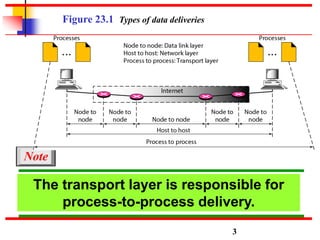
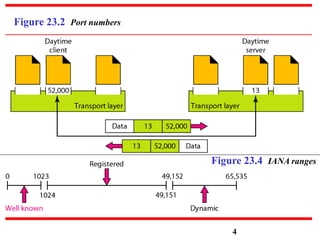
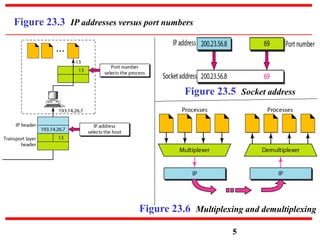
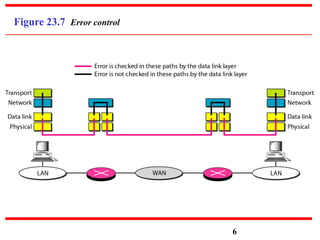
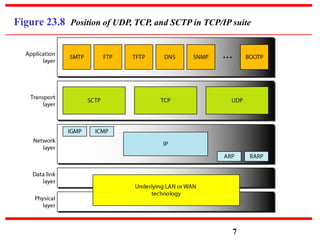
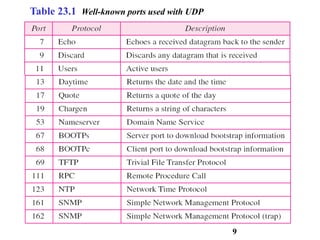
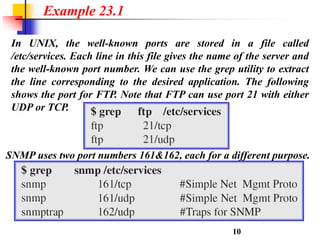
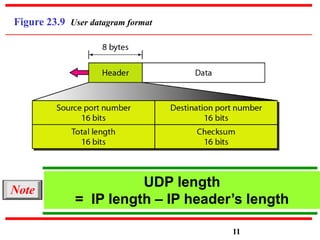
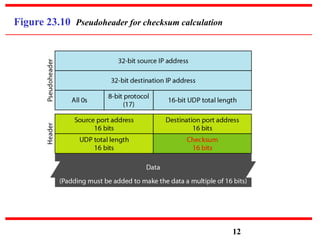
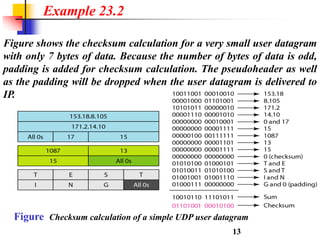
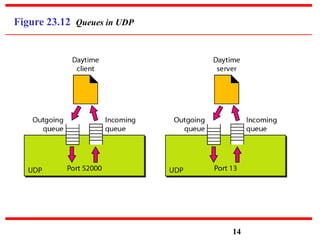
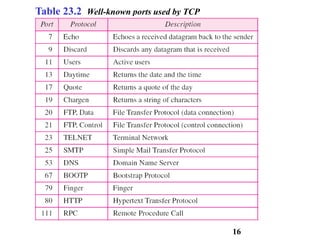
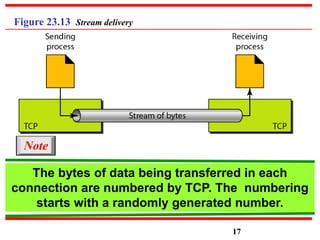
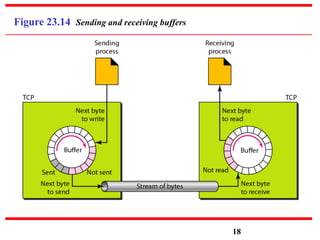
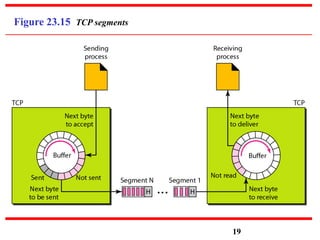
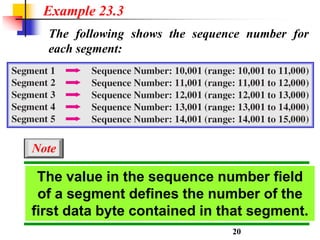
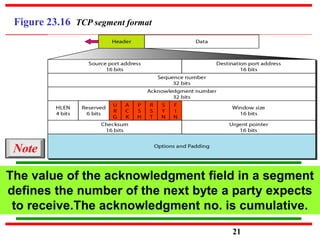
