Embed presentation
Download as PDF, PPTX


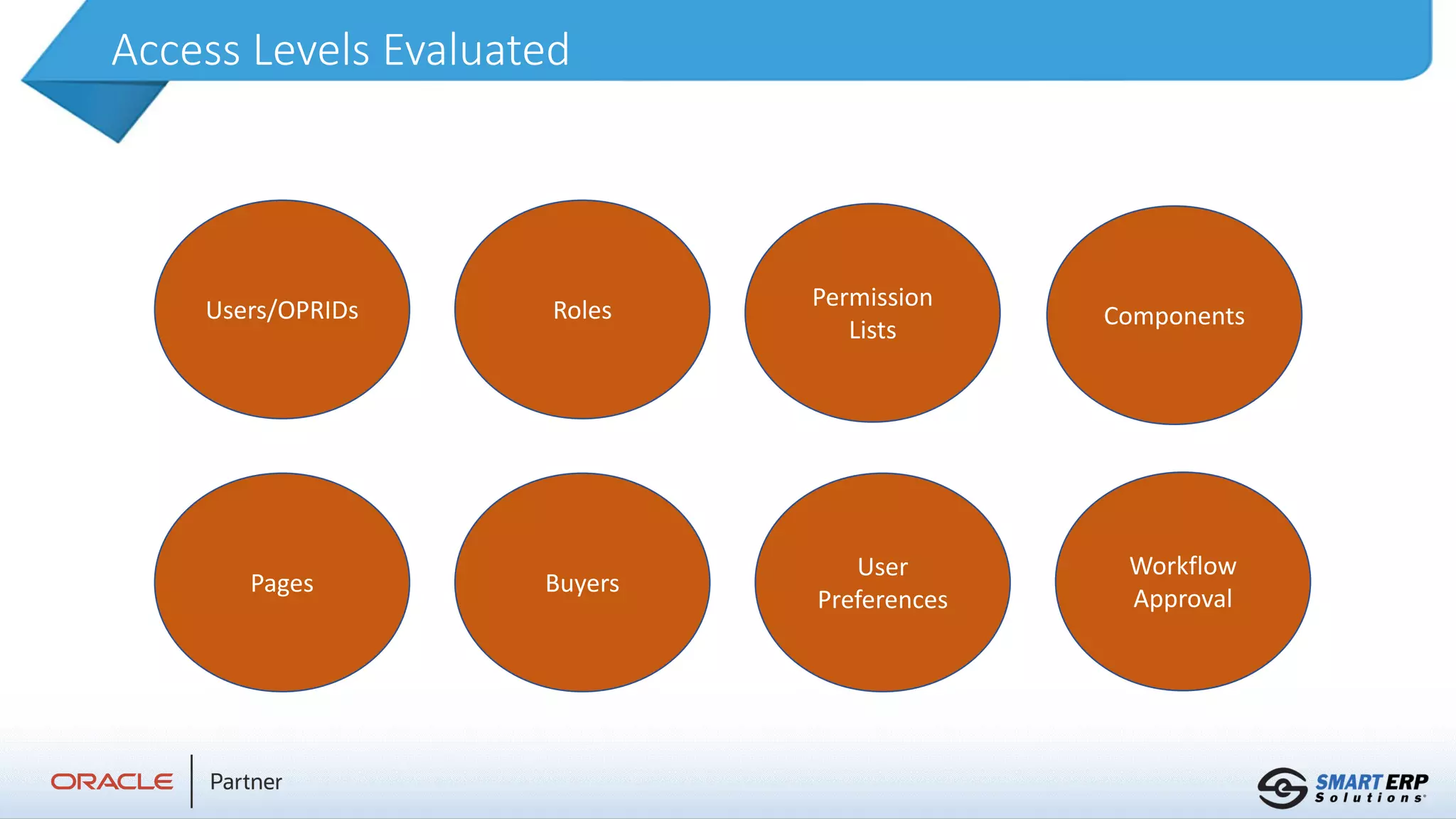

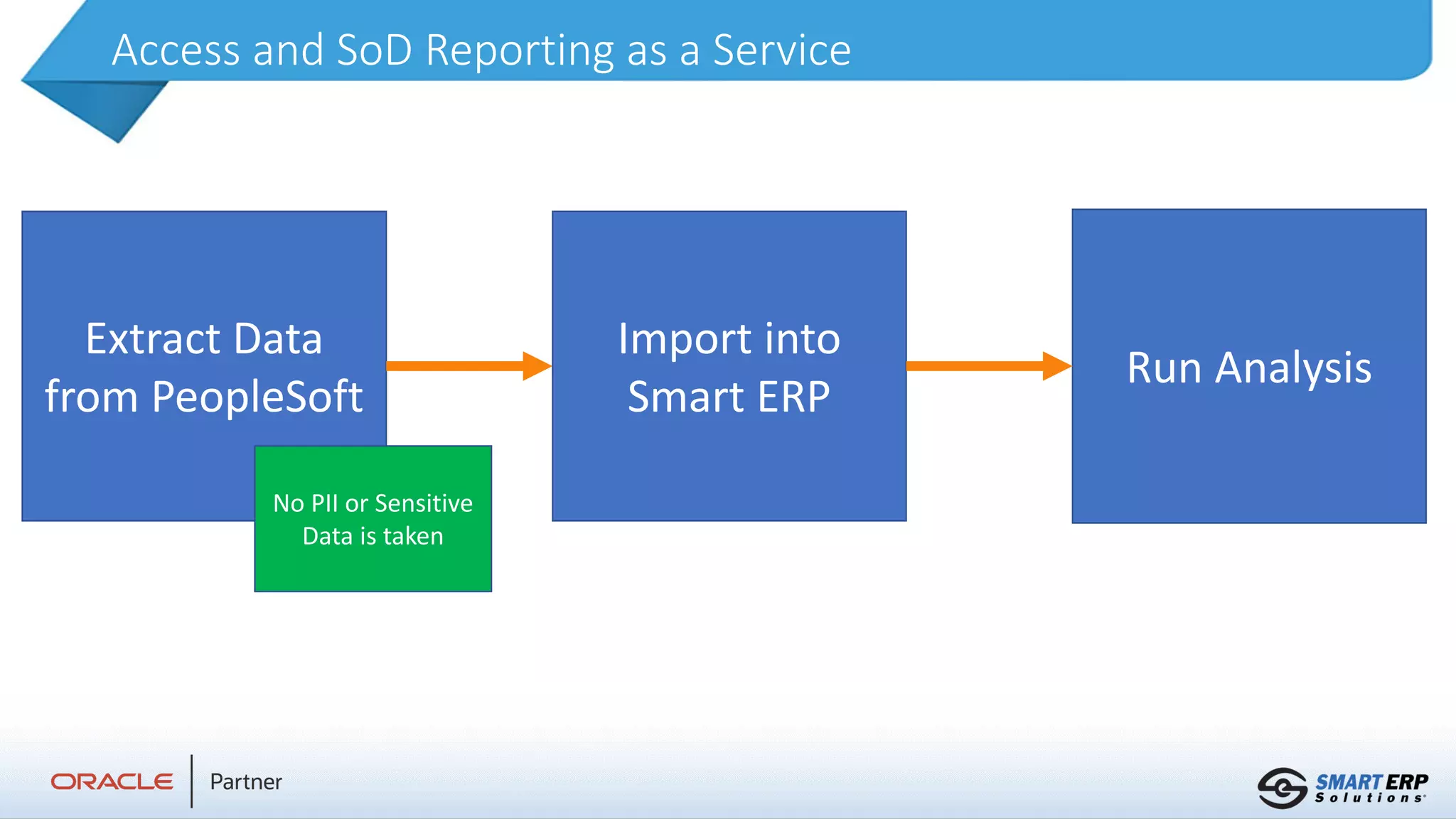




Lewis Hopkins, a senior applications consultant with 12 years of experience in governance, risk, and compliance, provides insights into smart ERP security services. The document outlines analysis and reporting on access and segregation of duties, customizations, and reporting services aimed at enhancing data security and compliance for organizations. It emphasizes the ability to tailor rules for different organizations while maintaining oversight on sensitive data access.










