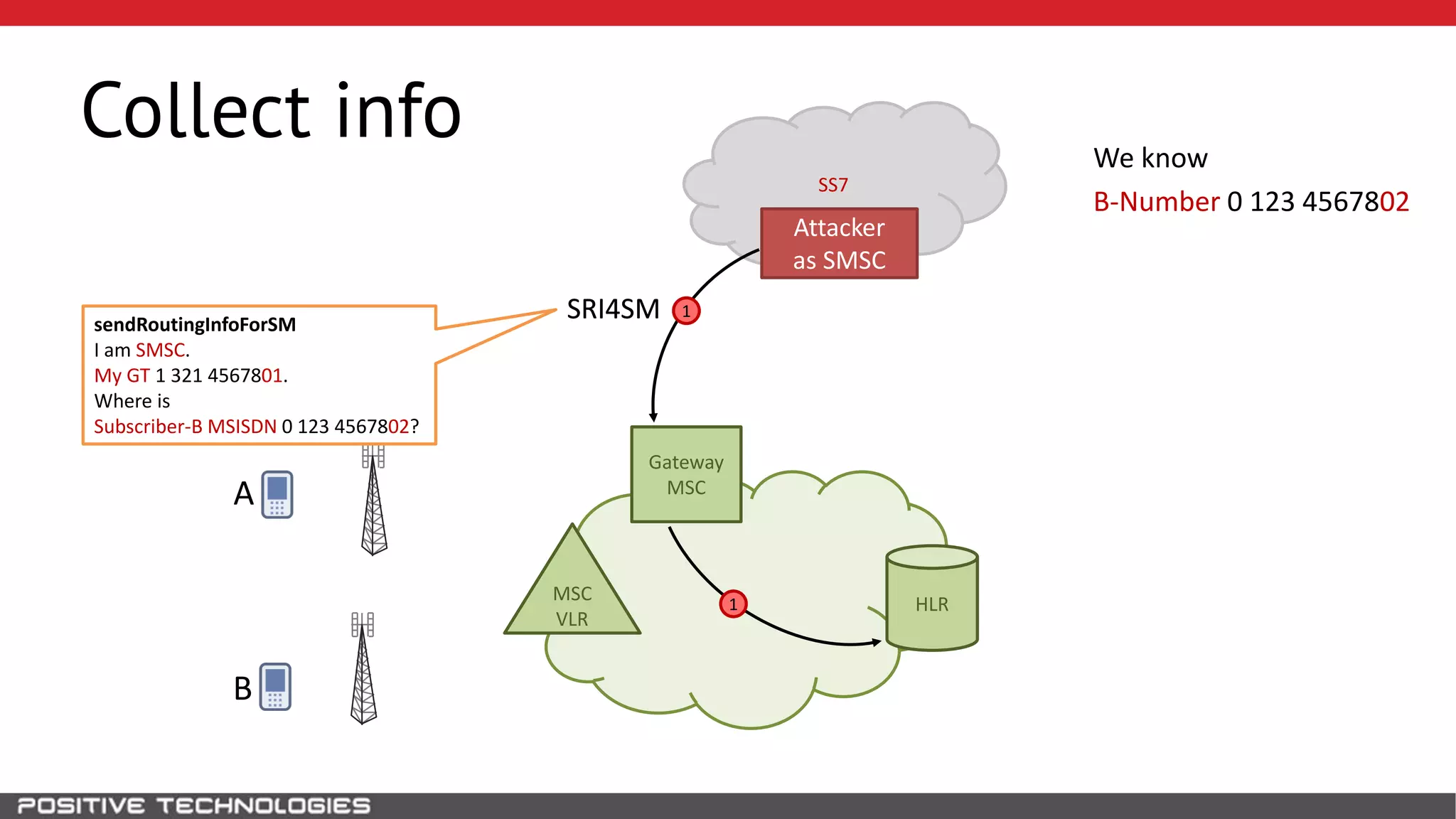
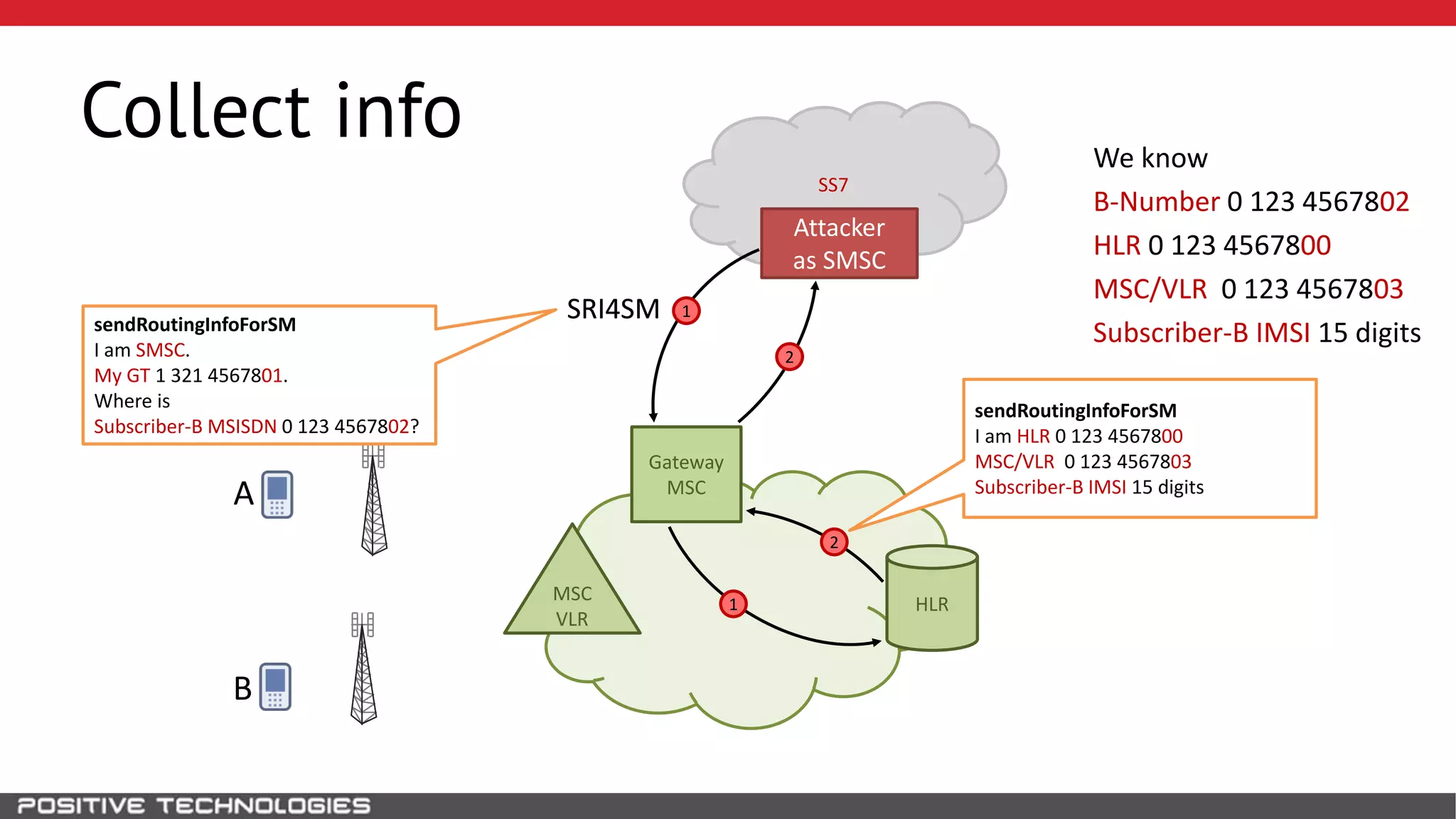
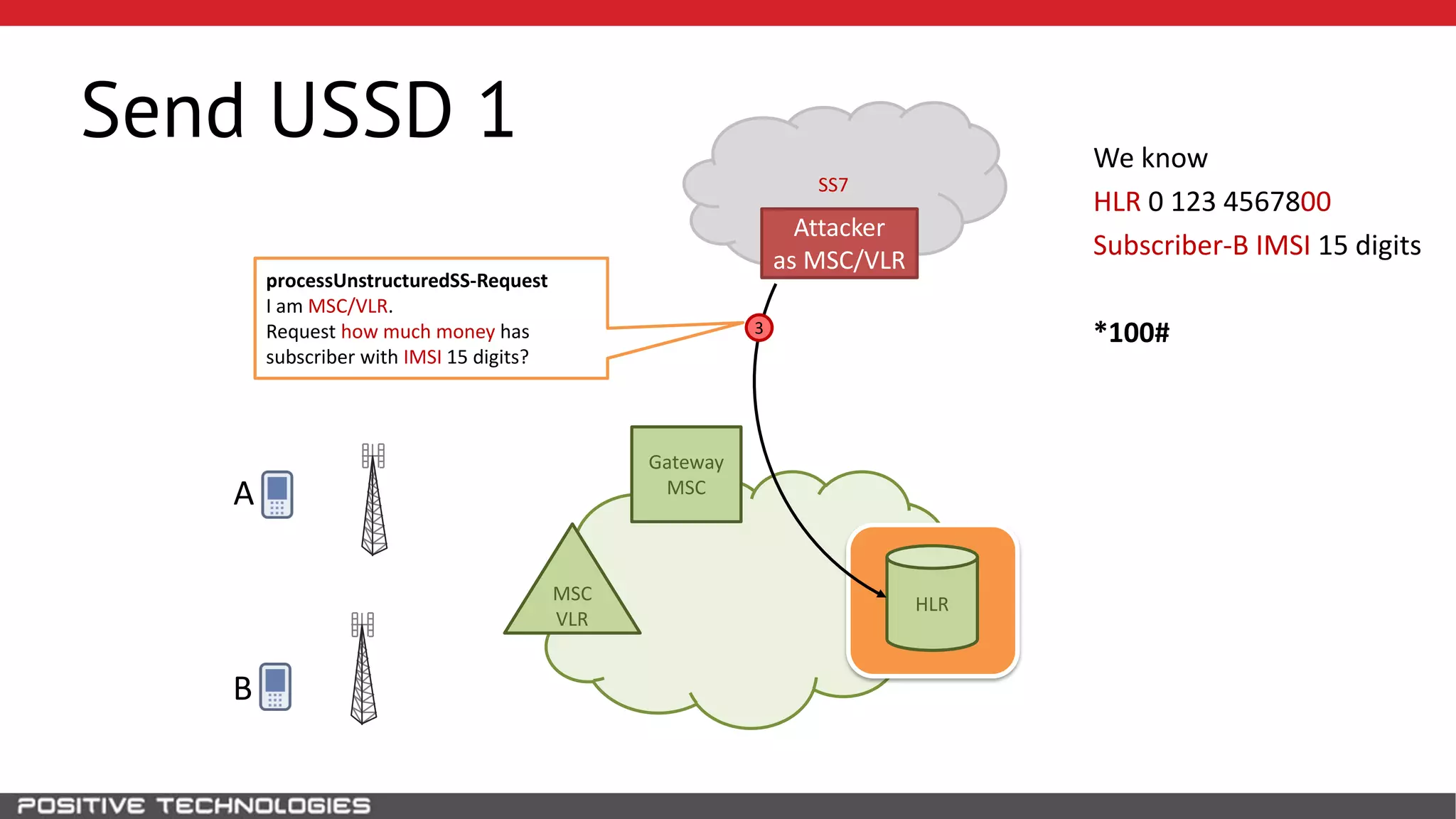
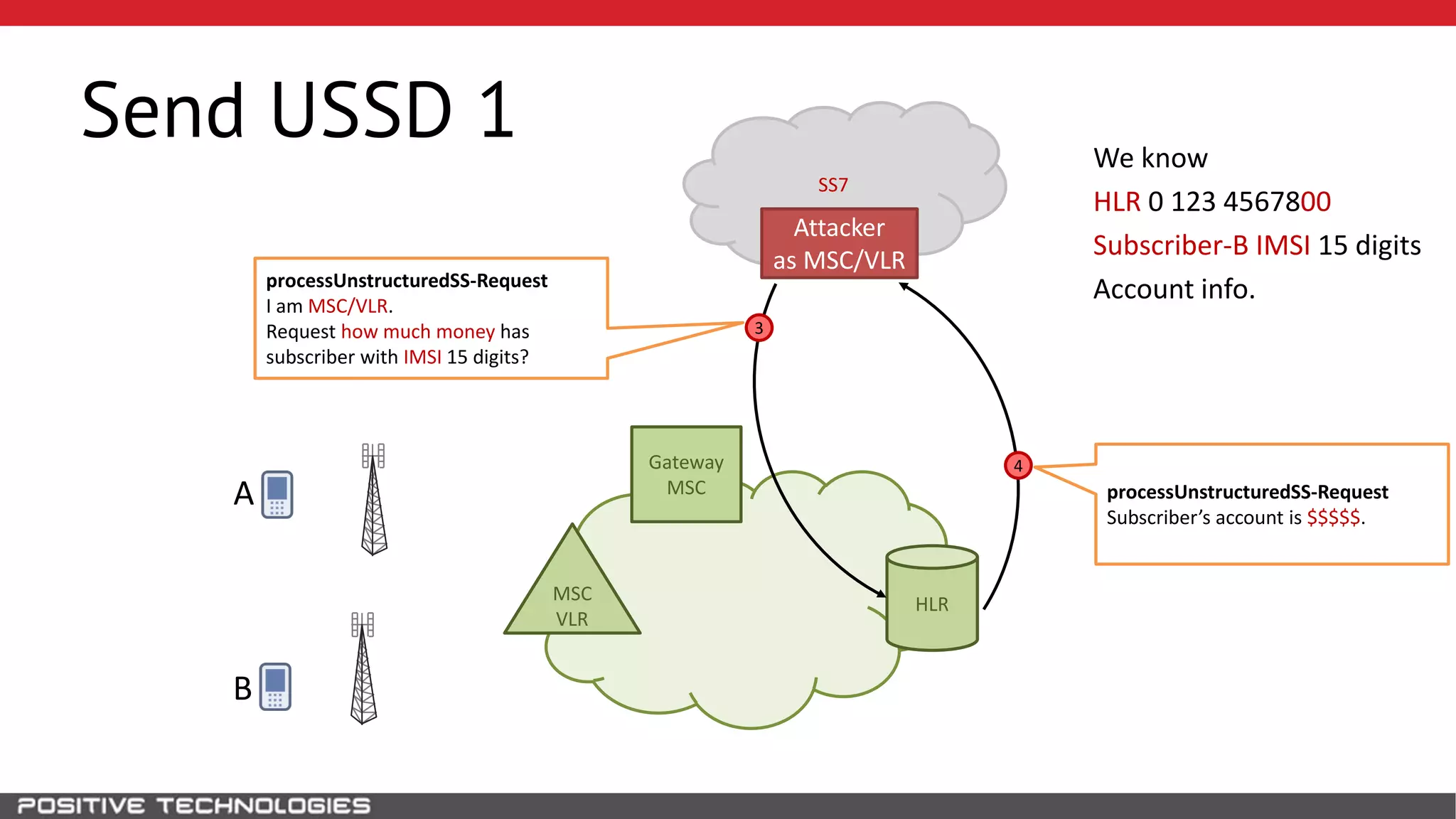
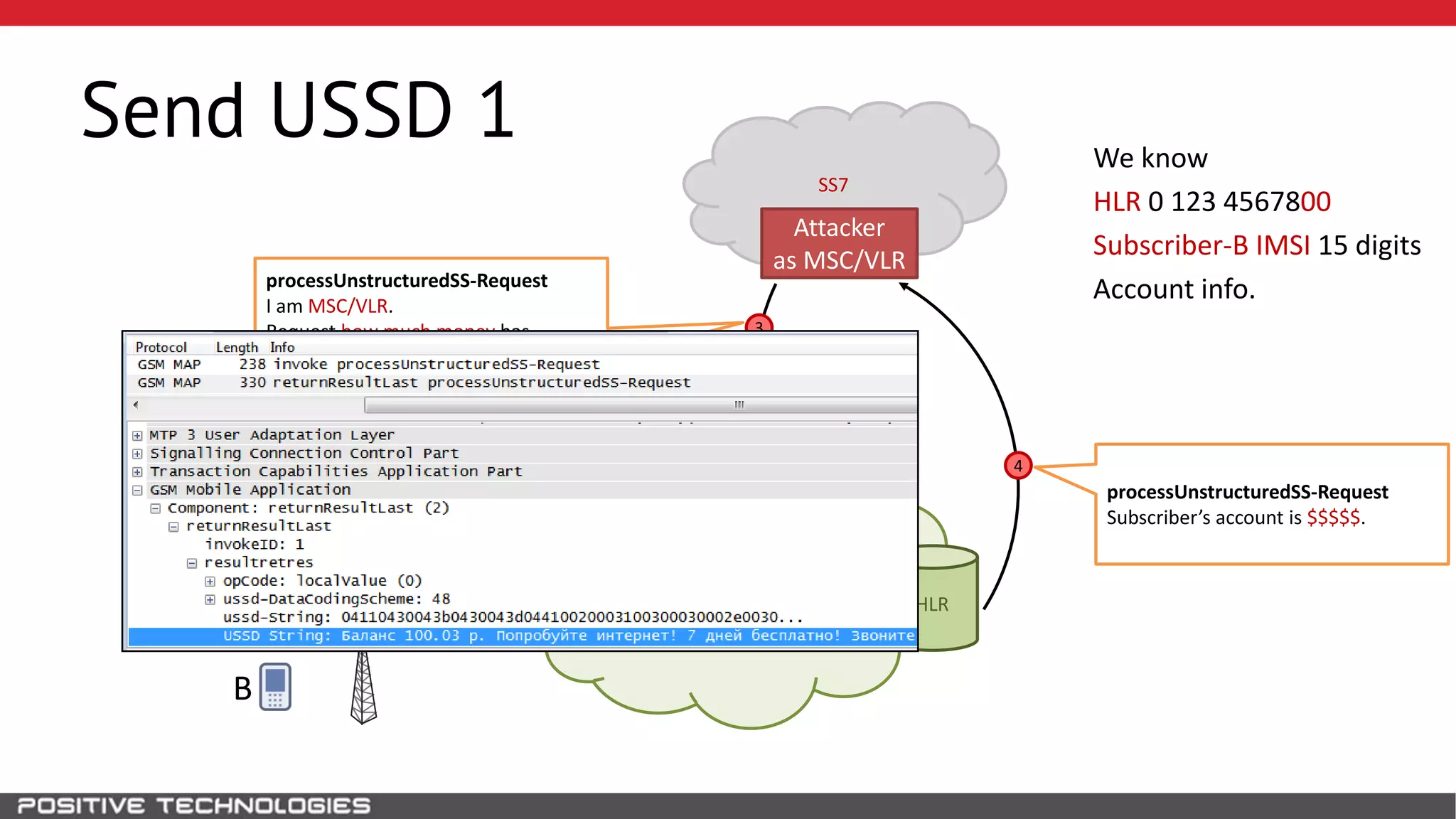
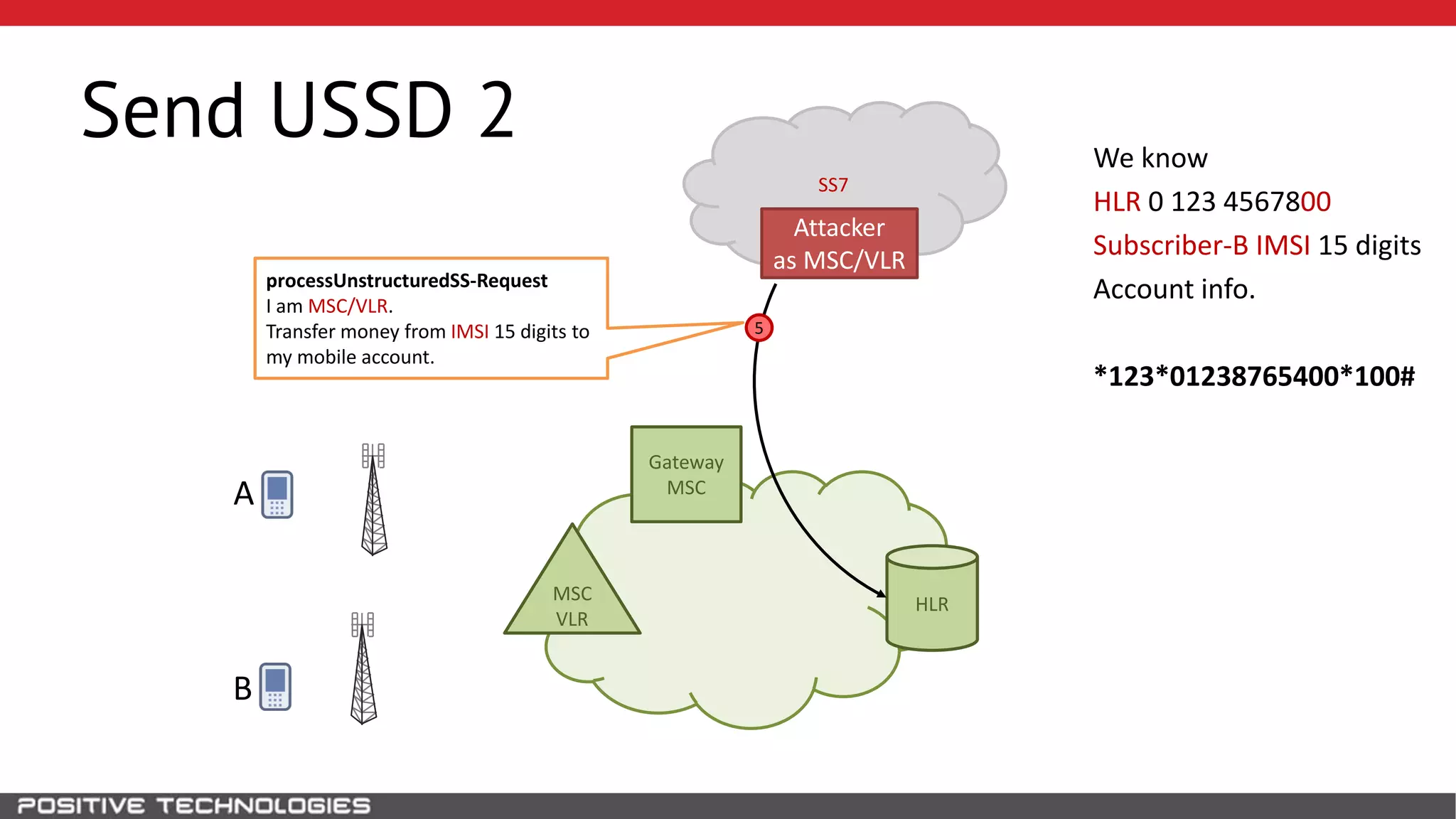
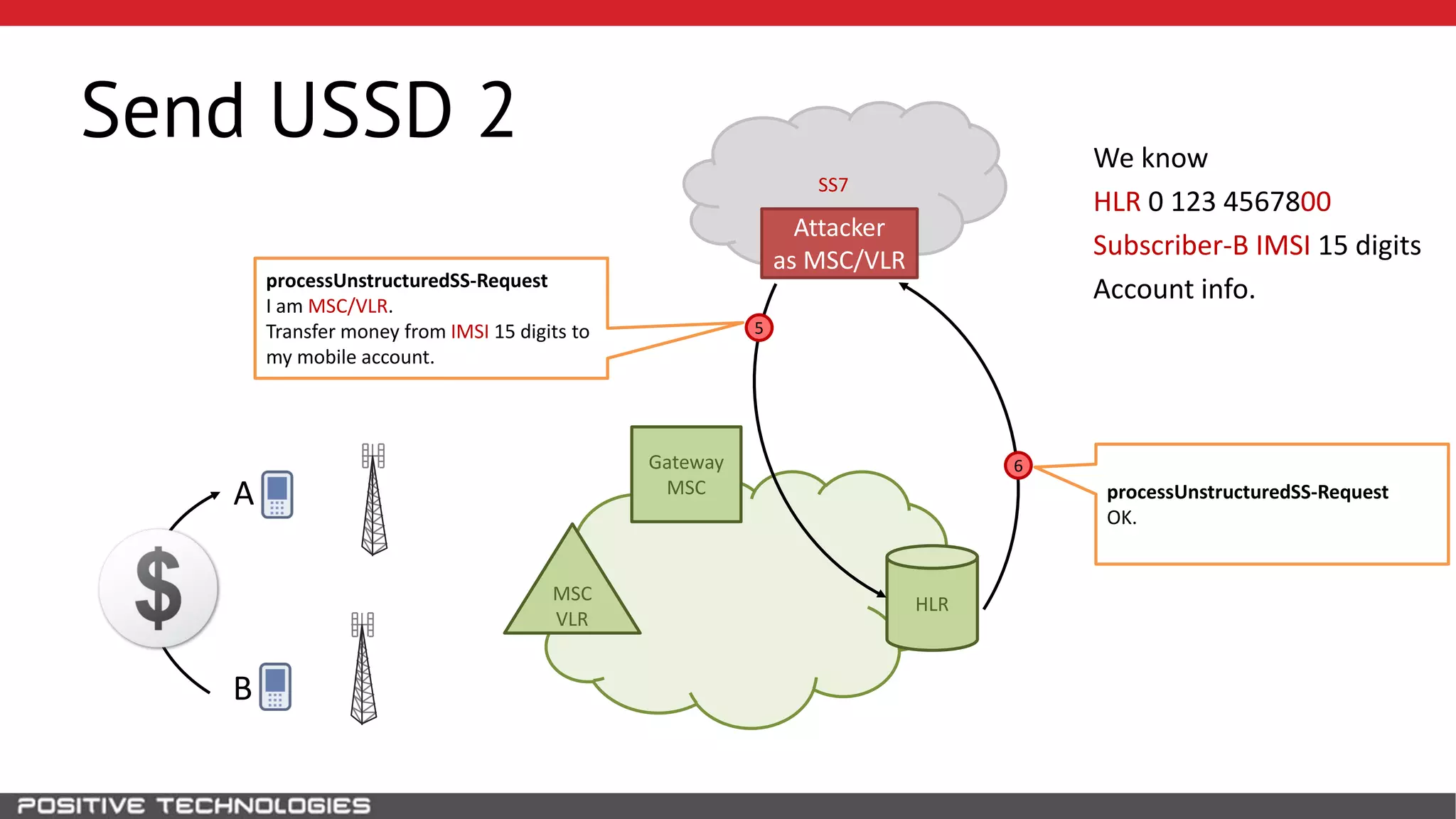