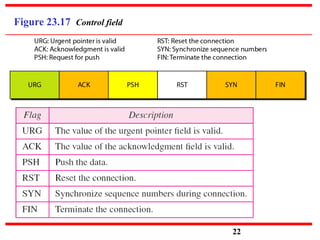
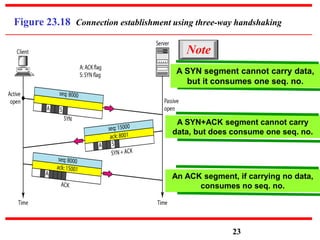
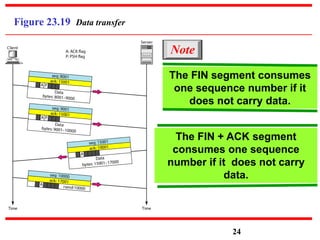
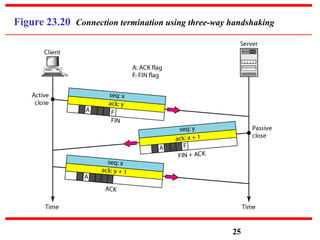
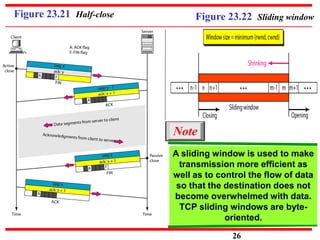
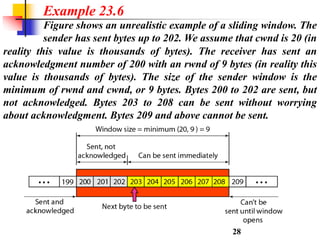
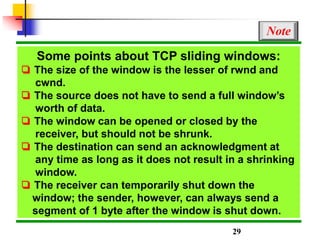
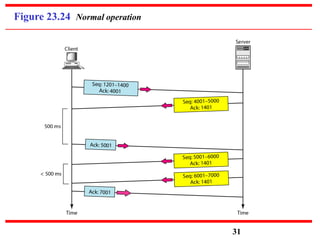
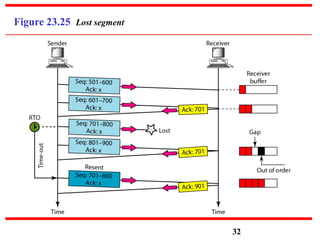
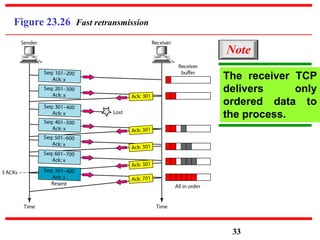
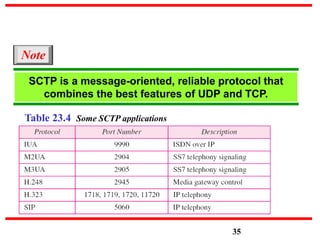
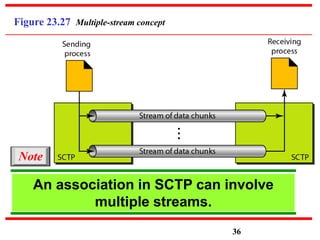
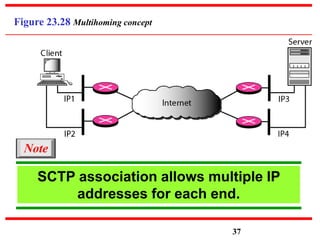
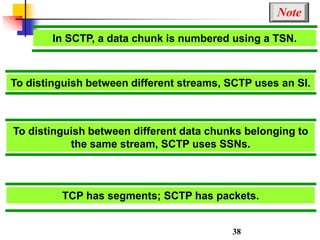
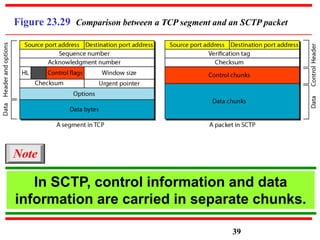
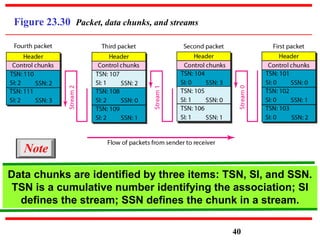
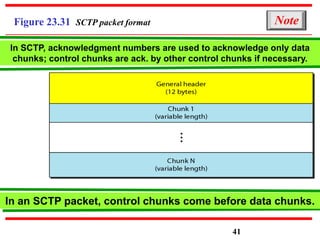
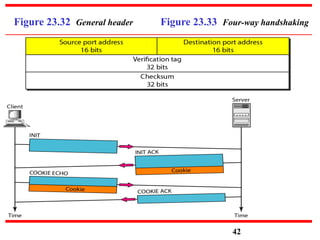
