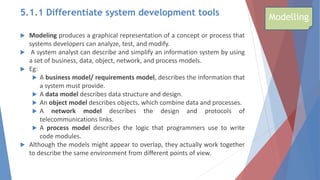
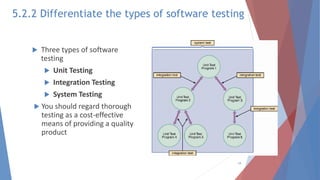
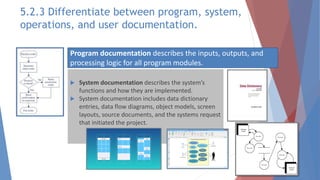
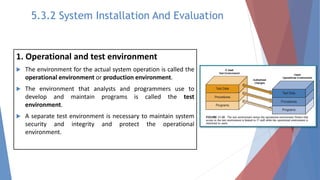
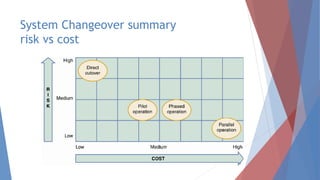
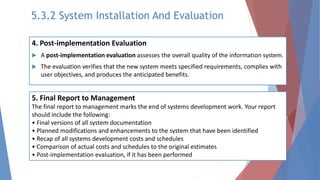
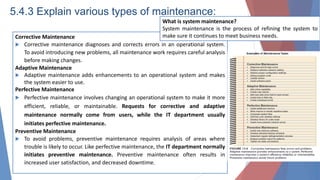
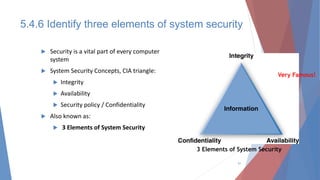
The document outlines key learning outcomes related to system implementation and support, including understanding system development tools, testing in projects, and the importance of documentation. It details various aspects of system analysis and design, such as modeling, prototyping, and the coding process, as well as types of software testing and the steps in system implementation. Additionally, it addresses system support, security, and maintenance, emphasizing user training and help desk functions.