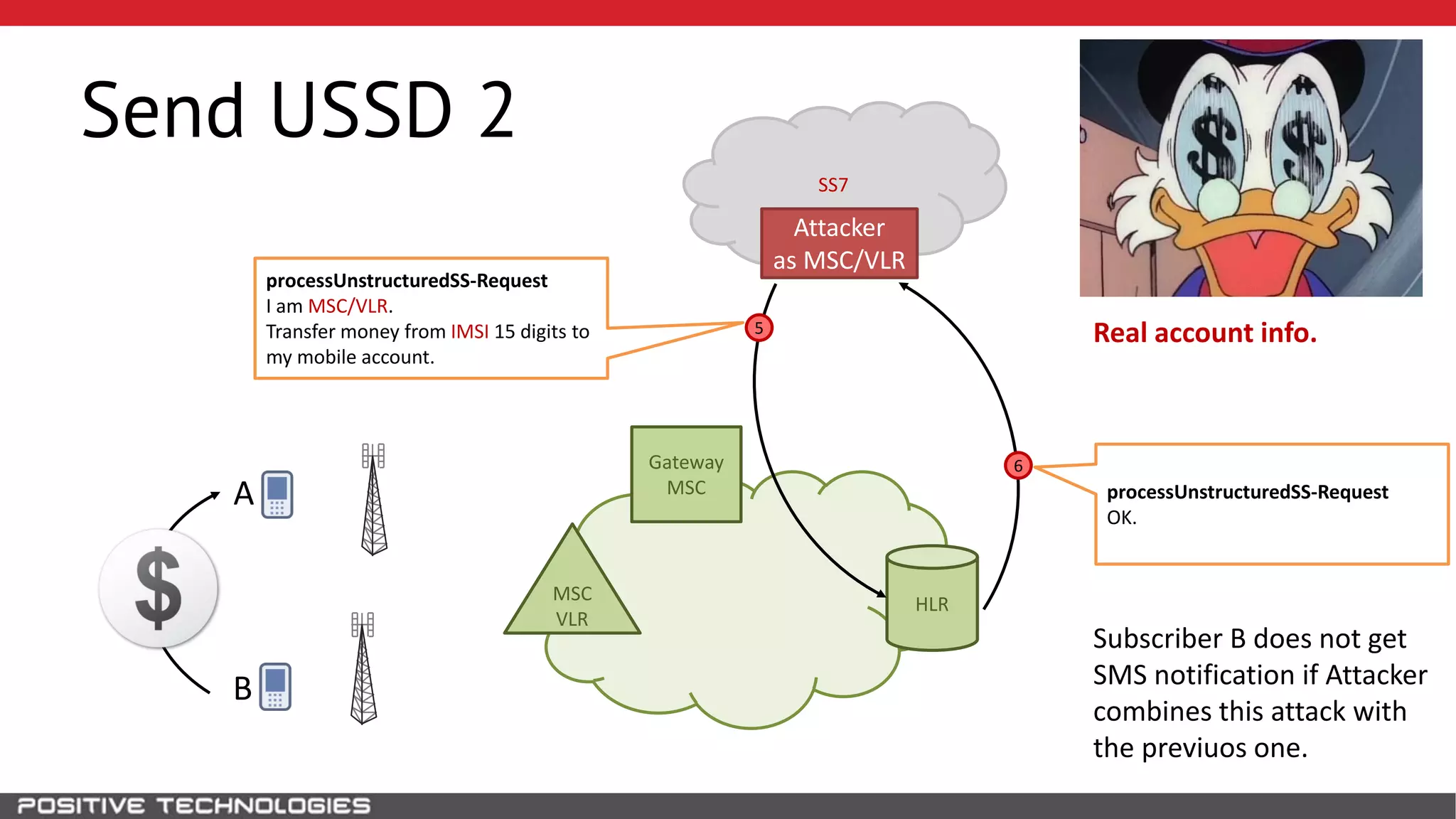
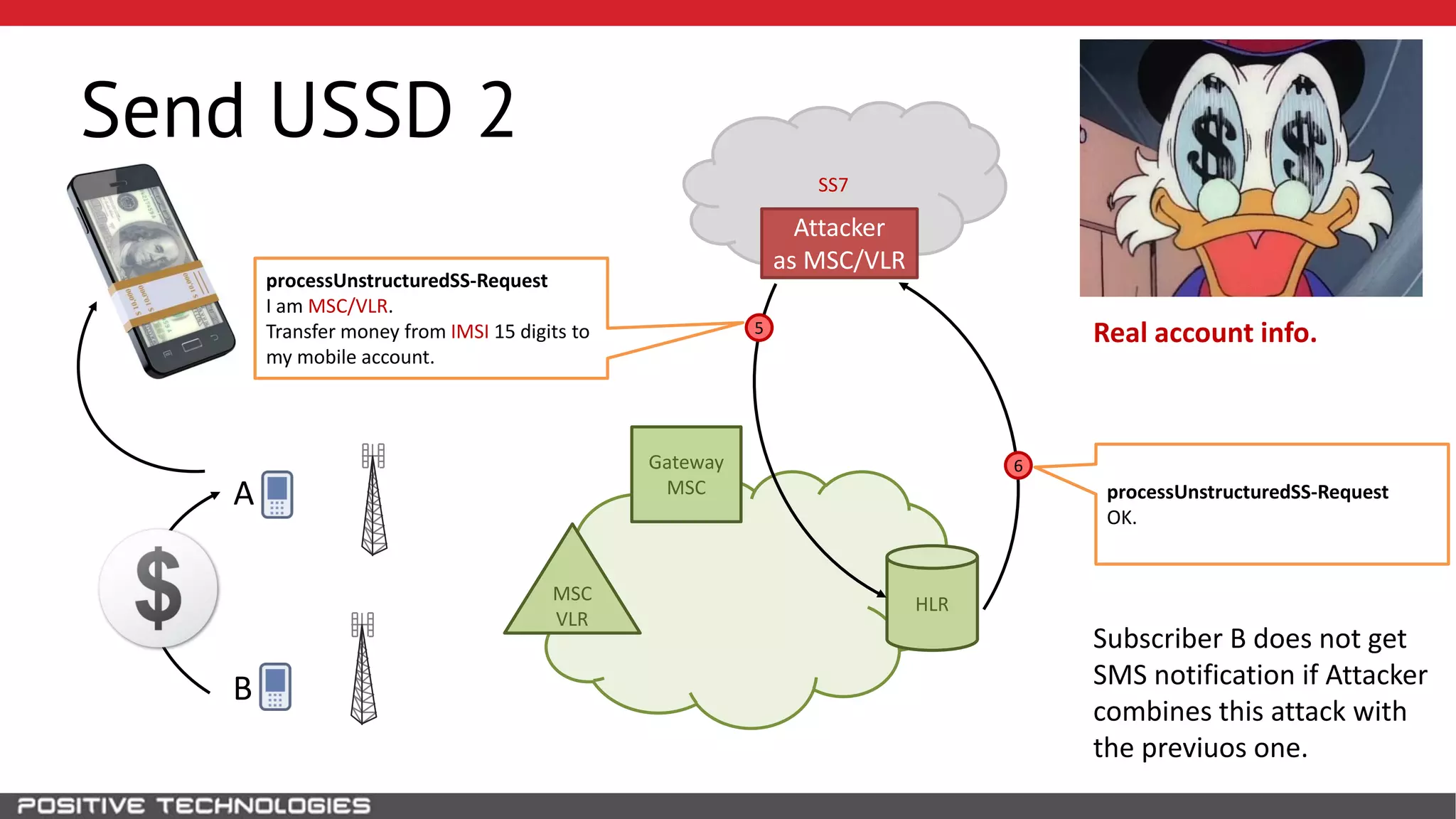
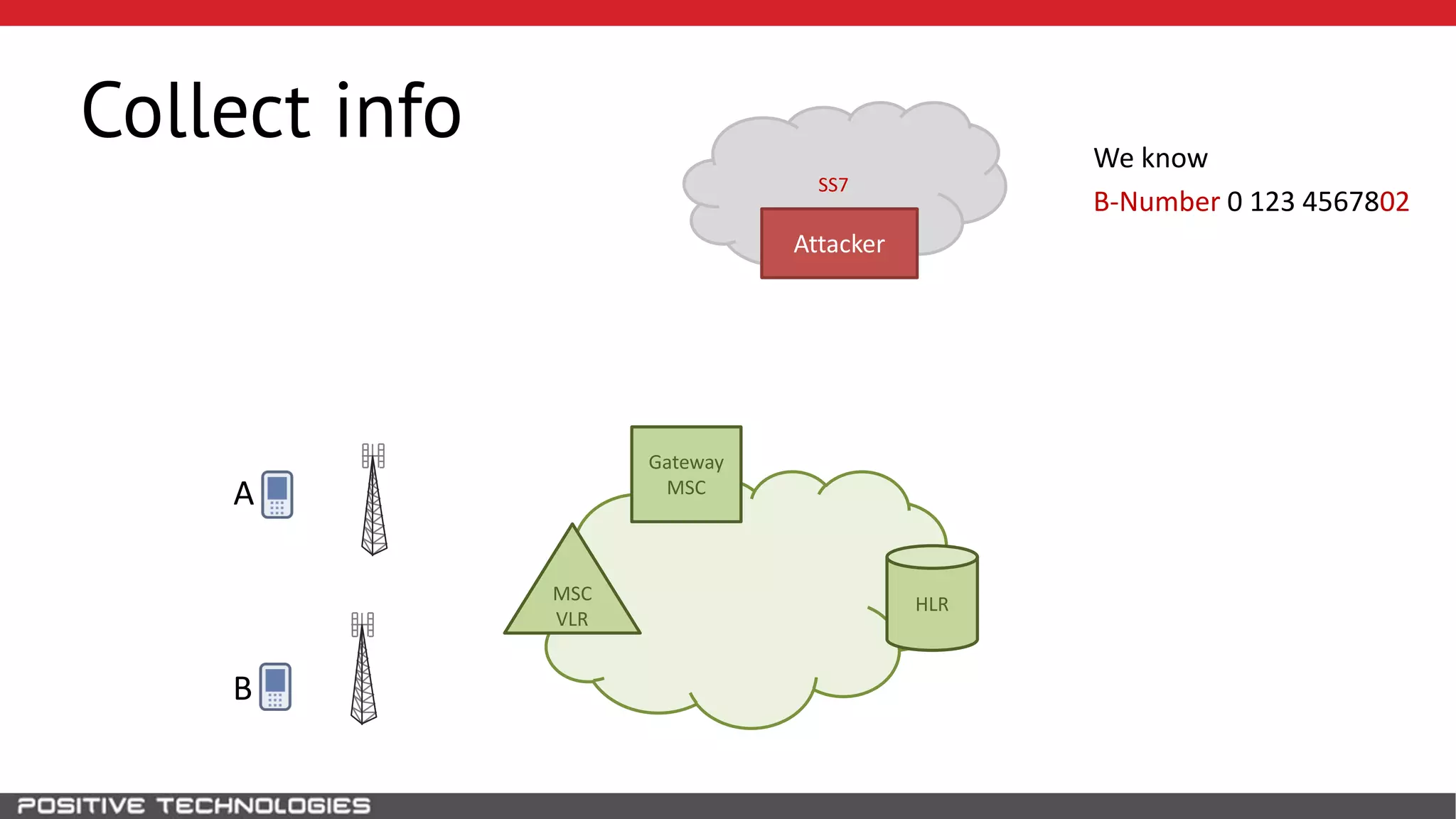
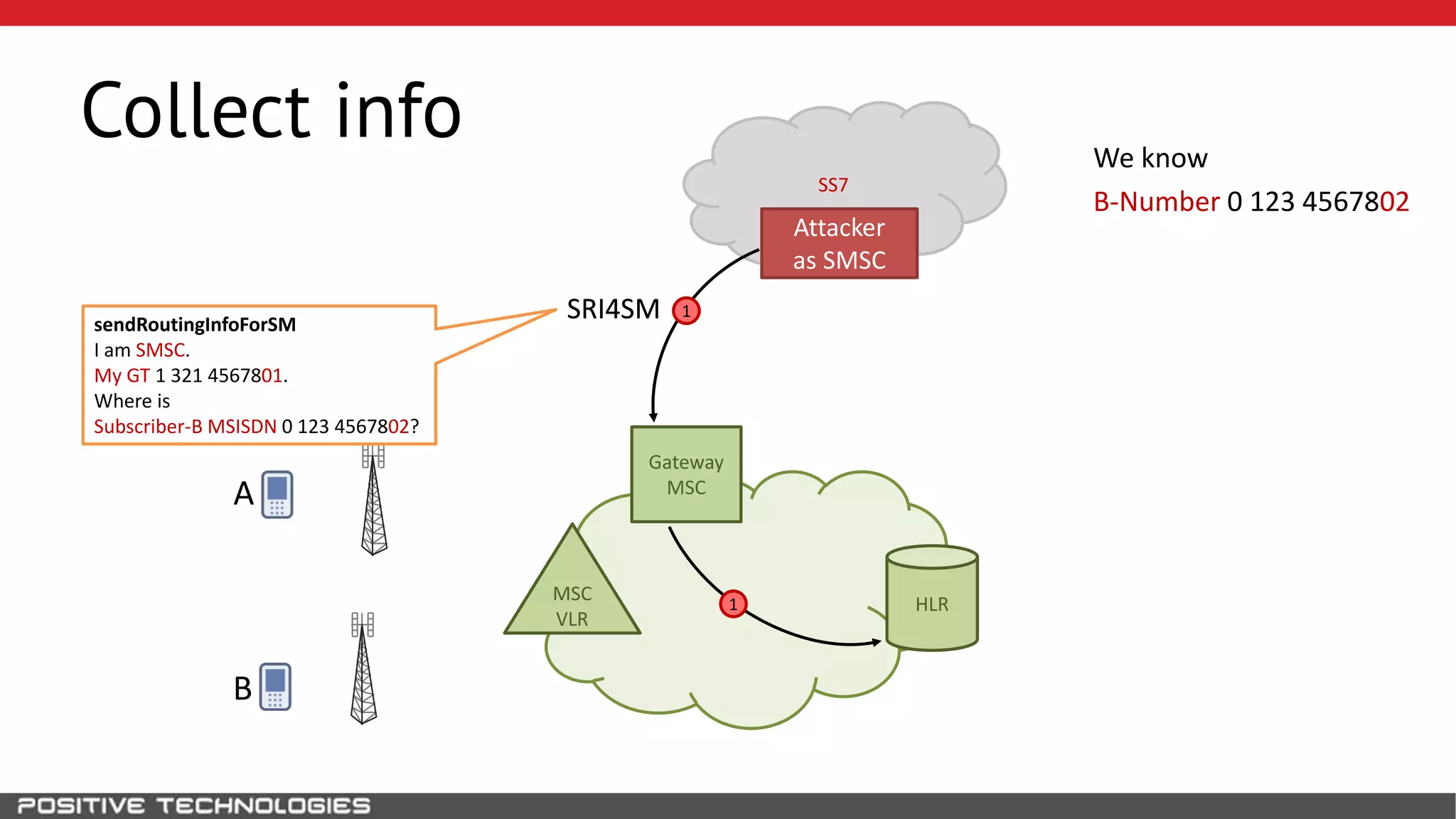
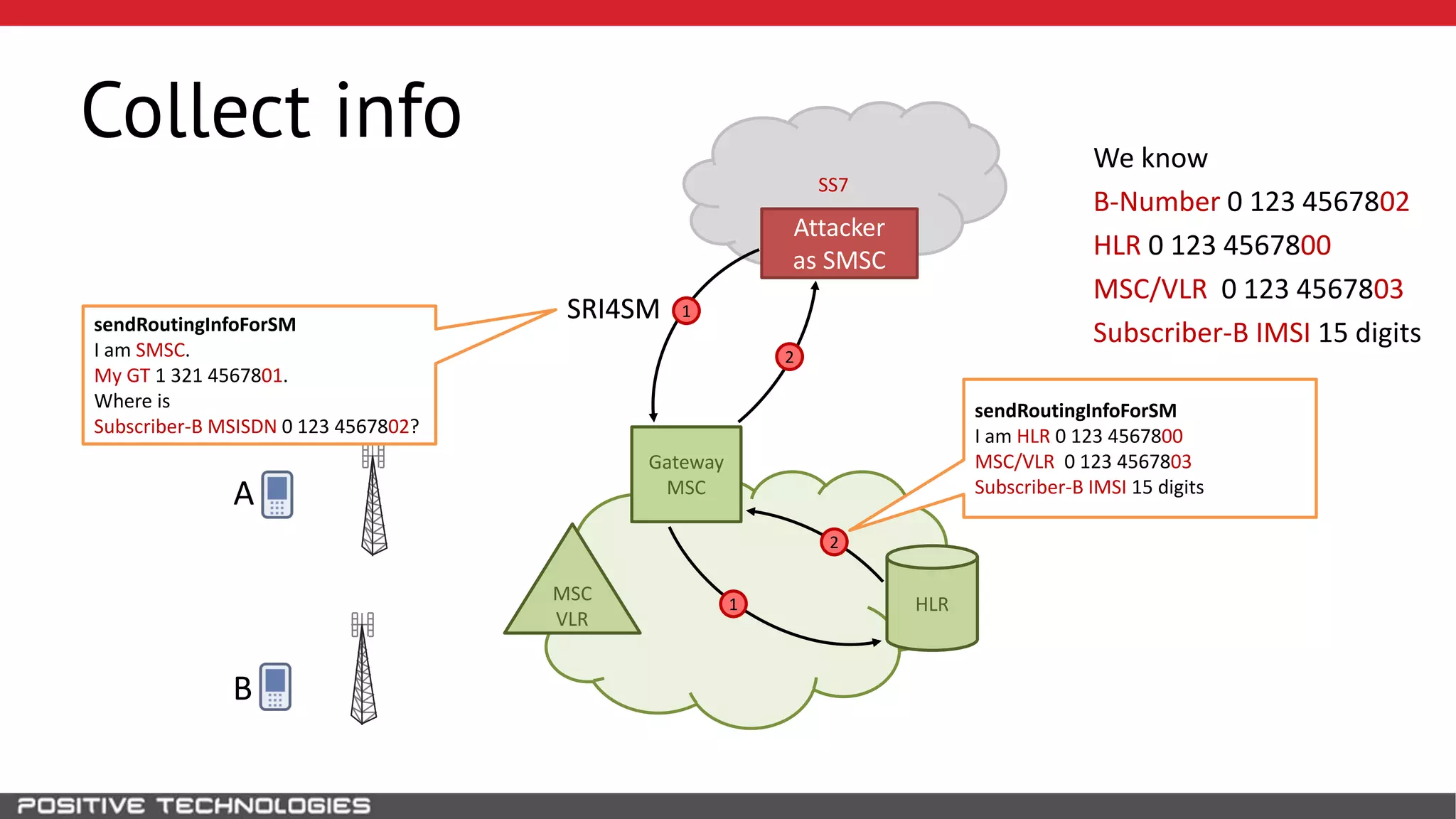
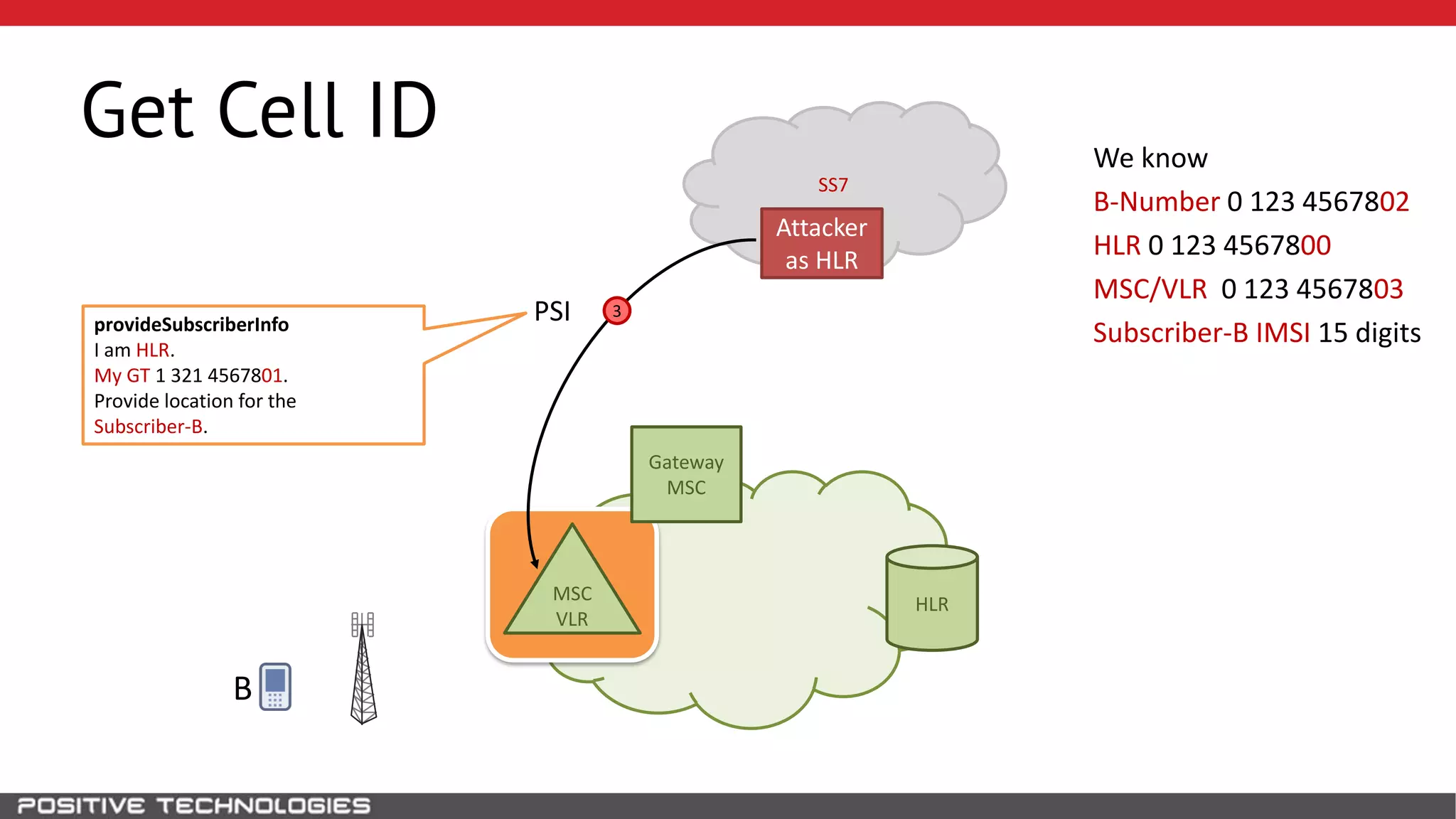