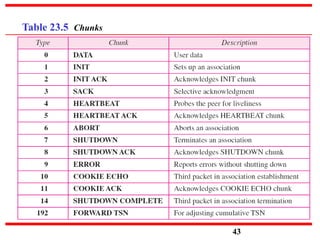
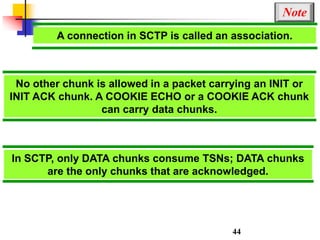
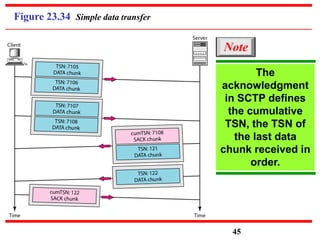
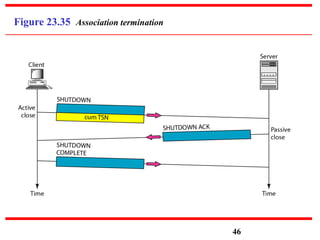
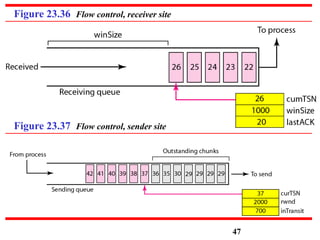
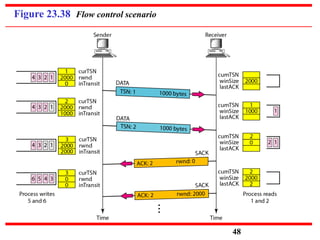
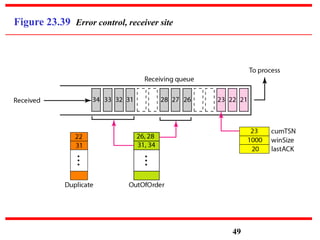
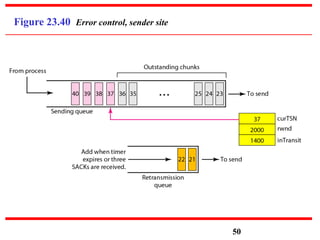
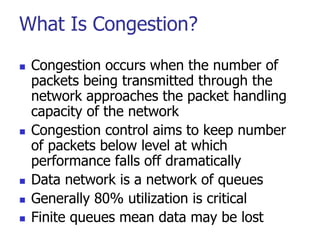
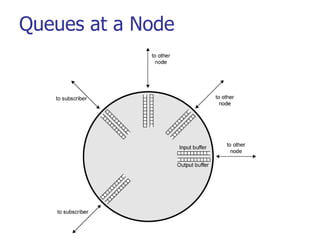
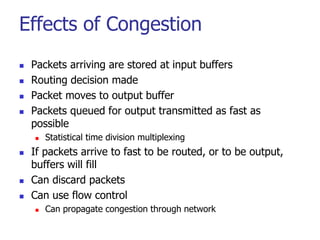
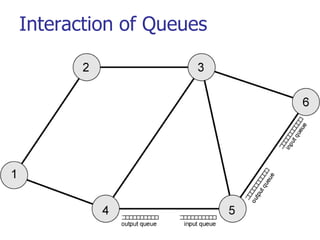
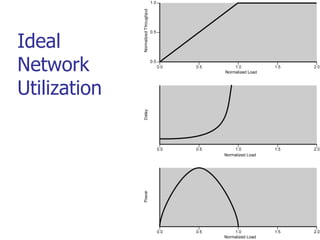
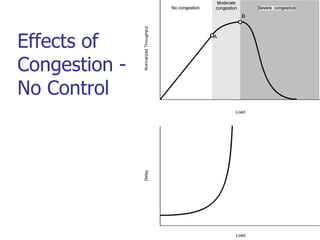
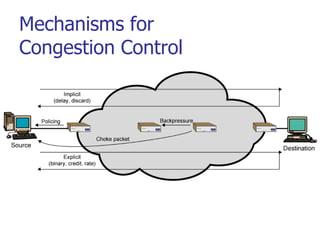
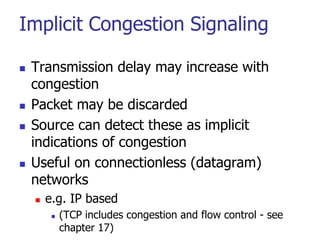
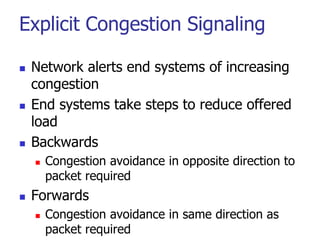
