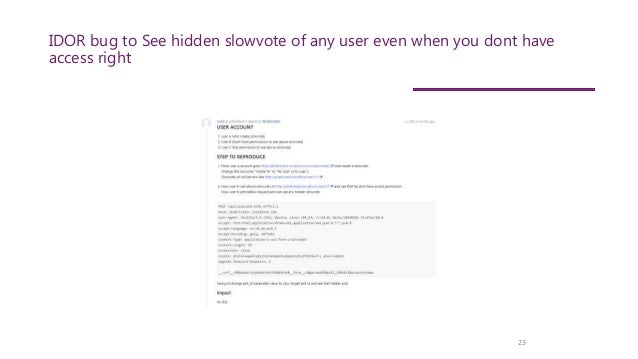
The document discusses a talk focused on hacking and securing RESTful APIs, aimed at developers familiar with API structures and common vulnerabilities. It highlights various security flaws, particularly through the lens of the OWASP API Security Top 10, and explains techniques for testing API security by manipulating requests to identify weaknesses. Notable vulnerabilities include insecure direct object references (IDOR) and excessive data exposure, emphasizing the importance of understanding potential security risks in API responses.


















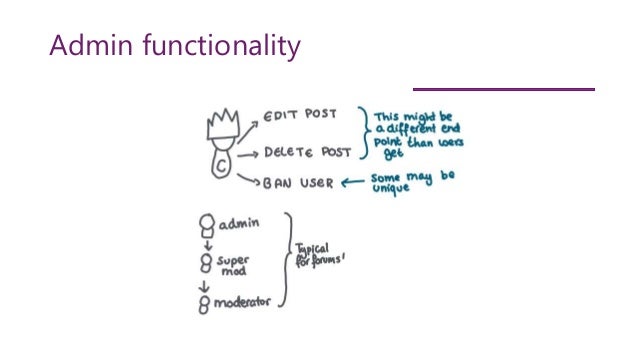

![[IDOR] Deleting other people's tasks
22](https://image.slidesharecdn.com/kpfslides-220416024305/95/2022-APIsecure_Go-Hack-Yourself-API-Hacking-for-Beginners-22-638.jpg)