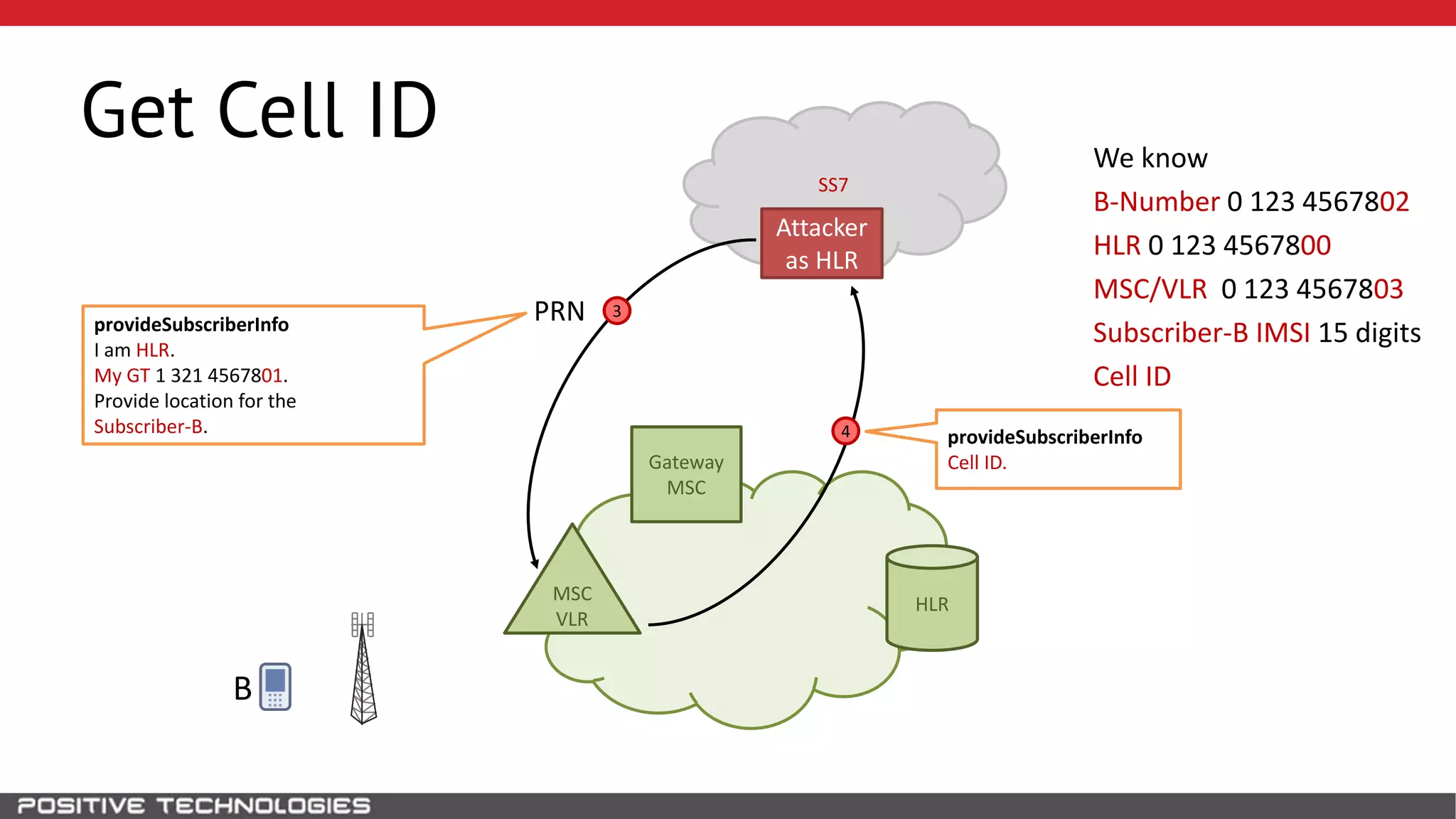
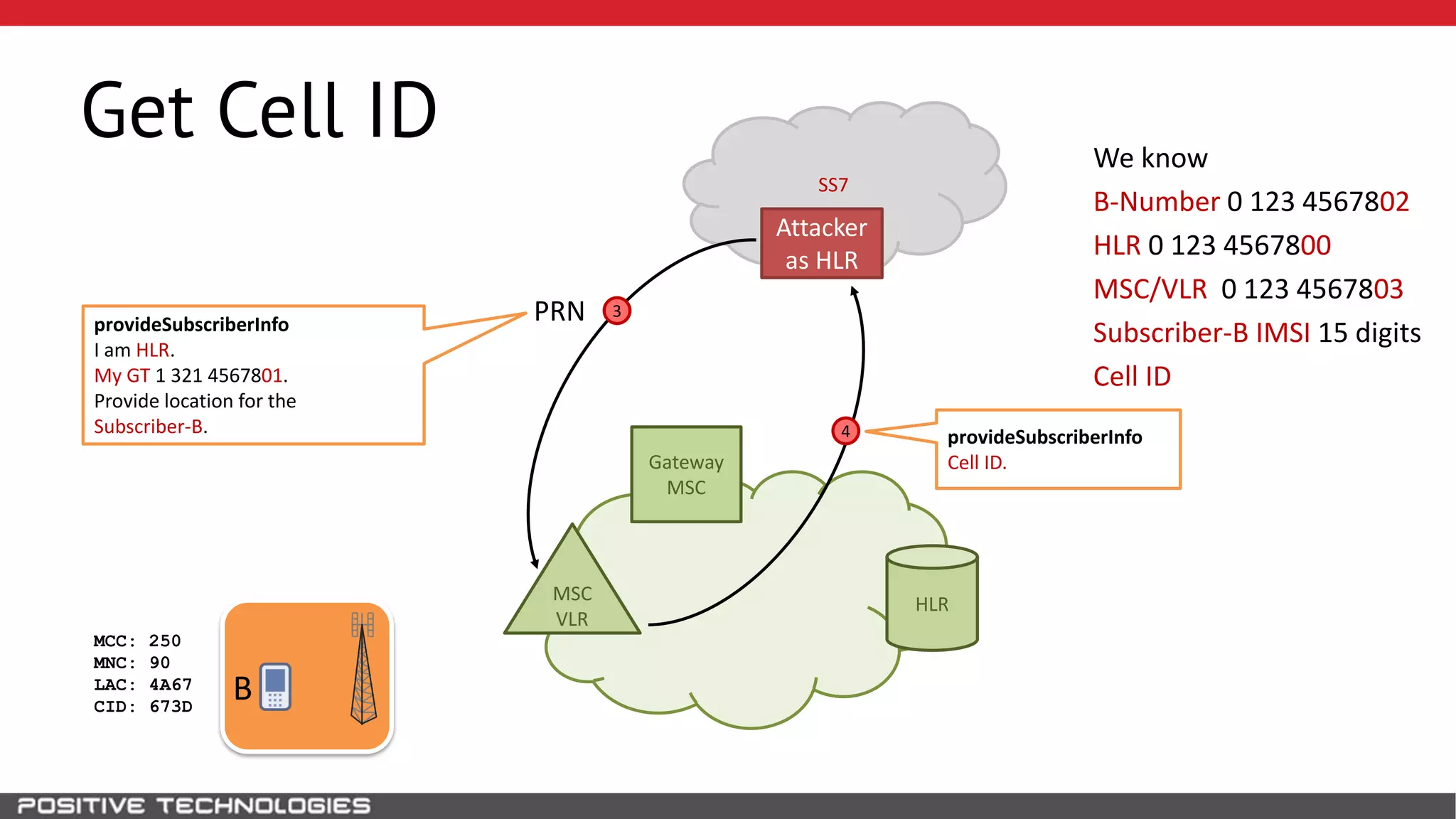
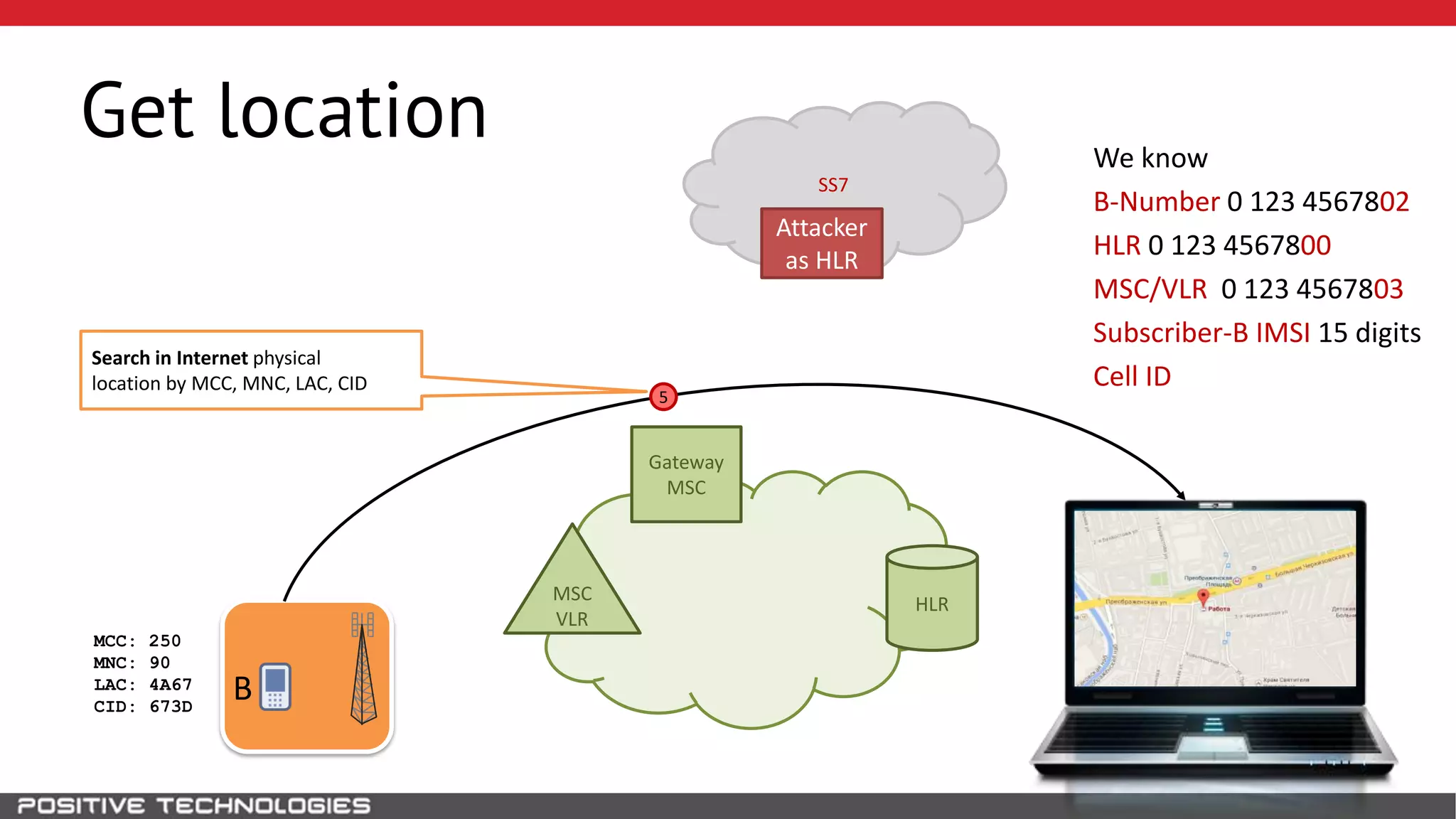
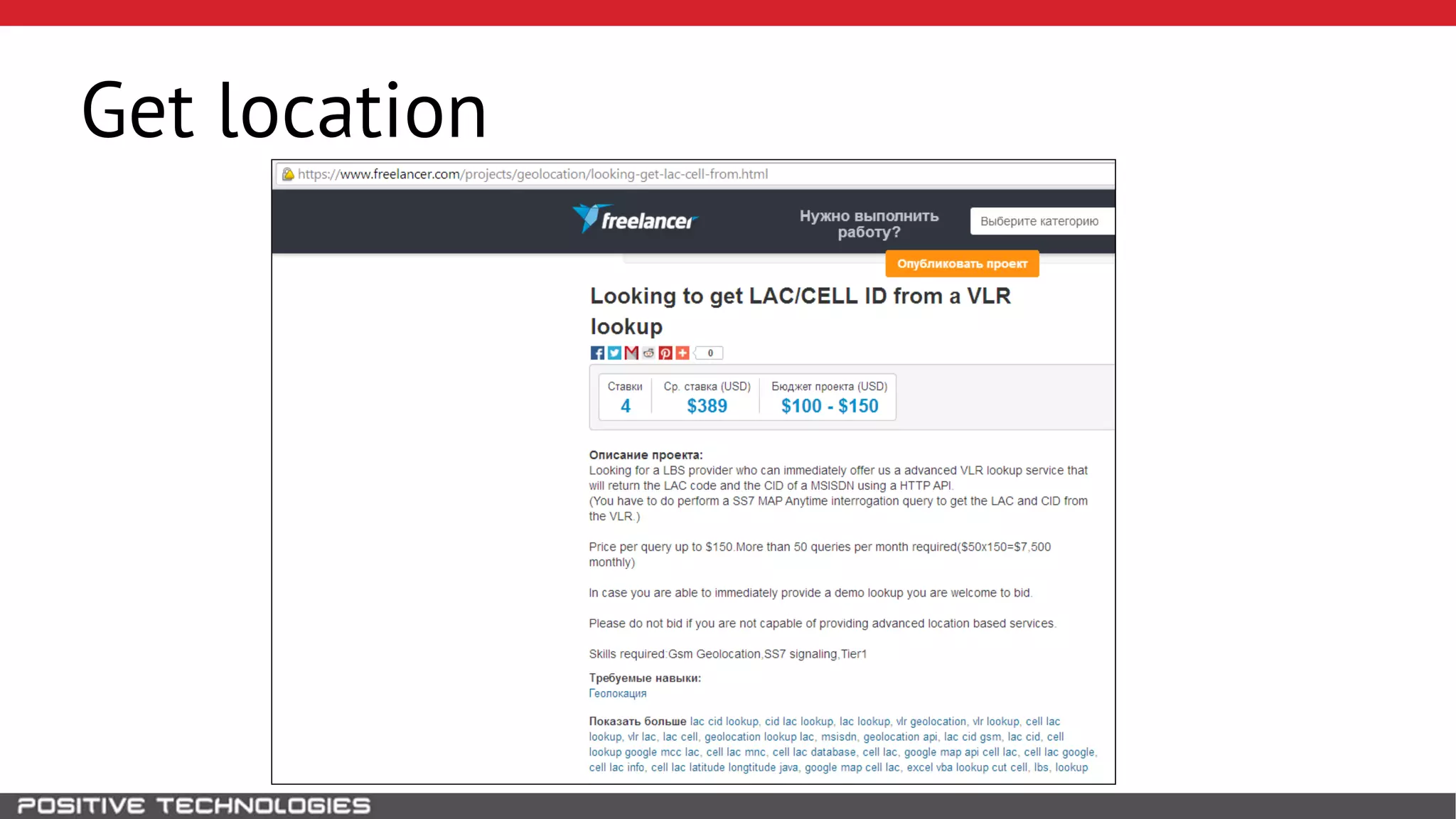
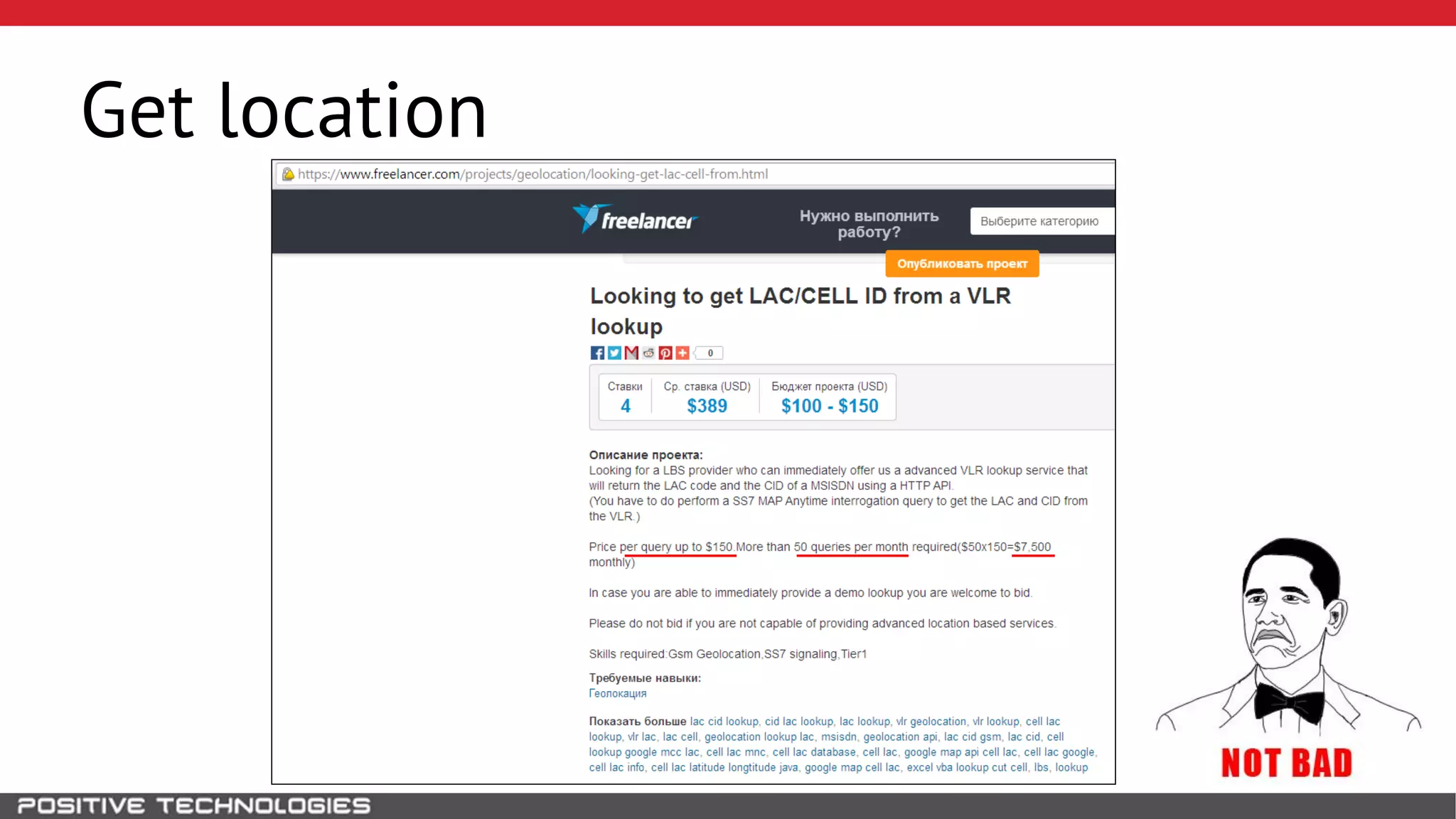
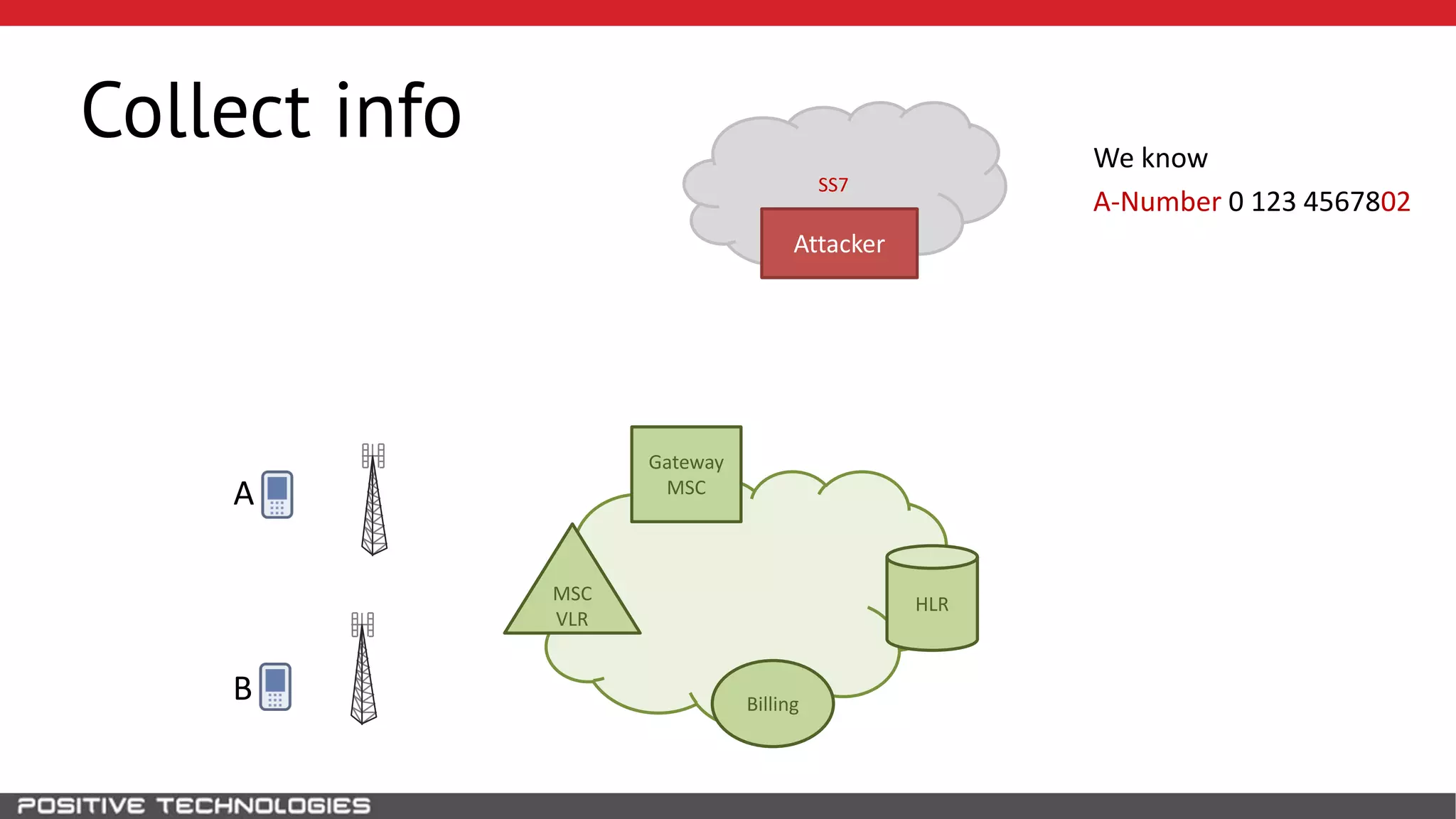
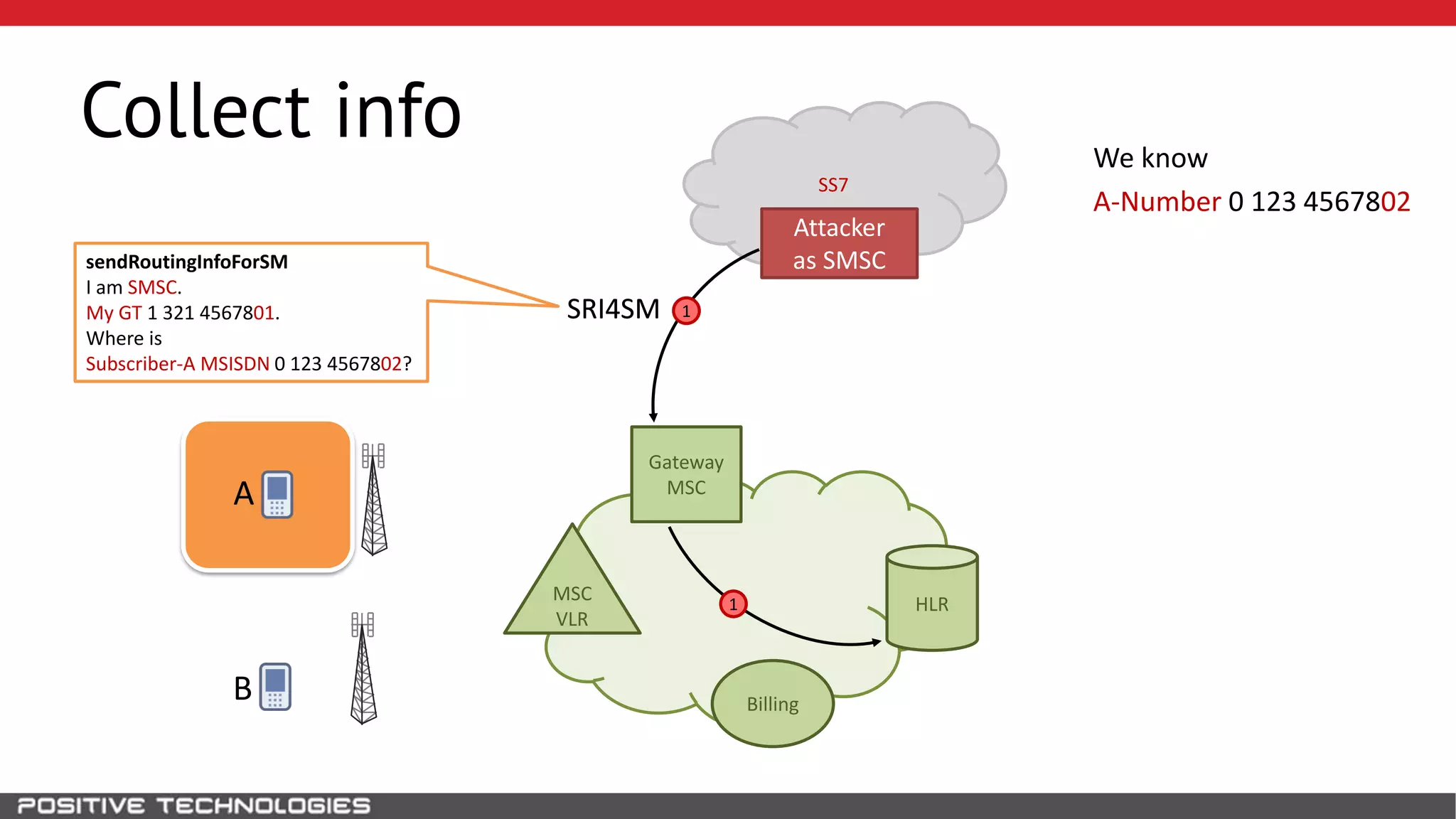