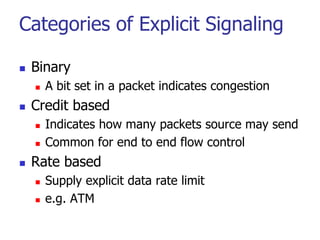
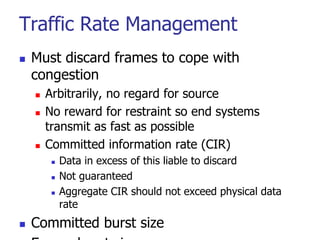
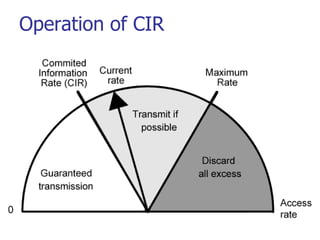
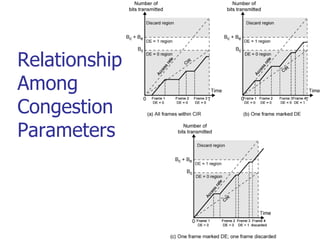
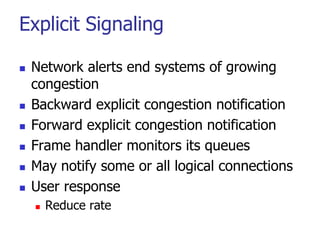
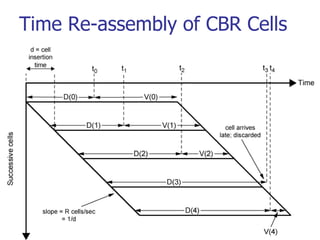
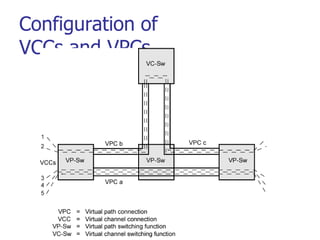
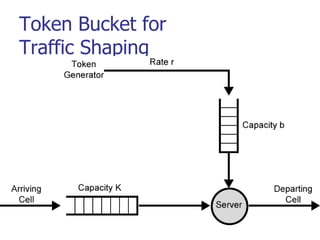
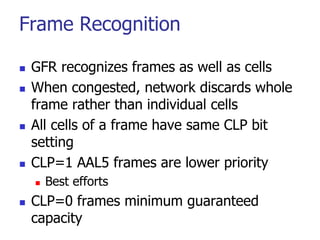
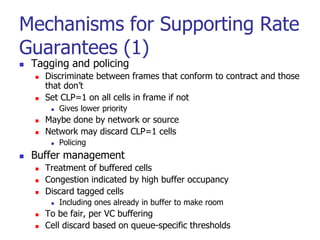
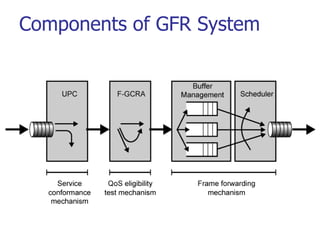
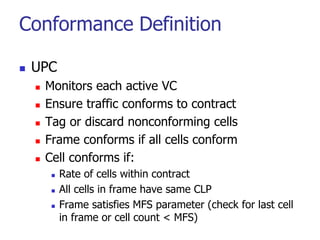
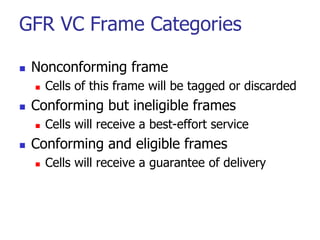
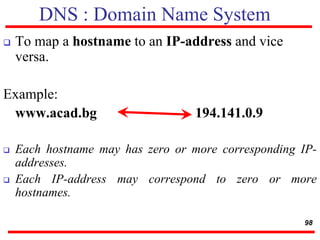
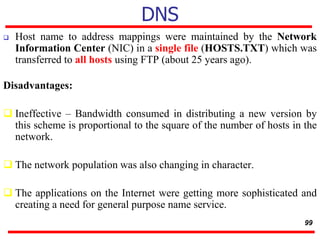
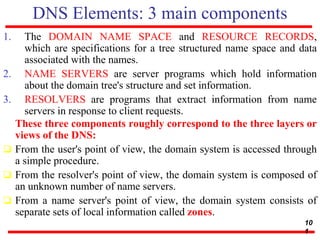
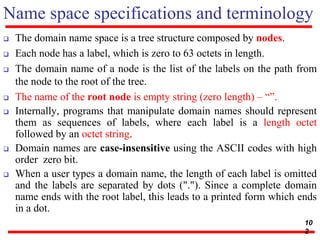
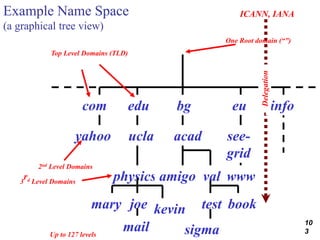
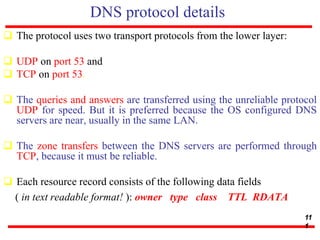
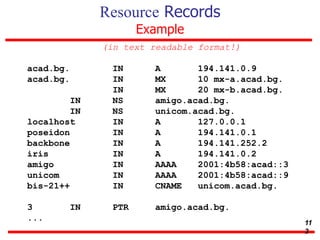
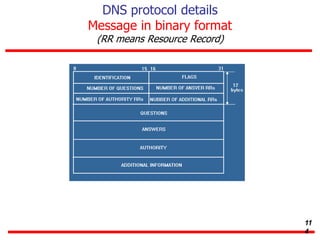
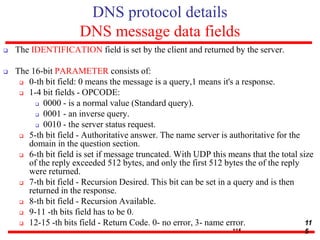
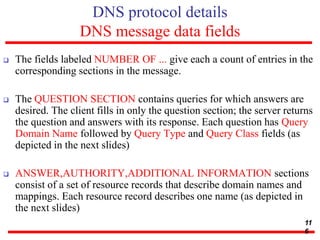
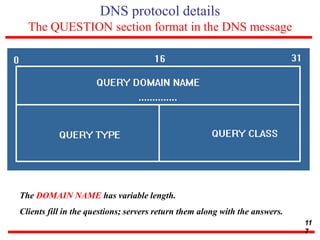
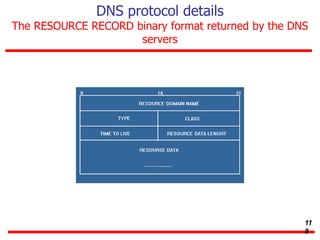
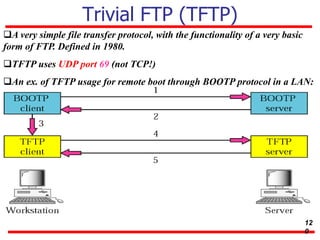
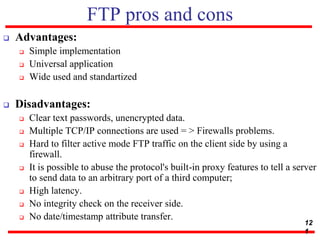
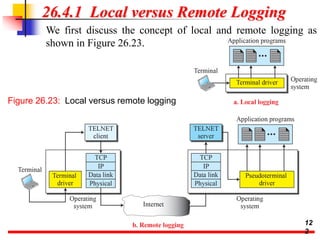
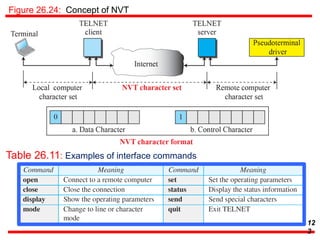
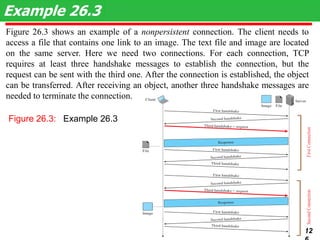
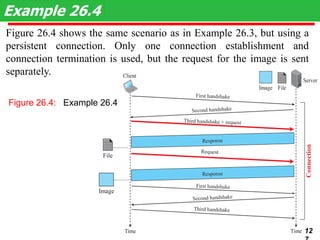
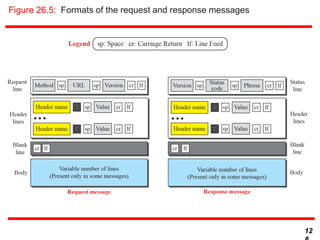
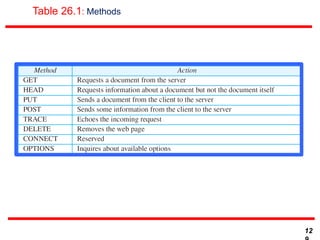
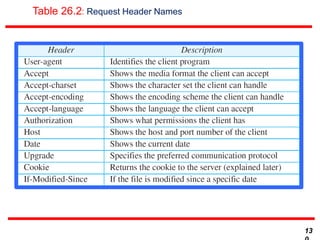
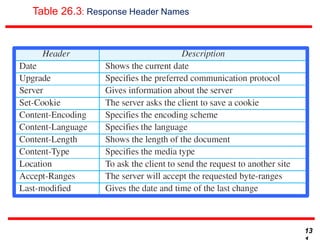