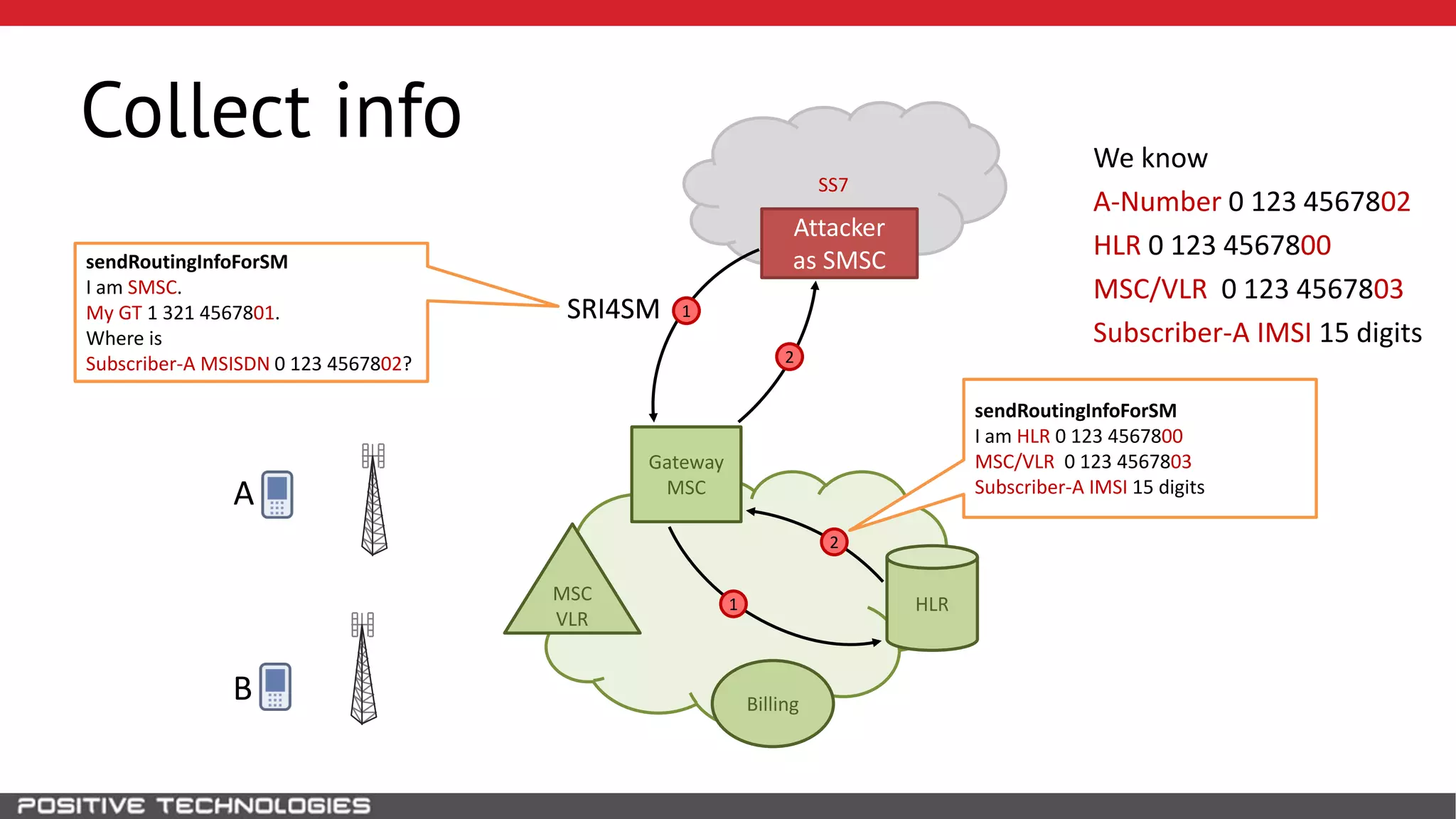
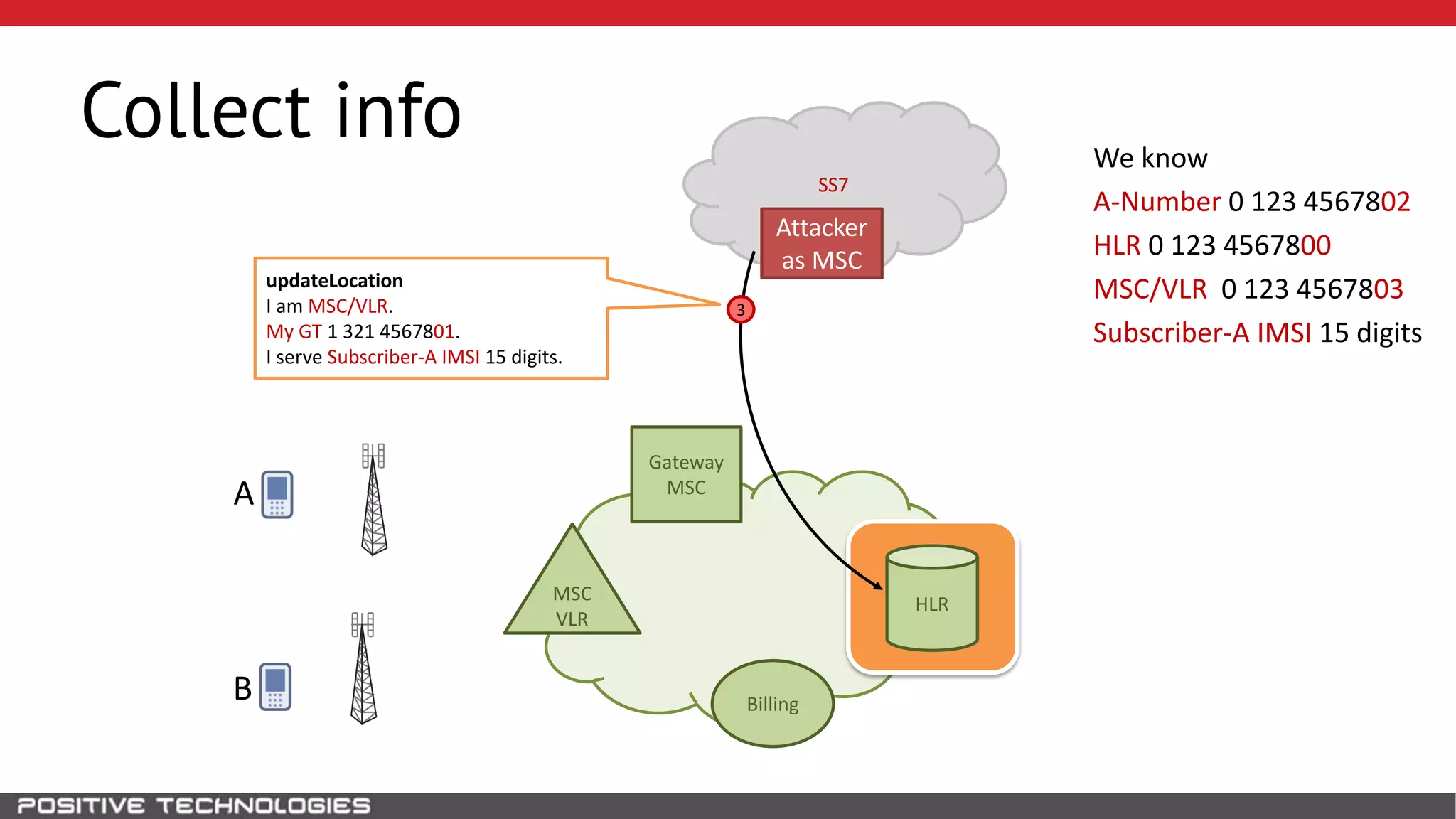
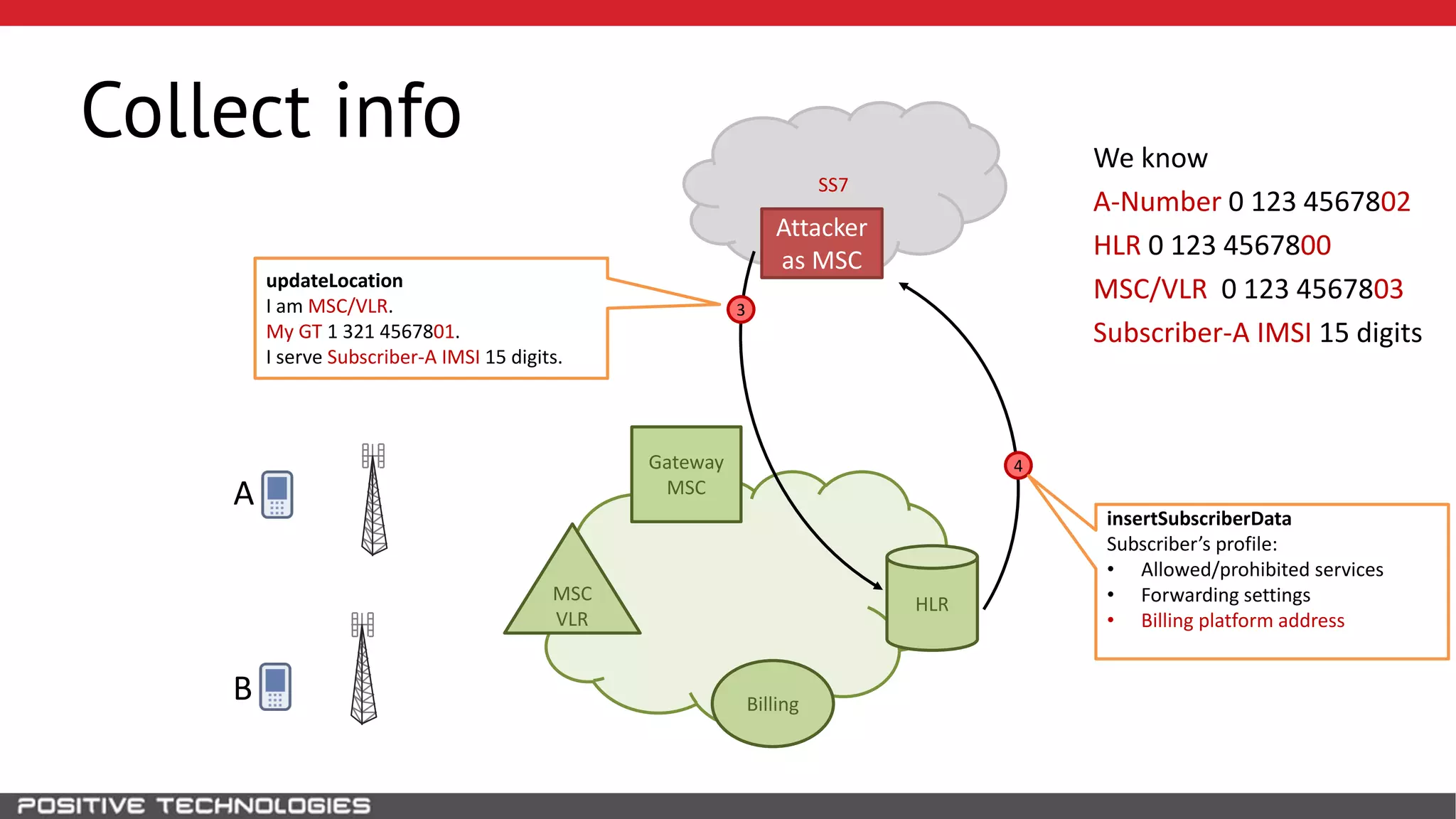
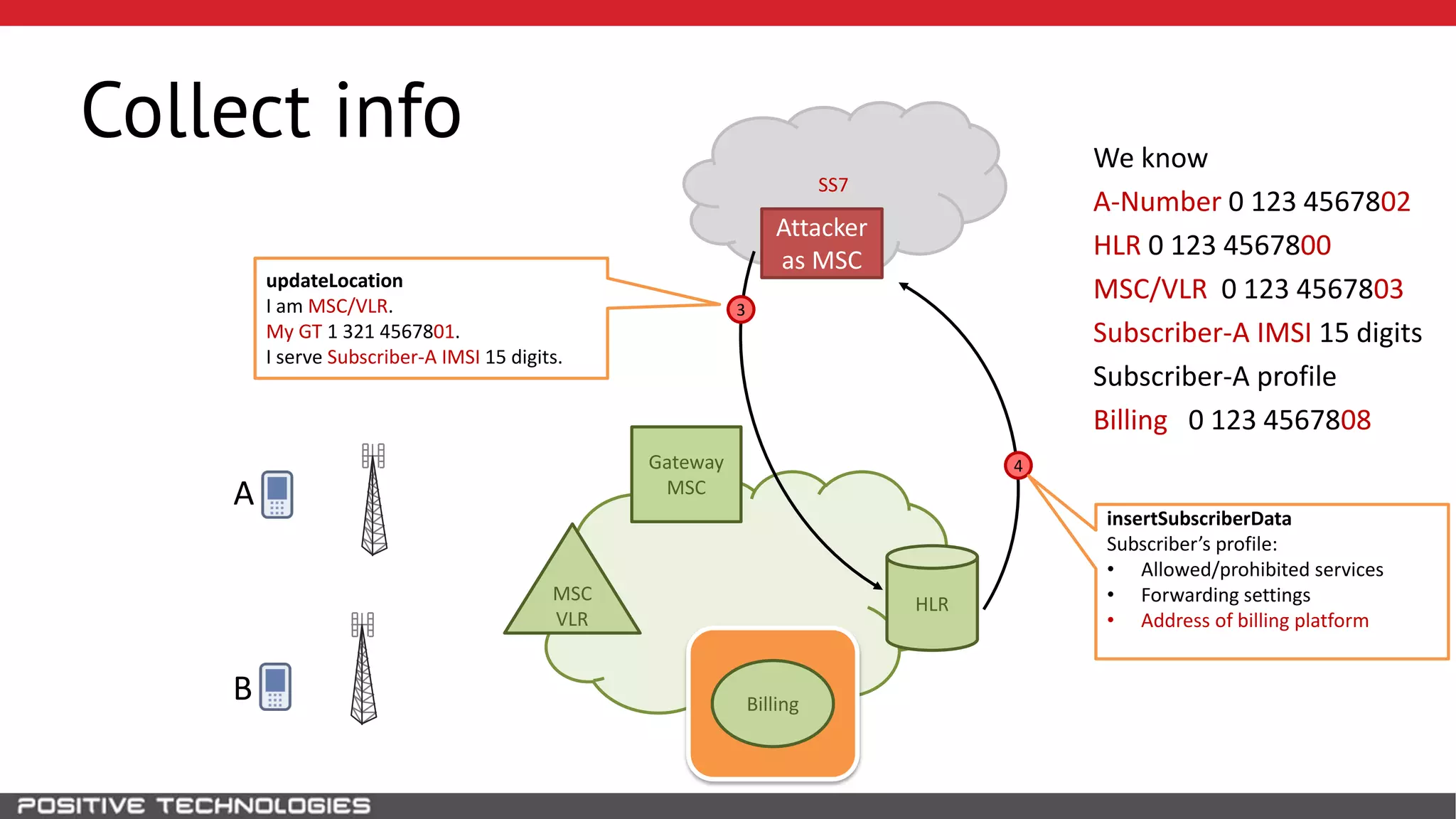
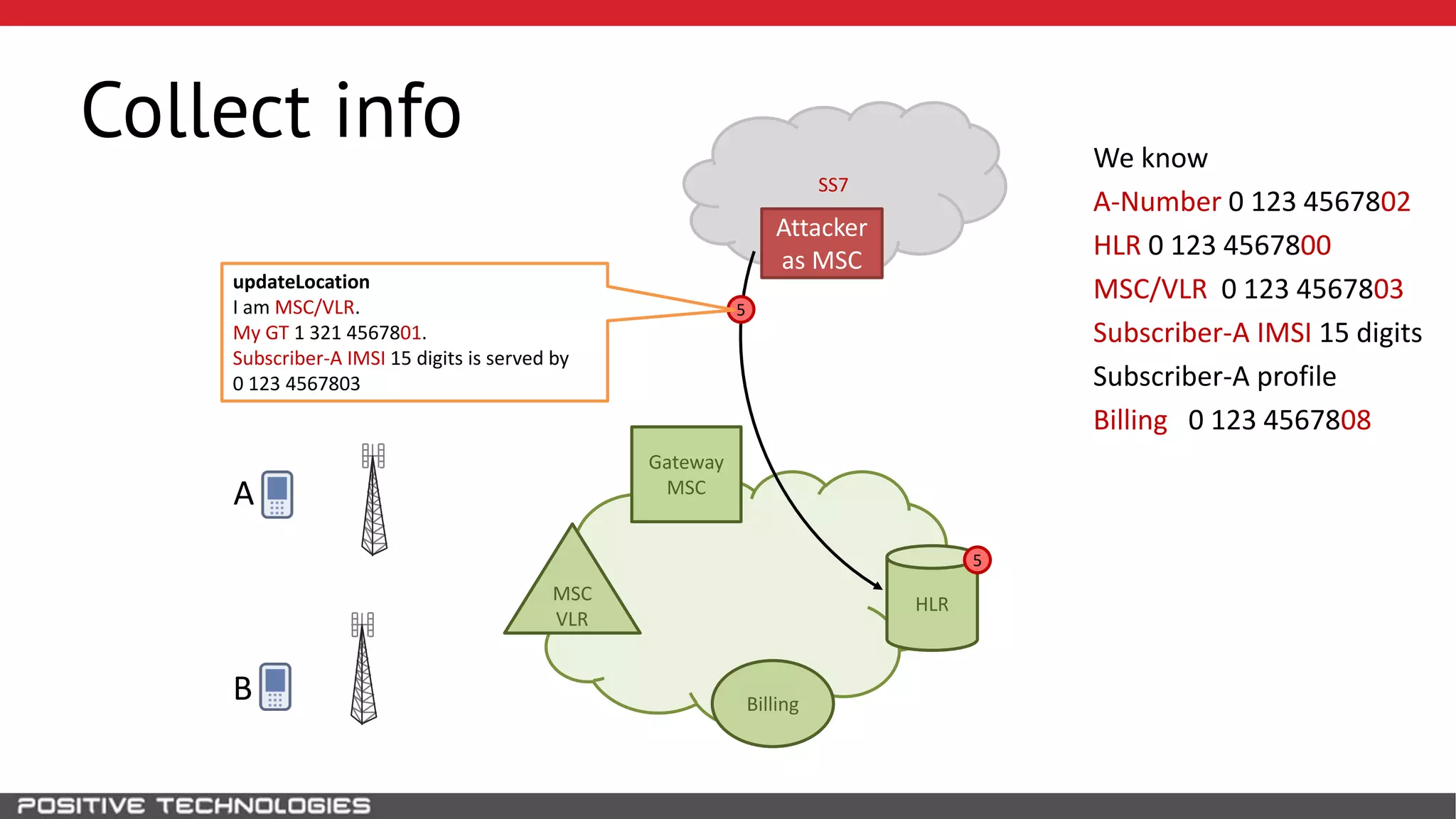
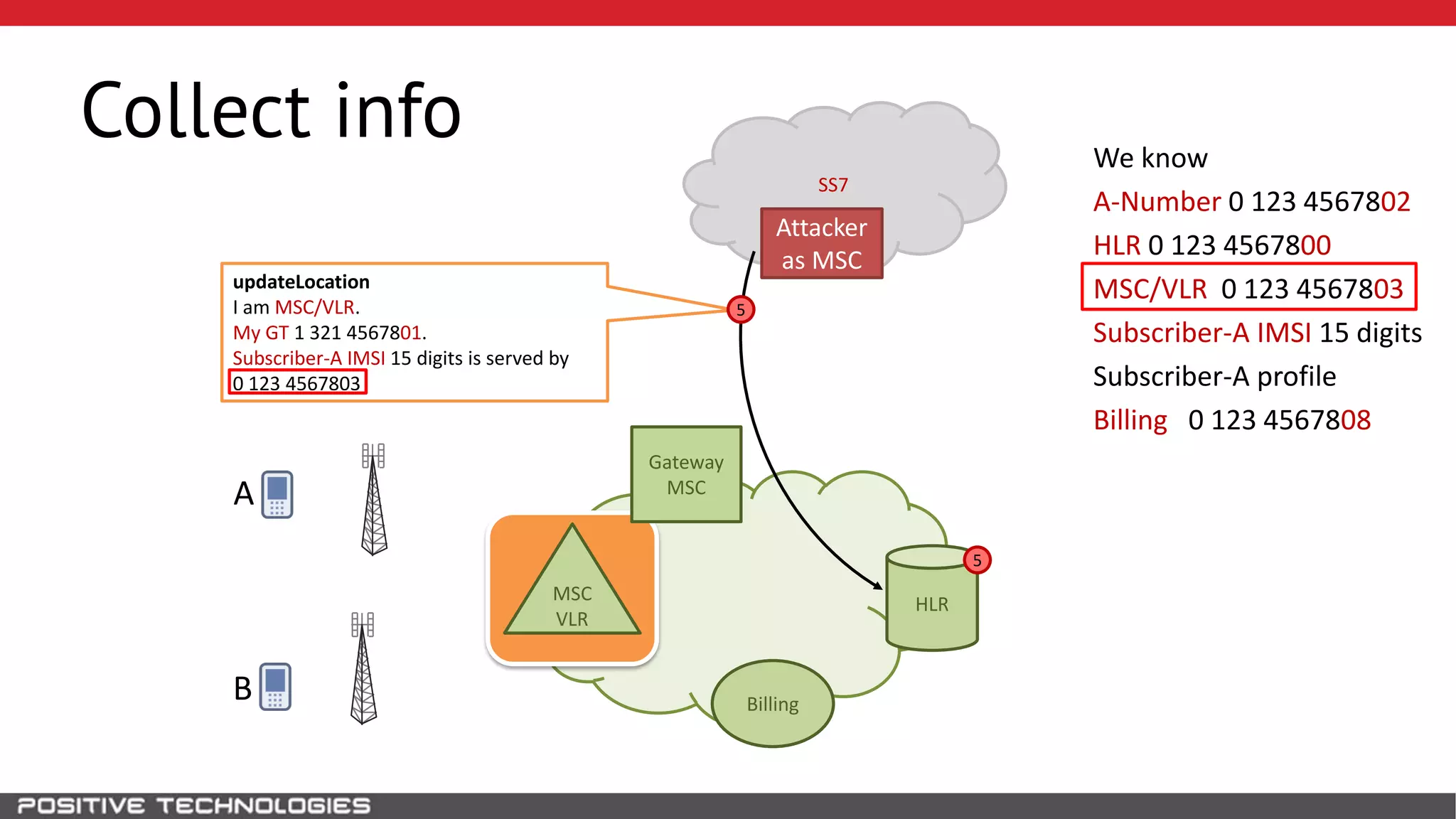