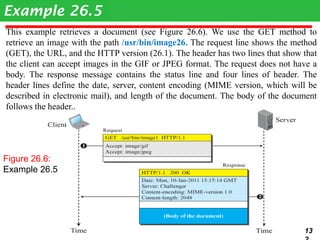
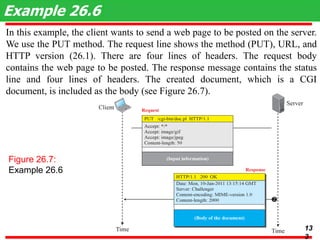
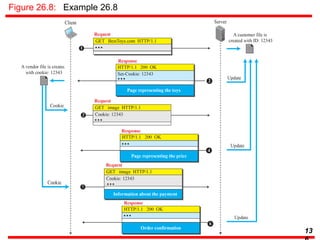
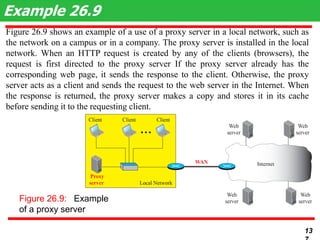
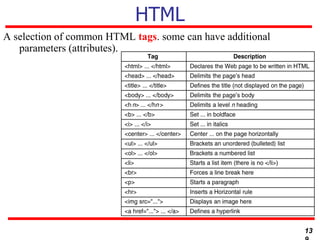
This document discusses various transport and application layer protocols. It covers process-to-process delivery at the transport layer using UDP and TCP. UDP is a connectionless, unreliable protocol while TCP provides reliable, connection-oriented delivery. It also discusses the Stream Control Transmission Protocol (SCTP) which is a newer message-oriented protocol. The document contains diagrams and examples to illustrate concepts like multiplexing, demultiplexing, segments, connections, and congestion control mechanisms.