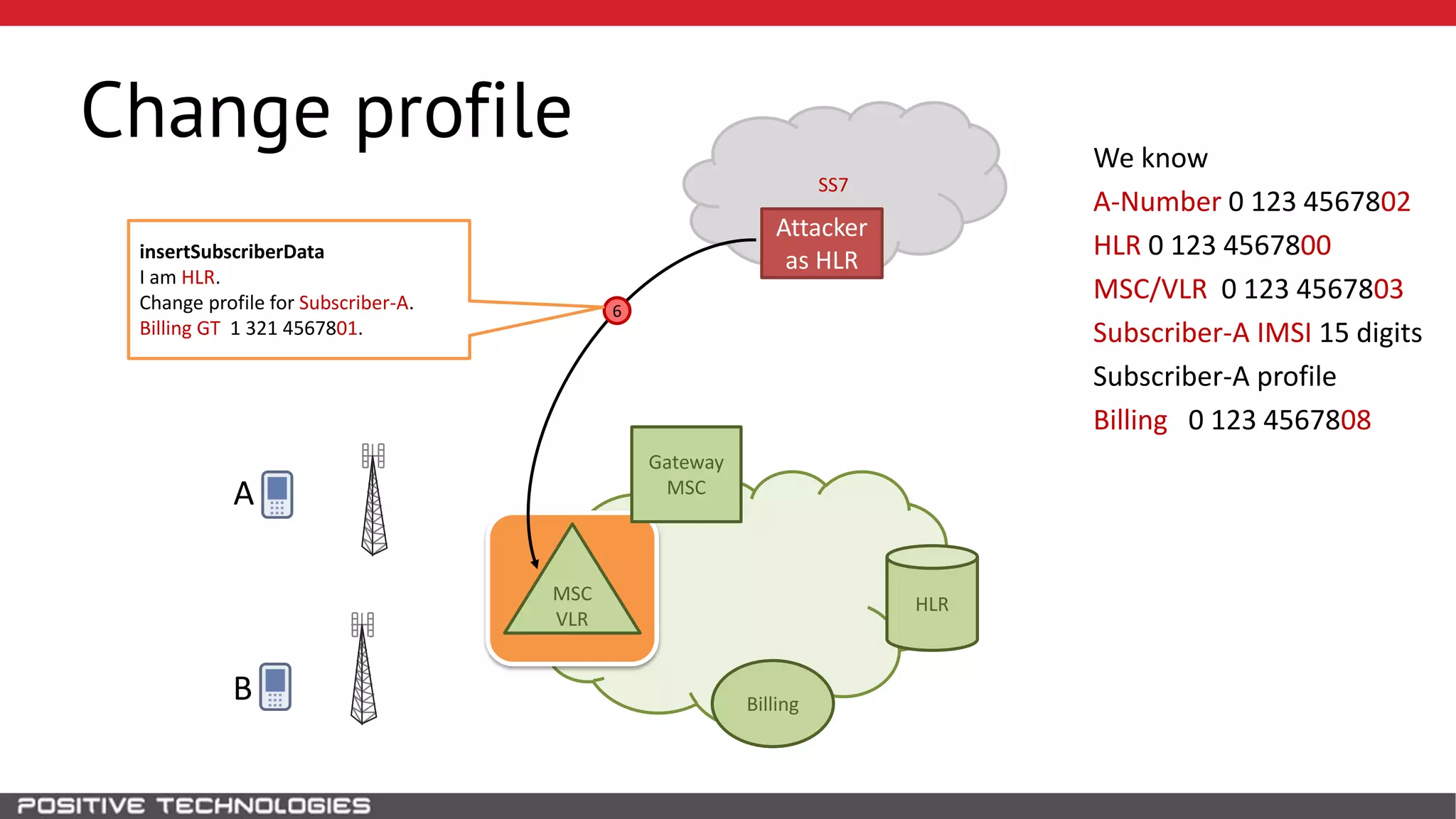
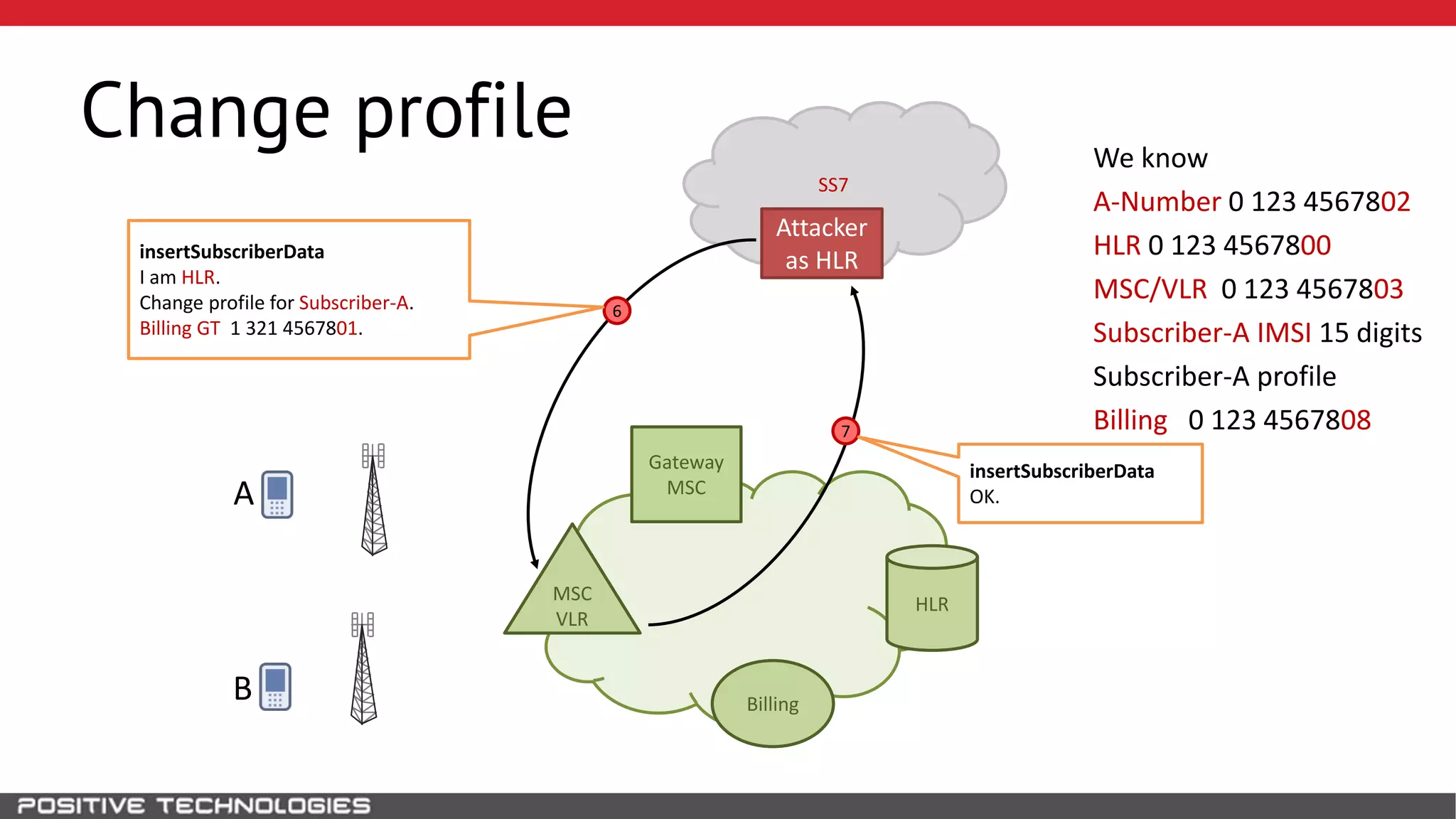
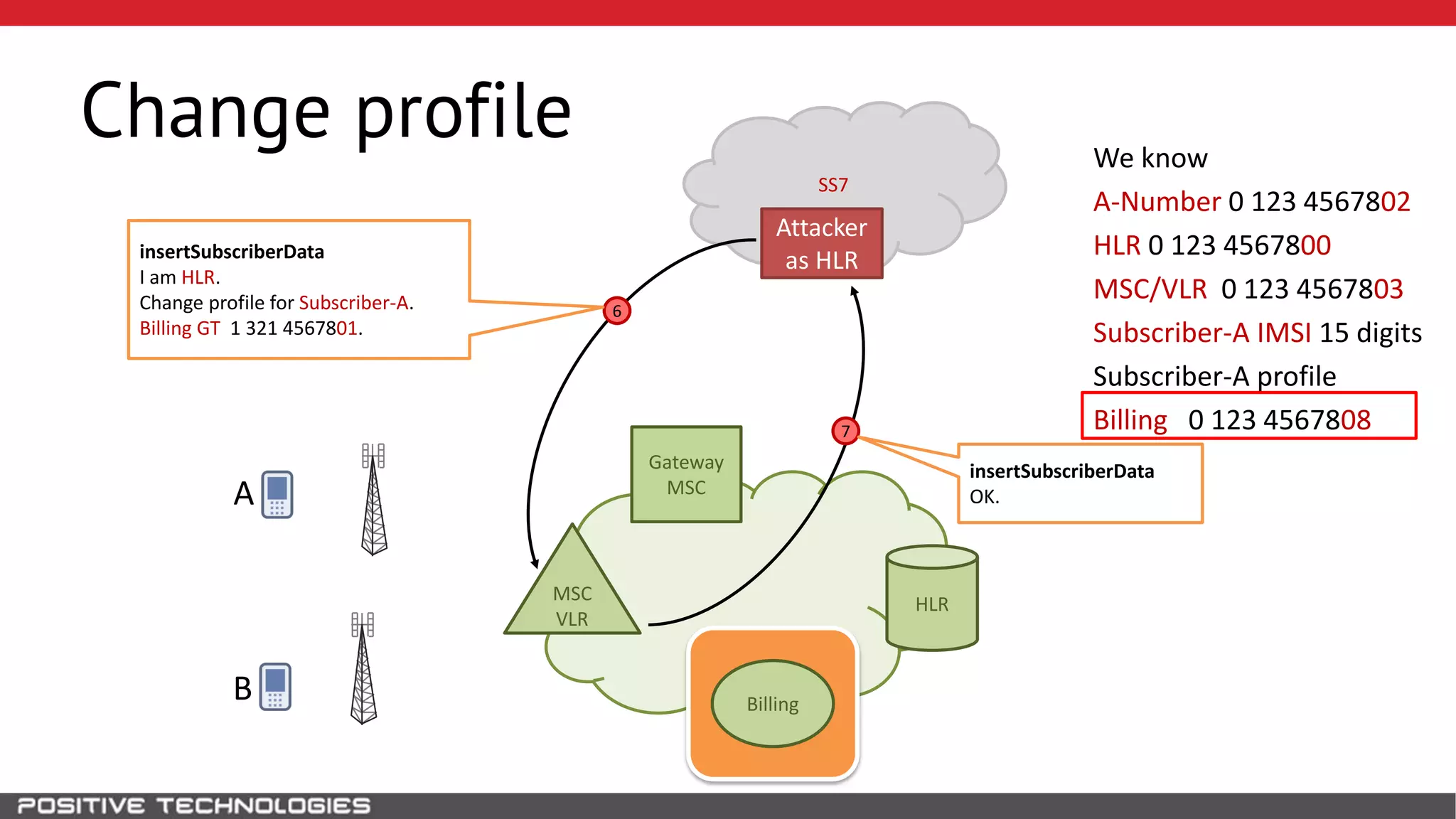
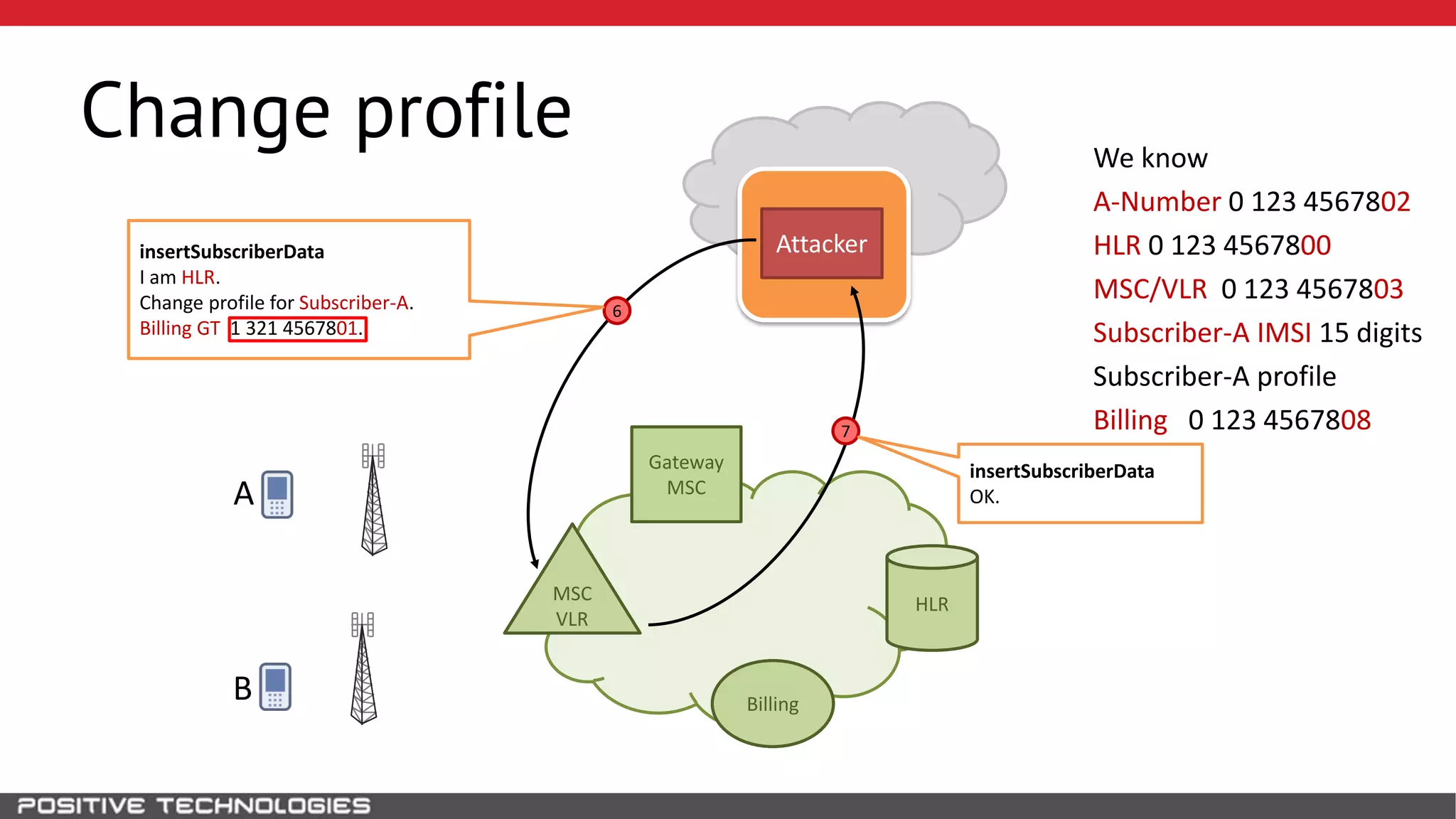
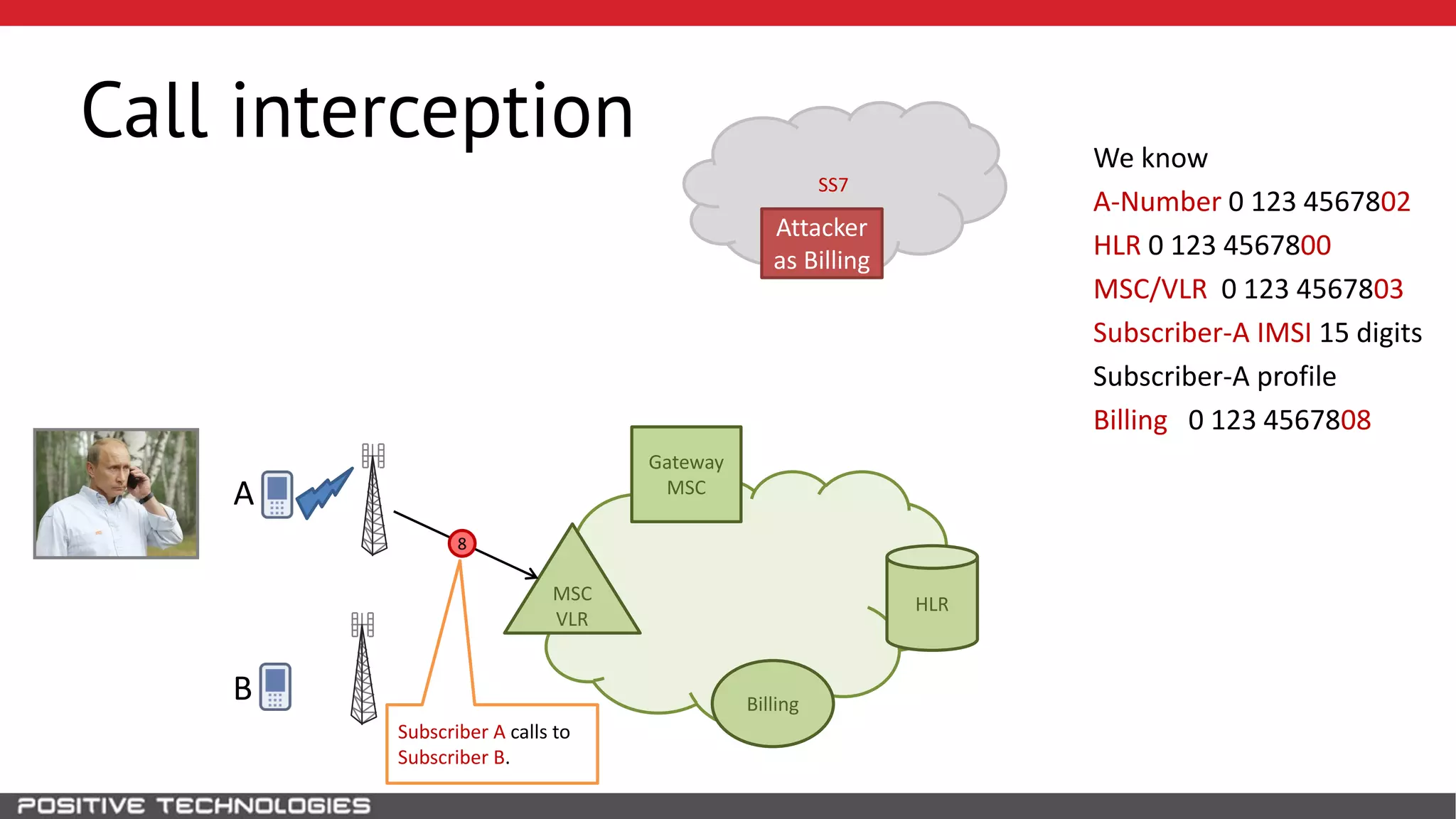
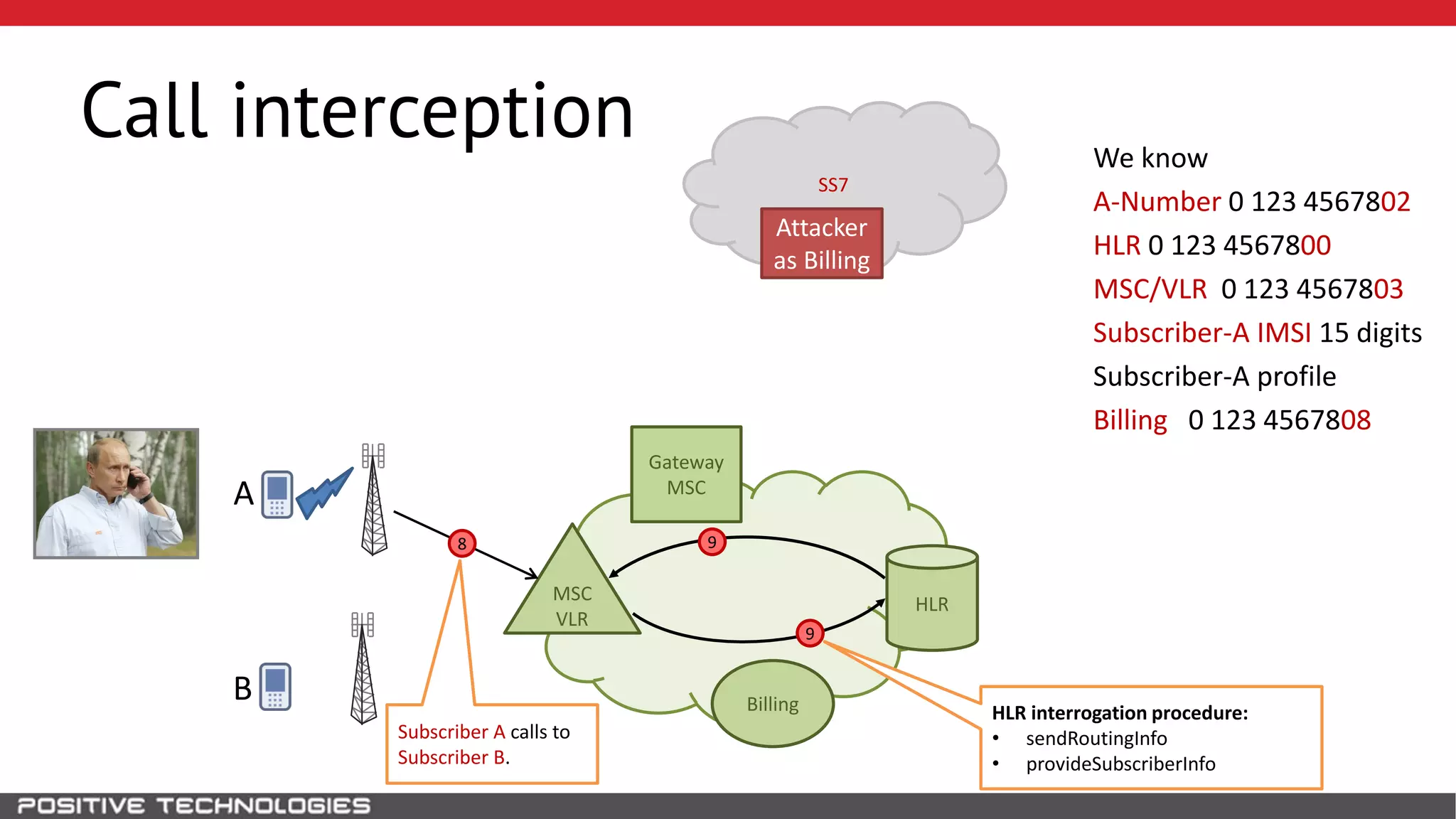
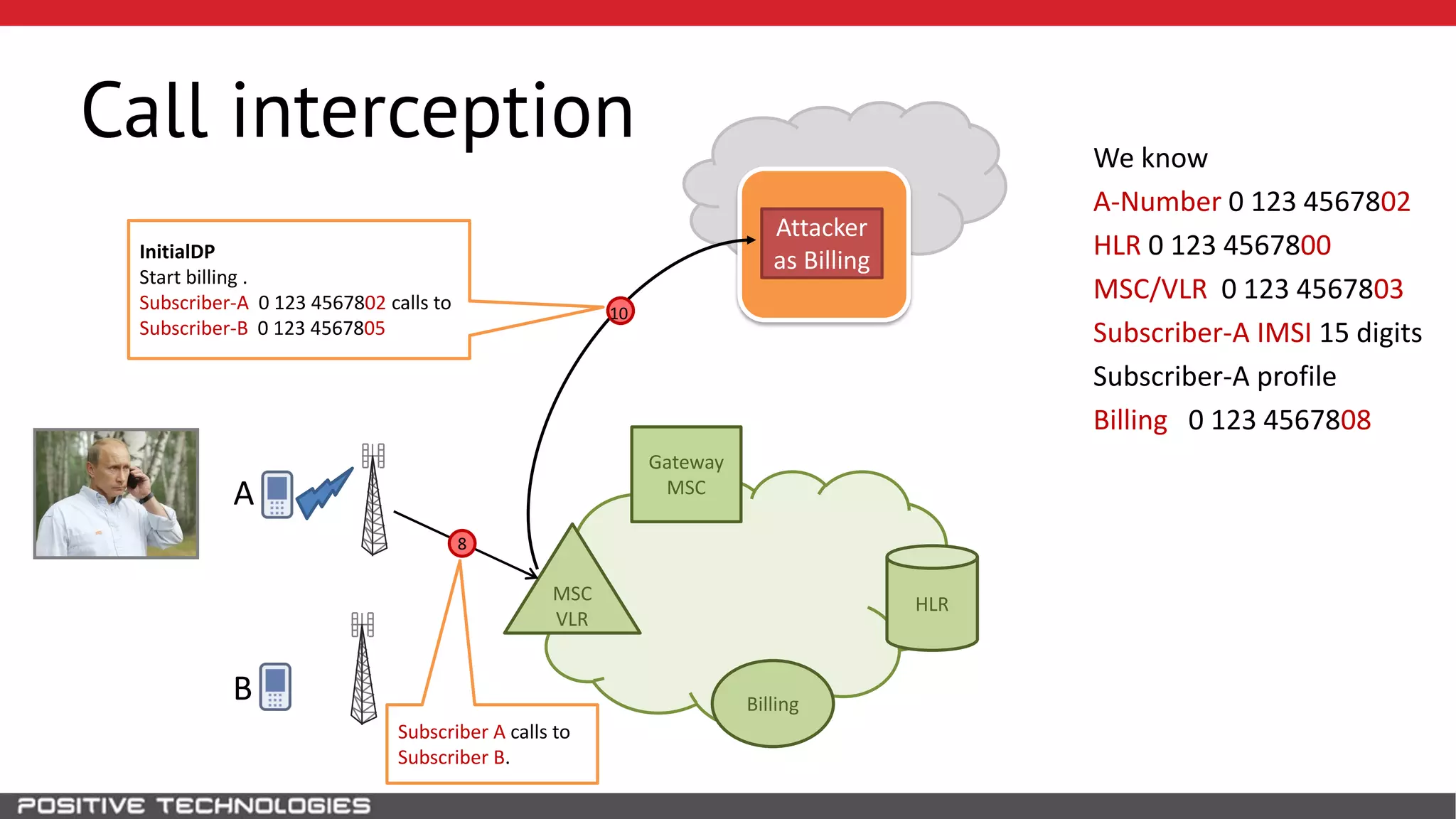
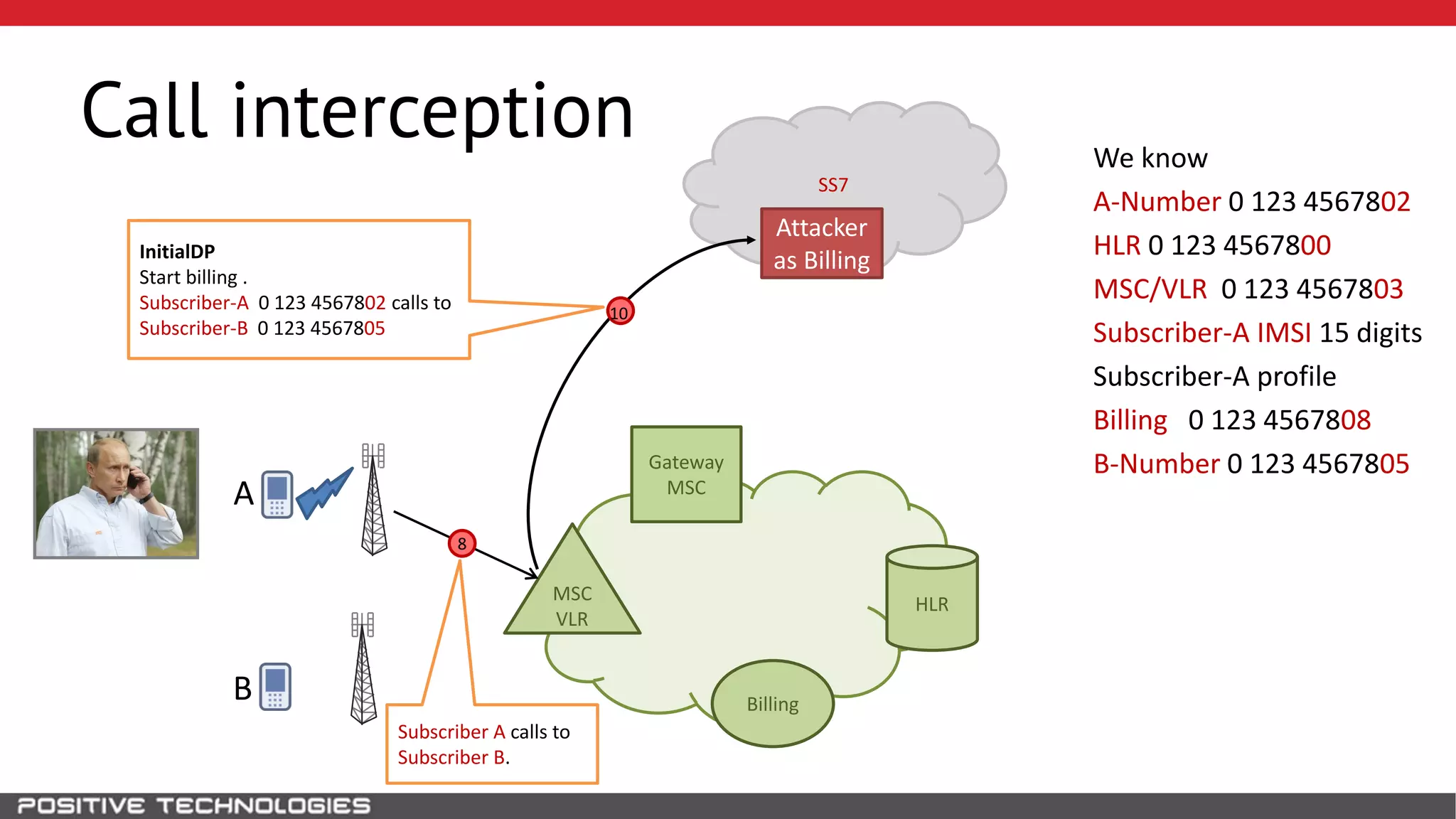
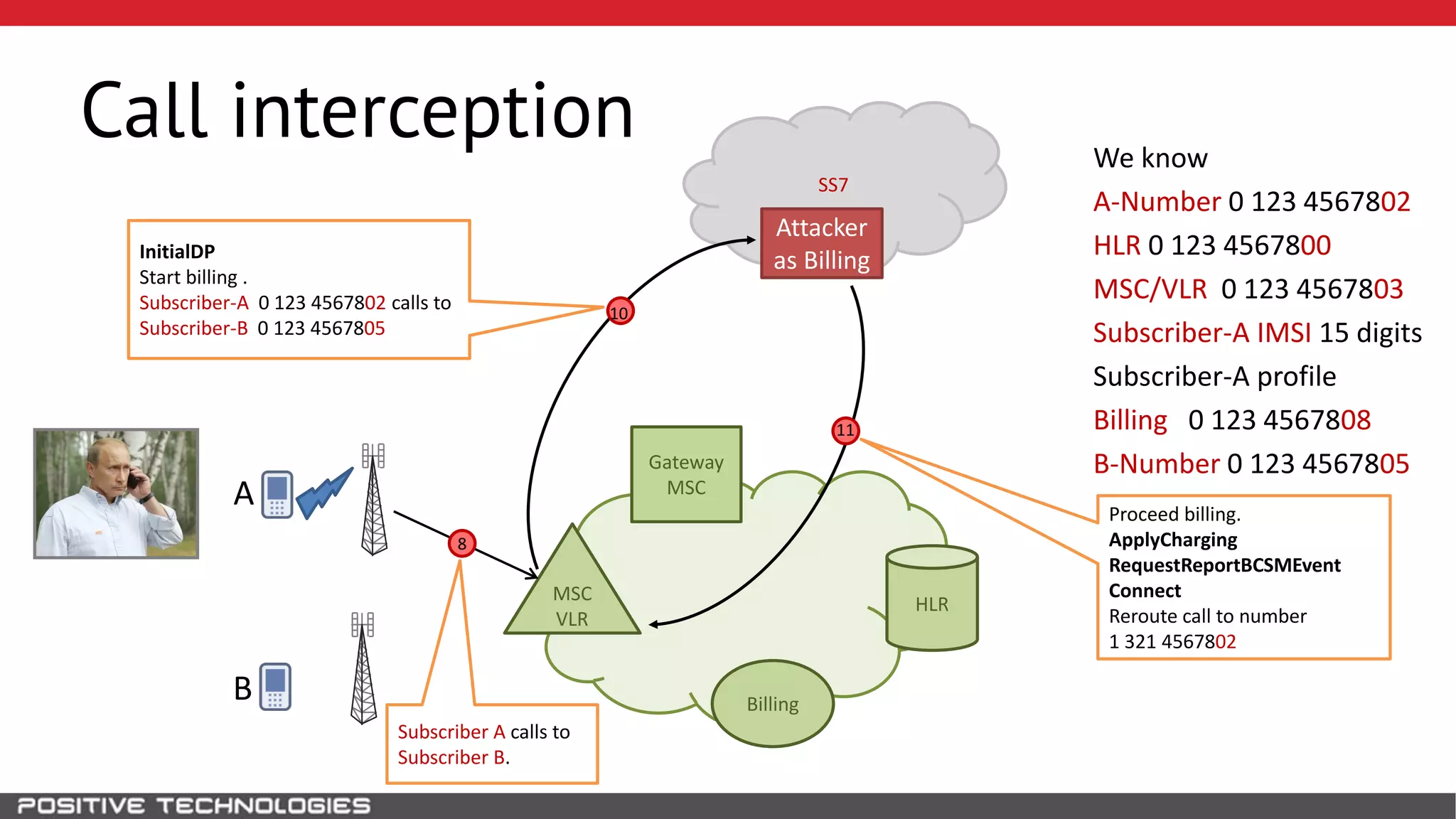
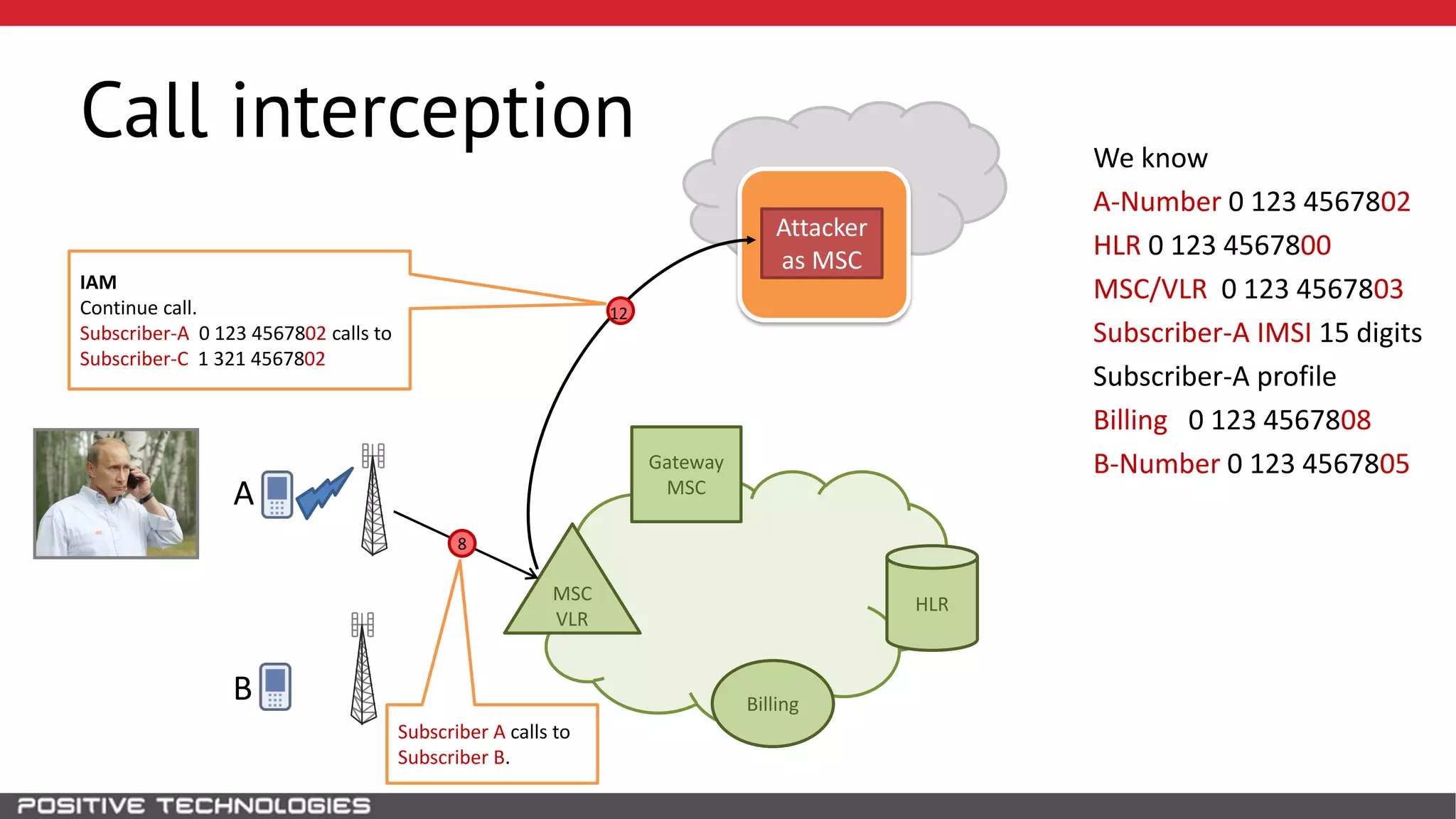
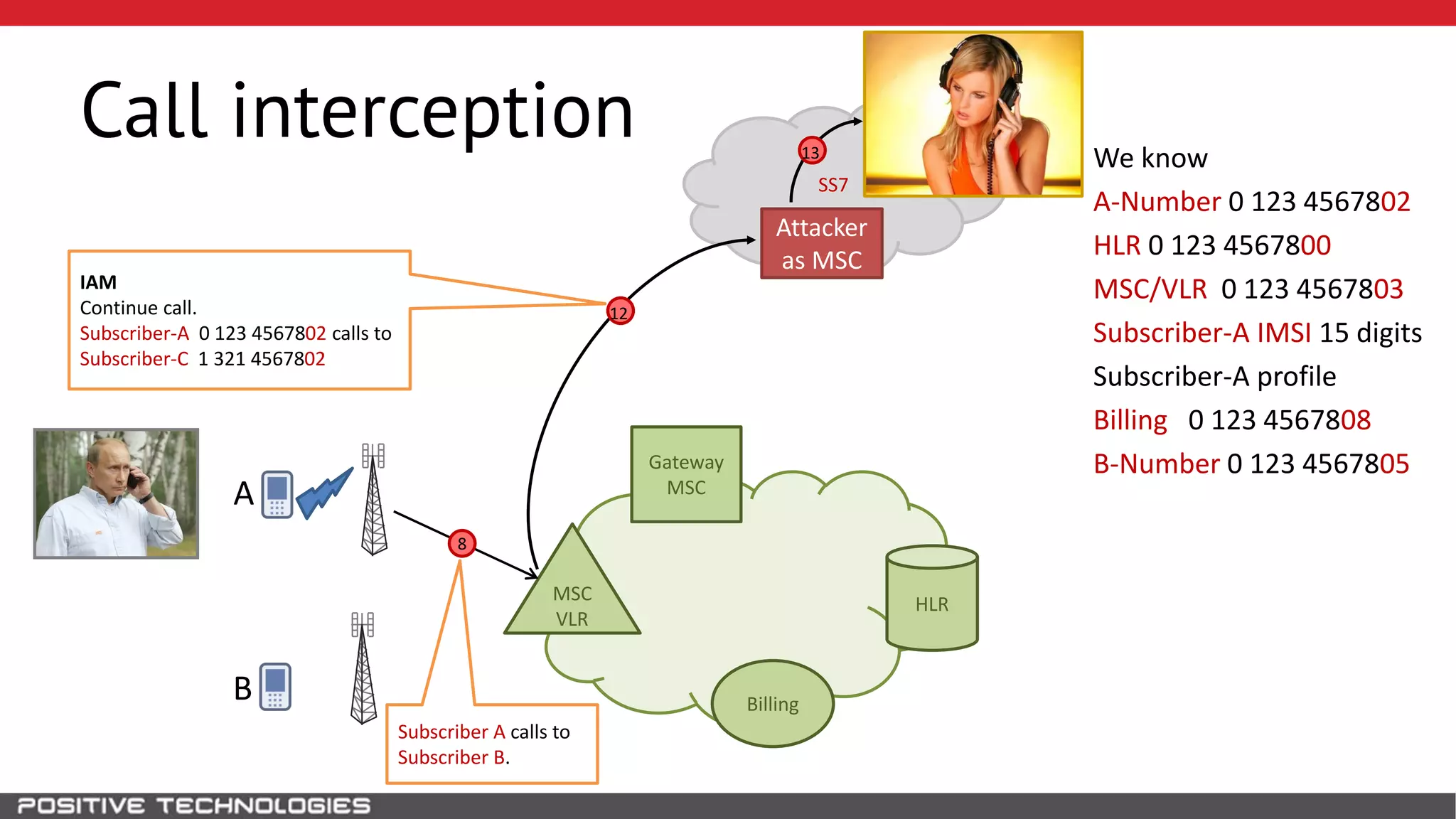
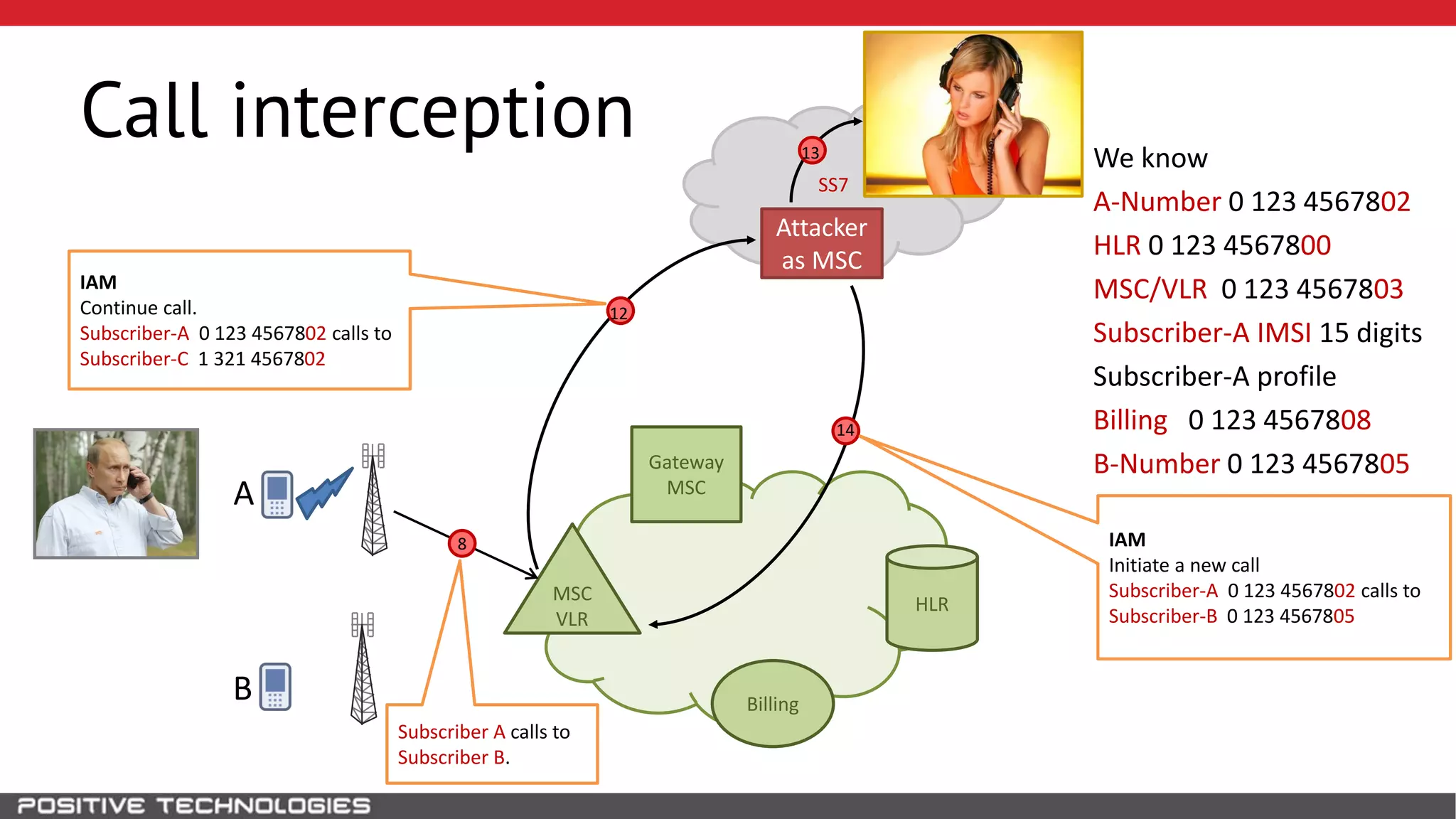
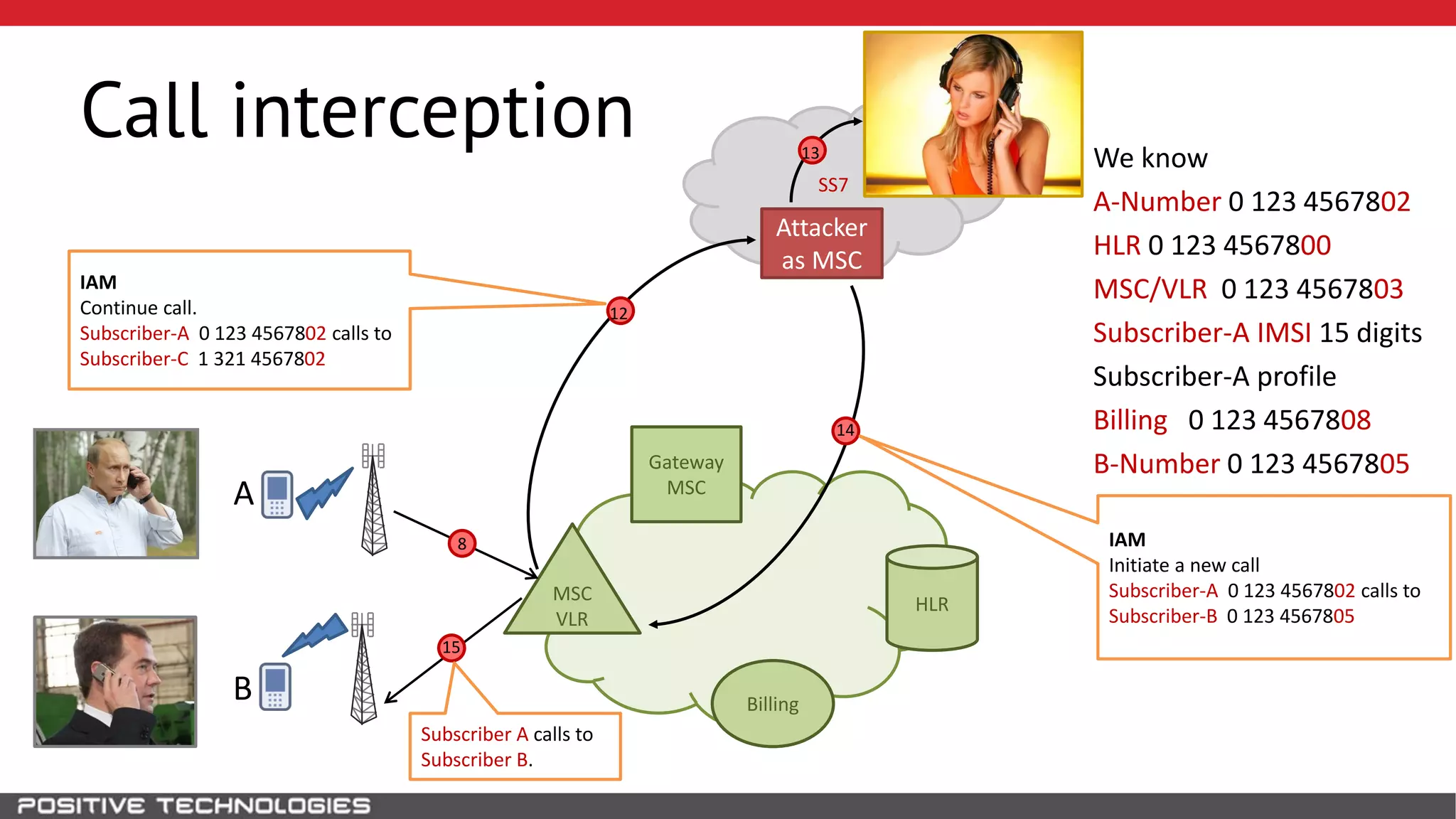
The document describes how to intercept mobile phone conversations and intercept text messages by exploiting vulnerabilities in the SS7 protocol. It explains how to collect a target's private information from the HLR like IMSI and location. It then shows how an attacker can spoof being an MSC or HLR to intercept calls and SMS, or conduct denial of service attacks by monopolizing the network's resources through endless signaling requests. The goal is to illustrate real threats to mobile network security from vulnerabilities in SS7 and inter-network connectivity.